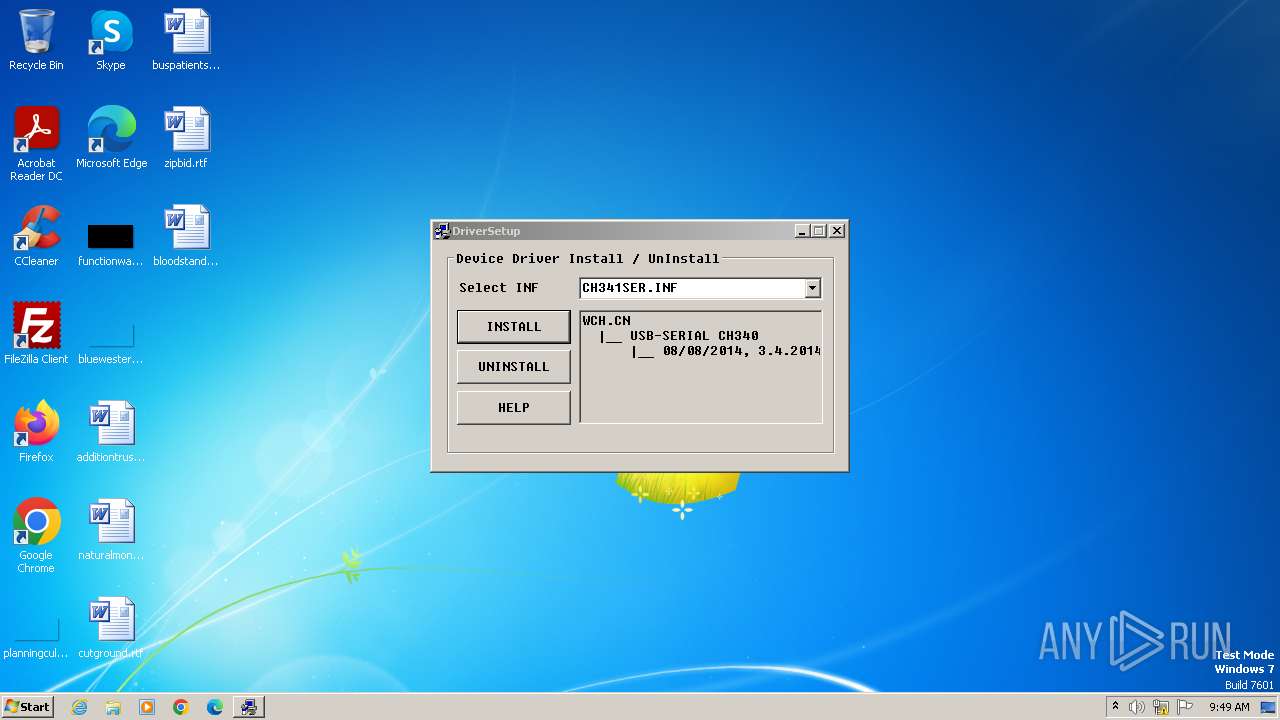
| File name: | CH341SER.EXE |
| Full analysis: | https://app.any.run/tasks/3f54262e-0db2-4ef5-9d6d-84599ba73002 |
| Verdict: | Malicious activity |
| Analysis date: | November 22, 2023, 09:49:43 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, RAR self-extracting archive |
| MD5: | 1AF3FDEBFBAB3E247FEB588AEA64DD64 |
| SHA1: | D557A8978877199BAFE2E7BAAC63ADAB17BED05D |
| SHA256: | 9CF96FDDF474EDA80F2B4C09F8EF19443CF6768429819E4CBA7B869291B7B8B5 |
| SSDEEP: | 6144:h8U2qy6rRZb7jxGYXDFJmWM93dYlGAGs:5zy6rRxEwJmdR+6s |
MALICIOUS
Drops the executable file immediately after the start
- CH341SER.EXE (PID: 3448)
- drvinst.exe (PID: 3584)
- SETUP.EXE (PID: 3464)
Creates a writable file in the system directory
- drvinst.exe (PID: 3584)
- SETUP.EXE (PID: 3464)
SUSPICIOUS
Drops a system driver (possible attempt to evade defenses)
- CH341SER.EXE (PID: 3448)
- SETUP.EXE (PID: 3464)
- drvinst.exe (PID: 3584)
Reads the Internet Settings
- CH341SER.EXE (PID: 3448)
Creates files in the driver directory
- drvinst.exe (PID: 3584)
- SETUP.EXE (PID: 3464)
Checks Windows Trust Settings
- drvinst.exe (PID: 3584)
INFO
Reads the computer name
- CH341SER.EXE (PID: 3448)
- SETUP.EXE (PID: 3464)
- drvinst.exe (PID: 3584)
Checks supported languages
- SETUP.EXE (PID: 3464)
- drvinst.exe (PID: 3584)
- CH341SER.EXE (PID: 3448)
Create files in a temporary directory
- SETUP.EXE (PID: 3464)
Reads the machine GUID from the registry
- SETUP.EXE (PID: 3464)
- drvinst.exe (PID: 3584)
Manual execution by a user
- WINWORD.EXE (PID: 3880)
- WINWORD.EXE (PID: 4012)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | WinRAR Self Extracting archive (94.3) |
|---|---|---|
| .scr | | | Windows screen saver (2.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.1) |
| .exe | | | Win32 Executable (generic) (0.8) |
| .exe | | | Win32 Executable Watcom C++ (generic) (0.4) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2007:05:22 06:59:14+02:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 5 |
| CodeSize: | 81920 |
| InitializedDataSize: | 22016 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1000 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
45
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3204 | "C:\WCH.CN\CH341SER\SETUP.EXE" | C:\WCH.CN\CH341SER\SETUP.EXE | — | CH341SER.EXE | |||||||||||
User: admin Integrity Level: MEDIUM Description: EXE For Driver Installation Exit code: 3221226540 Version: 1, 6, 8, 0 Modules
| |||||||||||||||
| 3448 | "C:\Users\admin\AppData\Local\Temp\CH341SER.EXE" | C:\Users\admin\AppData\Local\Temp\CH341SER.EXE | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3464 | "C:\WCH.CN\CH341SER\SETUP.EXE" | C:\WCH.CN\CH341SER\SETUP.EXE | CH341SER.EXE | ||||||||||||
User: admin Integrity Level: HIGH Description: EXE For Driver Installation Exit code: 1 Version: 1, 6, 8, 0 Modules
| |||||||||||||||
| 3584 | DrvInst.exe "4" "0" "C:\Users\admin\AppData\Local\Temp\{332cfc87-73d9-1450-1aea-b63444e7036f}\CH341SER.INF" "0" "6dbd0d02f" "0000054C" "WinSta0\Default" "000004AC" "208" "C:\WCH.CN\CH341SER" | C:\Windows\System32\drvinst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3880 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\additiontrust.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 4012 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\Desktop\bloodstandard.rtf" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
8 162
Read events
7 765
Write events
98
Delete events
299
Modification events
| (PID) Process: | (3448) CH341SER.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3448) CH341SER.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3448) CH341SER.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3448) CH341SER.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3464) SETUP.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3584) drvinst.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\17A\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3880) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3880) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: On | |||
| (PID) Process: | (3880) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: On | |||
| (PID) Process: | (3880) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: On | |||
Executable files
49
Suspicious files
31
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3464 | SETUP.EXE | C:\Users\admin\AppData\Local\Temp\{332cfc87-73d9-1450-1aea-b63444e7036f}\SET9726.tmp | executable | |
MD5:A9FC675D0029A525335B106487C7D578 | SHA256:50877BC8EA82BBAC833D25C9AC248E6FC9A240AB3C6D7E2C115667532C23676F | |||
| 3448 | CH341SER.EXE | C:\WCH.CN\CH341SER\SETUP.EXE | executable | |
MD5:181F68547D52360FC142AC3ADC2436B7 | SHA256:A8F306D5BA1A23F587283FD410313F50AC1AC5CE1268938B065130A0DC84C658 | |||
| 3448 | CH341SER.EXE | C:\WCH.CN\CH341SER\CH341SER.SYS | executable | |
MD5:A9FC675D0029A525335B106487C7D578 | SHA256:50877BC8EA82BBAC833D25C9AC248E6FC9A240AB3C6D7E2C115667532C23676F | |||
| 3448 | CH341SER.EXE | C:\WCH.CN\CH341SER\CH341PT.DLL | executable | |
MD5:69B6FEC924C30042D329AE56CA8925CC | SHA256:45494CE819C1B5C21ABB72DC47A0CA36807E0ED74CE55B631DA174C77A9B24DB | |||
| 3464 | SETUP.EXE | C:\Users\admin\AppData\Local\Temp\{332cfc87-73d9-1450-1aea-b63444e7036f}\CH341PT.DLL | executable | |
MD5:69B6FEC924C30042D329AE56CA8925CC | SHA256:45494CE819C1B5C21ABB72DC47A0CA36807E0ED74CE55B631DA174C77A9B24DB | |||
| 3448 | CH341SER.EXE | C:\WCH.CN\CH341SER\CH341S64.SYS | executable | |
MD5:3C0A1B6F538E00F318C109F4A3F29515 | SHA256:DE6CA1AE927081AC622F99AB9C77B2127CBB2DF597B4123A4AA2F3DA52CD64D5 | |||
| 3464 | SETUP.EXE | C:\Windows\INF\setupapi.dev.log | text | |
MD5:0E821E5ED00ECCEF1A8F01437B539934 | SHA256:5A44B28DD9F0E1F0622110A84B0E4F7CAF2FD535399BB1533E3C24FF8BF8220E | |||
| 3464 | SETUP.EXE | C:\Users\admin\AppData\Local\Temp\{332cfc87-73d9-1450-1aea-b63444e7036f}\SET9705.tmp | binary | |
MD5:715693624013826D337E792ED86376AC | SHA256:585FCA8AB9C8A13222760D6BBAB62CE4069D24F73BD304D89C54B5298B9420BD | |||
| 3464 | SETUP.EXE | C:\Users\admin\AppData\Local\Temp\{332cfc87-73d9-1450-1aea-b63444e7036f}\CH341SER.SYS | executable | |
MD5:A9FC675D0029A525335B106487C7D578 | SHA256:50877BC8EA82BBAC833D25C9AC248E6FC9A240AB3C6D7E2C115667532C23676F | |||
| 3464 | SETUP.EXE | C:\Users\admin\AppData\Local\Temp\{332cfc87-73d9-1450-1aea-b63444e7036f}\CH341SER.INF | binary | |
MD5:0ECFFBA87B80F54F7016DA633DD9AB1C | SHA256:0CBD34F89B0D11B386E07A825FAB531706F86E9DA44DCC536AC7C98A6D22C383 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2588 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |