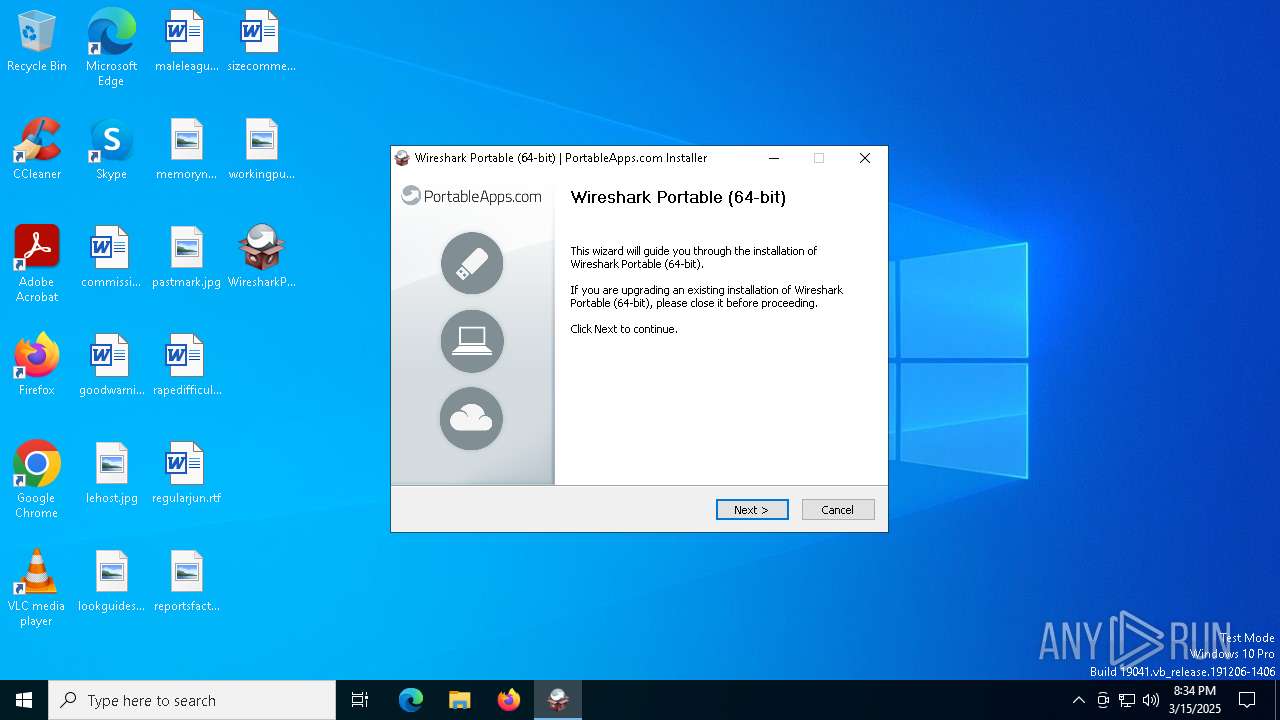
| File name: | WiresharkPortable64_4.4.5.paf.exe |
| Full analysis: | https://app.any.run/tasks/66a56d92-c38a-4223-98a2-ae1ddf75633f |
| Verdict: | Malicious activity |
| Analysis date: | March 15, 2025, 20:34:20 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | A5CF4AB9E84A1640DD9410DC4209170F |
| SHA1: | 4170D03763860D812C087A117DE87AE90AC945AB |
| SHA256: | 9DDF1720D31707DAA4F57FA61F43861602BD0F11F1298DCF56EA3CFC96F07A31 |
| SSDEEP: | 393216:THQDGuIcI6ZPuyo8nXQBwcWgiyAvTB0hYU3uFu2Orv2R7hR6xQtr0uJqQd:bcVK6kP86xeN0hYUD2SvIlcxQx0uJqg |
MALICIOUS
No malicious indicators.SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- WiresharkPortable64_4.4.5.paf.exe (PID: 7456)
The process creates files with name similar to system file names
- WiresharkPortable64_4.4.5.paf.exe (PID: 7456)
There is functionality for taking screenshot (YARA)
- WiresharkPortable64_4.4.5.paf.exe (PID: 7456)
Executable content was dropped or overwritten
- WiresharkPortable64_4.4.5.paf.exe (PID: 7456)
Process drops legitimate windows executable
- WiresharkPortable64_4.4.5.paf.exe (PID: 7456)
The process drops C-runtime libraries
- WiresharkPortable64_4.4.5.paf.exe (PID: 7456)
INFO
Checks supported languages
- WiresharkPortable64_4.4.5.paf.exe (PID: 7456)
Reads the computer name
- WiresharkPortable64_4.4.5.paf.exe (PID: 7456)
The sample compiled with english language support
- WiresharkPortable64_4.4.5.paf.exe (PID: 7456)
Create files in a temporary directory
- WiresharkPortable64_4.4.5.paf.exe (PID: 7456)
Checks proxy server information
- slui.exe (PID: 7736)
Reads the software policy settings
- slui.exe (PID: 7736)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2021:09:25 22:04:50+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 26624 |
| InitializedDataSize: | 428544 |
| UninitializedDataSize: | 16384 |
| EntryPoint: | 0x3640 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 4.4.5.0 |
| ProductVersionNumber: | 4.4.5.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| Comments: | For additional details, visit PortableApps.com |
| CompanyName: | PortableApps.com |
| FileDescription: | Wireshark Portable (64-bit) |
| FileVersion: | 4.4.5.0 |
| InternalName: | Wireshark Portable (64-bit) |
| LegalCopyright: | 2007-2022 PortableApps.com, PortableApps.com Installer 3.7.6.0 |
| LegalTrademarks: | Wireshark and the fin logo are registered trademarks of the Wireshark Foundation. PortableApps.com is a registered trademark of Rare Ideas, LLC. |
| OriginalFileName: | WiresharkPortable64_4.4.5.paf.exe |
| PortableAppscomAppID: | WiresharkPortable64 |
| PortableAppscomFormatVersion: | 3.7.6 |
| PortableAppscomInstallerVersion: | 3.7.6.0 |
| ProductName: | Wireshark Portable (64-bit) |
| ProductVersion: | 4.4.5.0 |
Total processes
122
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 7456 | "C:\Users\admin\Desktop\WiresharkPortable64_4.4.5.paf.exe" | C:\Users\admin\Desktop\WiresharkPortable64_4.4.5.paf.exe | explorer.exe | ||||||||||||
User: admin Company: PortableApps.com Integrity Level: MEDIUM Description: Wireshark Portable (64-bit) Version: 4.4.5.0 Modules
| |||||||||||||||
| 7736 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 483
Read events
3 483
Write events
0
Delete events
0
Modification events
Executable files
135
Suspicious files
45
Text files
1 174
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7456 | WiresharkPortable64_4.4.5.paf.exe | C:\Users\admin\AppData\Local\Temp\nsqEB9C.tmp\modern-header.bmp | image | |
MD5:EF7002C05FA20587367AFC21B45E79D3 | SHA256:37A4EE6B0C147DBC5E0BE0CCE1DFE24E9A02F87D4955975BFD7A7045A2F47CBE | |||
| 7456 | WiresharkPortable64_4.4.5.paf.exe | C:\Users\admin\Desktop\WiresharkPortable64\App\Wireshark\COPYING.txt | text | |
MD5:FFA10F40B98BE2C2BC9608F56827ED23 | SHA256:189B1AF95D661151E054CEA10C91B3D754E4DE4D3FECFB074C1FB29476F7167B | |||
| 7456 | WiresharkPortable64_4.4.5.paf.exe | C:\Users\admin\AppData\Local\Temp\nsqEB9C.tmp\System.dll | executable | |
MD5:CFF85C549D536F651D4FB8387F1976F2 | SHA256:8DC562CDA7217A3A52DB898243DE3E2ED68B80E62DDCB8619545ED0B4E7F65A8 | |||
| 7456 | WiresharkPortable64_4.4.5.paf.exe | C:\Users\admin\Desktop\WiresharkPortable64\App\Wireshark\Qt6Multimedia.dll | executable | |
MD5:A7C4F760D23A6E1C7D77C408FEA0BA4A | SHA256:C5B02FC4377667A09F3F7F694E2C82DD623373E70C2E3B900F7DAAEE1B6A7DFE | |||
| 7456 | WiresharkPortable64_4.4.5.paf.exe | C:\Users\admin\Desktop\WiresharkPortable64\App\AppInfo\Launcher\WiresharkPortable64.ini | text | |
MD5:205C7A933E1AE0C468EB07992842D02D | SHA256:31E648F31B2FCDF0D93A7168520E6DE903E337445D4CC3DCEA373E68717418A2 | |||
| 7456 | WiresharkPortable64_4.4.5.paf.exe | C:\Users\admin\Desktop\WiresharkPortable64\App\Wireshark\Qt6Gui.dll | executable | |
MD5:1813D6970143BC22EDE73E19739496B4 | SHA256:F01A483A831CD89764D043280E46014B658878D09A33B4C74BFBD8CD0CE4E31A | |||
| 7456 | WiresharkPortable64_4.4.5.paf.exe | C:\Users\admin\Desktop\WiresharkPortable64\App\Wireshark\Qt6Core.dll | executable | |
MD5:9E1E3D2E45493EEB00BD80F66A1180E9 | SHA256:D6A3503CFCAF464CFA99AC34C81256F3D0EC44C77A7F8C1C37BB7F116872FB7D | |||
| 7456 | WiresharkPortable64_4.4.5.paf.exe | C:\Users\admin\AppData\Local\Temp\nsqEB9C.tmp\nsDialogs.dll | executable | |
MD5:6C3F8C94D0727894D706940A8A980543 | SHA256:56B96ADD1978B1ABBA286F7F8982B0EFBE007D4A48B3DED6A4D408E01D753FE2 | |||
| 7456 | WiresharkPortable64_4.4.5.paf.exe | C:\Users\admin\AppData\Local\Temp\nsqEB9C.tmp\w7tbp.dll | executable | |
MD5:9A3031CC4CEF0DBA236A28EECDF0AFB5 | SHA256:53BB519E3293164947AC7CBD7E612F637D77A7B863E3534BA1A7E39B350D3C00 | |||
| 7456 | WiresharkPortable64_4.4.5.paf.exe | C:\Users\admin\Desktop\WiresharkPortable64\WiresharkPortable64.exe | executable | |
MD5:ABC58DD0FCB73F8BEA21A8EE2E008B68 | SHA256:6518D4406FAD6C0C6F0F4260D115A6E2F3EDD1C9388E1B8A26C549BFBE78DEF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
19
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
— | — | POST | 500 | 40.91.76.224:443 | https://activation-v2.sls.microsoft.com/SLActivateProduct/SLActivateProduct.asmx?configextension=Retail | unknown | xml | 512 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1244 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
7268 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7736 | slui.exe | 40.91.76.224:443 | activation-v2.sls.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |