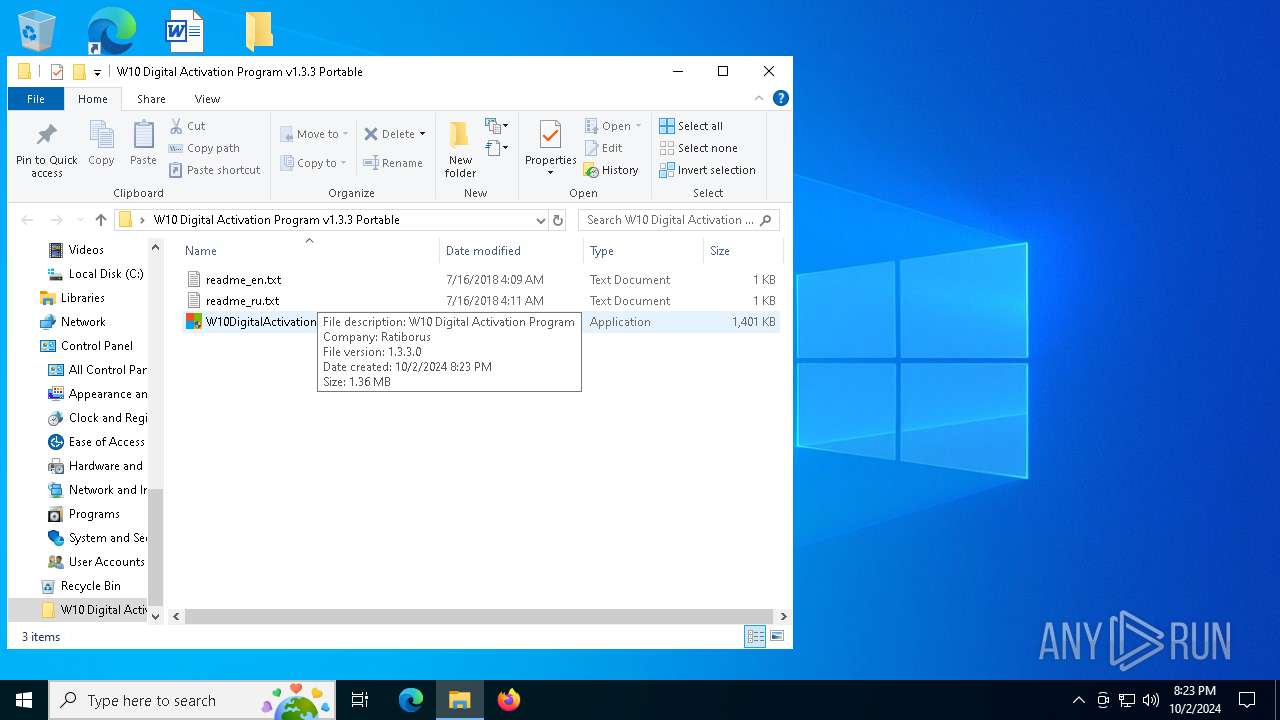
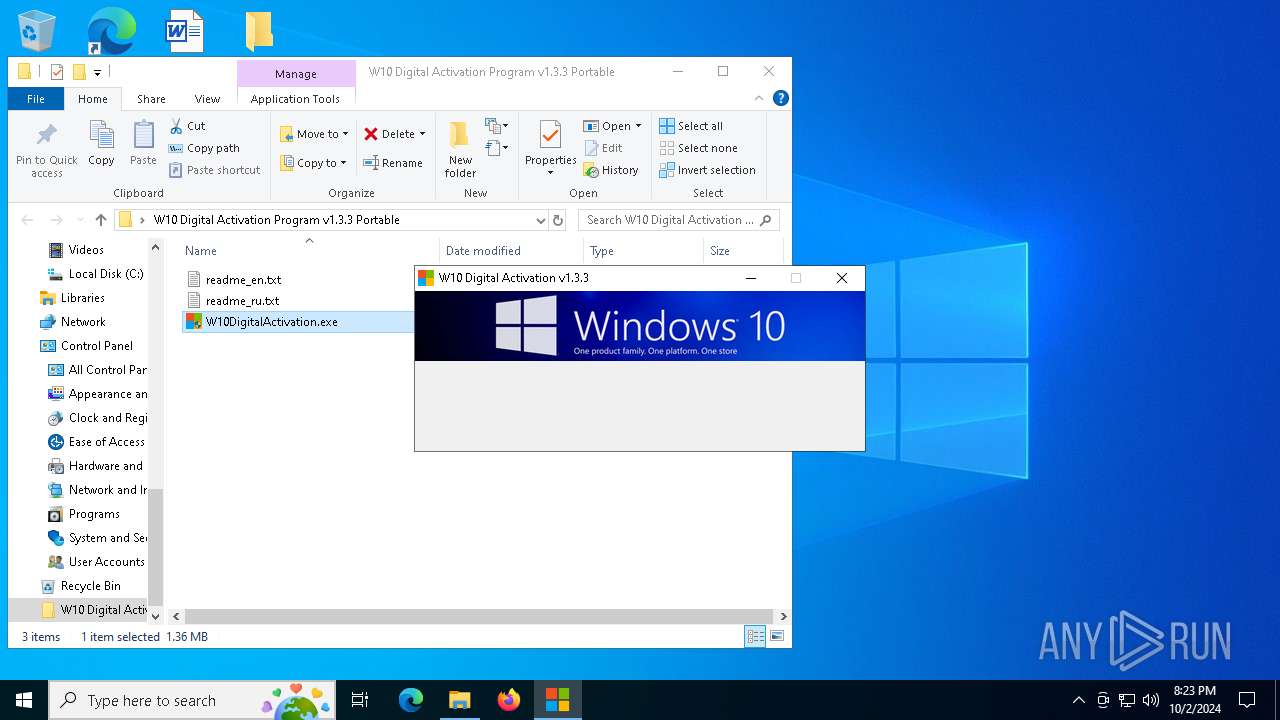
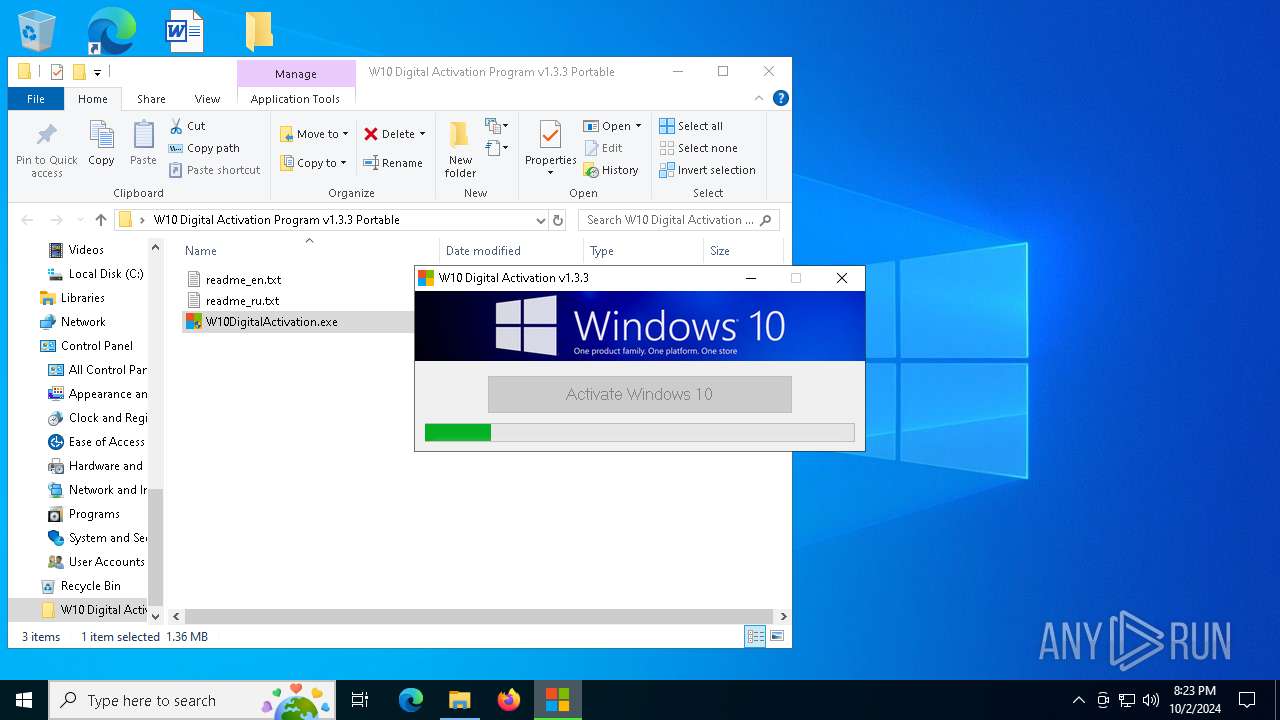
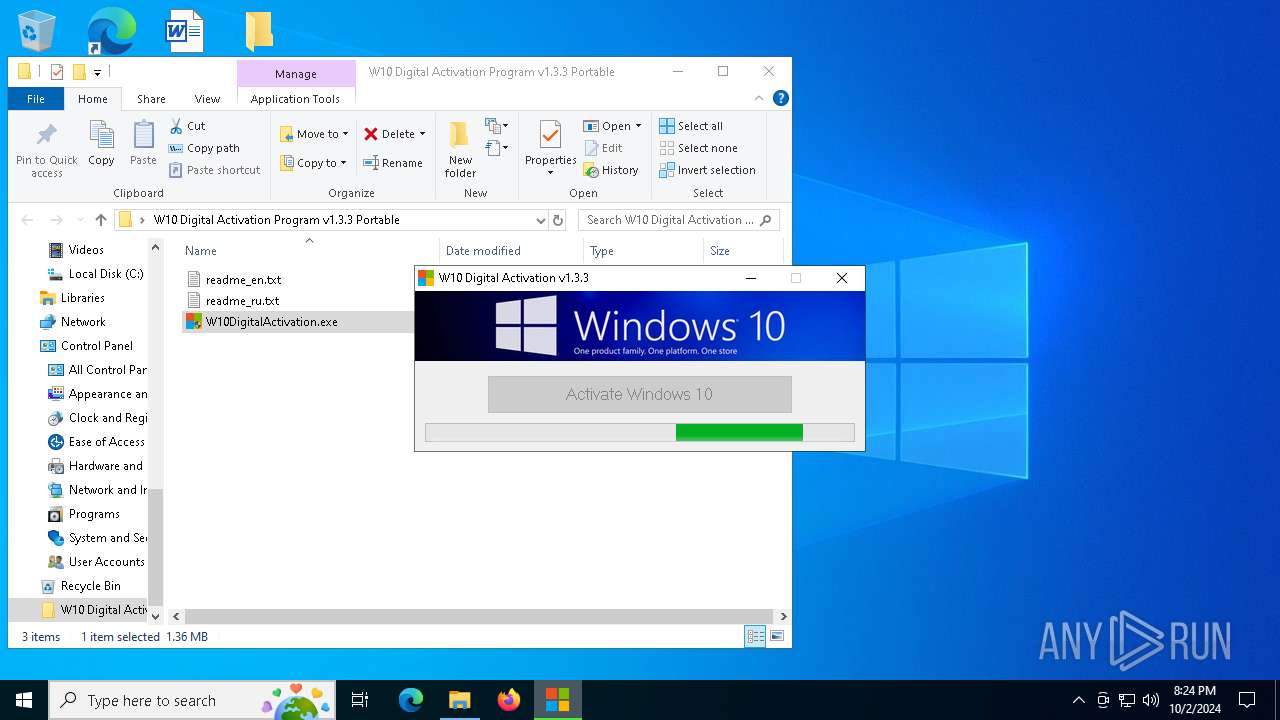
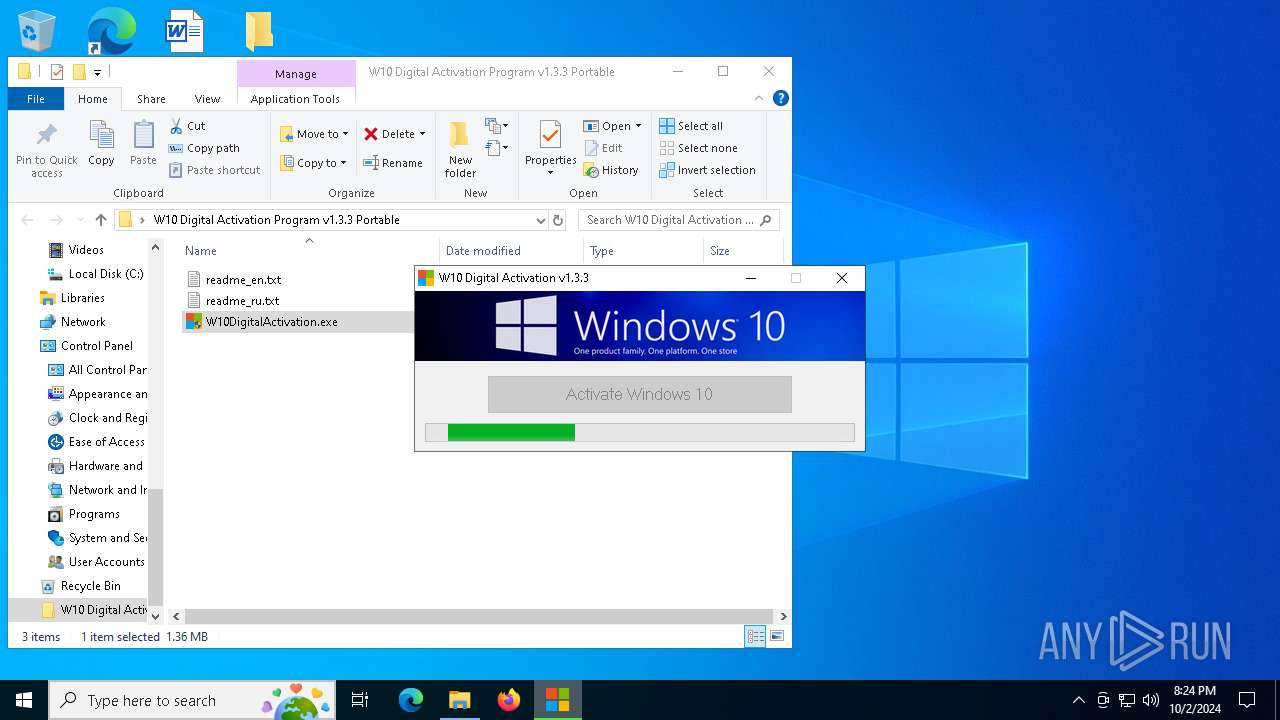
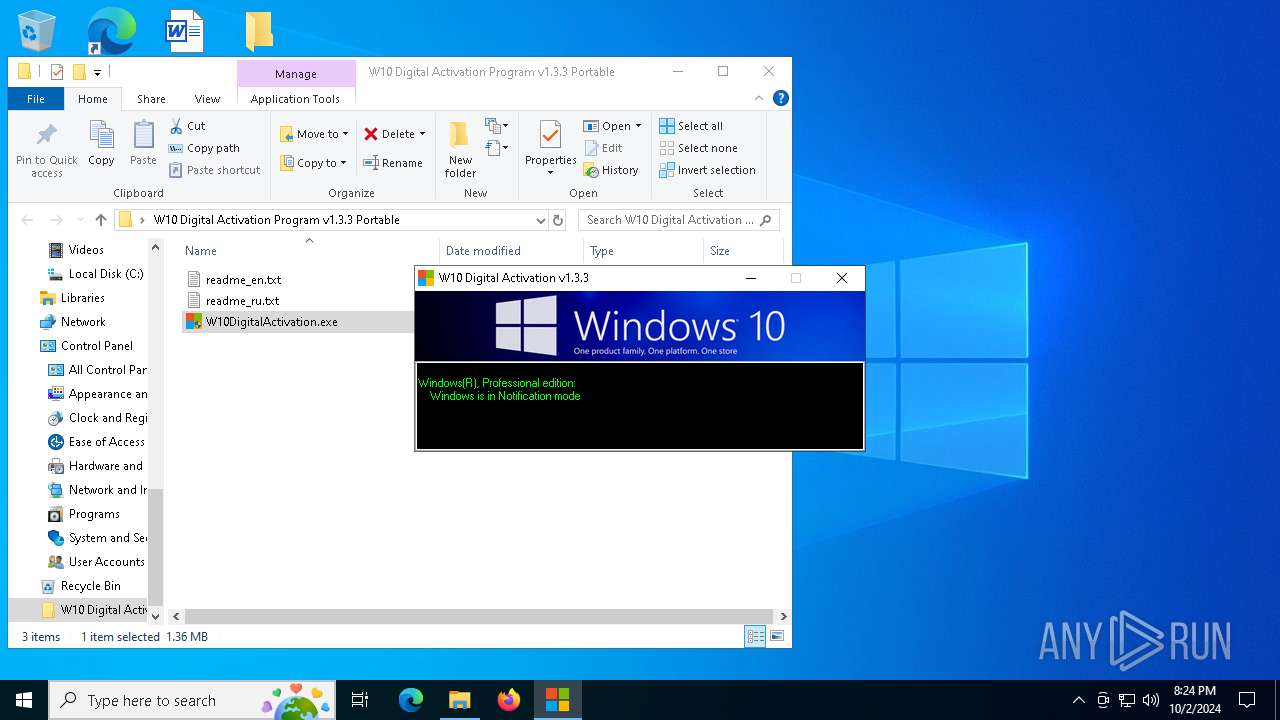
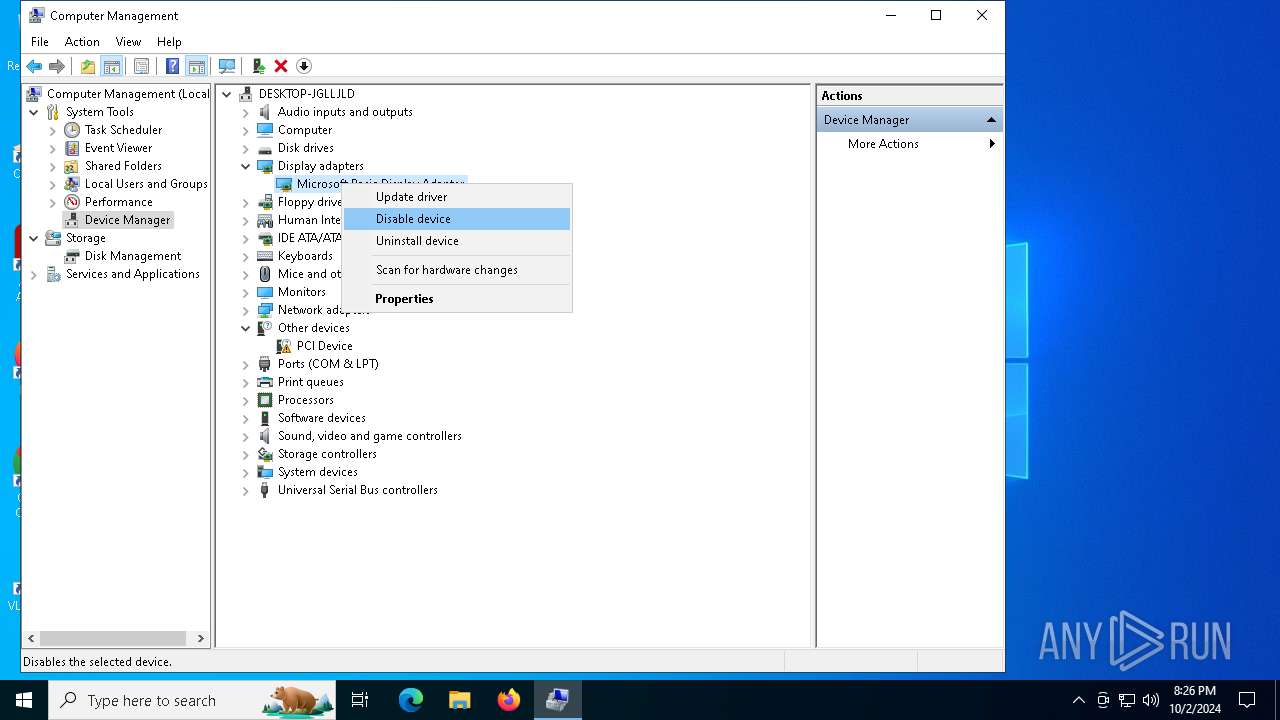
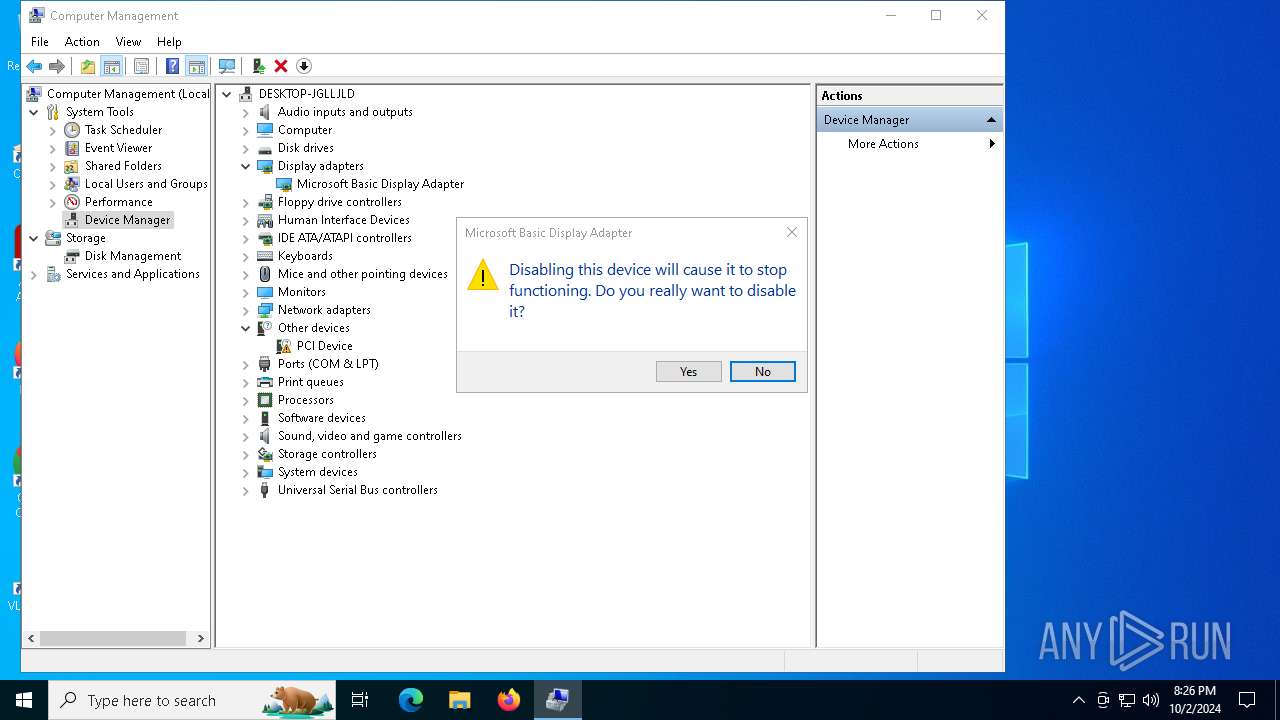
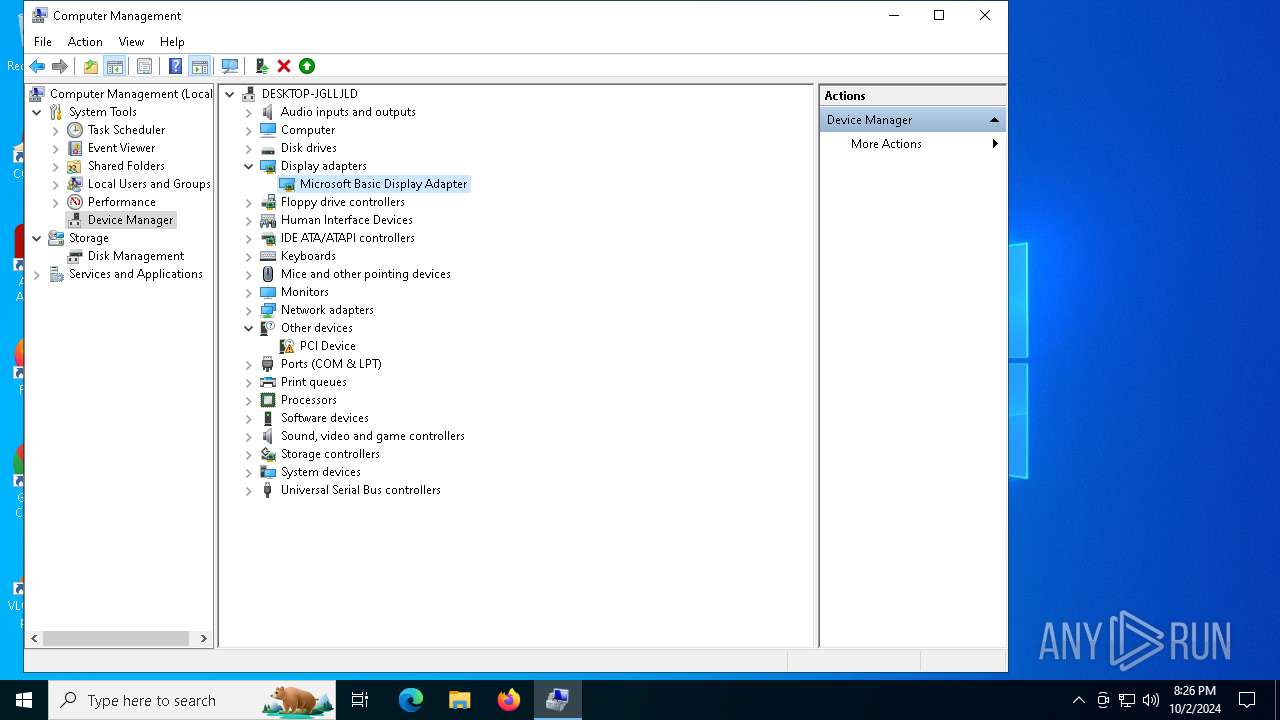
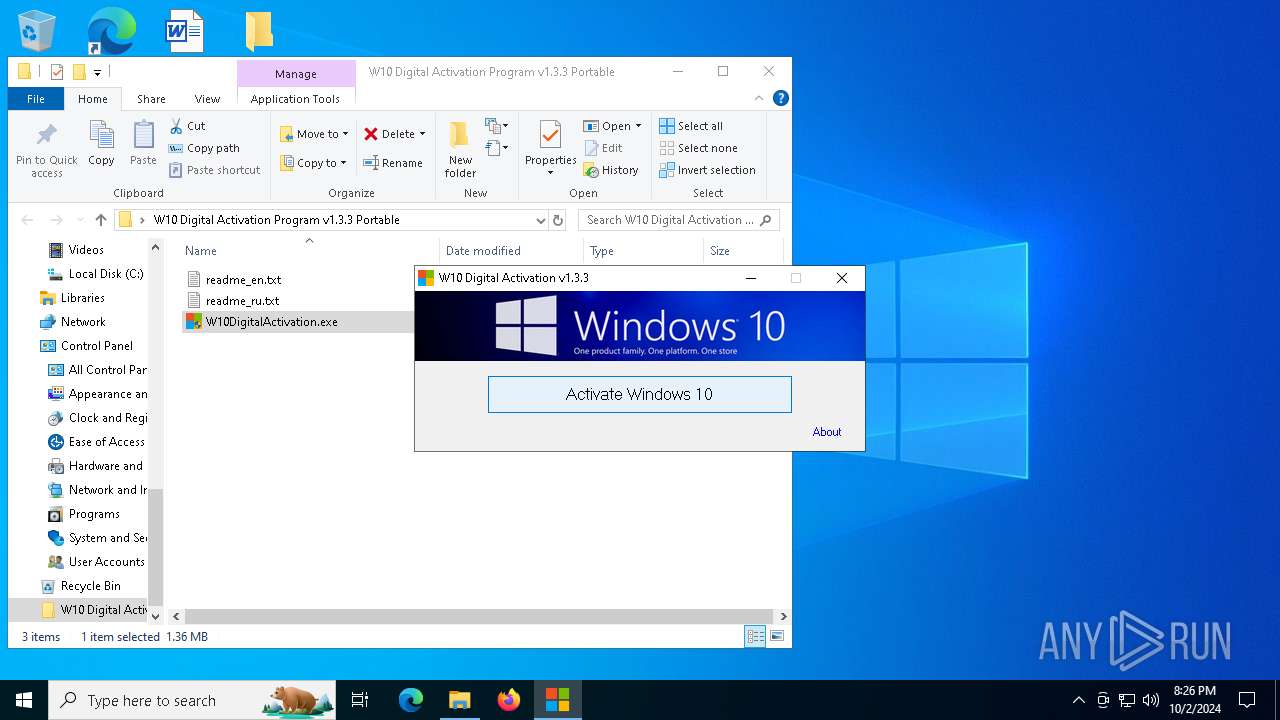
| File name: | W10 Digital Activation Program v1.3.3 Portable.7z |
| Full analysis: | https://app.any.run/tasks/07abe98f-5a8d-4aaa-b8da-701ac0589877 |
| Verdict: | Malicious activity |
| Analysis date: | October 02, 2024, 20:22:59 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.3 |
| MD5: | 78253C1C61CD01C3B821ADCF359F34FF |
| SHA1: | 727AB579C28C1E1AA6794F40929E10685D105562 |
| SHA256: | 9D0A673C999FEF8369E44B649282DC0EFF9D17640A1E619529F2AAA4279EECDD |
| SSDEEP: | 49152:jeQ/kxtvo9tms3pw++TgQe/IusAbFnlko11TDI9s4Hdm3+lRspHyhjPWUxV8hFYB:jTSns5wH9eAusGk+HGsMmOlRspsjPHrL |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process executes VB scripts
- cmd.exe (PID: 3916)
- cmd.exe (PID: 2180)
- cmd.exe (PID: 6644)
- cmd.exe (PID: 68)
- cmd.exe (PID: 368)
- cmd.exe (PID: 5060)
- cmd.exe (PID: 3188)
Process drops legitimate windows executable
- W10DigitalActivation.exe (PID: 1020)
- W10DigitalActivation.exe (PID: 7052)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 4544)
- cmd.exe (PID: 5376)
- cmd.exe (PID: 3180)
- cmd.exe (PID: 6832)
- cmd.exe (PID: 2424)
- cmd.exe (PID: 7112)
- cmd.exe (PID: 32)
Executable content was dropped or overwritten
- W10DigitalActivation.exe (PID: 1020)
- W10DigitalActivation.exe (PID: 7052)
Starts SC.EXE for service management
- cmd.exe (PID: 3860)
- cmd.exe (PID: 1504)
- cmd.exe (PID: 2980)
- cmd.exe (PID: 6308)
- cmd.exe (PID: 4896)
- cmd.exe (PID: 2632)
- cmd.exe (PID: 2912)
- cmd.exe (PID: 5984)
- cmd.exe (PID: 7016)
- cmd.exe (PID: 3588)
- cmd.exe (PID: 3876)
- cmd.exe (PID: 8)
Starts CMD.EXE for commands execution
- W10DigitalActivation.exe (PID: 1020)
- W10DigitalActivation.exe (PID: 7052)
Starts a Microsoft application from unusual location
- gatherosstate.exe (PID: 2932)
- gatherosstate.exe (PID: 7100)
Application launched itself
- ClipUp.exe (PID: 5092)
- ClipUp.exe (PID: 1744)
INFO
Manual execution by a user
- W10DigitalActivation.exe (PID: 1020)
- W10DigitalActivation.exe (PID: 5524)
- W10DigitalActivation.exe (PID: 3028)
- W10DigitalActivation.exe (PID: 7052)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 4276)
UPX packer has been detected
- W10DigitalActivation.exe (PID: 1020)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (gen) (100) |
|---|
Total processes
256
Monitored processes
102
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 8 | "C:\WINDOWS\Sysnative\cmd.exe" /c C:\WINDOWS\System32\sc.exe start wuauserv | C:\Windows\System32\cmd.exe | — | W10DigitalActivation.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 32 | "C:\WINDOWS\Sysnative\cmd.exe" /c reg.exe add "HKEY_LOCAL_MACHINE\SYSTEM\Tokens\Kernel" /f /v "Kernel-ProductInfo" /t REG_DWORD /d 48 | C:\Windows\System32\cmd.exe | — | W10DigitalActivation.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 68 | "C:\WINDOWS\Sysnative\cmd.exe" /c cscript.exe C:\WINDOWS\System32\slmgr.vbs //NoLogo /xpr | C:\Windows\System32\cmd.exe | — | W10DigitalActivation.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 368 | "C:\WINDOWS\Sysnative\cmd.exe" /c cscript.exe C:\WINDOWS\System32\slmgr.vbs //NoLogo /ipk VK7JG-NPHTM-C97JM-9MPGT-3V66T | C:\Windows\System32\cmd.exe | — | W10DigitalActivation.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 660 | reg.exe add "HKEY_LOCAL_MACHINE\SYSTEM\Tokens" /f /v "Channel" /t REG_SZ /d Retail | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 876 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 892 | C:\WINDOWS\System32\sc.exe start licensemanager | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 1056 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1008 | "C:\WINDOWS\Sysnative\cmd.exe" /c C:\WINDOWS\System32\ClipUp.exe -v -o -altto C:\WINDOWS\Temp\BIN\ | C:\Windows\System32\cmd.exe | — | W10DigitalActivation.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1020 | "C:\Users\admin\Desktop\W10 Digital Activation Program v1.3.3 Portable\W10DigitalActivation.exe" | C:\Users\admin\Desktop\W10 Digital Activation Program v1.3.3 Portable\W10DigitalActivation.exe | explorer.exe | ||||||||||||
User: admin Company: Ratiborus Integrity Level: HIGH Description: W10 Digital Activation Program Exit code: 0 Modules
| |||||||||||||||
| 1460 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 287
Read events
5 247
Write events
25
Delete events
15
Modification events
| (PID) Process: | (4276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (4276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\W10 Digital Activation Program v1.3.3 Portable.7z | |||
| (PID) Process: | (4276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (4276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 15 |
Value: | |||
| (PID) Process: | (4276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 14 |
Value: | |||
| (PID) Process: | (4276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 13 |
Value: | |||
| (PID) Process: | (4276) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | delete value | Name: | 12 |
Value: | |||
Executable files
5
Suspicious files
0
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4276 | WinRAR.exe | C:\Users\admin\Desktop\W10 Digital Activation Program v1.3.3 Portable\readme_ru.txt | text | |
MD5:58E55C4587FBC759665B134768B18DB1 | SHA256:8DA72B4220EFCB3312FC1E7BFEF666CFB069A702B6539C447D3F82312010F794 | |||
| 4276 | WinRAR.exe | C:\Users\admin\Desktop\W10 Digital Activation Program v1.3.3 Portable\W10DigitalActivation.exe | executable | |
MD5:75D55F4A935F45A521D1EE4EEABAB829 | SHA256:FF568AFFF784F2F8E6F76E8E0F8E2E8746317DEC4FCA0E941561B498EA22D4B3 | |||
| 1020 | W10DigitalActivation.exe | C:\Windows\Temp\BIN\gatherosstate.exe | executable | |
MD5:B13BC5B62F54607C334A6464D9B85CC8 | SHA256:51791625054B01802FD5AAA6C4A929827B369DFEF7B2891B5F55E0FA61AF0C7D | |||
| 1020 | W10DigitalActivation.exe | C:\Windows\Temp\BIN\slc.dll | executable | |
MD5:E2840606372AB67B7107CE757D506C28 | SHA256:37E20A504ADE965184D92ED5CA415CDE899090A6A20EA3ABF8C85FF9648B66F4 | |||
| 2300 | ClipUp.exe | C:\ProgramData\Microsoft\Windows\ClipSVC\Install\Migration\94ee03b2-4984-4b4e-a028-d6da9ecb3525.xml | text | |
MD5:85968406F5F6A5678D5C792518362DBC | SHA256:A89C7722A75368D4E9D8D80BEE1F925161A6E363C8CC4159F5E3F3FFCD423766 | |||
| 4276 | WinRAR.exe | C:\Users\admin\Desktop\W10 Digital Activation Program v1.3.3 Portable\readme_en.txt | text | |
MD5:E76FB6DDA71F6F7900F42BAF5CBB58F7 | SHA256:84D214B314F28A733401957401277217452C5407F0500D460ECA867A1C581C2B | |||
| 7100 | gatherosstate.exe | C:\Windows\Temp\BIN\GenuineTicket.xml | xml | |
MD5:A55D9F9AFB5A569B5D684AD1BD910858 | SHA256:ECB50BD9E53790E35A25D68BC774F2CCCCE28CF8DD74F68964425C9A4B878206 | |||
| 7052 | W10DigitalActivation.exe | C:\Windows\Temp\BIN\slc.dll | executable | |
MD5:E2840606372AB67B7107CE757D506C28 | SHA256:37E20A504ADE965184D92ED5CA415CDE899090A6A20EA3ABF8C85FF9648B66F4 | |||
| 2628 | ClipUp.exe | C:\Users\admin\AppData\Local\Temp\tem78B9.tmp | text | |
MD5:2E6B91EAC3ACDC84F0F35300929369E6 | SHA256:34725A4EB12DCD8C012CBFD885E96AB6CAD7F8BC04615F3D829E8A1DA1102DBD | |||
| 2628 | ClipUp.exe | C:\ProgramData\Microsoft\Windows\ClipSVC\Install\Migration\36e9e5b5-e5e5-4d03-9532-8bec17efa6c8.xml | text | |
MD5:9FDA611465BB1E56EB3580B2162DBB3A | SHA256:71001564DDC28069BB0262AE9311F0C0769FE59CCDDB83F56558D35F7B3B6DFF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
84
DNS requests
29
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4344 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2572 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1448 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6956 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
4344 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5336 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1448 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2572 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 23.35.238.131:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 40.113.103.199:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2572 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
browser.pipe.aria.microsoft.com |
| whitelisted |