| File name: | Install_Win11_Win10_10073_09232024.zip |
| Full analysis: | https://app.any.run/tasks/f93a4c1f-4092-49b0-9333-f97f7590f693 |
| Verdict: | Malicious activity |
| Analysis date: | October 08, 2024, 15:17:22 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 497EC7C52835CE95D900AE3355F7817D |
| SHA1: | 5F5E4E7DF06684AE3DADF600528E507C0C88C23F |
| SHA256: | 9D56D24BDFB15667E83DD656682FAB9C43354CBAE237730E40A9140F9FCEE13B |
| SSDEEP: | 98304:absU4DzikcrdQGGmnuEsyh85KXq1TGRcypRl34FAEnAB1QkXNAIKhIcunPD/QFld:4Z1DMf |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5036)
SUSPICIOUS
Executable content was dropped or overwritten
- Install_Win11_Win10_10073_09232024.exe (PID: 1700)
- setup.exe (PID: 1952)
- setup.exe (PID: 7156)
Executes as Windows Service
- VSSVC.exe (PID: 7040)
Drops a system driver (possible attempt to evade defenses)
- Install_Win11_Win10_10073_09232024.exe (PID: 1700)
Starts itself from another location
- setup.exe (PID: 1952)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 5036)
Manual execution by a user
- Install_Win11_Win10_10073_09232024.exe (PID: 1700)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:09:26 17:53:18 |
| ZipCRC: | 0x1a83caf3 |
| ZipCompressedSize: | 4907887 |
| ZipUncompressedSize: | 5100208 |
| ZipFileName: | Install_Win11_Win10_10073_09232024.exe |
Total processes
143
Monitored processes
12
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1700 | "C:\Users\admin\Desktop\Install_Win11_Win10_10073_09232024.exe" | C:\Users\admin\Desktop\Install_Win11_Win10_10073_09232024.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
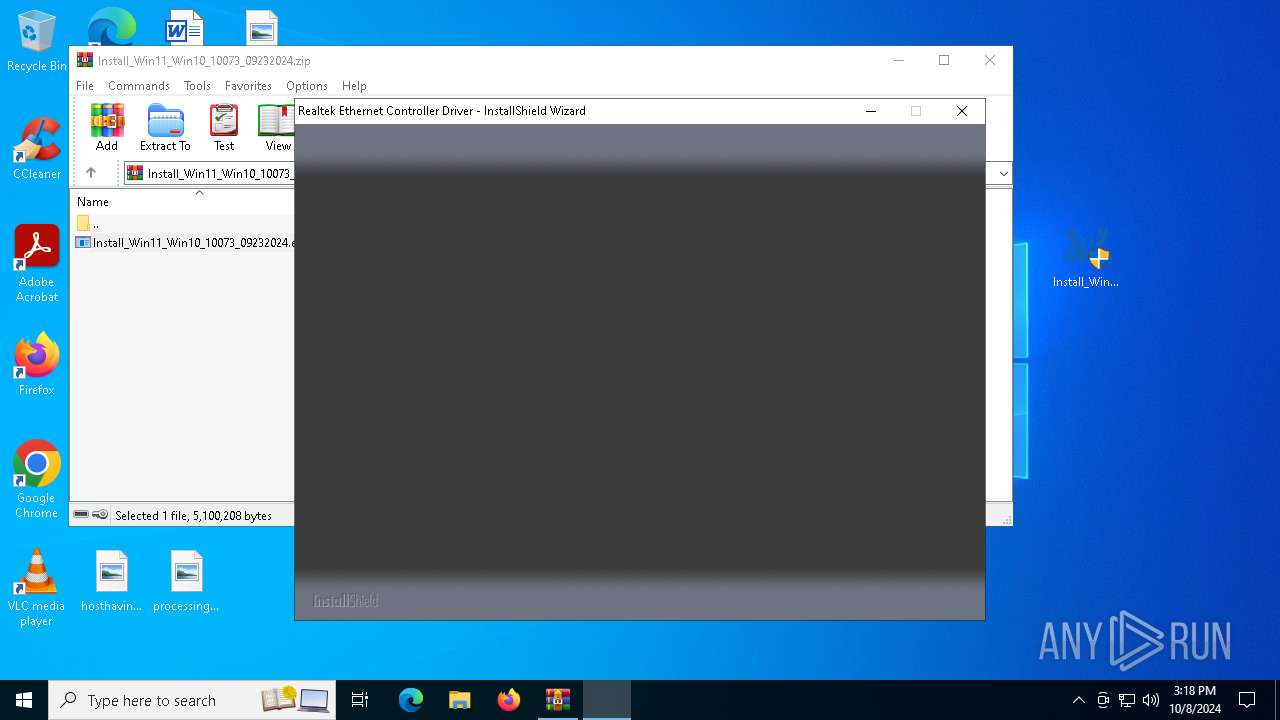
| 1952 | .\setup.exe | C:\Users\admin\AppData\Local\Temp\7zS4A664379\setup.exe | Install_Win11_Win10_10073_09232024.exe | ||||||||||||
User: admin Company: Realtek Integrity Level: HIGH Description: InstallScript Setup Launcher Unicode Version: 1.0.0.38 Modules
| |||||||||||||||
| 2428 | C:\Users\admin\AppData\Local\Temp\{ADCB9E7F-C88A-4CC7-A9EC-0F8A51B46545}\ISBEW64.exe {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{4EEA8ED6-E537-494D-9CE9-F559E03E292A} | C:\Users\admin\AppData\Local\Temp\{ADCB9E7F-C88A-4CC7-A9EC-0F8A51B46545}\ISBEW64.exe | — | setup.exe | |||||||||||
User: admin Company: Flexera Integrity Level: HIGH Description: InstallShield (R) 64-bit Setup Engine Exit code: 0 Version: 29.0.111 Modules
| |||||||||||||||
| 3944 | C:\Users\admin\AppData\Local\Temp\{ADCB9E7F-C88A-4CC7-A9EC-0F8A51B46545}\ISBEW64.exe {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{186DEFDE-FC44-4541-A8C2-478D494173FB} | C:\Users\admin\AppData\Local\Temp\{ADCB9E7F-C88A-4CC7-A9EC-0F8A51B46545}\ISBEW64.exe | — | setup.exe | |||||||||||
User: admin Company: Flexera Integrity Level: HIGH Description: InstallShield (R) 64-bit Setup Engine Exit code: 0 Version: 29.0.111 Modules
| |||||||||||||||
| 5036 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\Install_Win11_Win10_10073_09232024.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6380 | C:\Users\admin\AppData\Local\Temp\{ADCB9E7F-C88A-4CC7-A9EC-0F8A51B46545}\ISBEW64.exe {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{F548C3DE-1769-4AF3-9D33-9003FD4230FC} | C:\Users\admin\AppData\Local\Temp\{ADCB9E7F-C88A-4CC7-A9EC-0F8A51B46545}\ISBEW64.exe | — | setup.exe | |||||||||||
User: admin Company: Flexera Integrity Level: HIGH Description: InstallShield (R) 64-bit Setup Engine Version: 29.0.111 Modules
| |||||||||||||||
| 6384 | C:\Users\admin\AppData\Local\Temp\{ADCB9E7F-C88A-4CC7-A9EC-0F8A51B46545}\ISBEW64.exe {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{0C6E8A9A-3D98-4AC0-AFCE-84425C864A17} | C:\Users\admin\AppData\Local\Temp\{ADCB9E7F-C88A-4CC7-A9EC-0F8A51B46545}\ISBEW64.exe | — | setup.exe | |||||||||||
User: admin Company: Flexera Integrity Level: HIGH Description: InstallShield (R) 64-bit Setup Engine Exit code: 0 Version: 29.0.111 Modules
| |||||||||||||||
| 6392 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6444 | C:\Users\admin\AppData\Local\Temp\{ADCB9E7F-C88A-4CC7-A9EC-0F8A51B46545}\ISBEW64.exe {EFB7539B-24F3-46B6-AF6E-3B021B51EFEF}:{F7D66AA6-8D85-4811-A1F1-4D35F9886C22} | C:\Users\admin\AppData\Local\Temp\{ADCB9E7F-C88A-4CC7-A9EC-0F8A51B46545}\ISBEW64.exe | — | setup.exe | |||||||||||
User: admin Company: Flexera Integrity Level: HIGH Description: InstallShield (R) 64-bit Setup Engine Version: 29.0.111 Modules
| |||||||||||||||
| 7040 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 911
Read events
2 842
Write events
57
Delete events
12
Modification events
| (PID) Process: | (5036) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (5036) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Install_Win11_Win10_10073_09232024.zip | |||
| (PID) Process: | (5036) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5036) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5036) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5036) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7156) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion |
| Operation: | delete value | Name: | %IS_PREREQ%-Realtek Ethernet Controller Driver |
Value: | |||
| (PID) Process: | (7156) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion |
| Operation: | delete value | Name: | %IS_PREREQF%-Realtek Ethernet Controller Driver |
Value: | |||
| (PID) Process: | (7156) setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\RunOnce |
| Operation: | delete value | Name: | ISSetupPrerequisistes |
Value: | |||
| (PID) Process: | (7156) setup.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 40000000000000006E0EFF529519DB01F41B0000EC1B0000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
19
Suspicious files
46
Text files
592
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5036 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa5036.47521\Install_Win11_Win10_10073_09232024.exe | executable | |
MD5:9F08244D0DDC6C6BB59CD30FEC150A2F | SHA256:04D8C1E9B7D8456A6E5DAD96B5A27DB161EACD6C5A72D13B33C09C29513CDEC1 | |||
| 1700 | Install_Win11_Win10_10073_09232024.exe | C:\Users\admin\AppData\Local\Temp\7zS4A664379\0x040a.ini | text | |
MD5:B216BC7B827622578E60B0B37CE9C4C0 | SHA256:4E42D96CF24224D3ED43E7E14227B96FDE3B43235636480F8861DB0B048FFDDF | |||
| 1700 | Install_Win11_Win10_10073_09232024.exe | C:\Users\admin\AppData\Local\Temp\7zS4A664379\0x040c.ini | text | |
MD5:9A10EDDF9169F9508688EACE7B9E7797 | SHA256:D31B120F79C2FB8CD6F3FD7EDE220A30CA3BB84E4D3C8B05C1BCC833734D13CF | |||
| 1700 | Install_Win11_Win10_10073_09232024.exe | C:\Users\admin\AppData\Local\Temp\7zS4A664379\0x0403.ini | text | |
MD5:B306203AA1539AE5A541D42116066101 | SHA256:B456FC5A73D06BA3B76BF803A875A4CA742BE1C7AC7E1A88A35CB62CE3346E3B | |||
| 1700 | Install_Win11_Win10_10073_09232024.exe | C:\Users\admin\AppData\Local\Temp\7zS4A664379\0x040e.ini | text | |
MD5:DDC9D58C000E9E2E212541424A266BF7 | SHA256:2A00E14AD397F8C903E0D6C3CF1D1C98BA0560D577F31189B6A42F1D490BAFC2 | |||
| 1700 | Install_Win11_Win10_10073_09232024.exe | C:\Users\admin\AppData\Local\Temp\7zS4A664379\0x0410.ini | text | |
MD5:FFD754CB7FB9D6E7B999C7ECB444F8D1 | SHA256:4B13428BAAB7405A1125EFD93F3569875CD19477B38608D4DD2FE2CCD3861E0F | |||
| 1700 | Install_Win11_Win10_10073_09232024.exe | C:\Users\admin\AppData\Local\Temp\7zS4A664379\0x0414.ini | text | |
MD5:C2EEB17C18573974CDBFEB11647DC8BA | SHA256:8B4D38ACCA7EDEED68D2FB9DF91A501C272FDD42B06E0D142725F146FAC64B98 | |||
| 1700 | Install_Win11_Win10_10073_09232024.exe | C:\Users\admin\AppData\Local\Temp\7zS4A664379\0x0412.ini | text | |
MD5:59B2E4A2D3898F3E4F49186FF150E26C | SHA256:9416C7B55D1FD9DC06F20E1E3EBBAC1357217113833553D49586E339360529C7 | |||
| 1700 | Install_Win11_Win10_10073_09232024.exe | C:\Users\admin\AppData\Local\Temp\7zS4A664379\0x0411.ini | text | |
MD5:B807CE7552E96DC1928775956B9F422C | SHA256:3F0778538202A35483C084FB0B109F693A9853F64D6452DAA5C92AC75620AADC | |||
| 1700 | Install_Win11_Win10_10073_09232024.exe | C:\Users\admin\AppData\Local\Temp\7zS4A664379\0x0413.ini | text | |
MD5:715BA0228A81E4B327E0E21574F22B68 | SHA256:E2FA233AE46457D27061F7F2C6B06A7972B65070035FCBFF783B77F815F32A21 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
53
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3864 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3864 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
624 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5952 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1588 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5488 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4360 | SearchApp.exe | 2.23.209.187:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4020 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |