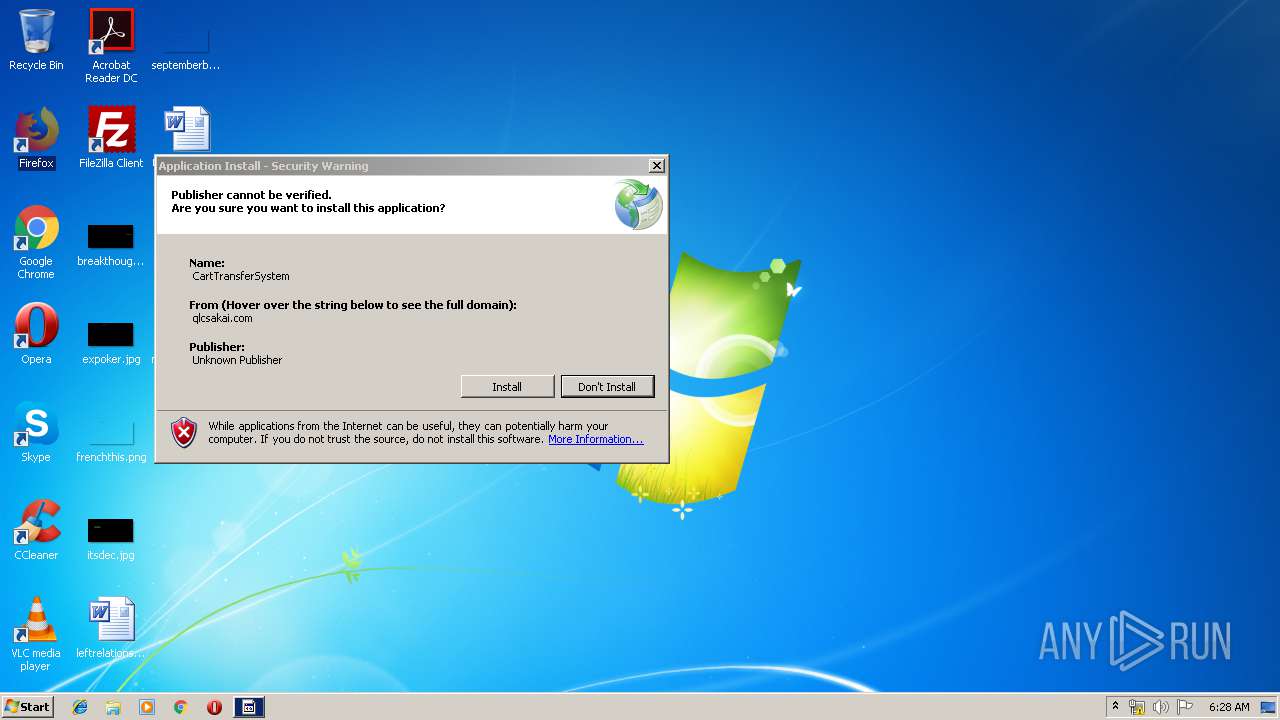
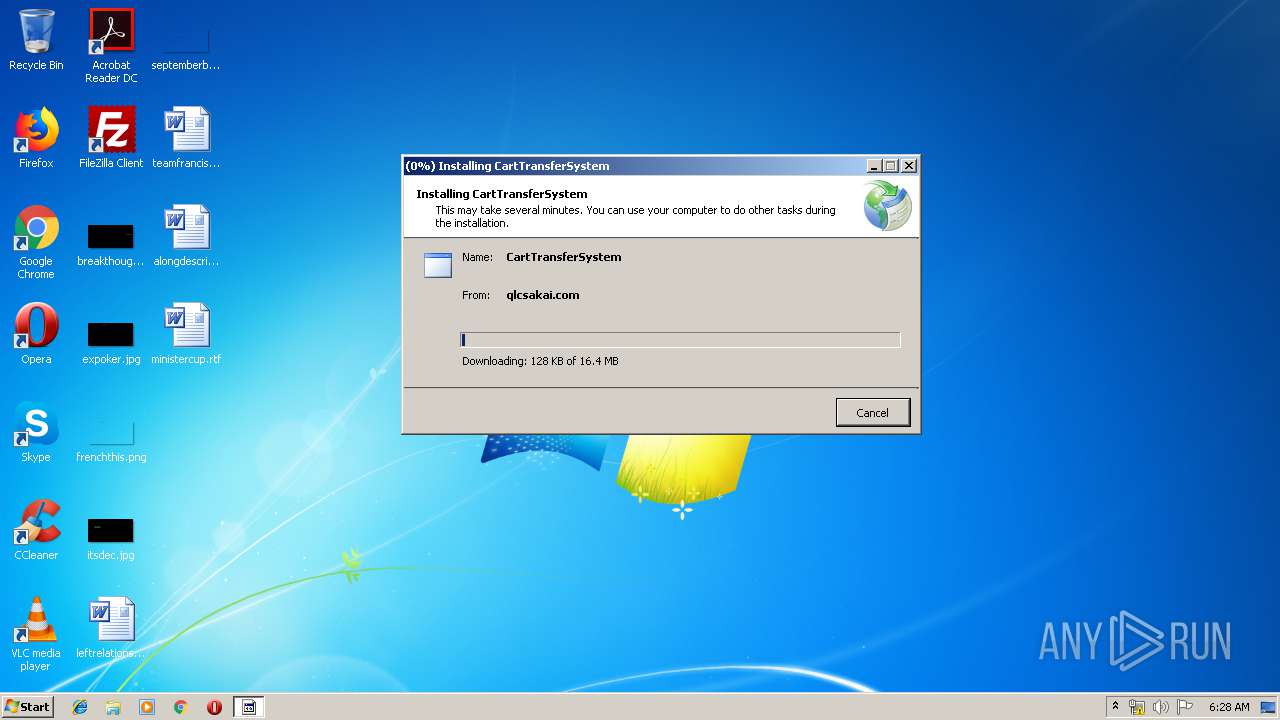
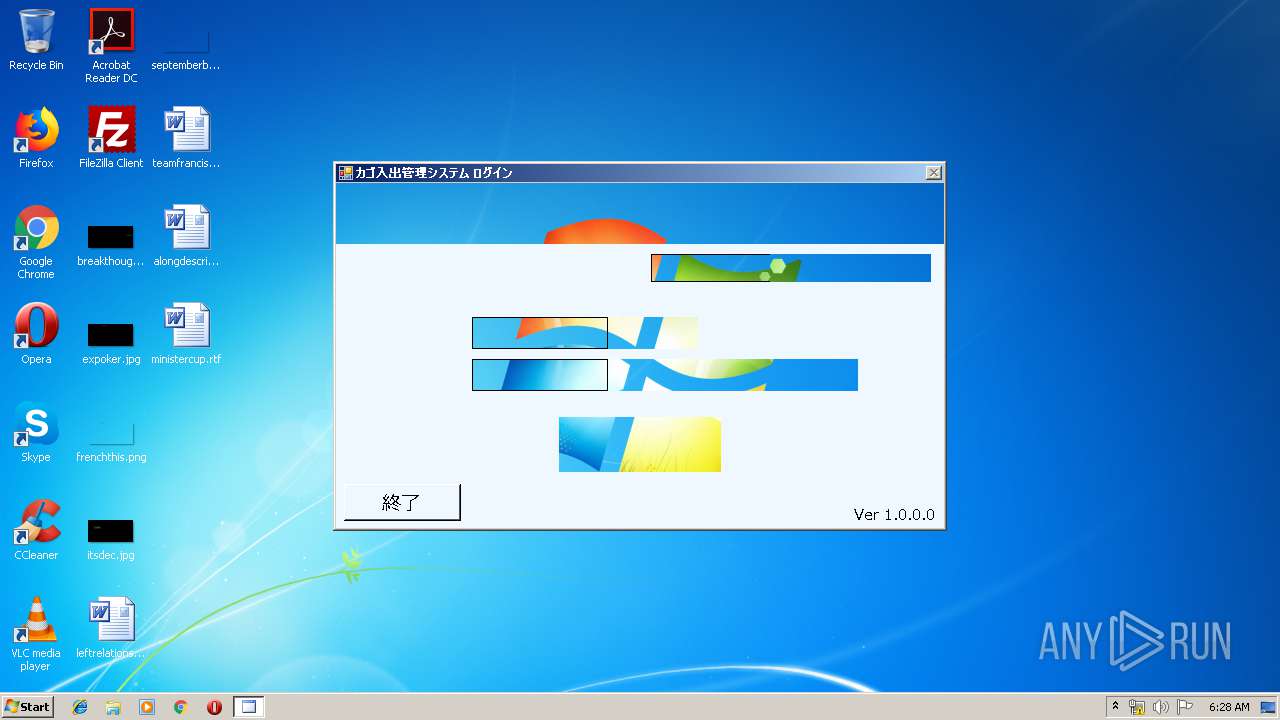
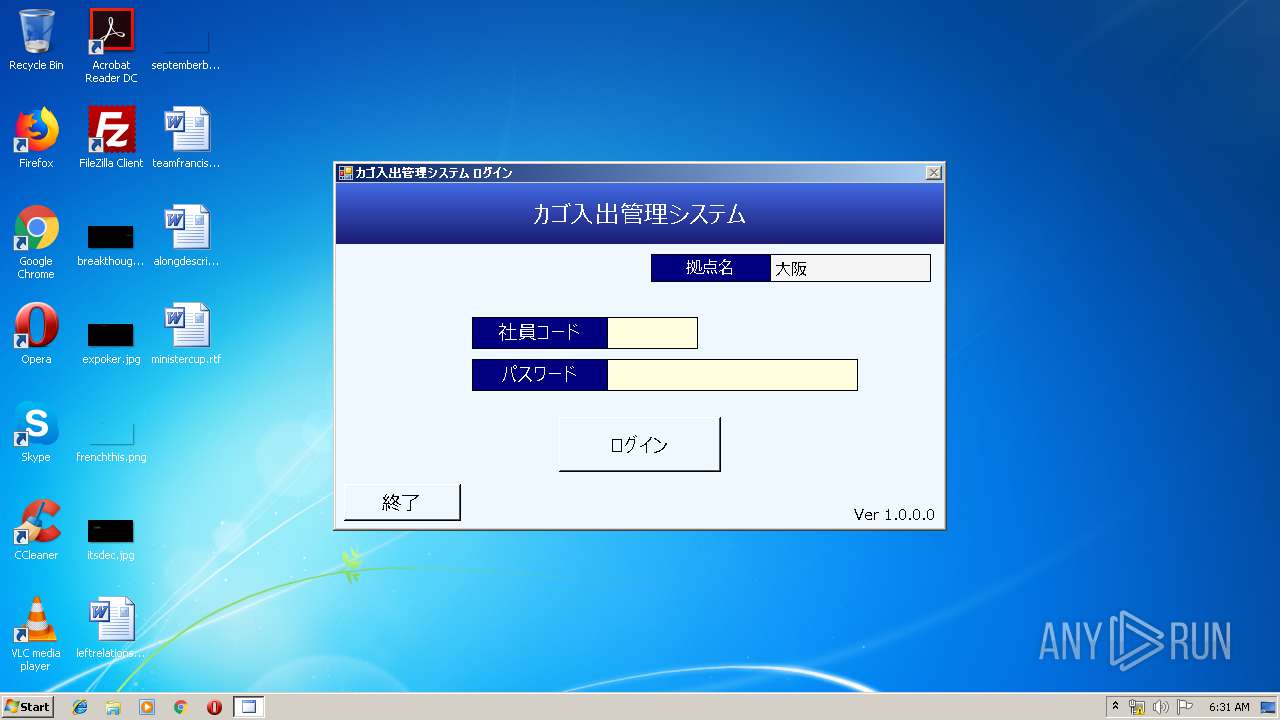
| URL: | https://qlcsakai.com/CartTransferSystem.application |
| Full analysis: | https://app.any.run/tasks/0da5e267-4e38-4320-bfe0-ca4d73b838d9 |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2019, 05:26:46 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | B4EA8FF011E9DDB48A996A6300A14335 |
| SHA1: | B6205F5BBE6CC0D9E1CF53E86CE2ED9BAB30E074 |
| SHA256: | 9D14E2C47FBD1BC4566FAC6008C7D6E55D88BFF9B86079F82E464F403892630A |
| SSDEEP: | 3:N8FmK9uREYE/uMQn:2FmK9oE/M |
MALICIOUS
Loads dropped or rewritten executable
- dfsvc.exe (PID: 2520)
- CartTransferSystem.exe (PID: 3252)
- CartTransferSystem.exe (PID: 4004)
Application was dropped or rewritten from another process
- CartTransferSystem.exe (PID: 3252)
- CartTransferSystem.exe (PID: 4004)
SUSPICIOUS
Reads Internet Cache Settings
- dfsvc.exe (PID: 2520)
Reads Environment values
- dfsvc.exe (PID: 2520)
Executable content was dropped or overwritten
- dfsvc.exe (PID: 2520)
Reads internet explorer settings
- dfsvc.exe (PID: 2520)
Creates files in the user directory
- dfsvc.exe (PID: 2520)
Creates a software uninstall entry
- dfsvc.exe (PID: 2520)
INFO
Changes internet zones settings
- iexplore.exe (PID: 1476)
Creates files in the user directory
- iexplore.exe (PID: 1232)
Application launched itself
- iexplore.exe (PID: 1476)
Reads Internet Cache Settings
- iexplore.exe (PID: 1232)
Reads internet explorer settings
- iexplore.exe (PID: 1232)
Reads settings of System Certificates
- CartTransferSystem.exe (PID: 3252)
- CartTransferSystem.exe (PID: 4004)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
39
Monitored processes
7
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1132 | "rundll32.exe" dfshim.dll,ShOpenVerbShortcut C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Microsoft\CartTransferSystem.appref-ms| | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1232 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1476 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1360 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\dfsvc.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\dfsvc.exe | — | iexplore.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: ClickOnce Exit code: 0 Version: 4.6.1055.0 built by: NETFXREL2 Modules
| |||||||||||||||
| 1476 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2520 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\dfsvc.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\dfsvc.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: ClickOnce Exit code: 0 Version: 4.6.1055.0 built by: NETFXREL2 Modules
| |||||||||||||||
| 3252 | "C:\Users\admin\AppData\Local\Apps\2.0\XTOOJQ5W.DXY\YYNEPNEH.KA2\cart..tion_2bfd6097e931d7c1_0001.0000_68cea65827dbfb73\CartTransferSystem.exe" | C:\Users\admin\AppData\Local\Apps\2.0\XTOOJQ5W.DXY\YYNEPNEH.KA2\cart..tion_2bfd6097e931d7c1_0001.0000_68cea65827dbfb73\CartTransferSystem.exe | dfsvc.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: カゴ入出管理システム Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
| 4004 | "C:\Users\admin\AppData\Local\Apps\2.0\XTOOJQ5W.DXY\YYNEPNEH.KA2\cart..tion_2bfd6097e931d7c1_0001.0000_68cea65827dbfb73\CartTransferSystem.exe" | C:\Users\admin\AppData\Local\Apps\2.0\XTOOJQ5W.DXY\YYNEPNEH.KA2\cart..tion_2bfd6097e931d7c1_0001.0000_68cea65827dbfb73\CartTransferSystem.exe | dfsvc.exe | ||||||||||||
User: admin Company: Microsoft Integrity Level: MEDIUM Description: カゴ入出管理システム Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
1 150
Read events
625
Write events
437
Delete events
88
Modification events
| (PID) Process: | (1476) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1476) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (1476) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (1476) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (1476) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1476) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000071000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1476) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {C41554F9-671A-11E9-A09E-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (1476) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (1476) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 1 | |||
| (PID) Process: | (1476) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E30704000400190005001B0008005001 | |||
Executable files
32
Suspicious files
22
Text files
51
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1476 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 1476 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 1232 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab6637.tmp | — | |
MD5:— | SHA256:— | |||
| 1232 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar6638.tmp | — | |
MD5:— | SHA256:— | |||
| 1232 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab6659.tmp | — | |
MD5:— | SHA256:— | |||
| 1232 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar665A.tmp | — | |
MD5:— | SHA256:— | |||
| 1232 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab6735.tmp | — | |
MD5:— | SHA256:— | |||
| 1232 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar6736.tmp | — | |
MD5:— | SHA256:— | |||
| 1476 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF14797B1BF33F6D2C.TMP | — | |
MD5:— | SHA256:— | |||
| 1476 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{C41554FA-671A-11E9-A09E-5254004A04AF}.dat | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
8
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1232 | iexplore.exe | GET | 200 | 2.16.186.81:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/5F3B8CF2F810B37D78B4CEEC1919C37334B9C774.crt | unknown | der | 891 b | whitelisted |
1232 | iexplore.exe | GET | 200 | 2.16.186.81:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | unknown | compressed | 55.6 Kb | whitelisted |
1476 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1476 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
1232 | iexplore.exe | 153.127.77.53:443 | qlcsakai.com | SAKURA Internet Inc. | JP | unknown |
1232 | iexplore.exe | 2.16.186.81:80 | www.download.windowsupdate.com | Akamai International B.V. | — | whitelisted |
2520 | dfsvc.exe | 153.127.77.53:443 | qlcsakai.com | SAKURA Internet Inc. | JP | unknown |
3252 | CartTransferSystem.exe | 153.127.77.53:443 | qlcsakai.com | SAKURA Internet Inc. | JP | unknown |
4004 | CartTransferSystem.exe | 153.127.77.53:443 | qlcsakai.com | SAKURA Internet Inc. | JP | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
qlcsakai.com |
| unknown |
www.download.windowsupdate.com |
| whitelisted |
Threats
Process | Message |
|---|---|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|
dfsvc.exe |
*** Status originated: -1073741811
*** Source File: d:\iso_whid\x86fre\base\isolation\hier_hierarchy.cpp, line 230
|