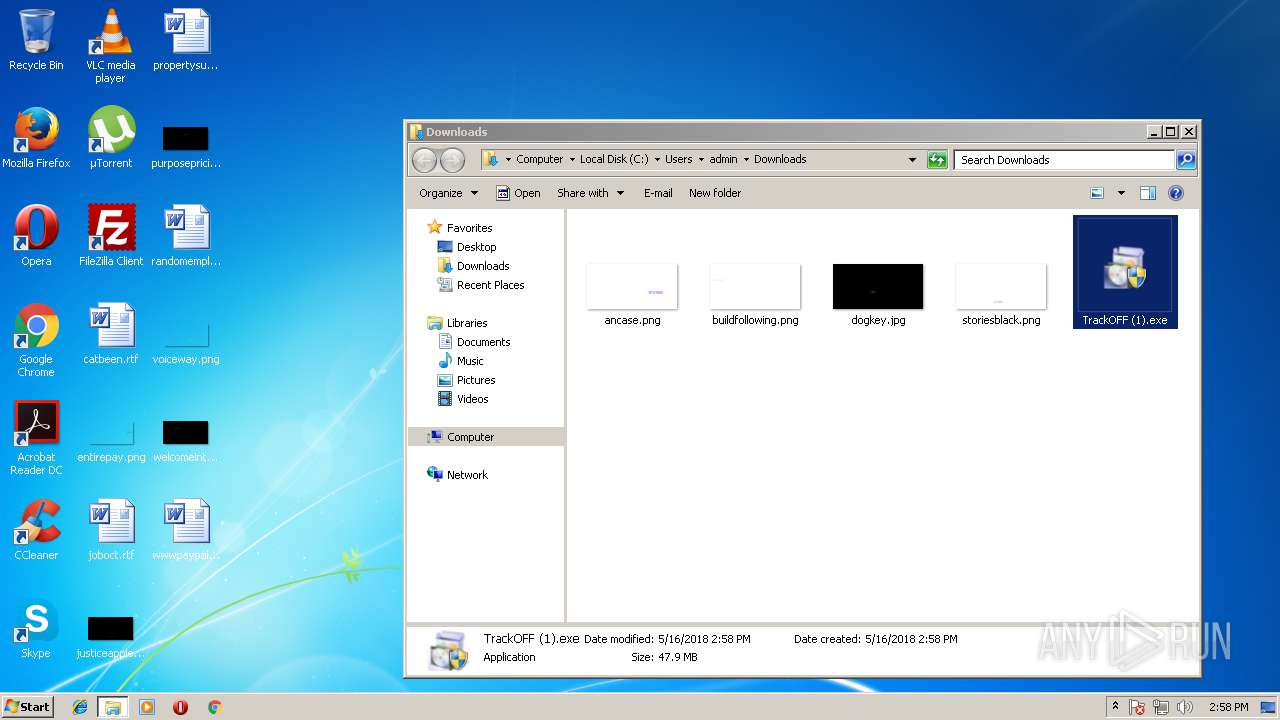
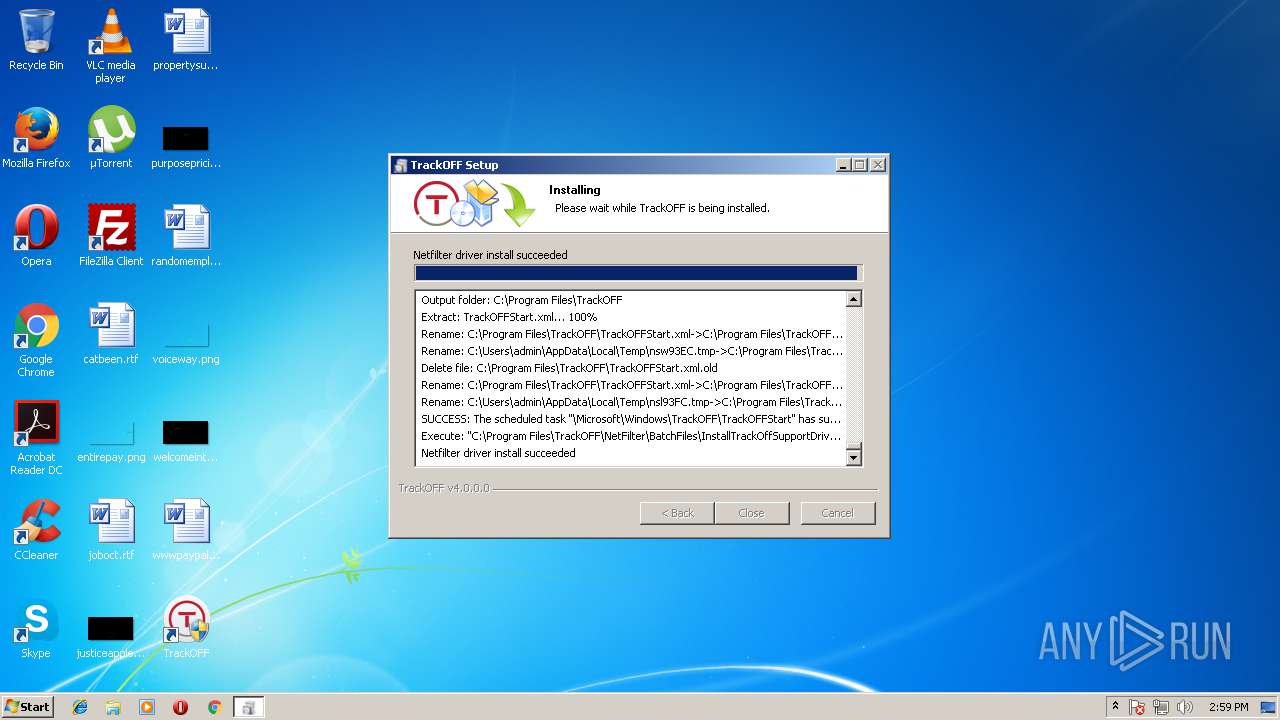
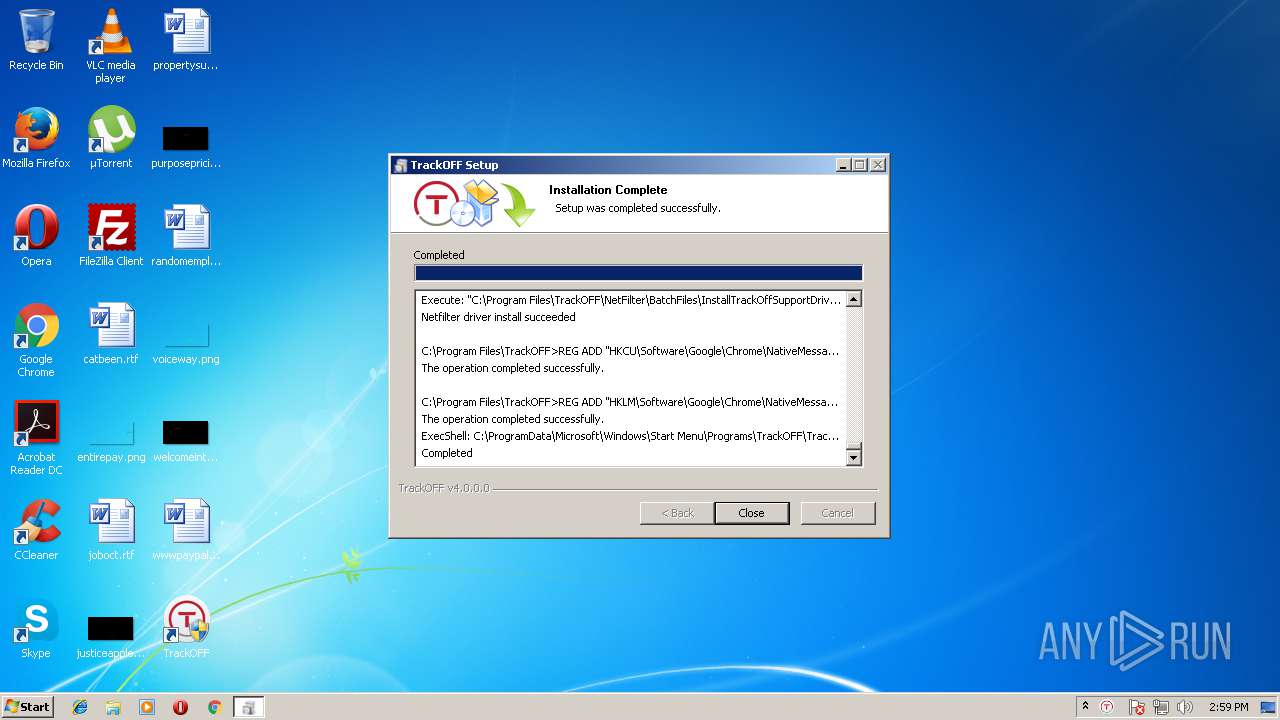
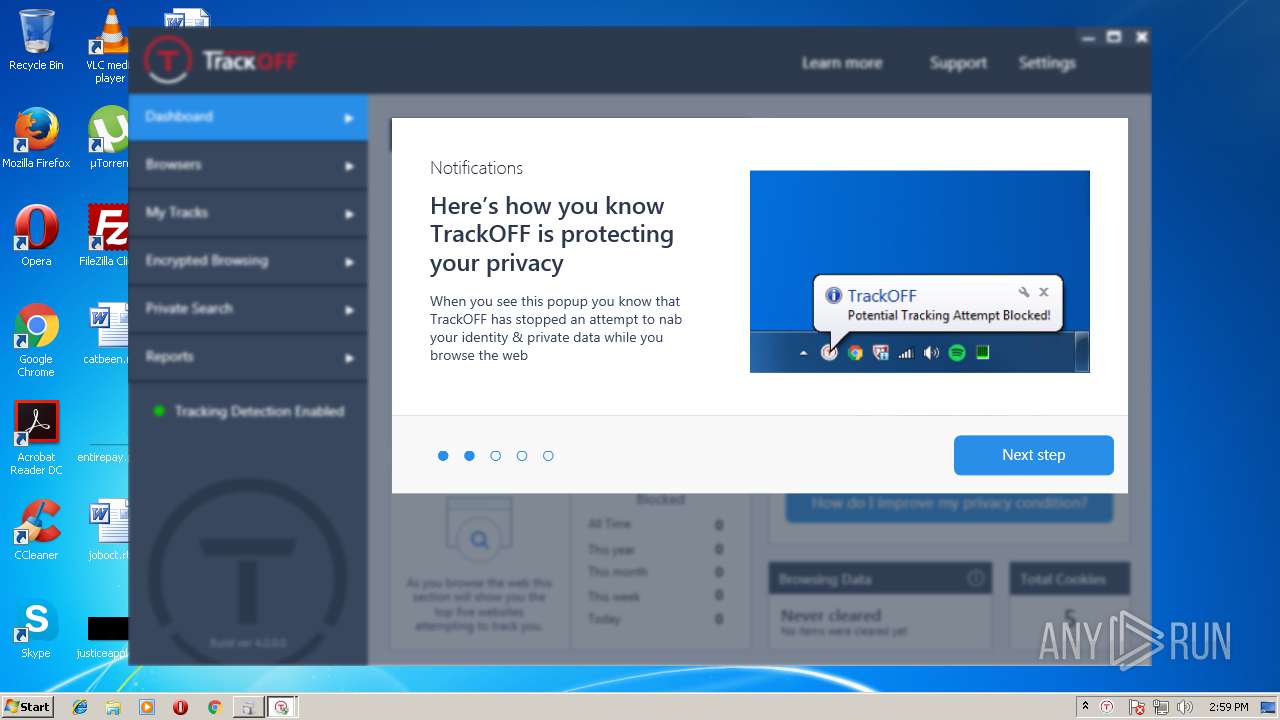
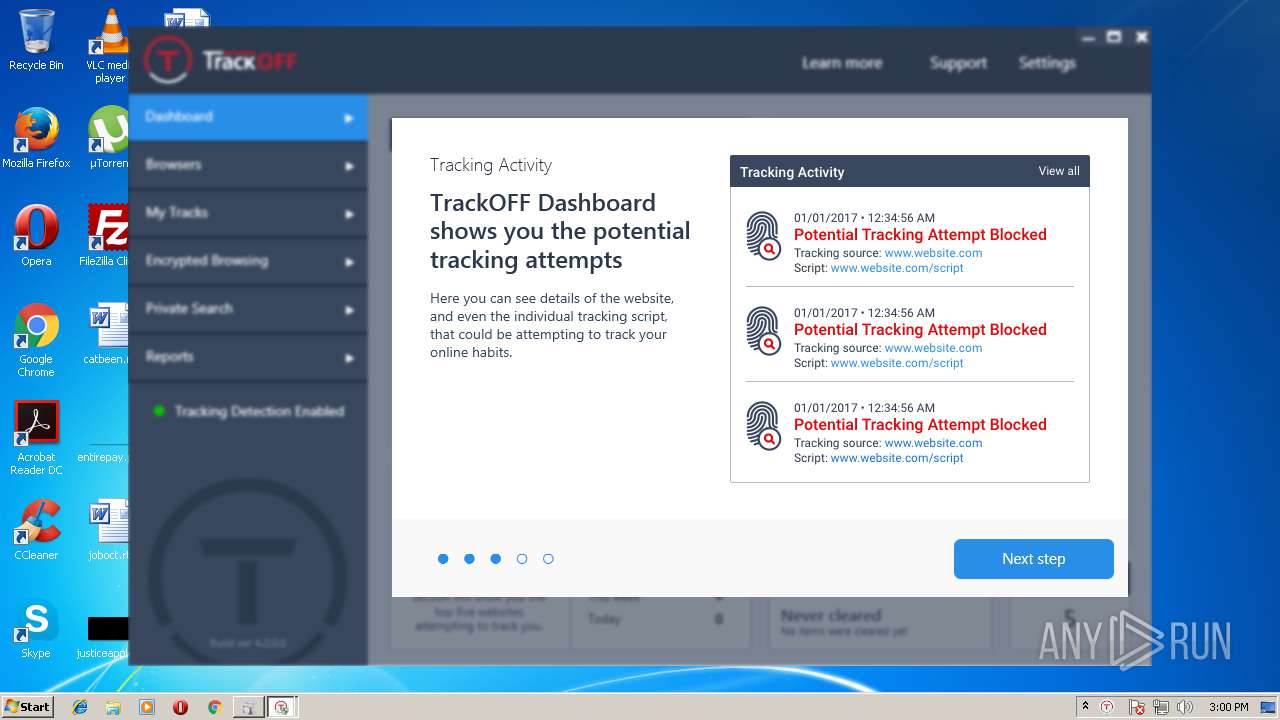
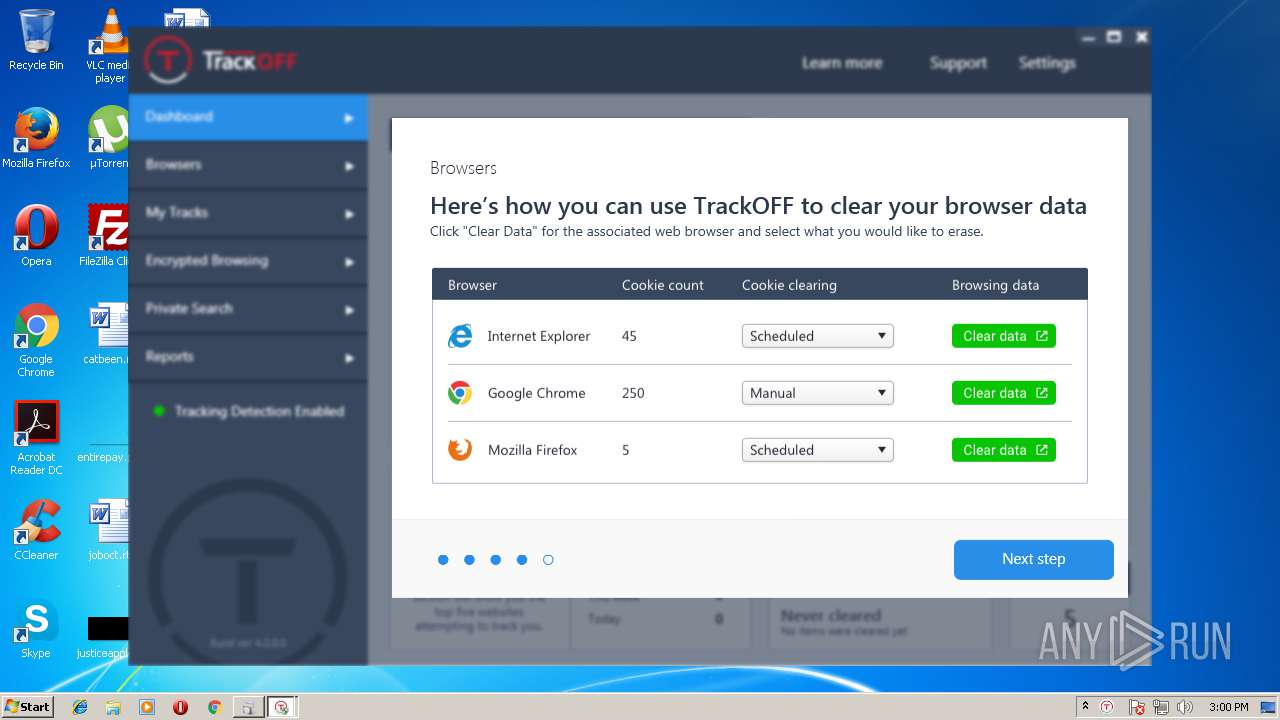
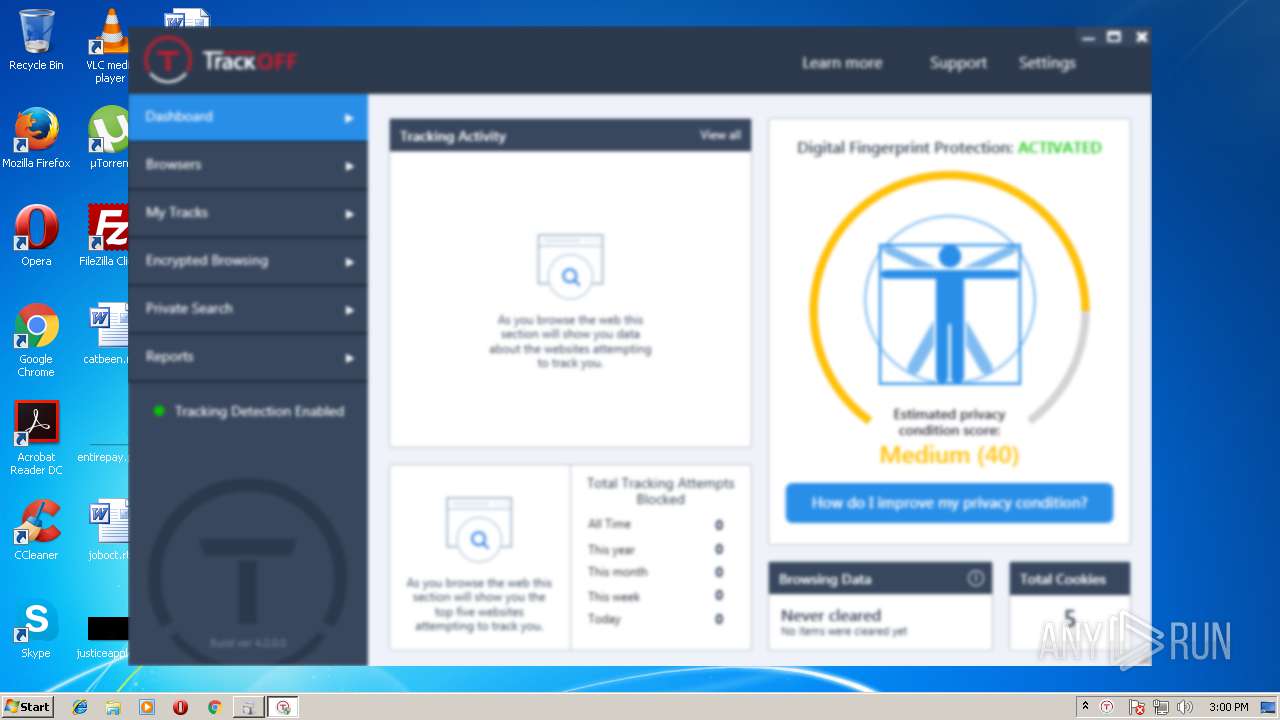
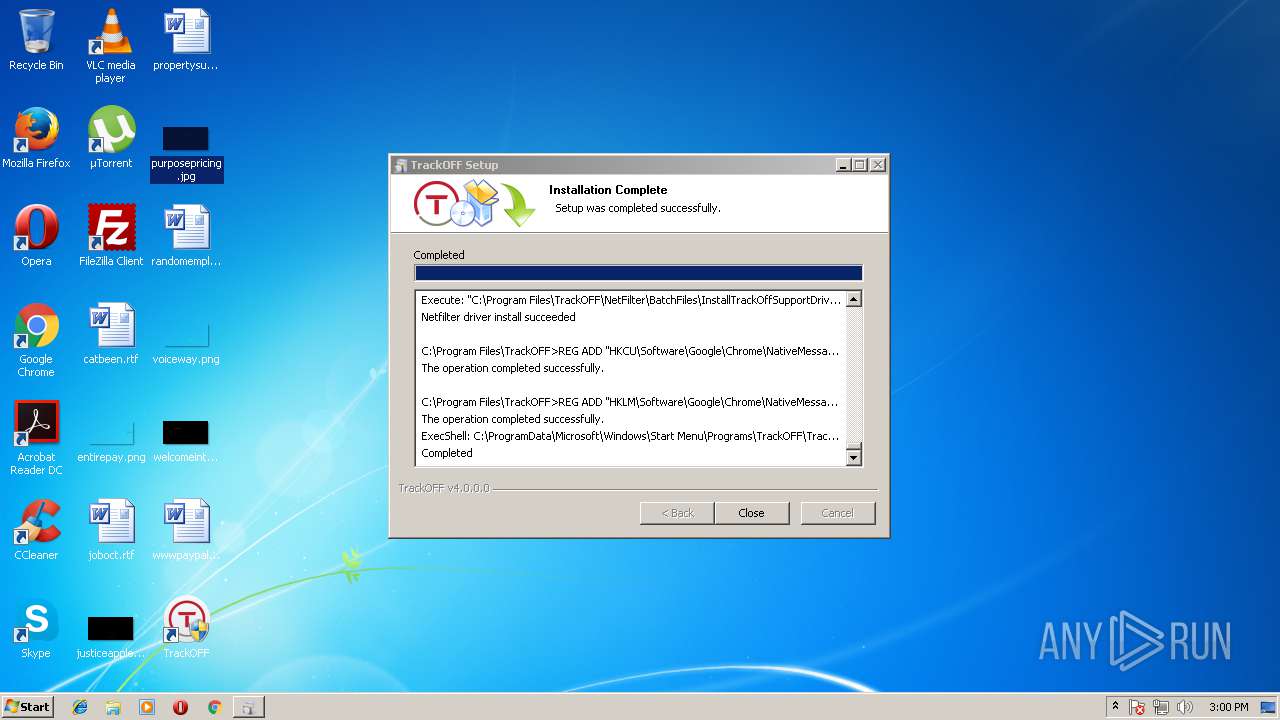
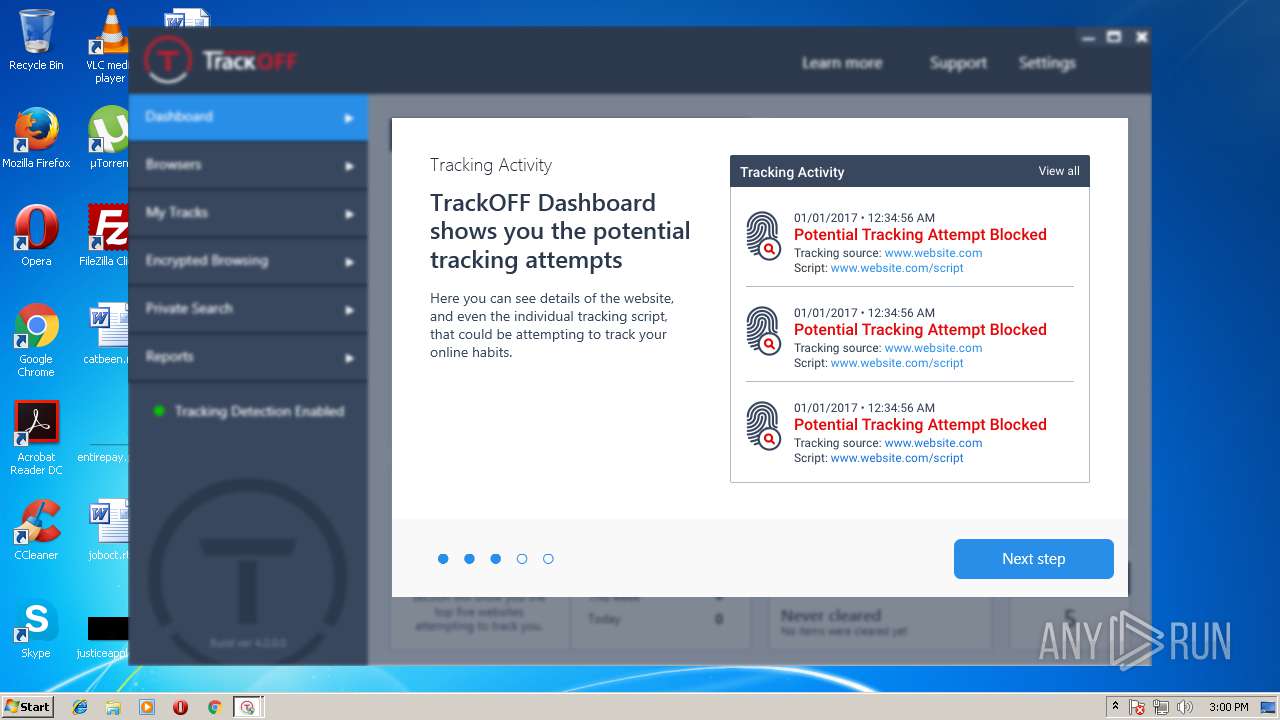
| download: | clicador_2.1.0.4.exe |
| Full analysis: | https://app.any.run/tasks/3069ed39-0303-4005-9f68-27dbcc59692b |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2018, 13:56:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | C996E5F2E6E616843453B24966ACB5B4 |
| SHA1: | D63E2E8320815C7AAA6AEC3C5D9C4D75EEAC4A67 |
| SHA256: | 9CE06BD5E0403289097D36A4F050DD9B2BED5B32892DF3068CC2C9C410603F6C |
| SSDEEP: | 12288:mrlMKUAbpMopS5fO39k2Tbdw/EcKZoQFavEvGg8g8It54gAMC5QBl:mRM0bpMopM4kZ8rFME+Fgv+T2Bl |
MALICIOUS
Changes settings of System certificates
- devcon32.exe (PID: 2896)
Uses Task Scheduler to run other applications
- ns940D.tmp (PID: 2968)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 3904)
SUSPICIOUS
Application launched itself
- software_reporter_tool.exe (PID: 2920)
Creates or modifies windows services
- TrackOFF (1).exe (PID: 2740)
- DrvInst.exe (PID: 3960)
- nfregdrv.exe (PID: 1436)
- DrvInst.exe (PID: 976)
- TrackOFFFilter.exe (PID: 3508)
- TrackOFFFilter.exe (PID: 3364)
Creates a software uninstall entry
- TrackOFF (1).exe (PID: 2740)
- TrackOFFApplication.exe (PID: 3228)
Starts application with an unusual extension
- TrackOFF (1).exe (PID: 2740)
Starts Microsoft Installer
- SQLServerCompactInstaller.exe (PID: 2640)
Creates files in the program directory
- SQLServerCompactInstaller.exe (PID: 2640)
- TrackOFF (1).exe (PID: 2740)
- TrackOFFApplication.exe (PID: 3228)
- EKAG20NT.EXE (PID: 3860)
Creates COM task schedule object
- msiexec.exe (PID: 3192)
Starts CMD.EXE for commands execution
- ns24B6.tmp (PID: 916)
- InstallTrackOffSupportDrivers_x86.exe (PID: 2744)
- ns9844.tmp (PID: 3300)
Creates files in the Windows directory
- devcon32.exe (PID: 2896)
- DrvInst.exe (PID: 3960)
- msiexec.exe (PID: 3192)
- DrvInst.exe (PID: 976)
- cmd.exe (PID: 4036)
Creates files in the driver directory
- DrvInst.exe (PID: 976)
- DrvInst.exe (PID: 3960)
- cmd.exe (PID: 4036)
Removes files from Windows directory
- DrvInst.exe (PID: 3960)
- DrvInst.exe (PID: 976)
Adds / modifies Windows certificates
- devcon32.exe (PID: 2896)
Creates files in the user directory
- TrackOFFApplication.exe (PID: 3228)
- TrackOFFApplication.exe (PID: 3808)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 900)
Searches for installed software
- TrackOFFApplication.exe (PID: 3228)
- TrackOFFApplication.exe (PID: 3808)
INFO
Application launched itself
- chrome.exe (PID: 1540)
- msiexec.exe (PID: 3192)
Dropped object may contain URL's
- chrome.exe (PID: 1540)
Loads the Task Scheduler COM API
- software_reporter_tool.exe (PID: 2920)
Creates files in the user directory
- chrome.exe (PID: 1540)
Creates files in the program directory
- msiexec.exe (PID: 3192)
Creates or modifies windows services
- msiexec.exe (PID: 3192)
- vssvc.exe (PID: 128)
Low-level read access rights to disk partition
- vssvc.exe (PID: 128)
Reads settings of System Certificates
- DrvInst.exe (PID: 3536)
- TrackOFFApplication.exe (PID: 3808)
- TrackOFFApplication.exe (PID: 3228)
Creates a software uninstall entry
- msiexec.exe (PID: 3192)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2015:12:31 15:25:58+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 155648 |
| InitializedDataSize: | 51712 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x245ca |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 15.14.0.0 |
| ProductVersionNumber: | 15.14.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Windows NT 32-bit |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Igor Pavlov |
| FileDescription: | 7z SFX |
| FileVersion: | 15.14 |
| InternalName: | 7z.sfx |
| LegalCopyright: | Copyright (c) 1999-2015 Igor Pavlov |
| OriginalFileName: | 7z.sfx.exe |
| ProductName: | 7-Zip |
| ProductVersion: | 15.14 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 31-Dec-2015 14:25:58 |
| Detected languages: |
|
| CompanyName: | Igor Pavlov |
| FileDescription: | 7z SFX |
| FileVersion: | 15.14 |
| InternalName: | 7z.sfx |
| LegalCopyright: | Copyright (c) 1999-2015 Igor Pavlov |
| OriginalFilename: | 7z.sfx.exe |
| ProductName: | 7-Zip |
| ProductVersion: | 15.14 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000100 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 31-Dec-2015 14:25:58 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00025E95 | 0x00026000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.66188 |
.rdata | 0x00027000 | 0x00005EE0 | 0x00006000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.34353 |
.data | 0x0002D000 | 0x0000457C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.95587 |
.sxdata | 0x00032000 | 0x00000004 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_LNK_INFO, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0.0203931 |
.rsrc | 0x00033000 | 0x00002090 | 0x00002200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 3.15518 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.44 | 688 | UNKNOWN | English - United States | RT_VERSION |
2 | 1.68942 | 296 | UNKNOWN | English - United States | RT_ICON |
26 | 1.80688 | 62 | UNKNOWN | English - United States | RT_STRING |
28 | 1.93734 | 66 | UNKNOWN | English - United States | RT_STRING |
29 | 2.18408 | 96 | UNKNOWN | English - United States | RT_STRING |
64 | 1.20724 | 48 | UNKNOWN | English - United States | RT_STRING |
97 | 3.34731 | 1088 | UNKNOWN | English - United States | RT_DIALOG |
188 | 3.1595 | 524 | UNKNOWN | English - United States | RT_STRING |
189 | 2.80372 | 228 | UNKNOWN | English - United States | RT_STRING |
207 | 1.43775 | 52 | UNKNOWN | English - United States | RT_STRING |
Imports
KERNEL32.dll |
MSVCRT.dll |
OLEAUT32.dll |
SHELL32.dll |
USER32.dll |
ole32.dll |
Total processes
97
Monitored processes
48
Malicious processes
6
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 128 | C:\Windows\system32\vssvc.exe | C:\Windows\system32\vssvc.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 860 | REG ADD "HKCU\Software\Google\Chrome\NativeMessagingHosts\com.google.chrome.example.echo" /ve /t REG_SZ /d "C:\Users\admin\AppData\Local\TrackOFF\Support\ChromeExtension\com.google.chrome.example.echo-win.json" /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 900 | cmd /c C:\Users\admin\AppData\Local\TrackOFF\Support\ChromeExtension\install_host.bat /S | C:\Windows\system32\cmd.exe | — | ns9844.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 916 | "C:\Users\admin\AppData\Local\Temp\nskB8CB.tmp\ns24B6.tmp" "C:\Program Files\TrackOFF\open_vpn_driver\addtaptrackoff.bat" | C:\Users\admin\AppData\Local\Temp\nskB8CB.tmp\ns24B6.tmp | — | TrackOFF (1).exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 976 | DrvInst.exe "2" "211" "ROOT\NET\0000" "C:\Windows\INF\oem4.inf" "oemvista.inf:tap0901:tap0901.ndi:9.0.0.21:tap0901" "6d14a44ff" "000005A4" "0000057C" "000004D4" | C:\Windows\system32\DrvInst.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Driver Installation Module Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1008 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1588,9628061844537207705,16855258831288847541,131072 --service-pipe-token=7FA78CA182ADE0AA1917F663F0AC6212 --lang=en-US --disable-client-side-phishing-detection --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --enable-pinch --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --content-image-texture-target=0,0,3553;0,1,3553;0,2,3553;0,3,3553;0,4,3553;0,5,3553;0,6,3553;0,7,3553;0,8,3553;0,9,3553;0,10,3553;0,11,3553;0,12,3553;0,13,3553;0,14,3553;0,15,3553;0,16,3553;0,17,3553;1,0,3553;1,1,3553;1,2,3553;1,3,3553;1,4,3553;1,5,3553;1,6,3553;1,7,3553;1,8,3553;1,9,3553;1,10,3553;1,11,3553;1,12,3553;1,13,3553;1,14,3553;1,15,3553;1,16,3553;1,17,3553;2,0,3553;2,1,3553;2,2,3553;2,3,3553;2,4,3553;2,5,3553;2,6,3553;2,7,3553;2,8,3553;2,9,3553;2,10,3553;2,11,3553;2,12,3553;2,13,3553;2,14,3553;2,15,3553;2,16,3553;2,17,3553;3,0,3553;3,1,3553;3,2,3553;3,3,3553;3,4,3553;3,5,3553;3,6,3553;3,7,3553;3,8,3553;3,9,3553;3,10,3553;3,11,3553;3,12,3553;3,13,3553;3,14,3553;3,15,3553;3,16,3553;3,17,3553;4,0,3553;4,1,3553;4,2,3553;4,3,3553;4,4,3553;4,5,3553;4,6,3553;4,7,3553;4,8,3553;4,9,3553;4,10,3553;4,11,3553;4,12,3553;4,13,3553;4,14,3553;4,15,3553;4,16,3553;4,17,3553 --disable-accelerated-video-decode --disable-gpu-compositing --enable-gpu-async-worker-context --service-request-channel-token=7FA78CA182ADE0AA1917F663F0AC6212 --renderer-client-id=4 --mojo-platform-channel-handle=1600 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 61.0.3163.100 Modules
| |||||||||||||||
| 1252 | devcon32 remove tap0901 | C:\Program Files\TrackOFF\open_vpn_driver\devcon32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Setup API Exit code: 0 Version: 6.1.7600.16385 (win7_wdk.100208-1538) Modules
| |||||||||||||||
| 1348 | C:\Windows\system32\MsiExec.exe -Embedding 38590312D7F7A5B72447C1DF2E1C2BD9 M Global\MSI0000 | C:\Windows\system32\MsiExec.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1436 | release\win32\nfregdrv.exe netfilter2 | C:\Program Files\TrackOFF\NetFilter\BatchFiles\release\win32\nfregdrv.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1524 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=3520 --on-initialized-event-handle=296 --parent-handle=300 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 61.0.3163.100 Modules
| |||||||||||||||
Total events
3 391
Read events
1 959
Write events
1 359
Delete events
73
Modification events
| (PID) Process: | (1524) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 1540-13170952631082375 |
Value: 259 | |||
| (PID) Process: | (1540) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1540) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1540) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1540) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1540) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 1 | |||
| (PID) Process: | (1540) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3708-13168704147815429 |
Value: 0 | |||
| (PID) Process: | (1540) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (1540) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 1540-13170952631082375 |
Value: 259 | |||
| (PID) Process: | (1540) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | metricsid |
Value: | |||
Executable files
0
Suspicious files
29
Text files
37
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000040.dbtmp | — | |
MD5:— | SHA256:— | |||
| 1540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\a32319c3-60f3-44ef-9c65-da2771077a17.tmp | — | |
MD5:— | SHA256:— | |||
| 1540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\IndexedDB\https_www.google.ru_0.indexeddb.leveldb\000001.dbtmp | — | |
MD5:— | SHA256:— | |||
| 1540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad\settings.dat | binary | |
MD5:— | SHA256:— | |||
| 1540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Cache\f_000002 | binary | |
MD5:— | SHA256:— | |||
| 1540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Session Storage\000001.dbtmp | — | |
MD5:— | SHA256:— | |||
| 1540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Local Storage\leveldb\LOG.old~RF1457b3.TMP | text | |
MD5:— | SHA256:— | |||
| 1540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Extension State\LOG.old | text | |
MD5:— | SHA256:— | |||
| 1540 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Extension Settings\pkedcjkdefgpdelpbcmbmeomcjbeemfm\LOG.old | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
12
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3228 | TrackOFFApplication.exe | POST | — | 104.236.103.61:80 | http://104.236.103.61/reportfirstrun.php | US | — | — | unknown |
3228 | TrackOFFApplication.exe | POST | 200 | 104.236.103.61:80 | http://104.236.103.61/reportactivate.php | US | text | 113 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1540 | chrome.exe | 172.217.18.3:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
1540 | chrome.exe | 172.217.23.163:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
1540 | chrome.exe | 104.20.42.6:443 | trackoff.com | Cloudflare Inc | US | shared |
3228 | TrackOFFApplication.exe | 104.236.103.61:80 | — | Digital Ocean, Inc. | US | unknown |
1540 | chrome.exe | 172.217.23.132:443 | www.google.com | Google Inc. | US | whitelisted |
1540 | chrome.exe | 172.217.16.206:443 | clients4.google.com | Google Inc. | US | whitelisted |
1540 | chrome.exe | 216.58.207.35:443 | www.google.ru | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
www.google.ru |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
trackoff.com |
| unknown |
www.google.com |
| malicious |
clients4.google.com |
| whitelisted |
Threats
Process | Message |
|---|---|
TrackOFFApplication.exe | Native library pre-loader is trying to load native SQLite library "C:\Program Files\TrackOFF\x86\SQLite.Interop.dll"...
|
TrackOFFApplication.exe | SQLite error (14): os_win.c:42250: (3) winOpen(C:\Users\admin\AppData\Roaming\Opera Software\Opera Stable\Cookies) - The system cannot find the path specified.
|
TrackOFFApplication.exe | SQLite error (14): os_win.c:42250: (3) winOpen(C:\Users\admin\AppData\Roaming\Opera Software\Opera Stable\Cookies) - The system cannot find the path specified.
|
TrackOFFApplication.exe | SQLite error (14): cannot open file at line 42259 of [bbd85d235f]
|
TrackOFFApplication.exe | SQLite error (14): os_win.c:42250: (3) winOpen(C:\Users\admin\AppData\Roaming\Opera Software\Opera Stable\Cookies) - The system cannot find the path specified.
|
TrackOFFApplication.exe | SQLite error (14): os_win.c:42250: (3) winOpen(C:\Users\admin\AppData\Roaming\Opera Software\Opera Stable\Cookies) - The system cannot find the path specified.
|
TrackOFFApplication.exe | SQLite error (14): cannot open file at line 42259 of [bbd85d235f]
|
TrackOFFApplication.exe | SQLite error (14): os_win.c:42250: (3) winOpen(C:\Users\admin\AppData\Roaming\Opera Software\Opera Stable\Cookies) - The system cannot find the path specified.
|
TrackOFFApplication.exe | SQLite error (14): os_win.c:42250: (3) winOpen(C:\Users\admin\AppData\Roaming\Opera Software\Opera Stable\Cookies) - The system cannot find the path specified.
|
TrackOFFApplication.exe | SQLite error (14): cannot open file at line 42259 of [bbd85d235f]
|