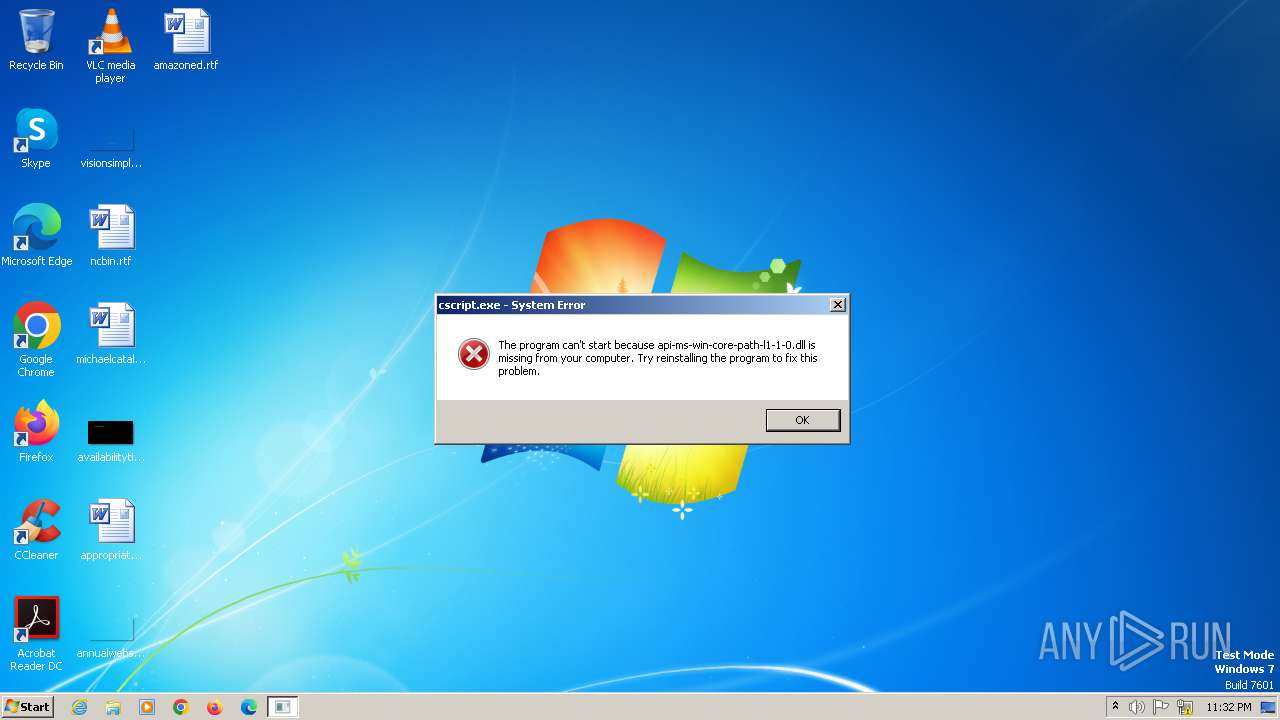
| File name: | cscript.exe |
| Full analysis: | https://app.any.run/tasks/afd5367d-31dc-4a5d-8830-7955fd19d42e |
| Verdict: | Malicious activity |
| Analysis date: | November 30, 2023, 23:31:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32+ executable (GUI) x86-64, for MS Windows |
| MD5: | 16A5CCEADAC88938E627D7EC9A0DCF7F |
| SHA1: | 7821CD004BCA8A52F27FDC9D5BA90E0FD085942B |
| SHA256: | 9DA23BFC87A60275ADF3D0EBDA2CE71FE65D7D03EFA21060E39652F0DF87129A |
| SSDEEP: | 98304:8rkPiI1suDbjR6Y9nCaNOMJYECTJklpS5bPjlYiLonqMnksUKfrC7lORacGp4BLl:hgohNWYDmS66 |
MALICIOUS
Drops the executable file immediately after the start
- cscript.exe (PID: 2264)
SUSPICIOUS
Process drops legitimate windows executable
- cscript.exe (PID: 2264)
The process drops C-runtime libraries
- cscript.exe (PID: 2264)
Loads Python modules
- cscript.exe (PID: 1168)
Application launched itself
- cscript.exe (PID: 2264)
INFO
Checks supported languages
- cscript.exe (PID: 2264)
- cscript.exe (PID: 1168)
Reads the computer name
- cscript.exe (PID: 2264)
Create files in a temporary directory
- cscript.exe (PID: 2264)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2023:11:30 14:26:29+01:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.37 |
| CodeSize: | 171008 |
| InitializedDataSize: | 115200 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc1a0 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.812.10240.16384 |
| ProductVersionNumber: | 5.812.10240.16384 |
| FileFlagsMask: | 0x0003 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Microsoft Corporation |
| FileDescription: | Microsoft ® Console Based Script Host |
| FileVersion: | 5.812.10240.16384 |
| InternalName: | cscript.exe |
| LegalCopyright: | © Microsoft Corporation. All rights reserved. |
| OriginalFileName: | cscript.exe |
| ProductName: | Microsoft ® Windows Script Host |
| ProductVersion: | 5.812.10240.16384 |
Total processes
34
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1168 | "C:\Users\admin\AppData\Local\Temp\cscript.exe" | C:\Users\admin\AppData\Local\Temp\cscript.exe | — | cscript.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 2264 | "C:\Users\admin\AppData\Local\Temp\cscript.exe" | C:\Users\admin\AppData\Local\Temp\cscript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
Total events
13
Read events
13
Write events
0
Delete events
0
Modification events
Executable files
18
Suspicious files
2
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2264 | cscript.exe | C:\Users\admin\AppData\Local\Temp\_MEI22642\_hashlib.pyd | executable | |
MD5:C8B153F0BE8569CE2C2DE3D55952D9C7 | SHA256:AF9F39D2A5D762214F6DE2C8FEC0A5BC6BE0B8223EF47164CAA4C6E3D6437A58 | |||
| 2264 | cscript.exe | C:\Users\admin\AppData\Local\Temp\_MEI22642\_bz2.pyd | executable | |
MD5:85C70974FAC8E621ED6E3E9A993FBD6F | SHA256:610983BBCB8EE27963C17EAD15E69AD76EC78FAC64DEB7345CA90D004034CDD6 | |||
| 2264 | cscript.exe | C:\Users\admin\AppData\Local\Temp\_MEI22642\_lzma.pyd | executable | |
MD5:BC2EBD2A95619AB14A16944B0AB8BDE5 | SHA256:AEB3FD8B855B35204B5088C7A1591CC1CA78FFFE707D70E41D99564B6CB617C6 | |||
| 2264 | cscript.exe | C:\Users\admin\AppData\Local\Temp\_MEI22642\_queue.pyd | executable | |
MD5:FCBB24550F59068A37EA09A490923C8A | SHA256:DE2AC6D99234A28DCF583D90DCA7256DE986FCA9E896C9AAFD1F18BB536978B8 | |||
| 2264 | cscript.exe | C:\Users\admin\AppData\Local\Temp\_MEI22642\VCRUNTIME140.dll | executable | |
MD5:4585A96CC4EEF6AAFD5E27EA09147DC6 | SHA256:A8F950B4357EC12CFCCDDC9094CCA56A3D5244B95E09EA6E9A746489F2D58736 | |||
| 2264 | cscript.exe | C:\Users\admin\AppData\Local\Temp\_MEI22642\_decimal.pyd | executable | |
MD5:3923E27B9378DA500039E996222FFEE6 | SHA256:0275B03041F966E587D1C4C50266C3FDFF1E1A65F652AD07B59CB85845B5457E | |||
| 2264 | cscript.exe | C:\Users\admin\AppData\Local\Temp\_MEI22642\_socket.pyd | executable | |
MD5:F6D0876B14BCA5A264EC231895D80072 | SHA256:BCBF9A952473E53F130CE77B0DB69FE08C5845CE10DBE8C320B40F171A15D6A8 | |||
| 2264 | cscript.exe | C:\Users\admin\AppData\Local\Temp\_MEI22642\_ssl.pyd | executable | |
MD5:53996068AE9CF68619DA8CB142410D5E | SHA256:CBD320C42277086CD962FD0B25842904CEB436346D380319625F54363F031DCF | |||
| 2264 | cscript.exe | C:\Users\admin\AppData\Local\Temp\_MEI22642\base_library.zip | compressed | |
MD5:3909F1A45B16C6C6EF797032DE7E3B61 | SHA256:56CCE68DA6A7EBD11AAB4B4A4E6A164647B42B29AE57656532C530D1E22E5B44 | |||
| 2264 | cscript.exe | C:\Users\admin\AppData\Local\Temp\_MEI22642\_sqlite3.pyd | executable | |
MD5:0FDEDCB9B3A45152239CA4B1AEA4B211 | SHA256:0FC03D25467850181C0FC4F0F8919C8C47CBA2BF578698D4354AA84FD810C7F7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
324 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1956 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |