| File name: | control.bat |
| Full analysis: | https://app.any.run/tasks/55fdc704-3a9c-4c02-958a-d3e09bc90903 |
| Verdict: | Malicious activity |
| Analysis date: | August 21, 2020, 10:24:25 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | Little-endian UTF-16 Unicode text, with very long lines, with no line terminators |
| MD5: | 553908FB97DE01FEDD83DFCC14D6CCD1 |
| SHA1: | D05C974C5CD0EDED2543EA805EDF012094FC80D4 |
| SHA256: | 9DCBD14AE1B047C21A3AE6C544D34B13BE8414C047519FA135249049204E7327 |
| SSDEEP: | 96:ub/Ax5xBKIbyfr28o9CD2Jw2ggSQNnFTaWJ:ueB |
MALICIOUS
Starts NET.EXE for service management
- cmd.exe (PID: 2128)
SUSPICIOUS
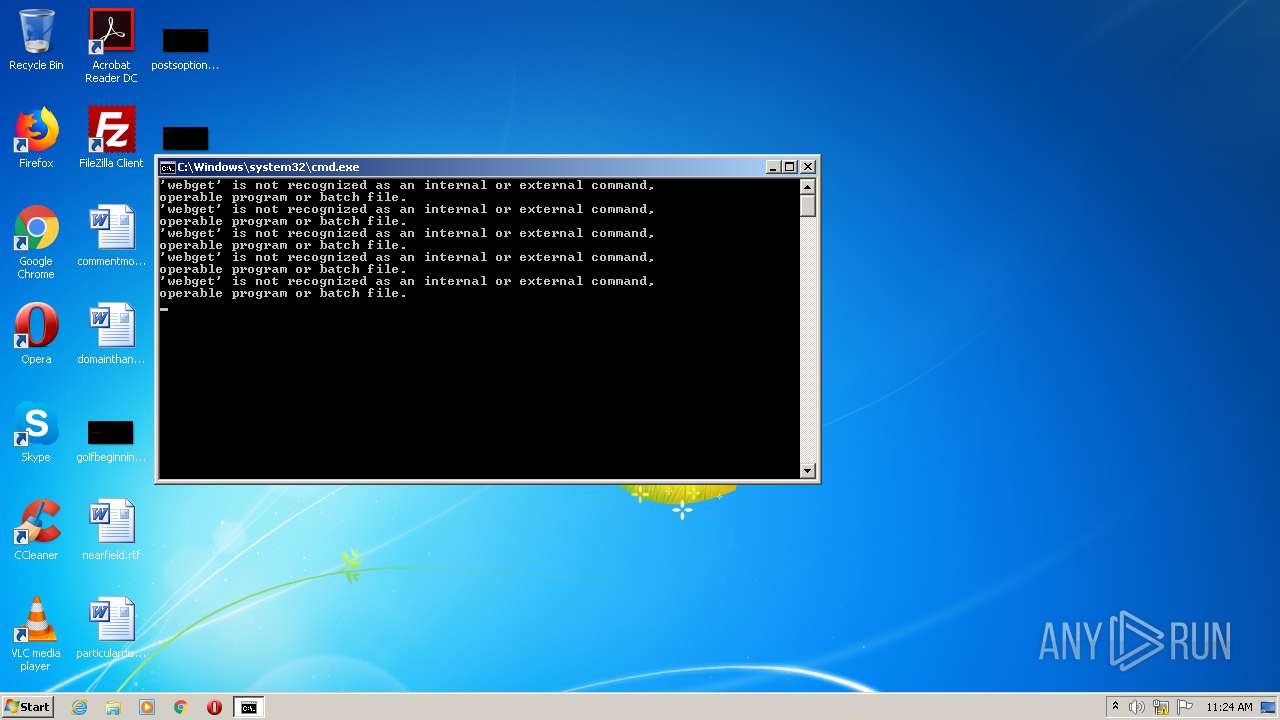
Uses WMIC.EXE to obtain a system information
- cmd.exe (PID: 2128)
Creates files in the Windows directory
- cmd.exe (PID: 2128)
Removes files from Windows directory
- cmd.exe (PID: 2128)
Starts SC.EXE for service management
- cmd.exe (PID: 2128)
Uses ATTRIB.EXE to modify file attributes
- cmd.exe (PID: 2128)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .txt | | | Text - UTF-16 (LE) encoded (66.6) |
|---|---|---|
| .mp3 | | | MP3 audio (33.3) |
Total processes
67
Monitored processes
23
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 560 | attrib +S +H +R C:\Windows\system32\System | C:\Windows\system32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 664 | C:\Windows\system32\net1 stop servicemains | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
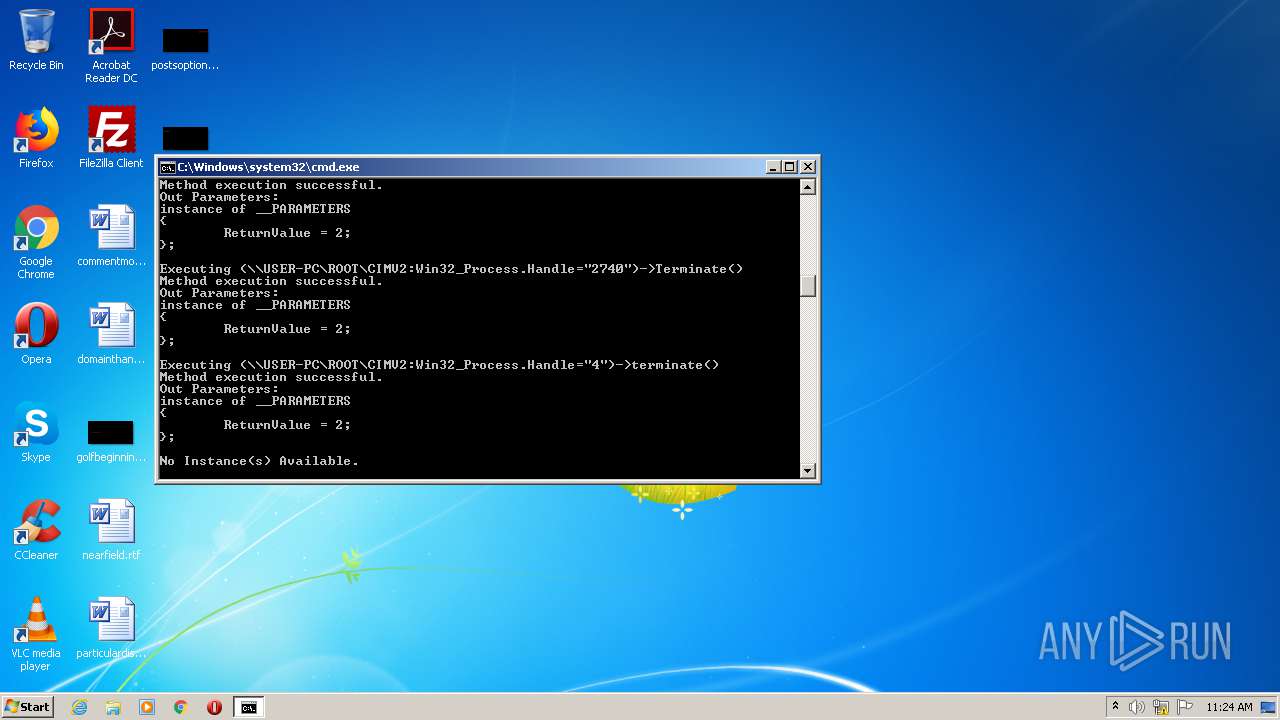
| 760 | wmic process where name="unitezip.exe" call terminate | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
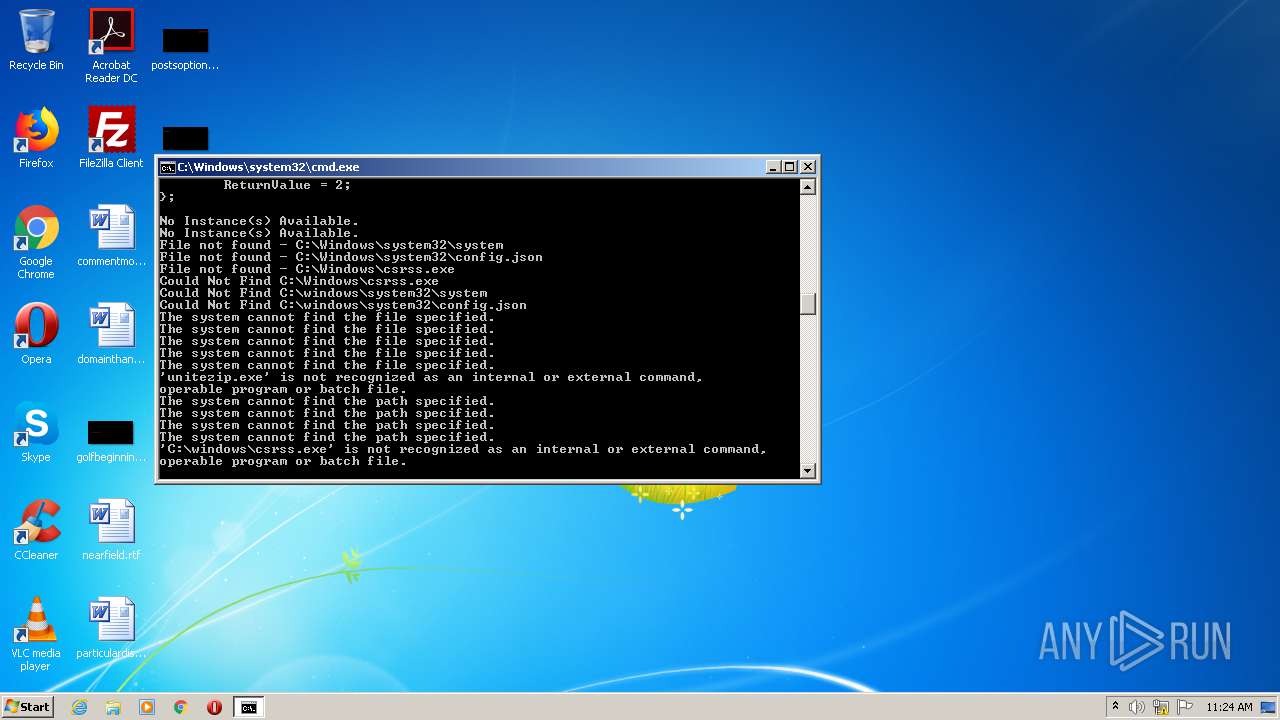
| 1320 | attrib -s -h -r C:\Windows\system32\config.json | C:\Windows\system32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1696 | attrib -s -h -r C:\Windows\system32\system | C:\Windows\system32\attrib.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Attribute Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1732 | net stop servicemains | C:\Windows\system32\net.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2080 | "C:\WINDOWS\regedit.exe" /s C:\Windows\temp\temp\1.reg | C:\WINDOWS\regedit.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2128 | cmd /c ""C:\Users\admin\Desktop\control.bat" " | C:\Windows\system32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2408 | find /i "C:\Windows\System32\System" C:\Windows\temp\p1.txt | C:\Windows\system32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2452 | C:\Windows\system32\net1 start clr_optimization_v3.5.30729_64 | C:\Windows\system32\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
85
Read events
81
Write events
4
Delete events
0
Modification events
| (PID) Process: | (2128) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2128) cmd.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
0
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2128 | cmd.exe | C:\Windows\Temp\p1.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
regedit.exe | REGEDIT: CreateFile failed, GetLastError() = 2
|