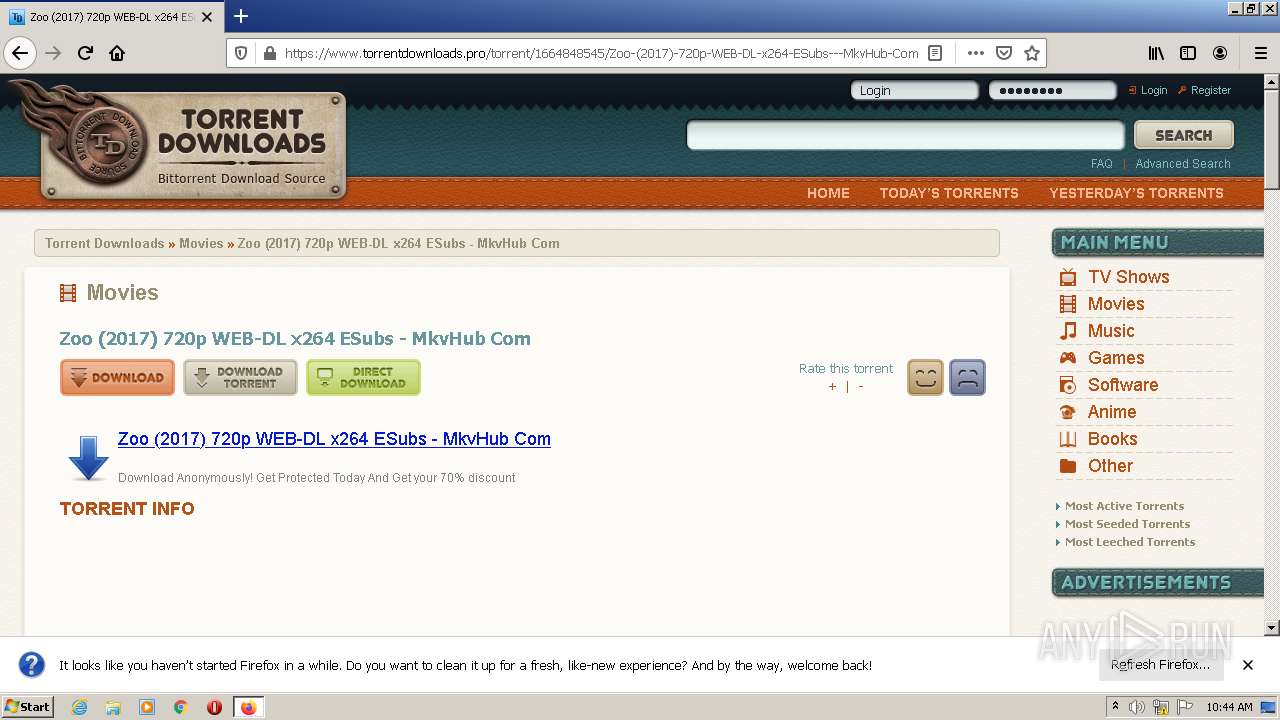
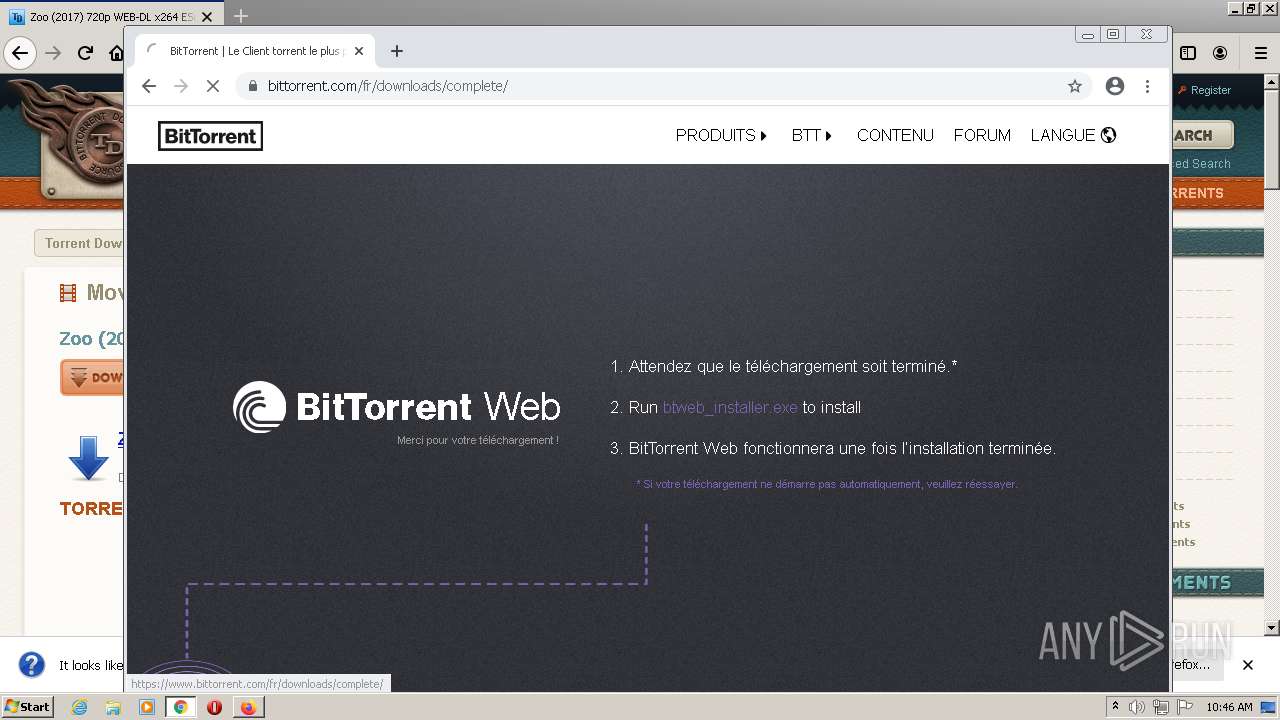
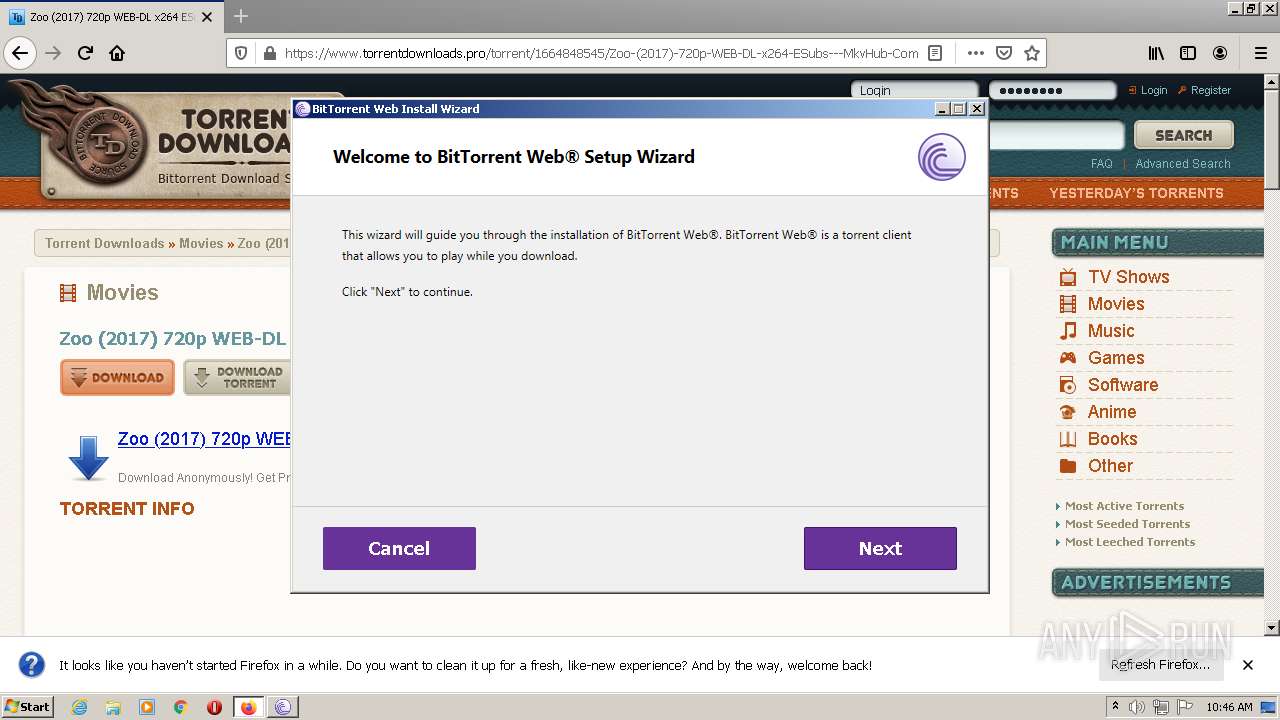
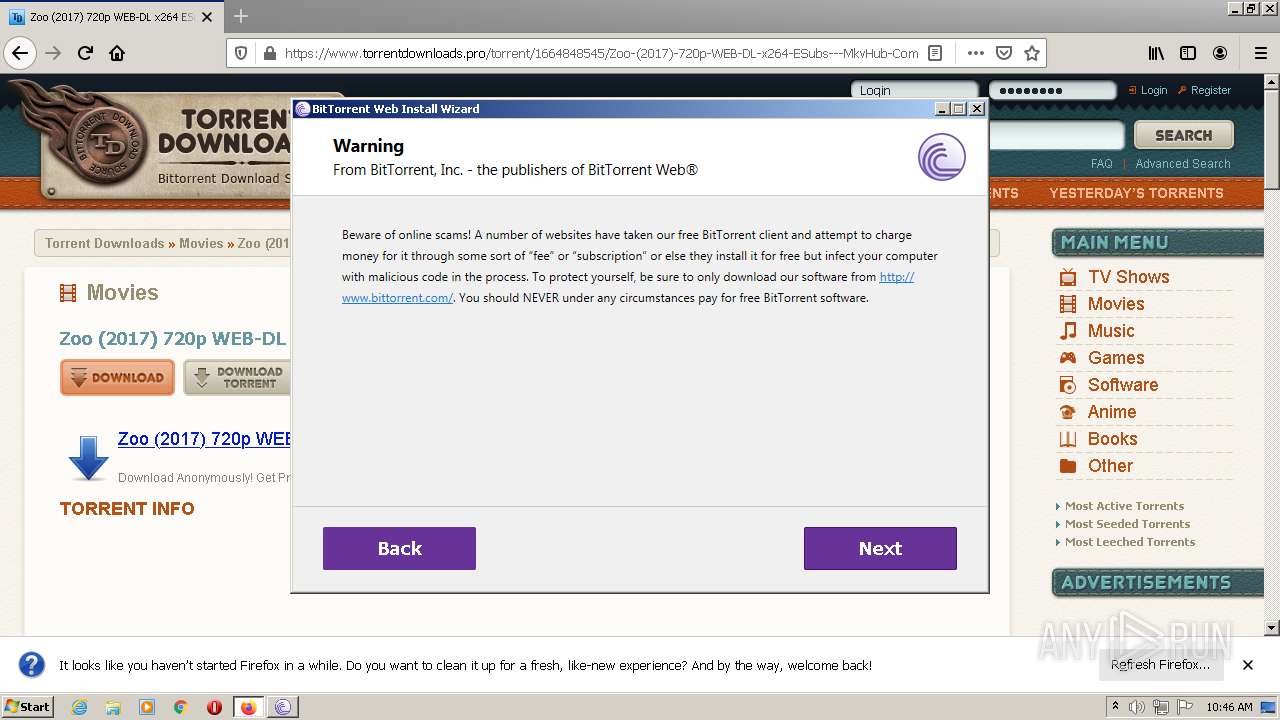
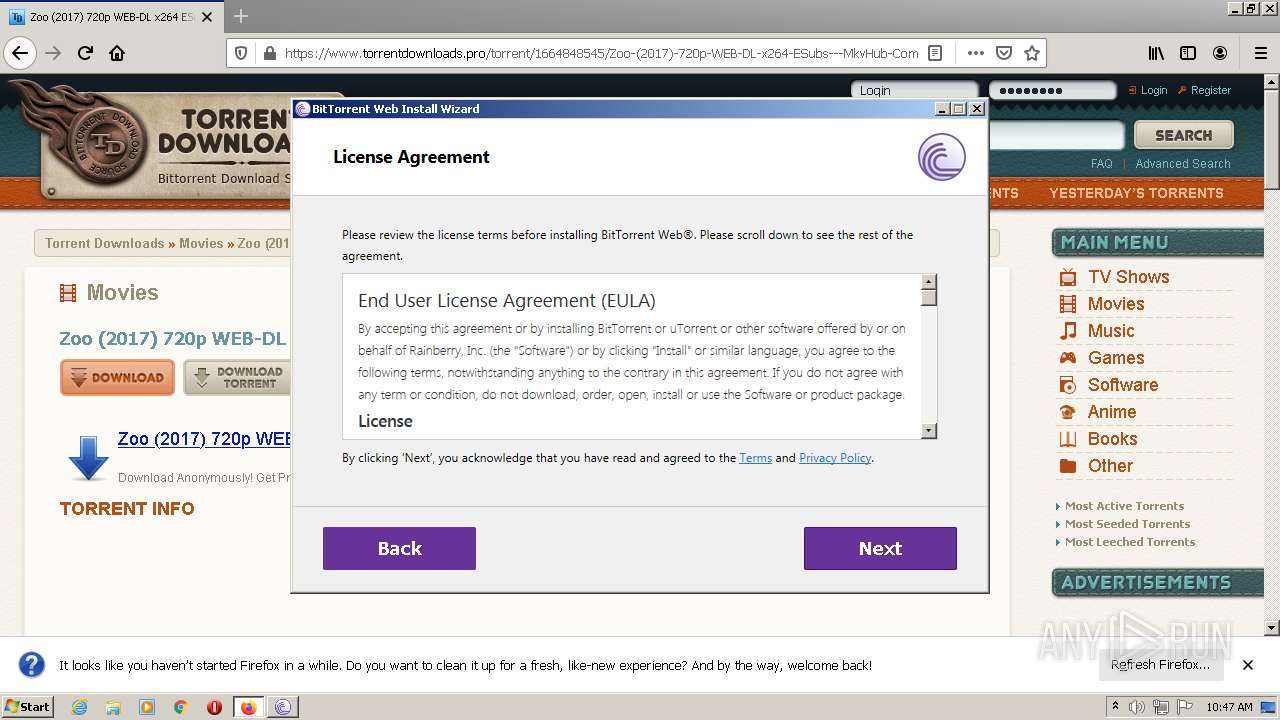
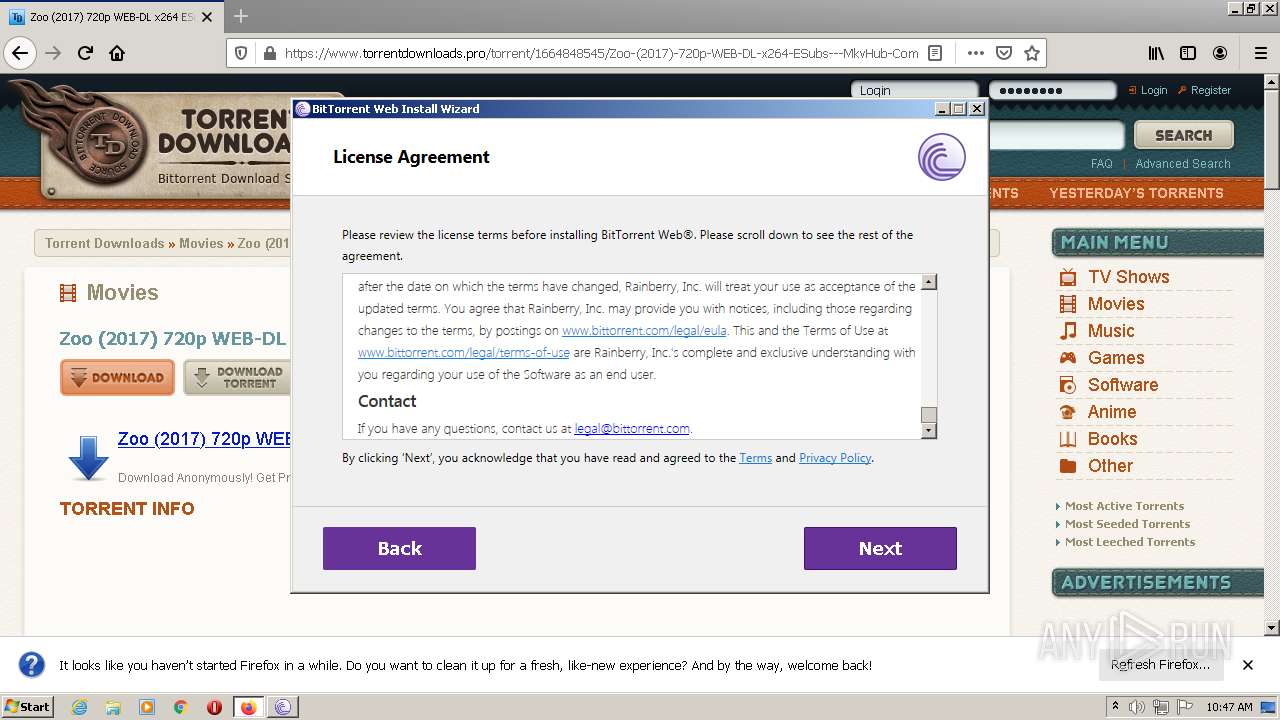
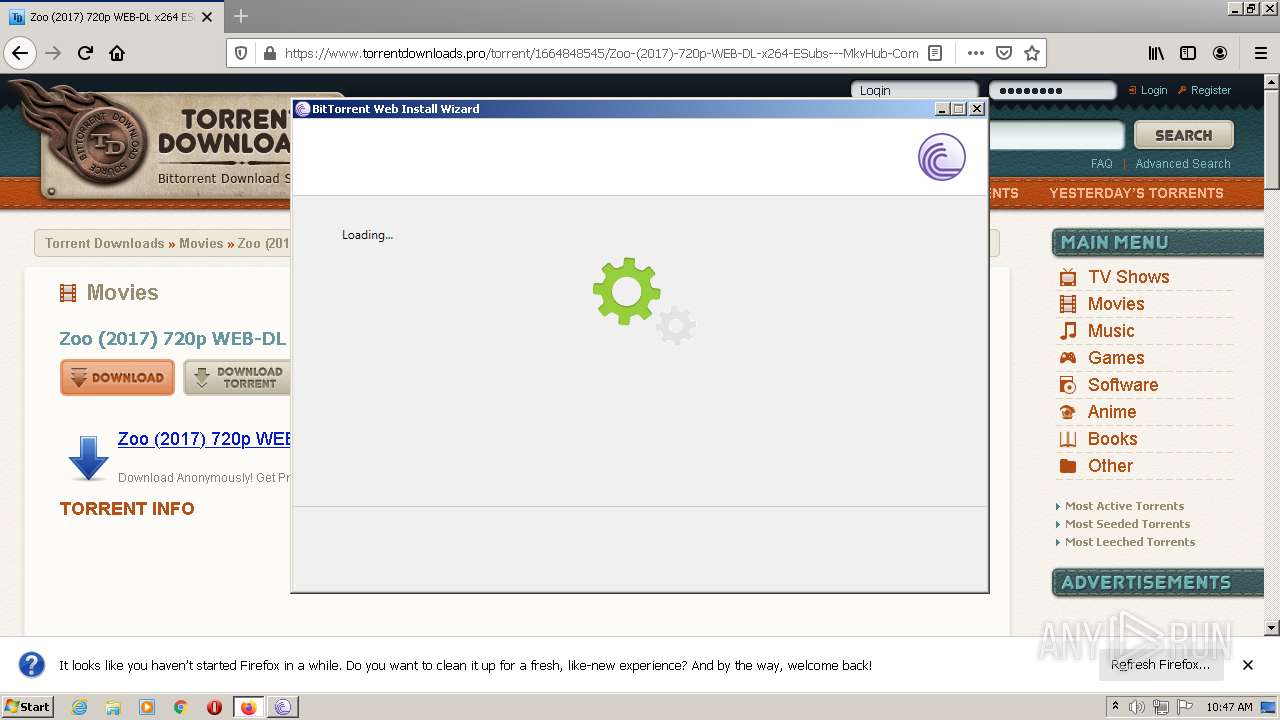
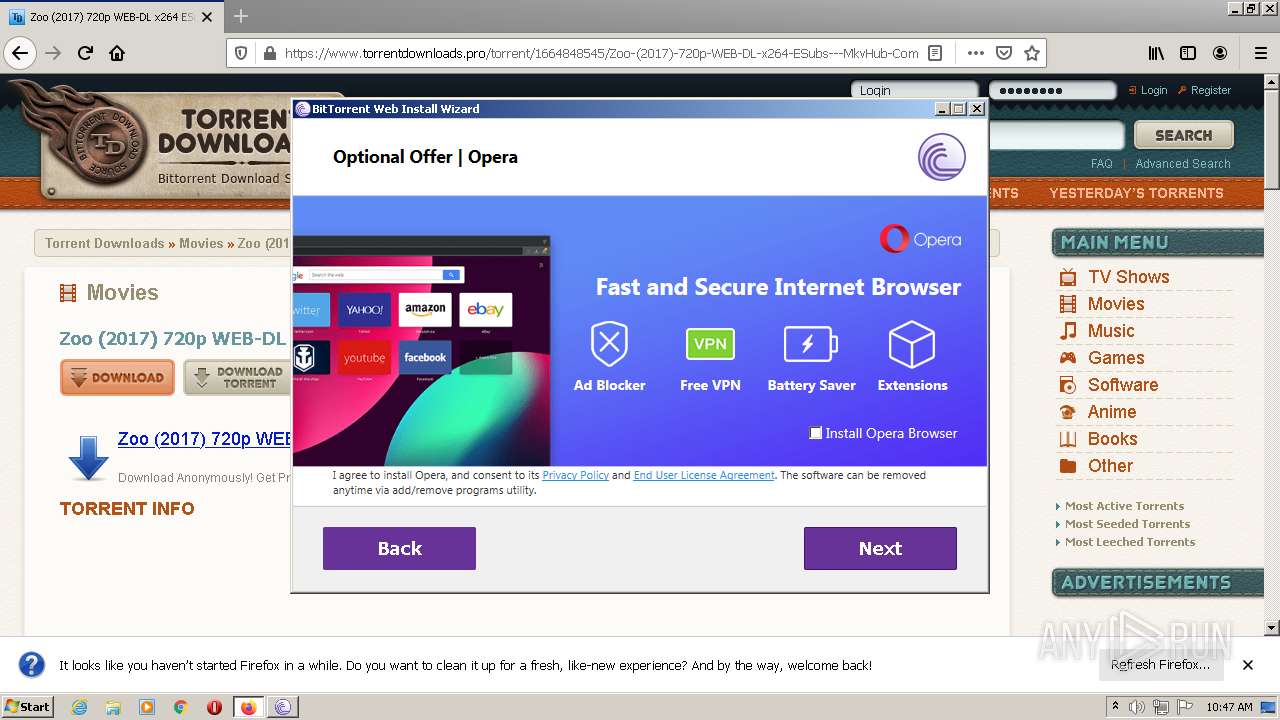
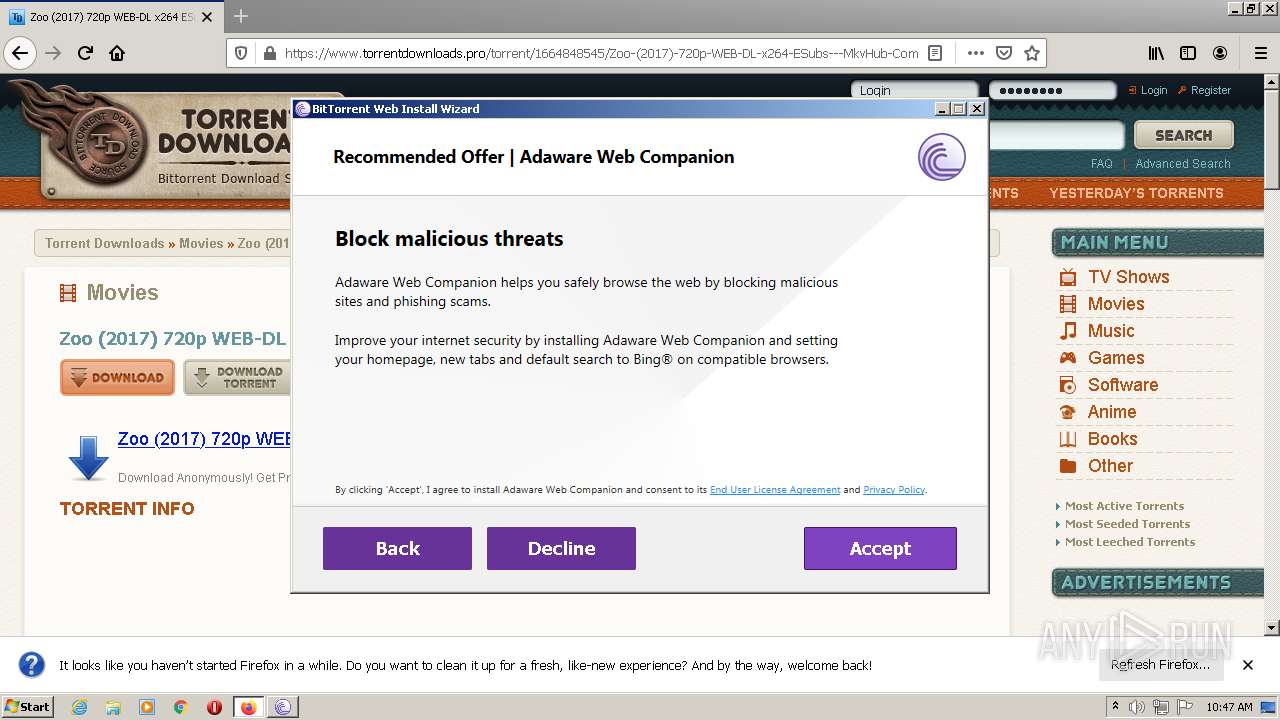
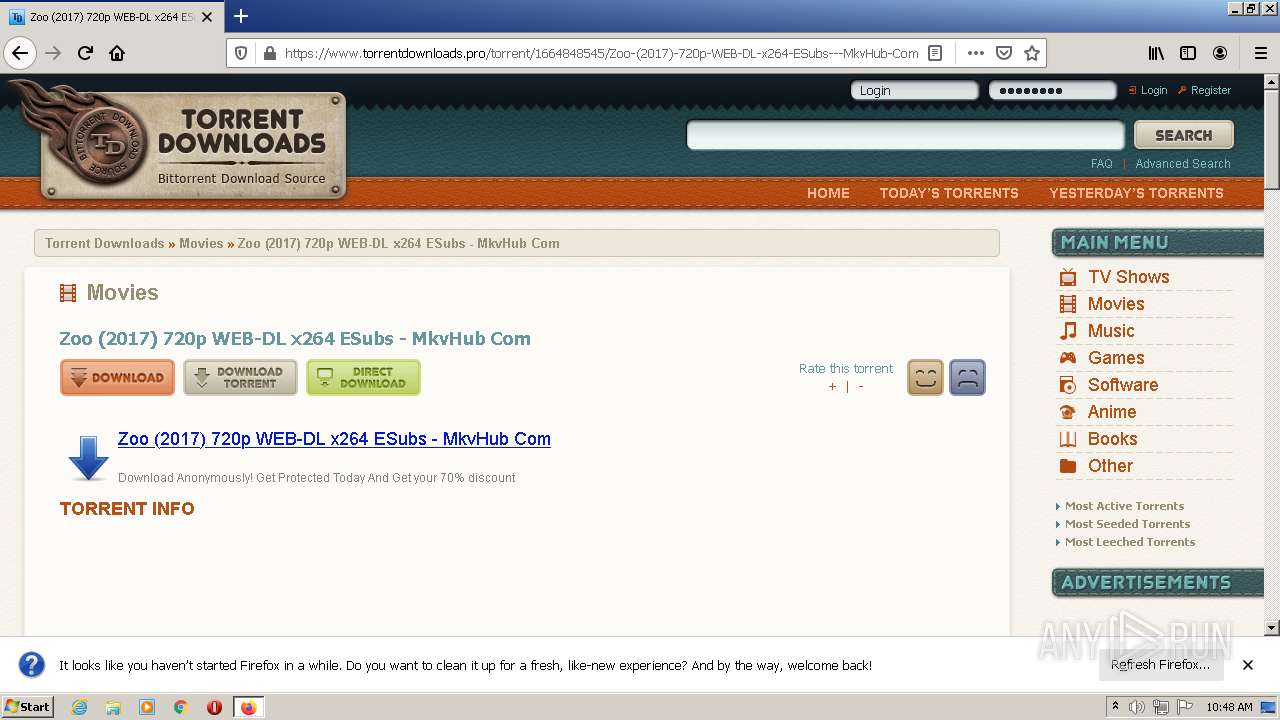
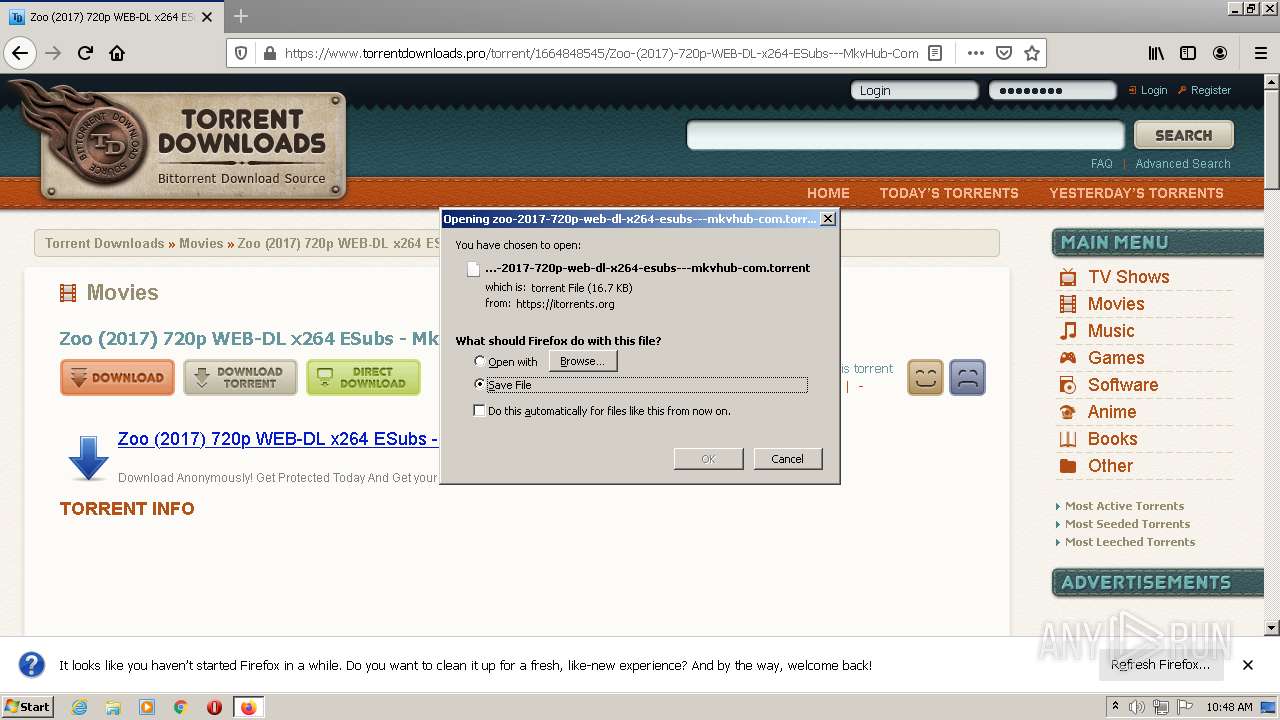
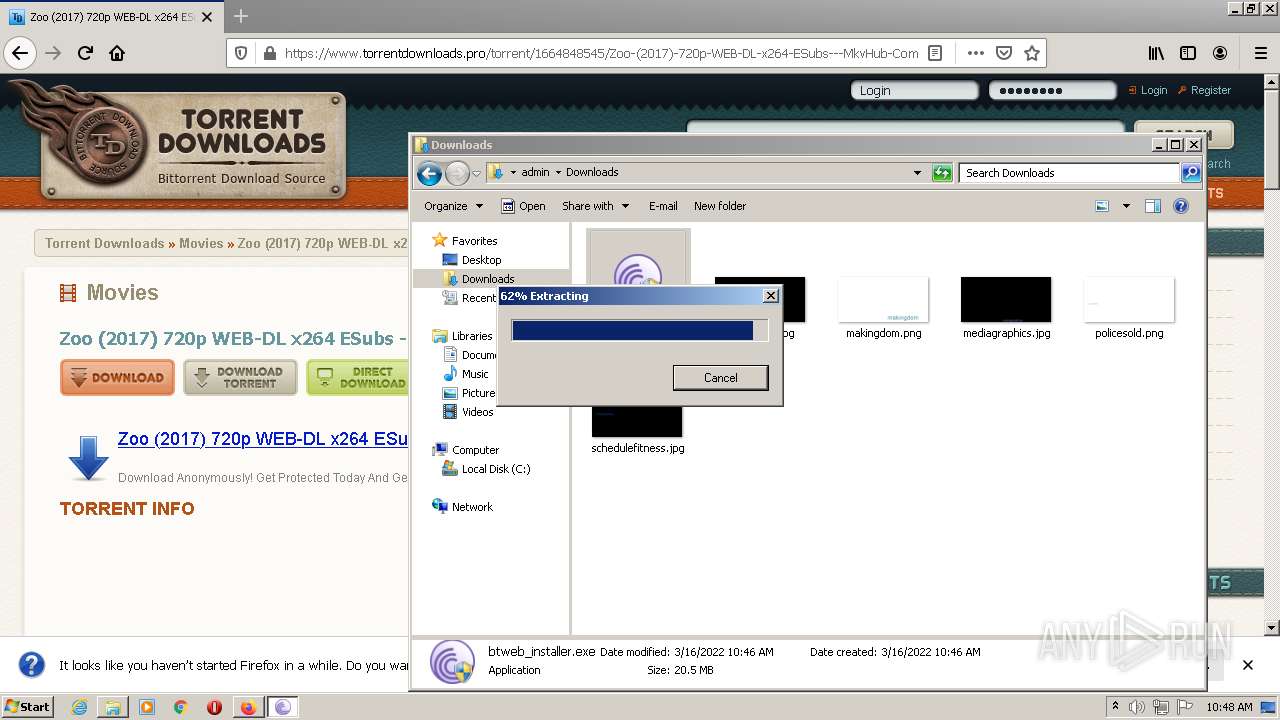
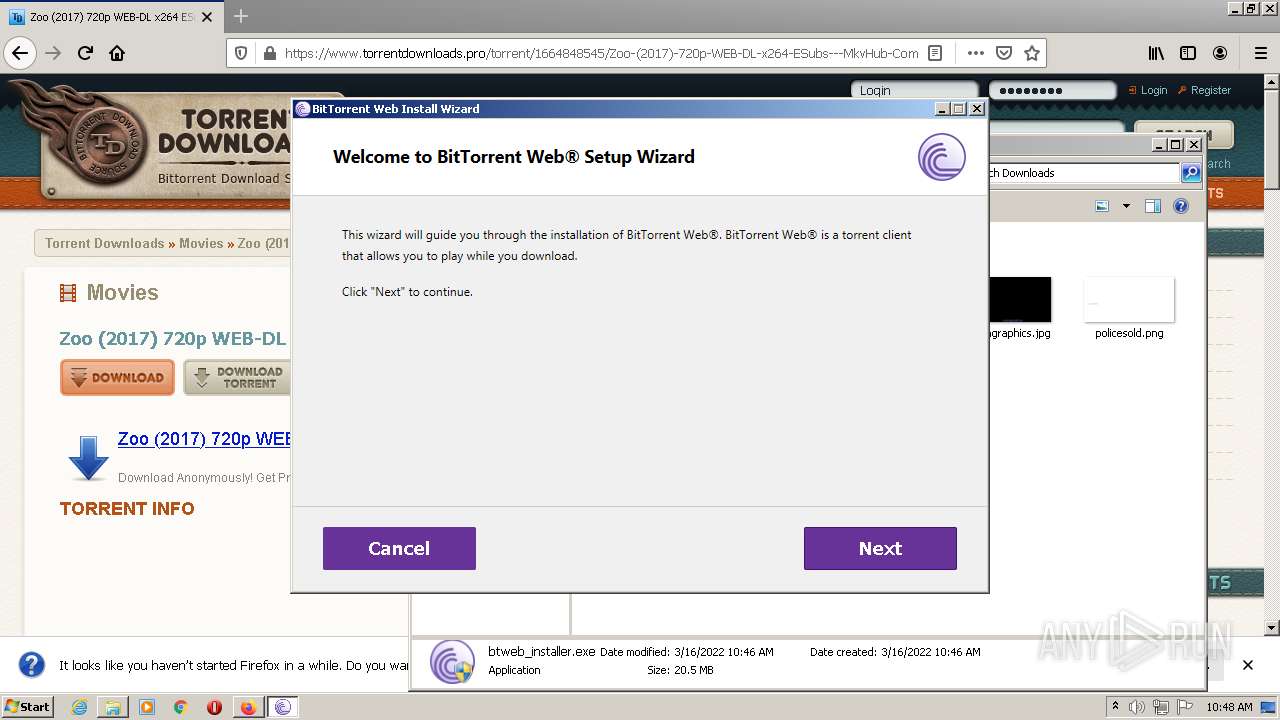
| URL: | https://www.torrentdownloads.pro/torrent/1664848545/Zoo-%282017%29-720p-WEB-DL-x264-ESubs---MkvHub-Com |
| Full analysis: | https://app.any.run/tasks/f7a5330b-f9e4-48c0-a2a4-efab75de66b1 |
| Verdict: | Malicious activity |
| Analysis date: | March 16, 2022, 10:44:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 16C65BF93572486C868ADF2AA9FD6DA9 |
| SHA1: | 8620DB257796085370D1EED444A4E427FB7E513C |
| SHA256: | 9CC3D4941B9CC09076D4AE55E0DB3C2FFE014566A0E213B1F7B165600AE66228 |
| SSDEEP: | 3:N8DSL2XeBz4L8XOKUTd6G4+YIkPjSyQHVhiT:2OLweBzMx6G4jSD+T |
MALICIOUS
Application was dropped or rewritten from another process
- btweb_installer.exe (PID: 3572)
- btweb_installer.exe (PID: 2260)
- GenericSetup.exe (PID: 1140)
- Carrier.exe (PID: 3824)
- btweb_installer.exe (PID: 1332)
- btweb_installer.exe (PID: 328)
- GenericSetup.exe (PID: 500)
- Carrier.exe (PID: 3148)
Actions looks like stealing of personal data
- GenericSetup.exe (PID: 1140)
- GenericSetup.exe (PID: 500)
Changes settings of System certificates
- GenericSetup.exe (PID: 1140)
Loads dropped or rewritten executable
- GenericSetup.exe (PID: 1140)
- GenericSetup.exe (PID: 500)
Drops executable file immediately after starts
- btweb_installer.exe (PID: 328)
SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 2320)
Executable content was dropped or overwritten
- chrome.exe (PID: 2320)
- chrome.exe (PID: 3248)
- btweb_installer.exe (PID: 2260)
- GenericSetup.exe (PID: 1140)
- btweb_installer.exe (PID: 328)
- GenericSetup.exe (PID: 500)
Drops a file with a compile date too recent
- chrome.exe (PID: 3248)
- chrome.exe (PID: 2320)
- btweb_installer.exe (PID: 2260)
- btweb_installer.exe (PID: 328)
Checks supported languages
- btweb_installer.exe (PID: 2260)
- GenericSetup.exe (PID: 1140)
- btweb_installer.exe (PID: 328)
- GenericSetup.exe (PID: 500)
Reads the computer name
- GenericSetup.exe (PID: 1140)
- GenericSetup.exe (PID: 500)
Drops a file that was compiled in debug mode
- btweb_installer.exe (PID: 2260)
- GenericSetup.exe (PID: 1140)
- btweb_installer.exe (PID: 328)
- GenericSetup.exe (PID: 500)
Reads Environment values
- GenericSetup.exe (PID: 1140)
- GenericSetup.exe (PID: 500)
Reads the Windows organization settings
- GenericSetup.exe (PID: 1140)
- GenericSetup.exe (PID: 500)
Reads Windows owner or organization settings
- GenericSetup.exe (PID: 1140)
- GenericSetup.exe (PID: 500)
Adds / modifies Windows certificates
- GenericSetup.exe (PID: 1140)
Searches for installed software
- GenericSetup.exe (PID: 1140)
- GenericSetup.exe (PID: 500)
INFO
Checks supported languages
- firefox.exe (PID: 3828)
- firefox.exe (PID: 3428)
- firefox.exe (PID: 1652)
- firefox.exe (PID: 2692)
- firefox.exe (PID: 3464)
- firefox.exe (PID: 2708)
- firefox.exe (PID: 3688)
- firefox.exe (PID: 1344)
- chrome.exe (PID: 2320)
- chrome.exe (PID: 1964)
- chrome.exe (PID: 336)
- chrome.exe (PID: 1108)
- chrome.exe (PID: 3332)
- chrome.exe (PID: 596)
- chrome.exe (PID: 3248)
- chrome.exe (PID: 2804)
- chrome.exe (PID: 3832)
- chrome.exe (PID: 2600)
- chrome.exe (PID: 3280)
- chrome.exe (PID: 1296)
- chrome.exe (PID: 484)
- chrome.exe (PID: 3476)
- chrome.exe (PID: 4060)
- chrome.exe (PID: 468)
- chrome.exe (PID: 1052)
- chrome.exe (PID: 456)
- chrome.exe (PID: 3188)
- chrome.exe (PID: 2148)
- chrome.exe (PID: 3920)
- chrome.exe (PID: 2032)
- chrome.exe (PID: 656)
- chrome.exe (PID: 2976)
- chrome.exe (PID: 3728)
- chrome.exe (PID: 3244)
- chrome.exe (PID: 2080)
- chrome.exe (PID: 2352)
- chrome.exe (PID: 3440)
- chrome.exe (PID: 3332)
- chrome.exe (PID: 3960)
- chrome.exe (PID: 2364)
- chrome.exe (PID: 2220)
- chrome.exe (PID: 2852)
- chrome.exe (PID: 3376)
- chrome.exe (PID: 2628)
- chrome.exe (PID: 2416)
- chrome.exe (PID: 1140)
- chrome.exe (PID: 3304)
- chrome.exe (PID: 3052)
- chrome.exe (PID: 3424)
- chrome.exe (PID: 2688)
- chrome.exe (PID: 3592)
- chrome.exe (PID: 3340)
- chrome.exe (PID: 3824)
- chrome.exe (PID: 548)
- explorer.exe (PID: 3200)
Reads the computer name
- firefox.exe (PID: 3828)
- firefox.exe (PID: 3688)
- firefox.exe (PID: 3428)
- firefox.exe (PID: 2692)
- firefox.exe (PID: 2708)
- firefox.exe (PID: 1652)
- firefox.exe (PID: 1344)
- chrome.exe (PID: 3248)
- chrome.exe (PID: 3332)
- chrome.exe (PID: 3832)
- chrome.exe (PID: 2320)
- chrome.exe (PID: 3440)
- chrome.exe (PID: 2852)
- chrome.exe (PID: 2628)
- chrome.exe (PID: 1140)
- chrome.exe (PID: 3304)
- chrome.exe (PID: 2688)
- chrome.exe (PID: 3340)
- chrome.exe (PID: 548)
- explorer.exe (PID: 3200)
Application launched itself
- firefox.exe (PID: 3828)
- firefox.exe (PID: 3464)
- chrome.exe (PID: 2320)
Reads CPU info
- firefox.exe (PID: 3828)
Creates files in the program directory
- firefox.exe (PID: 3828)
Creates files in the user directory
- firefox.exe (PID: 3828)
Reads the hosts file
- chrome.exe (PID: 3248)
- chrome.exe (PID: 2320)
Reads the date of Windows installation
- firefox.exe (PID: 3828)
- chrome.exe (PID: 2628)
Reads settings of System Certificates
- chrome.exe (PID: 3248)
- chrome.exe (PID: 2320)
- GenericSetup.exe (PID: 1140)
- GenericSetup.exe (PID: 500)
Manual execution by user
- chrome.exe (PID: 2320)
- explorer.exe (PID: 3200)
- btweb_installer.exe (PID: 1332)
- btweb_installer.exe (PID: 328)
Checks Windows Trust Settings
- chrome.exe (PID: 2320)
- GenericSetup.exe (PID: 1140)
- firefox.exe (PID: 3828)
- GenericSetup.exe (PID: 500)
Dropped object may contain Bitcoin addresses
- chrome.exe (PID: 2320)
- firefox.exe (PID: 3828)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
110
Monitored processes
63
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 328 | "C:\Users\admin\Downloads\btweb_installer.exe" | C:\Users\admin\Downloads\btweb_installer.exe | Explorer.EXE | ||||||||||||
User: admin Company: BitTorrent, Inc. Integrity Level: HIGH Description: BitTorrent Web Exit code: 0 Version: 1.2.7.4186 Modules
| |||||||||||||||
| 336 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1040,6892273810688063676,4024785856152859724,131072 --enable-features=PasswordImport --lang=en-US --extension-process --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2348 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 456 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1040,6892273810688063676,4024785856152859724,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=4036 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 468 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1040,6892273810688063676,4024785856152859724,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3360 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 484 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1040,6892273810688063676,4024785856152859724,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3172 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 500 | .\GenericSetup.exe | C:\Users\admin\AppData\Local\Temp\7zS84148085\GenericSetup.exe | btweb_installer.exe | ||||||||||||
User: admin Company: Adaware Integrity Level: HIGH Description: BitTorrent Web Exit code: 0 Version: 1.0.11.5351 Modules
| |||||||||||||||
| 548 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --field-trial-handle=1040,6892273810688063676,4024785856152859724,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=2164 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 596 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1040,6892273810688063676,4024785856152859724,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=2976 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 656 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1040,6892273810688063676,4024785856152859724,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=3348 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
| 1052 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --field-trial-handle=1040,6892273810688063676,4024785856152859724,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --mojo-platform-channel-handle=4280 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 86.0.4240.198 Modules
| |||||||||||||||
Total events
147 265
Read events
146 998
Write events
265
Delete events
2
Modification events
| (PID) Process: | (3464) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: 039AE9B6DB000000 | |||
| (PID) Process: | (3828) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 46A3E9B6DB000000 | |||
| (PID) Process: | (3828) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (3828) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (3828) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
| (PID) Process: | (3828) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableDefaultBrowserAgent |
Value: 0 | |||
| (PID) Process: | (3828) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|ServicesSettingsServer |
Value: https://firefox.settings.services.mozilla.com/v1 | |||
| (PID) Process: | (3828) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|SecurityContentSignatureRootHash |
Value: 97:E8:BA:9C:F1:2F:B3:DE:53:CC:42:A4:E6:57:7E:D6:4D:F4:93:C2:47:B4:14:FE:A0:36:81:8D:38:23:56:0E | |||
| (PID) Process: | (3828) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3828) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000003B010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A80164000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
24
Suspicious files
356
Text files
242
Unknown types
65
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3828 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 3828 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 3828 | firefox.exe | C:\Users\admin\AppData\Local\Temp\mz_etilqs_P12JffNYL233OLa | binary | |
MD5:— | SHA256:— | |||
| 3828 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-wal | binary | |
MD5:— | SHA256:— | |||
| 3828 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\settings\main\ms-language-packs\asrouter.ftl | text | |
MD5:— | SHA256:— | |||
| 3828 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\settings\main\ms-language-packs\asrouter.ftl.tmp | text | |
MD5:— | SHA256:— | |||
| 3828 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs.js | text | |
MD5:299A2B747C11E4BDA194E563FEA4A699 | SHA256:94EE461F62E8B4A0A65471A41E10C8C56722B73C0A019D76ACA7F5BAF109813E | |||
| 3828 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | binary | |
MD5:EA8B62857DFDBD3D0BE7D7E4A954EC9A | SHA256:792955295AE9C382986222C6731C5870BD0E921E7F7E34CC4615F5CD67F225DA | |||
| 3828 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\urlCache-current.bin | binary | |
MD5:994A33896BB41A278A315D0D796422B6 | SHA256:54EC50A20FFF8CC016710E49437CF6A11D3FE5EE7B28C185E4A9AAFEE2908B63 | |||
| 3828 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
54
TCP/UDP connections
269
DNS requests
389
Threats
22
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3828 | firefox.exe | POST | 200 | 2.16.186.25:80 | http://r3.o.lencr.org/ | unknown | der | 503 b | shared |
3828 | firefox.exe | POST | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3 | US | der | 472 b | whitelisted |
3828 | firefox.exe | POST | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3 | US | der | 471 b | whitelisted |
3828 | firefox.exe | POST | 200 | 2.16.186.8:80 | http://e1.o.lencr.org/ | unknown | der | 344 b | whitelisted |
3828 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
3828 | firefox.exe | POST | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3 | US | der | 471 b | whitelisted |
3828 | firefox.exe | POST | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3 | US | der | 471 b | whitelisted |
3828 | firefox.exe | POST | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gts1c3 | US | der | 472 b | whitelisted |
3828 | firefox.exe | POST | 200 | 2.16.186.8:80 | http://e1.o.lencr.org/ | unknown | der | 344 b | whitelisted |
3828 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3828 | firefox.exe | 34.107.221.82:80 | detectportal.firefox.com | — | US | whitelisted |
3828 | firefox.exe | 172.67.70.47:443 | www.torrentdownloads.pro | — | US | unknown |
3828 | firefox.exe | 52.40.22.163:443 | location.services.mozilla.com | Amazon.com, Inc. | US | unknown |
3828 | firefox.exe | 142.250.181.234:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
3828 | firefox.exe | 142.250.186.131:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
3828 | firefox.exe | 13.32.22.13:443 | content-signature-2.cdn.mozilla.net | Amazon.com, Inc. | US | unknown |
3828 | firefox.exe | 34.210.132.84:443 | push.services.mozilla.com | Amazon.com, Inc. | US | unknown |
3828 | firefox.exe | 65.9.66.38:443 | firefox-settings-attachments.cdn.mozilla.net | AT&T Services, Inc. | US | malicious |
3828 | firefox.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3828 | firefox.exe | 172.217.16.138:443 | ajax.googleapis.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
www.torrentdownloads.pro |
| suspicious |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
firefox.settings.services.mozilla.com |
| whitelisted |
location.services.mozilla.com |
| whitelisted |
locprod2-elb-us-west-2.prod.mozaws.net |
| whitelisted |
safebrowsing.googleapis.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
pki-goog.l.google.com |
| whitelisted |
push.services.mozilla.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3828 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
3828 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
3828 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
3828 | firefox.exe | Potentially Bad Traffic | ET INFO Terse Request for .txt - Likely Hostile |
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
— | — | Potentially Bad Traffic | ET INFO Observed DNS Query to .biz TLD |
— | — | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
— | — | Potential Corporate Privacy Violation | ET POLICY DNS Query For XXX Adult Site Top Level Domain |
11 ETPRO signatures available at the full report
Process | Message |
|---|---|
GenericSetup.exe | Error: File not found - genericsetup.wrappers.sciter:console.tis
|
GenericSetup.exe | at sciter:init-script.tis
|
GenericSetup.exe | |
GenericSetup.exe | |
GenericSetup.exe | file:resources/tis/TranslateOfferTemplate.tis(82) : warning :'async' does not contain any 'await'
|
GenericSetup.exe | Error: File not found - genericsetup.wrappers.sciter:console.tis
|
GenericSetup.exe | at sciter:init-script.tis
|
GenericSetup.exe | |
GenericSetup.exe | |
GenericSetup.exe | file:resources/tis/TranslateOfferTemplate.tis(82) : warning :'async' does not contain any 'await'
|