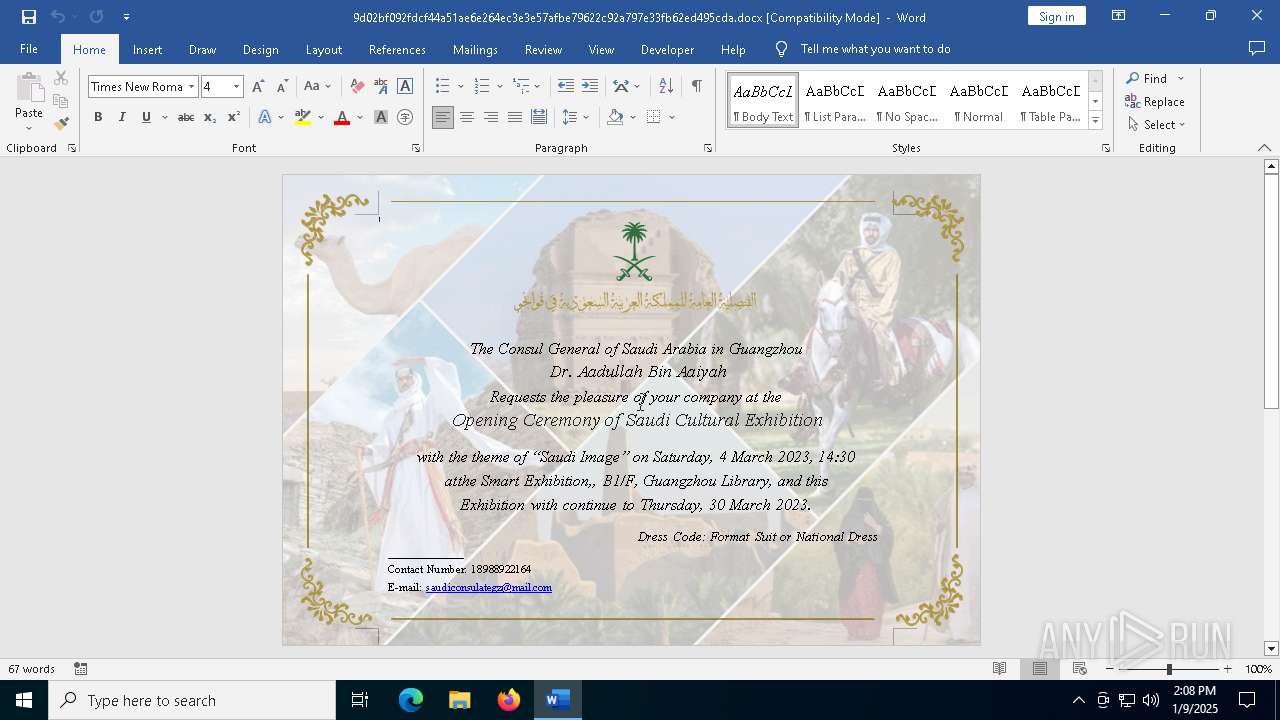
| File name: | 9d02bf092fdcf44a51ae6e264ec3e3e57afbe79622c92a797e33fb62ed495cda.docx |
| Full analysis: | https://app.any.run/tasks/de2470b7-97e6-4c93-a886-9f80847a49ea |
| Verdict: | Malicious activity |
| Analysis date: | January 09, 2025, 14:08:04 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | C87EB71FF038DF7B517644FA5C097EAC |
| SHA1: | 33F221579F95F623025B464F22A20DA66BE2B273 |
| SHA256: | 9D02BF092FDCF44A51AE6E264EC3E3E57AFBE79622C92A797E33FB62ED495CDA |
| SSDEEP: | 49152:IaZ+h3sO3qg/17759EqUOF0kkl807MqJJ5eZtVZg1npbbObNbVHxSi4zJgMyW8lv:Ioo3sTs1775SARkl57TJWZgnbbmlx4iL |
MALICIOUS
CVE-2022-30190 detected
- WINWORD.EXE (PID: 4816)
SIDEWINDER has been found (auto)
- WINWORD.EXE (PID: 4816)
Connects to the CnC server
- svchost.exe (PID: 2192)
SUSPICIOUS
No suspicious indicators.INFO
Sends debugging messages
- WINWORD.EXE (PID: 4816)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:12:12 09:02:04 |
| ZipCRC: | 0x057e5599 |
| ZipCompressedSize: | 248 |
| ZipUncompressedSize: | 737 |
| ZipFileName: | _rels/.rels |
XML
| Template: | Normal |
|---|---|
| TotalEditTime: | 4 minutes |
| Pages: | 1 |
| Words: | 75 |
| Characters: | 430 |
| Application: | Microsoft Office Word |
| DocSecurity: | None |
| Lines: | 3 |
| Paragraphs: | 1 |
| ScaleCrop: | No |
| Company: | - |
| LinksUpToDate: | No |
| CharactersWithSpaces: | 504 |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 15 |
| LastModifiedBy: | user |
| RevisionNumber: | 8 |
| CreateDate: | 2023:12:12 05:55:00Z |
| ModifyDate: | 2023:12:12 15:22:00Z |
| Created: | 2023:02:24 00:00:00Z |
| Creator: | Adobe Illustrator CC 23.0 (Windows) |
| LastSaved: | 2023:12:12 00:00:00Z |
XMP
| Title: | 2021国庆招待会邀请函 |
|---|
Total processes
143
Monitored processes
12
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1920 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\FLTLDR.EXE" C:\Program Files\Common Files\Microsoft Shared\GRPHFLT\JPEGIM32.FLT | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\FLTLDR.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Filter Loader Exit code: 3221225506 Version: 16.0.16026.20000 Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4816 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n C:\Users\admin\Desktop\9d02bf092fdcf44a51ae6e264ec3e3e57afbe79622c92a797e33fb62ed495cda.docx /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 6332 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "FEC6D460-82C7-4884-98DE-80CAE3B083DD" "81A6D66B-545D-415A-BC44-D453D6B266CA" "4816" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 6364 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\FLTLDR.EXE" C:\Program Files\Common Files\Microsoft Shared\GRPHFLT\JPEGIM32.FLT | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\FLTLDR.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Filter Loader Exit code: 3221225506 Version: 16.0.16026.20000 Modules
| |||||||||||||||
| 6368 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\FLTLDR.EXE" C:\Program Files\Common Files\Microsoft Shared\GRPHFLT\JPEGIM32.FLT | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\FLTLDR.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Filter Loader Exit code: 3221225506 Version: 16.0.16026.20000 Modules
| |||||||||||||||
| 6524 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\FLTLDR.EXE" C:\Program Files\Common Files\Microsoft Shared\GRPHFLT\JPEGIM32.FLT | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\FLTLDR.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Filter Loader Exit code: 3221225506 Version: 16.0.16026.20000 Modules
| |||||||||||||||
| 6792 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\FLTLDR.EXE" C:\Program Files\Common Files\Microsoft Shared\GRPHFLT\JPEGIM32.FLT | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\FLTLDR.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Filter Loader Exit code: 3221225506 Version: 16.0.16026.20000 Modules
| |||||||||||||||
| 6816 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\FLTLDR.EXE" C:\Program Files\Common Files\Microsoft Shared\GRPHFLT\JPEGIM32.FLT | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\FLTLDR.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Filter Loader Exit code: 3221225506 Version: 16.0.16026.20000 Modules
| |||||||||||||||
| 6828 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\FLTLDR.EXE" C:\Program Files\Common Files\Microsoft Shared\GRPHFLT\JPEGIM32.FLT | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\FLTLDR.EXE | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Filter Loader Exit code: 3221225506 Version: 16.0.16026.20000 Modules
| |||||||||||||||
Total events
9 847
Read events
9 556
Write events
274
Delete events
17
Modification events
| (PID) Process: | (4816) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (4816) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\4816 |
| Operation: | write | Name: | 0 |
Value: 0B0E105CD028433CAB2F499AA8F672AAFB6860230046C593D6D7FED3D8ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511D025D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (4816) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (4816) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (4816) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (4816) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (4816) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (4816) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (4816) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (4816) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
1
Suspicious files
17
Text files
23
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4816 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\6DC5F4FE-24B6-4AB3-AD0D-EBA99C152942 | xml | |
MD5:1999697121DE7545DA860DB45522394D | SHA256:405F0E6276D1A39550DFAD82FDFB4CEBBD0CAE763E88BCF0CAB2E99108186FCB | |||
| 4816 | WINWORD.EXE | C:\Users\admin\Desktop\~$02bf092fdcf44a51ae6e264ec3e3e57afbe79622c92a797e33fb62ed495cda.docx | pgc | |
MD5:C153F78CDA96A3F9CEAD7FFAAECDC271 | SHA256:F40704283FE9EF766EA1A1400524F8847298A73AD5AA2CEBD939CA46A14D4143 | |||
| 4816 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:D5AAE9559CC397B9F4E26087E9A07F19 | SHA256:518C1AE845FE9AC4FC1CC023DC0DE23D4062016DD44E7BD5F09D31345767AD26 | |||
| 4816 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:6BE1CE2E44D85D7DDB9602B75CD6A7CF | SHA256:C76FBE34F570AA0DD9BFBEF9472BD111F80B87C926B00490BA56B95F3E1A4677 | |||
| 4816 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:562533DE6A9AA5E0383A99653ADDFC01 | SHA256:5EAB45157A9CB44B1AA97491B80449E82738790410823BBC5C1C70125B0C9E3D | |||
| 4816 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 4816 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\9d02bf092fdcf44a51ae6e264ec3e3e57afbe79622c92a797e33fb62ed495cda.docx.LNK | binary | |
MD5:D4040CD5D078A046A4E17E0011A09CD1 | SHA256:8925BAED61E2519B68D1D70757CFA51D7C657EFBD3FD4DF2C4AA4479FBEF6515 | |||
| 4816 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:847C57FFF72C31E1DAC8CBAF1CC93761 | SHA256:95505FF5E40196F1B745DD2B5A5641C1852E84E1326D0162894209EE3681B617 | |||
| 4816 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\fb3b0dbfee58fac8.customDestinations-ms~RF13f437.TMP | binary | |
MD5:4FCB2A3EE025E4A10D21E1B154873FE2 | SHA256:90BF6BAA6F968A285F88620FBF91E1F5AA3E66E2BAD50FD16F37913280AD8228 | |||
| 4816 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\fb3b0dbfee58fac8.customDestinations-ms | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
11
TCP/UDP connections
43
DNS requests
28
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
4816 | WINWORD.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
2212 | SIHClient.exe | GET | 200 | 23.52.120.96:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4076 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
4816 | WINWORD.EXE | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.52.120.96:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5064 | SearchApp.exe | 2.16.110.193:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4816 | WINWORD.EXE | 52.109.32.97:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
4816 | WINWORD.EXE | 52.113.194.132:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4816 | WINWORD.EXE | 52.109.68.129:443 | roaming.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
login.live.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | A Network Trojan was detected | ET MALWARE TA399 SideWinder APT CnC Domain in DNS Lookup (mofa-gov-sa .direct888 .net) |
2192 | svchost.exe | A Network Trojan was detected | ET MALWARE TA399 SideWinder APT CnC Domain in DNS Lookup (mofa-gov-sa .direct888 .net) |
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|