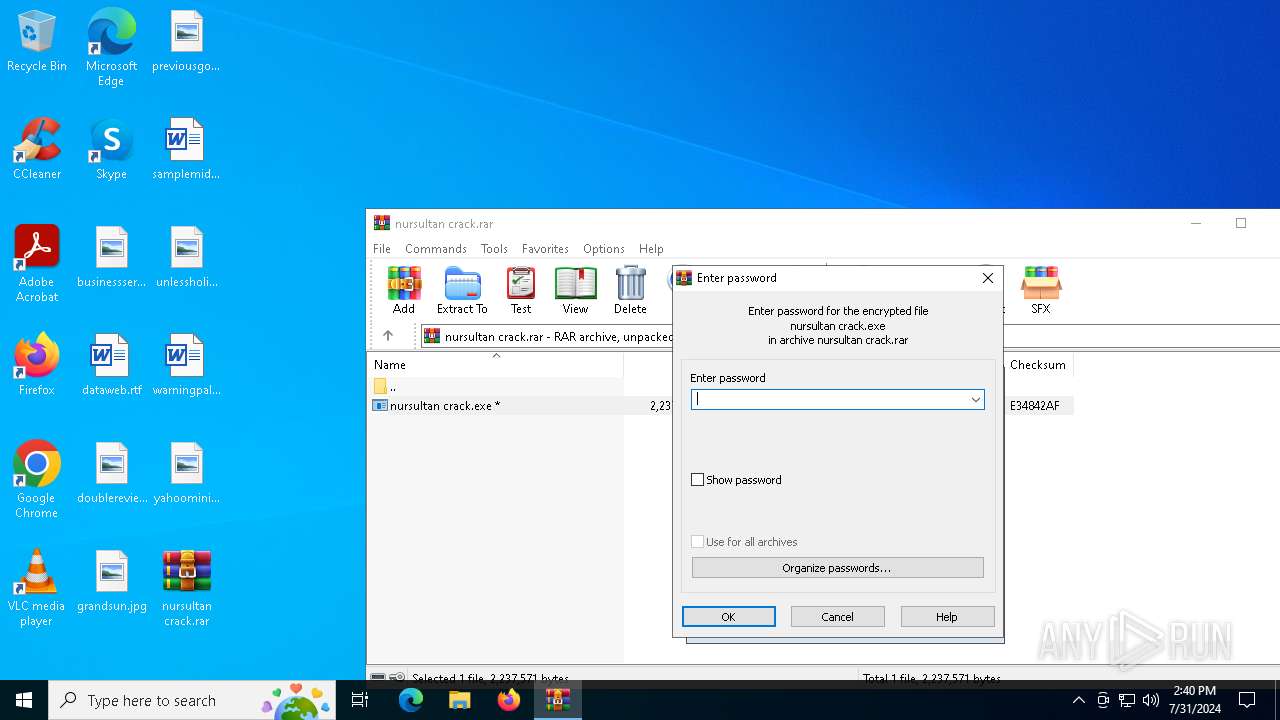
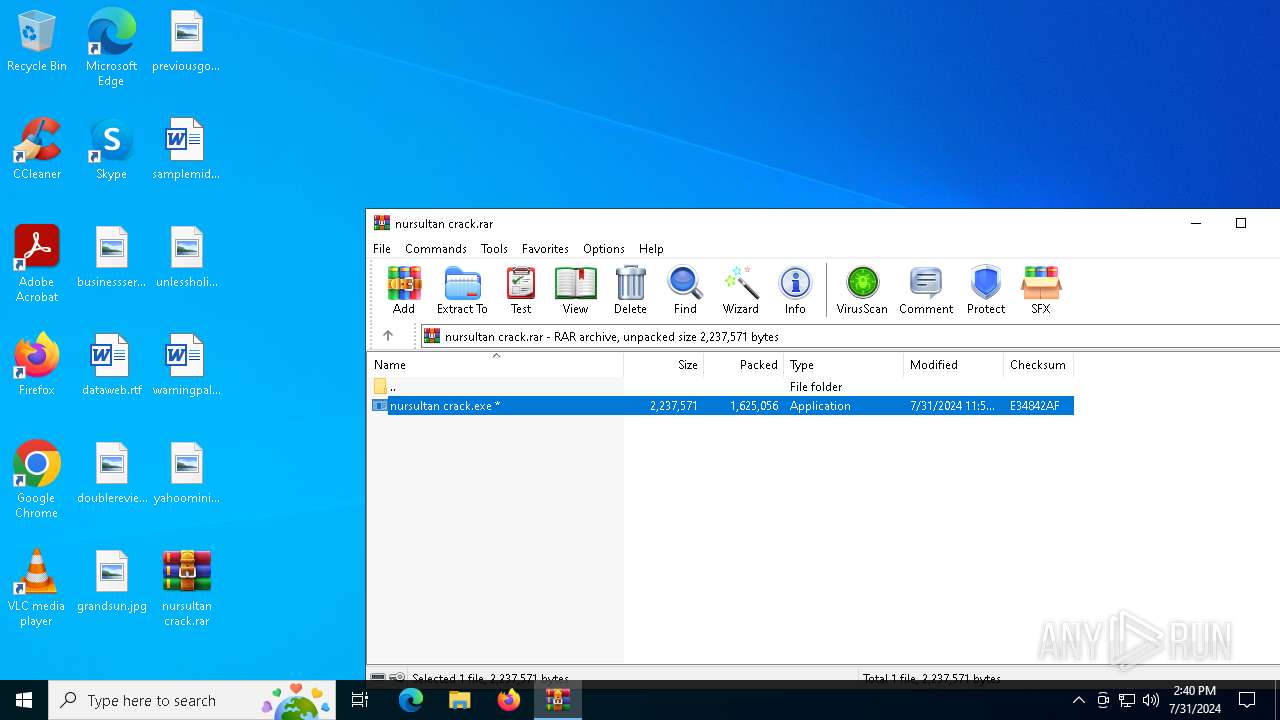
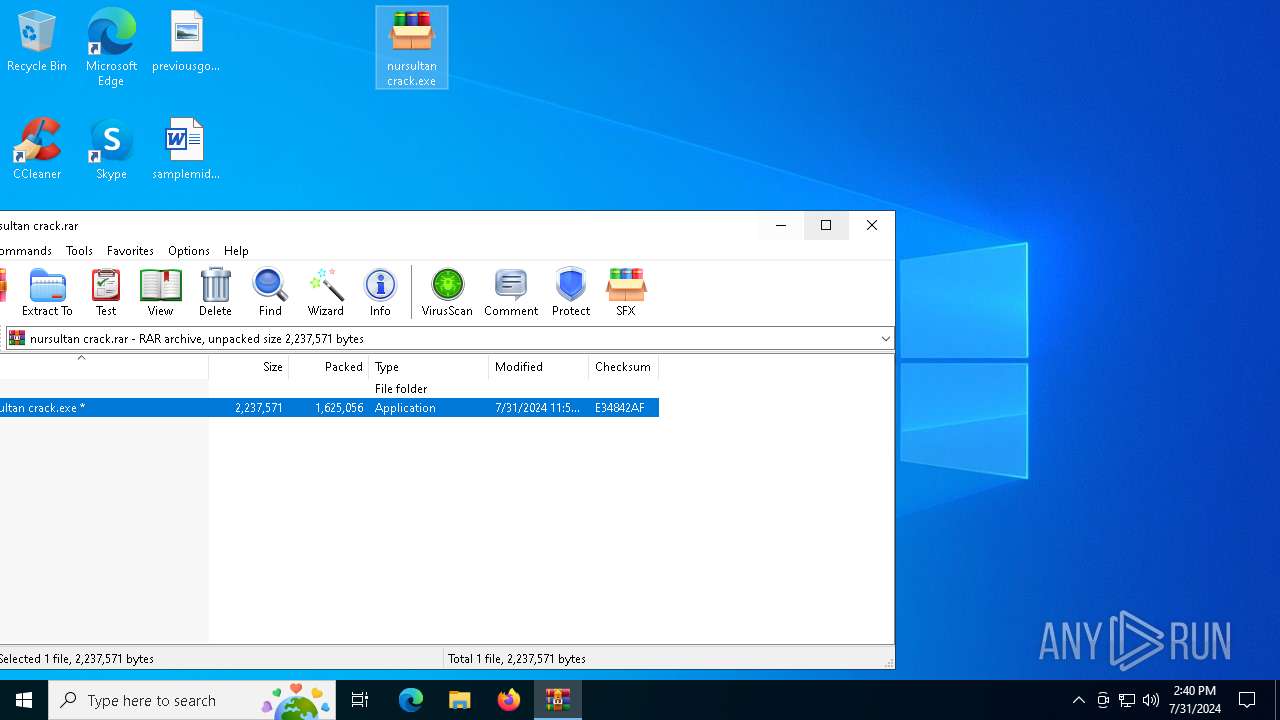
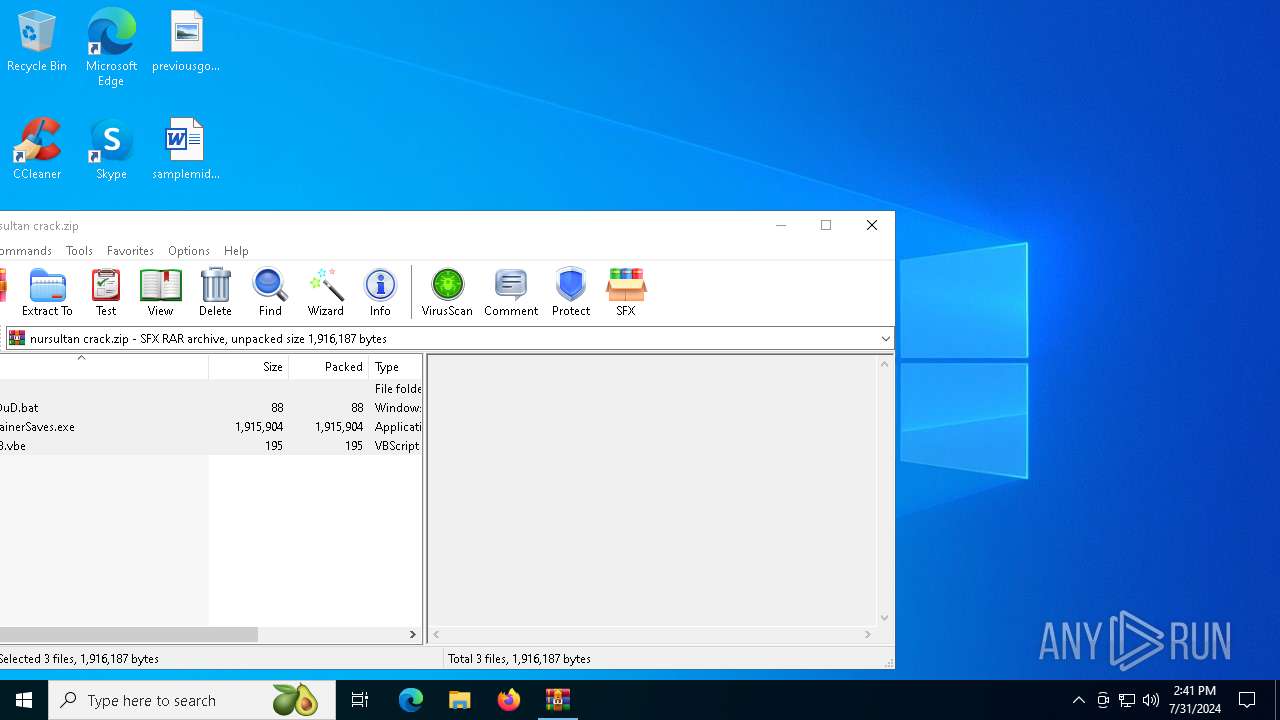
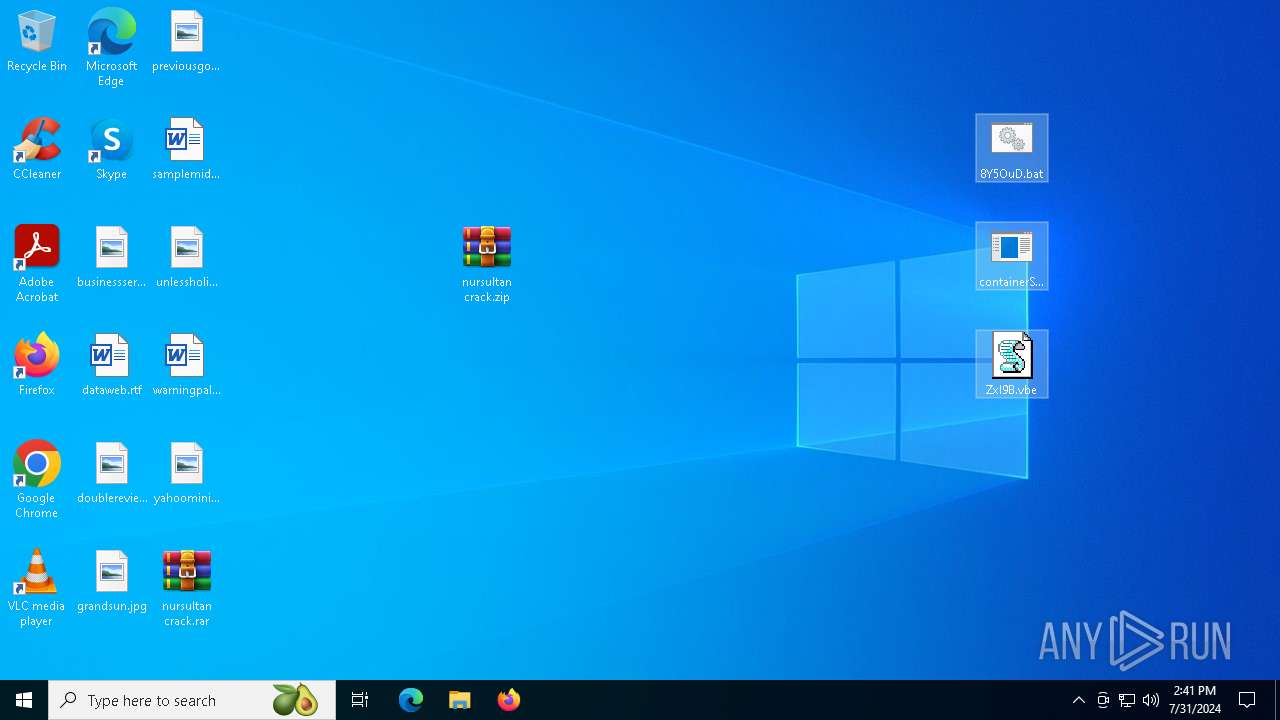
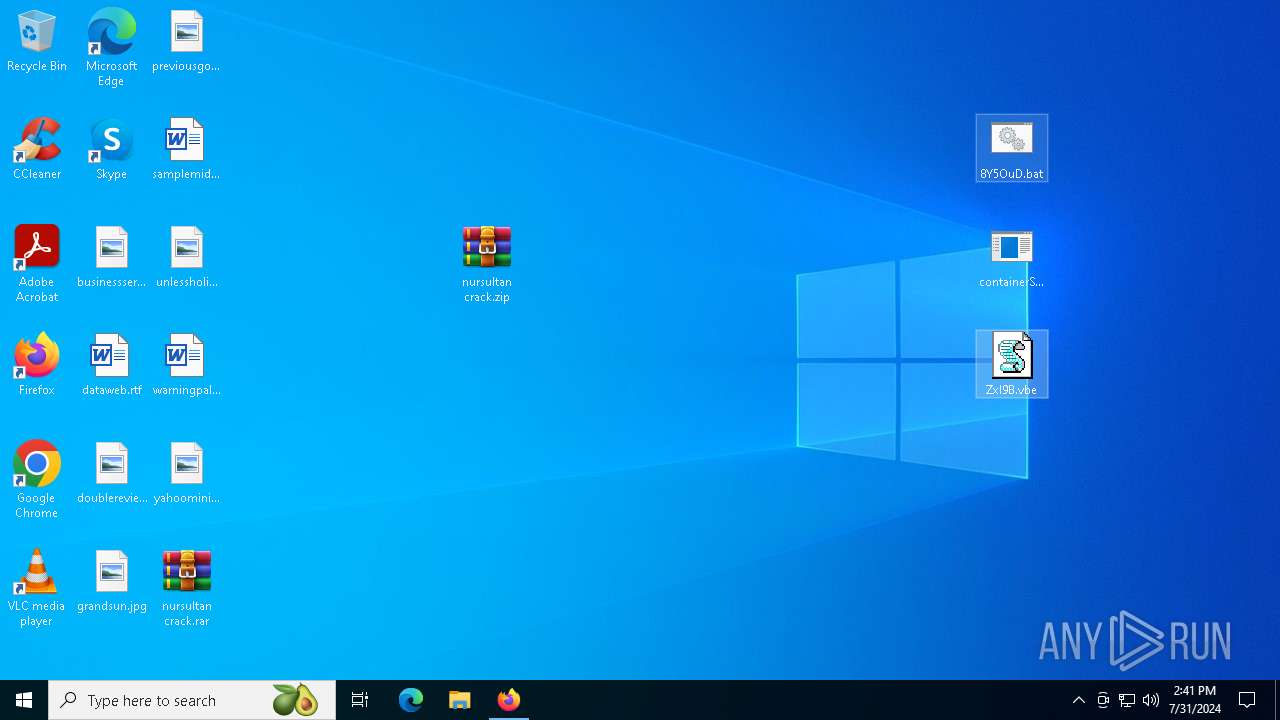
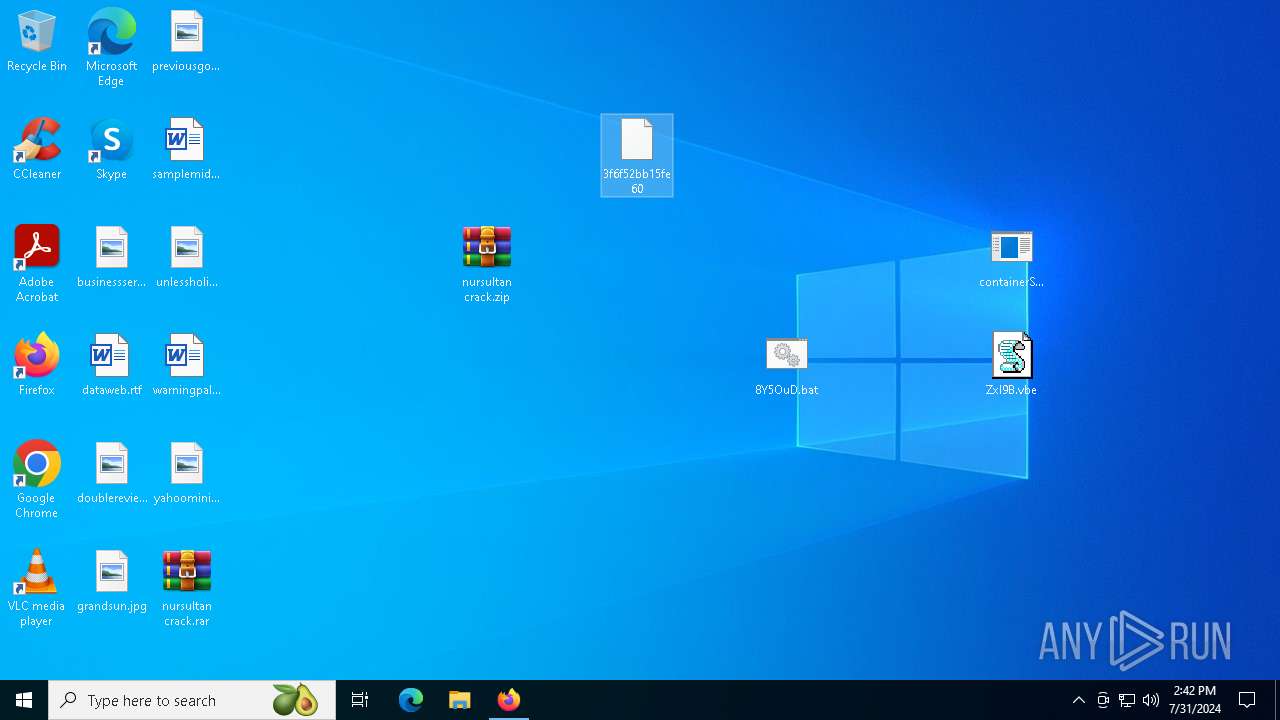
| File name: | nursultan crack.rar |
| Full analysis: | https://app.any.run/tasks/f734be86-0a1e-4080-a24b-5a07b0dcc103 |
| Verdict: | Malicious activity |
| Threats: | DCrat, also known as Dark Crystal RAT, is a remote access trojan (RAT), which was first introduced in 2018. It is a modular malware that can be customized to perform different tasks. For instance, it can steal passwords, crypto wallet information, hijack Telegram and Steam accounts, and more. Attackers may use a variety of methods to distribute DCrat, but phishing email campaigns are the most common. |
| Analysis date: | July 31, 2024, 14:40:24 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
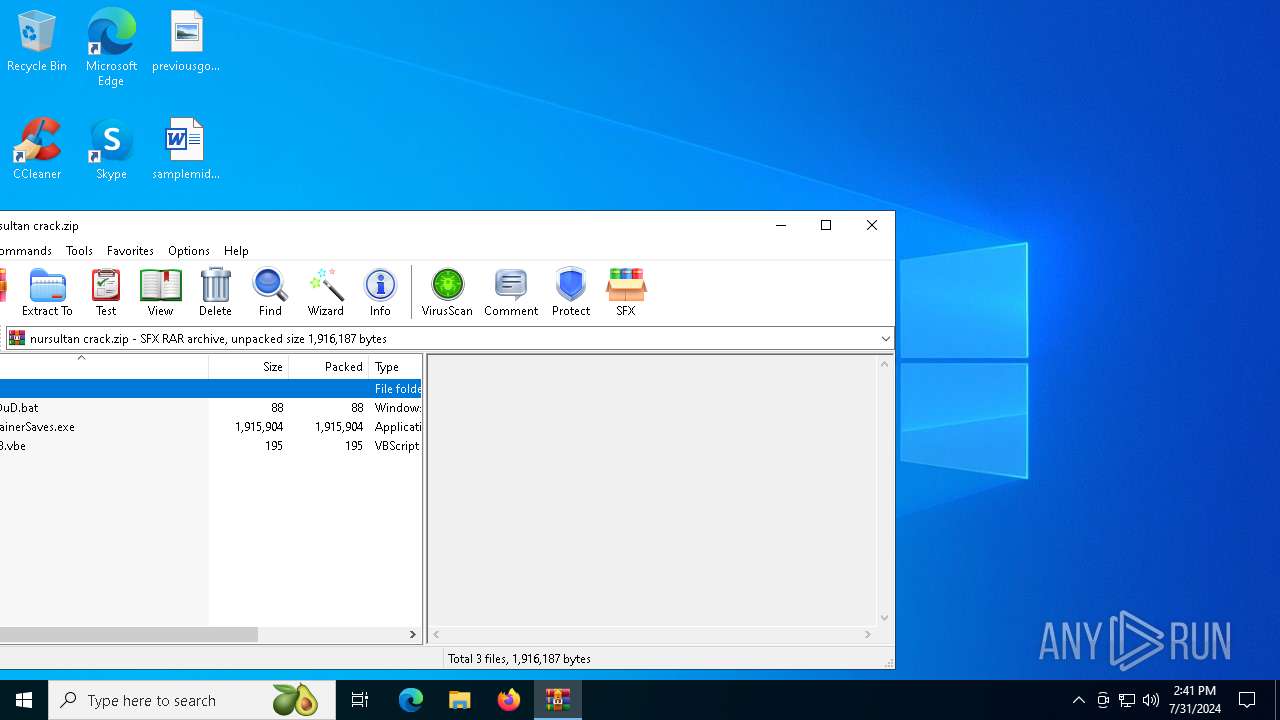
| File info: | RAR archive data, v5 |
| MD5: | B507764410C31CB6AF04D9BCA917BF8E |
| SHA1: | 65D44BF39FF33DBD9B0D79F7930C9E2F48364D3A |
| SHA256: | 9D9307576255F715555D9E9940F71C94C5676CF24FCE100C77854F0E92192E87 |
| SSDEEP: | 49152:N0nE9GOa1tLg2TINVVhuNHWpRVlC1JBt3smFtVH7/zg5j6xJWAKccrGFqEa1gGoD:+E3kLg2TTNurlkJ3hFX2+TW1cc68GGoD |
MALICIOUS
DCRAT has been detected (YARA)
- firefox.exe (PID: 3116)
SUSPICIOUS
Executable content was dropped or overwritten
- containerSaves.exe (PID: 904)
- csc.exe (PID: 6236)
Executed via WMI
- schtasks.exe (PID: 7952)
- schtasks.exe (PID: 8052)
- schtasks.exe (PID: 6608)
- schtasks.exe (PID: 7080)
- schtasks.exe (PID: 2396)
- schtasks.exe (PID: 4208)
- schtasks.exe (PID: 7060)
- schtasks.exe (PID: 3660)
- schtasks.exe (PID: 6804)
- schtasks.exe (PID: 6944)
- schtasks.exe (PID: 8168)
- schtasks.exe (PID: 6788)
- schtasks.exe (PID: 3116)
- schtasks.exe (PID: 4936)
- schtasks.exe (PID: 7256)
- schtasks.exe (PID: 7184)
- schtasks.exe (PID: 7288)
- schtasks.exe (PID: 7396)
Executing commands from a ".bat" file
- containerSaves.exe (PID: 904)
Starts application with an unusual extension
- cmd.exe (PID: 7360)
Starts CMD.EXE for commands execution
- containerSaves.exe (PID: 904)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 7360)
The executable file from the user directory is run by the CMD process
- firefox.exe (PID: 3116)
INFO
Manual execution by a user
- WinRAR.exe (PID: 6520)
- firefox.exe (PID: 4016)
- notepad.exe (PID: 6920)
- containerSaves.exe (PID: 7816)
- cmd.exe (PID: 2092)
- cmd.exe (PID: 1248)
- cmd.exe (PID: 6832)
- wscript.exe (PID: 1116)
- containerSaves.exe (PID: 8012)
- containerSaves.exe (PID: 4128)
- containerSaves.exe (PID: 7832)
- containerSaves.exe (PID: 6684)
- containerSaves.exe (PID: 7756)
- cmd.exe (PID: 7272)
- containerSaves.exe (PID: 904)
- containerSaves.exe (PID: 3648)
- containerSaves.exe (PID: 7212)
- containerSaves.exe (PID: 8044)
- containerSaves.exe (PID: 7796)
- containerSaves.exe (PID: 6836)
- containerSaves.exe (PID: 6824)
- containerSaves.exe (PID: 3568)
- containerSaves.exe (PID: 7636)
- containerSaves.exe (PID: 6692)
- notepad++.exe (PID: 4208)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6276)
- WinRAR.exe (PID: 6520)
Application launched itself
- firefox.exe (PID: 4016)
- firefox.exe (PID: 3140)
.NET Reactor protector has been detected
- firefox.exe (PID: 3116)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
199
Monitored processes
68
Malicious processes
3
Suspicious processes
0
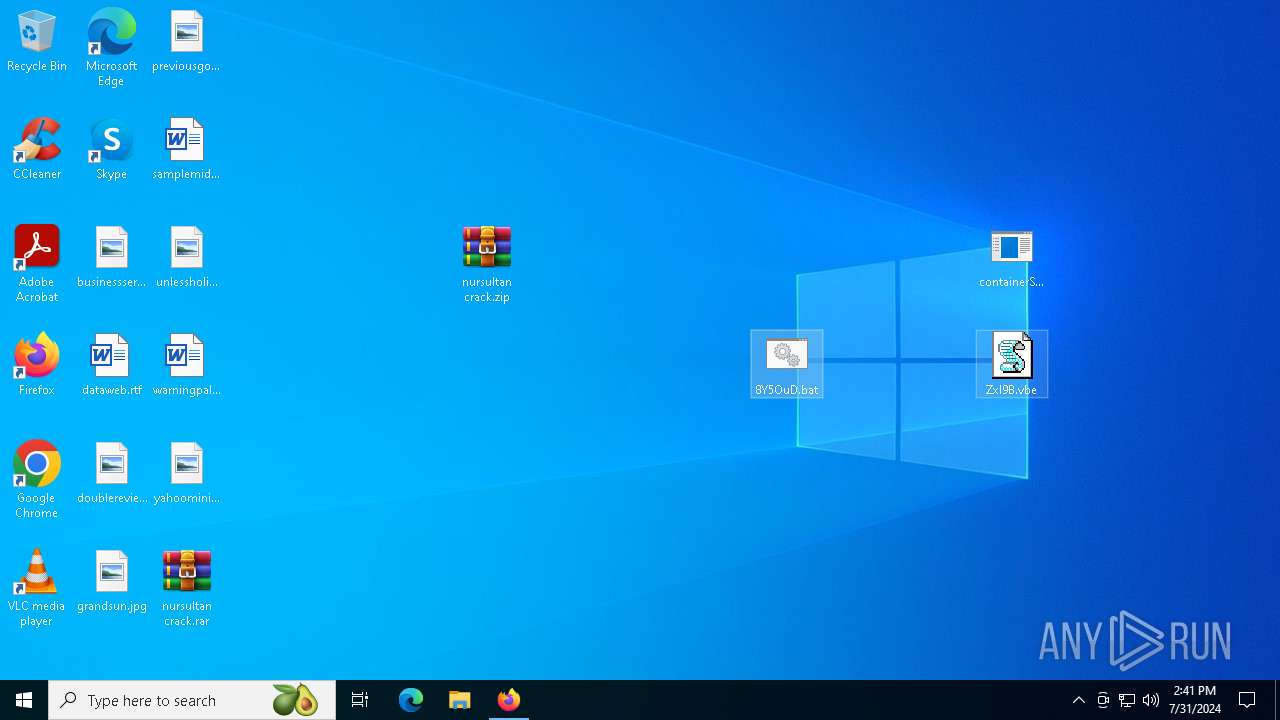
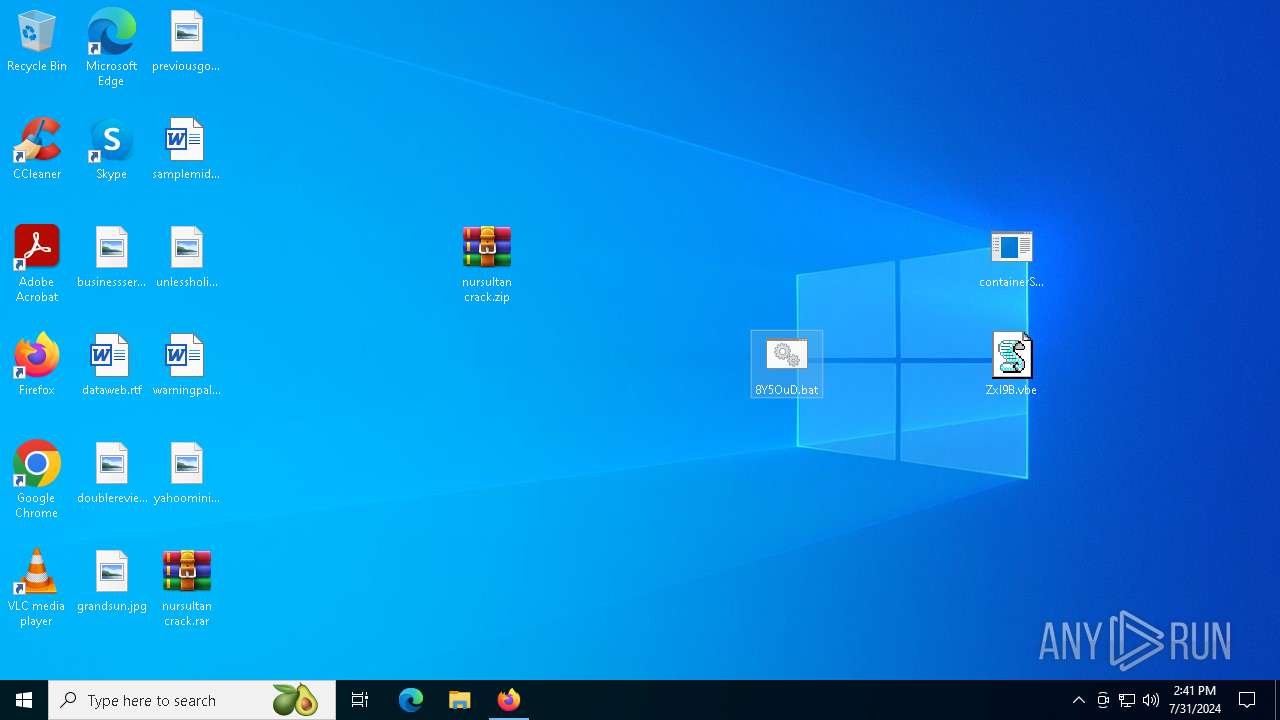
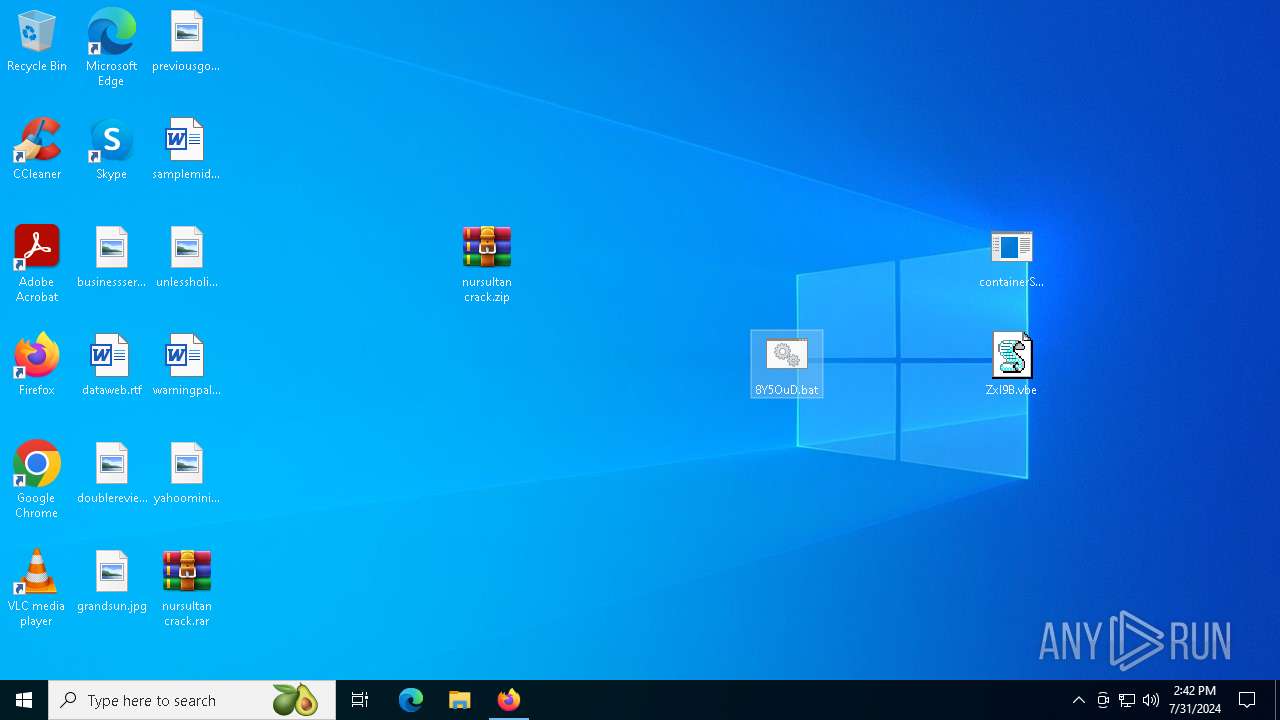
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process |
|---|---|---|---|---|
| 904 | "C:\Users\admin\Desktop\containerSaves.exe" | C:\Users\admin\Desktop\containerSaves.exe | explorer.exe | |
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 1.2.7.1277 | ||||
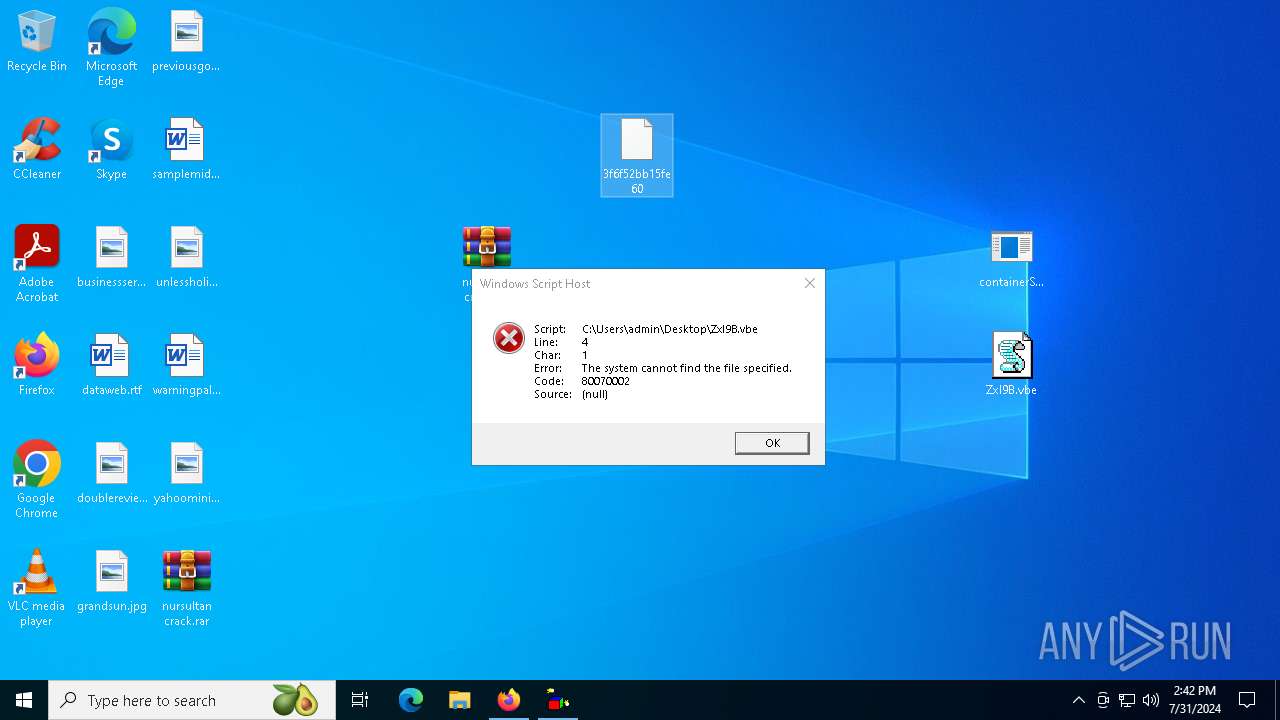
| 1116 | "C:\WINDOWS\System32\WScript.exe" "C:\Users\admin\Desktop\ZxI9B.vbe" | C:\Windows\System32\wscript.exe | — | explorer.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 | ||||
| 1248 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\8Y5OuD.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 1928 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel=2272 -parentBuildID 20240213221259 -prefsHandle 2264 -prefMapHandle 2260 -prefsLen 30537 -prefMapSize 244343 -win32kLockedDown -appDir "C:\Program Files\Mozilla Firefox\browser" - {b3d594aa-61c9-4adf-9f29-16d2de02df9e} 3140 "\\.\pipe\gecko-crash-server-pipe.3140" 2254e97f910 socket | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe |
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Version: 123.0 | ||||
| 2092 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\8Y5OuD.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 2212 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | csc.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 2396 | schtasks.exe /create /tn "WaaSMedicAgentW" /sc MINUTE /mo 9 /tr "'C:\Users\admin\Recent\WaaSMedicAgent.exe'" /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 2700 | ping -n 10 localhost | C:\Windows\System32\PING.EXE | — | cmd.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
| 2928 | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe /NOLOGO /READONLY /MACHINE:IX86 "/OUT:C:\Users\admin\AppData\Local\Temp\RESAB1B.tmp" "c:\Users\admin\AppData\Local\Microsoft\OneDrive\CSC3C40410894EA4474B4A5A0346DAFCA8C.TMP" | C:\Windows\Microsoft.NET\Framework64\v4.0.30319\cvtres.exe | — | csc.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft® Resource File To COFF Object Conversion Utility Exit code: 0 Version: 14.32.31326.0 | ||||
| 3116 | schtasks.exe /create /tn "System" /sc ONLOGON /tr "'C:\Windows\Tasks\System.exe'" /rl HIGHEST /f | C:\Windows\System32\schtasks.exe | — | WmiPrvSE.exe |
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Task Scheduler Configuration Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) | ||||
Total events
6 909
Read events
6 866
Write events
43
Delete events
0
Modification events
| (PID) Process: | (6276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (6276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\nursultan crack.rar | |||
| (PID) Process: | (6276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (6276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (6276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFC7FFFFFFD200000087030000A5020000 | |||
Executable files
13
Suspicious files
138
Text files
46
Unknown types
20
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 6520 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6520.17280\8Y5OuD.bat | text | |
MD5:1A18CF51A1D89659E6E5397A5CF44FA8 | SHA256:— | |||
| 3140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 3140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs-1.js | text | |
MD5:E28BB9F50EAAA7DA3BFB24A1F3AE368D | SHA256:— | |||
| 6520 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6520.17280\containerSaves.exe | executable | |
MD5:ACEF1B925624EBCC2E9FC1B0D5E71048 | SHA256:— | |||
| 3140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 6276 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb6276.15389\nursultan crack.exe | executable | |
MD5:91B6E2CC213F22984B9DFF6BB715887E | SHA256:— | |||
| 6520 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa6520.17280\ZxI9B.vbe | vbe | |
MD5:11DE6B9311D4360454360C72BFA5B20A | SHA256:— | |||
| 3140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 3140 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2823318777ntouromlalnodry--naod.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
118
DNS requests
147
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | POST | 200 | 195.138.255.18:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
— | — | POST | 200 | 142.250.185.163:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
— | — | POST | 200 | 142.250.185.163:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
— | — | POST | 200 | 195.138.255.18:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
— | — | POST | 200 | 195.138.255.24:80 | http://r11.o.lencr.org/ | unknown | — | — | unknown |
— | — | POST | 200 | 142.250.185.163:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5796 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
3140 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2120 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | unknown |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | unknown |
5796 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
5336 | SearchApp.exe | 2.23.209.182:443 | www.bing.com | Akamai International B.V. | GB | unknown |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | unknown |
— | — | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| unknown |
google.com |
| unknown |
www.bing.com |
| unknown |
ocsp.digicert.com |
| unknown |
login.live.com |
| unknown |
th.bing.com |
| unknown |
client.wns.windows.com |
| unknown |
fd.api.iris.microsoft.com |
| unknown |
arc.msn.com |
| unknown |
slscr.update.microsoft.com |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Cloudflare content delivery network (cdnjs .cloudflare .com) |