| File name: | Sixaxis Toolkit.zip |
| Full analysis: | https://app.any.run/tasks/6bb98f49-a424-4fcd-896c-3ed8575ee543 |
| Verdict: | Malicious activity |
| Analysis date: | December 19, 2021, 16:03:47 |
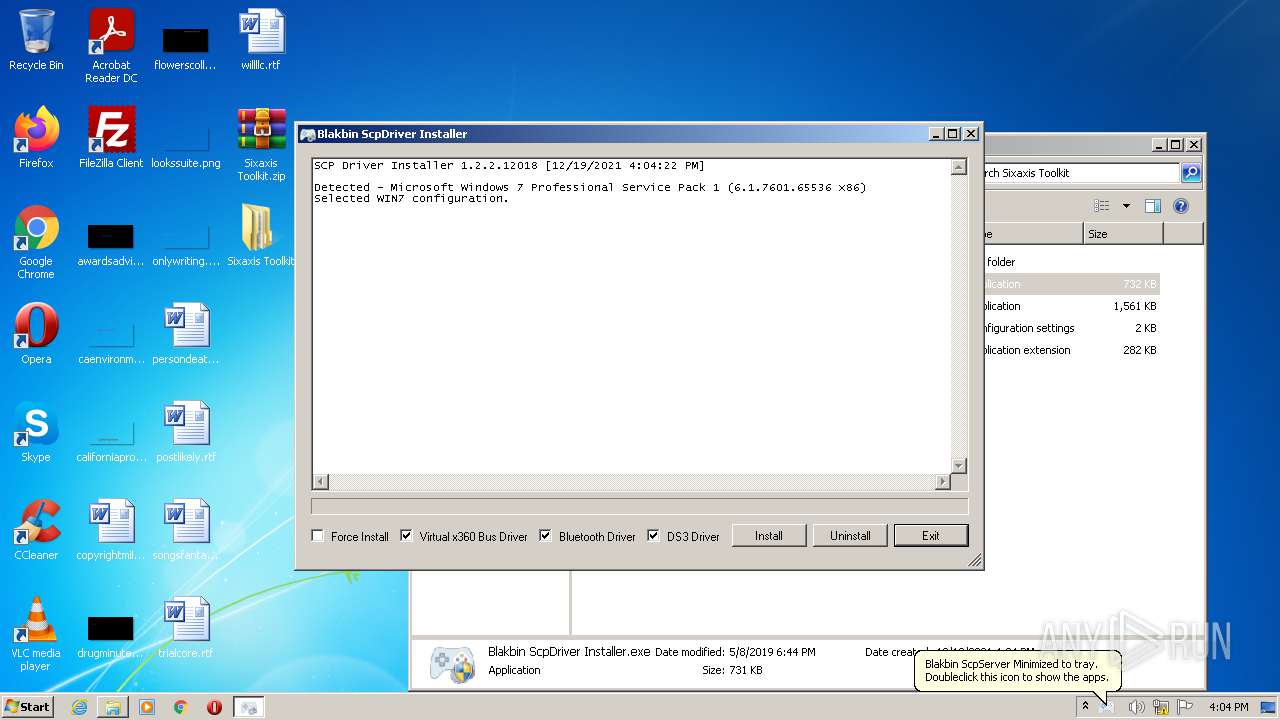
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | FC51B6D72C1DC78F821A4D16A01A82CB |
| SHA1: | 7407BF4E66D3DAEC9FDF015D5E3B3F6D2A8326FA |
| SHA256: | 9DF4D2DB8F3AE775C2EC7B2D89F54081D7BA363F96AD691461EB822AA54E57B1 |
| SSDEEP: | 196608:SkrBGizoFi5d3PotQvWiqCG+d74tXnv1+Weeva9oaJ+kgUzASOGqK8vsh:Skr9z4gd3rkQUtf1+caSaRZ8Sd8w |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 3288)
- Blakbin ScpServer.exe (PID: 804)
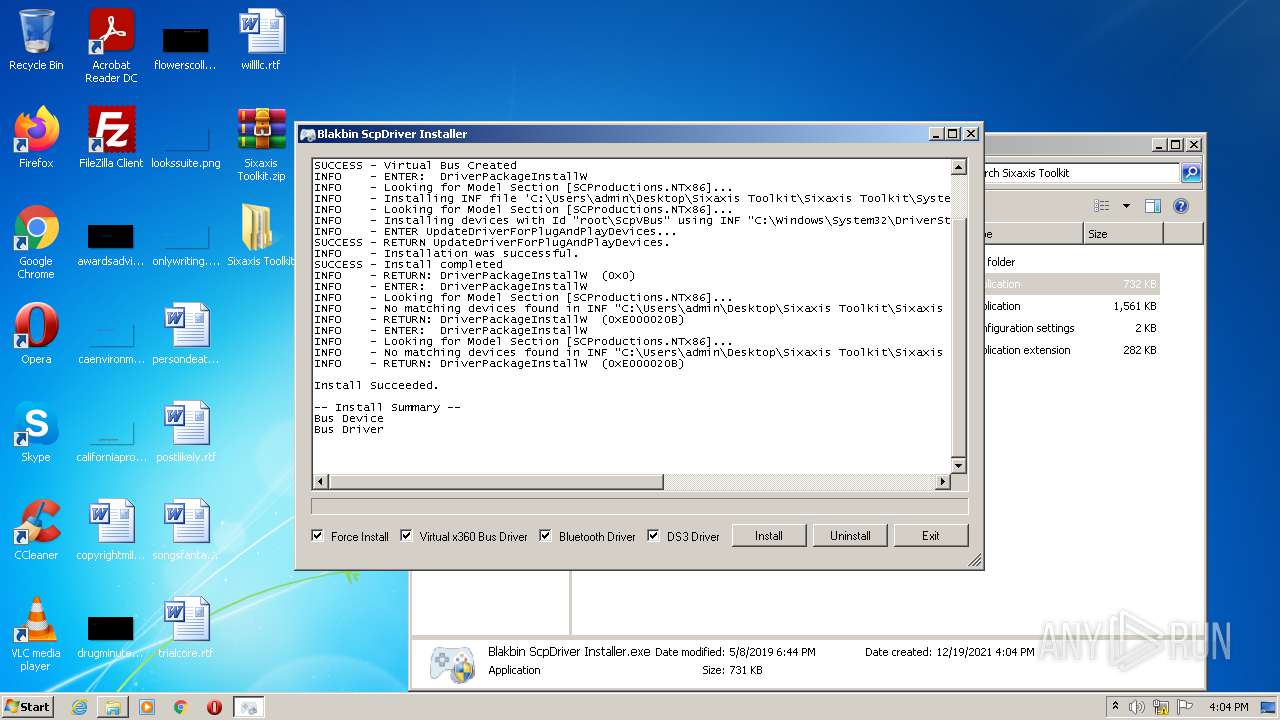
- Blakbin ScpDriver Installer.exe (PID: 3152)
Application was dropped or rewritten from another process
- Blakbin ScpServer.exe (PID: 804)
- Blakbin ScpDriver Installer.exe (PID: 3232)
- Blakbin ScpDriver Installer.exe (PID: 3152)
Drops executable file immediately after starts
- DrvInst.exe (PID: 2868)
SUSPICIOUS
Drops a file that was compiled in debug mode
- WinRAR.exe (PID: 3476)
- Blakbin ScpDriver Installer.exe (PID: 3152)
- DrvInst.exe (PID: 2868)
- DrvInst.exe (PID: 3052)
Checks supported languages
- WinRAR.exe (PID: 3476)
- Blakbin ScpServer.exe (PID: 804)
- Blakbin ScpDriver Installer.exe (PID: 3152)
- DrvInst.exe (PID: 2868)
Reads the computer name
- WinRAR.exe (PID: 3476)
- Blakbin ScpServer.exe (PID: 804)
- Blakbin ScpDriver Installer.exe (PID: 3152)
- DrvInst.exe (PID: 2868)
Drops a file with too old compile date
- WinRAR.exe (PID: 3476)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3476)
- Blakbin ScpDriver Installer.exe (PID: 3152)
- DrvInst.exe (PID: 2868)
- DrvInst.exe (PID: 3052)
Reads default file associations for system extensions
- SearchProtocolHost.exe (PID: 3288)
Executed via COM
- DrvInst.exe (PID: 2868)
- DrvInst.exe (PID: 3052)
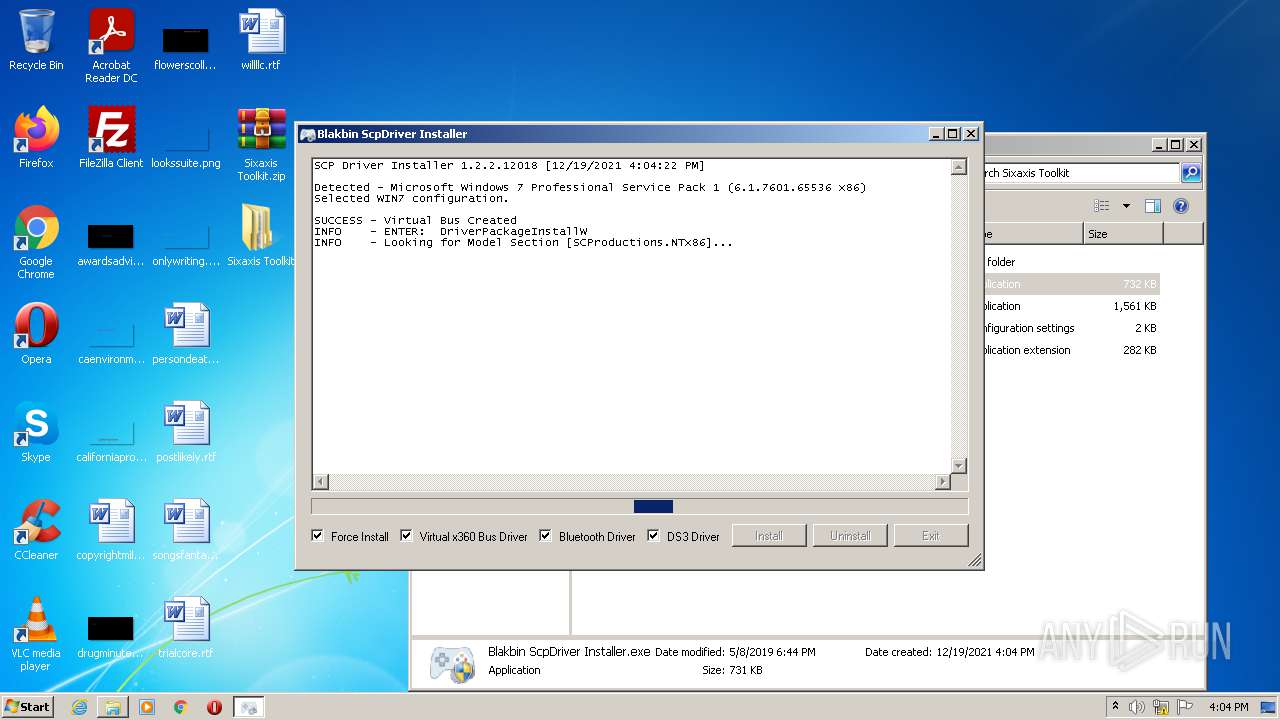
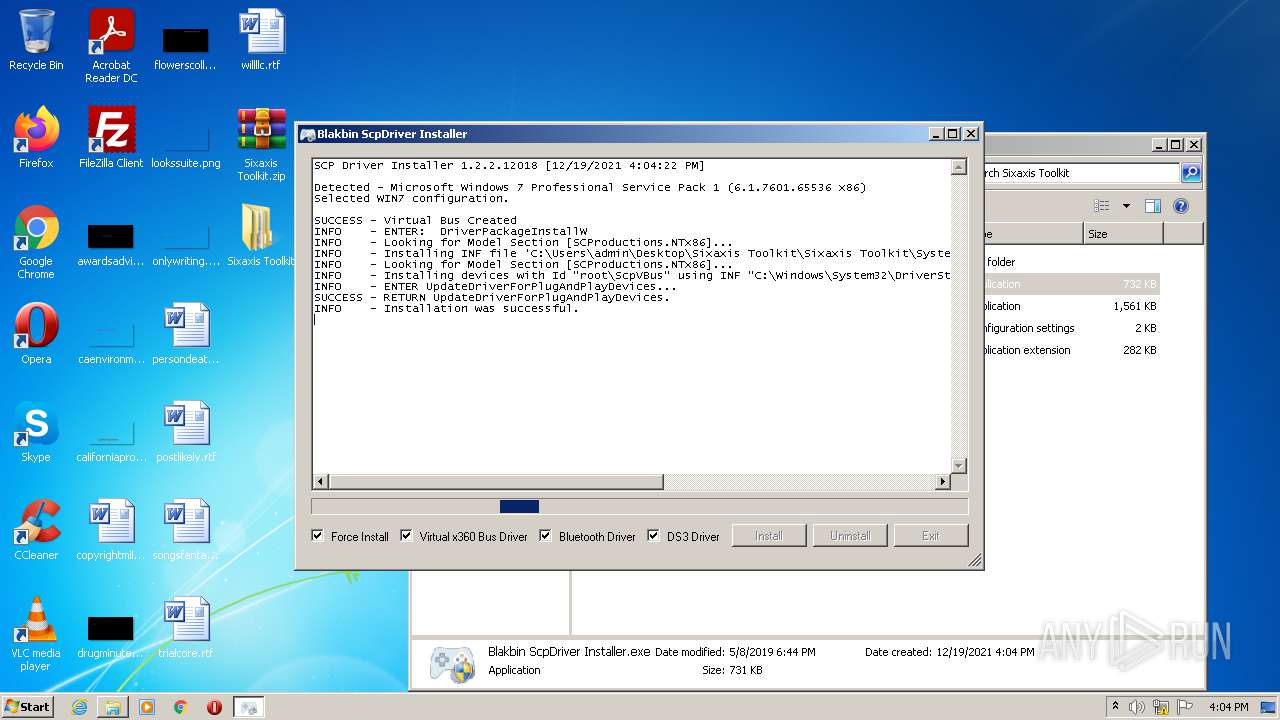
Creates files in the driver directory
- DrvInst.exe (PID: 2868)
Removes files from Windows directory
- DrvInst.exe (PID: 2868)
Creates files in the Windows directory
- DrvInst.exe (PID: 2868)
Uses RUNDLL32.EXE to load library
- DrvInst.exe (PID: 2868)
Executed as Windows Service
- vssvc.exe (PID: 3032)
Reads Environment values
- vssvc.exe (PID: 3032)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 3476)
Manual execution by user
- Blakbin ScpServer.exe (PID: 804)
- Blakbin ScpDriver Installer.exe (PID: 3232)
- Blakbin ScpDriver Installer.exe (PID: 3152)
Reads settings of System Certificates
- Blakbin ScpDriver Installer.exe (PID: 3152)
- DrvInst.exe (PID: 2868)
- rundll32.exe (PID: 3076)
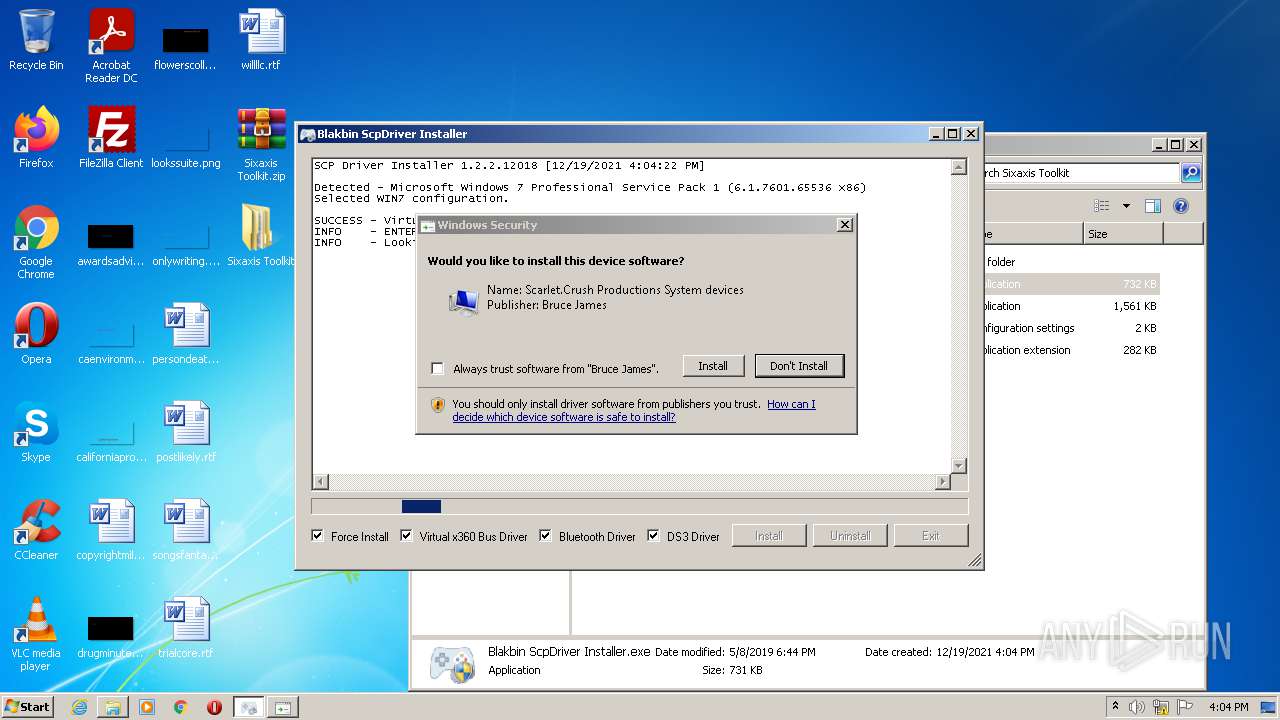
Checks Windows Trust Settings
- DrvInst.exe (PID: 2868)
- Blakbin ScpDriver Installer.exe (PID: 3152)
- rundll32.exe (PID: 3076)
Checks supported languages
- rundll32.exe (PID: 3076)
- vssvc.exe (PID: 3032)
Reads the computer name
- rundll32.exe (PID: 3076)
- vssvc.exe (PID: 3032)
Searches for installed software
- DrvInst.exe (PID: 2868)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | Sixaxis Toolkit/ |
|---|---|
| ZipUncompressedSize: | - |
| ZipCompressedSize: | - |
| ZipCRC: | 0x00000000 |
| ZipModifyDate: | 2021:10:11 23:38:23 |
| ZipCompression: | None |
| ZipBitFlag: | - |
| ZipRequiredVersion: | 20 |
Total processes
50
Monitored processes
9
Malicious processes
5
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
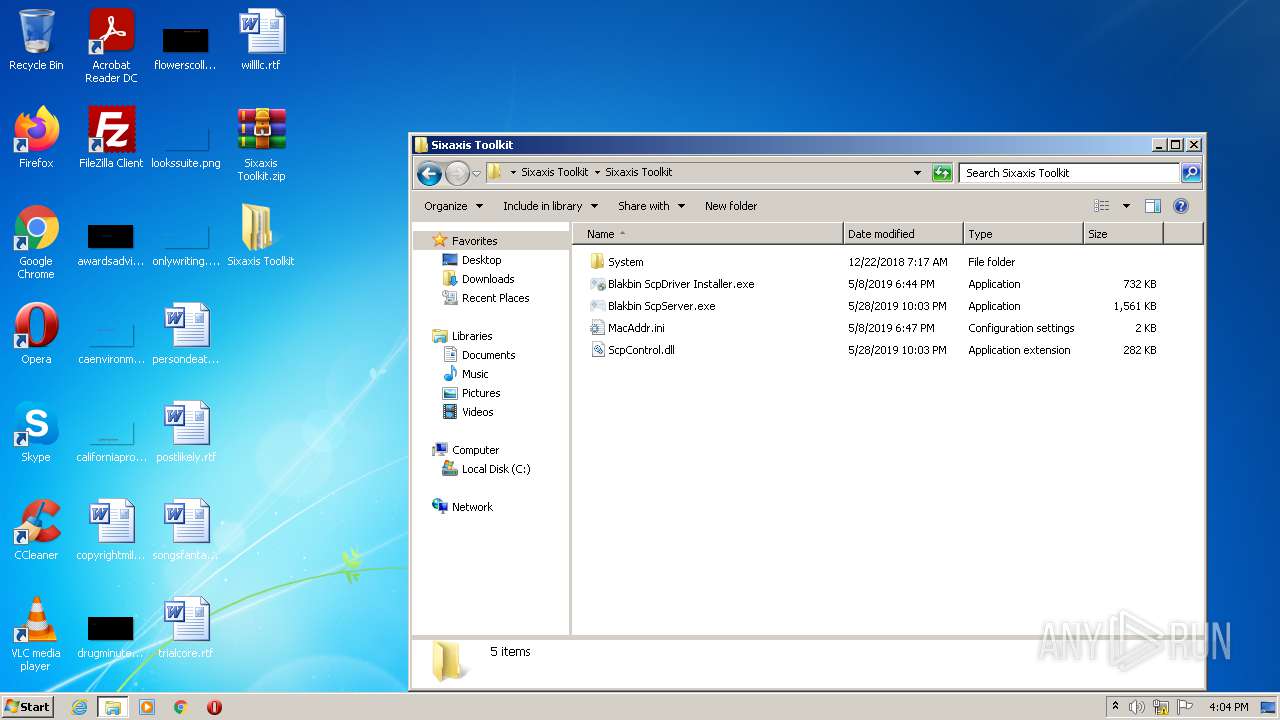
| 804 | "C:\Users\admin\Desktop\Sixaxis Toolkit\Sixaxis Toolkit\Blakbin ScpServer.exe" | C:\Users\admin\Desktop\Sixaxis Toolkit\Sixaxis Toolkit\Blakbin ScpServer.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Blakbin Integrity Level: MEDIUM Description: ScpServer +Mod by Blakbin Exit code: 0 Version: 1.2.2.15519 Modules
| |||||||||||||||
| 2868 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{63cff363-6dc7-50e7-32cd-986ed6793621}\ScpVBus.inf" "0" "601545a47" "000005D8" "WinSta0\Default" "000004CC" "208" "C:\Users\admin\Desktop\Sixaxis Toolkit\Sixaxis Toolkit\System\Driver" | C:\Windows\system32\DrvInst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3032 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft� Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3052 | DrvInst.exe "2" "211" "ROOT\SYSTEM\0001" "C:\Windows\INF\oem5.inf" "scpvbus.inf:SCProductions.NTx86:ScpVBus_Install:1.0.0.103:root\scpvbus" "6b5cfab93" "000004CC" "000005EC" "000005F4" | C:\Windows\system32\DrvInst.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3076 | rundll32.exe C:\Windows\system32\pnpui.dll,InstallSecurityPromptRunDllW 20 Global\{532162e3-6e7e-50b8-e8e5-6a2f5495e92a} Global\{13624e3d-c202-29ae-ed8e-2d410e40074f} C:\Windows\System32\DriverStore\Temp\{0b329fb1-d69b-7cde-1a2c-413661096b08}\ScpVBus.inf C:\Windows\System32\DriverStore\Temp\{0b329fb1-d69b-7cde-1a2c-413661096b08}\ScpVBus.cat | C:\Windows\system32\rundll32.exe | — | DrvInst.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3152 | "C:\Users\admin\Desktop\Sixaxis Toolkit\Sixaxis Toolkit\Blakbin ScpDriver Installer.exe" | C:\Users\admin\Desktop\Sixaxis Toolkit\Sixaxis Toolkit\Blakbin ScpDriver Installer.exe | Explorer.EXE | ||||||||||||
User: admin Company: Blakbin Integrity Level: HIGH Description: ScpDriver Exit code: 0 Version: 1.2.2.12018 Modules
| |||||||||||||||
| 3232 | "C:\Users\admin\Desktop\Sixaxis Toolkit\Sixaxis Toolkit\Blakbin ScpDriver Installer.exe" | C:\Users\admin\Desktop\Sixaxis Toolkit\Sixaxis Toolkit\Blakbin ScpDriver Installer.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Blakbin Integrity Level: MEDIUM Description: ScpDriver Exit code: 3221226540 Version: 1.2.2.12018 Modules
| |||||||||||||||
| 3288 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe2_ Global\UsGthrCtrlFltPipeMssGthrPipe2 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\system32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7601.24542 (win7sp1_ldr_escrow.191209-2211) Modules
| |||||||||||||||
| 3476 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\Sixaxis Toolkit.zip" | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
17 673
Read events
17 429
Write events
244
Delete events
0
Modification events
| (PID) Process: | (3476) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3476) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3476) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3476) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3476) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3476) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Sixaxis Toolkit.zip | |||
| (PID) Process: | (3476) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3476) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3476) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3476) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
25
Suspicious files
20
Text files
9
Unknown types
15
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3476 | WinRAR.exe | C:\Users\admin\Desktop\Sixaxis Toolkit\Sixaxis Toolkit\System\Config\ScpControl.xml | xml | |
MD5:— | SHA256:— | |||
| 3476 | WinRAR.exe | C:\Users\admin\Desktop\Sixaxis Toolkit\Sixaxis Toolkit\Blakbin ScpDriver Installer.exe | executable | |
MD5:— | SHA256:— | |||
| 3476 | WinRAR.exe | C:\Users\admin\Desktop\Sixaxis Toolkit\Sixaxis Toolkit\Blakbin ScpServer.exe | executable | |
MD5:— | SHA256:— | |||
| 3476 | WinRAR.exe | C:\Users\admin\Desktop\Sixaxis Toolkit\Sixaxis Toolkit\MacAddr.ini | text | |
MD5:— | SHA256:— | |||
| 3476 | WinRAR.exe | C:\Users\admin\Desktop\Sixaxis Toolkit\Sixaxis Toolkit\System\Config\ScpMapper.xml | xml | |
MD5:— | SHA256:— | |||
| 3476 | WinRAR.exe | C:\Users\admin\Desktop\Sixaxis Toolkit\Sixaxis Toolkit\System\Config\ScpDriver.xml | xml | |
MD5:— | SHA256:— | |||
| 3476 | WinRAR.exe | C:\Users\admin\Desktop\Sixaxis Toolkit\Sixaxis Toolkit\ScpControl.dll | executable | |
MD5:— | SHA256:— | |||
| 3476 | WinRAR.exe | C:\Users\admin\Desktop\Sixaxis Toolkit\Sixaxis Toolkit\System\Driver\amd64\WdfCoInstaller01009.dll | executable | |
MD5:4DA5DA193E0E4F86F6F8FD43EF25329A | SHA256:18487B4FF94EDCCC98ED59D9FCA662D4A1331C5F1E14DF8DB3093256DD9F1C3E | |||
| 3476 | WinRAR.exe | C:\Users\admin\Desktop\Sixaxis Toolkit\Sixaxis Toolkit\System\Driver\amd64\DIFxAPI.dll | executable | |
MD5:1A2E5109C2BB5C68D499E17B83ACB73A | SHA256:E70BBCEE0D01658CCD201EBE0F0E547B9DAFF01B7C593A0FDD0C64E5F45D6F11 | |||
| 3476 | WinRAR.exe | C:\Users\admin\Desktop\Sixaxis Toolkit\Sixaxis Toolkit\System\Driver\amd64\ScpVBus.sys | executable | |
MD5:0447065A6E10774EFCECFDD0EB970A79 | SHA256:384A9AC72E756F96D43EE4B144A466564476AFD8778092C979116BB29A514433 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report