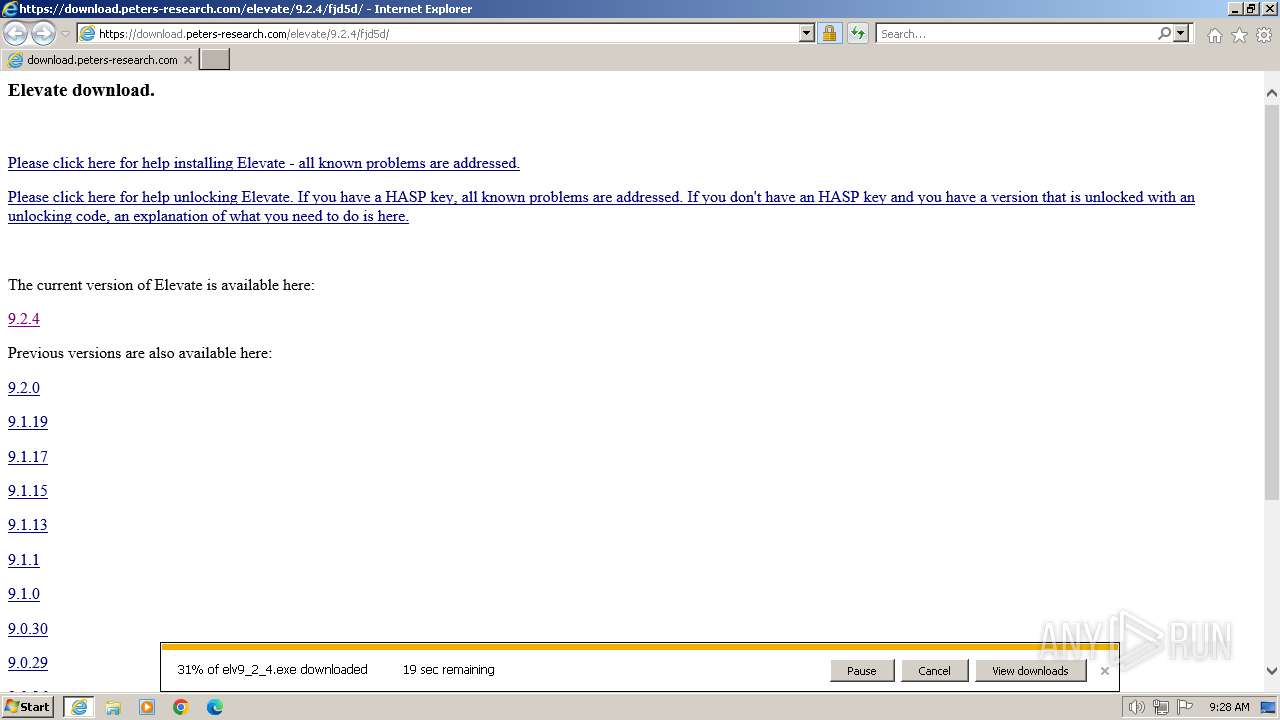
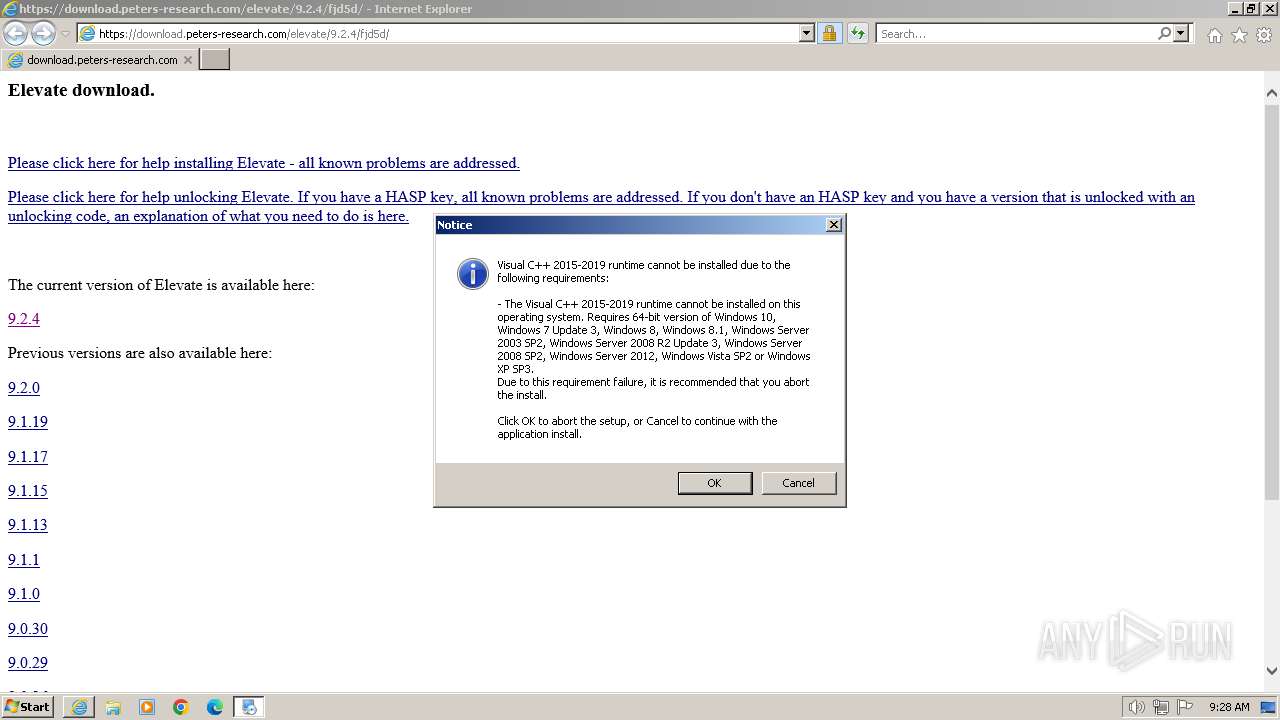
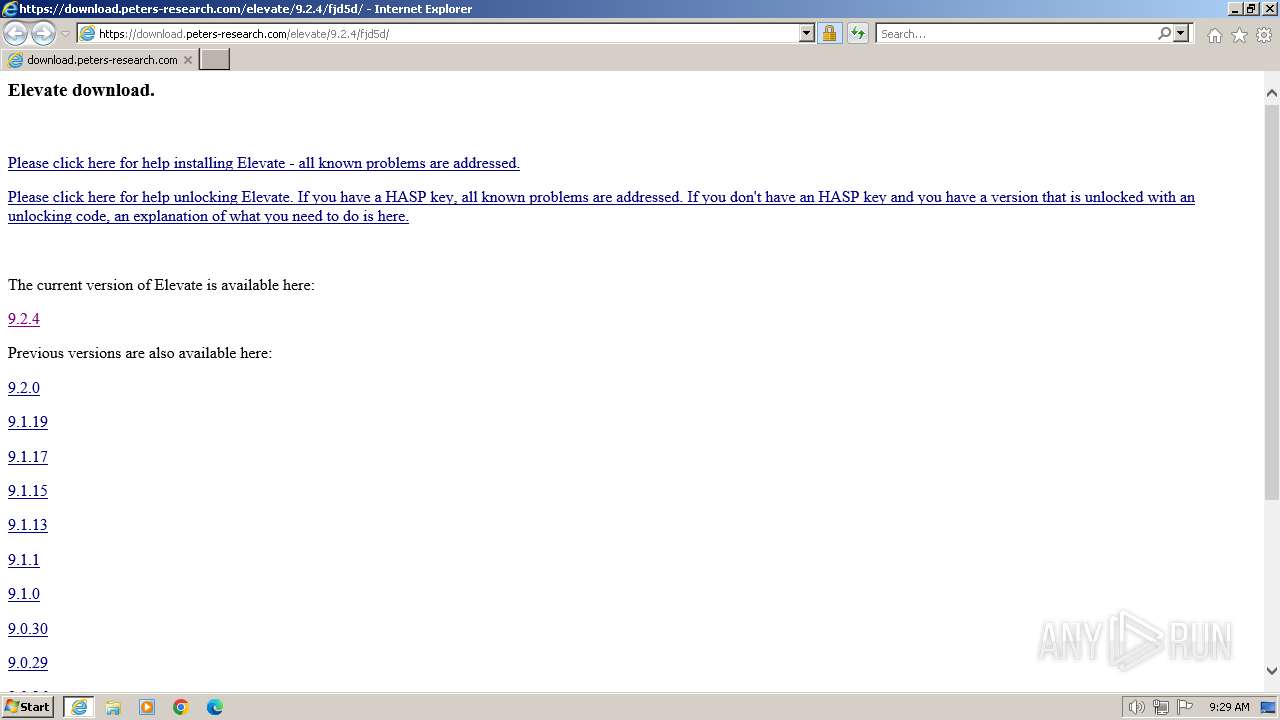
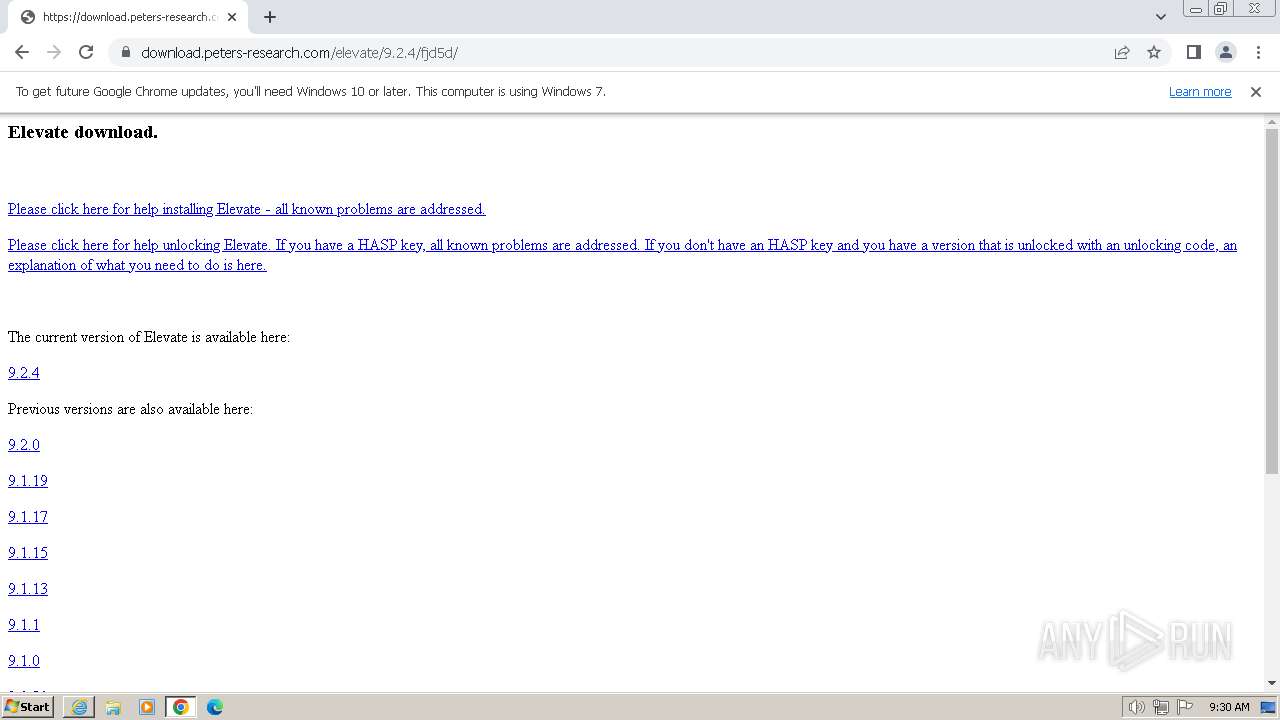
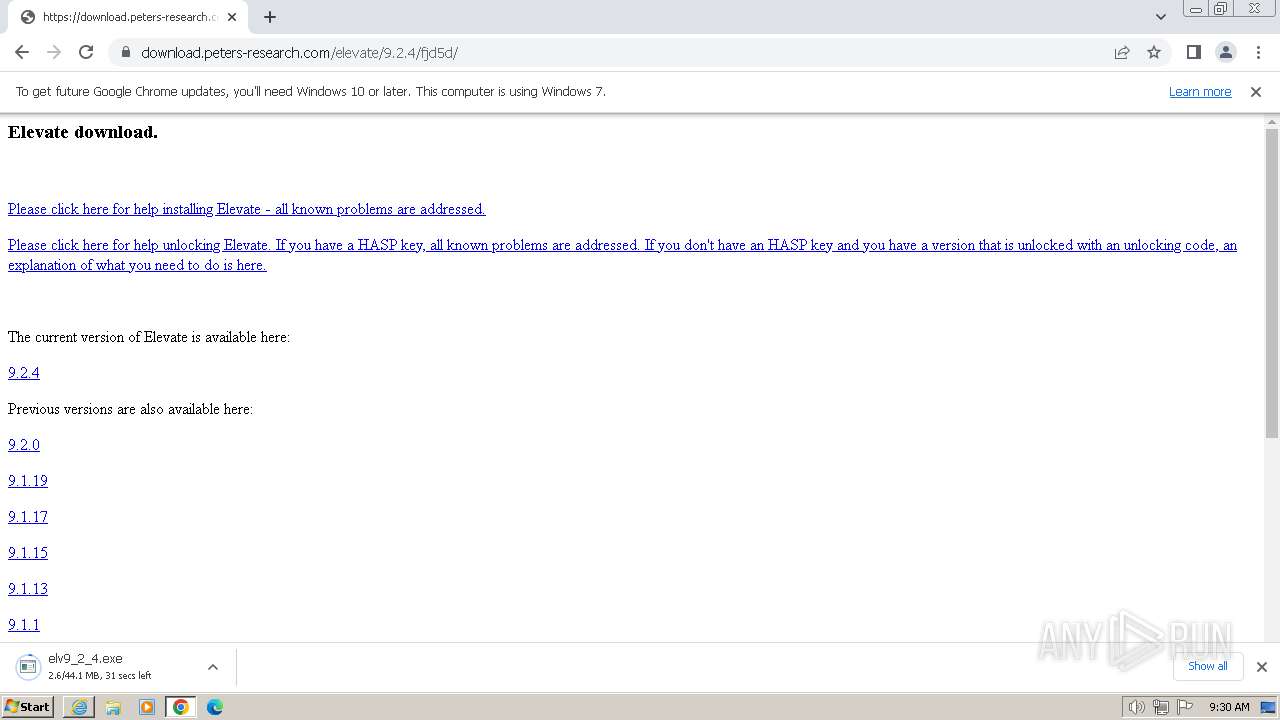
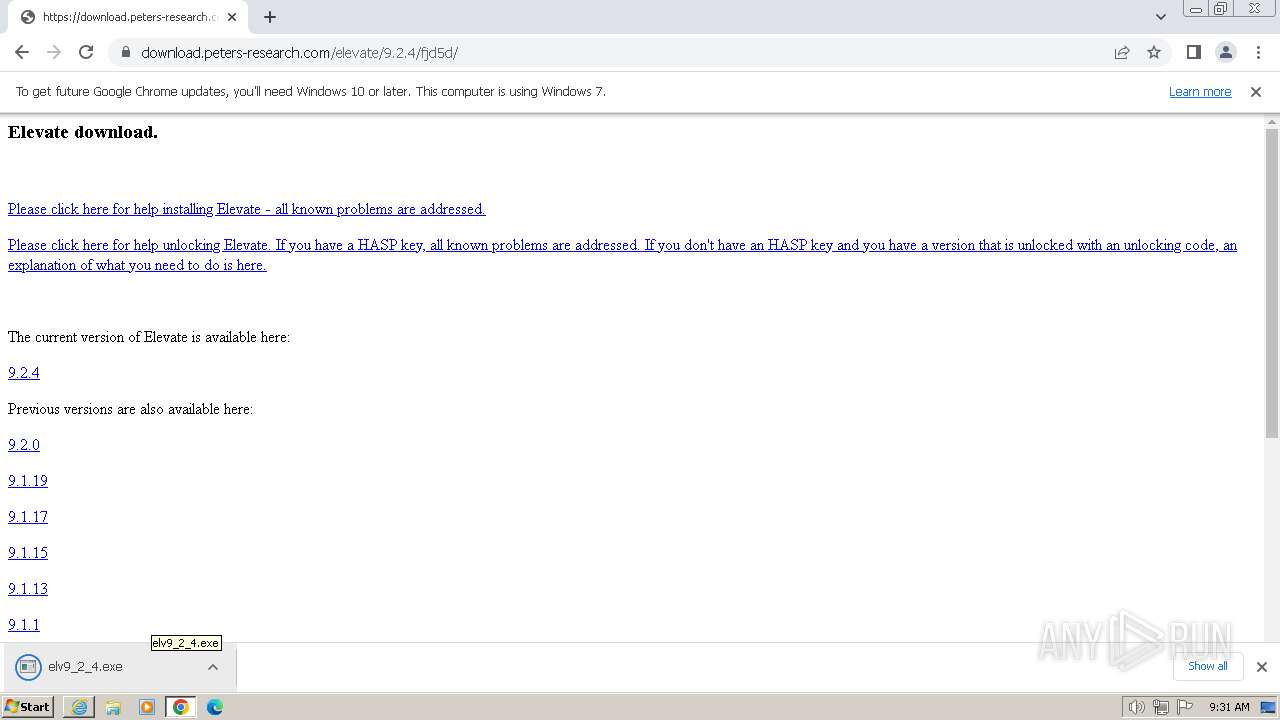
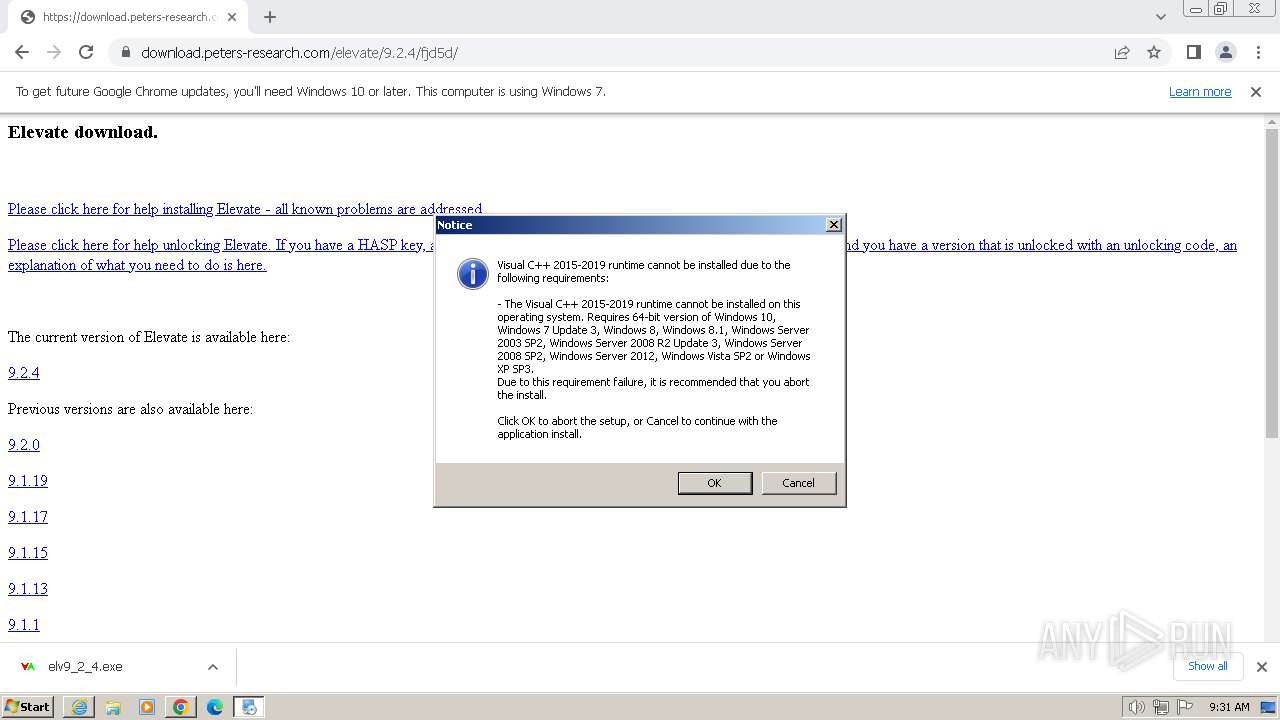
| URL: | https://download.peters-research.com/elevate/9.2.4/fjd5d/ |
| Full analysis: | https://app.any.run/tasks/ba6e7548-53d3-4040-b7c4-8482c1baf013 |
| Verdict: | Malicious activity |
| Analysis date: | January 29, 2024, 09:27:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | AF49BC3DE191133B4E5A8E76CB8694F6 |
| SHA1: | 5310584D94151539F4AE681E0DC6C69C8323946D |
| SHA256: | 9D3779E972FD757864D999F0DCE0A7882395DCCA015C62BF5F857025D2099365 |
| SSDEEP: | 3:N8SElqAfXAkXaTE964m8:2SK7/A/TNR8 |
MALICIOUS
Drops the executable file immediately after the start
- elv9_2_4.exe (PID: 3472)
- irsetup.exe (PID: 3760)
- vcredist_x86.exe (PID: 4092)
- elv9_2_4.exe (PID: 3360)
- irsetup.exe (PID: 292)
- vcredist_x86.exe (PID: 3784)
SUSPICIOUS
Executable content was dropped or overwritten
- elv9_2_4.exe (PID: 3472)
- irsetup.exe (PID: 3760)
- vcredist_x86.exe (PID: 4092)
- irsetup.exe (PID: 292)
- elv9_2_4.exe (PID: 3360)
- vcredist_x86.exe (PID: 3784)
Reads the Internet Settings
- elv9_2_4.exe (PID: 3472)
- elv9_2_4.exe (PID: 3360)
Reads the Windows owner or organization settings
- irsetup.exe (PID: 3760)
- irsetup.exe (PID: 292)
Process drops legitimate windows executable
- irsetup.exe (PID: 3760)
- vcredist_x86.exe (PID: 4092)
- irsetup.exe (PID: 292)
- vcredist_x86.exe (PID: 3784)
Starts a Microsoft application from unusual location
- vcredist_x86.exe (PID: 4092)
- vcredist_x86.exe (PID: 3784)
INFO
Application launched itself
- iexplore.exe (PID: 2580)
- chrome.exe (PID: 2360)
- chrome.exe (PID: 3872)
Executable content was dropped or overwritten
- iexplore.exe (PID: 2584)
- chrome.exe (PID: 3872)
Manual execution by a user
- chrome.exe (PID: 2360)
- explorer.exe (PID: 2348)
- chrome.exe (PID: 3872)
Drops the executable file immediately after the start
- iexplore.exe (PID: 2584)
- chrome.exe (PID: 3872)
Create files in a temporary directory
- elv9_2_4.exe (PID: 3472)
- irsetup.exe (PID: 3760)
- install.exe (PID: 1780)
- elv9_2_4.exe (PID: 3360)
- irsetup.exe (PID: 292)
- install.exe (PID: 3732)
The process uses the downloaded file
- iexplore.exe (PID: 2580)
- chrome.exe (PID: 3288)
- chrome.exe (PID: 3872)
Reads the computer name
- elv9_2_4.exe (PID: 3472)
- irsetup.exe (PID: 3760)
- vcredist_x86.exe (PID: 4092)
- install.exe (PID: 1780)
- elv9_2_4.exe (PID: 3360)
- irsetup.exe (PID: 292)
- vcredist_x86.exe (PID: 3784)
- install.exe (PID: 3732)
Checks supported languages
- elv9_2_4.exe (PID: 3472)
- irsetup.exe (PID: 3760)
- vcredist_x86.exe (PID: 4092)
- elv9_2_4.exe (PID: 3360)
- vcredist_x86.exe (PID: 3784)
- install.exe (PID: 3732)
- install.exe (PID: 1780)
- irsetup.exe (PID: 292)
Reads Environment values
- vcredist_x86.exe (PID: 4092)
- vcredist_x86.exe (PID: 3784)
Reads the machine GUID from the registry
- vcredist_x86.exe (PID: 4092)
- install.exe (PID: 1780)
- vcredist_x86.exe (PID: 3784)
- install.exe (PID: 3732)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
93
Monitored processes
44
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 292 | "C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\irsetup.exe" __IRAOFF:1796642 "__IRAFN:C:\Users\admin\Downloads\elv9_2_4.exe" "__IRCT:0" "__IRTSS:0" "__IRSID:S-1-5-21-1302019708-1500728564-335382590-1000" | C:\Users\admin\AppData\Local\Temp\_ir_sf_temp_0\irsetup.exe | elv9_2_4.exe | ||||||||||||
User: admin Company: Indigo Rose Corporation Integrity Level: HIGH Description: Setup Application Exit code: 5 Version: 9.5.3.0 Modules
| |||||||||||||||
| 884 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6bc88b38,0x6bc88b48,0x6bc88b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 884 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --first-renderer-process --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=6 --mojo-platform-channel-handle=2152 --field-trial-handle=1160,i,2806290548077819821,487614043702189967,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1548 | "C:\Users\admin\Downloads\elv9_2_4.exe" | C:\Users\admin\Downloads\elv9_2_4.exe | — | chrome.exe | |||||||||||
User: admin Company: Peters Research Ltd Integrity Level: MEDIUM Description: Elevate Setup Application Exit code: 3221226540 Version: 9.2.4.0 Modules
| |||||||||||||||
| 1596 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --disable-quic --mojo-platform-channel-handle=3484 --field-trial-handle=1160,i,2806290548077819821,487614043702189967,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1736 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2272 --field-trial-handle=1160,i,2806290548077819821,487614043702189967,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1780 | c:\03036fcbc5883bfae560bd64\.\install.exe /q | C:\03036fcbc5883bfae560bd64\install.exe | — | vcredist_x86.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: External Installer Exit code: 0 Version: 9.0.30729.5677 built by: QFE Modules
| |||||||||||||||
| 2348 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2360 | "C:\Program Files\Google\Chrome\Application\chrome.exe" "--disable-features=OptimizationGuideModelDownloading,OptimizationHintsFetching,OptimizationTargetPrediction,OptimizationHints" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 2376 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --mojo-platform-channel-handle=1372 --field-trial-handle=1112,i,930604250760029024,4477619128980505917,131072 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
Total events
29 859
Read events
29 626
Write events
221
Delete events
12
Modification events
| (PID) Process: | (2580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2580) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
35
Suspicious files
102
Text files
95
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2584 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 2584 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar954A.tmp | cat | |
MD5:9C0C641C06238516F27941AA1166D427 | SHA256:4276AF3669A141A59388BC56A87F6614D9A9BDDDF560636C264219A7EB11256F | |||
| 2584 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:0A11B7904218FA8B656C922B37DCE4B7 | SHA256:5CCDE16383E9059EC816B377FF2582806643418164FA38AA5FA5487FC4ECD2A6 | |||
| 2580 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\EAF8AA29A62AB29E614331747385D816_F9E4DC0B9D5C777357D7DB8DEF51118A | der | |
MD5:E5BAEC50EB97E2657E3DBFF1AD701673 | SHA256:4CEF4B9A4F0836EC91164F873858B5FEEA58ECA372B2C6F510E9C35E33FCDCA6 | |||
| 2360 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF156c02.TMP | — | |
MD5:— | SHA256:— | |||
| 2360 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2584 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\5237B19BEFD37CEC19A885F5C8D684BA | binary | |
MD5:74E9D5BB3CCE486B6A3BEECB333B4307 | SHA256:5F621D7C4A7966F0F7E3C31274251C4E93E4AF7630B93452B561C57511038BC5 | |||
| 2584 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\fjd5d[1].htm | html | |
MD5:B7721E64C84D7CEDBDD481F2B9BD47EE | SHA256:0558DE26F3BBB31AC2C7120A4ECD8B9AB021734079434497057FAD52D105C7E5 | |||
| 2584 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\5237B19BEFD37CEC19A885F5C8D684BA | binary | |
MD5:151378F91CACB1E40A09A86E4EA31217 | SHA256:2D562540E5CD1D3E53F382C468871DE03D2234F897544208A6C4B0FDA128A22E | |||
| 2584 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar954C.tmp | cat | |
MD5:9C0C641C06238516F27941AA1166D427 | SHA256:4276AF3669A141A59388BC56A87F6614D9A9BDDDF560636C264219A7EB11256F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
42
DNS requests
45
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2584 | iexplore.exe | GET | 304 | 23.32.238.218:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?a0aa2a2858c872c9 | unknown | — | — | unknown |
2584 | iexplore.exe | GET | 200 | 23.32.238.218:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?d66bcfdf10b71413 | unknown | compressed | 65.2 Kb | unknown |
2584 | iexplore.exe | GET | 200 | 184.24.77.61:80 | http://r3.o.lencr.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBRI2smg%2ByvTLU%2Fw3mjS9We3NfmzxAQUFC6zF7dYVsuuUAlA5h%2BvnYsUwsYCEgOfNPfC74nlJL%2BXwtti5%2BnkYA%3D%3D | unknown | binary | 503 b | unknown |
2580 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 313 b | unknown |
2580 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAxq6XzO1ZmDhpCgCp6lMhQ%3D | unknown | binary | 471 b | unknown |
2580 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
2580 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | binary | 471 b | unknown |
2580 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
2584 | iexplore.exe | GET | 304 | 23.32.238.218:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?da46b50ef2a0354a | unknown | — | — | unknown |
2584 | iexplore.exe | GET | 200 | 23.32.238.218:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?09ca35c5e0844a72 | unknown | compressed | 65.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2584 | iexplore.exe | 77.68.82.55:443 | download.peters-research.com | IONOS SE | GB | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2584 | iexplore.exe | 23.32.238.218:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2584 | iexplore.exe | 69.192.161.44:80 | x1.c.lencr.org | AKAMAI-AS | DE | unknown |
2584 | iexplore.exe | 184.24.77.61:80 | r3.o.lencr.org | Akamai International B.V. | DE | unknown |
2580 | iexplore.exe | 77.68.82.55:443 | download.peters-research.com | IONOS SE | GB | unknown |
2580 | iexplore.exe | 23.32.238.218:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
2580 | iexplore.exe | 104.126.37.177:443 | www.bing.com | Akamai International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
download.peters-research.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
x1.c.lencr.org |
| whitelisted |
r3.o.lencr.org |
| shared |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |