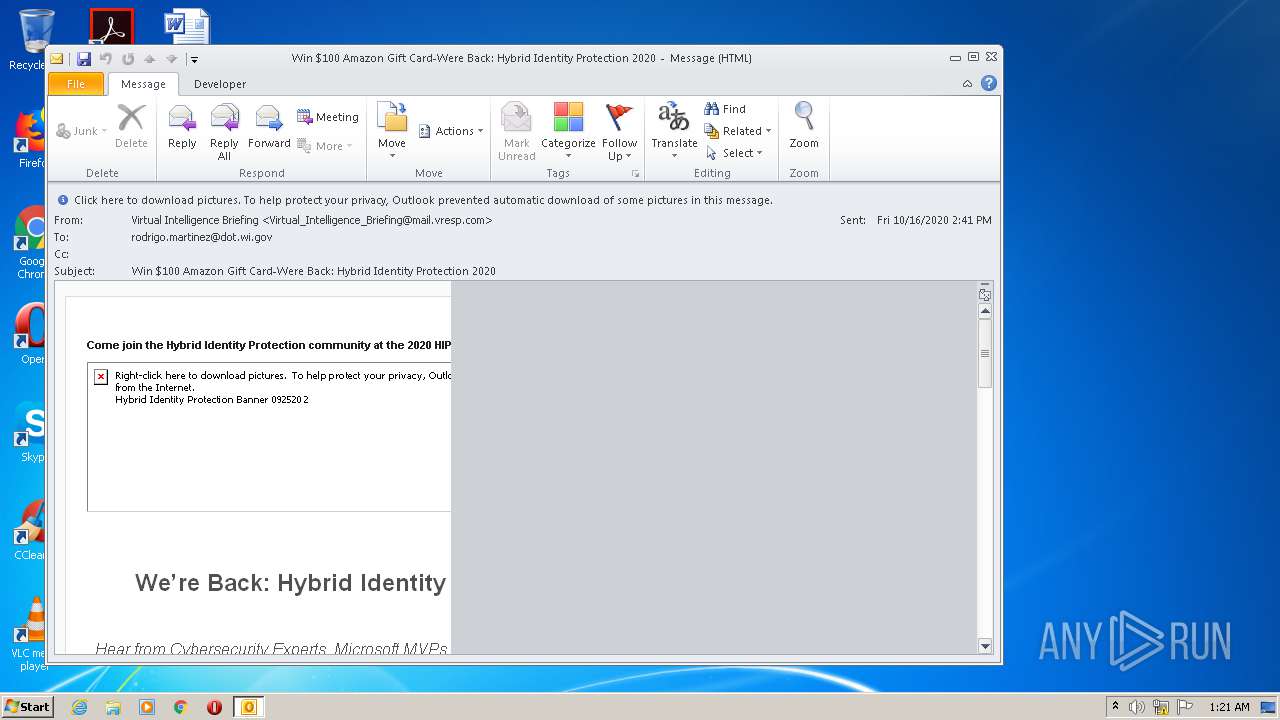
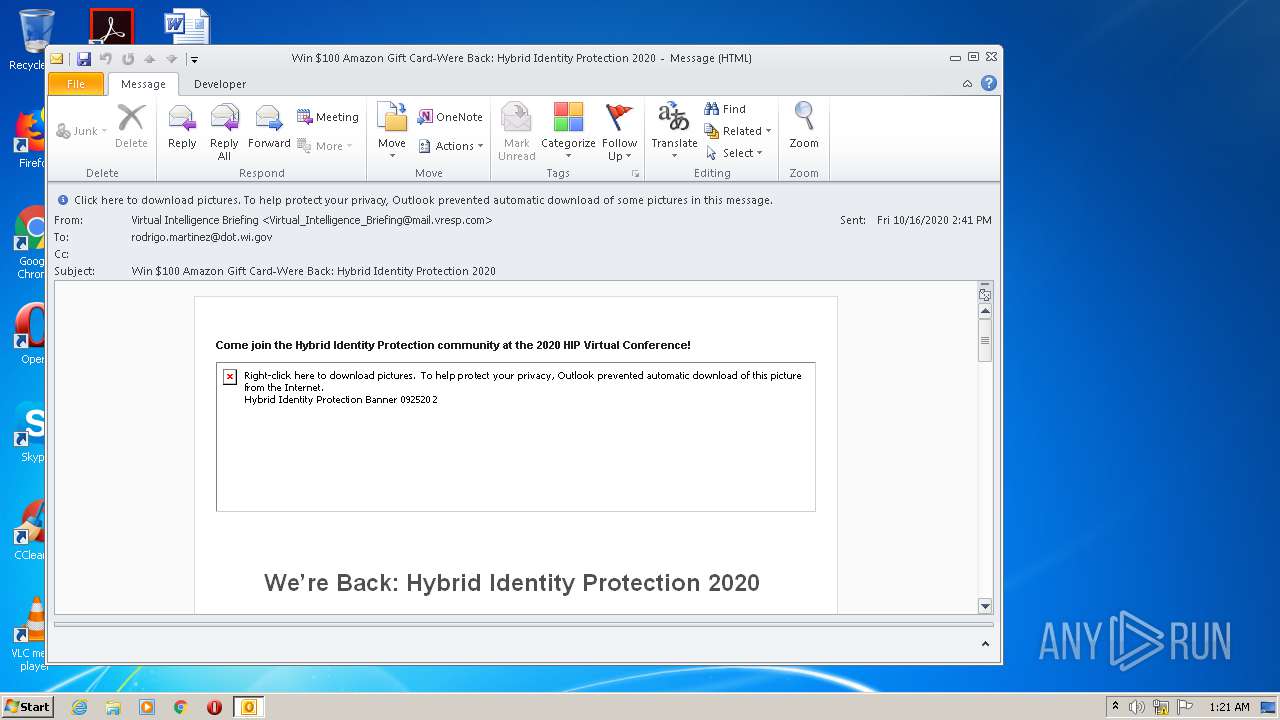
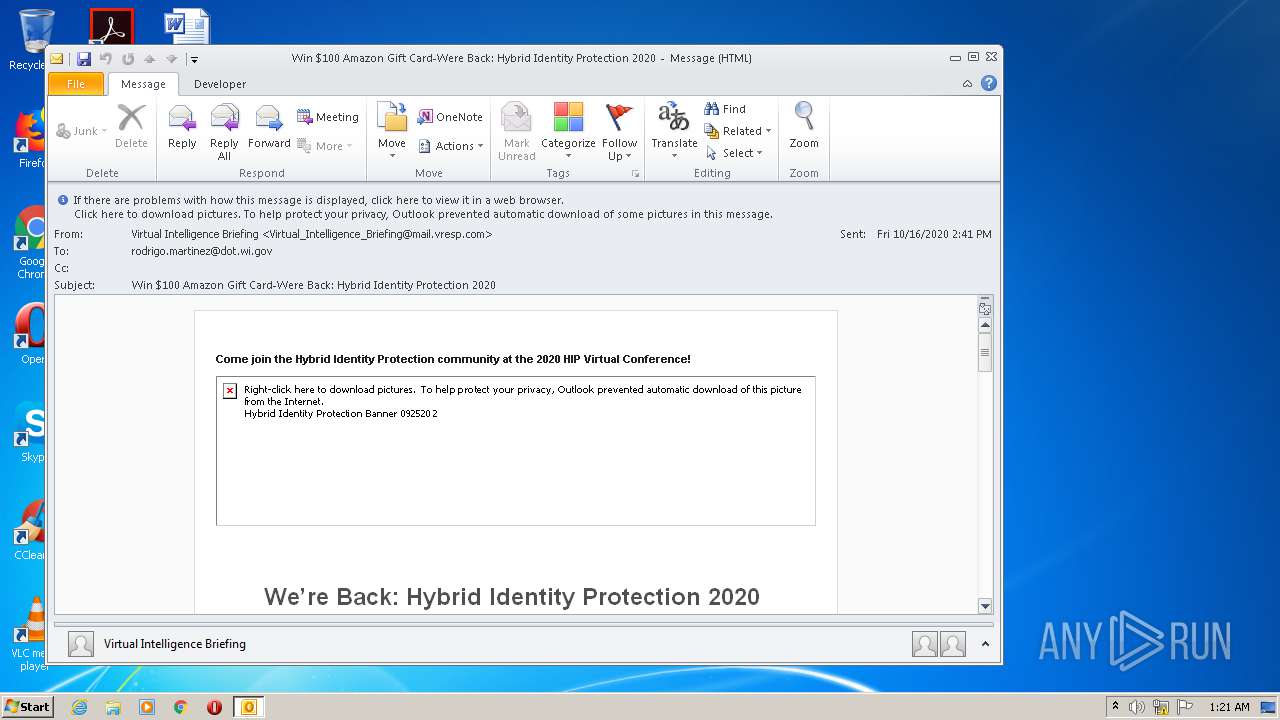
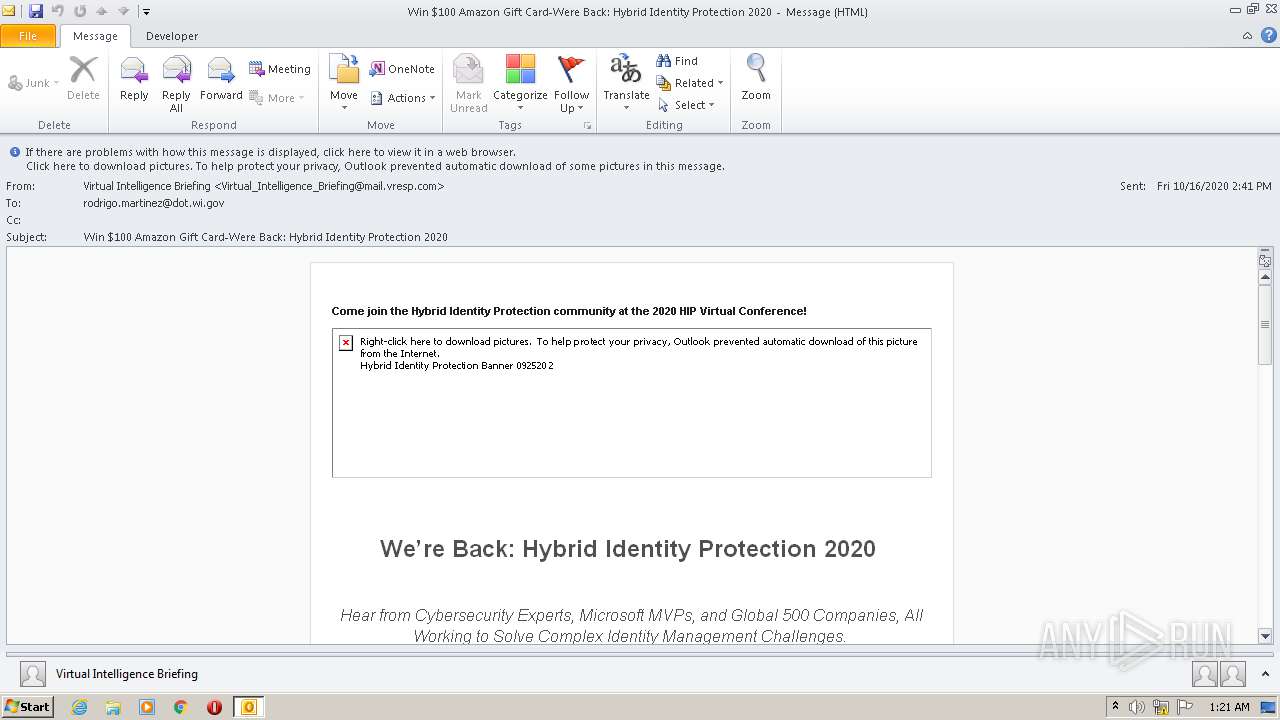
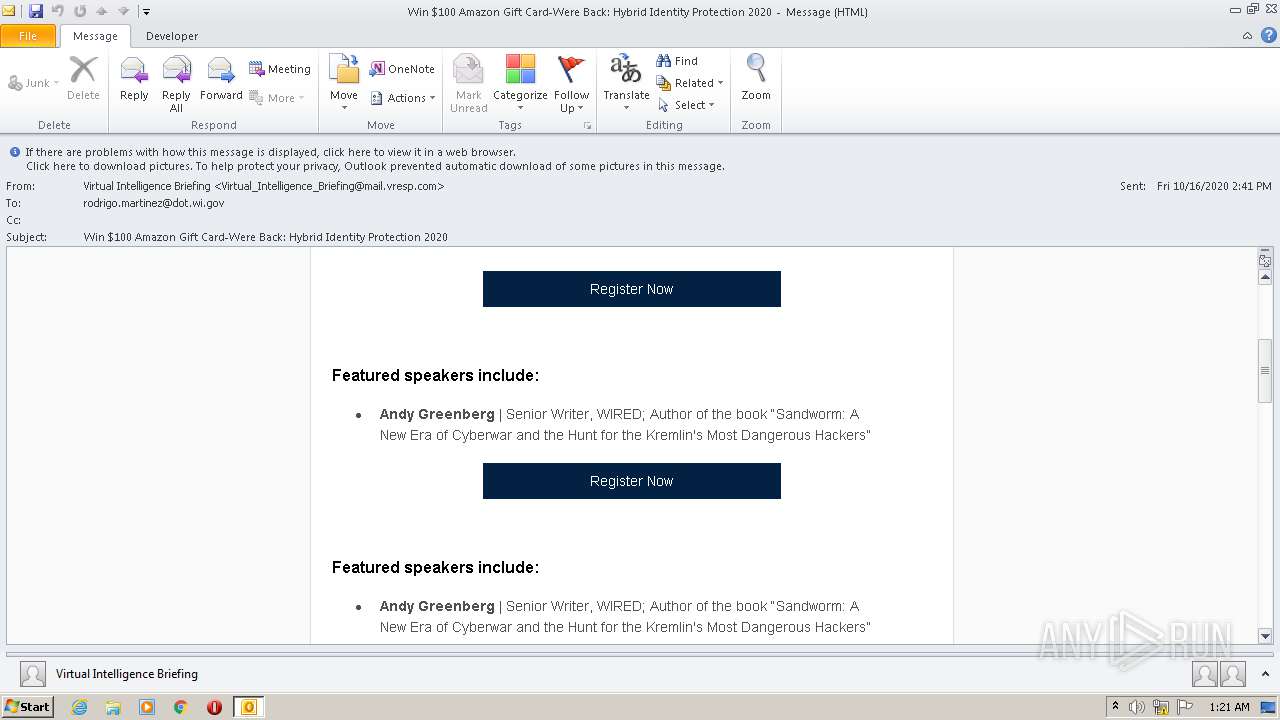
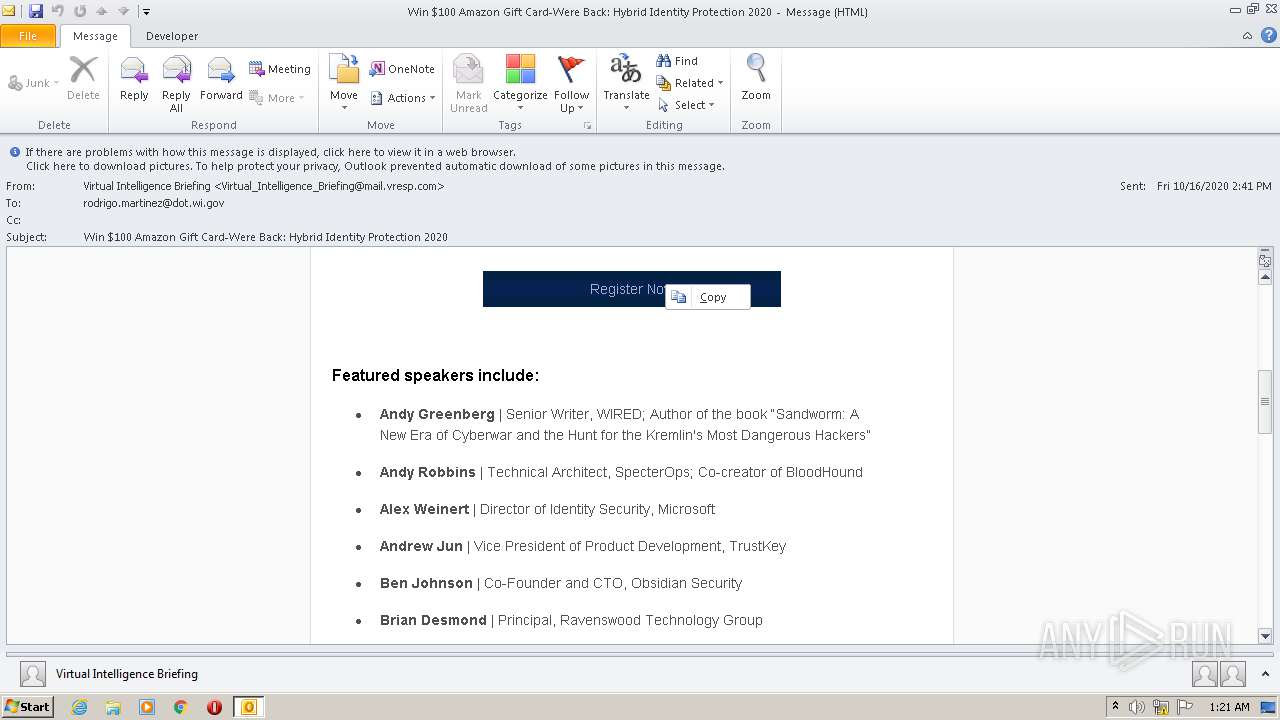
| File name: | Win $100 Amazon Gift Card-Were Back Hybrid Identity Protection 2020.msg |
| Full analysis: | https://app.any.run/tasks/f4573485-f661-4056-a718-8a00e71ea3dc |
| Verdict: | Malicious activity |
| Analysis date: | October 20, 2020, 00:21:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | CC578532D0B7C65FE840F38C065C2072 |
| SHA1: | FBD2ED1FEFAEB1F3920F929ABBC2E272D52BE431 |
| SHA256: | 9D080575833A4468A2C1190BF7EC8F9597CB9177210AB685534918863F49DD91 |
| SSDEEP: | 3072:VF9XVu2Xf3xPDkJtxtLp+LyobpvdXsnYbJ1:VFe2Xf3xrkJf7iycpv9s |
MALICIOUS
Unusual execution from Microsoft Office
- OUTLOOK.EXE (PID: 2064)
SUSPICIOUS
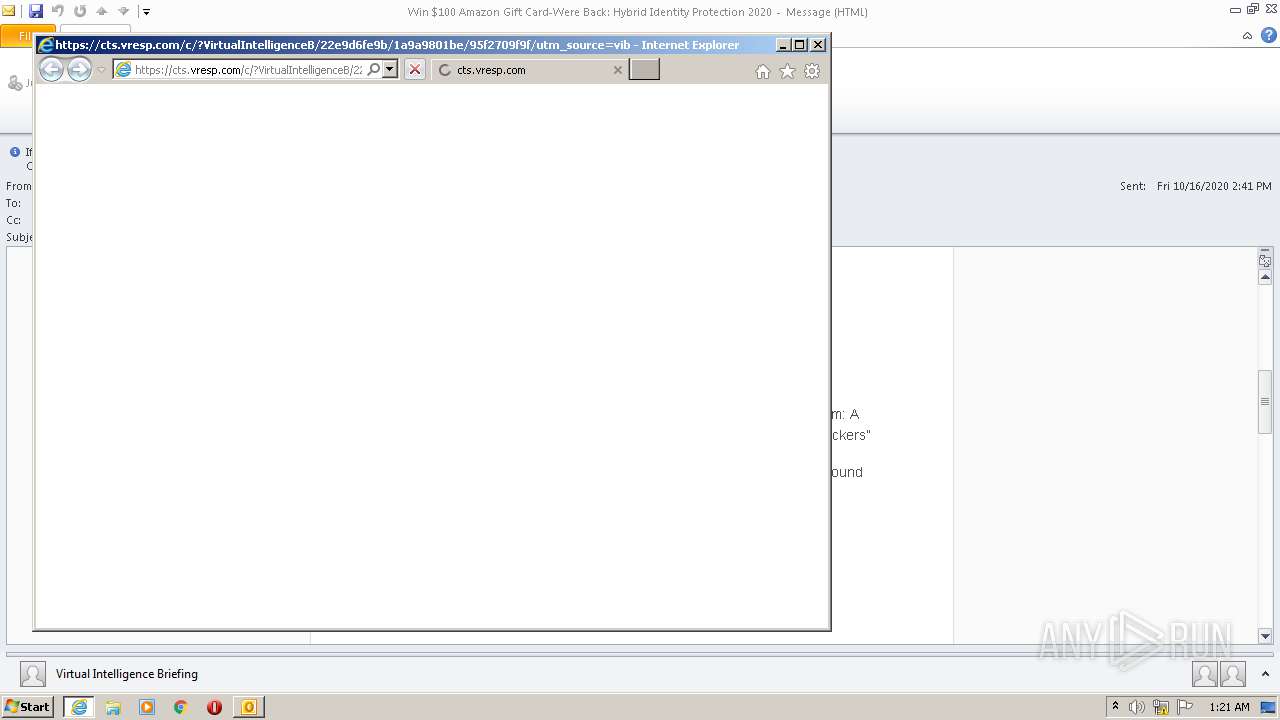
Starts Internet Explorer
- OUTLOOK.EXE (PID: 2064)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2064)
Creates files in the user directory
- OUTLOOK.EXE (PID: 2064)
- iexplore.exe (PID: 4064)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 2064)
- iexplore.exe (PID: 2356)
- iexplore.exe (PID: 4064)
Application launched itself
- iexplore.exe (PID: 2356)
- chrome.exe (PID: 4044)
Changes internet zones settings
- iexplore.exe (PID: 2356)
Reads settings of System Certificates
- iexplore.exe (PID: 4064)
- iexplore.exe (PID: 2356)
- chrome.exe (PID: 3724)
Reads internet explorer settings
- iexplore.exe (PID: 4064)
Manual execution by user
- chrome.exe (PID: 4044)
Reads the hosts file
- chrome.exe (PID: 3724)
- chrome.exe (PID: 4044)
Changes settings of System certificates
- iexplore.exe (PID: 2356)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2356)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (45.3) |
|---|---|---|
| .oft | | | Outlook Form Template (26.5) |
Total processes
58
Monitored processes
19
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 632 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,7546137116029934680,11513802558572645732,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=9751135688695674864 --mojo-platform-channel-handle=3320 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 948 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1008,7546137116029934680,11513802558572645732,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=1093073674342344893 --renderer-client-id=13 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2536 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2064 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\Win $100 Amazon Gift Card-Were Back Hybrid Identity Protection 2020.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
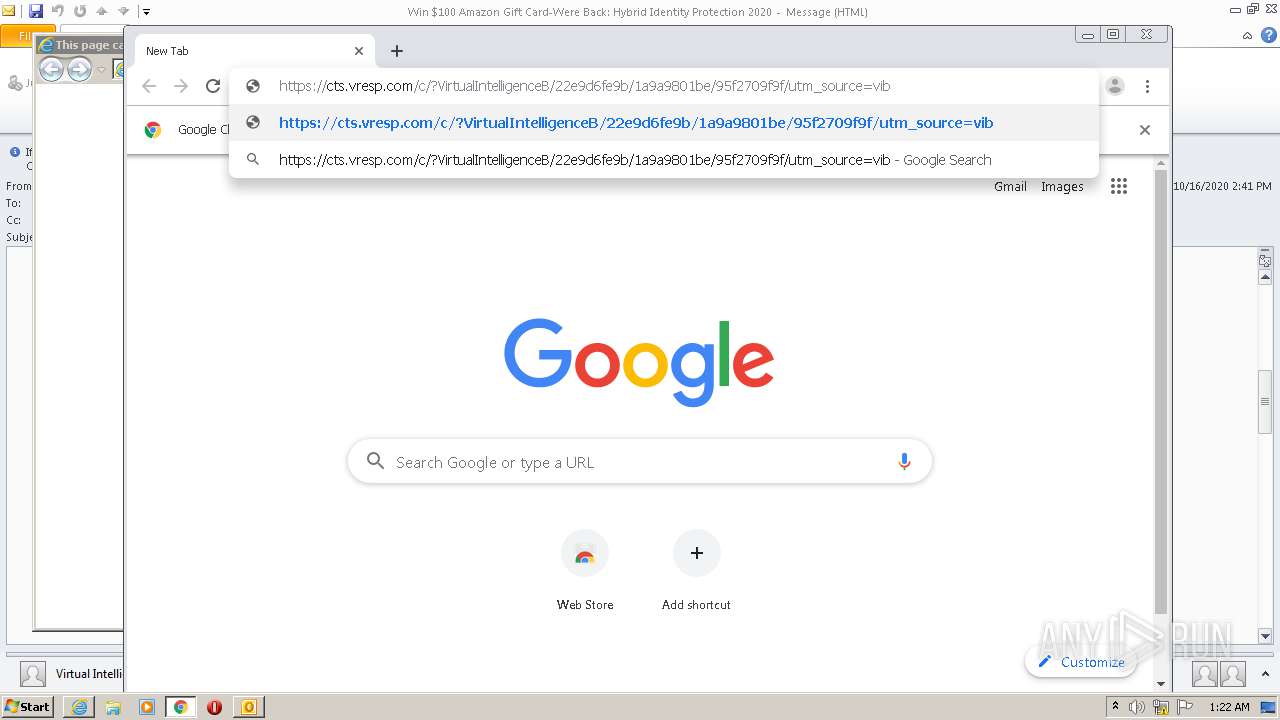
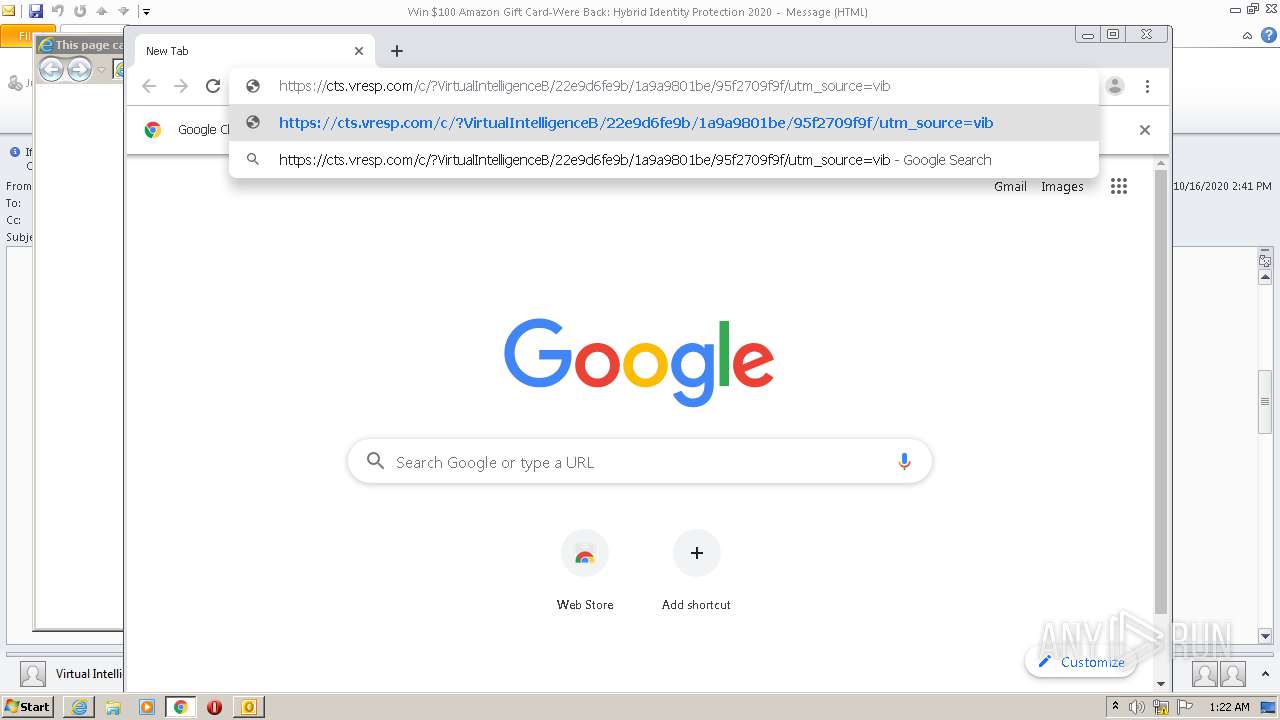
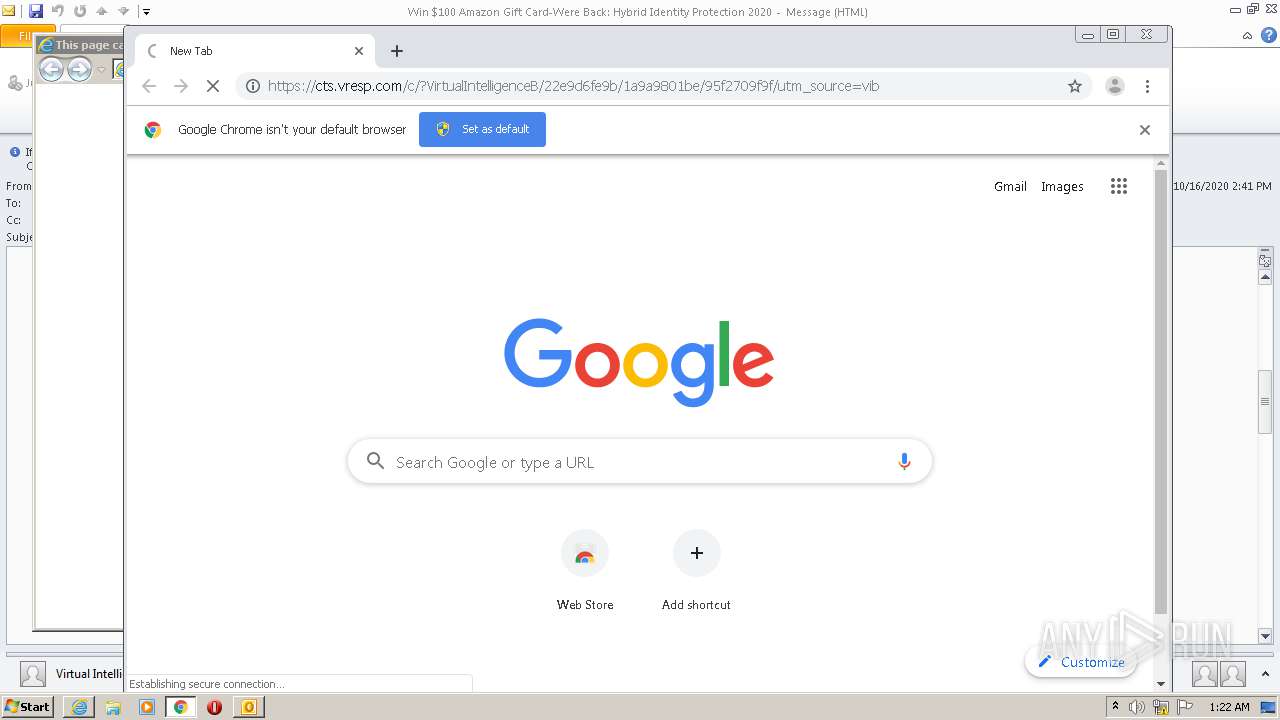
| 2356 | "C:\Program Files\Internet Explorer\iexplore.exe" https://cts.vresp.com/c/?VirtualIntelligenceB/22e9d6fe9b/1a9a9801be/95f2709f9f/utm_source=vib | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2704 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=1732 --on-initialized-event-handle=324 --parent-handle=328 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2744 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,7546137116029934680,11513802558572645732,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=18313611353120999185 --mojo-platform-channel-handle=3328 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2820 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1008,7546137116029934680,11513802558572645732,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=1855444979180336782 --renderer-client-id=10 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3684 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 3240 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1008,7546137116029934680,11513802558572645732,131072 --enable-features=PasswordImport --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9891632511989170640 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2496 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 3320 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,7546137116029934680,11513802558572645732,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=15018204389586909236 --mojo-platform-channel-handle=3508 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 3356 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1008,7546137116029934680,11513802558572645732,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=12640865304269123274 --mojo-platform-channel-handle=3432 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
2 441
Read events
1 742
Write events
674
Delete events
25
Modification events
| (PID) Process: | (2064) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2064) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (2064) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (2064) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (2064) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (2064) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (2064) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (2064) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (2064) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (2064) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
120
Text files
108
Unknown types
10
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2064 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVR4134.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2064 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\mso4636.tmp | — | |
MD5:— | SHA256:— | |||
| 4064 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab808F.tmp | — | |
MD5:— | SHA256:— | |||
| 4064 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar809F.tmp | — | |
MD5:— | SHA256:— | |||
| 2064 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 2064 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2356 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 4064 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\4344B8AF97AF3A423D9EE52899963CDE_04BA5175756E3BA9FC5BDAE2E0F4AA53 | der | |
MD5:— | SHA256:— | |||
| 4064 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\75VZAY3V.txt | text | |
MD5:— | SHA256:— | |||
| 4064 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\4344B8AF97AF3A423D9EE52899963CDE_04BA5175756E3BA9FC5BDAE2E0F4AA53 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
50
DNS requests
37
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2064 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
4064 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAVG%2Fhgj9%2BGUHaOfzhTEYXM%3D | US | der | 471 b | whitelisted |
4064 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://status.geotrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBR3enuod9bxDxzpICGW%2B2sabjf17QQUkFj%2FsJx1qFFUd7Ht8qNDFjiebMUCEApYuMXoydkUzhHJOZjpTAY%3D | US | der | 471 b | whitelisted |
— | — | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2356 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
— | — | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
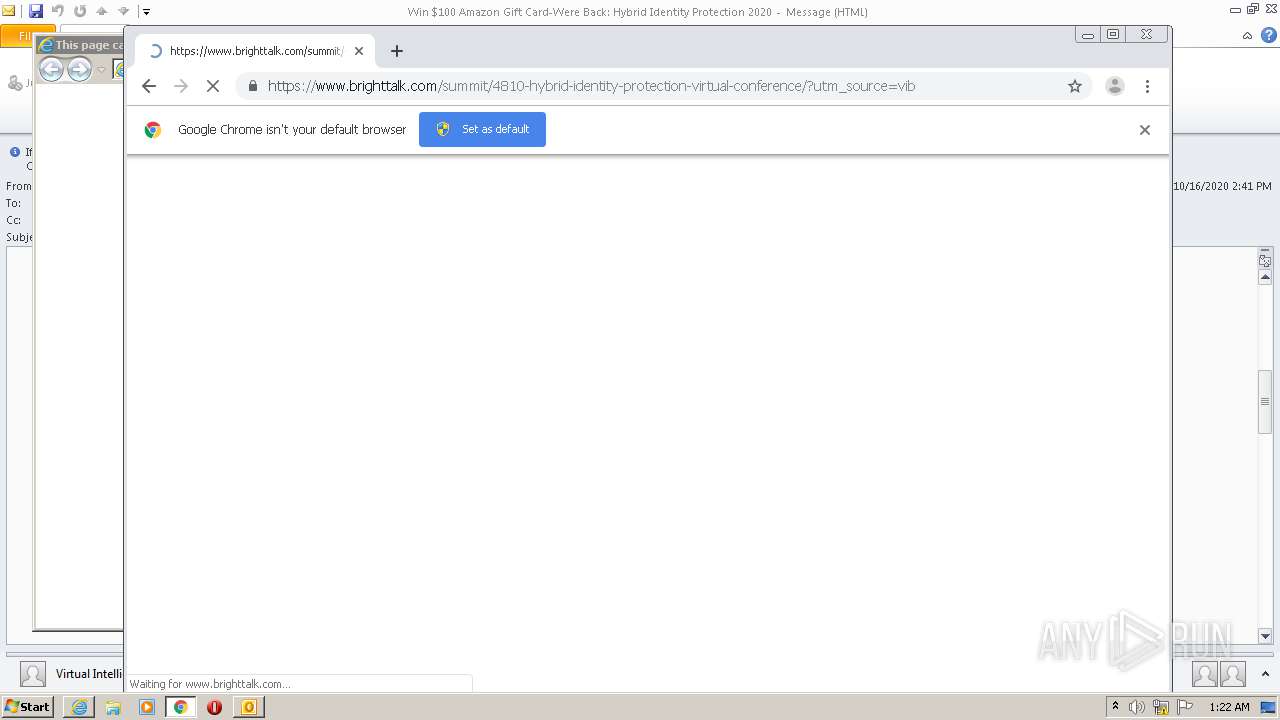
4064 | iexplore.exe | 104.111.229.43:443 | www.brighttalk.com | Akamai International B.V. | NL | unknown |
— | — | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3724 | chrome.exe | 172.217.18.173:443 | accounts.google.com | Google Inc. | US | whitelisted |
3724 | chrome.exe | 172.217.23.163:443 | www.gstatic.com | Google Inc. | US | whitelisted |
3724 | chrome.exe | 172.217.16.170:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3724 | chrome.exe | 172.217.16.142:443 | apis.google.com | Google Inc. | US | whitelisted |
4064 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
— | — | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2064 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
3724 | chrome.exe | 172.217.18.170:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
cts.vresp.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
status.geotrust.com |
| whitelisted |
www.brighttalk.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
4064 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |
4064 | iexplore.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |