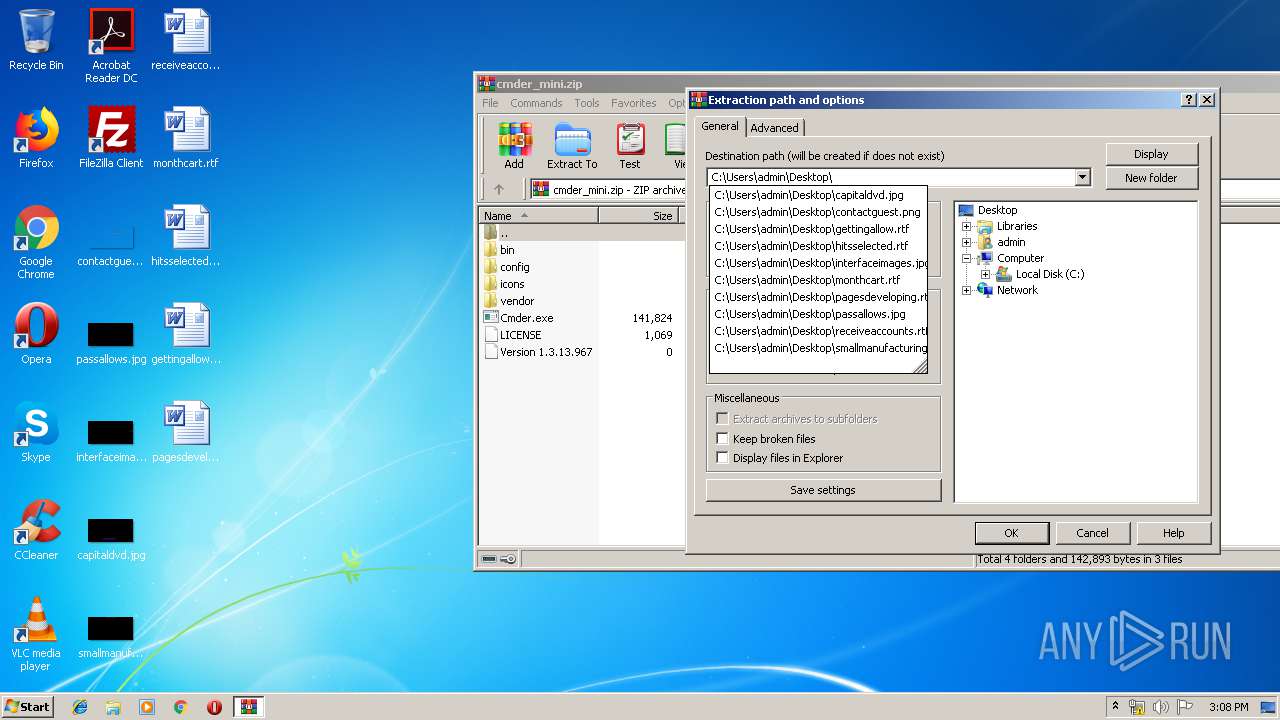
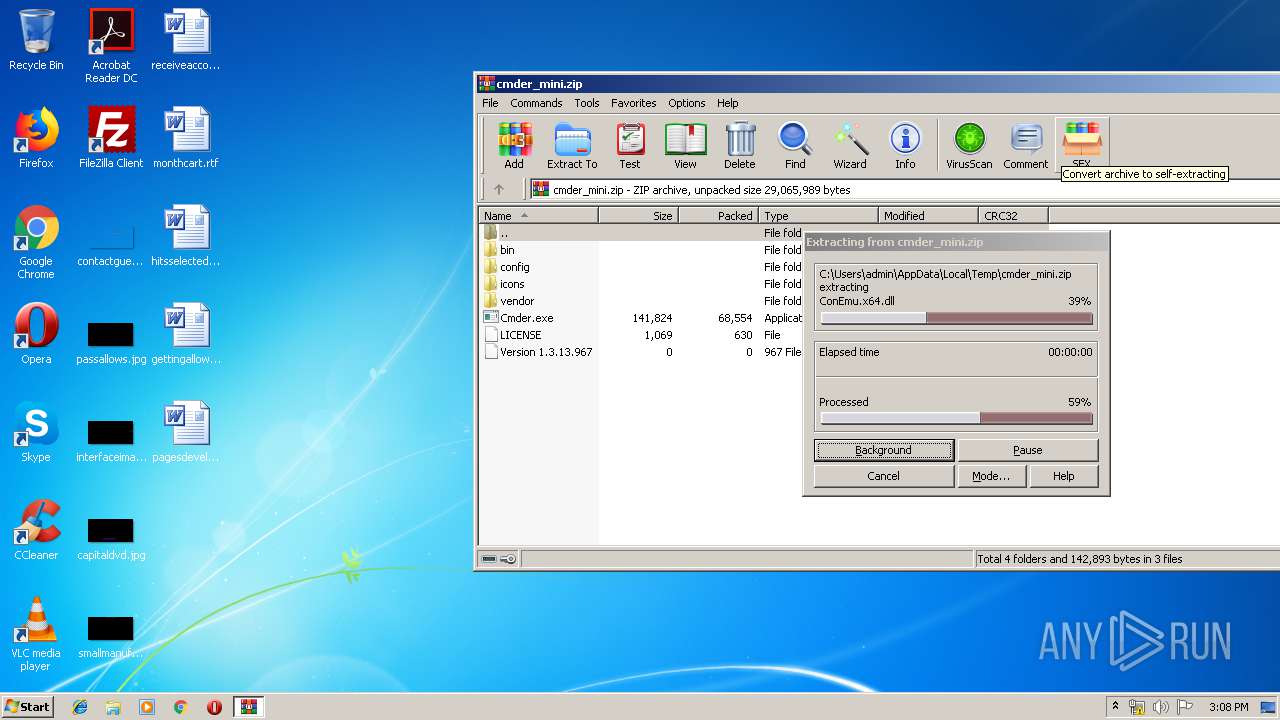
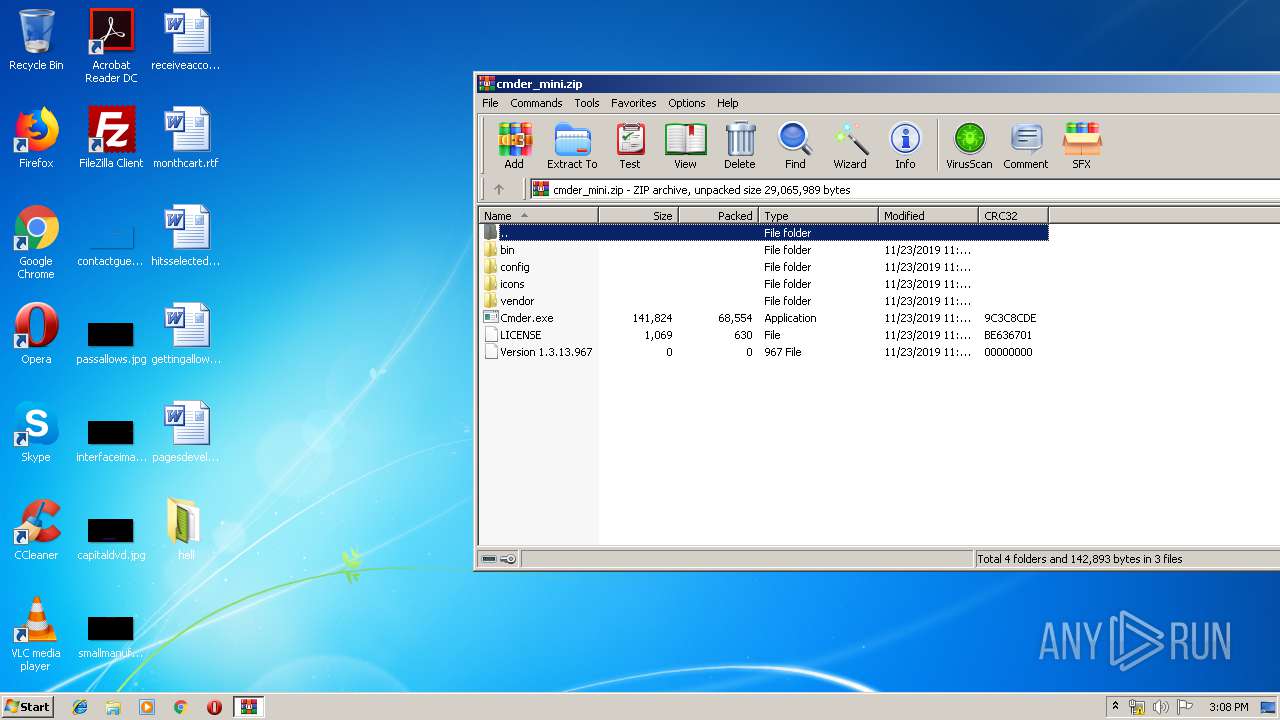
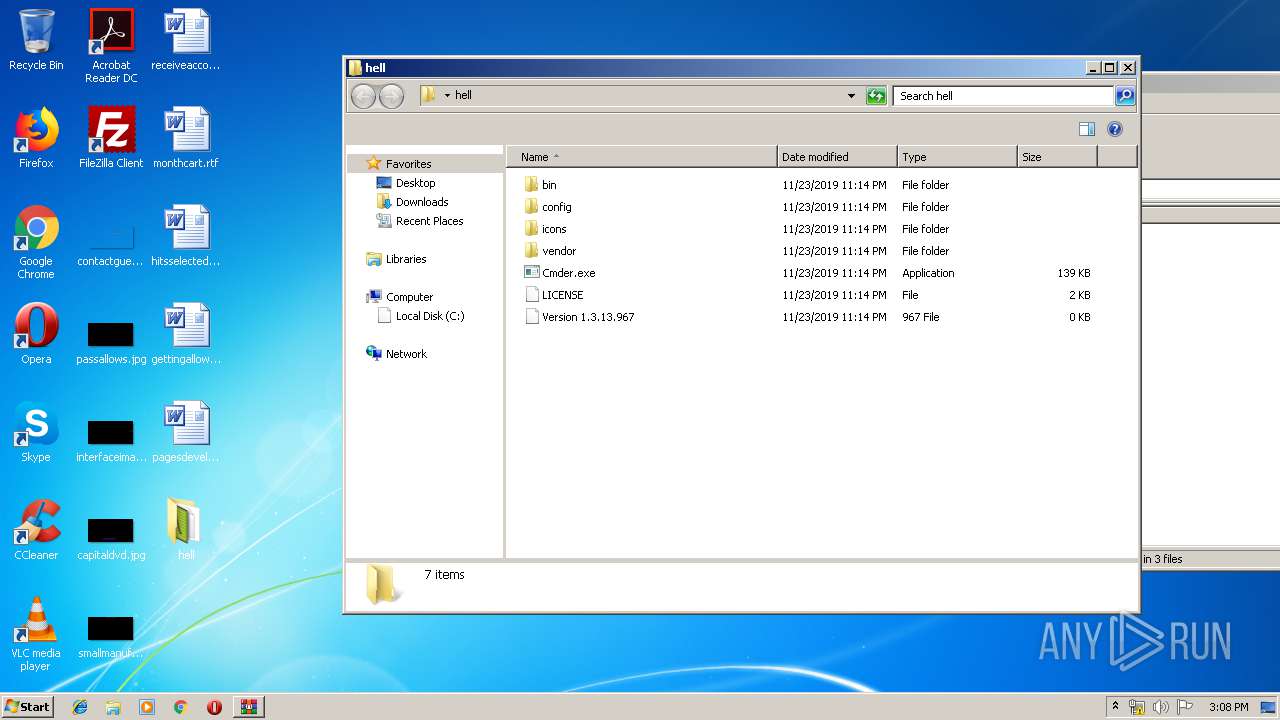
| File name: | cmder_mini.zip |
| Full analysis: | https://app.any.run/tasks/38a32464-f1e8-4f24-831d-65bd354d23a1 |
| Verdict: | Malicious activity |
| Analysis date: | January 06, 2020, 15:06:37 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 532DA19C62937052AA1626882AE10E9D |
| SHA1: | BA3ED4D89A04D2739751CFE24D1E170B64F7593A |
| SHA256: | 9D1A2D50AF8C335E29F7A2BA4536D3AC1CE2423C030486AF184D91A5BA77A021 |
| SSDEEP: | 196608:z7f/BwqrrczhV+ln7WKeKwj9uOwgf/RSRbwWd2iFDcdjRCnKwpFp4Ujl8Lfq18:Ze1V+dWKeKgfJvsDKS4NLfqm |
MALICIOUS
Detects Cygwin installation
- WinRAR.exe (PID: 892)
Application was dropped or rewritten from another process
- Cmder.exe (PID: 1532)
- ConEmu.exe (PID: 2088)
- ConEmuC.exe (PID: 4080)
- ConEmuC.exe (PID: 2560)
- clink_x86.exe (PID: 3552)
Loads dropped or rewritten executable
- ConEmu.exe (PID: 2088)
- ConEmuC.exe (PID: 2560)
- SearchProtocolHost.exe (PID: 3532)
- cmd.exe (PID: 2060)
- cmd.exe (PID: 3028)
- find.exe (PID: 3316)
- cmd.exe (PID: 2400)
- find.exe (PID: 992)
- find.exe (PID: 3884)
- cmd.exe (PID: 3892)
- find.exe (PID: 856)
- cmd.exe (PID: 2108)
- cmd.exe (PID: 3564)
- where.exe (PID: 4064)
- cmd.exe (PID: 1048)
- doskey.exe (PID: 3264)
- clink_x86.exe (PID: 3552)
SUSPICIOUS
Creates files in the user directory
- ConEmuC.exe (PID: 4080)
Starts CMD.EXE for commands execution
- ConEmuC.exe (PID: 2560)
- cmd.exe (PID: 2060)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 892)
Application launched itself
- cmd.exe (PID: 2060)
INFO
Manual execution by user
- Cmder.exe (PID: 1532)
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 892)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xpi | | | Mozilla Firefox browser extension (44.4) |
|---|---|---|
| .kmz | | | Google Earth saved working session (33.3) |
| .zip | | | ZIP compressed archive (22.2) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2019:11:23 23:14:04 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | bin/ |
Total processes
56
Monitored processes
20
Malicious processes
12
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 856 | C:\Windows\System32\find /i "\tccle" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 892 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\cmder_mini.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 992 | C:\Windows\System32\find /i "\cmd.exe" | C:\Windows\System32\find.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (grep) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1048 | C:\Windows\system32\cmd.exe /S /D /c" echo C:\Windows\system32\cmd.exe " | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1532 | "C:\Users\admin\Desktop\hell\Cmder.exe" | C:\Users\admin\Desktop\hell\Cmder.exe | — | explorer.exe | |||||||||||
User: admin Company: Samuel Vasko Integrity Level: MEDIUM Description: Cmder: Lovely Console Emulator. Exit code: 0 Version: 1.3.13.967 Modules
| |||||||||||||||
| 2060 | "C:\Windows\system32\cmd.exe" /k ""C:\Users\admin\Desktop\hell\vendor\conemu-maximus5\..\init.bat" " | C:\Windows\system32\cmd.exe | — | ConEmuC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2088 | /Icon "C:\Users\admin\Desktop\hell\icons\cmder.ico" /Title Cmder | C:\Users\admin\Desktop\hell\vendor\conemu-maximus5\ConEmu.exe | — | Cmder.exe | |||||||||||
User: admin Company: ConEmu-Maximus5 Integrity Level: MEDIUM Description: Console Emulator (x86) Exit code: 0 Version: 191012 Modules
| |||||||||||||||
| 2108 | C:\Windows\system32\cmd.exe /c dir /b *.bat *.cmd 2>nul | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2400 | C:\Windows\system32\cmd.exe /S /D /c" echo C:\Windows\system32\cmd.exe " | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2560 | "C:\Users\admin\Desktop\hell\vendor\conemu-maximus5\ConEmu\ConEmuC.exe" /CINMODE=600020 /AID=3928 /GID=2088 /GHWND=000701D0 /BW=158 /BH=39 /BZ=1000 "/FN=Lucida Console" /FW=3 /FH=5 /TA=10100007 /HIDE /ROOT cmd /k ""%ConEmuDir%\..\init.bat" " | C:\Users\admin\Desktop\hell\vendor\conemu-maximus5\ConEmu\ConEmuC.exe | — | ConEmu.exe | |||||||||||
User: admin Company: ConEmu-Maximus5 Integrity Level: MEDIUM Description: ConEmu console extender (x86) Exit code: 0 Version: 191012 Modules
| |||||||||||||||
Total events
908
Read events
858
Write events
50
Delete events
0
Modification events
| (PID) Process: | (892) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (892) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (892) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (892) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\cmder_mini.zip | |||
| (PID) Process: | (892) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (892) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (892) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (892) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (892) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\cmder_mini | |||
| (PID) Process: | (892) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\AppData\Local\Temp\cmder_mini | |||
Executable files
72
Suspicious files
2
Text files
464
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 892 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\cmder_mini\vendor\bin\cmder_diag.sh | text | |
MD5:— | SHA256:— | |||
| 892 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\cmder_mini\vendor\bin\cexec.cmd | text | |
MD5:— | SHA256:— | |||
| 892 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\cmder_mini\vendor\clink-completions\.appveyor.yml | text | |
MD5:— | SHA256:— | |||
| 892 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\cmder_mini\icons\cmder_blue.ico | image | |
MD5:AB73ACD3217CFE41365F402E181D7BDC | SHA256:E977865AE134627546CEA5C2812D97EE0ED95BFF9E1898FE34914752BF874A9D | |||
| 892 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\cmder_mini\icons\cmder_purple.ico | image | |
MD5:6FBFB21B19D1F121677D7A65C85DA161 | SHA256:1590442D927F83FCB972F9222B0C601F09DF381AD5A5F3E1787B59F19839BB75 | |||
| 892 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\cmder_mini\vendor\bin\alias.cmd | text | |
MD5:— | SHA256:— | |||
| 892 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\cmder_mini\icons\cmder_yellow.ico | image | |
MD5:44BF5A22AABAC9066A8615CCE90EF072 | SHA256:1BD776A7FD5D6D22DE7162253817B39C992FAA0DF58AE0819ED52F2650BC1A5A | |||
| 892 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\cmder_mini\vendor\bin\cmder_diag.ps1 | text | |
MD5:— | SHA256:— | |||
| 892 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\cmder_mini\icons\cmder_red.ico | image | |
MD5:234F158B4045CC13FDF6169B126C3A34 | SHA256:C1EAA6BC7E0C4879C7E63C5CD8B273803C7E309086CF5016D5F477DE3201A175 | |||
| 892 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\cmder_mini\bin\Readme.md | text | |
MD5:2AE7FF8D39775C0D3D8D115EEE20D9F1 | SHA256:52BFAD419624895FC121501AE2A4F6F49F41BD2D6EA0321E16A669B813AAC7A9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
1
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4080 | ConEmuC.exe | 185.199.108.153:443 | conemu.github.io | GitHub, Inc. | NL | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
conemu.github.io |
| whitelisted |