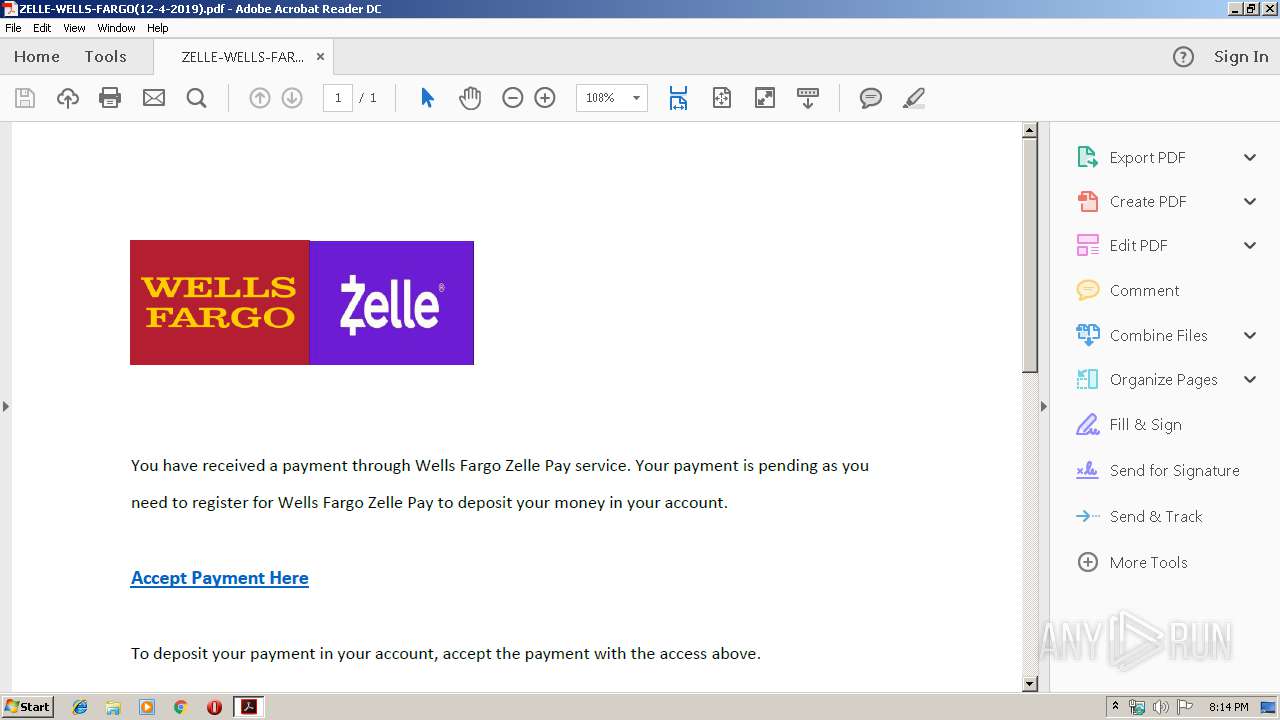
| File name: | ZELLE-WELLS-FARGO(12-4-2019).pdf |
| Full analysis: | https://app.any.run/tasks/ca3c1e62-c94c-4416-8e9e-c04c1a32dc1d |
| Verdict: | Malicious activity |
| Analysis date: | December 06, 2019, 20:14:10 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/pdf |
| File info: | PDF document, version 1.7 |
| MD5: | 318DA83F290772F1E968D5FCD30B02B1 |
| SHA1: | B9CFA97A9ED25411B888C3A5E78C6E904E8C3B34 |
| SHA256: | 9D7552C55CE8A90C25A769AA3E8344B39A3561819CCD9C6B5CE1ABF08B41AA3B |
| SSDEEP: | 1536:JCp7Xu7QQPLgexpQzcbsXxkRElaP0FfyIQd9j9YBqrlGNUjj:opwcexizusXxEElo0nQd9j9YgMNUn |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts Internet Explorer
- AcroRd32.exe (PID: 2200)
Modifies files in Chrome extension folder
- chrome.exe (PID: 2056)
Creates files in the program directory
- AdobeARM.exe (PID: 1520)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 2928)
Application launched itself
- AcroRd32.exe (PID: 2200)
- RdrCEF.exe (PID: 856)
- iexplore.exe (PID: 564)
- chrome.exe (PID: 3348)
- chrome.exe (PID: 2056)
Reads the hosts file
- RdrCEF.exe (PID: 856)
- chrome.exe (PID: 2208)
- chrome.exe (PID: 2056)
- chrome.exe (PID: 3348)
- chrome.exe (PID: 3336)
Creates files in the user directory
- iexplore.exe (PID: 2928)
- iexplore.exe (PID: 564)
Changes internet zones settings
- iexplore.exe (PID: 564)
Manual execution by user
- chrome.exe (PID: 3348)
- chrome.exe (PID: 2056)
Reads internet explorer settings
- iexplore.exe (PID: 2928)
Reads settings of System Certificates
- chrome.exe (PID: 2208)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| | | Adobe Portable Document Format (100) |
EXIF
| PDFVersion: | 1.7 |
|---|---|
| Linearized: | No |
| PageCount: | 1 |
| Language: | en-US |
| TaggedPDF: | Yes |
| Author: | Rohan Poddar |
| Creator: | Microsoft Word |
| CreateDate: | 2019:12:04 04:54:49-08:00 |
| ModifyDate: | 2019:12:04 04:54:49-08:00 |
XMP
| XMPToolkit: | 3.1-701 |
|---|---|
| Creator: | Rohan Poddar |
| CreatorTool: | Microsoft Word |
| CreateDate: | 2019:12:04 04:54:49-08:00 |
| ModifyDate: | 2019:12:04 04:54:49-08:00 |
| DocumentID: | uuid:70B5A763-D451-4BD7-97C9-73994F627066 |
| InstanceID: | uuid:70B5A763-D451-4BD7-97C9-73994F627066 |
Total processes
94
Monitored processes
59
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 496 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1000,3432460692962190385,4772360428161906782,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=7260784446553706434 --mojo-platform-channel-handle=984 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 564 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 856 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16448250 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe RdrCEF Exit code: 0 Version: 15.23.20053.211670 Modules
| |||||||||||||||
| 1016 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1000,3432460692962190385,4772360428161906782,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=10052008411807607961 --mojo-platform-channel-handle=2668 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1028 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=992,7554595763079660211,4342126350308277870,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=7609559275339821659 --mojo-platform-channel-handle=1008 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1048 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1000,3432460692962190385,4772360428161906782,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=13562000493559651886 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2440 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1096 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer "C:\Users\admin\Downloads\ZELLE-WELLS-FARGO(12-4-2019).pdf" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 0 Version: 15.23.20070.215641 Modules
| |||||||||||||||
| 1328 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=3432 --on-initialized-event-handle=312 --parent-handle=316 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1404 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=992,7554595763079660211,4342126350308277870,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=2798466207617080158 --mojo-platform-channel-handle=3312 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1520 | "C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" /PRODUCT:Reader /VERSION:15.0 /MODE:3 | C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Reader and Acrobat Manager Exit code: 0 Version: 1.824.27.2646 Modules
| |||||||||||||||
Total events
1 708
Read events
1 455
Write events
244
Delete events
9
Modification events
| (PID) Process: | (1096) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\ExitSection |
| Operation: | write | Name: | bLastExitNormal |
Value: 0 | |||
| (PID) Process: | (1096) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral |
| Operation: | write | Name: | bExpandRHPInViewer |
Value: 1 | |||
| (PID) Process: | (1096) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\NoTimeOut |
| Operation: | write | Name: | smailto |
Value: 5900 | |||
| (PID) Process: | (2200) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral\cRecentFiles\c1 |
| Operation: | write | Name: | aFS |
Value: DOS | |||
| (PID) Process: | (2200) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral\cRecentFiles\c1 |
| Operation: | write | Name: | tDIText |
Value: /C/Users/admin/Downloads/ZELLE-WELLS-FARGO(12-4-2019).pdf | |||
| (PID) Process: | (2200) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral\cRecentFiles\c1 |
| Operation: | write | Name: | tFileName |
Value: ZELLE-WELLS-FARGO(12-4-2019).pdf | |||
| (PID) Process: | (2200) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral\cRecentFiles\c1 |
| Operation: | write | Name: | tFileSource |
Value: local | |||
| (PID) Process: | (2200) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral\cRecentFiles\c1 |
| Operation: | write | Name: | sFileAncestors |
Value: 5B5D00 | |||
| (PID) Process: | (2200) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral\cRecentFiles\c1 |
| Operation: | write | Name: | sDI |
Value: 2F432F55736572732F61646D696E2F446F776E6C6F6164732F5A454C4C452D57454C4C532D464152474F2831322D342D32303139292E70646600 | |||
| (PID) Process: | (2200) AcroRd32.exe | Key: | HKEY_CURRENT_USER\Software\Adobe\Acrobat Reader\DC\AVGeneral\cRecentFiles\c1 |
| Operation: | write | Name: | sDate |
Value: 443A32303139313230363230313433325A00 | |||
Executable files
0
Suspicious files
42
Text files
327
Unknown types
30
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1096 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages-journal | — | |
MD5:— | SHA256:— | |||
| 1096 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\Cache\AdobeFnt16.lst.1096 | — | |
MD5:— | SHA256:— | |||
| 1096 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeFnt16.lst.1096 | — | |
MD5:— | SHA256:— | |||
| 564 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 564 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 1096 | AcroRd32.exe | C:\Users\admin\AppData\LocalLow\Adobe\Acrobat\DC\ReaderMessages | sqlite | |
MD5:— | SHA256:— | |||
| 1096 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\UserCache.bin | binary | |
MD5:— | SHA256:— | |||
| 2200 | AcroRd32.exe | C:\Users\admin\AppData\Local\Adobe\Acrobat\DC\AdobeSysFnt15.lst | ps | |
MD5:— | SHA256:— | |||
| 1096 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9R1hht465_s1f4lx_ug.tmp | — | |
MD5:— | SHA256:— | |||
| 1096 | AcroRd32.exe | C:\Users\admin\AppData\Local\Temp\acrord32_sbx\A9Rhv22rr_s1f4ly_ug.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
45
DNS requests
32
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
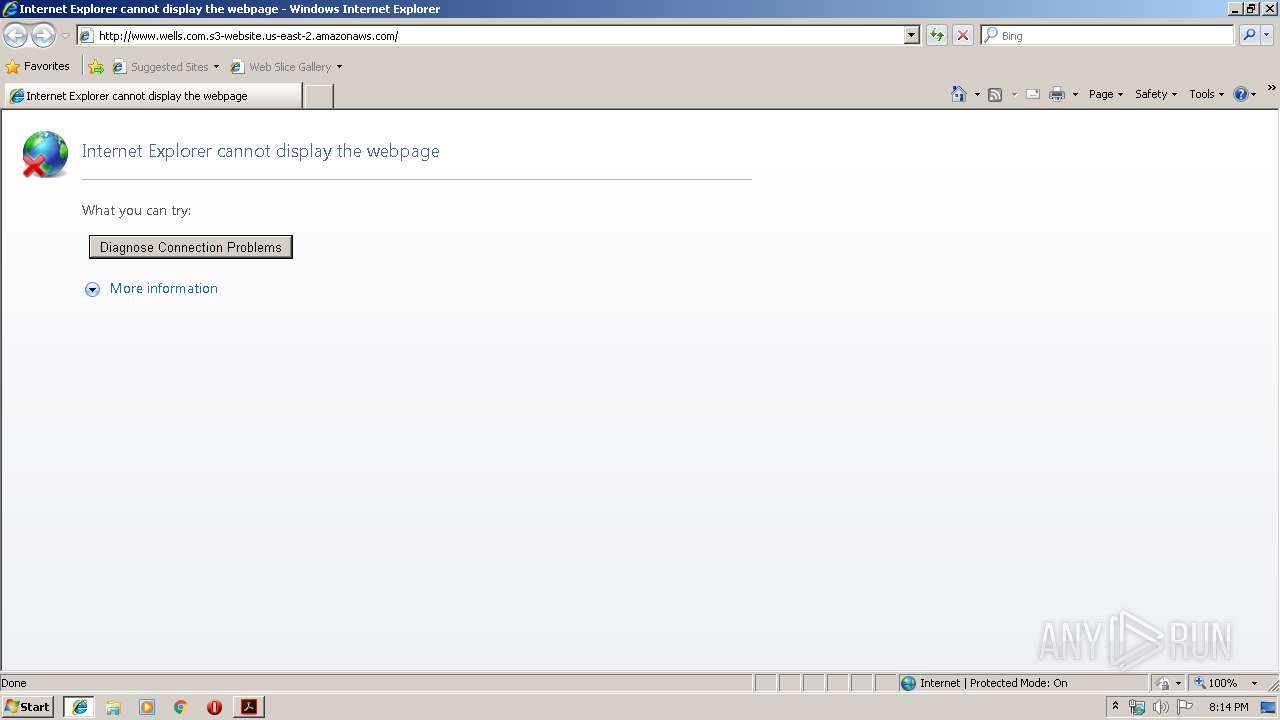
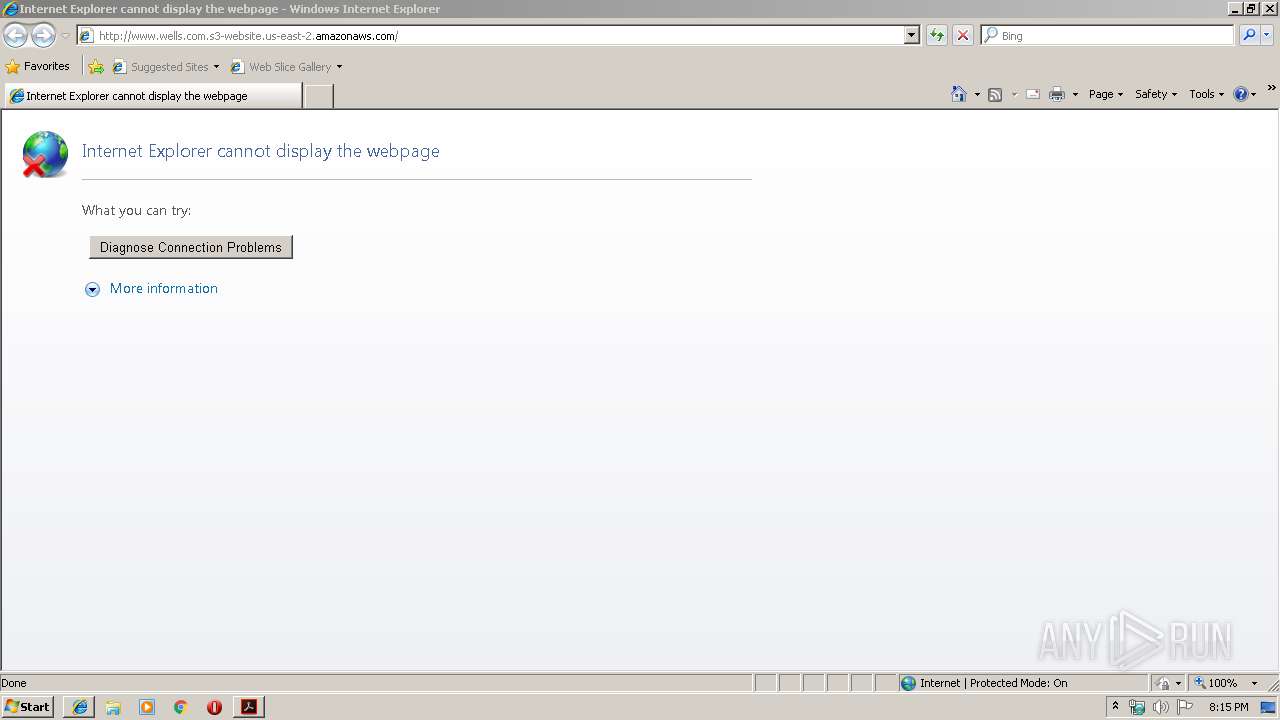
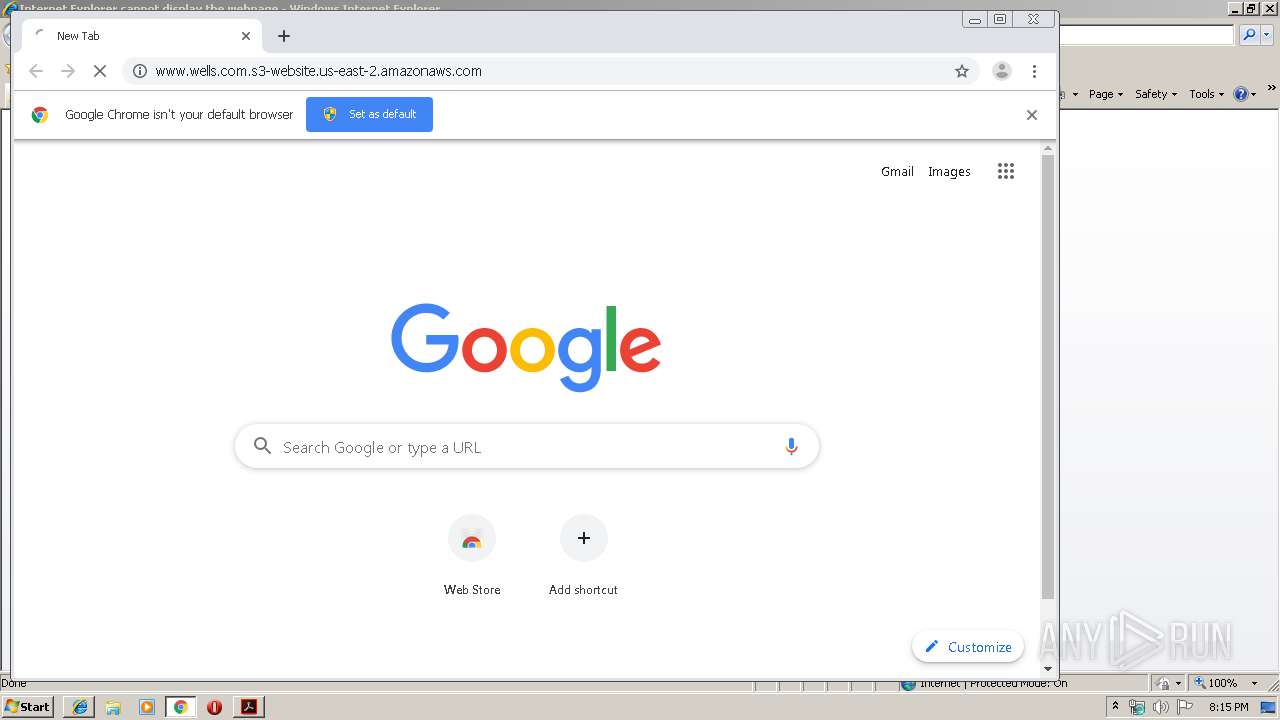
2928 | iexplore.exe | GET | 301 | 52.219.84.227:80 | http://www.wells.com.s3-website.us-east-2.amazonaws.com/ | US | — | — | shared |
2200 | AcroRd32.exe | GET | 304 | 2.16.186.57:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/280_15_23_20070.zip | unknown | — | — | whitelisted |
2208 | chrome.exe | GET | 301 | 52.219.84.92:80 | http://www.wells.com.s3-website.us-east-2.amazonaws.com/ | US | — | — | shared |
2200 | AcroRd32.exe | GET | 304 | 2.16.186.57:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/277_15_23_20070.zip | unknown | — | — | whitelisted |
2200 | AcroRd32.exe | GET | 304 | 2.16.186.57:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/278_15_23_20070.zip | unknown | — | — | whitelisted |
2200 | AcroRd32.exe | GET | 304 | 2.16.186.57:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/281_15_23_20070.zip | unknown | — | — | whitelisted |
2200 | AcroRd32.exe | GET | 304 | 2.16.186.57:80 | http://acroipm2.adobe.com/15/rdr/ENU/win/nooem/none/consumer/message.zip | unknown | — | — | whitelisted |
2208 | chrome.exe | GET | 302 | 172.217.18.174:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOWVmQUFXS041NV9ZVXlJVWwxbGc5TUM4dw/7519.422.0.3_pkedcjkdefgpdelpbcmbmeomcjbeemfm.crx | US | html | 534 b | whitelisted |
2208 | chrome.exe | GET | 200 | 185.180.12.141:80 | http://r2---sn-n02xgoxufvg3-8pxe.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvOTRmQUFXVHlhaGJaUTdMLWtCSkNJUl9ZQQ/1.0.0.5_nmmhkkegccagdldgiimedpiccmgmieda.crx?cms_redirect=yes&mip=185.183.107.227&mm=28&mn=sn-n02xgoxufvg3-8pxe&ms=nvh&mt=1575663197&mv=m&mvi=1&pl=24&shardbypass=yes | AT | crx | 293 Kb | whitelisted |
564 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2200 | AcroRd32.exe | 2.18.233.74:443 | armmf.adobe.com | Akamai International B.V. | — | whitelisted |
2208 | chrome.exe | 172.217.18.3:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
2208 | chrome.exe | 172.217.23.106:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2208 | chrome.exe | 172.217.22.35:443 | www.google.com.ua | Google Inc. | US | whitelisted |
2208 | chrome.exe | 172.217.22.99:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
2208 | chrome.exe | 216.58.210.3:443 | www.gstatic.com | Google Inc. | US | whitelisted |
2208 | chrome.exe | 172.217.21.238:443 | ogs.google.com | Google Inc. | US | whitelisted |
2208 | chrome.exe | 172.217.21.206:443 | apis.google.com | Google Inc. | US | whitelisted |
2208 | chrome.exe | 216.58.207.36:443 | www.google.com | Google Inc. | US | whitelisted |
2208 | chrome.exe | 52.219.84.92:80 | www.wells.com.s3-website.us-east-2.amazonaws.com | Amazon.com, Inc. | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
www.wells.com.s3-website.us-east-2.amazonaws.com |
| shared |
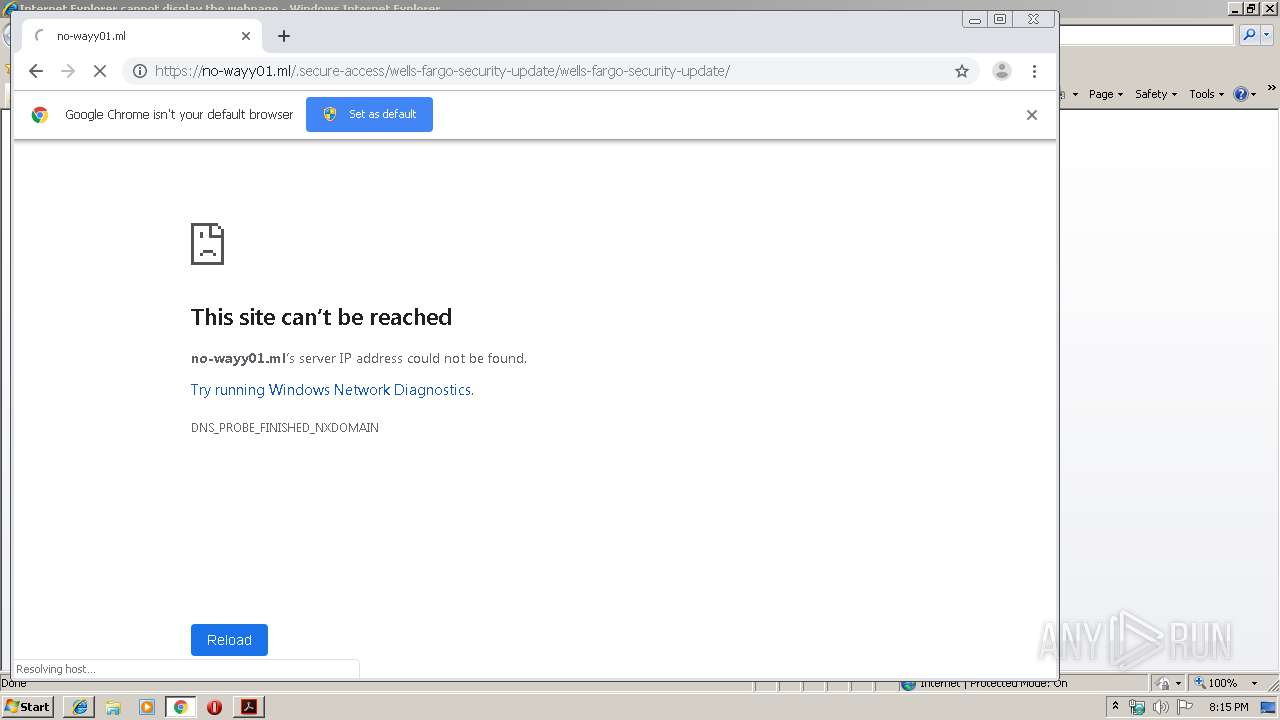
no-wayy01.ml |
| unknown |
acroipm2.adobe.com |
| whitelisted |
armmf.adobe.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com.ua |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET INFO DNS Query for Suspicious .ml Domain |