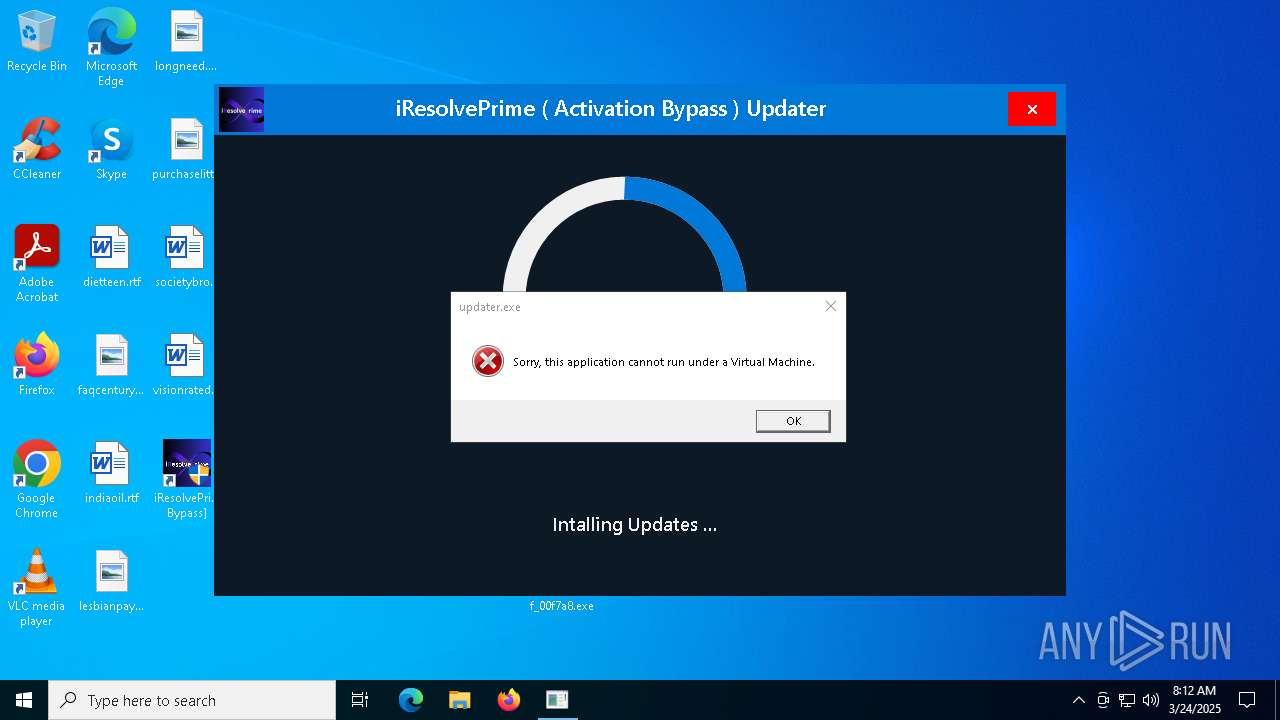
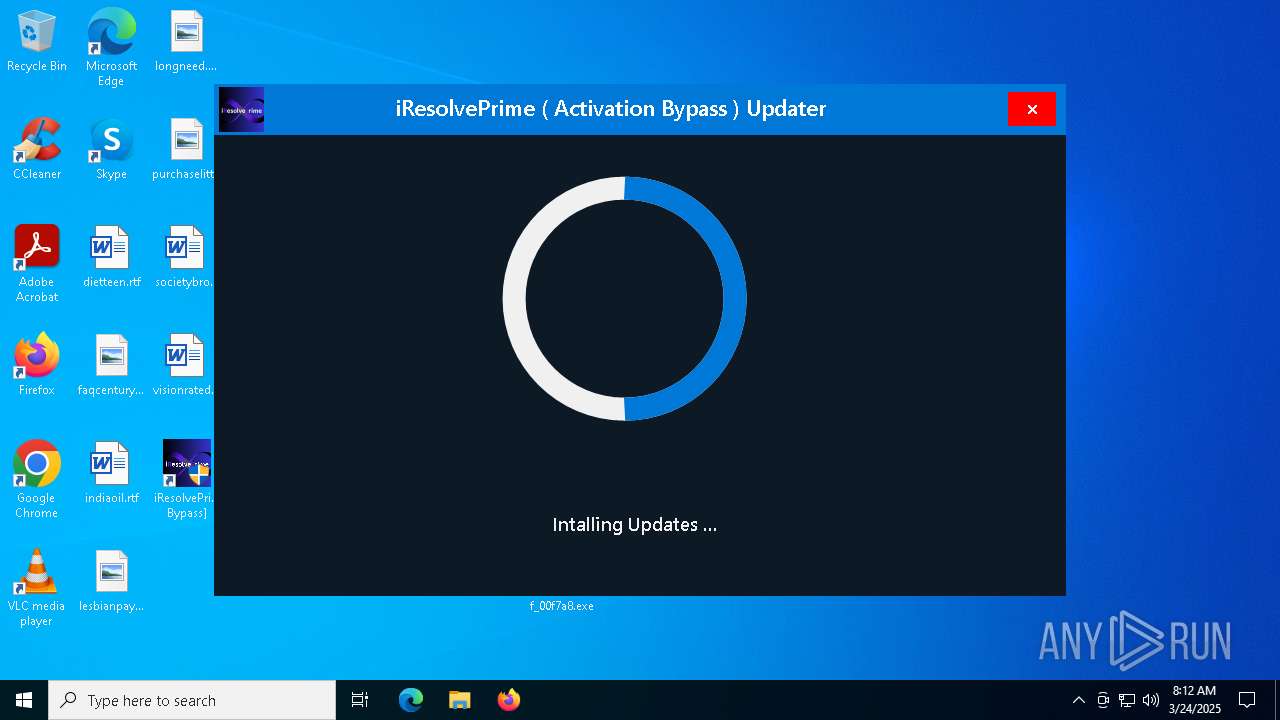
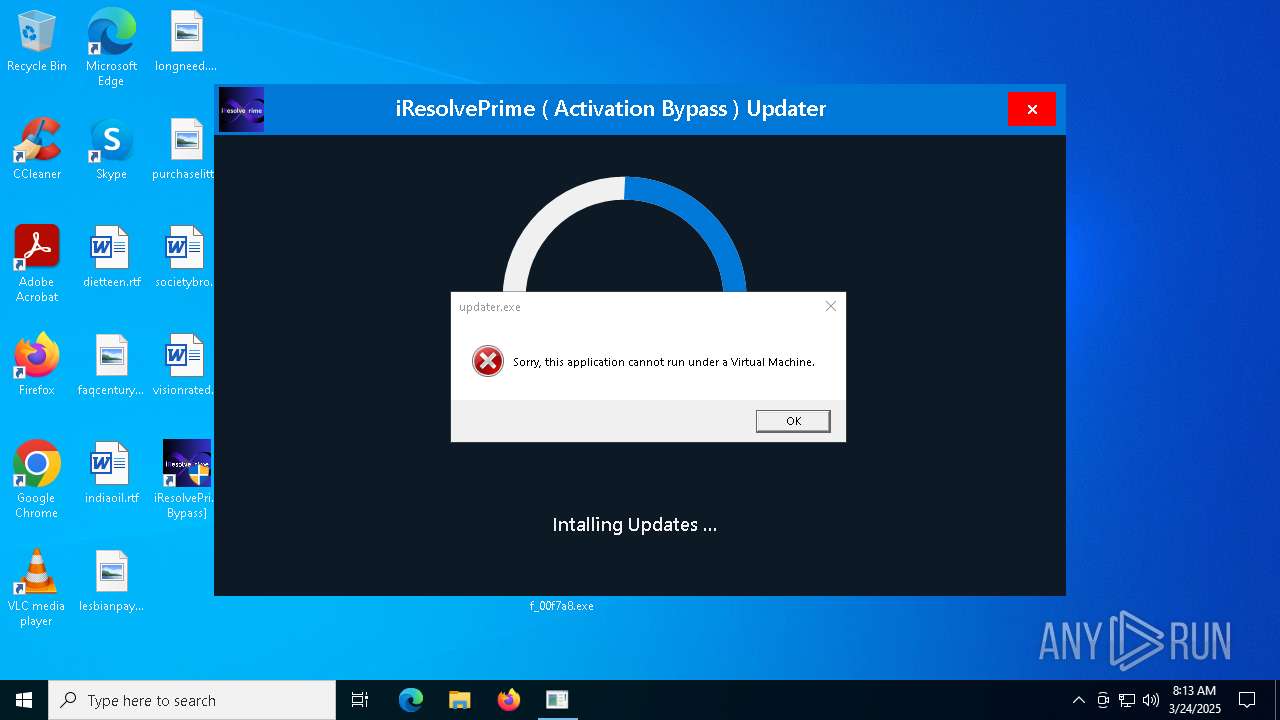
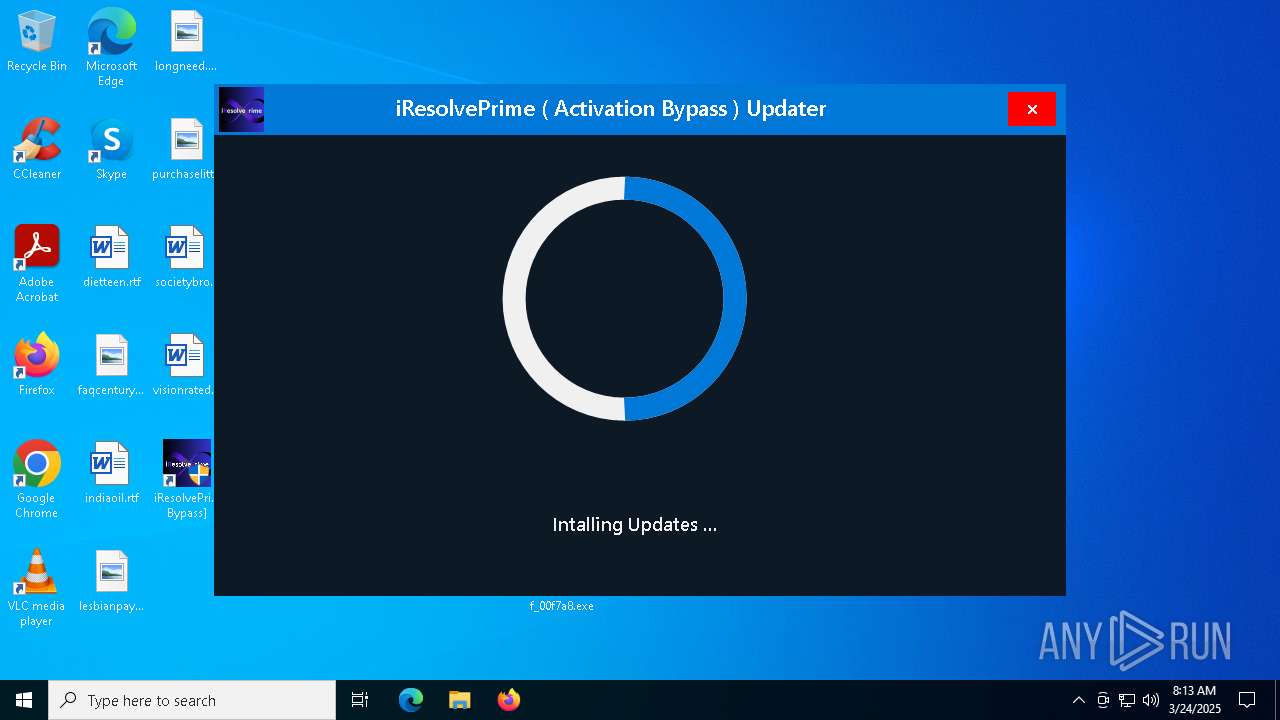
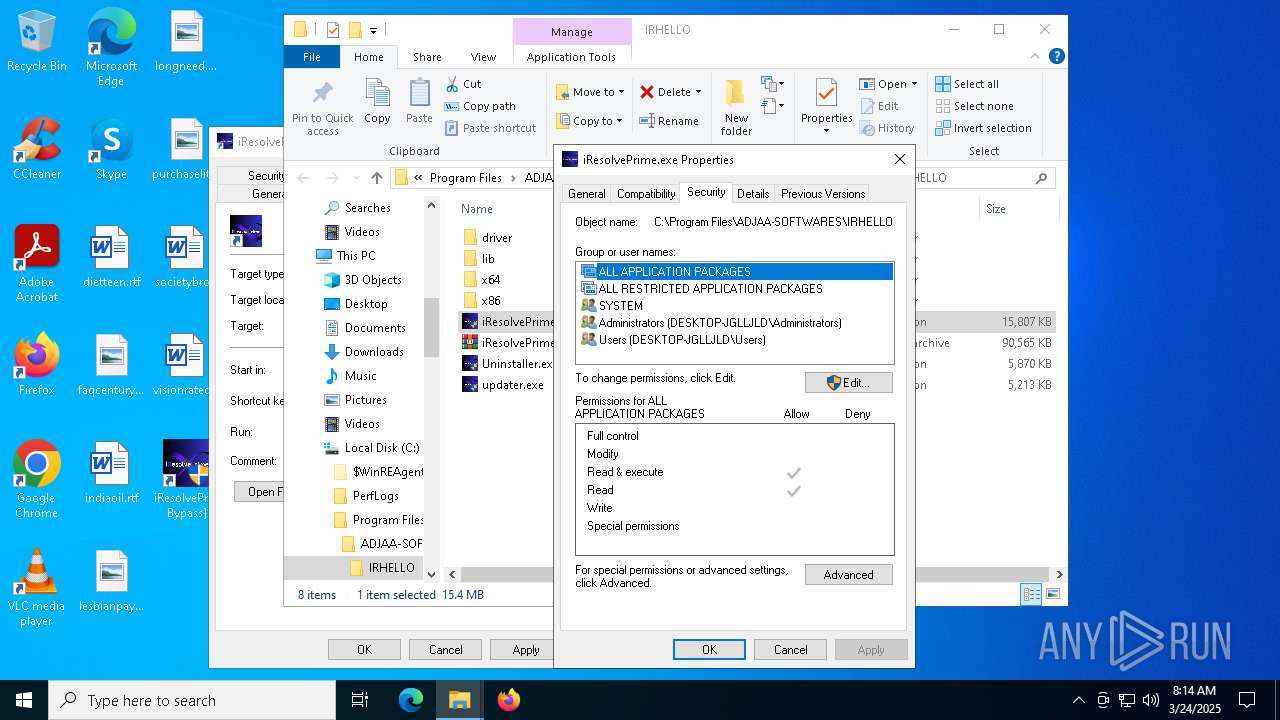
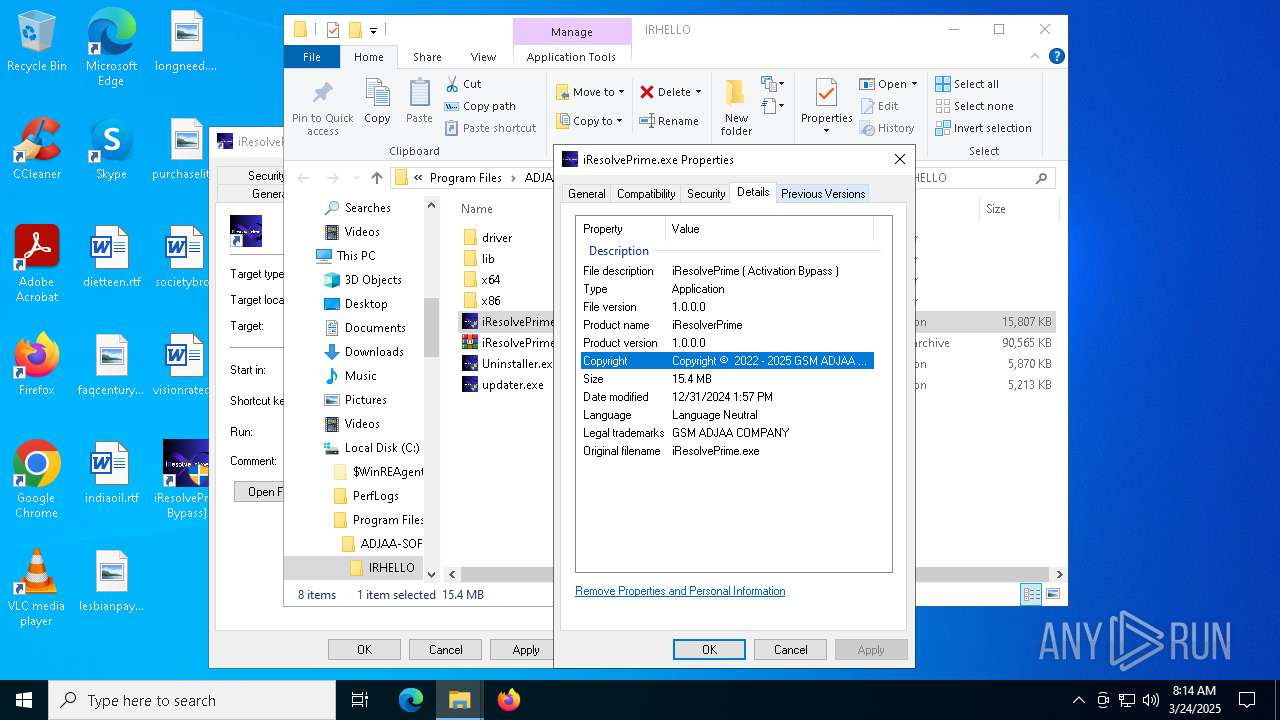
| File name: | MDE_File_Sample_f58abdb5e8a7b5d3358d3fdb3bd758369d4fd0a0.zip |
| Full analysis: | https://app.any.run/tasks/6f474ccb-79b7-4be3-ba52-f29825d01f1d |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 08:10:51 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | F69B3061F528EB6395C0F15E64D000C2 |
| SHA1: | 869C404C3CAA34324E361184661B1A4BC19E1D68 |
| SHA256: | 9CC6BFD4A0D33A2C9056A292D6E17FEEAA5DF391612A76CF56560DC597F9D6B8 |
| SSDEEP: | 98304:of7T2slHjal/oZlwG9B/yPs3d00u04mbQ22LBZVGnB/yZkdKEJ5lvKJoUNPGqopD:q63c1MP9Na |
MALICIOUS
Executing a file with an untrusted certificate
- f_00f7a8.exe (PID: 4224)
- f_00f7a8.exe (PID: 6436)
- f_00f7a8.exe (PID: 5548)
- f_00f7a8.exe (PID: 8156)
Changes Windows Defender settings
- cmd.exe (PID: 7400)
- cmd.exe (PID: 7504)
- cmd.exe (PID: 7760)
- cmd.exe (PID: 6768)
- cmd.exe (PID: 8024)
- cmd.exe (PID: 4892)
- cmd.exe (PID: 1072)
- cmd.exe (PID: 5232)
Changes settings for real-time protection
- powershell.exe (PID: 1328)
- powershell.exe (PID: 7832)
- powershell.exe (PID: 5720)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 7504)
- cmd.exe (PID: 4892)
- cmd.exe (PID: 1072)
- cmd.exe (PID: 5232)
XORed URL has been found (YARA)
- f_00f7a8.exe (PID: 6436)
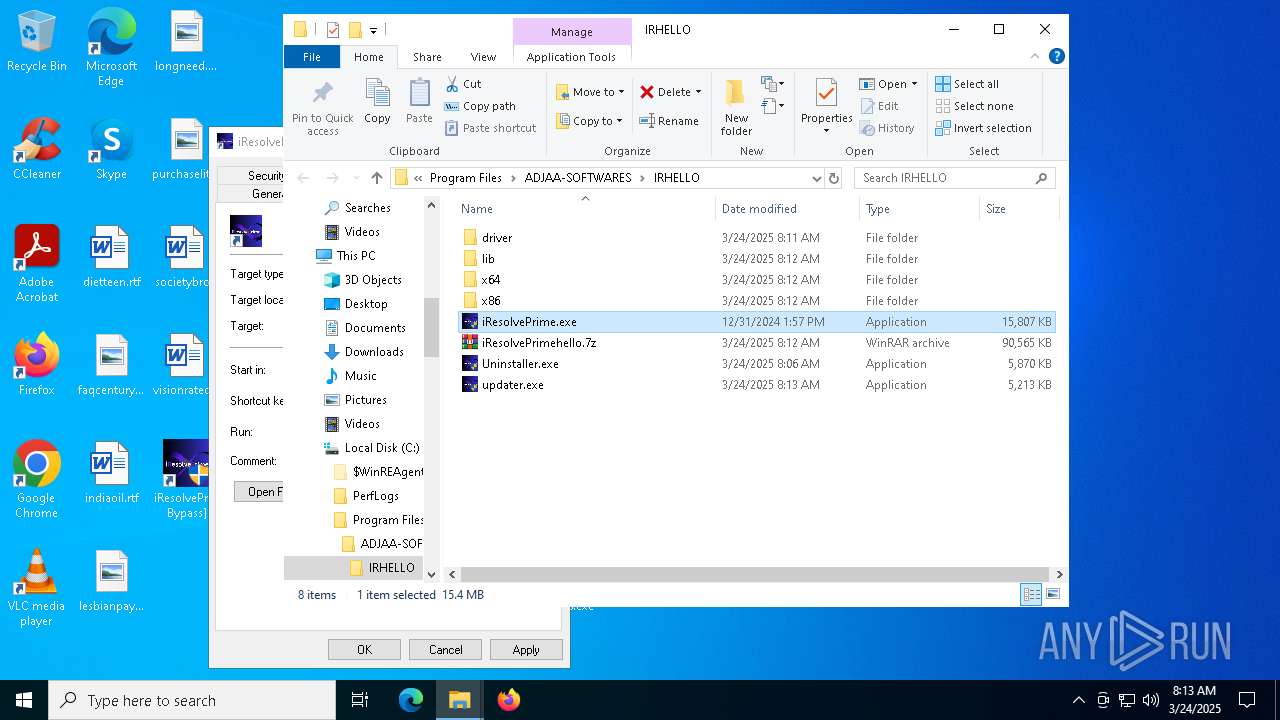
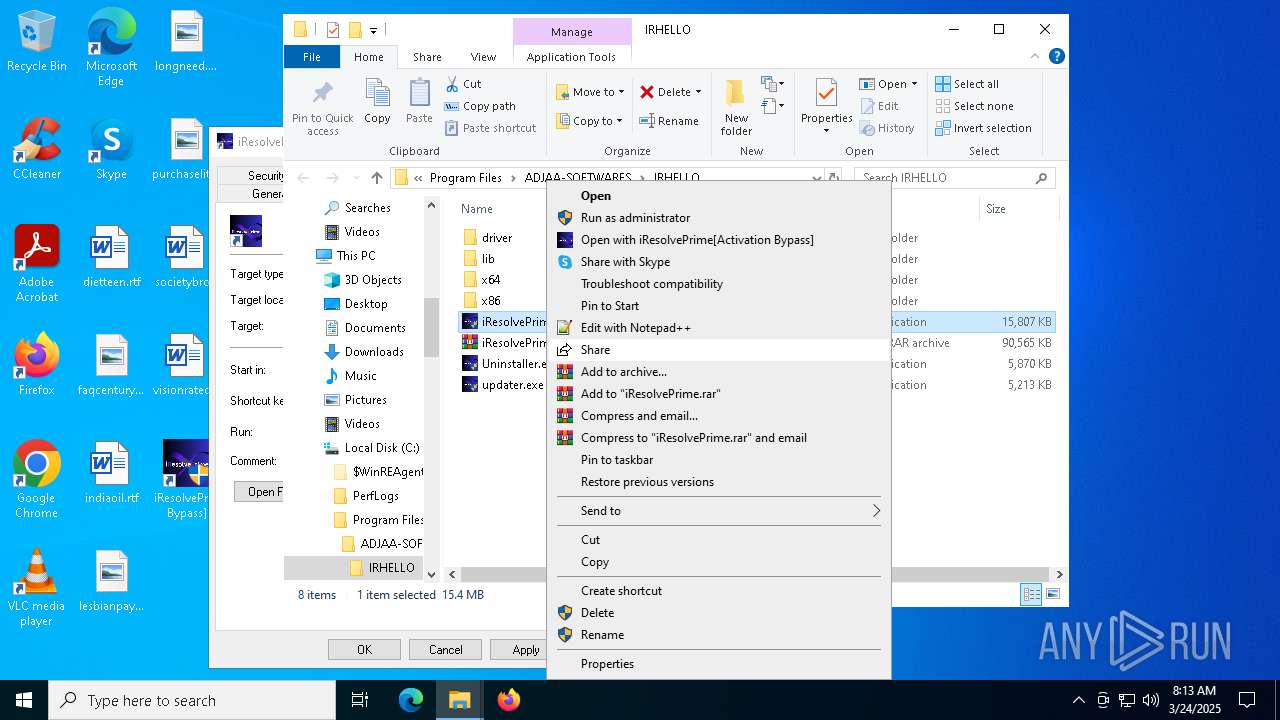
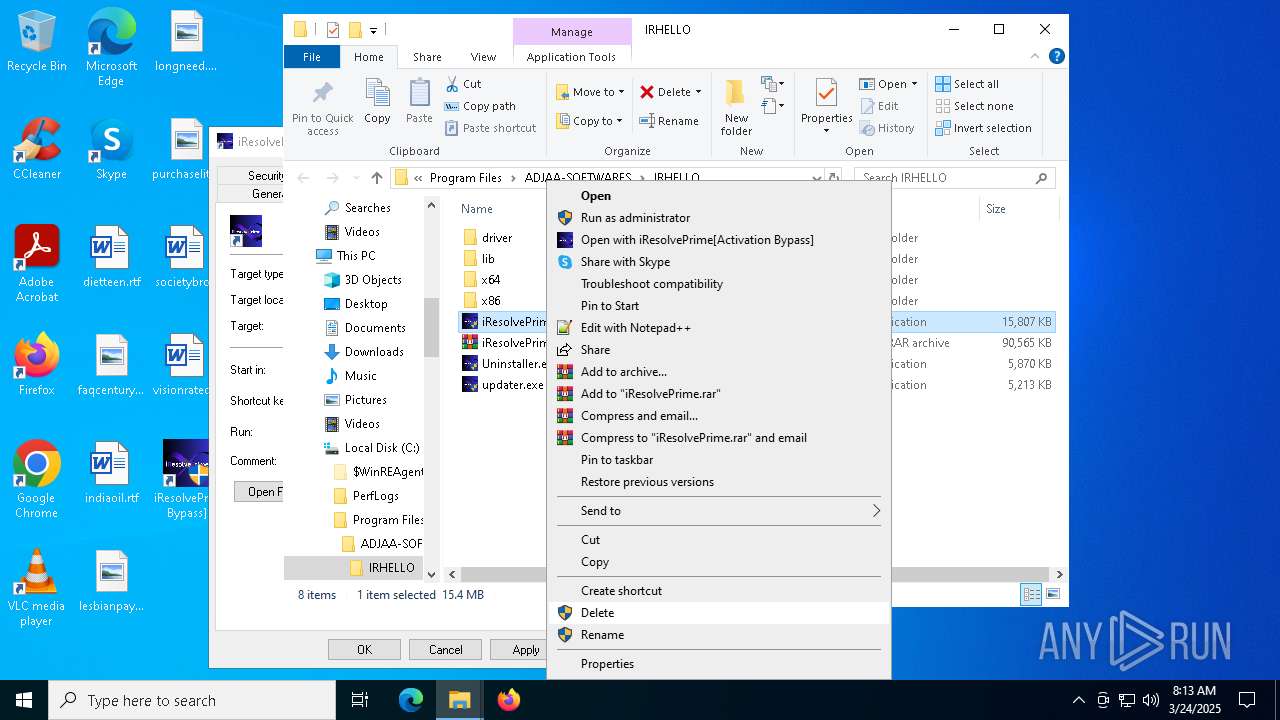
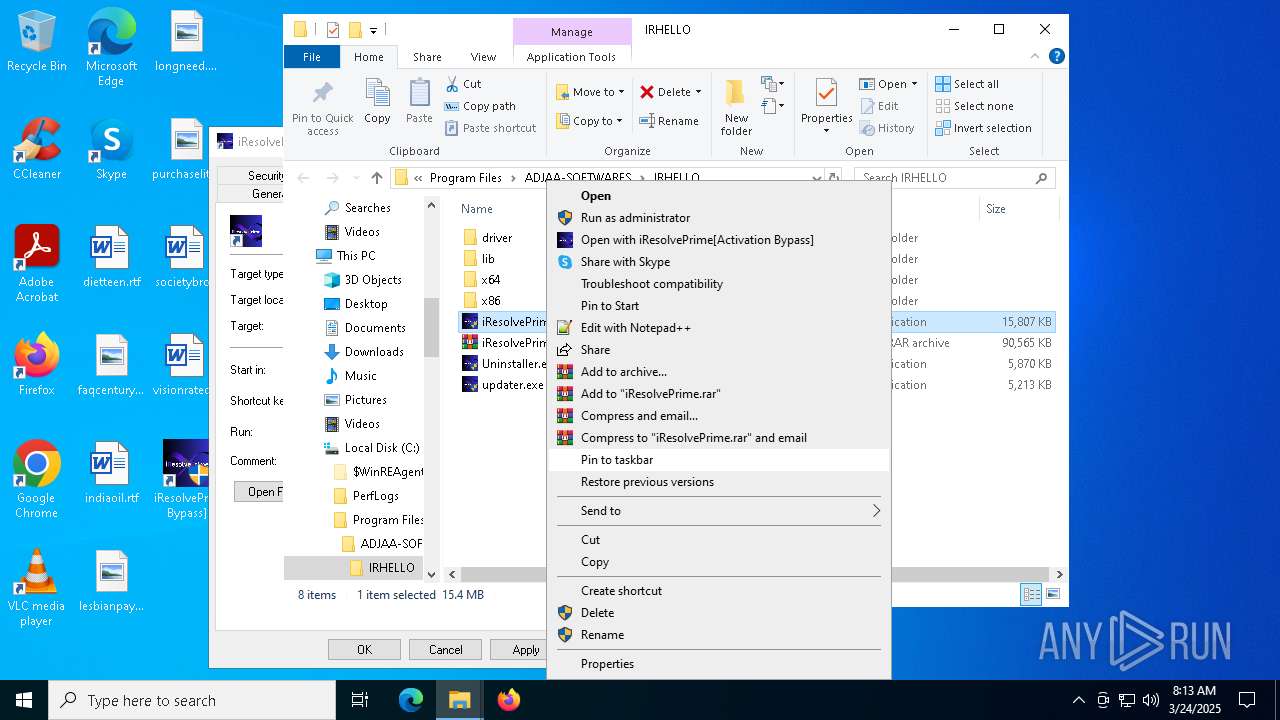
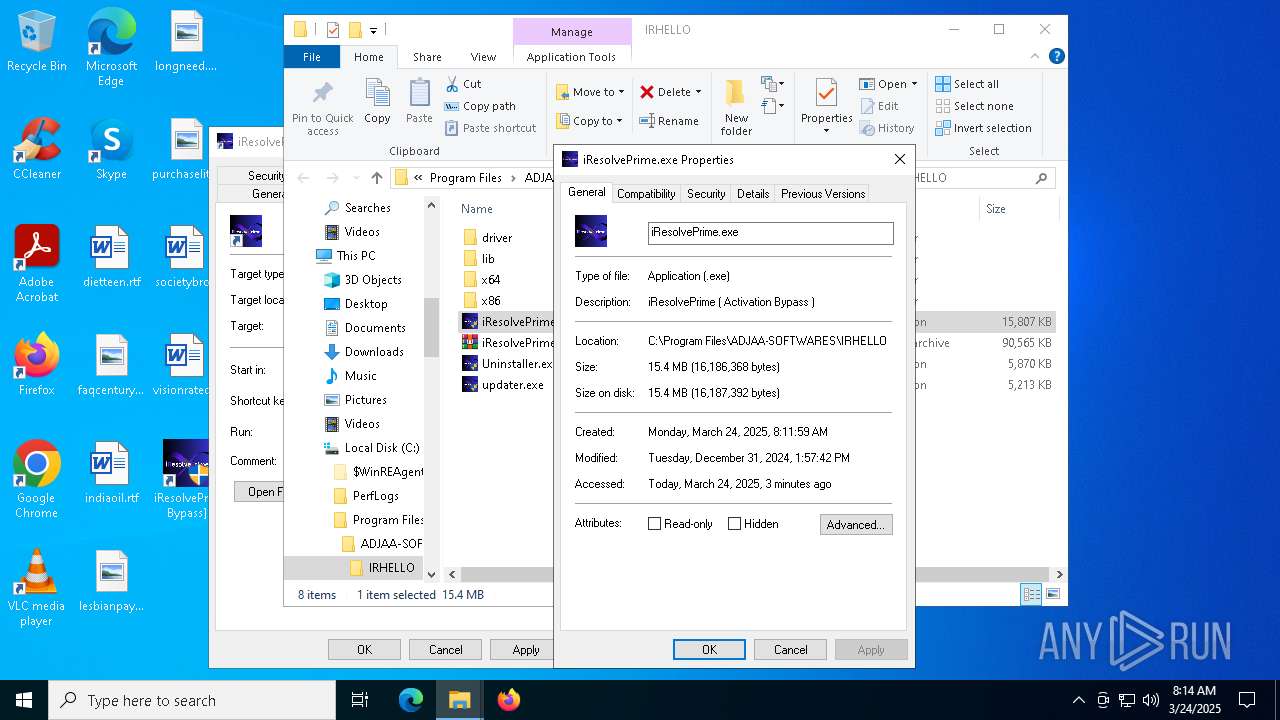
- iResolvePrime.exe (PID: 7892)
- iResolvePrime.exe (PID: 2096)
Adds process to the Windows Defender exclusion list
- cmd.exe (PID: 7760)
SUSPICIOUS
Starts CMD.EXE for commands execution
- f_00f7a8.exe (PID: 6436)
- iResolvePrime.exe (PID: 7892)
- iResolvePrime.exe (PID: 2096)
Script disables Windows Defender's real-time protection
- cmd.exe (PID: 7400)
- cmd.exe (PID: 6768)
- cmd.exe (PID: 8024)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7400)
- cmd.exe (PID: 7504)
- cmd.exe (PID: 7760)
- cmd.exe (PID: 6768)
- cmd.exe (PID: 8024)
- cmd.exe (PID: 4892)
- cmd.exe (PID: 1072)
- cmd.exe (PID: 5232)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 7504)
- cmd.exe (PID: 4892)
- cmd.exe (PID: 1072)
- cmd.exe (PID: 5232)
Script adds exclusion process to Windows Defender
- cmd.exe (PID: 7760)
Executable content was dropped or overwritten
- f_00f7a8.exe (PID: 6436)
- iResolvePrime.exe (PID: 2096)
Reads security settings of Internet Explorer
- ShellExperienceHost.exe (PID: 7404)
- f_00f7a8.exe (PID: 6436)
- iResolvePrime.exe (PID: 7892)
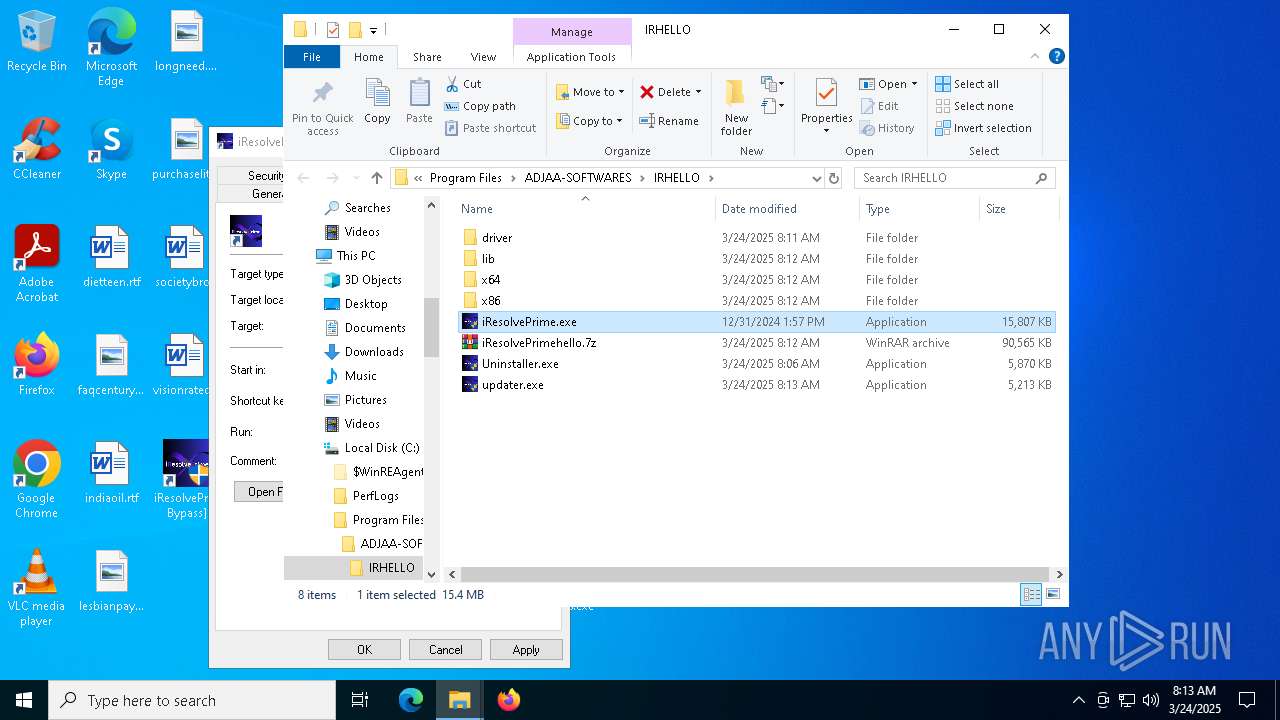
Drops 7-zip archiver for unpacking
- f_00f7a8.exe (PID: 6436)
Drops a system driver (possible attempt to evade defenses)
- f_00f7a8.exe (PID: 6436)
Process drops legitimate windows executable
- f_00f7a8.exe (PID: 6436)
The process drops C-runtime libraries
- f_00f7a8.exe (PID: 6436)
Process drops SQLite DLL files
- f_00f7a8.exe (PID: 6436)
There is functionality for taking screenshot (YARA)
- iResolvePrime.exe (PID: 7892)
- iResolvePrime.exe (PID: 2096)
Reads the date of Windows installation
- iResolvePrime.exe (PID: 7892)
INFO
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 7684)
Manual execution by a user
- f_00f7a8.exe (PID: 6436)
- f_00f7a8.exe (PID: 4224)
- f_00f7a8.exe (PID: 5548)
- f_00f7a8.exe (PID: 8156)
- iResolvePrime.exe (PID: 6800)
- iResolvePrime.exe (PID: 2096)
Checks supported languages
- f_00f7a8.exe (PID: 6436)
- f_00f7a8.exe (PID: 5548)
- ShellExperienceHost.exe (PID: 7404)
- iResolvePrime.exe (PID: 7892)
- updater.exe (PID: 7972)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 660)
- BackgroundTransferHost.exe (PID: 7472)
- BackgroundTransferHost.exe (PID: 8076)
- BackgroundTransferHost.exe (PID: 7848)
- BackgroundTransferHost.exe (PID: 7684)
Checks proxy server information
- BackgroundTransferHost.exe (PID: 7684)
- f_00f7a8.exe (PID: 6436)
- iResolvePrime.exe (PID: 7892)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 7684)
- iResolvePrime.exe (PID: 2096)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2384)
Reads the computer name
- f_00f7a8.exe (PID: 6436)
- ShellExperienceHost.exe (PID: 7404)
- updater.exe (PID: 7972)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 1328)
- powershell.exe (PID: 5504)
- powershell.exe (PID: 7896)
- powershell.exe (PID: 7832)
- powershell.exe (PID: 5720)
- powershell.exe (PID: 6392)
- powershell.exe (PID: 8092)
- powershell.exe (PID: 900)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 5504)
- powershell.exe (PID: 7896)
- powershell.exe (PID: 1328)
- powershell.exe (PID: 7832)
- powershell.exe (PID: 5720)
- powershell.exe (PID: 6392)
- powershell.exe (PID: 8092)
- powershell.exe (PID: 900)
Creates files in the program directory
- f_00f7a8.exe (PID: 6436)
- iResolvePrime.exe (PID: 7892)
- iResolvePrime.exe (PID: 2096)
Reads the machine GUID from the registry
- f_00f7a8.exe (PID: 6436)
- iResolvePrime.exe (PID: 7892)
Disables trace logs
- f_00f7a8.exe (PID: 6436)
- iResolvePrime.exe (PID: 7892)
The sample compiled with english language support
- f_00f7a8.exe (PID: 6436)
The sample compiled with arabic language support
- f_00f7a8.exe (PID: 6436)
SQLite executable
- f_00f7a8.exe (PID: 6436)
Process checks computer location settings
- f_00f7a8.exe (PID: 6436)
- iResolvePrime.exe (PID: 7892)
Reads Environment values
- iResolvePrime.exe (PID: 7892)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
xor-url
(PID) Process(6436) f_00f7a8.exe
Decrypted-URLs (3)https://gsmadjaa.com/support/
https://gsmadjaa.xyz/update/iResolvehello.php
https://iresolveprime.gsmadjaa.com/bypassicloud.php
(PID) Process(7892) iResolvePrime.exe
Decrypted-URLs (19)http://schemas.microsoft.com/SMI/2005/WindowsSettings
http://schemas.microsoft.com/SMI/2016/WindowsSettings
https://api.ipify.org/
https://api.telegram.org/bot5272081738:AAH33Xu6C6bDaVvQKJI-xMldq7fZBYLz3oE/sendMessage?chat_id=...........&text=
https://api.telegram.org/bot6267929589:AAH6aAM4MgRB871zlKxLAVEjaGk-Z61vKHM/sendMessage?chat_id=2121212318&text=
https://api64.ipify.org
https://docs.microsoft.com/windows/win32/fileio/maximum-file-path-limitation
https://gsmadjaa.com/checkout/index.php?type=iresolvehello&sft=aVJlc29sdmVQcmltZSAoQWN0aXZhdGlvbiBCeXBhc3Mp&init=
https://gsmadjaa.com/iressource/model.php?read=
https://gsmadjaa.com/panel/
https://gsmadjaa.xyz/data/adjaa.dll
https://gsmadjaa.xyz/pc/mac.php?mac_key=
https://gsmadjaa.xyz/update/iResolvePrimehello.7z
https://gsmadjaa.xyz/update/iResolvehello.php
https://gsmadjaa.xyz/update/irtest.txt
https://software.gsmadjaa.com/
https://t.me/gsmadjaa2005
https://t.me/iResolvePrime
https://www.trustpilot.com/evaluate/gsmadjaa.com?utm_source=Trustpilot&utm_medium=email&utm_campaign=trustpilot_email
(PID) Process(2096) iResolvePrime.exe
Decrypted-URLs (19)http://schemas.microsoft.com/SMI/2005/WindowsSettings
http://schemas.microsoft.com/SMI/2016/WindowsSettings
https://api.ipify.org/
https://api.telegram.org/bot5272081738:AAH33Xu6C6bDaVvQKJI-xMldq7fZBYLz3oE/sendMessage?chat_id=...........&text=
https://api.telegram.org/bot6267929589:AAH6aAM4MgRB871zlKxLAVEjaGk-Z61vKHM/sendMessage?chat_id=2121212318&text=
https://api64.ipify.org
https://docs.microsoft.com/windows/win32/fileio/maximum-file-path-limitation
https://gsmadjaa.com/checkout/index.php?type=iresolvehello&sft=aVJlc29sdmVQcmltZSAoQWN0aXZhdGlvbiBCeXBhc3Mp&init=
https://gsmadjaa.com/iressource/model.php?read=
https://gsmadjaa.com/panel/
https://gsmadjaa.xyz/data/adjaa.dll
https://gsmadjaa.xyz/pc/mac.php?mac_key=
https://gsmadjaa.xyz/update/iResolvePrimehello.7z
https://gsmadjaa.xyz/update/iResolvehello.php
https://gsmadjaa.xyz/update/irtest.txt
https://software.gsmadjaa.com/
https://t.me/gsmadjaa2005
https://t.me/iResolvePrime
https://www.trustpilot.com/evaluate/gsmadjaa.com?utm_source=Trustpilot&utm_medium=email&utm_campaign=trustpilot_email
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:03:24 08:06:50 |
| ZipCRC: | 0x46e6d452 |
| ZipCompressedSize: | 5511496 |
| ZipUncompressedSize: | 6010024 |
| ZipFileName: | f_00f7a8 |
Total processes
195
Monitored processes
50
Malicious processes
11
Suspicious processes
6
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 456 | "cmd" ipconfig /flushdns | C:\Windows\System32\cmd.exe | — | iResolvePrime.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 660 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 900 | powershell Add-MpPreference -ExclusionPath """C:\Program Files\ADJAA-SOFTWARES\IRHELLO""" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1072 | "cmd.exe" | C:\Windows\System32\cmd.exe | — | iResolvePrime.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | powershell Set-MpPreference -DisableRealtimeMonitoring $false | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1616 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
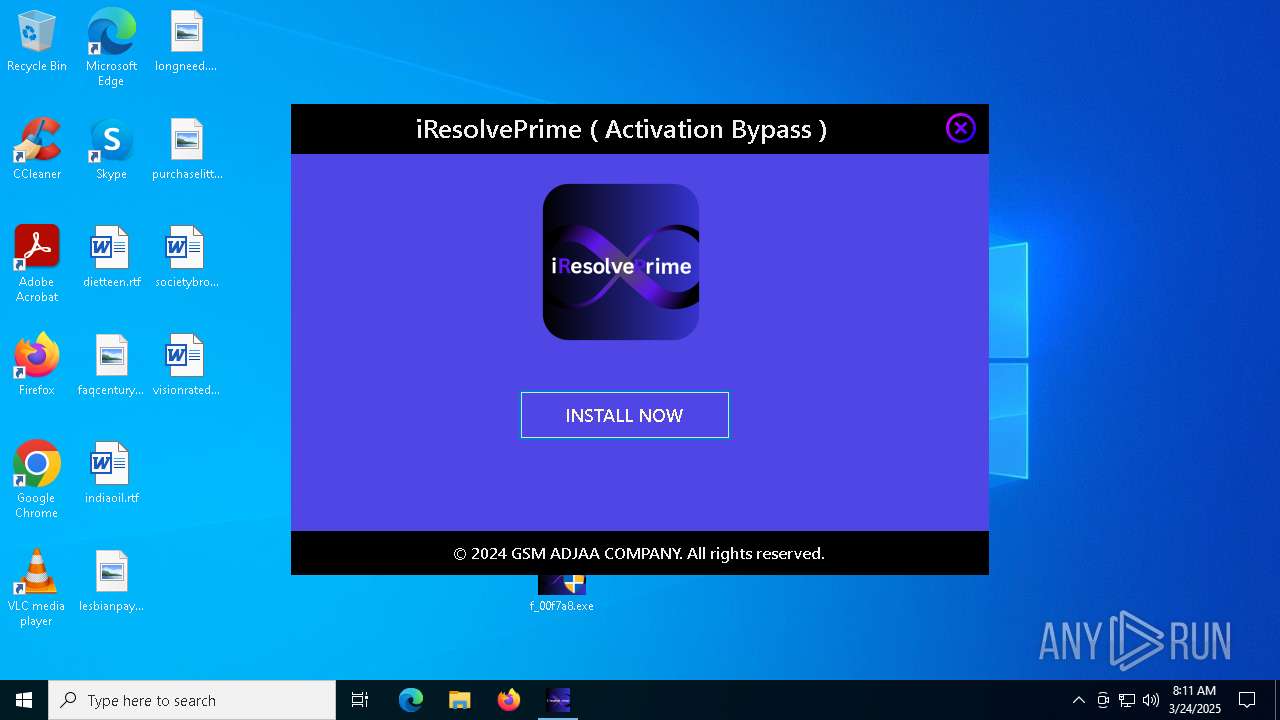
| 2096 | "C:\Program Files\ADJAA-SOFTWARES\IRHELLO\iResolvePrime.exe" | C:\Program Files\ADJAA-SOFTWARES\IRHELLO\iResolvePrime.exe | explorer.exe | ||||||||||||
User: admin Company: GSM ADJAA COMPANY Integrity Level: HIGH Description: iResolvePrime ( Activation Bypass ) Exit code: 4294967295 Version: 1.0.0.0 Modules
xor-url(PID) Process(2096) iResolvePrime.exe Decrypted-URLs (19)http://schemas.microsoft.com/SMI/2005/WindowsSettings http://schemas.microsoft.com/SMI/2016/WindowsSettings https://api.ipify.org/ https://api.telegram.org/bot5272081738:AAH33Xu6C6bDaVvQKJI-xMldq7fZBYLz3oE/sendMessage?chat_id=...........&text= https://api.telegram.org/bot6267929589:AAH6aAM4MgRB871zlKxLAVEjaGk-Z61vKHM/sendMessage?chat_id=2121212318&text= https://api64.ipify.org https://docs.microsoft.com/windows/win32/fileio/maximum-file-path-limitation https://gsmadjaa.com/checkout/index.php?type=iresolvehello&sft=aVJlc29sdmVQcmltZSAoQWN0aXZhdGlvbiBCeXBhc3Mp&init= https://gsmadjaa.com/iressource/model.php?read= https://gsmadjaa.com/panel/ https://gsmadjaa.xyz/data/adjaa.dll https://gsmadjaa.xyz/pc/mac.php?mac_key= https://gsmadjaa.xyz/update/iResolvePrimehello.7z https://gsmadjaa.xyz/update/iResolvehello.php https://gsmadjaa.xyz/update/irtest.txt https://software.gsmadjaa.com/ https://t.me/gsmadjaa2005 https://t.me/iResolvePrime https://www.trustpilot.com/evaluate/gsmadjaa.com?utm_source=Trustpilot&utm_medium=email&utm_campaign=trustpilot_email | |||||||||||||||
| 2108 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2384 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\MDE_File_Sample_f58abdb5e8a7b5d3358d3fdb3bd758369d4fd0a0.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2960 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
51 433
Read events
51 349
Write events
84
Delete events
0
Modification events
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\MDE_File_Sample_f58abdb5e8a7b5d3358d3fdb3bd758369d4fd0a0.zip | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (2384) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
Executable files
262
Suspicious files
14
Text files
42
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7684 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\ef40b03e-d229-4c0e-97c7-8315947e46be.down_data | — | |
MD5:— | SHA256:— | |||
| 7684 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\Content\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:4872BABAF39AA62B8D32695EBB7E9173 | SHA256:2EE85DF86EE29BBEB3DCA81AA29B6DE204F605A2769B84C728A329178A2D0999 | |||
| 7684 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\Microsoft\CryptnetUrlCache\MetaData\26C212D9399727259664BDFCA073966E_F9F7D6A7ECE73106D2A8C63168CDA10D | binary | |
MD5:5E52D9C60D41439285038CB7FAD8F6DB | SHA256:4CEB486830B40DF3FA3753A2EC2CAB8891E1F84C445D839CFE559BDA397067B4 | |||
| 2384 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2384.17091\f_00f7a8 | executable | |
MD5:BADA330A2595390D070C7E08AC4ACF34 | SHA256:D77D7A324BD82C52982A4168E2CF5E7A8C9E8B89404740475D617BDD213F9559 | |||
| 7684 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\23c825ca-fe85-4020-b772-95ea4407b001.e68cc23d-2626-4fd4-b7bb-176a0411db0e.down_meta | binary | |
MD5:8B5C8E13A98ADA5DE23444307727A9B1 | SHA256:36846AC786D8B71ADAC719AE0D4788C49C193237B3581CC6FDCF91ADE7F8E9B6 | |||
| 7684 | BackgroundTransferHost.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.ContentDeliveryManager_cw5n1h2txyewy\AC\BackgroundTransferApi\ef40b03e-d229-4c0e-97c7-8315947e46be.e68cc23d-2626-4fd4-b7bb-176a0411db0e.down_meta | binary | |
MD5:8B5C8E13A98ADA5DE23444307727A9B1 | SHA256:36846AC786D8B71ADAC719AE0D4788C49C193237B3581CC6FDCF91ADE7F8E9B6 | |||
| 1328 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_jka3tuq3.zhb.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1328 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_hwgykns3.zmk.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1328 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_dlx2ihe5.vlh.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7896 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_pvc1hbeb.qv2.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
29
DNS requests
20
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.18:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6876 | backgroundTaskHost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
7684 | BackgroundTransferHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7608 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7608 | SIHClient.exe | GET | 200 | 2.23.246.101:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.16.164.18:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3216 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 20.190.160.14:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
6876 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6876 | backgroundTaskHost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
7684 | BackgroundTransferHost.exe | 23.15.178.234:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
6436 | f_00f7a8.exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
7892 | iResolvePrime.exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
2096 | iResolvePrime.exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |