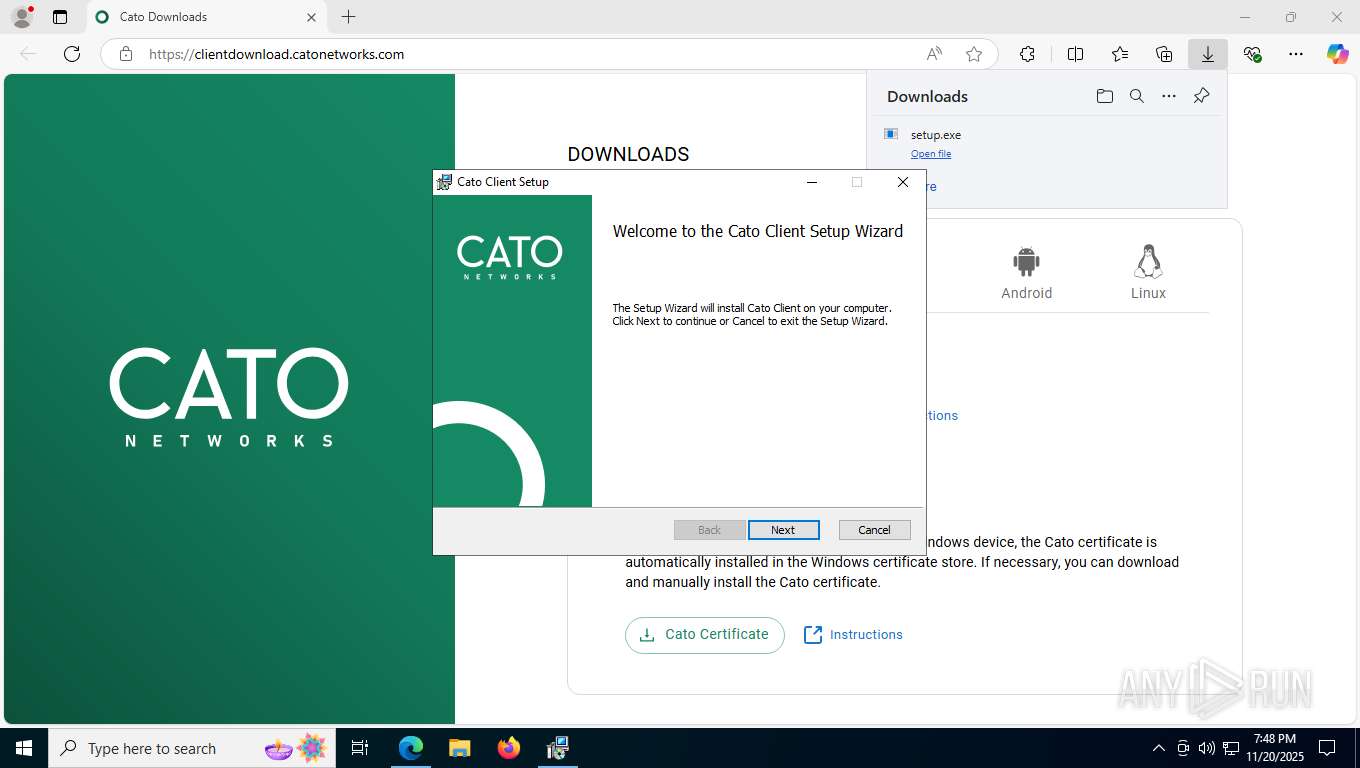
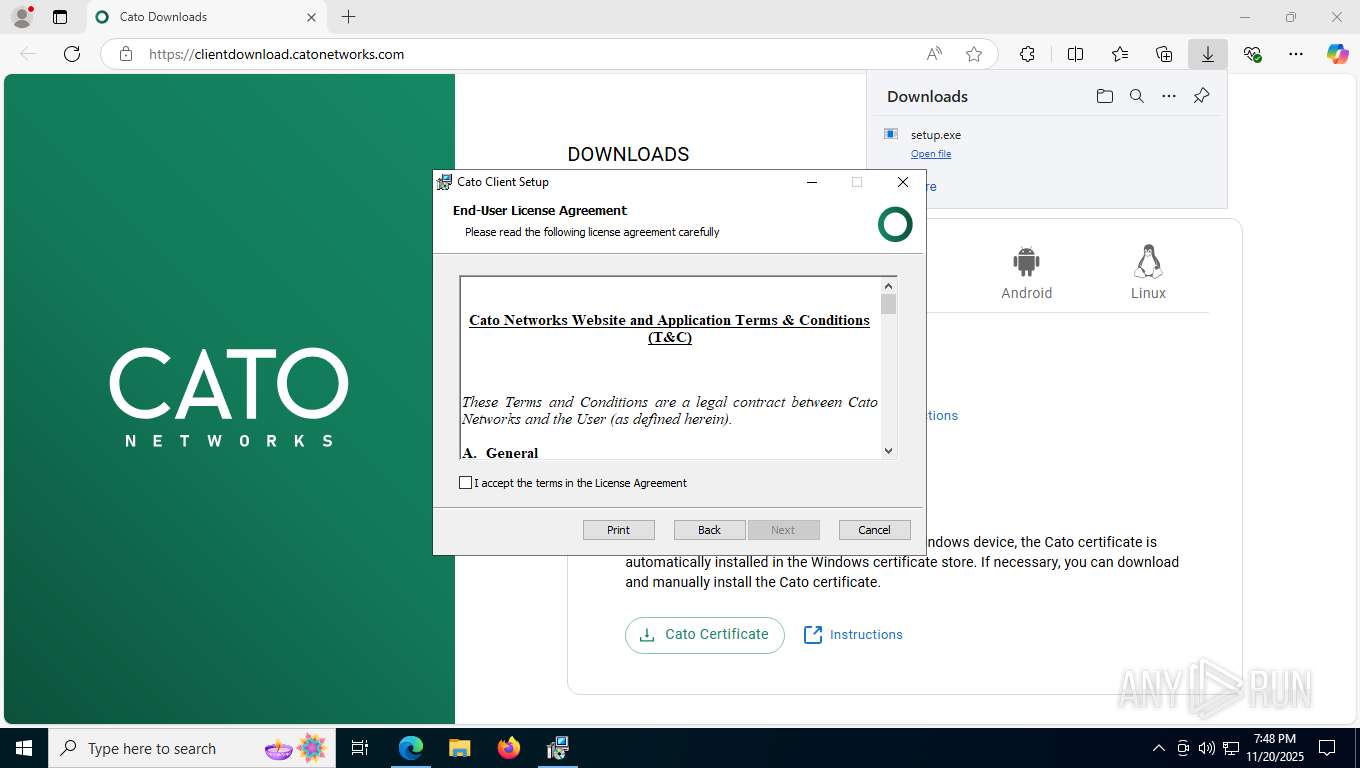
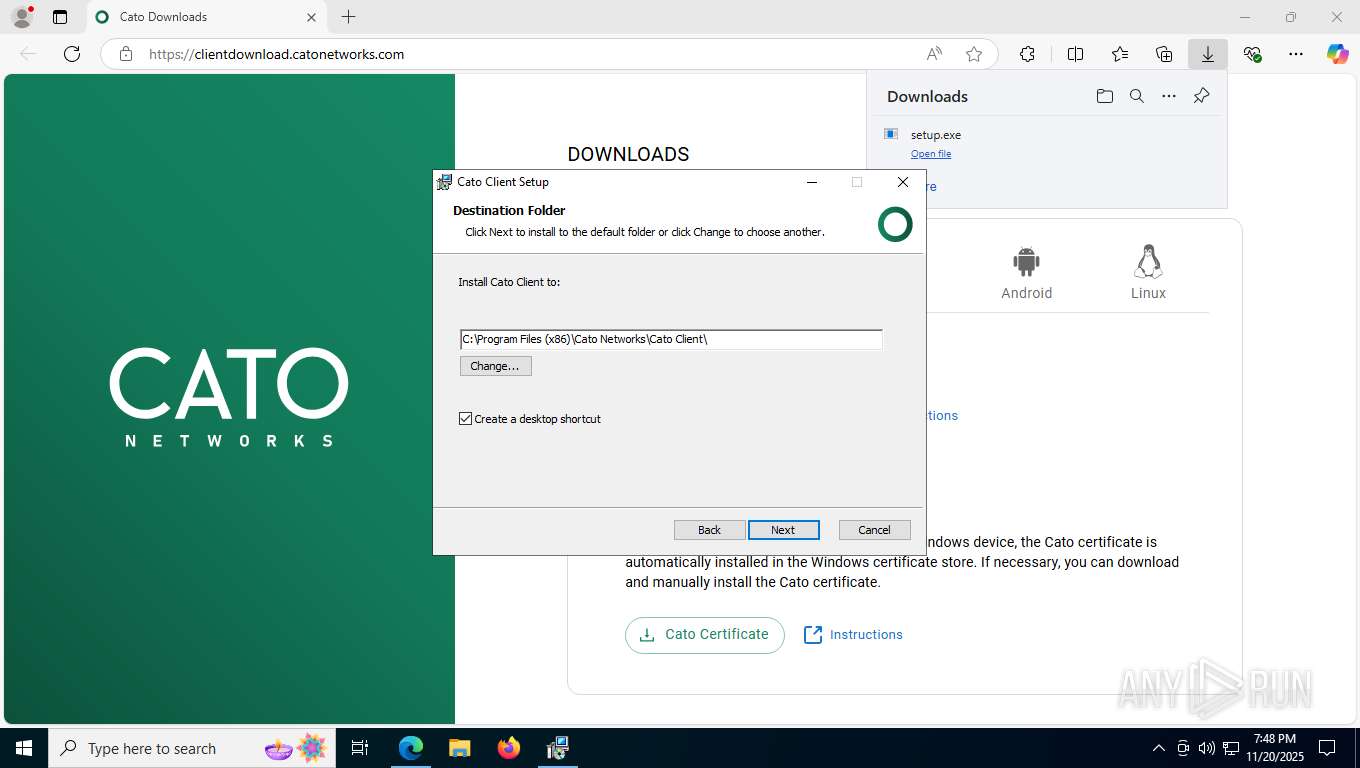
| URL: | https://clientdownload.catonetworks.com/ |
| Full analysis: | https://app.any.run/tasks/e8201f34-0551-4a08-8b9e-9d0bd96030b1 |
| Verdict: | Malicious activity |
| Analysis date: | November 20, 2025, 19:47:49 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | B03E6E3A6974A879CA75B911FF6060B7 |
| SHA1: | 92CE363DF116243EB83D97111CD8456554281446 |
| SHA256: | 9DDBE31FA481935B1529D90CF20D0A979E643E45DD34D67D2E4ADA09CEDC8D42 |
| SSDEEP: | 3:N8Uf9lRSMsK3n:2Uf9lRSMsK3 |
MALICIOUS
Changes settings of System certificates
- certutil.exe (PID: 2880)
- certutil.exe (PID: 7904)
- certutil.exe (PID: 1060)
- certutil.exe (PID: 5728)
- msiexec.exe (PID: 3684)
Changes the autorun value in the registry
- rundll32.exe (PID: 8148)
SUSPICIOUS
Malware-specific behavior (creating "System.dll" in Temp)
- setup.exe (PID: 6780)
Executable content was dropped or overwritten
- setup.exe (PID: 6780)
- rundll32.exe (PID: 6016)
- rundll32.exe (PID: 2432)
- rundll32.exe (PID: 2432)
- rundll32.exe (PID: 8148)
- winvpnclient.cli.exe (PID: 2144)
The process creates files with name similar to system file names
- setup.exe (PID: 6780)
There is functionality for taking screenshot (YARA)
- setup.exe (PID: 6780)
Executes as Windows Service
- VSSVC.exe (PID: 7288)
- winvpnclient.cli.exe (PID: 2144)
Adds/modifies Windows certificates
- certutil.exe (PID: 2880)
- certutil.exe (PID: 7904)
- certutil.exe (PID: 1060)
- msiexec.exe (PID: 3684)
- certutil.exe (PID: 5728)
The process drops C-runtime libraries
- msiexec.exe (PID: 896)
Process drops legitimate windows executable
- msiexec.exe (PID: 896)
Drops a system driver (possible attempt to evade defenses)
- msiexec.exe (PID: 896)
- rundll32.exe (PID: 2432)
- drvinst.exe (PID: 2692)
- msiexec.exe (PID: 3684)
- drvinst.exe (PID: 7720)
- drvinst.exe (PID: 8196)
- winvpnclient.cli.exe (PID: 2144)
Application launched itself
- msiexec.exe (PID: 896)
Creates files in the driver directory
- msiexec.exe (PID: 3684)
Restarts service on failure
- sc.exe (PID: 8048)
Non windows owned service launched
- winvpnclient.cli.exe (PID: 2144)
Searches for installed software
- winvpnclient.cli.exe (PID: 2144)
Suspicious use of NETSH.EXE
- cmd.exe (PID: 8476)
- cmd.exe (PID: 8660)
- cmd.exe (PID: 8852)
Starts CMD.EXE for commands execution
- winvpnclient.cli.exe (PID: 2144)
Uses REG/REGEDIT.EXE to modify registry
- msiexec.exe (PID: 412)
INFO
Application launched itself
- msedge.exe (PID: 2184)
Checks supported languages
- identity_helper.exe (PID: 5456)
- setup.exe (PID: 6780)
- msiexec.exe (PID: 896)
- msiexec.exe (PID: 7144)
- msiexec.exe (PID: 8020)
- drvinst.exe (PID: 2692)
- msiexec.exe (PID: 412)
- msiexec.exe (PID: 3684)
- drvinst.exe (PID: 7952)
- drvinst.exe (PID: 7720)
- drvinst.exe (PID: 8008)
- winvpnclient.cli.exe (PID: 2144)
- drvinst.exe (PID: 8196)
- drvinst.exe (PID: 8408)
Reads the computer name
- identity_helper.exe (PID: 5456)
- msiexec.exe (PID: 896)
- msiexec.exe (PID: 7144)
- msiexec.exe (PID: 8020)
- msiexec.exe (PID: 3684)
- msiexec.exe (PID: 412)
- drvinst.exe (PID: 2692)
- drvinst.exe (PID: 7952)
- drvinst.exe (PID: 7720)
- drvinst.exe (PID: 8008)
- drvinst.exe (PID: 8408)
- winvpnclient.cli.exe (PID: 2144)
- drvinst.exe (PID: 8196)
Reads Environment values
- identity_helper.exe (PID: 5456)
The sample compiled with english language support
- msedge.exe (PID: 2184)
- msiexec.exe (PID: 896)
- drvinst.exe (PID: 7720)
- msiexec.exe (PID: 3684)
- winvpnclient.cli.exe (PID: 2144)
- drvinst.exe (PID: 8196)
Executable content was dropped or overwritten
- msedge.exe (PID: 2184)
- msiexec.exe (PID: 4568)
- msiexec.exe (PID: 896)
- msiexec.exe (PID: 3684)
Creates files in the program directory
- setup.exe (PID: 6780)
- rundll32.exe (PID: 2432)
- winvpnclient.cli.exe (PID: 2144)
Create files in a temporary directory
- setup.exe (PID: 6780)
- msiexec.exe (PID: 4568)
- rundll32.exe (PID: 6016)
- msiexec.exe (PID: 3684)
Manages system restore points
- SrTasks.exe (PID: 7936)
Reads the machine GUID from the registry
- msiexec.exe (PID: 3684)
- drvinst.exe (PID: 2692)
- drvinst.exe (PID: 7720)
- winvpnclient.cli.exe (PID: 2144)
- drvinst.exe (PID: 8196)
Launching a file from a Registry key
- rundll32.exe (PID: 8148)
Disables trace logs
- netsh.exe (PID: 8800)
- netsh.exe (PID: 8920)
- netsh.exe (PID: 8544)
Checks proxy server information
- slui.exe (PID: 148)
Manual execution by a user
- rundll32.exe (PID: 9208)
- rundll32.exe (PID: 1632)
- rundll32.exe (PID: 356)
- rundll32.exe (PID: 8396)
- rundll32.exe (PID: 4280)
- rundll32.exe (PID: 8608)
- rundll32.exe (PID: 8684)
Reads security settings of Internet Explorer
- rundll32.exe (PID: 4280)
- rundll32.exe (PID: 8396)
- rundll32.exe (PID: 356)
- rundll32.exe (PID: 8608)
- rundll32.exe (PID: 9208)
- rundll32.exe (PID: 1632)
- rundll32.exe (PID: 8684)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
244
Monitored processes
87
Malicious processes
2
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 148 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
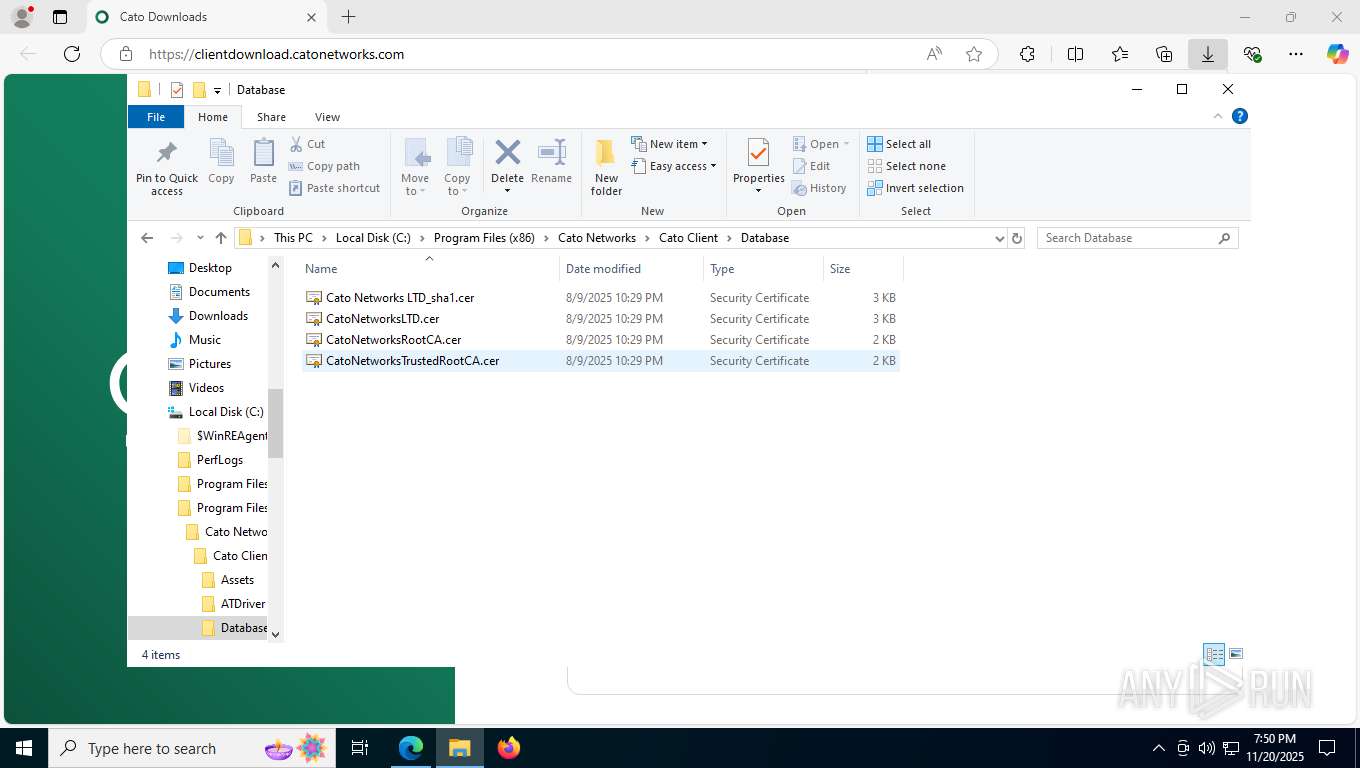
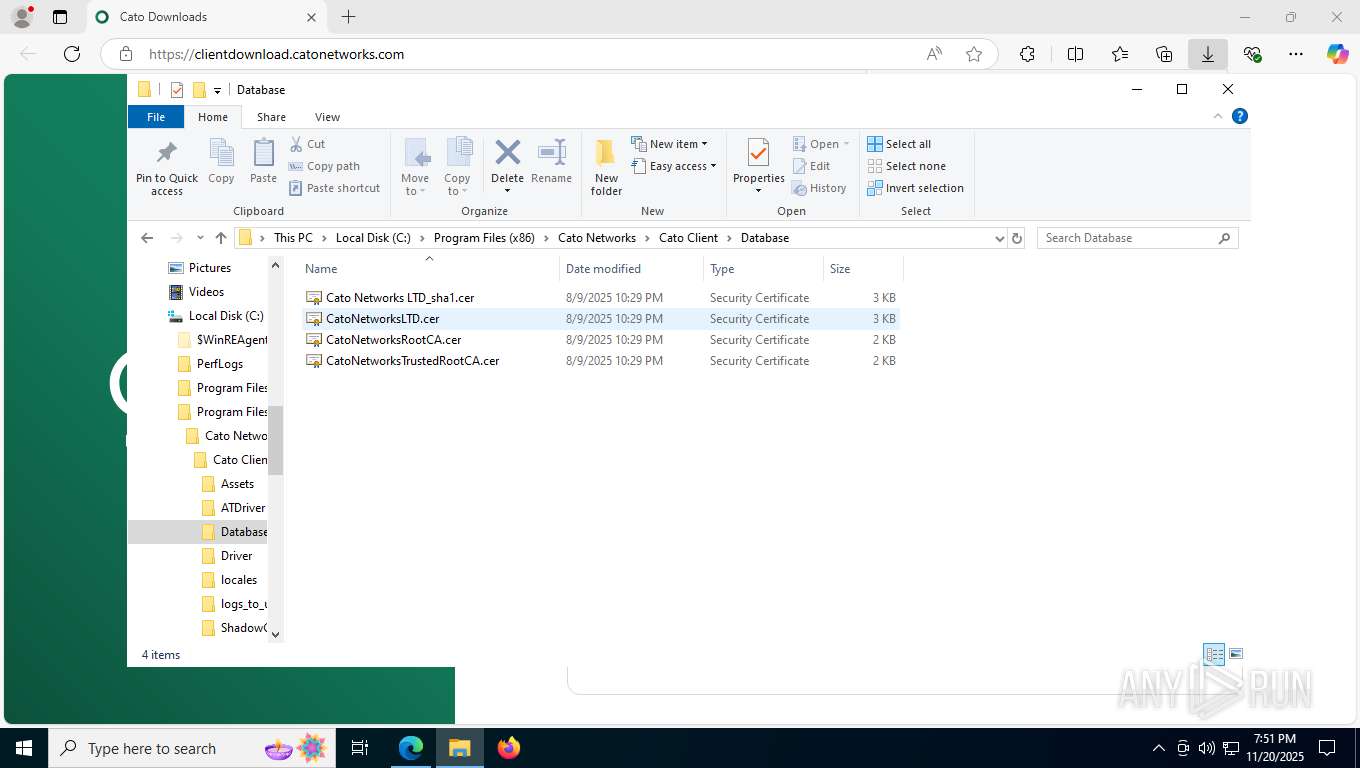
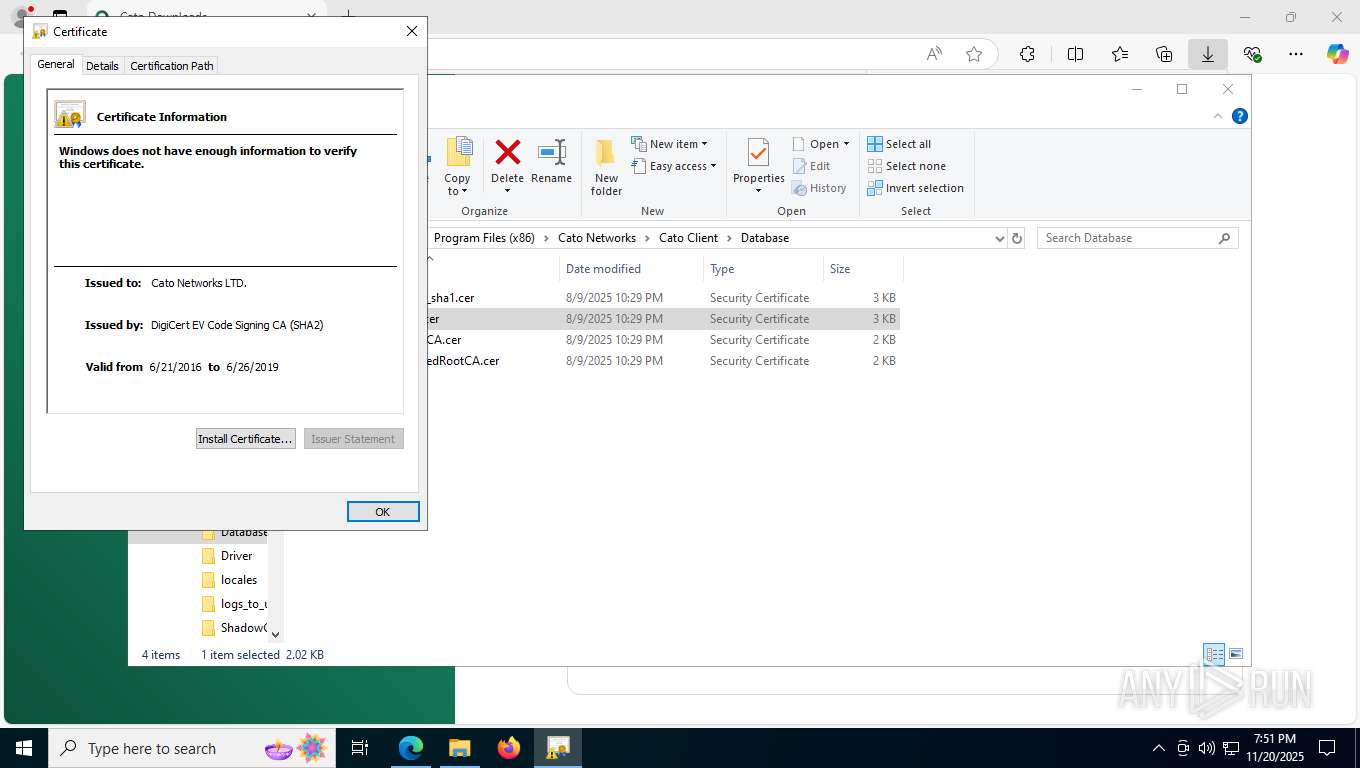
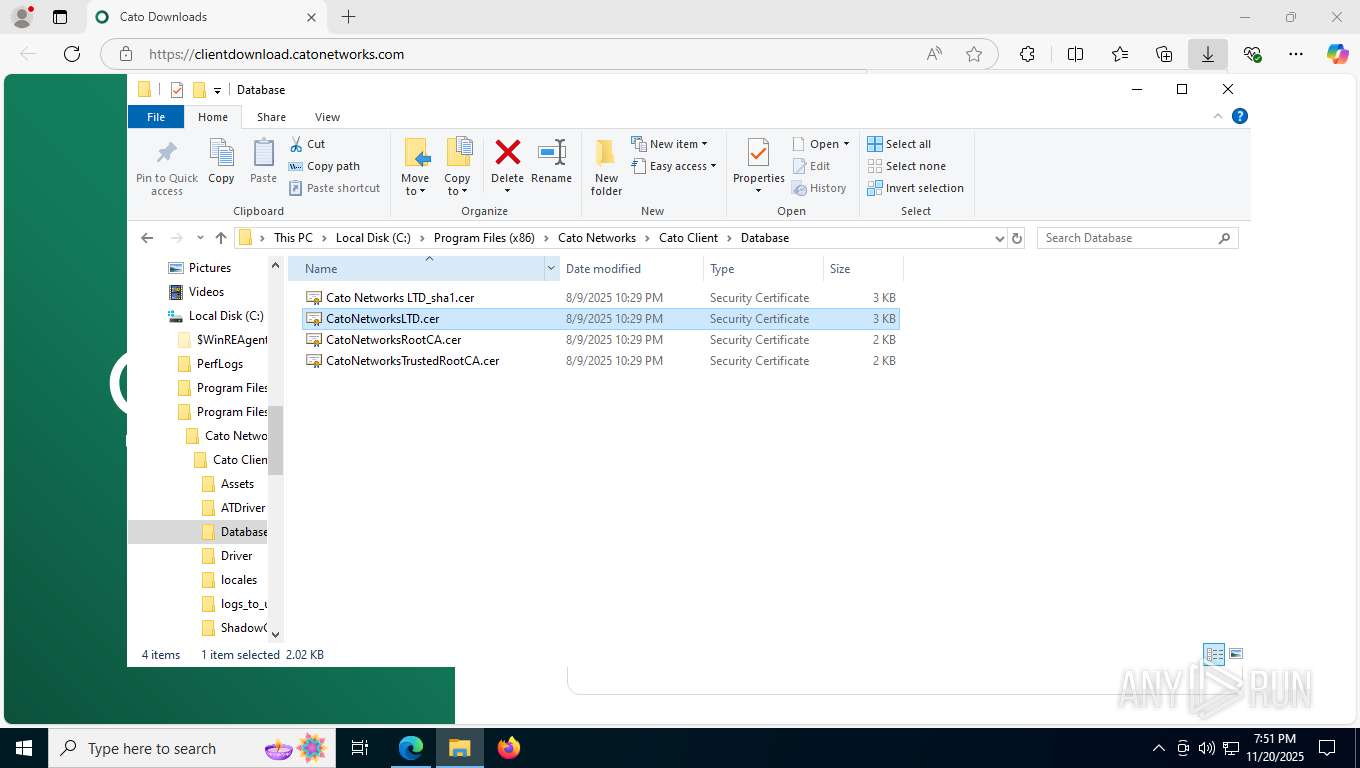
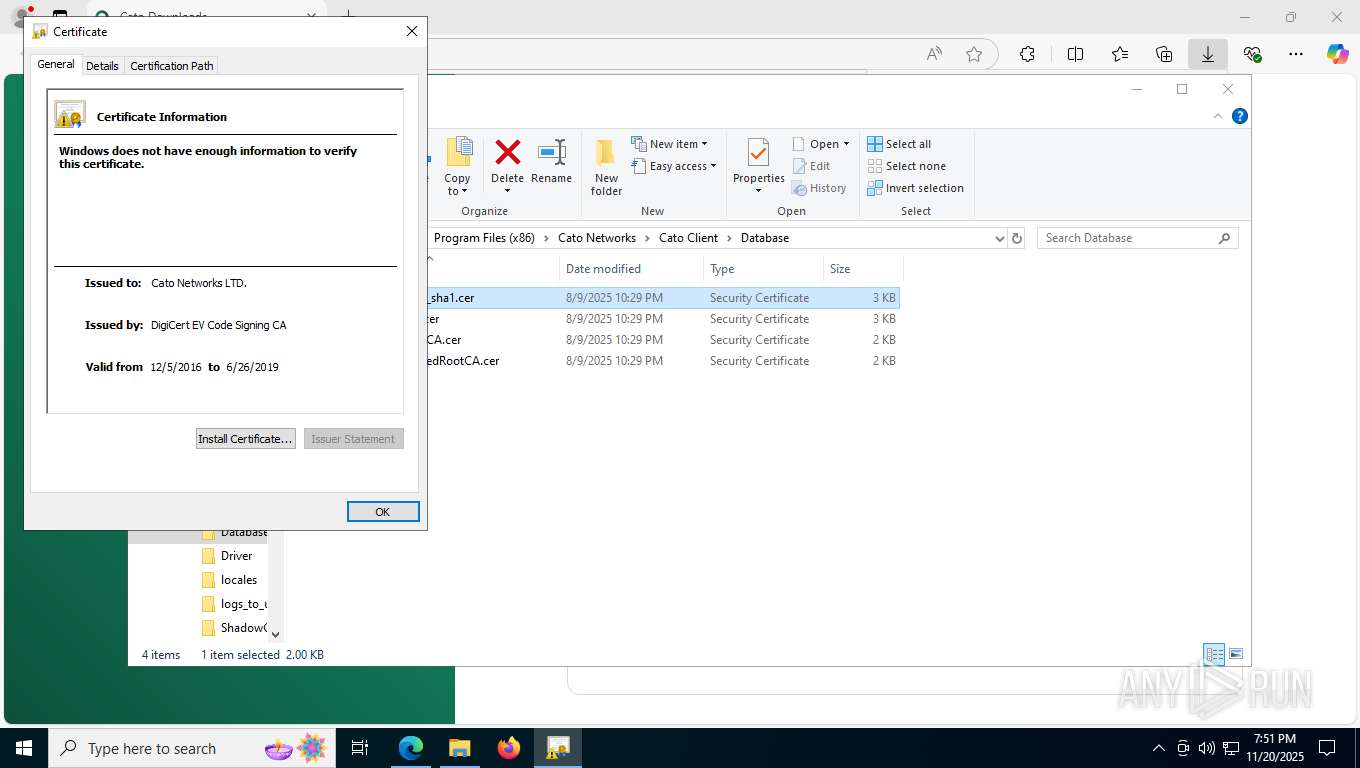
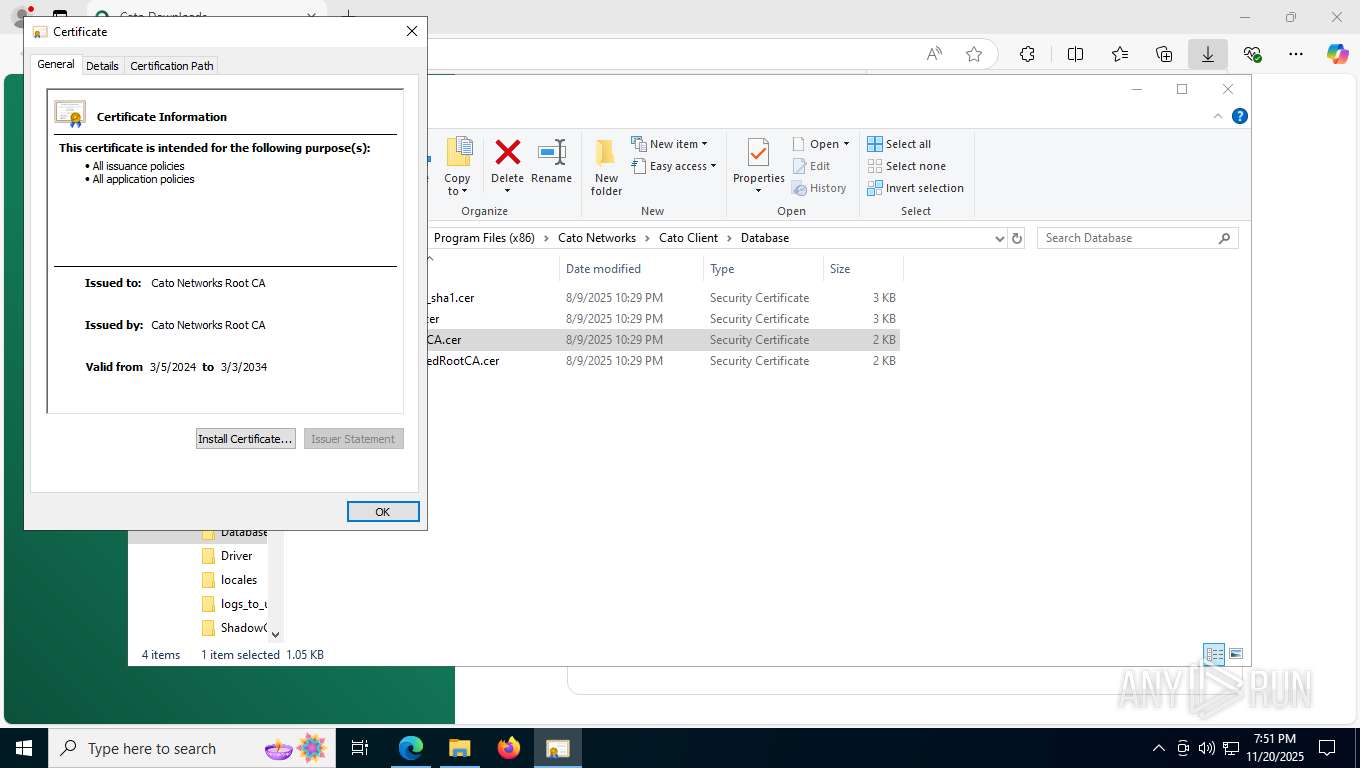
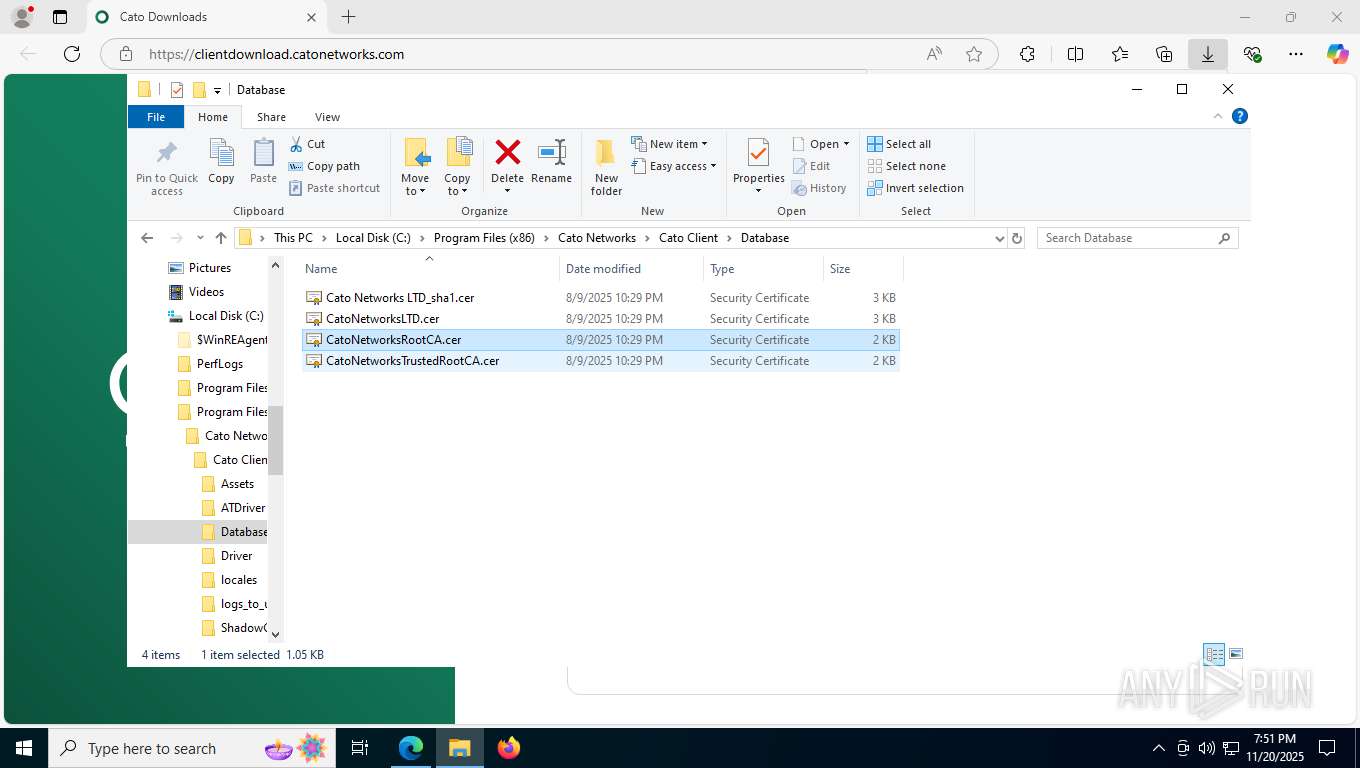
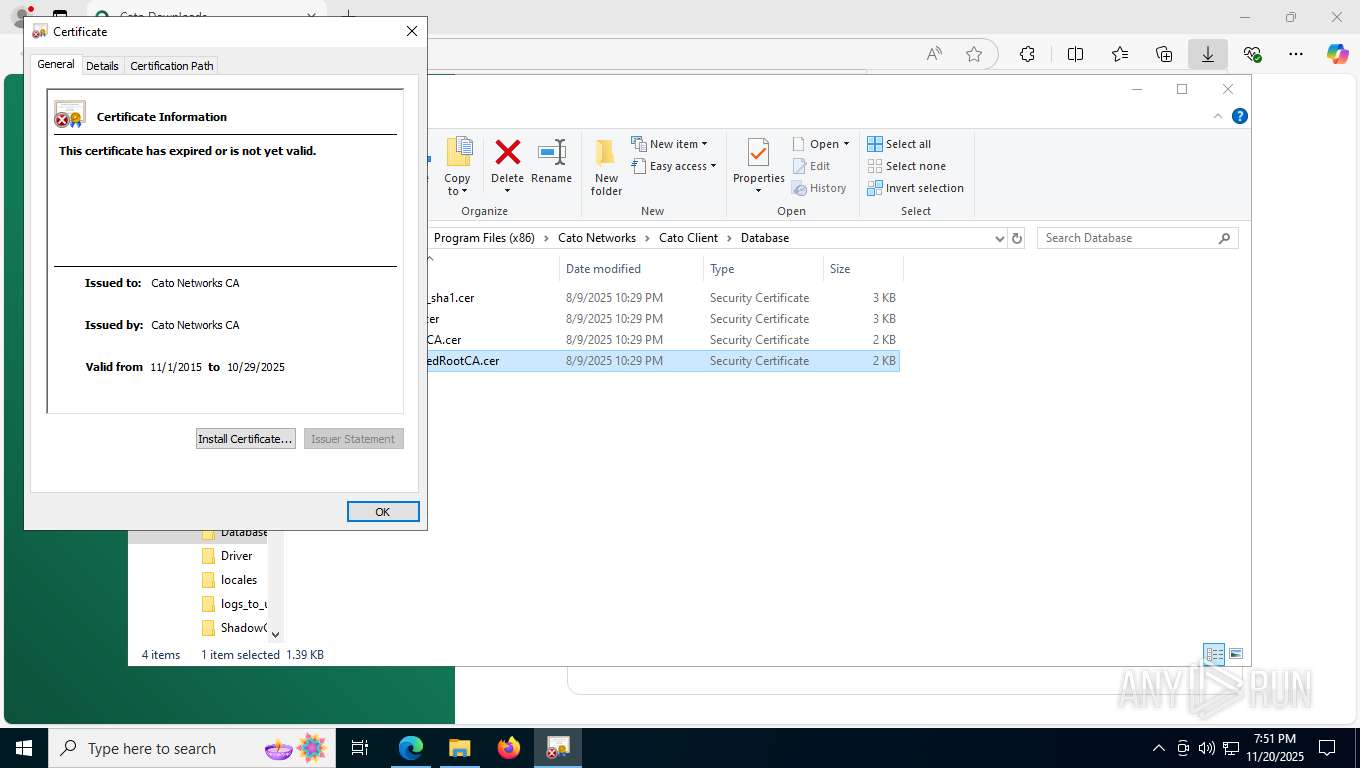
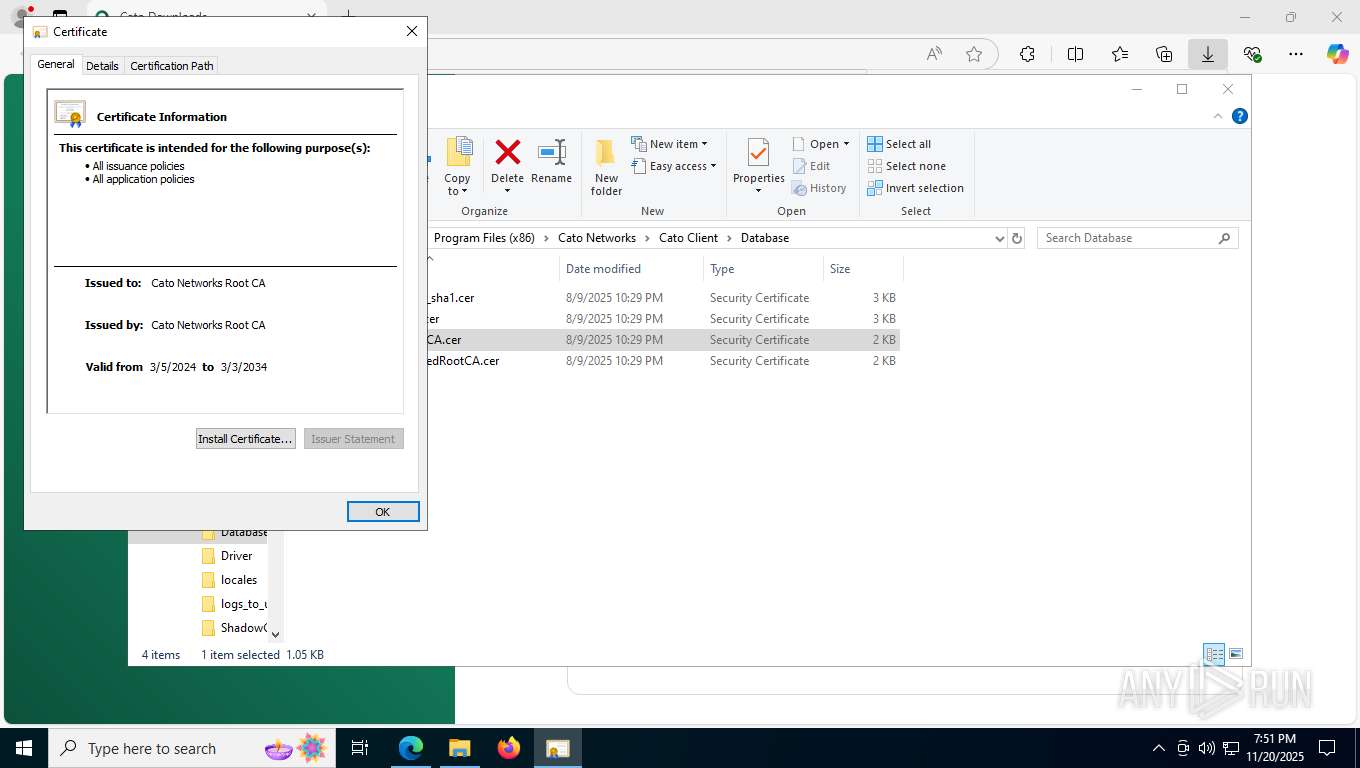
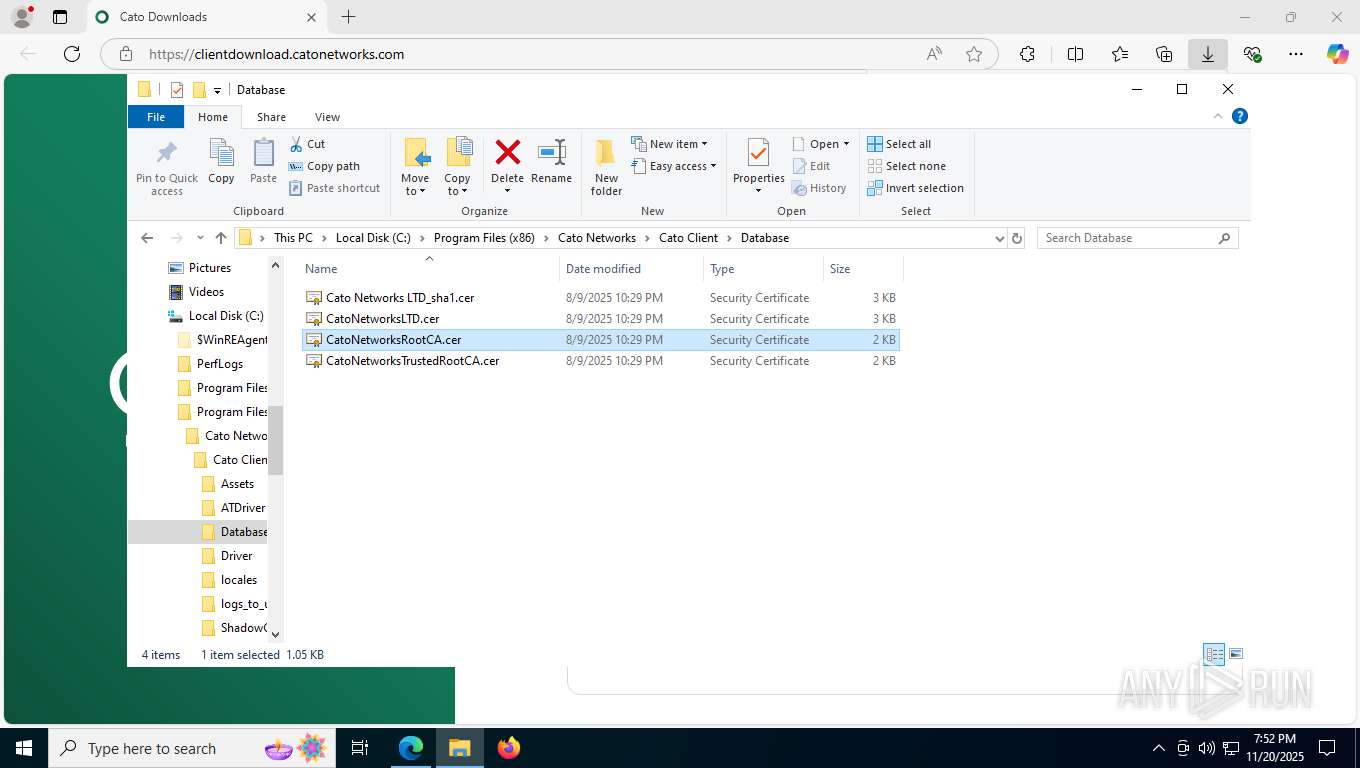
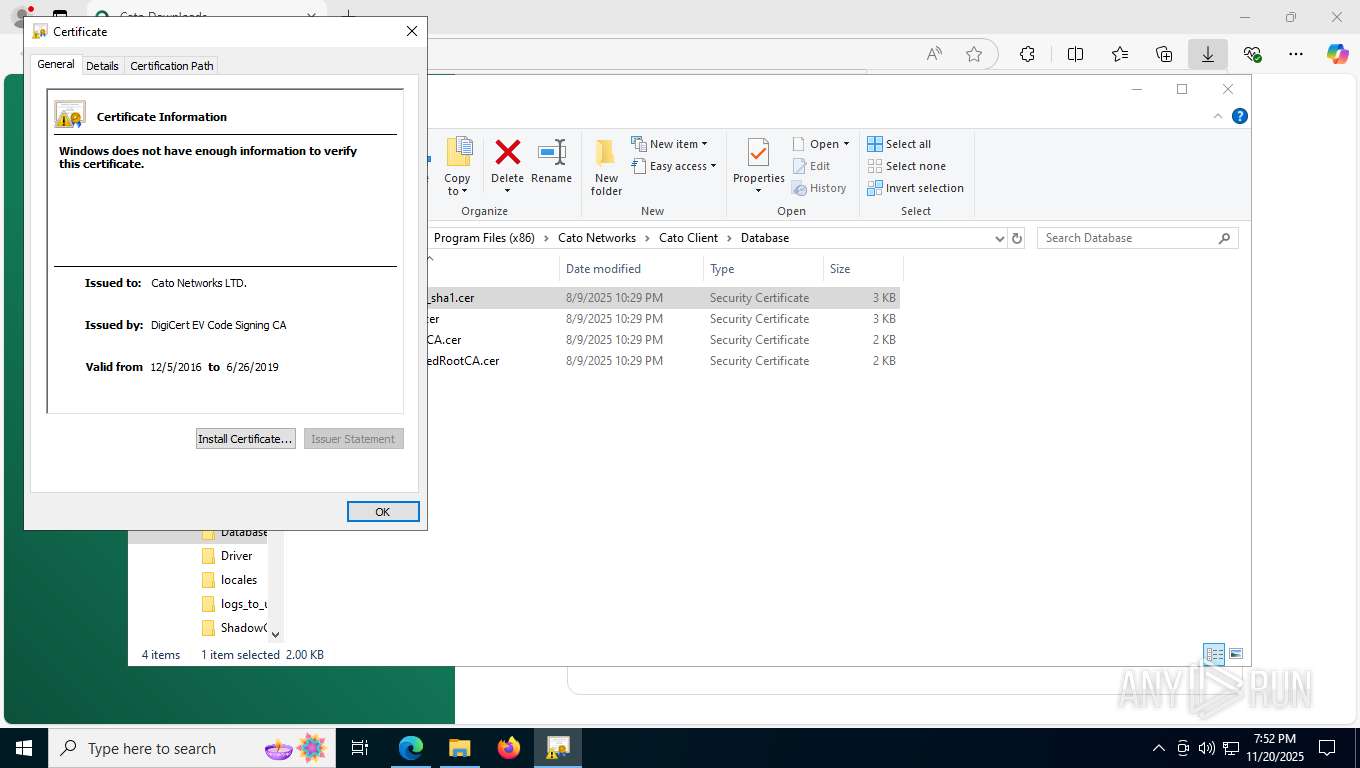
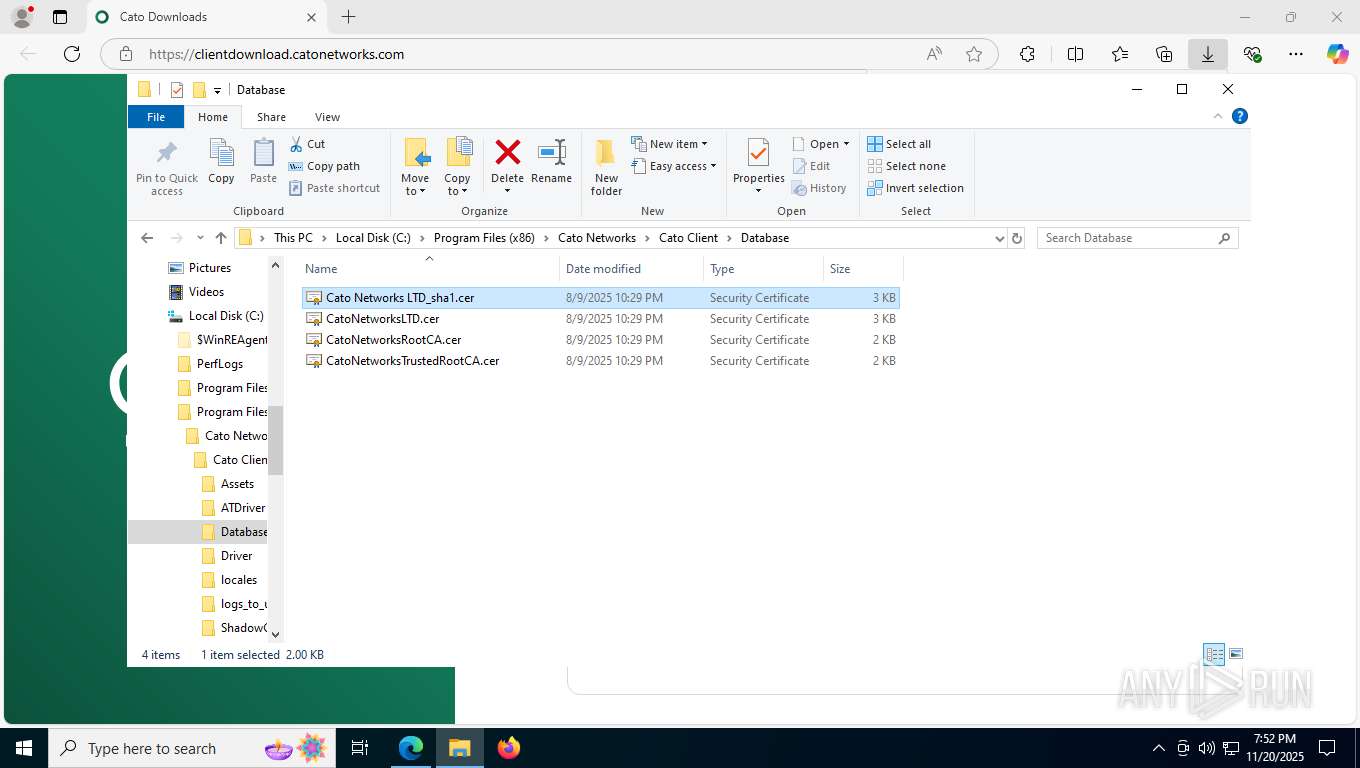
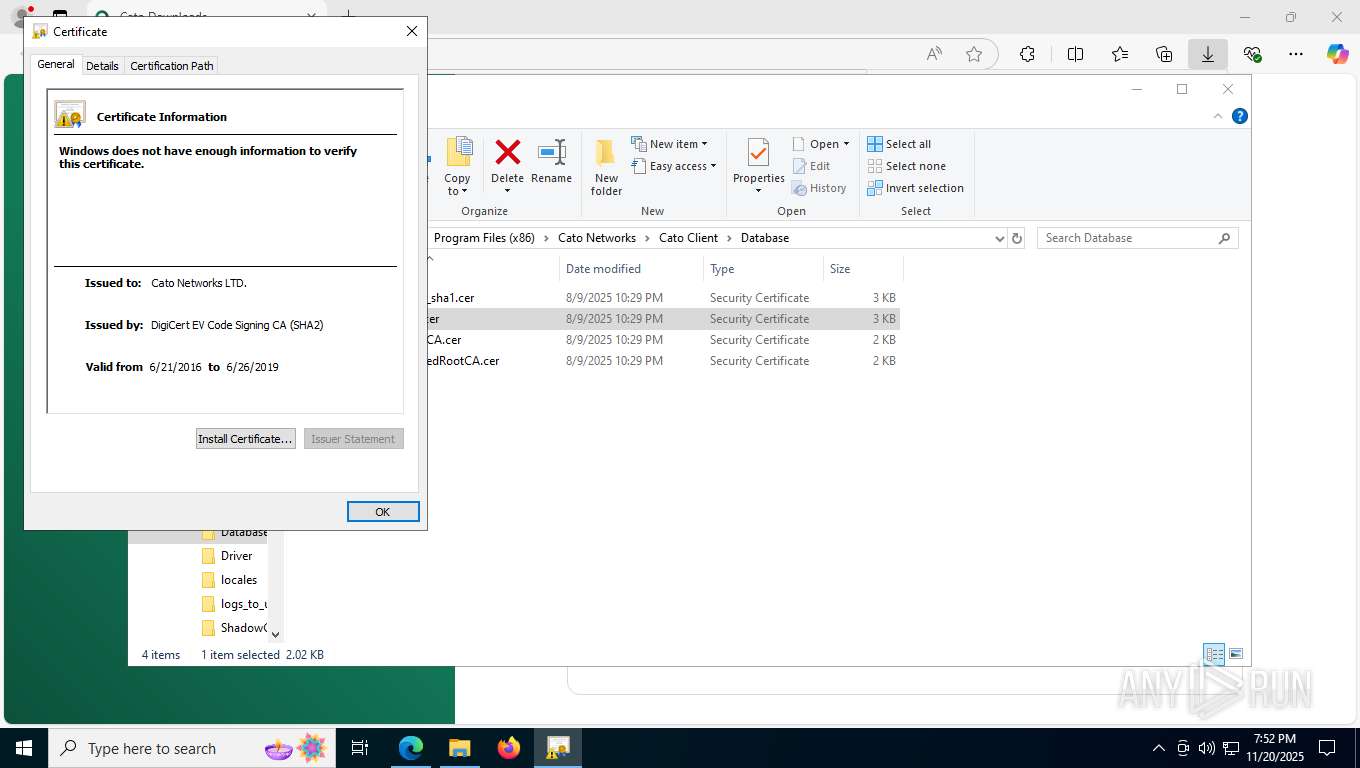
| 356 | "C:\WINDOWS\system32\rundll32.exe" cryptext.dll,CryptExtOpenCER C:\Program Files (x86)\Cato Networks\Cato Client\Database\Cato Networks LTD_sha1.cer | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 412 | C:\Windows\syswow64\MsiExec.exe -Embedding 642F5ECC2CA1F60BD2D04B5FE4DEEE36 E Global\MSI0000 | C:\Windows\SysWOW64\msiexec.exe | msiexec.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 896 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1060 | C:\WINDOWS\SysWOW64\certutil -addstore Root "C:\Program Files (x86)\Cato Networks\Cato Client\Database\CatoNetworksTrustedRootCA.cer" | C:\Windows\SysWOW64\certutil.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CertUtil.exe Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1148 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_collections.mojom.CollectionsDataManager --lang=en-US --service-sandbox-type=collections --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=4644,i,18028799496143744650,3810291794171371087,262144 --variations-seed-version --mojo-platform-channel-handle=6100 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 1464 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | sc.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1632 | "C:\WINDOWS\system32\rundll32.exe" cryptext.dll,CryptExtOpenCER C:\Program Files (x86)\Cato Networks\Cato Client\Database\Cato Networks LTD_sha1.cer | C:\Windows\System32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2056 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=quarantine.mojom.Quarantine --lang=en-US --service-sandbox-type=none --disable-quic --string-annotations --always-read-main-dll --field-trial-handle=6700,i,18028799496143744650,3810291794171371087,262144 --variations-seed-version --mojo-platform-channel-handle=7060 /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 133.0.3065.92 Modules
| |||||||||||||||
| 2144 | "C:\Program Files (x86)\Cato Networks\Cato Client\winvpnclient.cli.exe" | C:\Program Files (x86)\Cato Networks\Cato Client\winvpnclient.cli.exe | services.exe | ||||||||||||
User: SYSTEM Company: Cato Networks LTD. Integrity Level: SYSTEM Description: Cato Networks SDP Service Version: 5.18.5.8316 Modules
| |||||||||||||||
Total events
50 234
Read events
49 964
Write events
235
Delete events
35
Modification events
| (PID) Process: | (4568) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{618736E0-3C3D-11CF-810C-00AA00389B71}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (4568) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Interface\{618736E0-3C3D-11CF-810C-00AA00389B71}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (4568) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Volatile\00\MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{03022430-ABC4-11D0-BDE2-00AA001A1953}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (4568) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Volatile\00\MACHINE\SOFTWARE\Classes\Interface\{03022430-ABC4-11D0-BDE2-00AA001A1953}\TypeLib |
| Operation: | write | Name: | Version |
Value: 1.1 | |||
| (PID) Process: | (896) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000EF88C8AB565ADC0180030000081F0000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (896) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000EF88C8AB565ADC0180030000081F0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (896) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000003E5E1EAC565ADC0180030000081F0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (896) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000003E5E1EAC565ADC0180030000081F0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (896) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000D4BF20AC565ADC0180030000081F0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (896) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 15 | |||
Executable files
189
Suspicious files
267
Text files
79
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF161b8b.TMP | — | |
MD5:— | SHA256:— | |||
| 2184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF161b7c.TMP | — | |
MD5:— | SHA256:— | |||
| 2184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old~RF161b7c.TMP | — | |
MD5:— | SHA256:— | |||
| 2184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\ClientCertificates\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old~RF161b9b.TMP | — | |
MD5:— | SHA256:— | |||
| 2184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF161b9b.TMP | — | |
MD5:— | SHA256:— | |||
| 2184 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
30
TCP/UDP connections
80
DNS requests
79
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3332 | svchost.exe | GET | 206 | 185.160.60.100:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/ddbf4492-d475-4fe4-bcde-6cbac56f6034?P1=1763844346&P2=404&P3=2&P4=JkbUhgUkMZhBKKOk%2f3Q%2fGsB3pypQqMedK%2b6s2gCwKsUXbF4%2bCvA2oDASwb7xp%2bFiOtHTjfkt%2bcVq%2fzt9R67YQA%3d%3d | unknown | — | — | whitelisted |
3100 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.3.crl | unknown | — | — | whitelisted |
3332 | svchost.exe | HEAD | 200 | 185.160.60.100:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/ddbf4492-d475-4fe4-bcde-6cbac56f6034?P1=1763844346&P2=404&P3=2&P4=JkbUhgUkMZhBKKOk%2f3Q%2fGsB3pypQqMedK%2b6s2gCwKsUXbF4%2bCvA2oDASwb7xp%2bFiOtHTjfkt%2bcVq%2fzt9R67YQA%3d%3d | unknown | — | — | whitelisted |
7376 | msedge.exe | GET | 200 | 150.171.28.11:80 | http://edge.microsoft.com/browsernetworktime/time/1/current?cup2key=2:h5mVXSgiAbjiciuZfUNDudpwPCO87cJYWHX8FR6O-vM&cup2hreq=e3b0c44298fc1c149afbf4c8996fb92427ae41e4649b934ca495991b7852b855 | unknown | — | — | whitelisted |
6492 | svchost.exe | GET | 200 | 95.101.35.8:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4452 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3332 | svchost.exe | GET | 200 | 185.160.60.100:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4c4fdee0-d69c-42b7-bf5c-3ec046e9dfc9?P1=1763844351&P2=404&P3=2&P4=cz3G9rBIaRBWA2LaTHwN5kg4R8GCUYtqZlBG4Zqdx5l%2fGfbDJuTt%2flkGWAnv%2b9bPgDRPZaRJPz9Q6QHX6fngoA%3d%3d | unknown | — | — | whitelisted |
3332 | svchost.exe | HEAD | 200 | 185.160.60.100:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/4c4fdee0-d69c-42b7-bf5c-3ec046e9dfc9?P1=1763844351&P2=404&P3=2&P4=cz3G9rBIaRBWA2LaTHwN5kg4R8GCUYtqZlBG4Zqdx5l%2fGfbDJuTt%2flkGWAnv%2b9bPgDRPZaRJPz9Q6QHX6fngoA%3d%3d | unknown | — | — | whitelisted |
3332 | svchost.exe | HEAD | 200 | 185.160.60.100:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/550117a4-8c0f-4d0d-8ff8-7c3caccb0e8a?P1=1763844353&P2=404&P3=2&P4=F0%2bl%2f4VG9kFSBskI%2bzjO7U9W1%2fpqKakcYMCsZnSm1lIQTEyzXvkF44UhompMCxIm2zDa1YHtMiDi1dGfku6Z8w%3d%3d | unknown | — | — | whitelisted |
3332 | svchost.exe | HEAD | 200 | 185.160.60.100:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/fa2a82d6-5b86-46d7-867a-3eb80ab6bdaf?P1=1763844349&P2=404&P3=2&P4=Dk4Qlt5%2fz1U6h1CGHeich%2fM7QXBXMGONASa2CPmb%2fvWMwrUvG24IHczc1RAidDrrORCBrg9WXrjMZZPzQMxlHA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6492 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5596 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5040 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
7376 | msedge.exe | 150.171.28.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7376 | msedge.exe | 150.171.22.17:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7376 | msedge.exe | 150.171.28.11:80 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7376 | msedge.exe | 107.154.248.90:443 | clientdownload.catonetworks.com | INCAPSULA | US | whitelisted |
7376 | msedge.exe | 92.123.104.45:443 | copilot.microsoft.com | Akamai International B.V. | DE | whitelisted |
7376 | msedge.exe | 92.123.104.61:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
clientdownload.catonetworks.com |
| whitelisted |
copilot.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
xpaywalletcdn.azureedge.net |
| whitelisted |
update.googleapis.com |
| whitelisted |
edgeassetservice.azureedge.net |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] JS obfuscation by obfuscator.io |
— | — | Potential Corporate Privacy Violation | ET INFO PE EXE or DLL Windows file download HTTP |
— | — | Potentially Bad Traffic | ET INFO Executable served from Amazon S3 |
— | — | Potentially Bad Traffic | SUSPICIOUS [ANY.RUN] JS obfuscation by obfuscator.io |
— | — | Generic Protocol Command Decode | SURICATA HTTP Request unrecognized authorization method |
Process | Message |
|---|---|
msiexec.exe | 20/11/25 19:48:29.733 Info SetScmAccessibleProp: called |
msiexec.exe | |
msiexec.exe | 20/11/25 19:48:29.734 Info setScmAccessibleProp: Service Control Manager is accessible |
msiexec.exe | |
msiexec.exe | |
msiexec.exe | |
msiexec.exe | |
msiexec.exe | 20/11/25 19:48:59.884 Info WriteDevLog: InstallDriver Start |
msiexec.exe | 20/11/25 19:48:59.884 Info WriteDevLog: cmdRemove: MSG_REMOVE_TAIL_NONE |
msiexec.exe | 20/11/25 19:48:59.884 Info WriteDevLog: cmdInstall: got valid parameters |