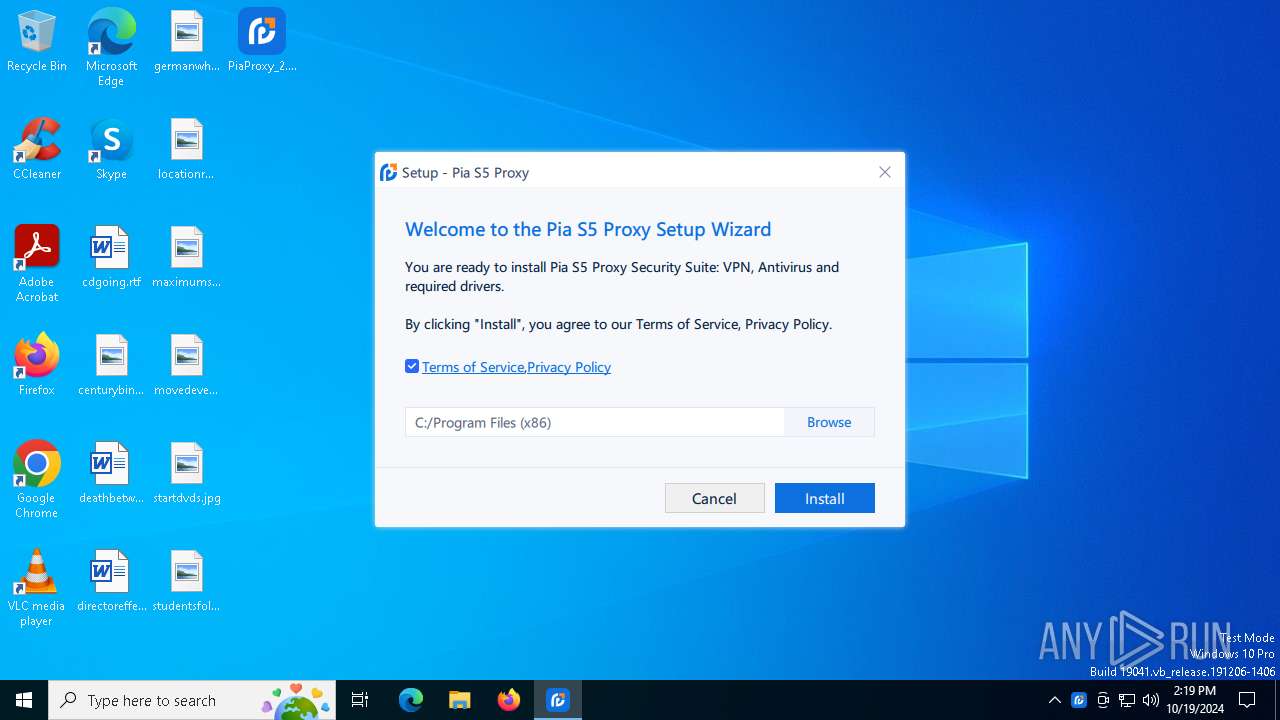
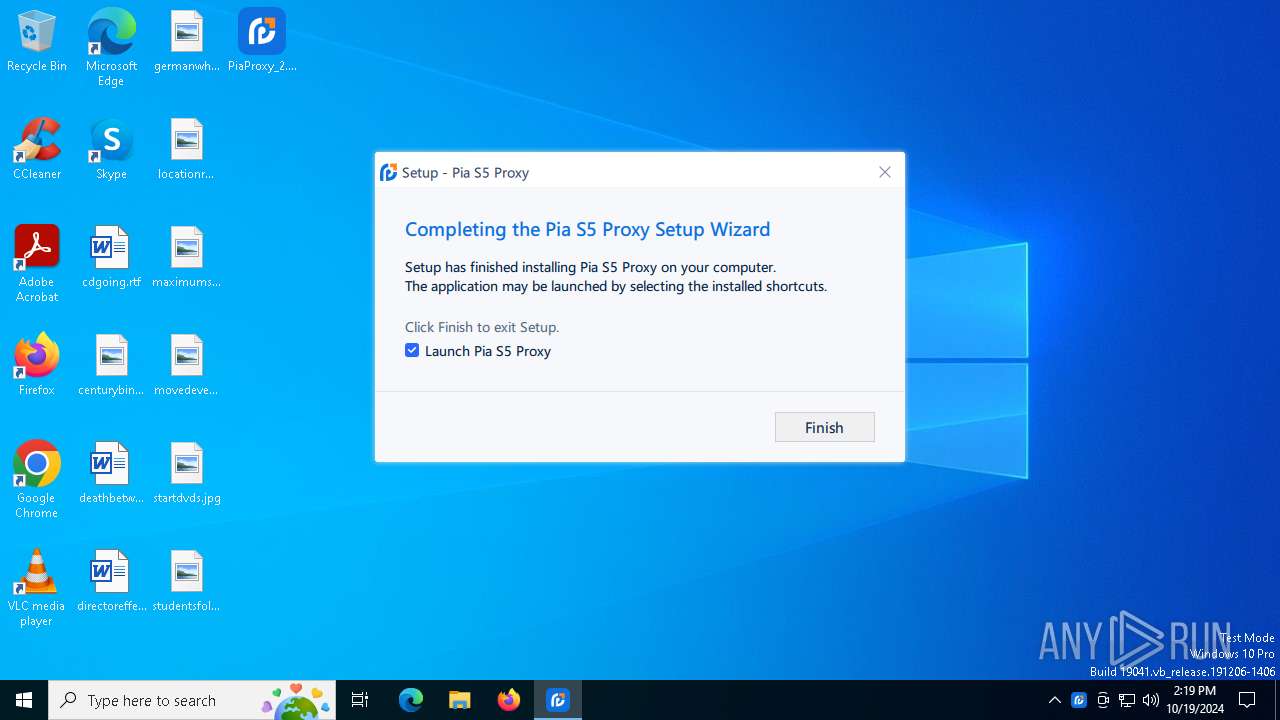
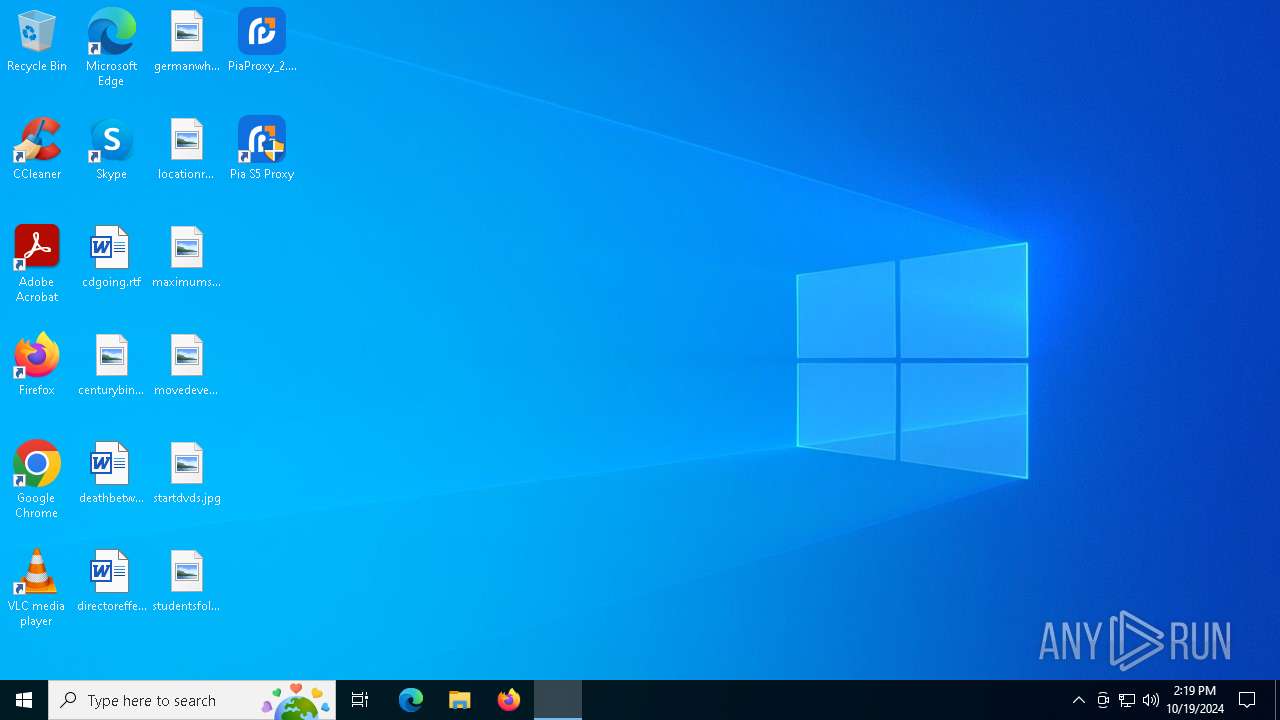
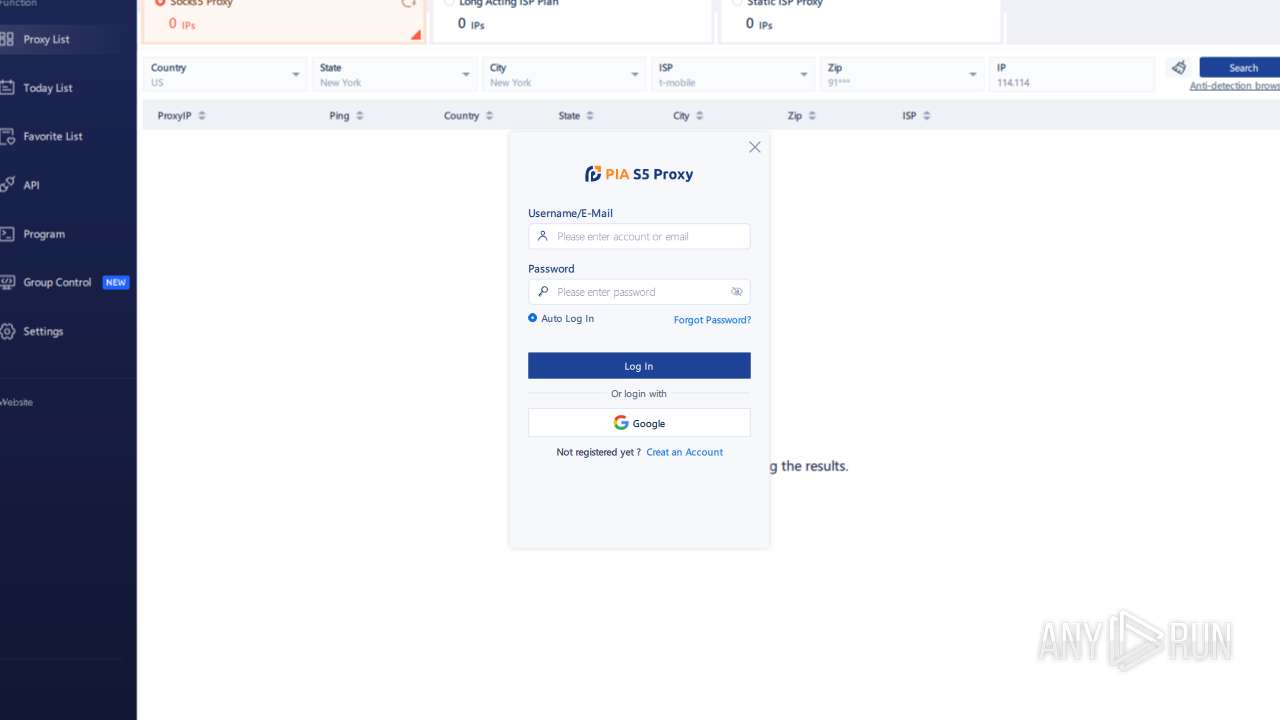
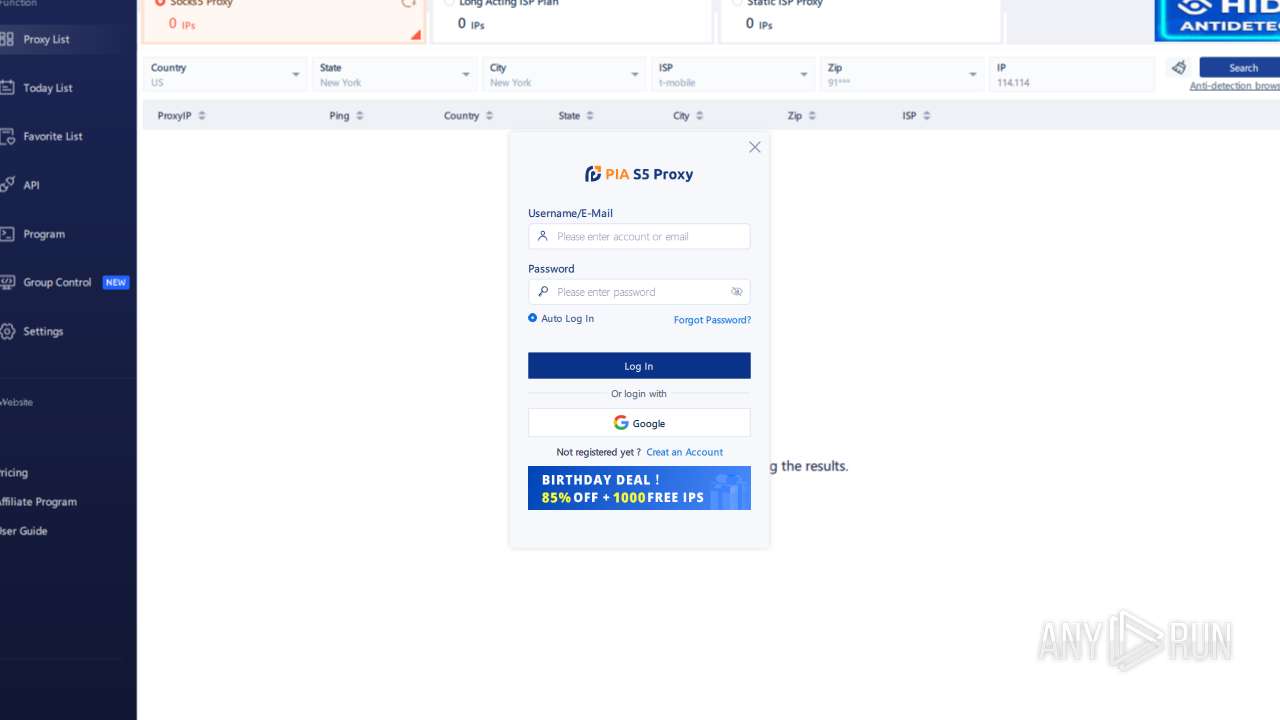
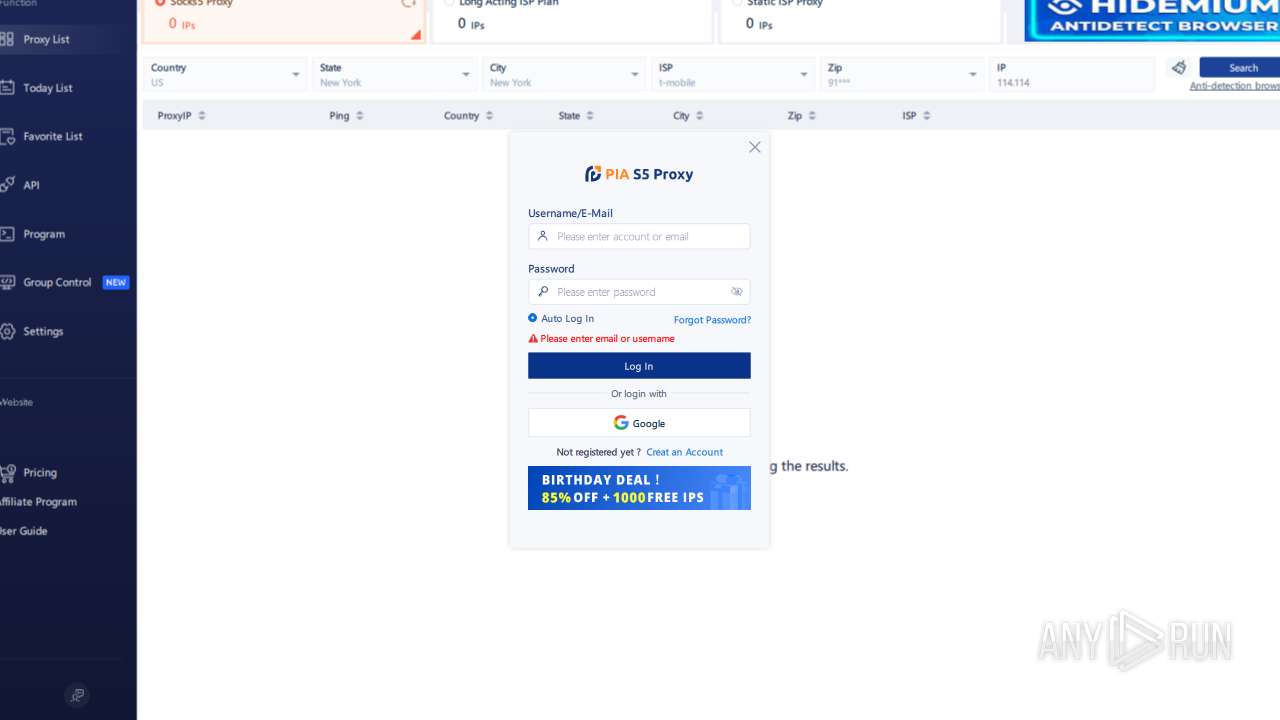
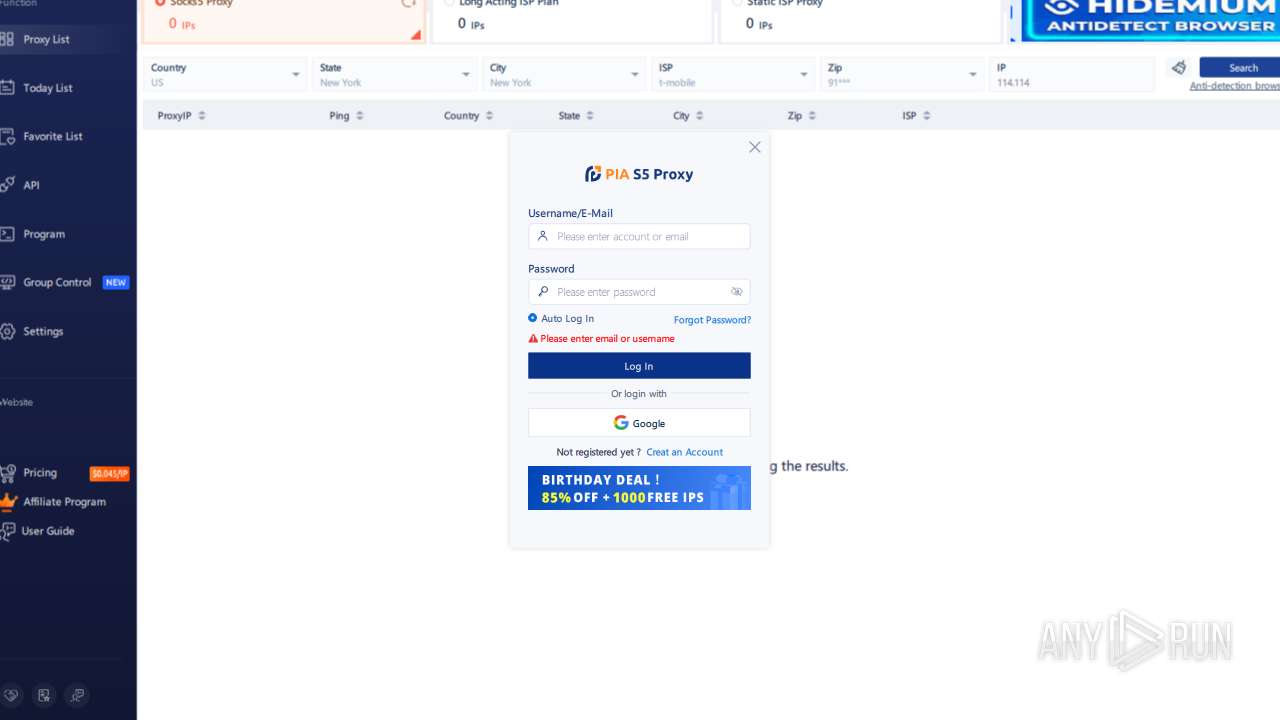
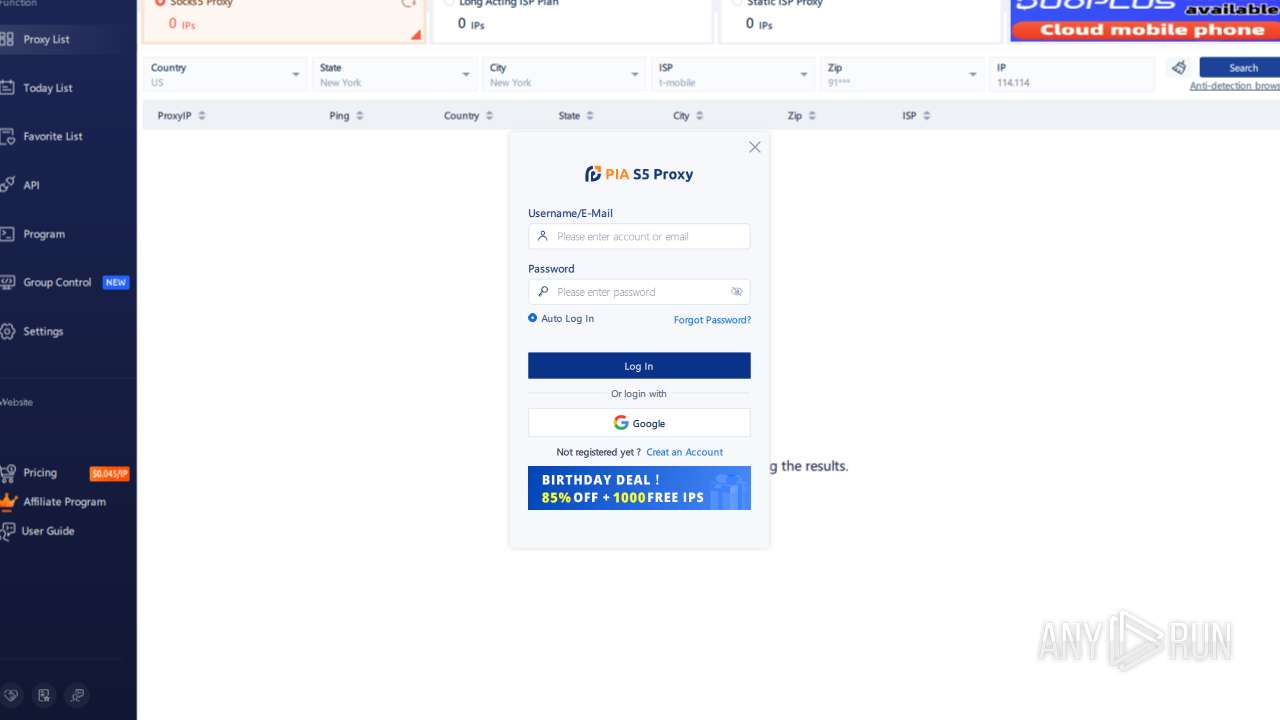
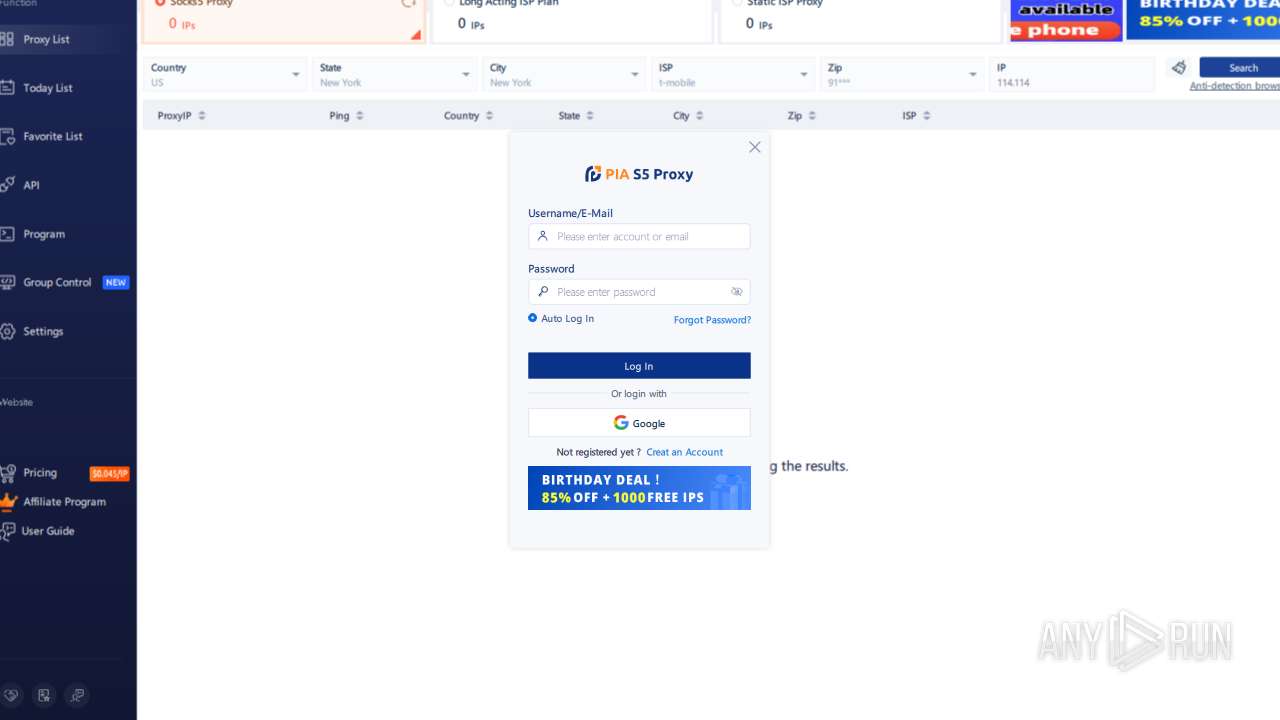
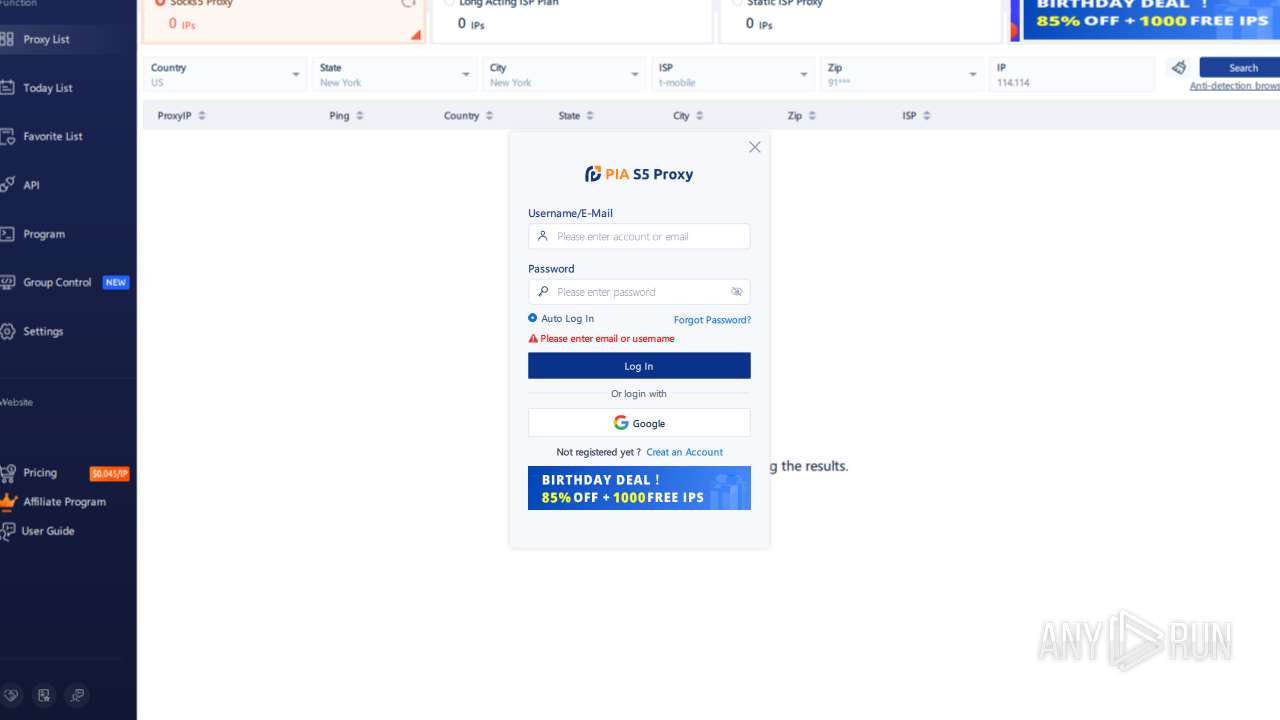
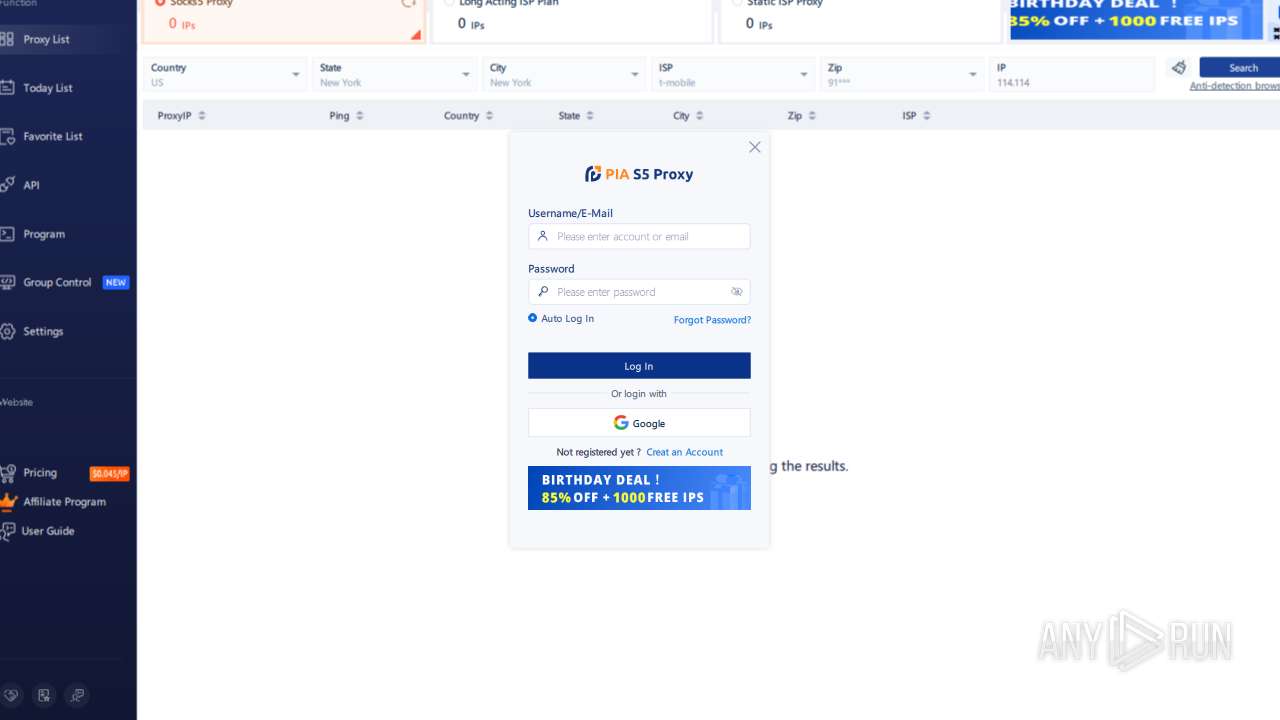
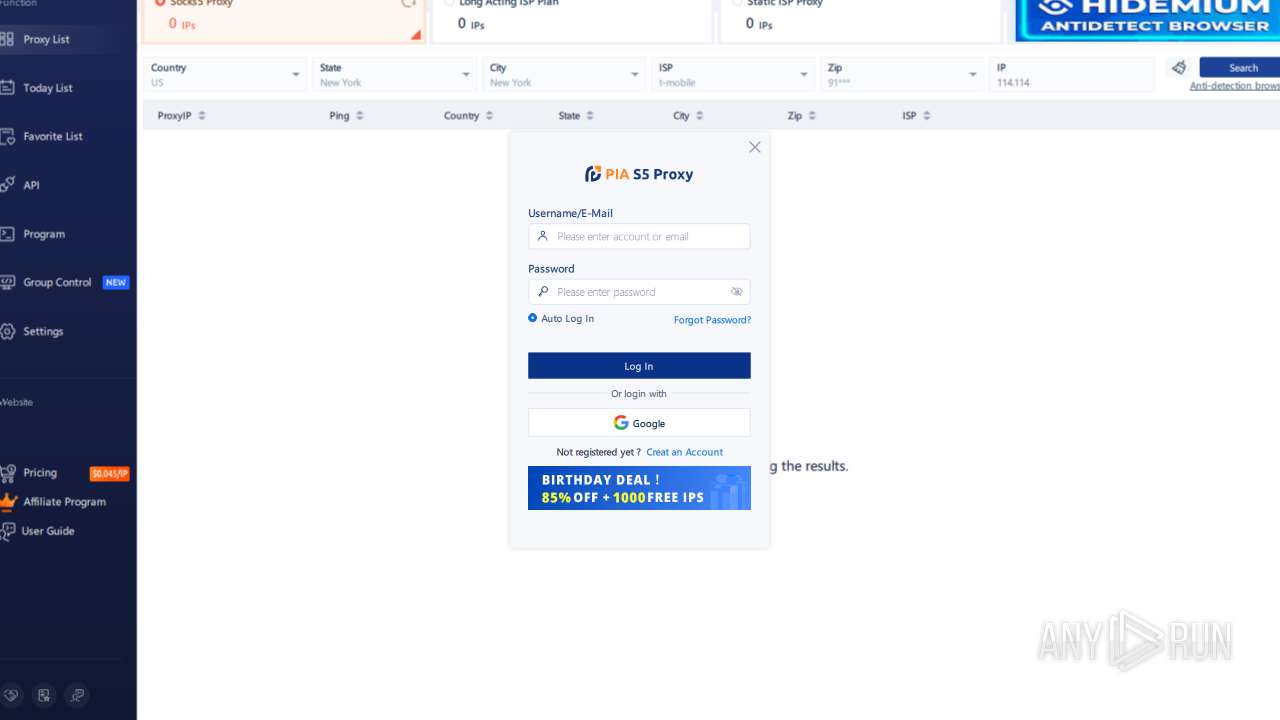
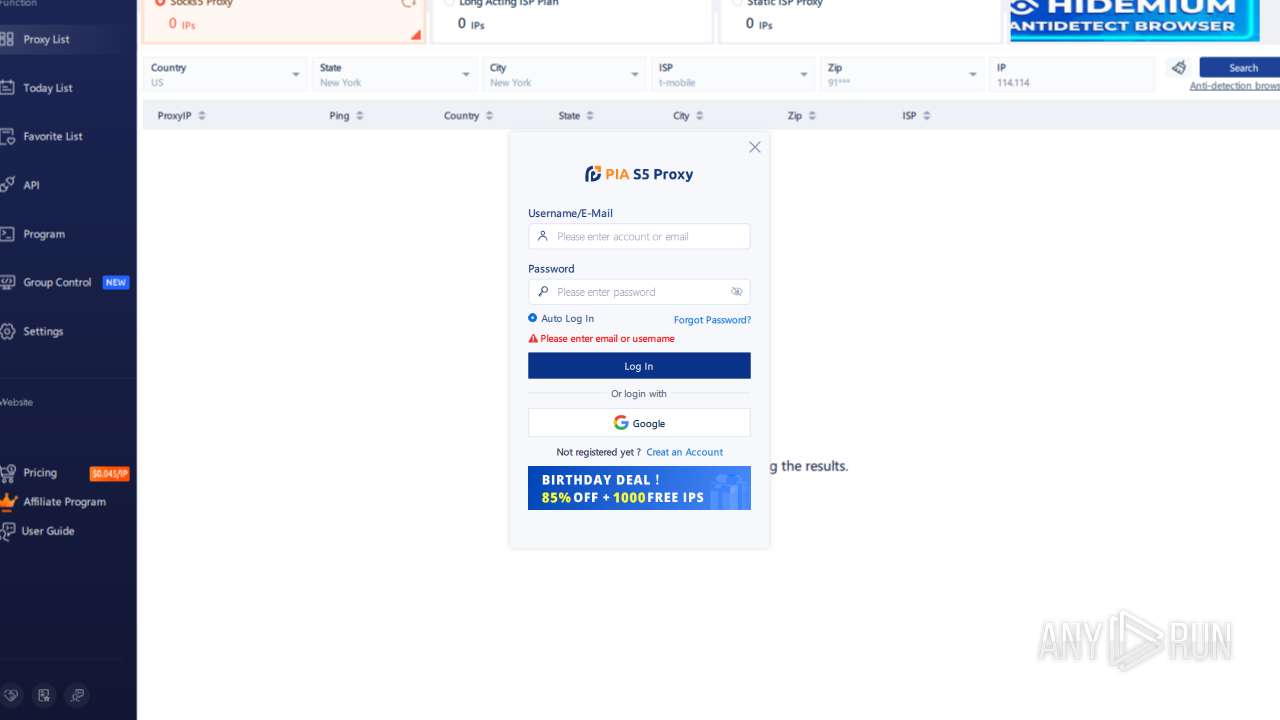
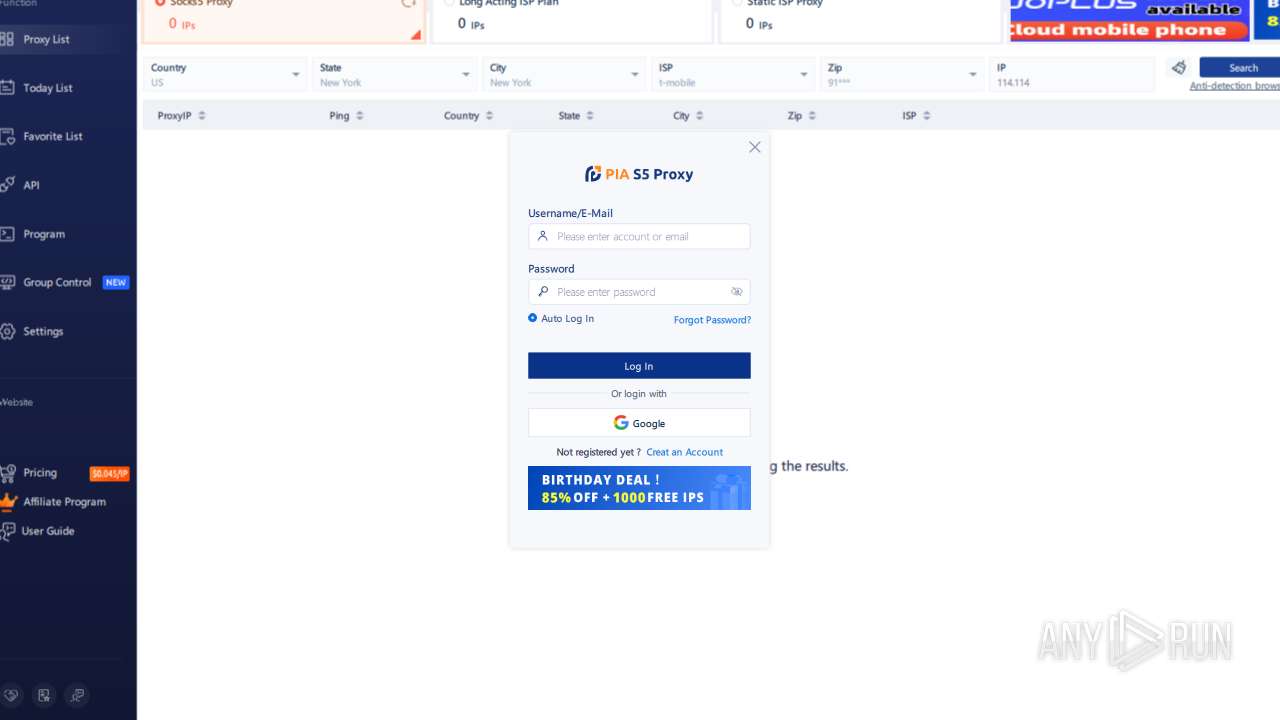
| File name: | PiaProxy_2.1.7_202409061452_Cus.exe |
| Full analysis: | https://app.any.run/tasks/1721c9aa-c106-4645-b8a6-8fc9aeceffad |
| Verdict: | Malicious activity |
| Analysis date: | October 19, 2024, 14:18:48 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 258A8AB87F035049DF8BBBFD010543E2 |
| SHA1: | 9C02D1AD6303737B17F20B7DB12279BD2E6E6E14 |
| SHA256: | 9D9E27A465351588B5E0860A1881658F7E1BAB99AEE3182039A06AB8067E3448 |
| SSDEEP: | 196608:tkRBL1eC3FQ49X2I/VrlxvayplBd2v+f+sth:tUBIC1Q4okjbPQ+WsH |
MALICIOUS
Changes the autorun value in the registry
- install.exe (PID: 6180)
- PiaProxy.exe (PID: 3772)
SUSPICIOUS
The process drops C-runtime libraries
- PiaProxy_2.1.7_202409061452_Cus.exe (PID: 3852)
- install.exe (PID: 6180)
Drops a system driver (possible attempt to evade defenses)
- PiaProxy_2.1.7_202409061452_Cus.exe (PID: 3852)
- install.exe (PID: 6180)
Process drops legitimate windows executable
- PiaProxy_2.1.7_202409061452_Cus.exe (PID: 3852)
- install.exe (PID: 6180)
Executable content was dropped or overwritten
- PiaProxy_2.1.7_202409061452_Cus.exe (PID: 3852)
- install.exe (PID: 6180)
Reads security settings of Internet Explorer
- PiaProxy_2.1.7_202409061452_Cus.exe (PID: 3852)
Searches for installed software
- install.exe (PID: 6180)
Creates file in the systems drive root
- update.exe (PID: 2364)
Creates a software uninstall entry
- install.exe (PID: 6180)
INFO
Create files in a temporary directory
- PiaProxy_2.1.7_202409061452_Cus.exe (PID: 3852)
- install.exe (PID: 6180)
- PiaProxy.exe (PID: 3772)
Checks supported languages
- PiaProxy_2.1.7_202409061452_Cus.exe (PID: 3852)
- install.exe (PID: 6180)
- PiaProxy.exe (PID: 3772)
- update.exe (PID: 2364)
Reads the computer name
- PiaProxy_2.1.7_202409061452_Cus.exe (PID: 3852)
- install.exe (PID: 6180)
- PiaProxy.exe (PID: 3772)
- update.exe (PID: 2364)
The process uses the downloaded file
- PiaProxy_2.1.7_202409061452_Cus.exe (PID: 3852)
Sends debugging messages
- install.exe (PID: 6180)
- PiaProxy.exe (PID: 3772)
- update.exe (PID: 2364)
Process checks computer location settings
- PiaProxy_2.1.7_202409061452_Cus.exe (PID: 3852)
Creates files or folders in the user directory
- install.exe (PID: 6180)
- PiaProxy.exe (PID: 3772)
- update.exe (PID: 2364)
Creates files in the program directory
- install.exe (PID: 6180)
- PiaProxy.exe (PID: 3772)
- update.exe (PID: 2364)
Reads the machine GUID from the registry
- install.exe (PID: 6180)
- PiaProxy.exe (PID: 3772)
- update.exe (PID: 2364)
Checks proxy server information
- PiaProxy.exe (PID: 3772)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (76.4) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (12.4) |
| .exe | | | Generic Win/DOS Executable (5.5) |
| .exe | | | DOS Executable Generic (5.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2017:08:11 13:54:06+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 188928 |
| InitializedDataSize: | 181248 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1cec9 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
132
Monitored processes
5
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2364 | "C:\Program Files (x86)\PiaProxy_cata\update.exe" "C:/Program Files (x86)/PiaProxy_cata/update.exe" --check_enable --lang _en | C:\Program Files (x86)\PiaProxy_cata\update.exe | PiaProxy.exe | ||||||||||||
User: admin Company: MARS BROTHERS LIMITED Integrity Level: HIGH Description: PiaProxy Exit code: 0 Version: 0.1.0.0 Modules
| |||||||||||||||
| 3772 | "C:\Program Files (x86)\PiaProxy_cata\PiaProxy.exe" | C:\Program Files (x86)\PiaProxy_cata\PiaProxy.exe | install.exe | ||||||||||||
User: admin Company: MARS BROTHERS LIMITED Integrity Level: HIGH Description: PiaProxy Version: 0.1.0.0 Modules
| |||||||||||||||
| 3852 | "C:\Users\admin\Desktop\PiaProxy_2.1.7_202409061452_Cus.exe" | C:\Users\admin\Desktop\PiaProxy_2.1.7_202409061452_Cus.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 6180 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\PiaProxy_release\install.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\PiaProxy_release\install.exe | PiaProxy_2.1.7_202409061452_Cus.exe | ||||||||||||
User: admin Company: MARS BROTHERS LIMITED Integrity Level: HIGH Description: PiaProxy Exit code: 0 Version: 0.1.0.0 Modules
| |||||||||||||||
| 7136 | "C:\Users\admin\AppData\Local\Temp\RarSFX0\PiaProxy_release\install.exe" | C:\Users\admin\AppData\Local\Temp\RarSFX0\PiaProxy_release\install.exe | — | PiaProxy_2.1.7_202409061452_Cus.exe | |||||||||||
User: admin Company: MARS BROTHERS LIMITED Integrity Level: MEDIUM Description: PiaProxy Exit code: 3221226540 Version: 0.1.0.0 Modules
| |||||||||||||||
Total events
4 076
Read events
4 065
Write events
11
Delete events
0
Modification events
| (PID) Process: | (6180) install.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | PiaProxy |
Value: C:/Program Files (x86)/PiaProxy_cata/PiaProxy.exe | |||
| (PID) Process: | (6180) install.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\PiaProxy |
| Operation: | write | Name: | InstallPath |
Value: C:\Program Files (x86) | |||
| (PID) Process: | (6180) install.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\PiaProxy |
| Operation: | write | Name: | DisplayCata |
Value: C:\Program Files (x86)\PiaProxy_cata | |||
| (PID) Process: | (6180) install.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\PiaProxy |
| Operation: | write | Name: | DisplayName |
Value: Pia S5 Proxy | |||
| (PID) Process: | (6180) install.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\PiaProxy |
| Operation: | write | Name: | DisplayVersion |
Value: 2.1.7 | |||
| (PID) Process: | (6180) install.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\PiaProxy |
| Operation: | write | Name: | Publisher |
Value: MARS BROTHERS | |||
| (PID) Process: | (6180) install.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\PiaProxy |
| Operation: | write | Name: | UninstallString |
Value: C:\Program Files (x86)\PiaProxy_cata\uninstall.exe | |||
| (PID) Process: | (6180) install.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\PiaProxy |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files (x86)\PiaProxy_cata\uninstall.exe | |||
| (PID) Process: | (6180) install.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\PiaProxy |
| Operation: | write | Name: | EstimatedSize |
Value: 1360 | |||
| (PID) Process: | (6180) install.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\PiaProxy |
| Operation: | write | Name: | InstallTime |
Value: FCBF136700000000 | |||
Executable files
132
Suspicious files
586
Text files
842
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3852 | PiaProxy_2.1.7_202409061452_Cus.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\PiaProxy_release\QtQuick\Controls\Private\StackView.js | text | |
MD5:50B211F802E57ACA8AC9228EFC05D00F | SHA256:48180D35E367EFF46892D99E5BB05210F0930F87F1AB2EE12C9F642288E03836 | |||
| 3852 | PiaProxy_2.1.7_202409061452_Cus.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\PiaProxy_release\install.exe | executable | |
MD5:A39359F1380EE171086A9FF85A7EB6F9 | SHA256:07248D5910927055118419A5D7AAFBC0FE2E6FC1CA7A737C0CF08177BC0A8E50 | |||
| 3852 | PiaProxy_2.1.7_202409061452_Cus.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\PiaProxy_release\QtQuick\Controls\Private\style.js | text | |
MD5:42B5203954B0E4D9EFC477B558D3C8FD | SHA256:E337C73325AE18763172A328B819B036E6F42C412A77454731B14AC5F05A1E3D | |||
| 3852 | PiaProxy_2.1.7_202409061452_Cus.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\PiaProxy_release\socks5\PiaS5ProxyDivert.exe | executable | |
MD5:8F5BC5C89B412B4F4ED5E5B7951447AC | SHA256:F88FCC8D74F0043EC0E2F1098447EDD2D94970D05897ABD4D8901781713CECCC | |||
| 3852 | PiaProxy_2.1.7_202409061452_Cus.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\PiaProxy_release\file_flag.ini | binary | |
MD5:0CB12EDFF5B77DFAC686C0D0B8E669F7 | SHA256:71E01CEFFA00BFF46FC4FCE7D3A940E86362E37F7F5AB69C9647044BEF1FDA03 | |||
| 3852 | PiaProxy_2.1.7_202409061452_Cus.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\PiaProxy_release\QtQuick\Controls\Private\CalendarUtils.js | text | |
MD5:8EF9D96911E8B0AE9E2562662A516405 | SHA256:71E7B220AF9B62B2EBCAEE5B93D435C5A33BC6848CF29F785BCE082858C100AB | |||
| 3852 | PiaProxy_2.1.7_202409061452_Cus.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\PiaProxy_release\PiaProxy.exe | executable | |
MD5:B284BED9B32C0231B32CAB110B739EB0 | SHA256:05A0D5C087FF4FC966ED13DEB294592BFF19B6D2E9FF4AEDAD4D06AA63F9FC22 | |||
| 3852 | PiaProxy_2.1.7_202409061452_Cus.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\PiaProxy_release\socks5\hxxd.dll | executable | |
MD5:8BAA5B17B3AEF7252625861EDF60D17F | SHA256:D970BBB5727975525206B6DEE88904E33A0AE85DEDFC7CD3DC200CD899B86366 | |||
| 3852 | PiaProxy_2.1.7_202409061452_Cus.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\PiaProxy_release\libeay32.dll | executable | |
MD5:9C8B228D392411AEEC50905C2D80CF5D | SHA256:2C125702A00050B7175BEFB29E58749C8B63E33D51E6093AC04175C303084A83 | |||
| 3852 | PiaProxy_2.1.7_202409061452_Cus.exe | C:\Users\admin\AppData\Local\Temp\RarSFX0\PiaProxy_release\libgcc_s_dw2-1.dll | executable | |
MD5:043B39434829CE93637B1801D57B2082 | SHA256:4D2E2D408D399D066B0AAEF2047F7A33515C13C589832DE0D9F1BA87A530C394 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
47
TCP/UDP connections
69
DNS requests
15
Threats
13
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | — | 172.67.74.242:443 | https://download.piaproxy.com/file/img/7thlogcn.png | unknown | — | — | unknown |
— | — | POST | — | 104.26.14.22:443 | https://standbyruapi.piaproxy.com/api/socks/config | unknown | — | — | unknown |
— | — | GET | — | 104.26.15.22:443 | https://download.piaproxy.com/file/img/PIAs5-banner263-90px-en.jpg | unknown | — | — | unknown |
6944 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | — | 172.67.74.242:443 | https://download.piaproxy.com/file/img/7thlogen.png | unknown | — | — | unknown |
— | — | GET | — | 104.26.15.22:443 | https://download.piaproxy.com/file/img/PIAs5-banner263-90px-en.jpg | unknown | — | — | unknown |
— | — | GET | — | 104.26.14.22:443 | https://download.piaproxy.com/file/img/7thQten.png | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6944 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 104.126.37.160:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5488 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6944 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ipchanger-fjny.oss-cn-hongkong.aliyuncs.com |
| unknown |
standbyruapi.piaproxy.com |
| unknown |
download.piaproxy.com |
| unknown |
standbyapi.piaproxy.com |
| unknown |
self.events.data.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2172 | svchost.exe | Misc activity | ET INFO DNS Query to Alibaba Cloud CDN Domain (aliyuncs .com) |
6180 | install.exe | Misc activity | ET INFO Observed Alibaba Cloud CDN Domain (aliyuncs .com in TLS SNI) |
3772 | PiaProxy.exe | Misc activity | ET INFO Observed Alibaba Cloud CDN Domain (aliyuncs .com in TLS SNI) |
2364 | update.exe | Misc activity | ET INFO Observed Alibaba Cloud CDN Domain (aliyuncs .com in TLS SNI) |
9 ETPRO signatures available at the full report
Process | Message |
|---|---|
install.exe | CApp Exe Begin...
|
install.exe | QT_VERSION 329984
|
install.exe | AA_EnableHighDpiScaling
|
install.exe | AppRun...
|
PiaProxy.exe | CApp Exe Begin...
|
PiaProxy.exe | QT_VERSION 329984
|
PiaProxy.exe | AA_EnableHighDpiScaling
|
PiaProxy.exe | AppRun...
|
update.exe | CAppCustom Exe Begin...
|
update.exe | appExist.isRunning() true
|