| File name: | advchange.exe |
| Full analysis: | https://app.any.run/tasks/c99254d1-04c2-4f0a-a1f1-ba05bc97c1b2 |
| Verdict: | Malicious activity |
| Analysis date: | February 21, 2024, 20:40:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | D1899042E23CF24F60235AB211901203 |
| SHA1: | 936035CAC244E94E9F1F28FC14EA72EF317D8B4F |
| SHA256: | 9CEDE11DBA203CE7E15EF03DC5E0BC89CEFE33567F256753734DA2535C01D53A |
| SSDEEP: | 6144:FU9jpmRl4DOXD02IaRkfyBzHlXTCLaerOVv6+LKyNpG:KbXLaerEvZLRvG |
MALICIOUS
Drops the executable file immediately after the start
- advchange.exe (PID: 4052)
SUSPICIOUS
Reads settings of System Certificates
- advchange.exe (PID: 4052)
Checks Windows Trust Settings
- advchange.exe (PID: 4052)
Reads security settings of Internet Explorer
- advchange.exe (PID: 4052)
Reads the Internet Settings
- advchange.exe (PID: 4052)
INFO
Checks supported languages
- wmpnscfg.exe (PID: 3288)
- advchange.exe (PID: 4052)
Reads the computer name
- wmpnscfg.exe (PID: 3288)
- advchange.exe (PID: 4052)
Reads the machine GUID from the registry
- advchange.exe (PID: 4052)
Create files in a temporary directory
- advchange.exe (PID: 4052)
- reg.exe (PID: 3708)
Reads the software policy settings
- advchange.exe (PID: 4052)
Creates files or folders in the user directory
- advchange.exe (PID: 4052)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2093:01:18 13:34:02+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32 |
| LinkerVersion: | 48 |
| CodeSize: | 349184 |
| InitializedDataSize: | 110592 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x57332 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 2.2.1.21 |
| ProductVersionNumber: | 2.2.1.21 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
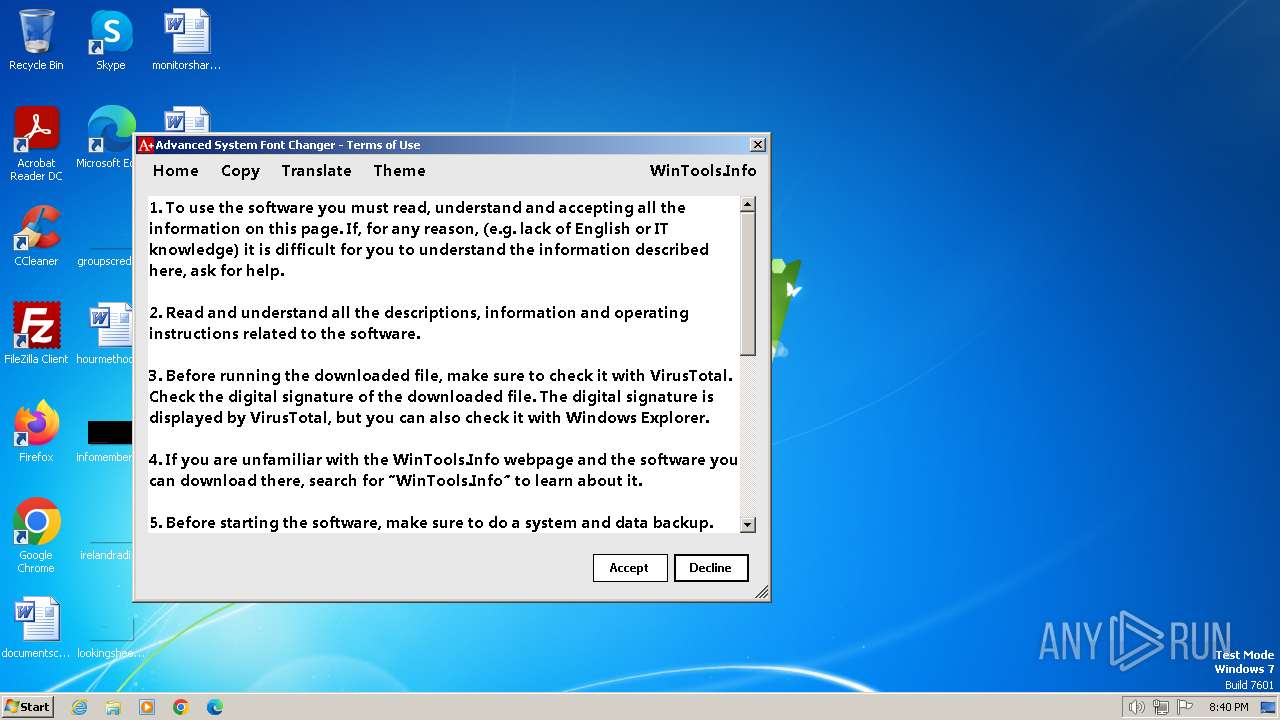
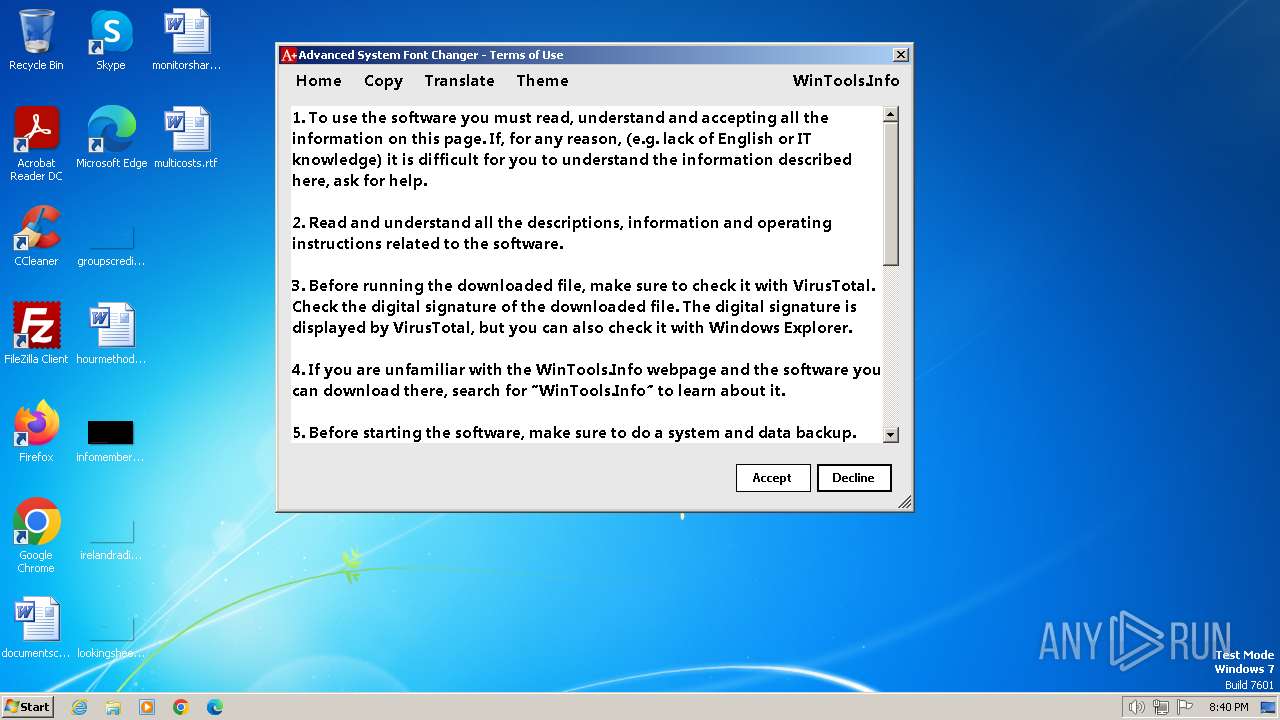
| Comments: | https://www.wintools.info |
| CompanyName: | WinTools.Info |
| FileDescription: | Advanced System Font Changer |
| FileVersion: | 2.2.1.21 |
| InternalName: | advchange.exe |
| LegalCopyright: | Peter Panisz |
| LegalTrademarks: | WinTools.Info |
| OriginalFileName: | advchange.exe |
| ProductName: | Advanced System Font Changer |
| ProductVersion: | 2.2.1.21 |
| AssemblyVersion: | 2.2.1.21 |
Total processes
39
Monitored processes
3
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3288 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3708 | "reg.exe" export "HKEY_CURRENT_USER\Control Panel\Desktop\WindowMetrics" "C:\Users\admin\AppData\Local\Temp\WindowMetrics.reg" /y | C:\Windows\System32\reg.exe | — | advchange.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4052 | "C:\Users\admin\AppData\Local\Temp\advchange.exe" | C:\Users\admin\AppData\Local\Temp\advchange.exe | explorer.exe | ||||||||||||
User: admin Company: WinTools.Info Integrity Level: MEDIUM Description: Advanced System Font Changer Exit code: 0 Version: 2.2.1.21 Modules
| |||||||||||||||
Total events
6 673
Read events
6 628
Write events
45
Delete events
0
Modification events
| (PID) Process: | (4052) advchange.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (4052) advchange.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (4052) advchange.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (4052) advchange.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (4052) advchange.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (4052) advchange.exe | Key: | HKEY_CURRENT_USER\Software\Panisz |
| Operation: | write | Name: | 4B1C653B-99FB-4056-BAA2-9F15A576D722 |
Value: 01000000D08C9DDF0115D1118C7A00C04FC297EB01000000DBDD10622BD67741A42163F361389C4700000000020000000000106600000001000020000000DE62877B9BD8DECC6B4B1249F44272DD888C0CCEDAB2D0C9DCAB16459F9AB4AA000000000E800000000200002000000010A05404310E740A50CBAEE7D09EA93F55C59FE720557FB7079AE991A25E02CC20000000A8DD9422817203DC34BB1B824B8CA553068FC30680EACE11842ACC2B8A680A8F400000007978D19D07268ACAB0670D65C84040DAA7AECF0BB6D013A36C8F1CD7DB5D781E143B0B5DEC3E2335ECADCA6BA6A18EBA2C36F051EF03492323150231CE216471 | |||
| (PID) Process: | (4052) advchange.exe | Key: | HKEY_CURRENT_USER\Software\Panisz\WindowMetrics |
| Operation: | write | Name: | BorderWidth |
Value: -15 | |||
| (PID) Process: | (4052) advchange.exe | Key: | HKEY_CURRENT_USER\Software\Panisz\WindowMetrics |
| Operation: | write | Name: | CaptionFont |
Value: F5FFFFFF000000000000000000000000BC02000000000001000000005400610068006F006D00610000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4052) advchange.exe | Key: | HKEY_CURRENT_USER\Software\Panisz\WindowMetrics |
| Operation: | write | Name: | CaptionHeight |
Value: -270 | |||
| (PID) Process: | (4052) advchange.exe | Key: | HKEY_CURRENT_USER\Software\Panisz\WindowMetrics |
| Operation: | write | Name: | CaptionWidth |
Value: -270 | |||
Executable files
0
Suspicious files
6
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4052 | advchange.exe | C:\Users\admin\AppData\Local\WinTools.Info\advchange.exe_Url_swpp4cxe02ha10c4td1bvxm0pnnh5fcb\2.2.1.21\user.config | xml | |
MD5:B18BFA514911775348E2018AF69A2623 | SHA256:3DC444EB66DD51E3642D3EBED67A33EF76FF712811E0869D4D3F881D65F2150D | |||
| 4052 | advchange.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CE8B5763061589BB1835A4B6566F644D | binary | |
MD5:1A941AF15BA3C478542937F57A0F9DEE | SHA256:59EC62062665CFF7B9DF305D2E252CA94B194C862F87F3D903EAFC60C92F4E91 | |||
| 4052 | advchange.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\77EC63BDA74BD0D0E0426DC8F8008506 | binary | |
MD5:710F278C95007C8E44DA1DF999590799 | SHA256:4AAE12B6A552E7F71BF073E0E98D2012B5228BB68A9CBE86842AF163164B0632 | |||
| 4052 | advchange.exe | C:\Users\admin\AppData\Local\WinTools.Info\advchange.exe_Url_swpp4cxe02ha10c4td1bvxm0pnnh5fcb\2.2.1.21\dyj4kgrj.newcfg | xml | |
MD5:B18BFA514911775348E2018AF69A2623 | SHA256:3DC444EB66DD51E3642D3EBED67A33EF76FF712811E0869D4D3F881D65F2150D | |||
| 4052 | advchange.exe | C:\Users\admin\AppData\Local\Temp\TarF86A.tmp | cat | |
MD5:9C0C641C06238516F27941AA1166D427 | SHA256:4276AF3669A141A59388BC56A87F6614D9A9BDDDF560636C264219A7EB11256F | |||
| 4052 | advchange.exe | C:\Users\admin\AppData\Local\WinTools.Info\advchange.exe_Url_swpp4cxe02ha10c4td1bvxm0pnnh5fcb\2.2.1.21\0iznb4ou.newcfg | xml | |
MD5:5833D7919FFE46189247BAFDAC0423D2 | SHA256:71A70DE2F9D98937B187353E17BE58E226AA442C3886A244C393ADF431741B47 | |||
| 4052 | advchange.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CE8B5763061589BB1835A4B6566F644D | der | |
MD5:DE1FF69E84AEA7B421CE1E587DD18498 | SHA256:BEB00B30839B9BC32C32E4447905950641F26421B15ED089198B518AE2EA1B99 | |||
| 3708 | reg.exe | C:\Users\admin\AppData\Local\Temp\WindowMetrics.reg | text | |
MD5:23F540947F96ACE40A40C185043222CC | SHA256:5374D00790DA43DC97A325355EFCF45F1B1EFDD76430B94D8D072BBCAA8679DE | |||
| 4052 | advchange.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:AC05D27423A85ADC1622C714F2CB6184 | SHA256:C6456E12E5E53287A547AF4103E0397CB9697E466CF75844312DC296D43D144D | |||
| 4052 | advchange.exe | C:\Users\admin\AppData\Local\WinTools.Info\advchange.exe_Url_swpp4cxe02ha10c4td1bvxm0pnnh5fcb\2.2.1.21\iredqxbj.newcfg | xml | |
MD5:DCE1FD9F7BD3E5FC4FCAA5F11194DD27 | SHA256:6204EADA6B46F1E577A9C02FEE65282F1B4344DE8128717995DAE316F0B5A4D1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
6
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4052 | advchange.exe | GET | 200 | 193.42.222.125:80 | http://rootca2017-ca1.e-szigno.hu/rootca2017.crt | unknown | binary | 580 b | unknown |
4052 | advchange.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?43acbfd2d70810b3 | unknown | compressed | 65.2 Kb | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4052 | advchange.exe | 193.42.222.125:80 | rootca2017-ca1.e-szigno.hu | MICROSEC Szamitastechnikai Fejleszto zartkoruen mukodo reszvenytarsasag | HU | unknown |
4052 | advchange.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
rootca2017-ca1.e-szigno.hu |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |