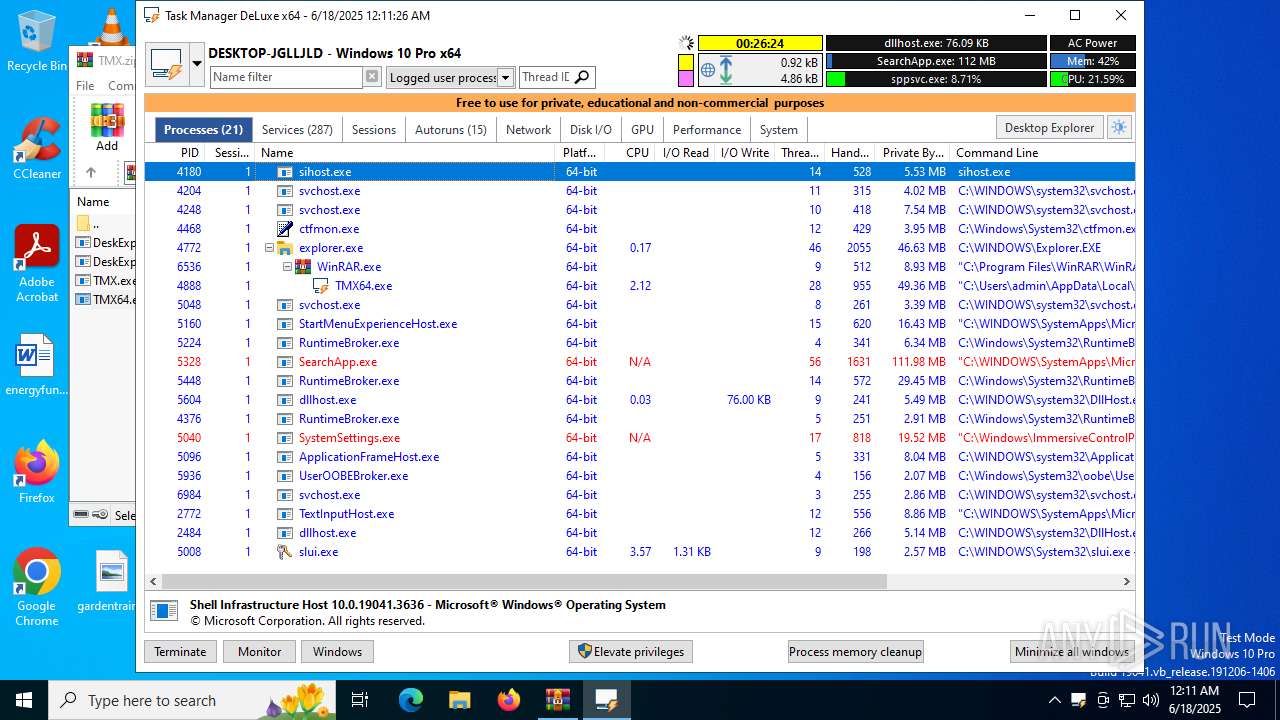
| File name: | TMX.zip |
| Full analysis: | https://app.any.run/tasks/bf9e83ff-932c-43a9-a97a-54f25215566f |
| Verdict: | Malicious activity |
| Analysis date: | June 18, 2025, 00:10:25 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 335F1A5F293487BE3BE6BD4C3F0E1200 |
| SHA1: | 73E9E4CC6C727E73502E76B4F447E86063605F64 |
| SHA256: | 9D1A14F4FCE1B0183A61261350DD62FB9D85F31B47D46D42AB2C2A0EDBD85600 |
| SSDEEP: | 98304:enchX3OCMRzWhGAiEZP8HLOAK/kqE1fBArPfwMMb3ptJDiOLCWxGhC822qeAbpSx:EuheN3KLVCUDMqS33gn9i+ |
MALICIOUS
Executing a file with an untrusted certificate
- TMX64.exe (PID: 4888)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 6536)
- TMX64.exe (PID: 4888)
The process checks if it is being run in the virtual environment
- TMX64.exe (PID: 4888)
Reads the BIOS version
- TMX64.exe (PID: 4888)
Read disk information to detect sandboxing environments
- TMX64.exe (PID: 4888)
Reads the date of Windows installation
- TMX64.exe (PID: 4888)
Reads the Windows owner or organization settings
- TMX64.exe (PID: 4888)
There is functionality for taking screenshot (YARA)
- TMX64.exe (PID: 4888)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 6536)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6536)
Checks supported languages
- TMX64.exe (PID: 4888)
Reads the computer name
- TMX64.exe (PID: 4888)
Reads Environment values
- TMX64.exe (PID: 4888)
Reads product name
- TMX64.exe (PID: 4888)
Reads the machine GUID from the registry
- TMX64.exe (PID: 4888)
Checks proxy server information
- TMX64.exe (PID: 4888)
Creates files or folders in the user directory
- TMX64.exe (PID: 4888)
Reads the time zone
- TMX64.exe (PID: 4888)
Disables trace logs
- TMX64.exe (PID: 4888)
Reads CPU info
- TMX64.exe (PID: 4888)
Reads Windows Product ID
- TMX64.exe (PID: 4888)
Compiled with Borland Delphi (YARA)
- TMX64.exe (PID: 4888)
Process checks whether UAC notifications are on
- TMX64.exe (PID: 4888)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:03:28 08:54:00 |
| ZipCRC: | 0xf2485f99 |
| ZipCompressedSize: | 4227233 |
| ZipUncompressedSize: | 4425336 |
| ZipFileName: | TMX.exe |
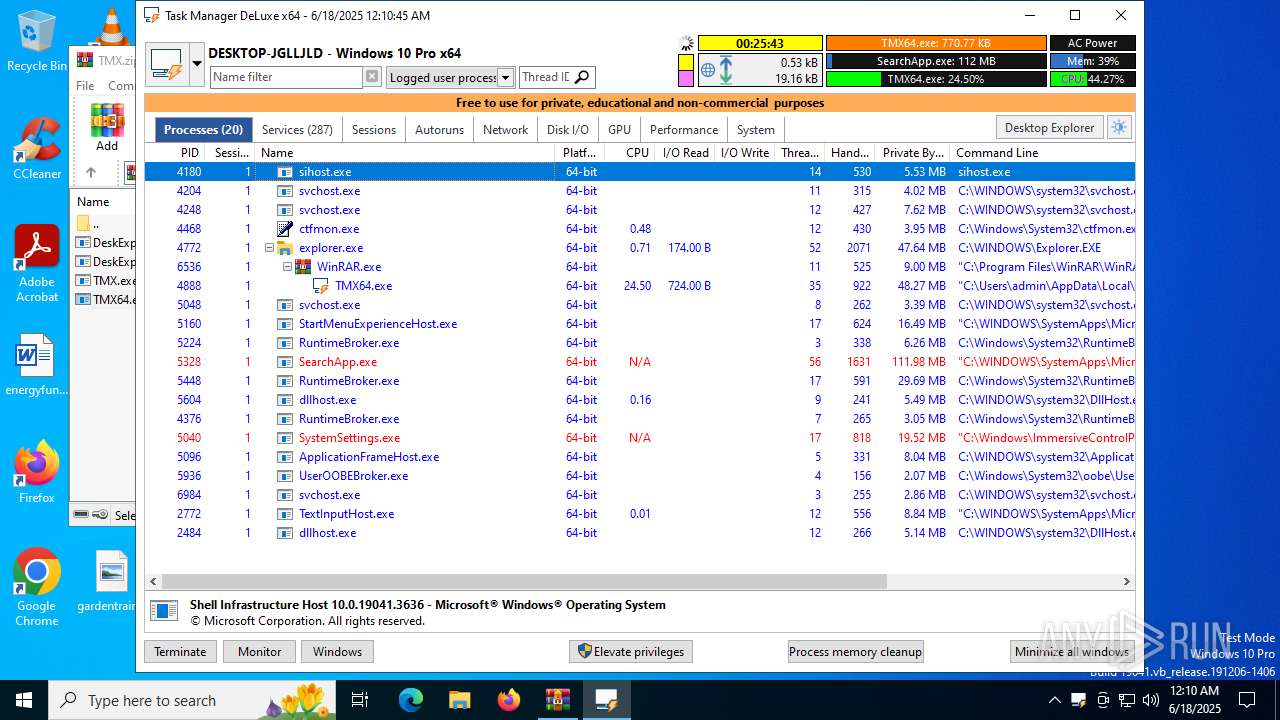
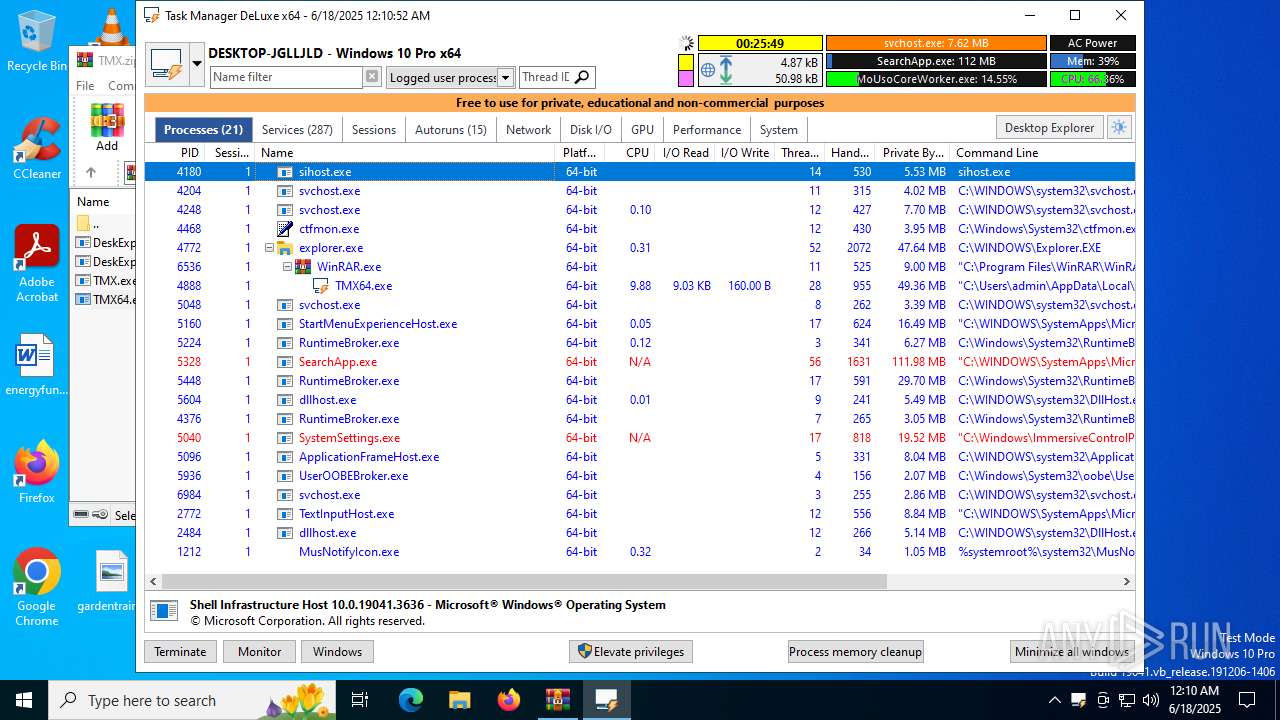
Total processes
137
Monitored processes
3
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4888 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa6536.24973\TMX64.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa6536.24973\TMX64.exe | WinRAR.exe | ||||||||||||
User: admin Company: MiTeC Integrity Level: MEDIUM Description: Task Manager DeLuxe Version: 4.9.0.0 Modules
| |||||||||||||||
| 5008 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6536 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\TMX.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
Total events
19 293
Read events
19 272
Write events
21
Delete events
0
Modification events
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\TMX.zip | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6536) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
4
Suspicious files
0
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
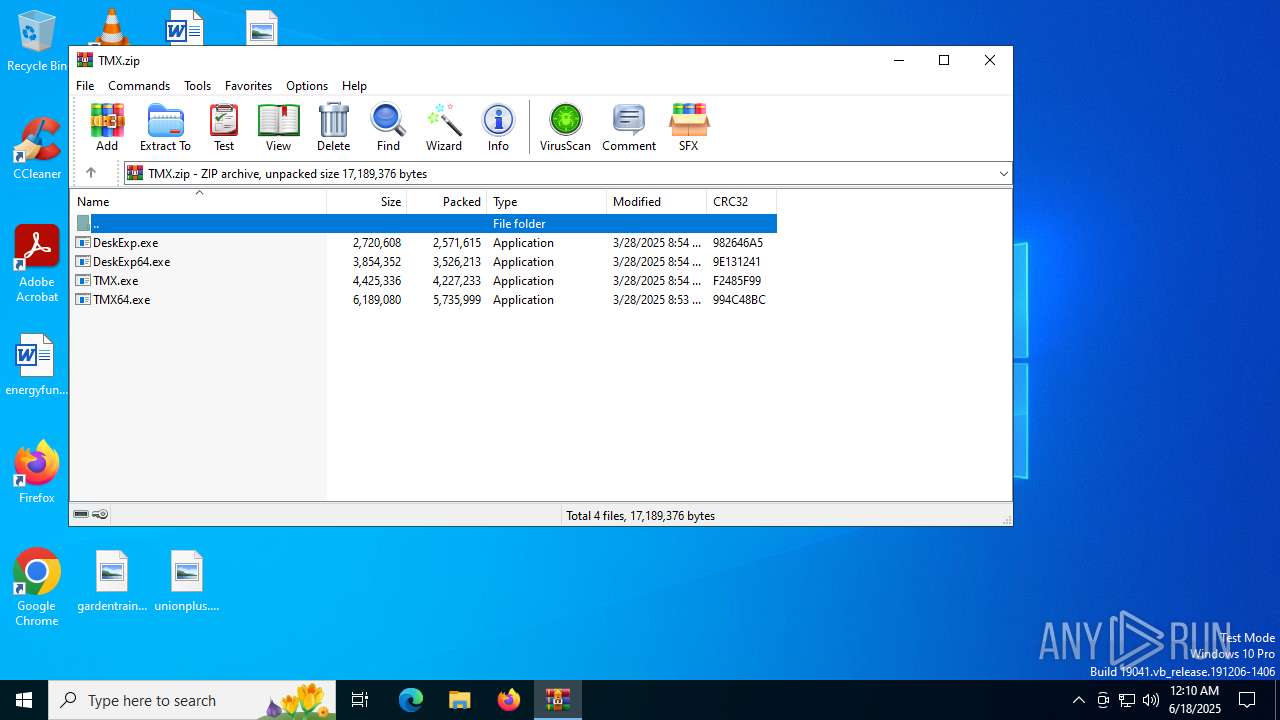
| 6536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6536.24973\TMX.exe | executable | |
MD5:DDEDCCFC95ECDC65A46A58B3D1ABFB57 | SHA256:45C177446DA4AC0CA6E2BC4A87D840FFADFC5B9ABB45733205DF62820EFB9399 | |||
| 6536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6536.24973\DeskExp.exe | executable | |
MD5:C9F2F1E456B7F1BE2036F43D6FCFF94F | SHA256:F4709AE8278798424067C525B36E143D8BA489CC62B48F6A6375903FD3982075 | |||
| 6536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6536.24973\TMX64.exe | executable | |
MD5:A145D6272C90D37CC4DE7CED17D9A03A | SHA256:BFC87A2F695D0D5DDE96918BF57415B1D4A6CDE801FF107C9A9DCFECE32B1786 | |||
| 6536 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa6536.24973\DeskExp64.exe | executable | |
MD5:F827B9B1354A69580CD109B0E1BDDCBA | SHA256:6408F98E8ACC117F061BFC5491540162B30D97495697C47D58A105A3D2D48CB0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
32
DNS requests
28
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4888 | TMX64.exe | GET | — | 142.250.184.228:80 | http://www.google.com/ | unknown | — | — | whitelisted |
4888 | TMX64.exe | GET | — | 142.250.184.228:80 | http://www.google.com/ | unknown | — | — | whitelisted |
4888 | TMX64.exe | GET | — | 142.250.184.228:80 | http://www.google.com/ | unknown | — | — | whitelisted |
4888 | TMX64.exe | GET | — | 142.250.184.228:80 | http://www.google.com/ | unknown | — | — | whitelisted |
3620 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3620 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4888 | TMX64.exe | GET | — | 142.250.184.228:80 | http://www.google.com/ | unknown | — | — | whitelisted |
4888 | TMX64.exe | GET | — | 142.250.184.228:80 | http://www.google.com/ | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
5944 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4832 | RUXIMICS.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4888 | TMX64.exe | 142.250.184.228:80 | www.google.com | GOOGLE | US | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
160.229.35.23.in-addr.arpa |
| unknown |
146.78.124.51.in-addr.arpa |
| unknown |
248.123.211.172.in-addr.arpa |
| unknown |
143.23.48.23.in-addr.arpa |
| unknown |
158.240.127.40.in-addr.arpa |
| unknown |
102.1.168.192.in-addr.arpa |
| unknown |