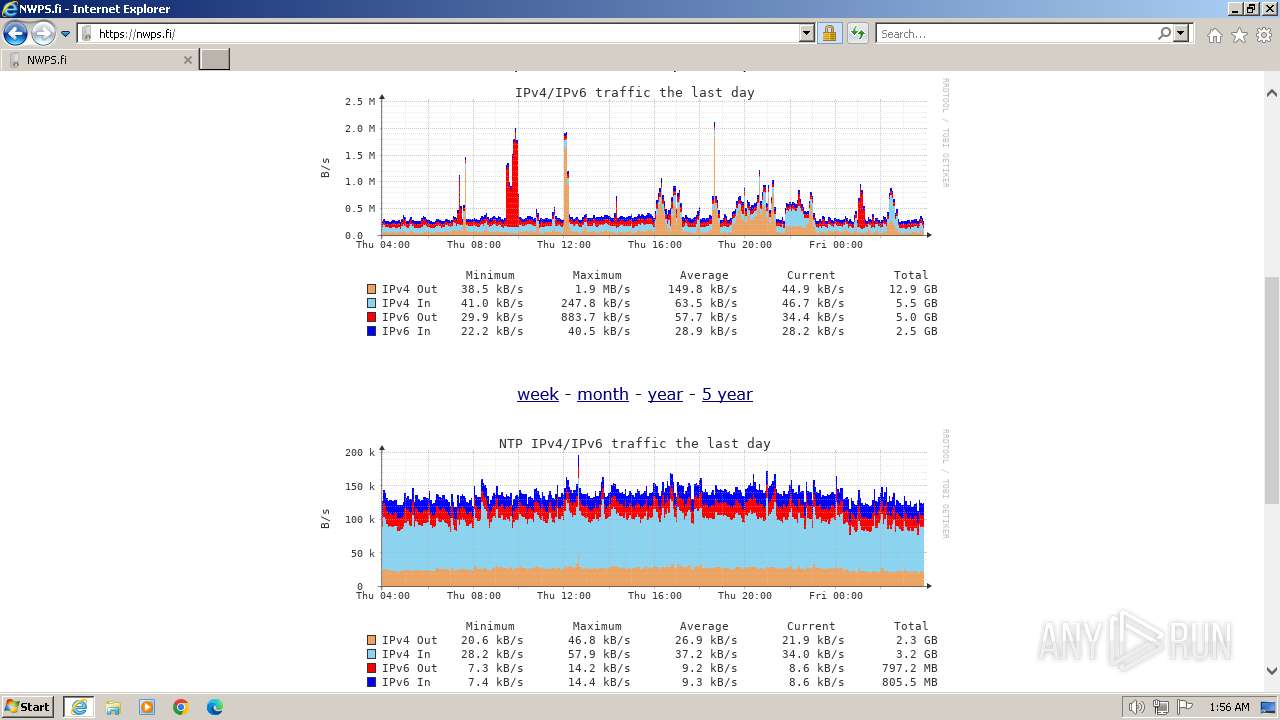
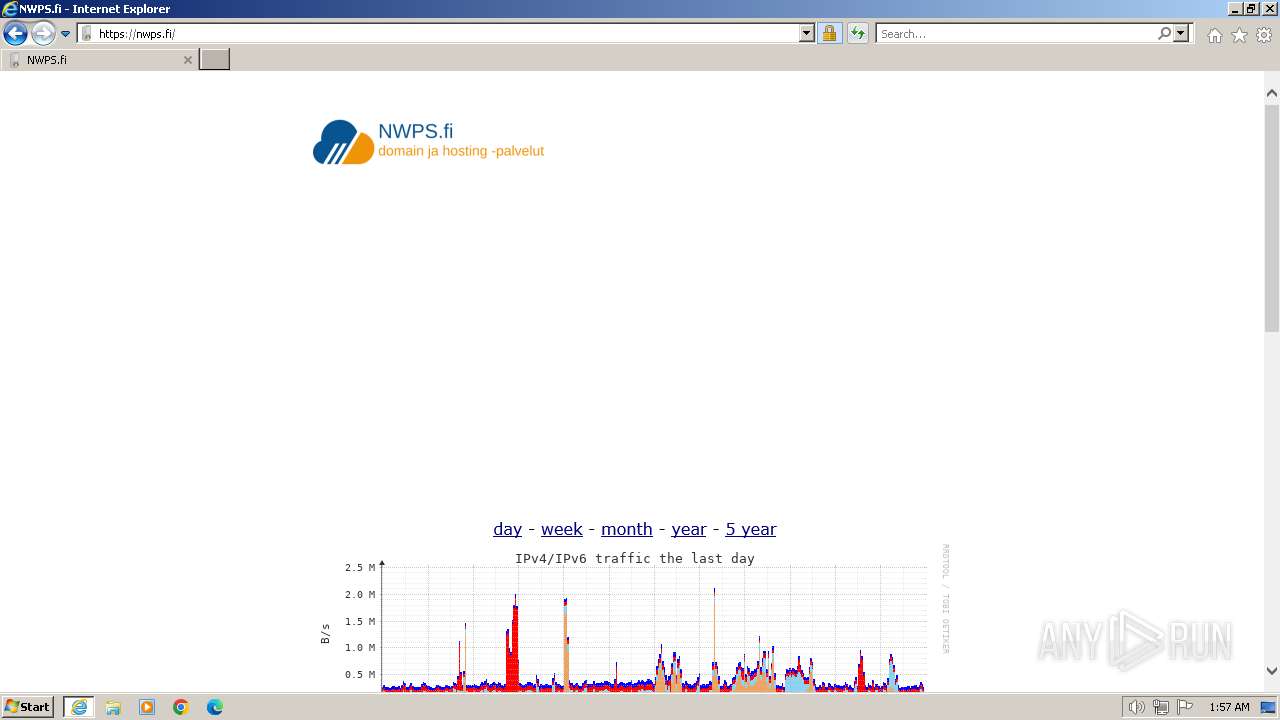
| URL: | sektori.org |
| Full analysis: | https://app.any.run/tasks/8cc86566-1e7a-4bd8-a122-87348b61ed53 |
| Verdict: | Malicious activity |
| Analysis date: | December 29, 2023, 01:56:09 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | E184C53CD8123E3F3C2D74EBC244FAED |
| SHA1: | E284D29188FDB04608D073EA8CE46032C043CB51 |
| SHA256: | 9D1858DE35EB3F12EBECB803E3D4F90FB6E9B688AC707AB6300D0B8B3D64F025 |
| SSDEEP: | 3:VXRXCn:9RXCn |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Application launched itself
- iexplore.exe (PID: 2040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
36
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 392 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2040 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2040 | "C:\Program Files\Internet Explorer\iexplore.exe" "sektori.org" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
20 027
Read events
19 936
Write events
87
Delete events
4
Modification events
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (2040) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
30
Text files
39
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 392 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\BSUQWGDI.htm | html | |
MD5:3D74124C30DDF88FCB44FD96805C51CC | SHA256:7AD96493BADE8ABF96DA2781C99C5F1B7860183E09C6269CE2861497072FE550 | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | der | |
MD5:B64E88A37D675D5609215B9269E015D7 | SHA256:1CBF59E619AC6B648D2D3A5C0CB7B5094B5FBE2E22A7F3097A61D5AA65AF49DB | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | der | |
MD5:AC89A852C2AAA3D389B2D2DD312AD367 | SHA256:0B720E19270C672F9B6E0EC40B468AC49376807DE08A814573FE038779534F45 | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\DOMStore\DOTBATAV\sektori[1].xml | text | |
MD5:C1DDEA3EF6BBEF3E7060A1A9AD89E4C5 | SHA256:B71E4D17274636B97179BA2D97C742735B6510EB54F22893D3A2DAFF2CEB28DB | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\f[1].txt | binary | |
MD5:2B2C9E9E9F5F671D943686F0BD7E9B65 | SHA256:40B7D9702578D10A6C13FF22628960DC63A3615C38F427365CF8E4177A9748EF | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A16C6C16D94F76E0808C087DFC657D99_622063C24DB418AA522B5CFF45000BF1 | binary | |
MD5:83788EAFC476D3365DB1B9AEA329BFB0 | SHA256:6C08533BFA7767E579407C10B9F6B8E4009CBE69F572C4960D71815AF3A60EB5 | |||
| 2040 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\favicon[1].ico | image | |
MD5:B5C4259CD1693AD4947286C427AEB6BB | SHA256:208476F25E9CDD47D9AC355D7395FD5E56E2E3AC584324C6F2003537196C4EB3 | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\f[1].txt | text | |
MD5:3915E76225AD5B114263EAD0ED6DC002 | SHA256:DCD14E42C75BDB80EC5AB264830EF13AB3FE6F549368F20D9C5247F35D0310D6 | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\zrt_lookup[1].htm | html | |
MD5:97FFD112C3D24BE35A61F683B7EADFF0 | SHA256:06A4985DDEEFBD112B1F64B1DB40A32F7A1B22FDDF810AA12AE57EBFACA8FCB3 | |||
| 392 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
42
DNS requests
20
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
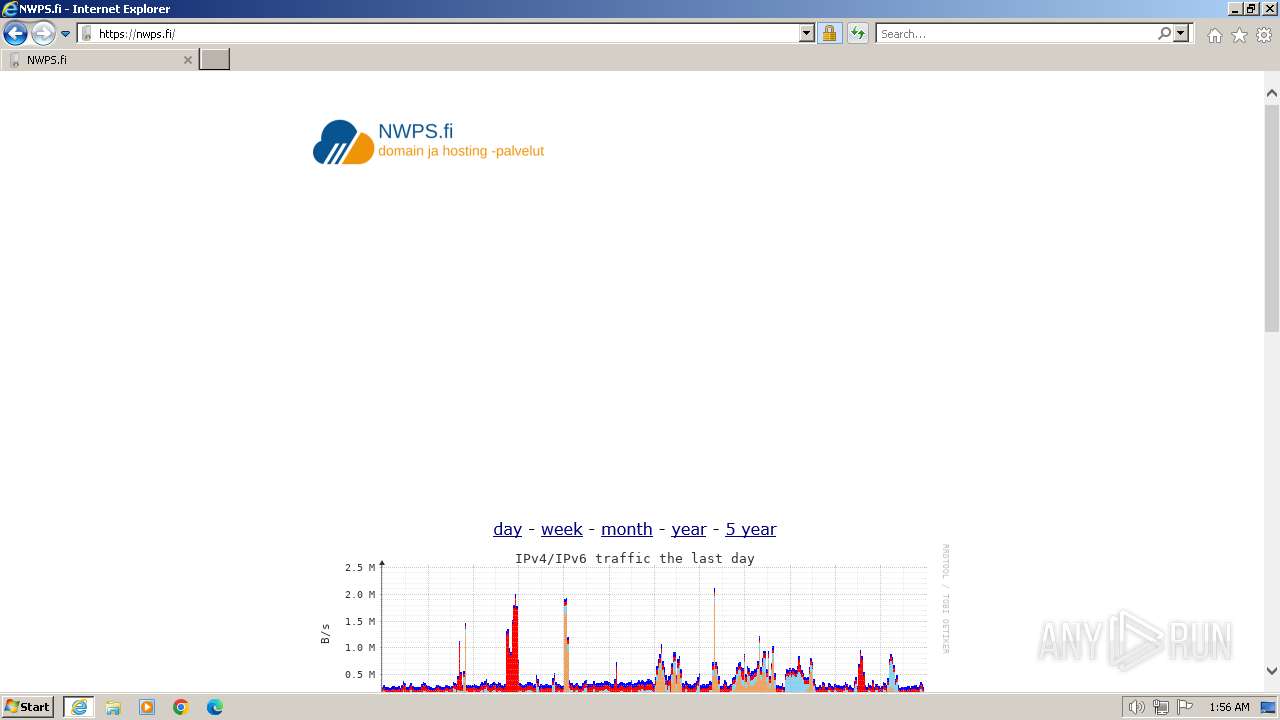
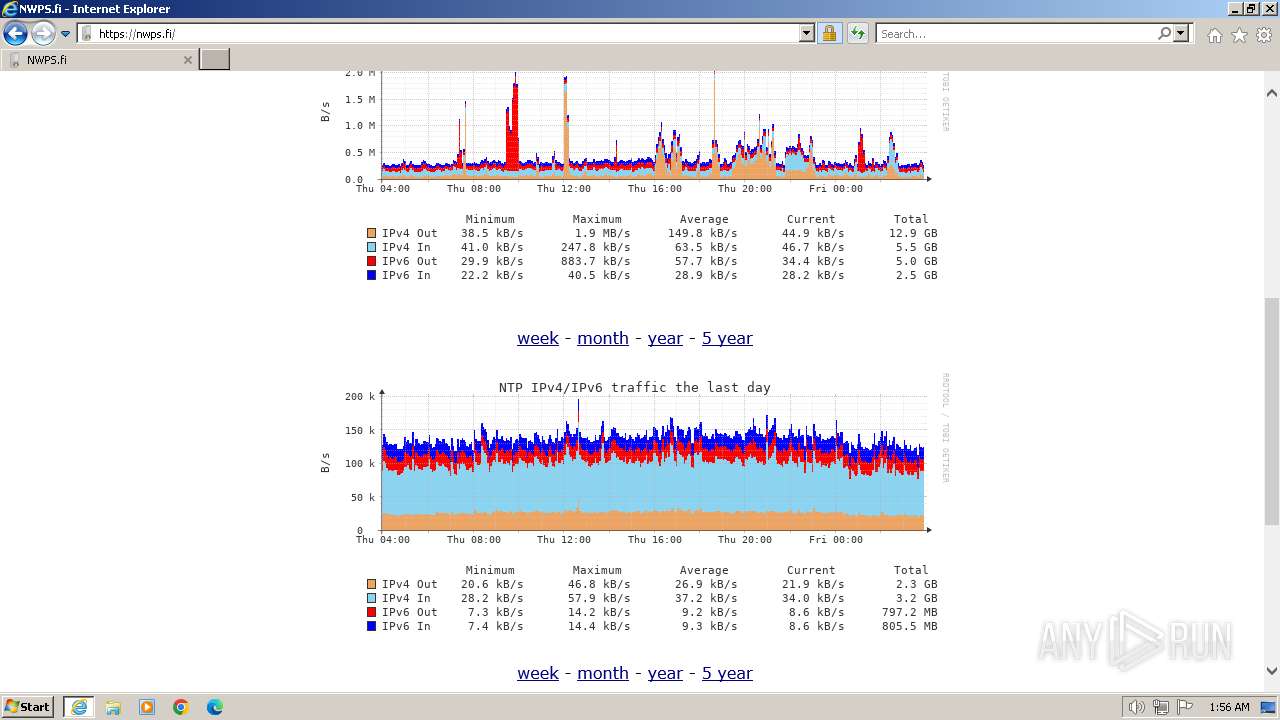
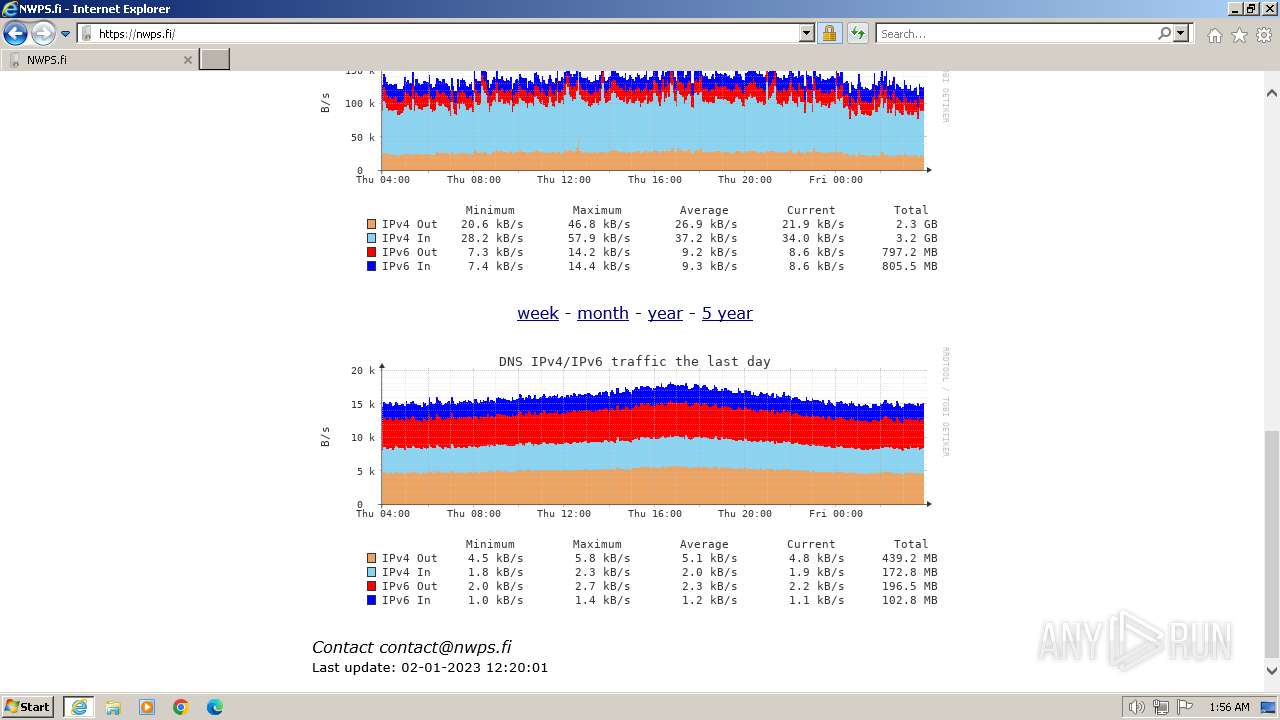
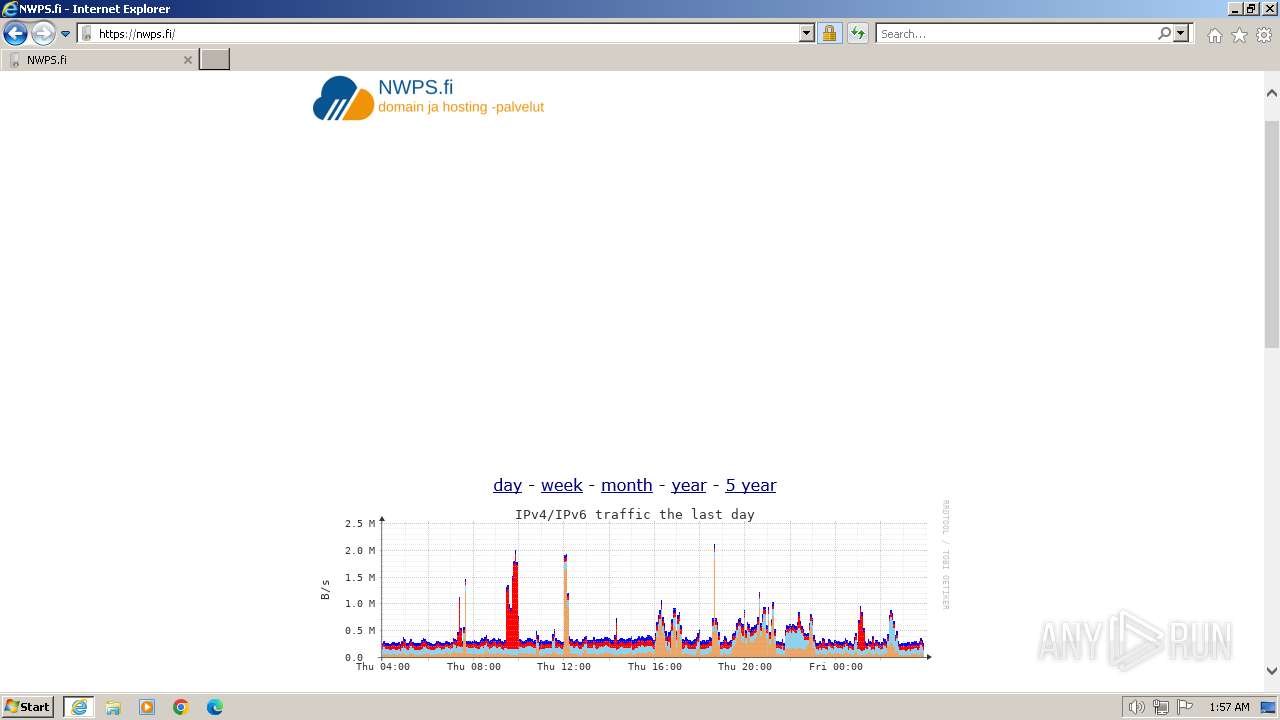
392 | iexplore.exe | GET | 200 | 95.216.138.141:80 | http://sektori.org/ | unknown | html | 260 b | unknown |
392 | iexplore.exe | GET | 200 | 173.222.108.243:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f1ccb56d74be6756 | unknown | compressed | 4.66 Kb | unknown |
392 | iexplore.exe | GET | 200 | 172.217.16.131:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEGupzMnM%2BqGaCjIQPyd58u0%3D | unknown | binary | 471 b | unknown |
2040 | iexplore.exe | GET | 200 | 95.216.138.141:80 | http://sektori.org/favicon.ico | unknown | image | 31.2 Kb | unknown |
392 | iexplore.exe | GET | 200 | 172.217.16.131:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEDEixfO34qnbCeE6N8VMp00%3D | unknown | binary | 471 b | unknown |
392 | iexplore.exe | GET | 200 | 172.217.16.131:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDHvwlxZ6tgTQmj1PR%2BmThA | unknown | binary | 472 b | unknown |
2040 | iexplore.exe | GET | 304 | 173.222.108.243:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?ce83dcf70518f919 | unknown | — | — | unknown |
392 | iexplore.exe | GET | 200 | 173.222.108.243:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?da7d239c2d634b3e | unknown | compressed | 65.2 Kb | unknown |
2040 | iexplore.exe | GET | 304 | 173.222.108.243:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1a6e676fbb64f2cc | unknown | — | — | unknown |
392 | iexplore.exe | GET | 200 | 172.217.16.131:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | unknown | binary | 724 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
392 | iexplore.exe | 95.216.138.141:80 | sektori.org | Hetzner Online GmbH | FI | unknown |
392 | iexplore.exe | 142.250.184.194:443 | pagead2.googlesyndication.com | GOOGLE | US | unknown |
392 | iexplore.exe | 173.222.108.243:80 | ctldl.windowsupdate.com | Akamai International B.V. | CH | unknown |
392 | iexplore.exe | 172.217.16.131:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
392 | iexplore.exe | 142.250.185.130:443 | googleads.g.doubleclick.net | GOOGLE | US | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
2040 | iexplore.exe | 95.216.138.141:80 | sektori.org | Hetzner Online GmbH | FI | unknown |
392 | iexplore.exe | 142.250.185.65:443 | tpc.googlesyndication.com | GOOGLE | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
sektori.org |
| unknown |
pagead2.googlesyndication.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
googleads.g.doubleclick.net |
| whitelisted |
tpc.googlesyndication.com |
| whitelisted |
www.google.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | A Network Trojan was detected | ET MALWARE DNS Query for a known malware domain (sektori.org) |