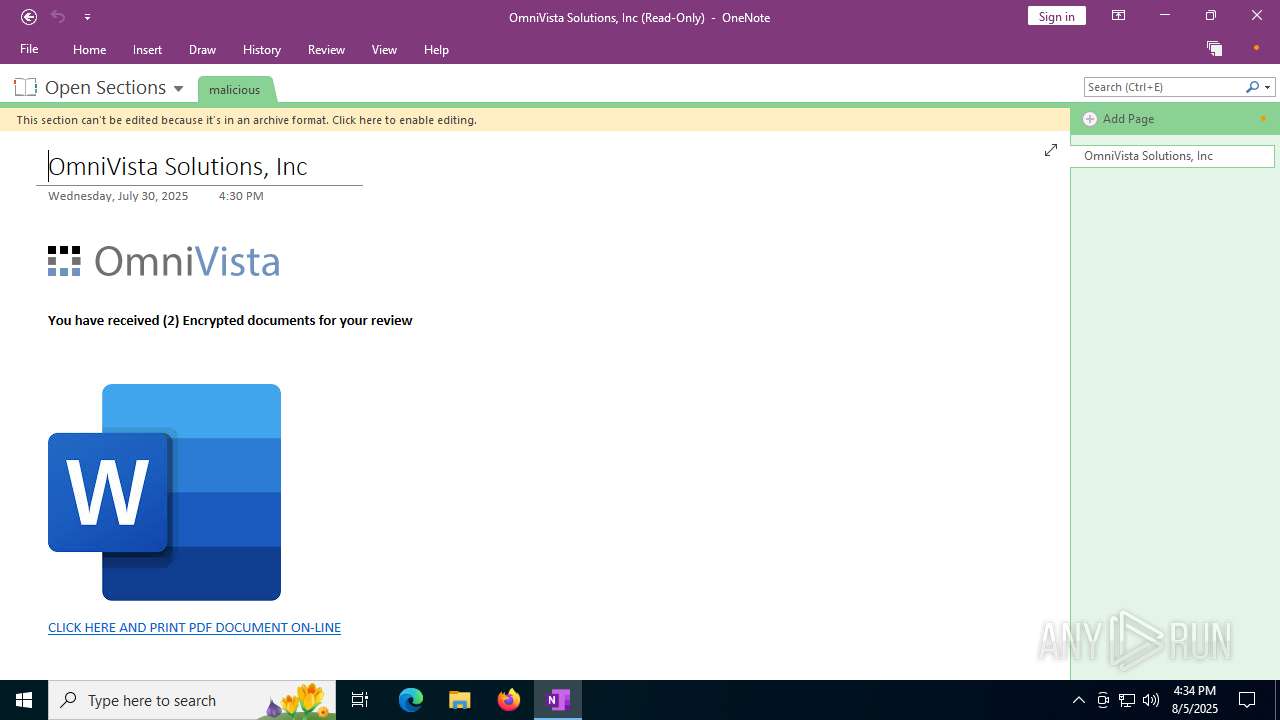
| File name: | malicious.one |
| Full analysis: | https://app.any.run/tasks/8a13d8a3-d28f-48e4-bb90-ecb2d5b72aba |
| Verdict: | Malicious activity |
| Analysis date: | August 05, 2025, 16:34:42 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/onenote |
| File info: | Microsoft OneNote |
| MD5: | E242FE4C643508CD943C71C96677CC96 |
| SHA1: | 224B33EB97D8AEE018FAD8C79254CC256163F0D1 |
| SHA256: | 9DE9B5815F23DFBDC142408BB3DBB9D5D1B79DF8F5599B540AAA643506691EAA |
| SSDEEP: | 768:8uiC8SOnD390Wb1/jt898OFII/L4W8Diw9Dohlm6TAO:/K0y/jt+8OFIIei6oCaAO |
MALICIOUS
No malicious indicators.SUSPICIOUS
Detected use of alternative data streams (AltDS)
- ONENOTE.EXE (PID: 6264)
Creates file in the systems drive root
- ONENOTE.EXE (PID: 6264)
INFO
Checks supported languages
- ONENOTEM.EXE (PID: 4580)
Reads the computer name
- ONENOTEM.EXE (PID: 4580)
Reads Microsoft Office registry keys
- ONENOTEM.EXE (PID: 4580)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
143
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4580 | /tsr | C:\Program Files\Microsoft Office\root\Office16\ONENOTEM.EXE | — | ONENOTE.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Send to OneNote Tool Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 6264 | "C:\Program Files\Microsoft Office\Root\Office16\ONENOTE.EXE" C:\Users\admin\AppData\Local\Temp\malicious.one | C:\Program Files\Microsoft Office\root\Office16\ONENOTE.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft OneNote Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 7040 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
7 815
Read events
7 582
Write events
219
Delete events
14
Modification events
| (PID) Process: | (6264) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (6264) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (6264) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (6264) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (6264) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\OneNote\General |
| Operation: | write | Name: | DateLastAttemptedOpeningLocalNotebooksOnBoot |
Value: 6258E6DB2606DC01 | |||
| (PID) Process: | (6264) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ExperimentConfigs\Ecs |
| Operation: | write | Name: | LicenseSKUInfo |
Value: std::wstring|OneNoteFreeRetail | |||
| (PID) Process: | (6264) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\onenote.exe\ETWMonitor\{02FD33DF-F746-4A10-93A0-2BC6273BC8E4} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6264) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\onenote.exe\ETWMonitor\{F562BB8E-422D-4B5C-B20E-90D710F7D11C} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6264) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\onenote.exe\ETWMonitor |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (6264) ONENOTE.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\ClientTelemetry\RulesMetadata\onenote.exe\ULSMonitor |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
0
Suspicious files
7
Text files
6
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6264 | ONENOTE.EXE | C:\Users\admin\AppData\Local\Microsoft\OneNote\16.0\cache\tmp\0000000B.bin | image | |
MD5:F9ED84C97E638315A6F153F3074B3514 | SHA256:7EC4314F4FF405F42284371790D3A1A3F0FC71D28937DA704613C7B5C55DF4B0 | |||
| 6264 | ONENOTE.EXE | C:\Users\admin\AppData\Local\Microsoft\OneNote\16.0\cache\tmp\0000000A.bin | image | |
MD5:9CC9D971034F83BBD6E73C7160935380 | SHA256:AF7810982F00E34BEE3CDCDCF1E2DBB904D809D971F37F9452E263D8D80EB313 | |||
| 6264 | ONENOTE.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\F4CCC649-F6D9-4A40-80F7-427193B61EA7 | xml | |
MD5:398E74111688D8BD13C8357C9BC0E9FA | SHA256:2D005D8C561C427DFD8BA3FE7935851B72A0124AB206B974E45FD49BDD2F50F4 | |||
| 6264 | ONENOTE.EXE | C:\Users\admin\AppData\Roaming\Microsoft\UProof\ExcludeDictionaryEN0409.lex | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 6264 | ONENOTE.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:0310AE1D5048ED04B3EA4C11F86C2AD3 | SHA256:699B1DC3E870D479B38A71C4C5367E4C72C6FCA104425B0C3A9CD8872AF600EC | |||
| 6264 | ONENOTE.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\5475cb191e478c39370a215b2da98a37e9dc813d.tbres | binary | |
MD5:2E3DECE6828FFB491589723F9AA34957 | SHA256:A9646ED6C41B23B4D287174A7130941CF913A3EF3D748FB1932545030490BC35 | |||
| 6264 | ONENOTE.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | der | |
MD5:92A8E1C34C96249D6C61F183037746E5 | SHA256:4214B811CC5980704B369572E602B354DB8B1DCD229F6046AC7C5646CC62B86C | |||
| 6264 | ONENOTE.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\QZ0G06GY60YGBMD29TYM.temp | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 6264 | ONENOTE.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\1bc9bbbe61f14501.customDestinations-ms~RF18f18f.TMP | binary | |
MD5:C32BC52A21EFE066C95CF6C4935220D7 | SHA256:0635BCDAD77D46DF9604BBAE323D88772F55AB176C3224E110B4154660DA3916 | |||
| 6264 | ONENOTE.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:877546372EE9F71057C3AF420FA7E720 | SHA256:5D6F082480B37E7285DE95C2B6FCFB1A28F856BE699B2736A6F91637D7660202 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
27
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6356 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.25:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6264 | ONENOTE.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
3756 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3756 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4456 | RUXIMICS.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1268 | svchost.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6264 | ONENOTE.EXE | 52.109.76.240:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6264 | ONENOTE.EXE | 52.123.129.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6356 | svchost.exe | 20.190.160.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6356 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
ONENOTE.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|