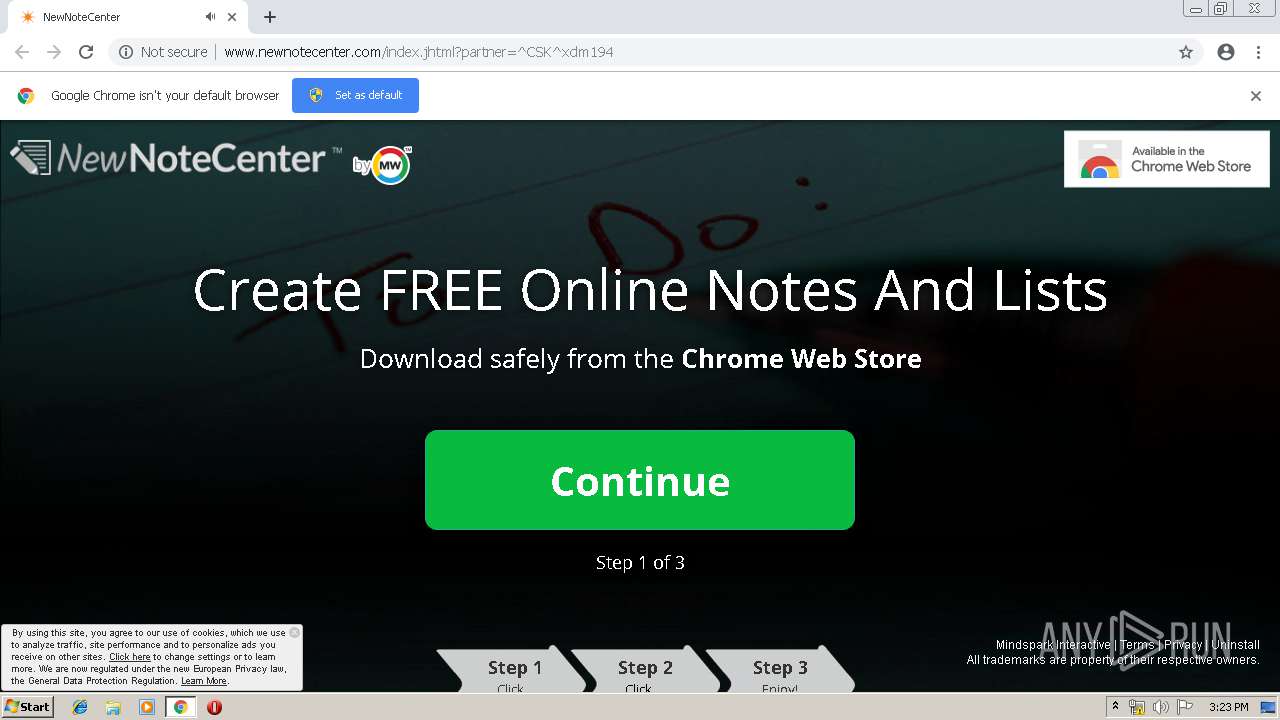
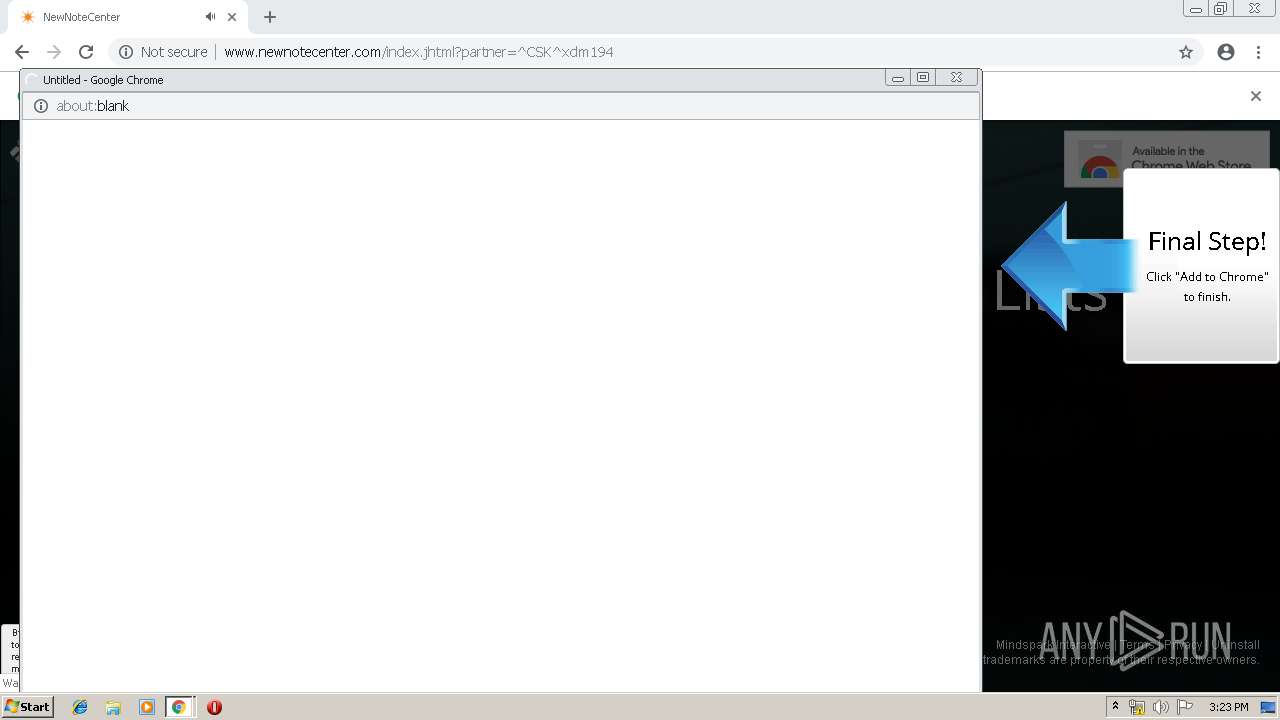
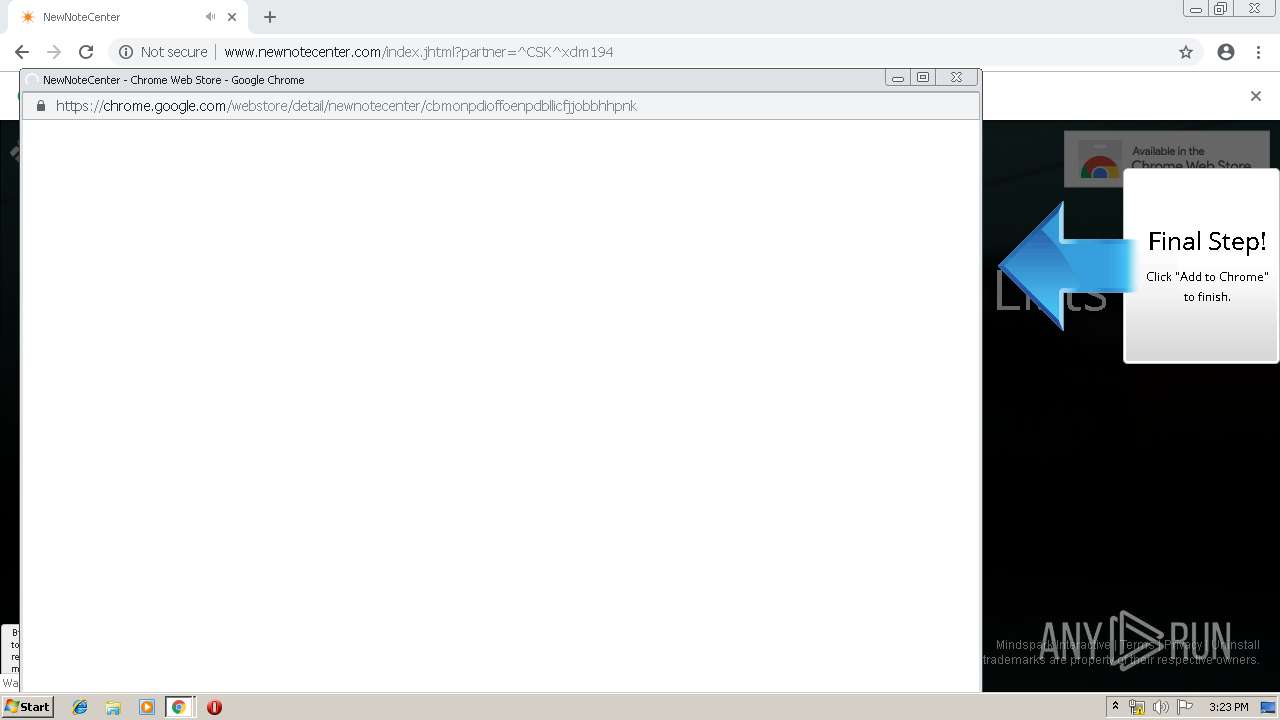
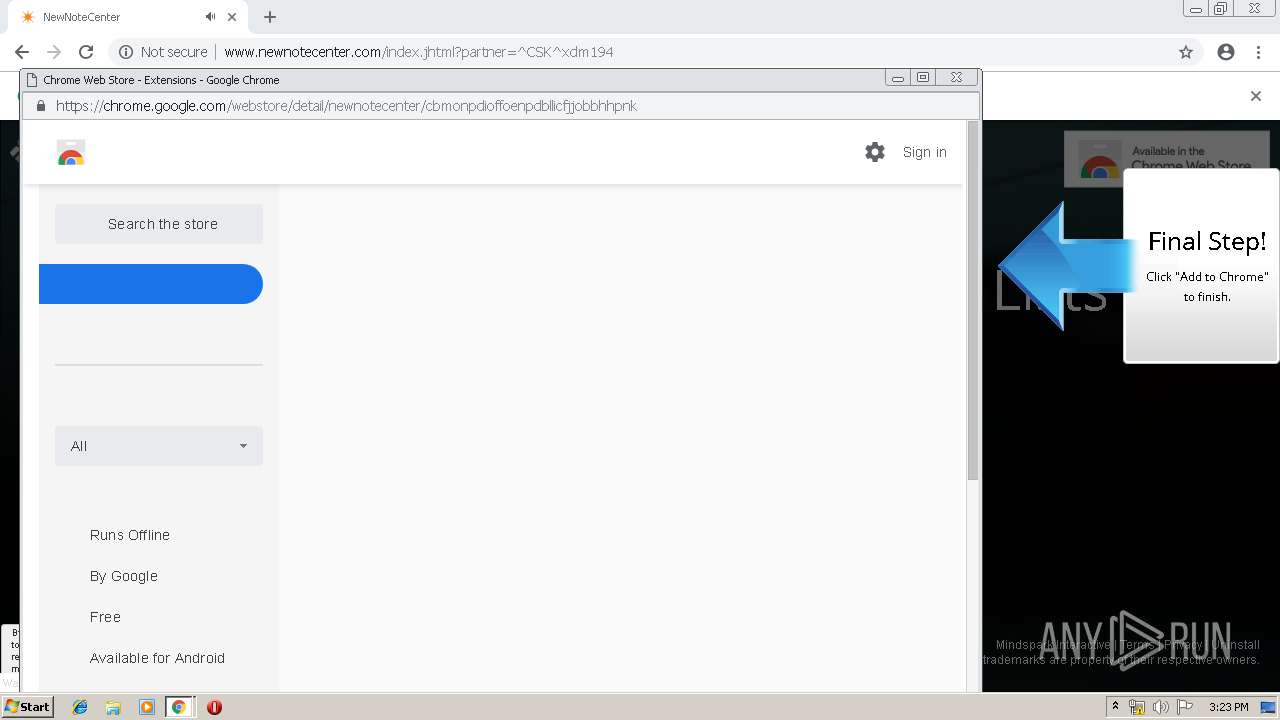
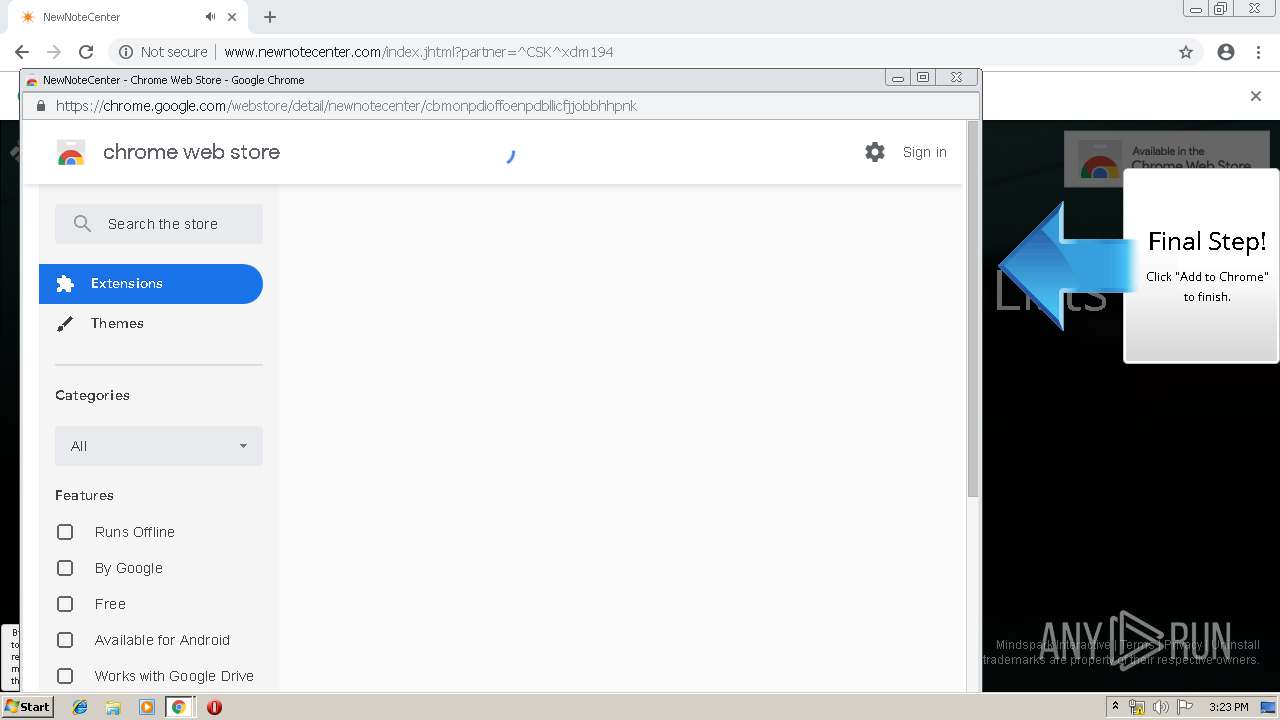
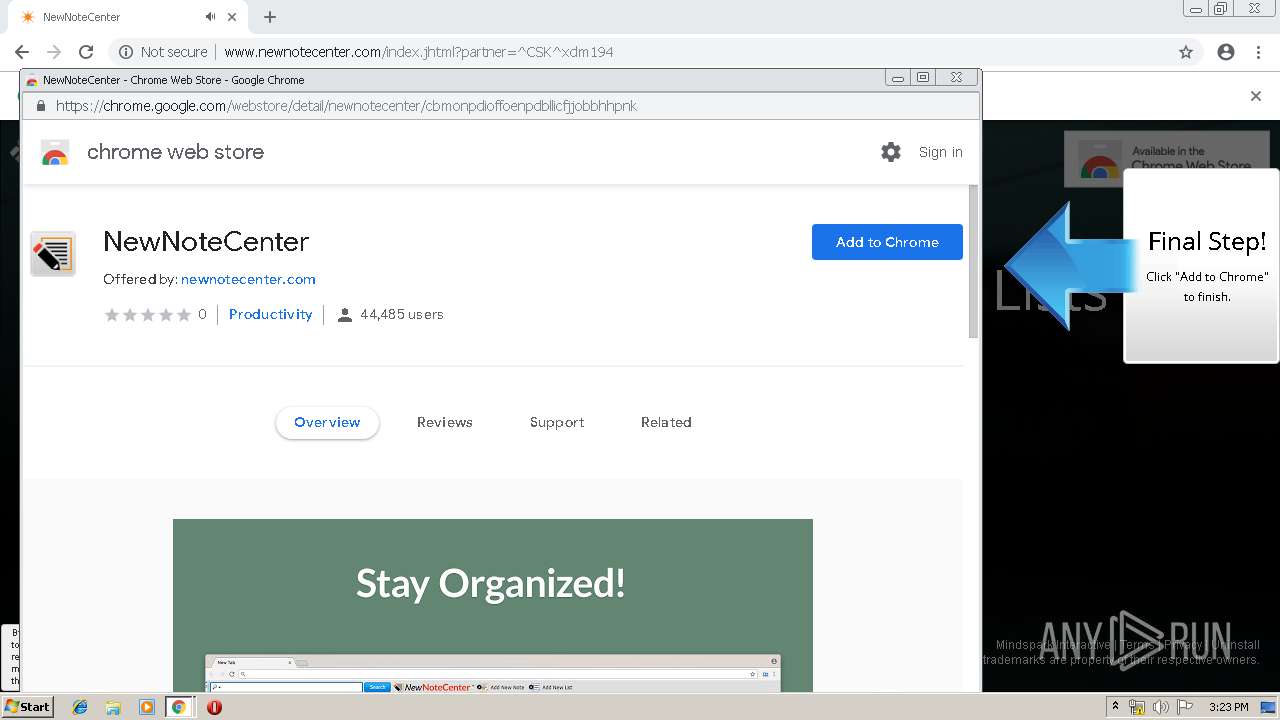
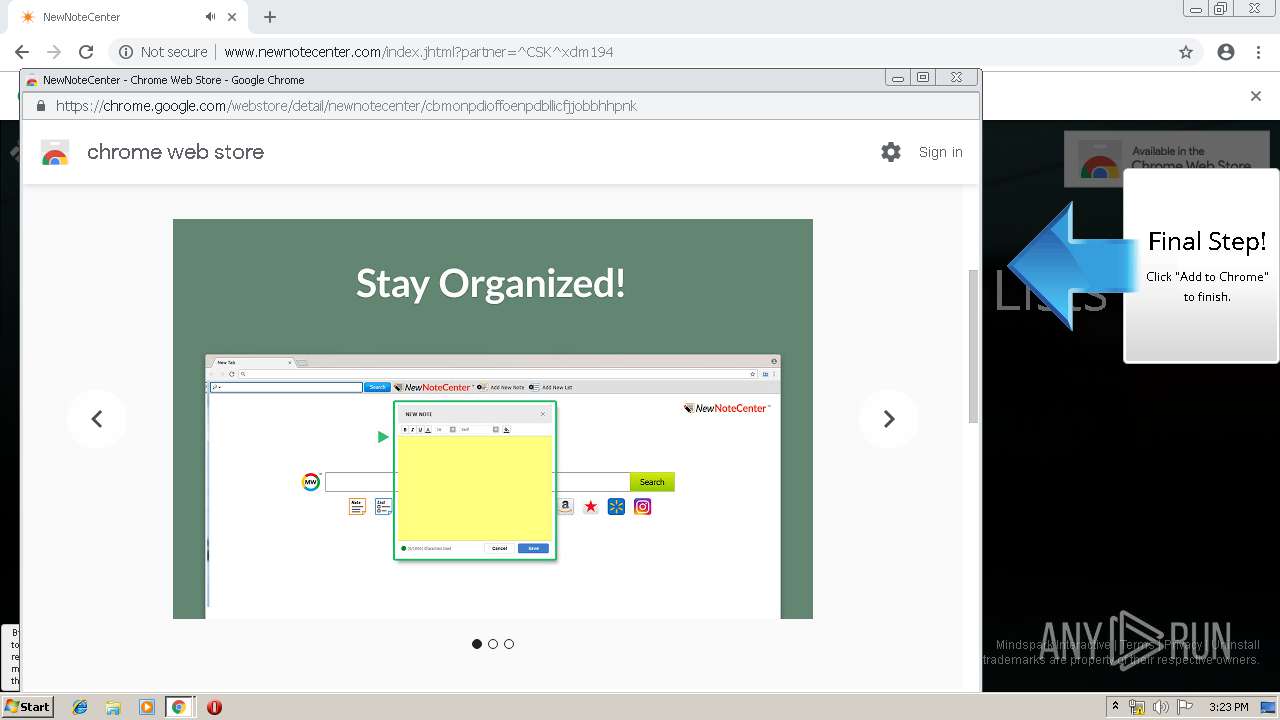
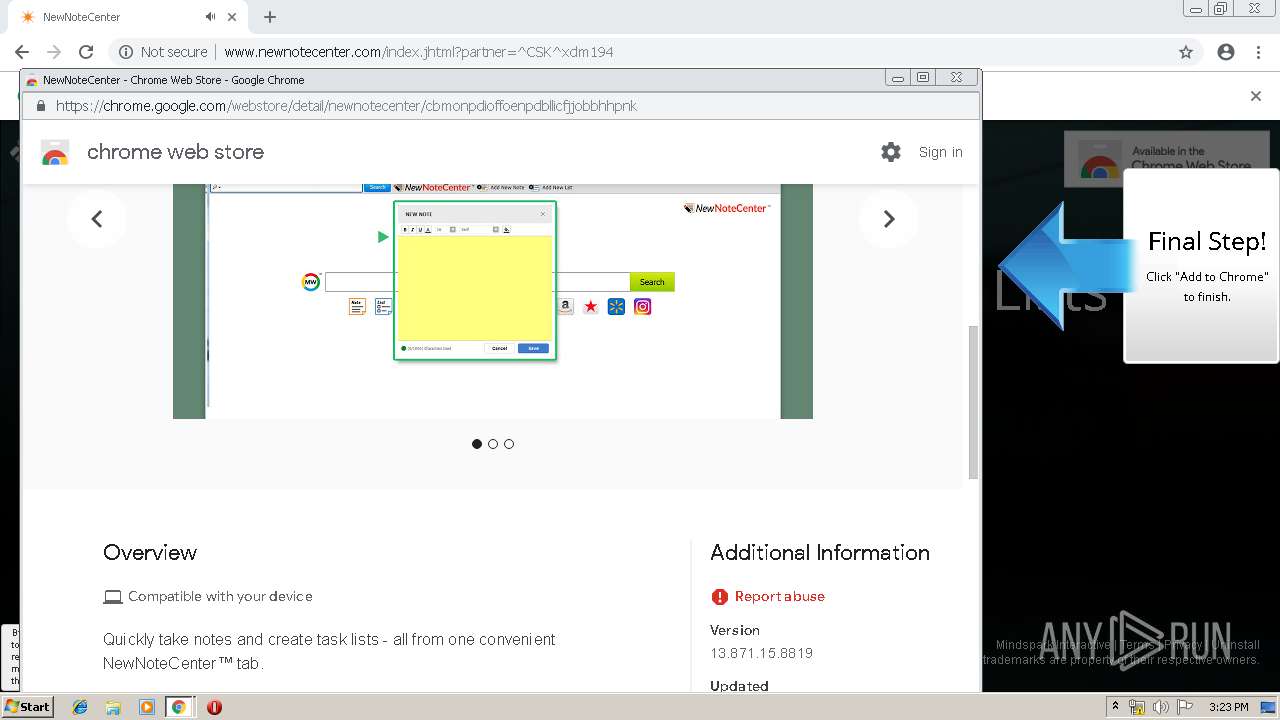
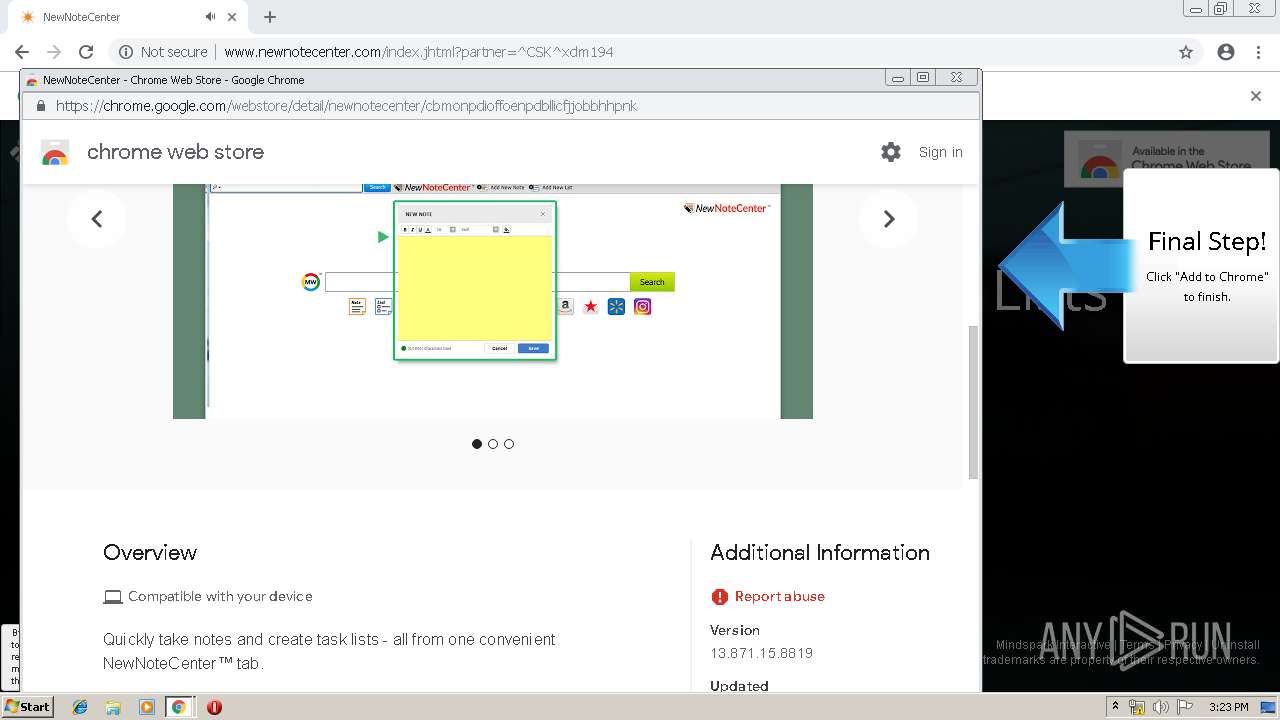
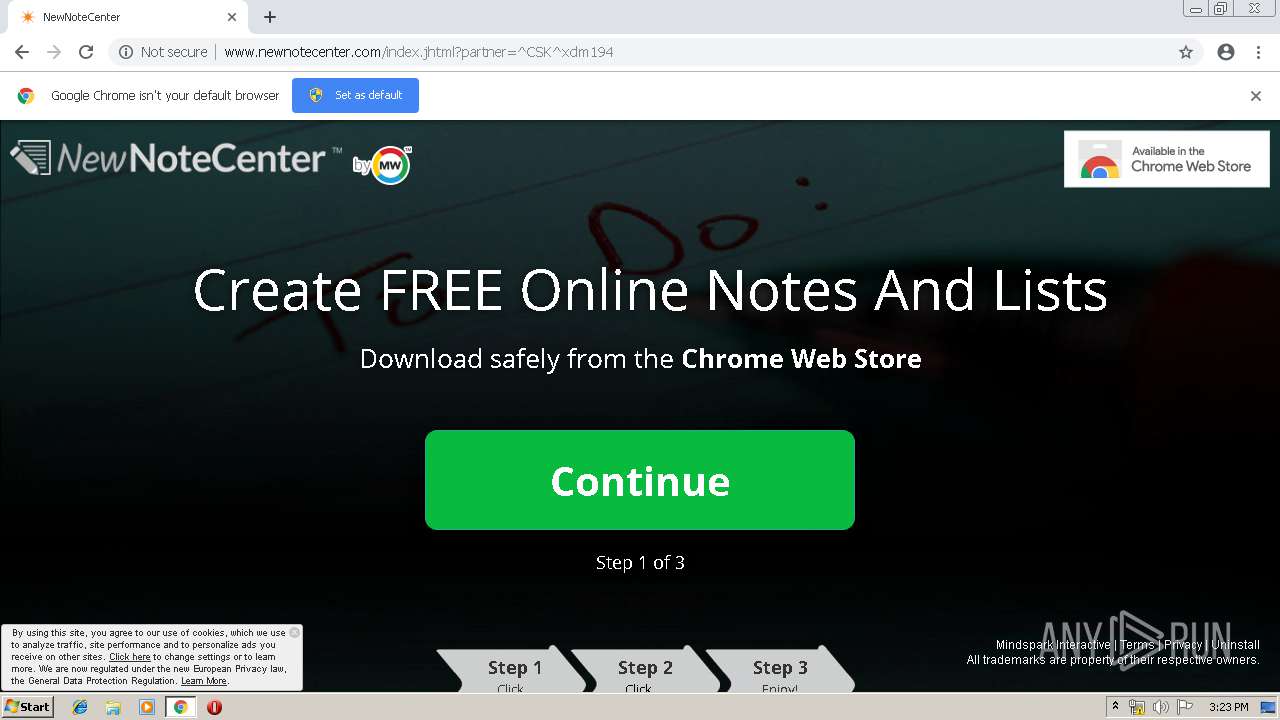
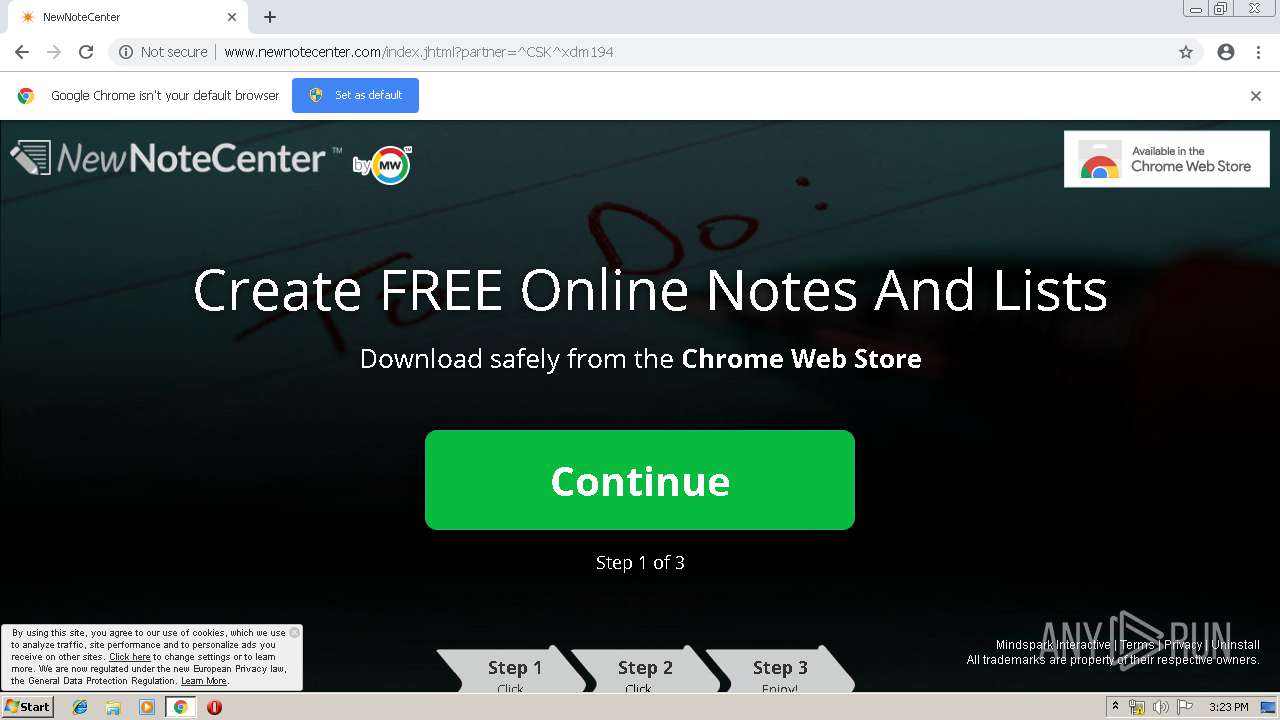
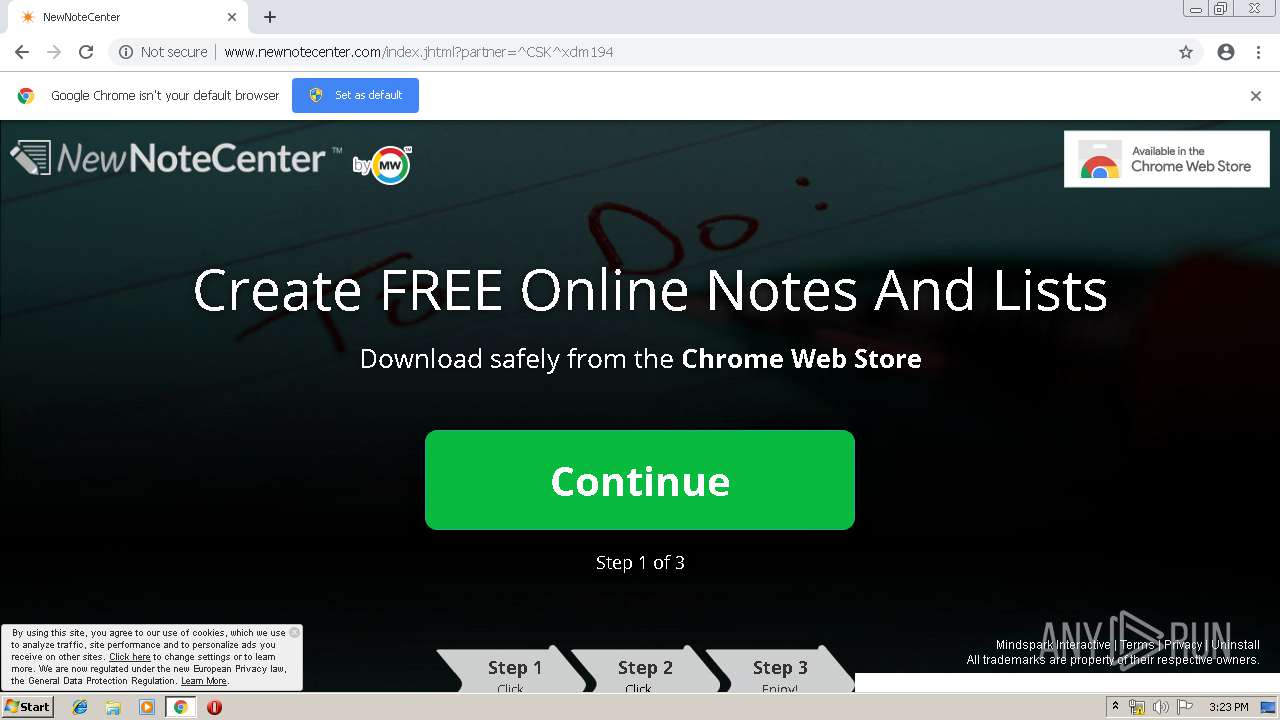
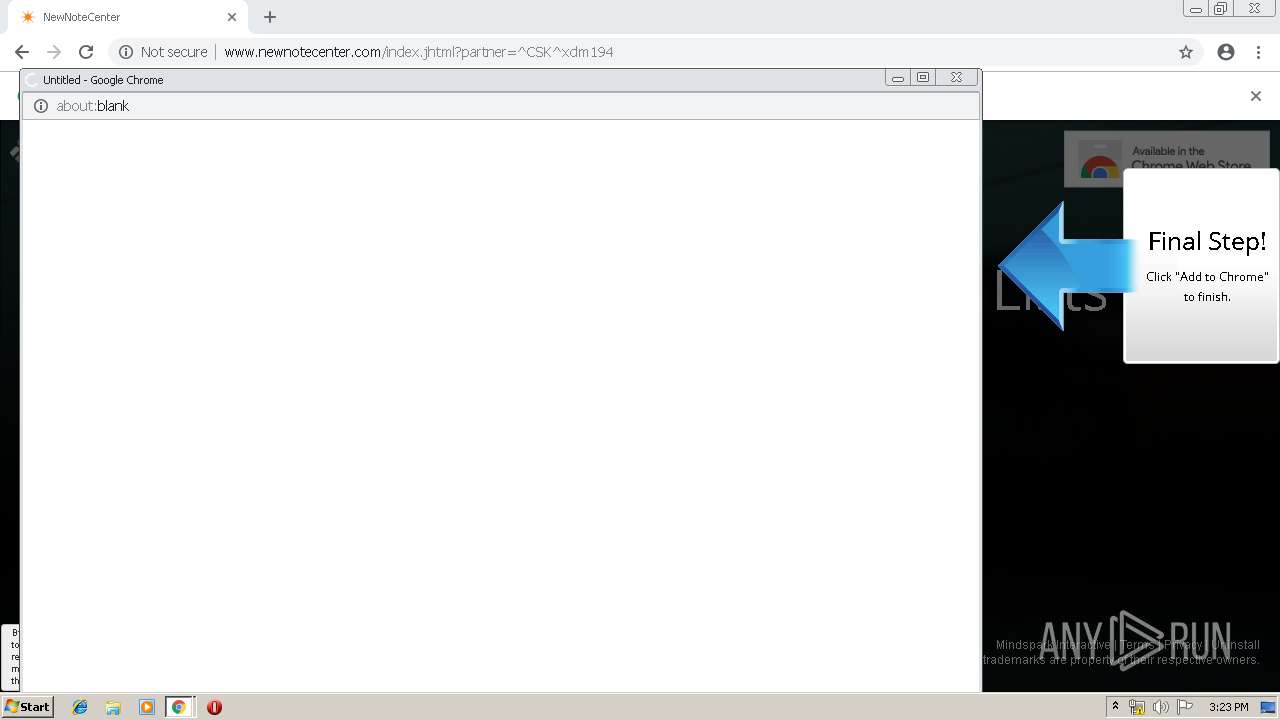
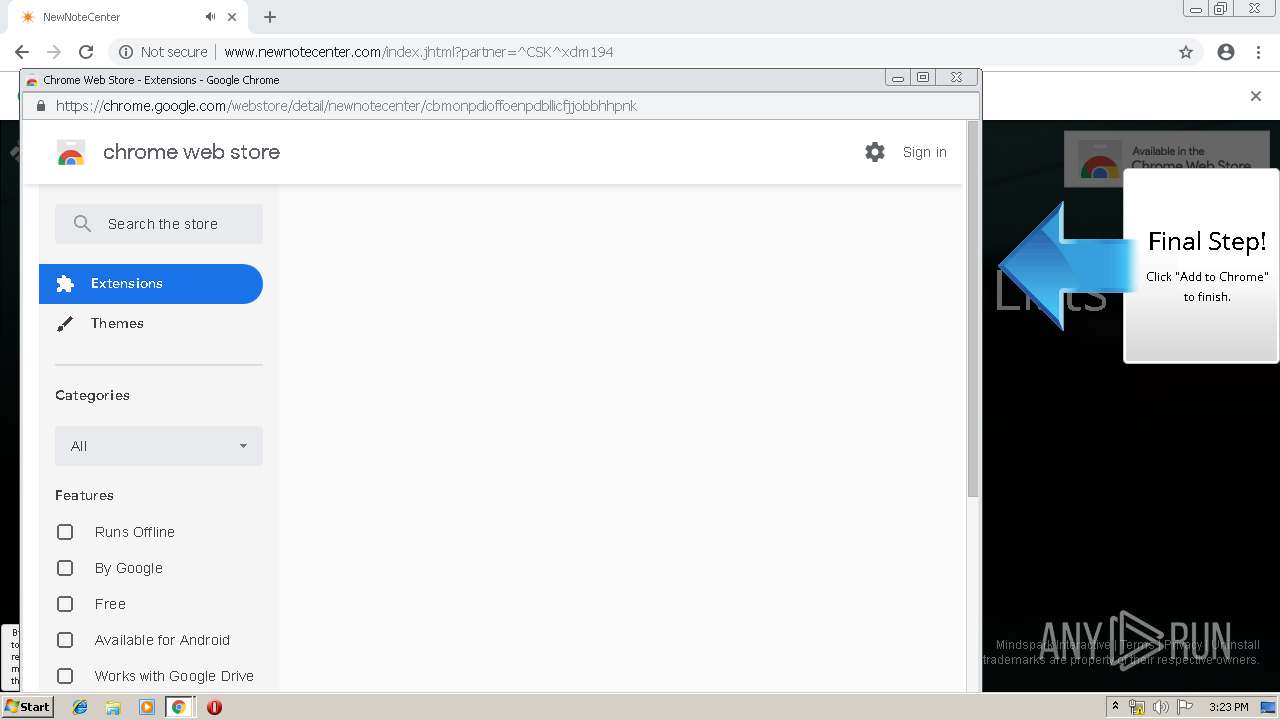
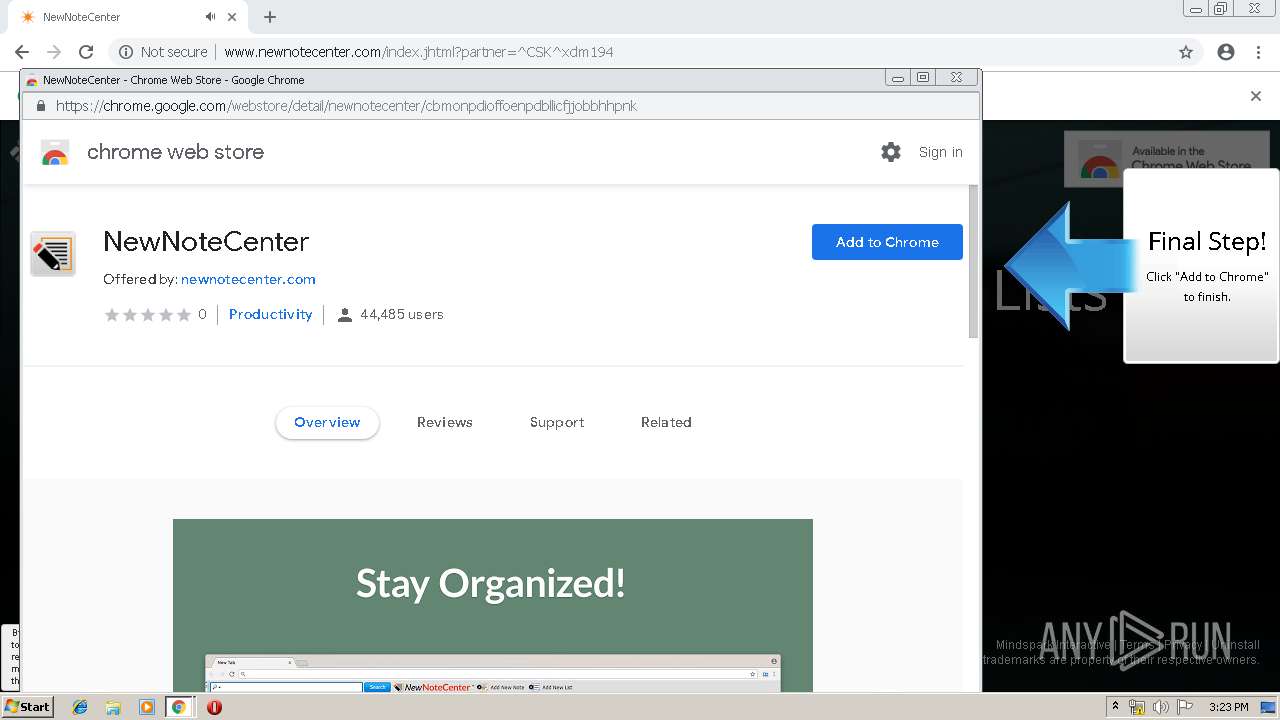
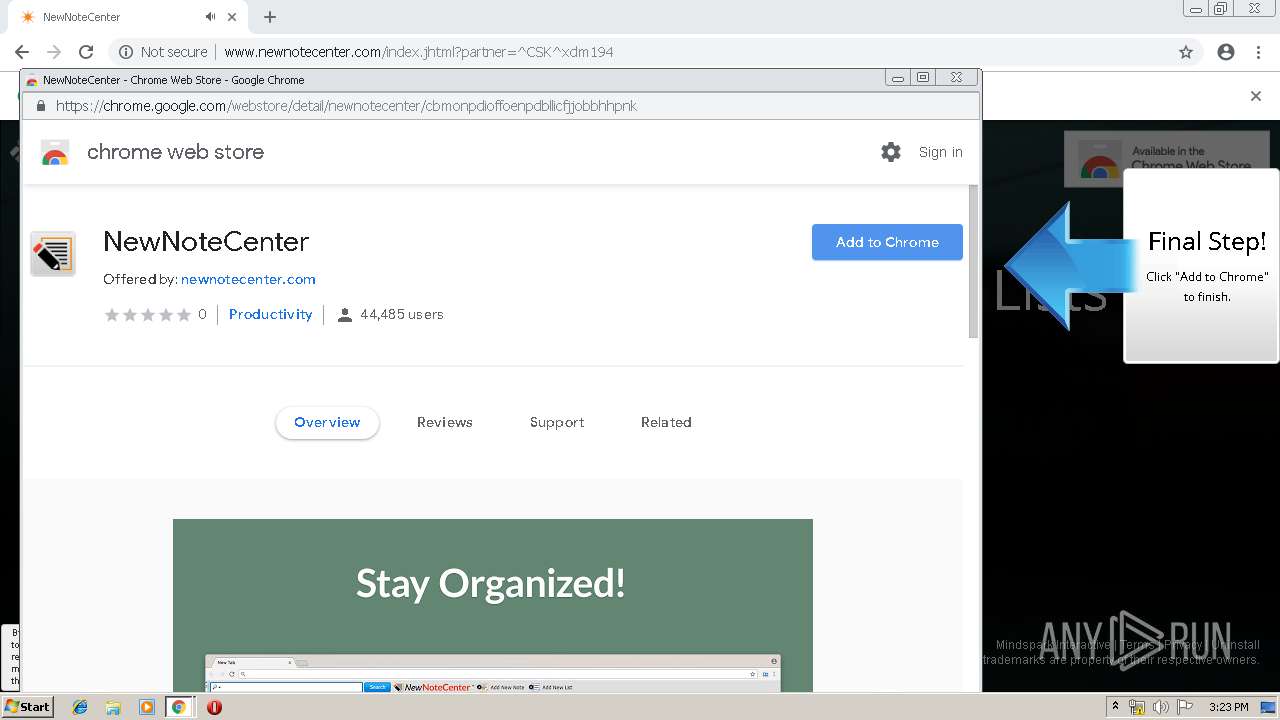
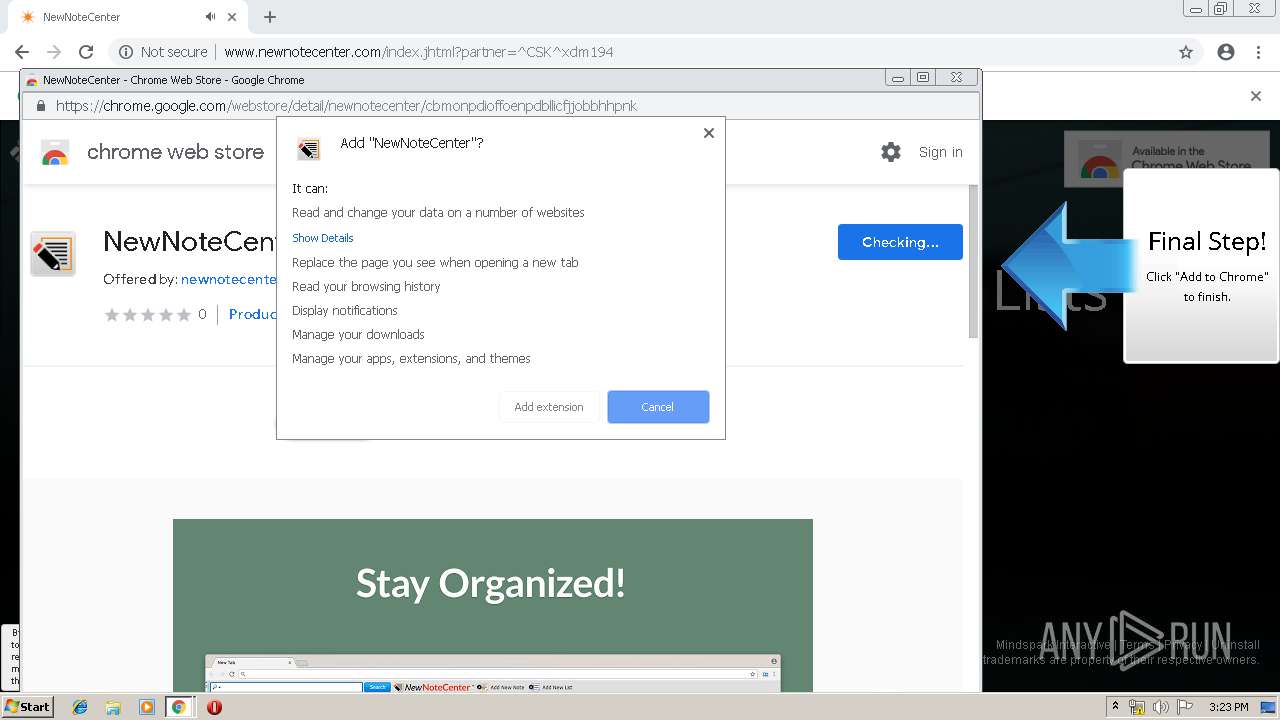
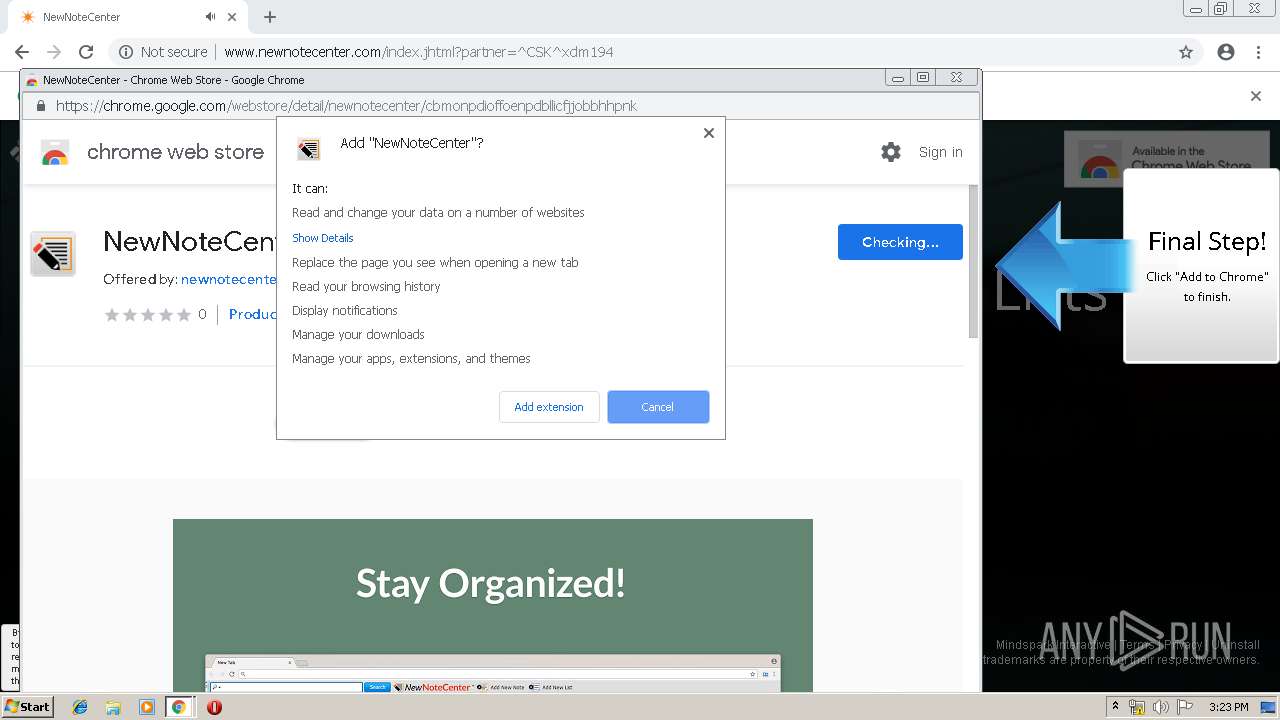
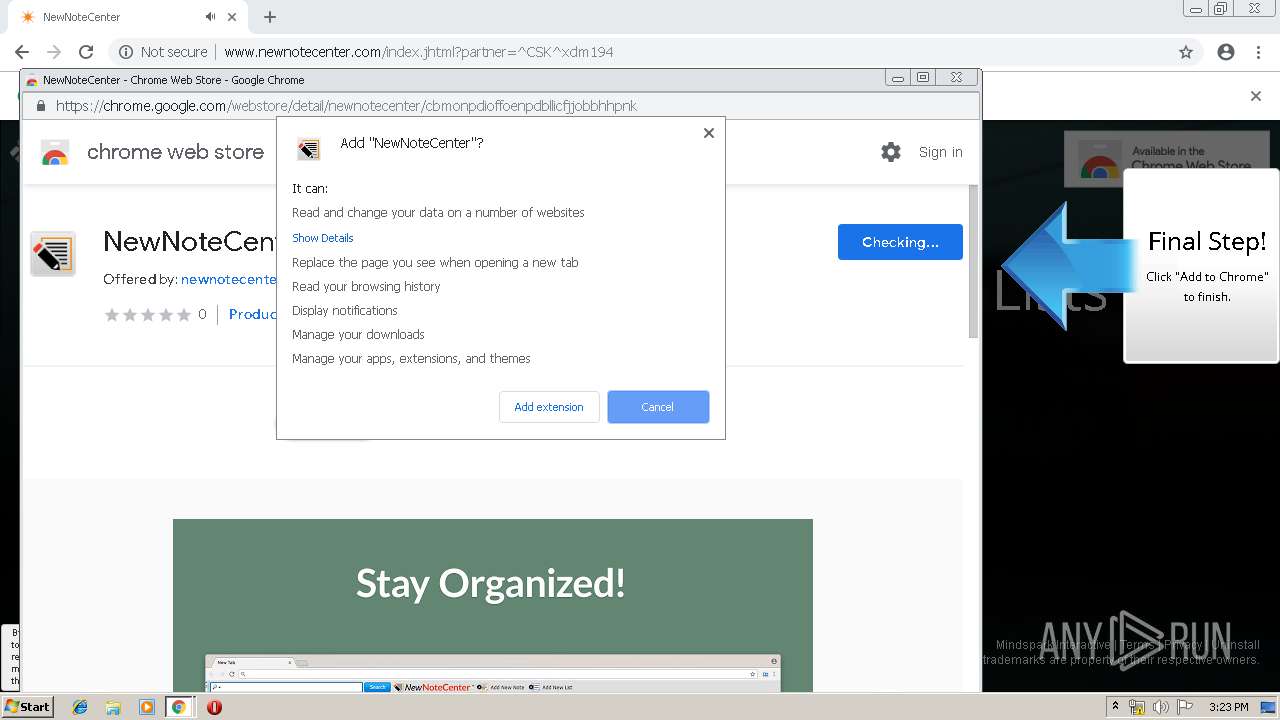
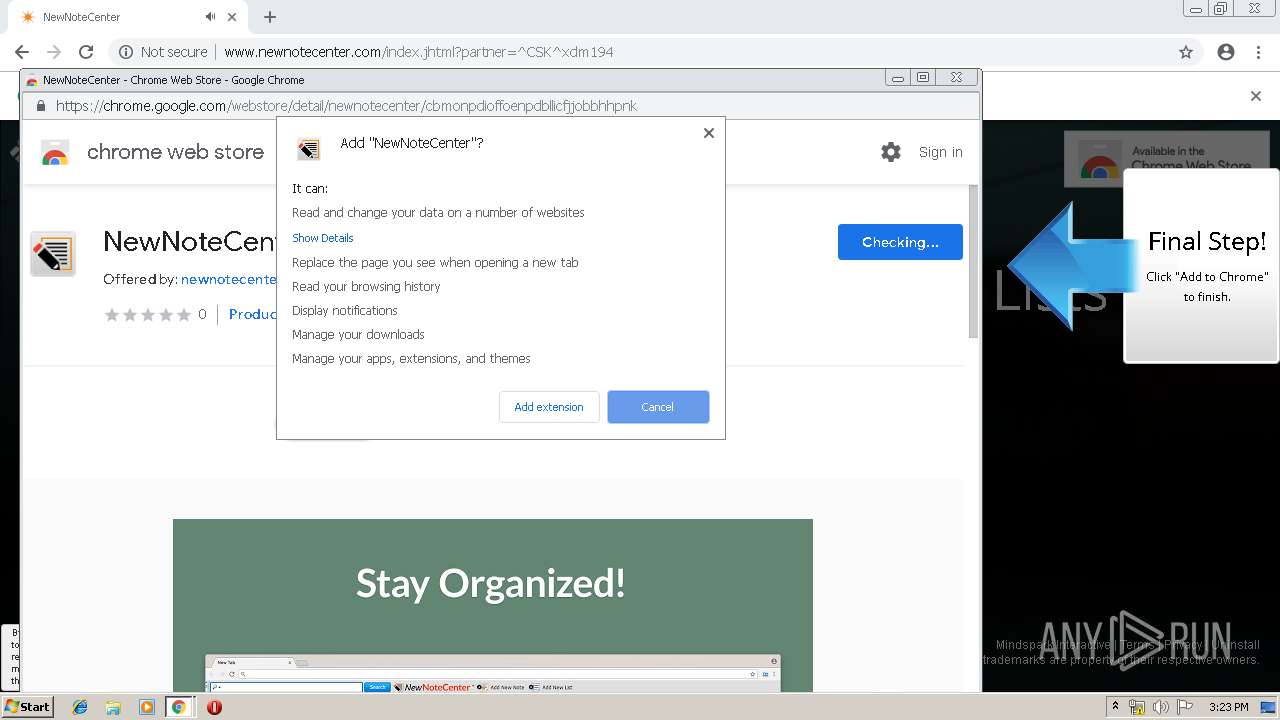
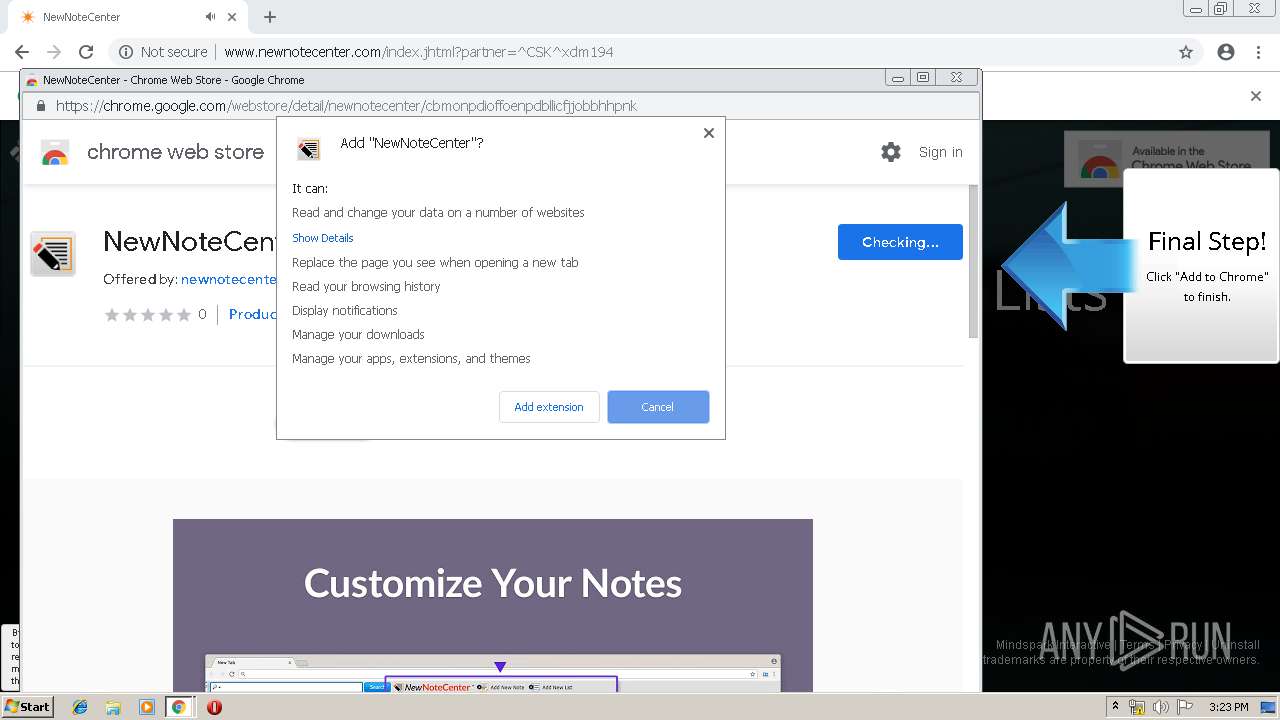
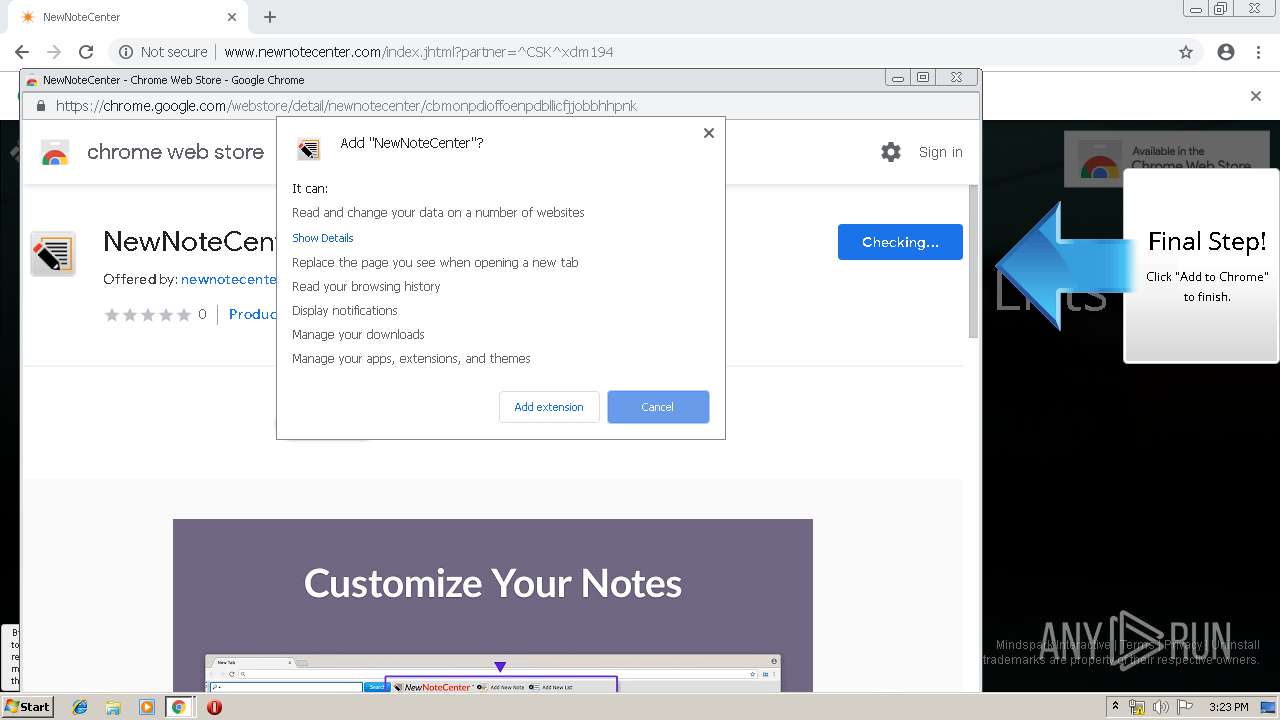
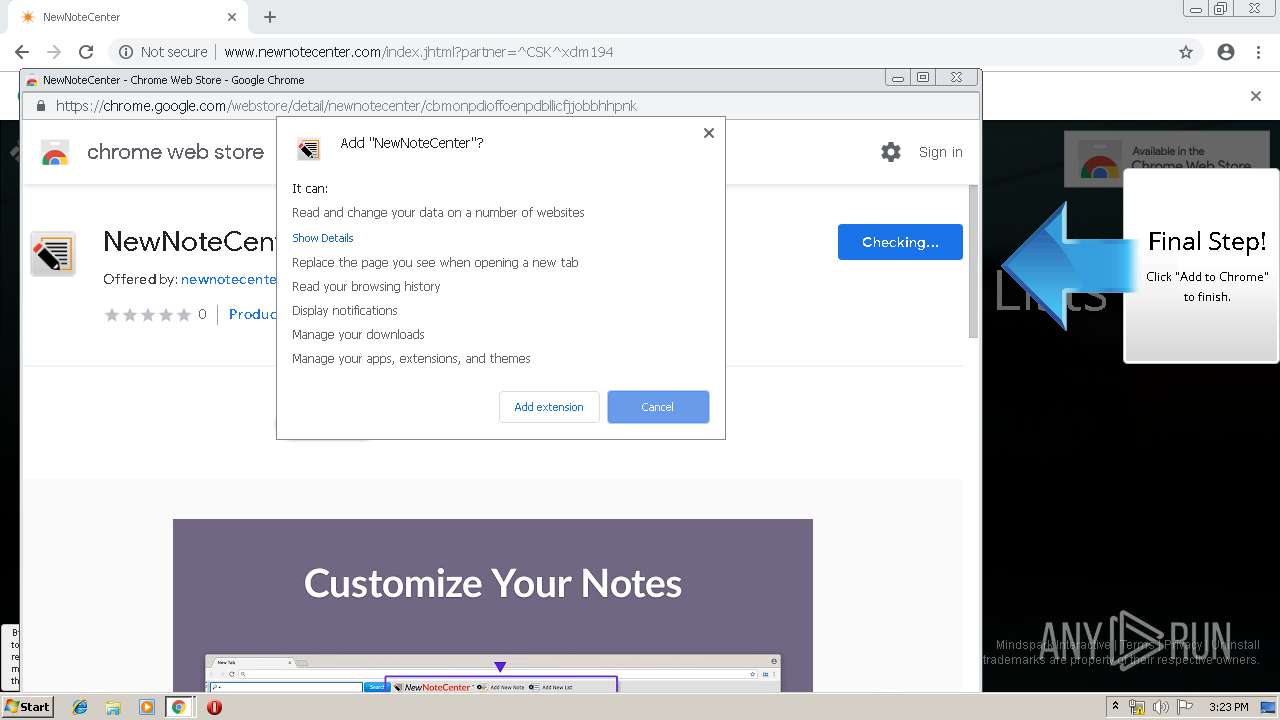
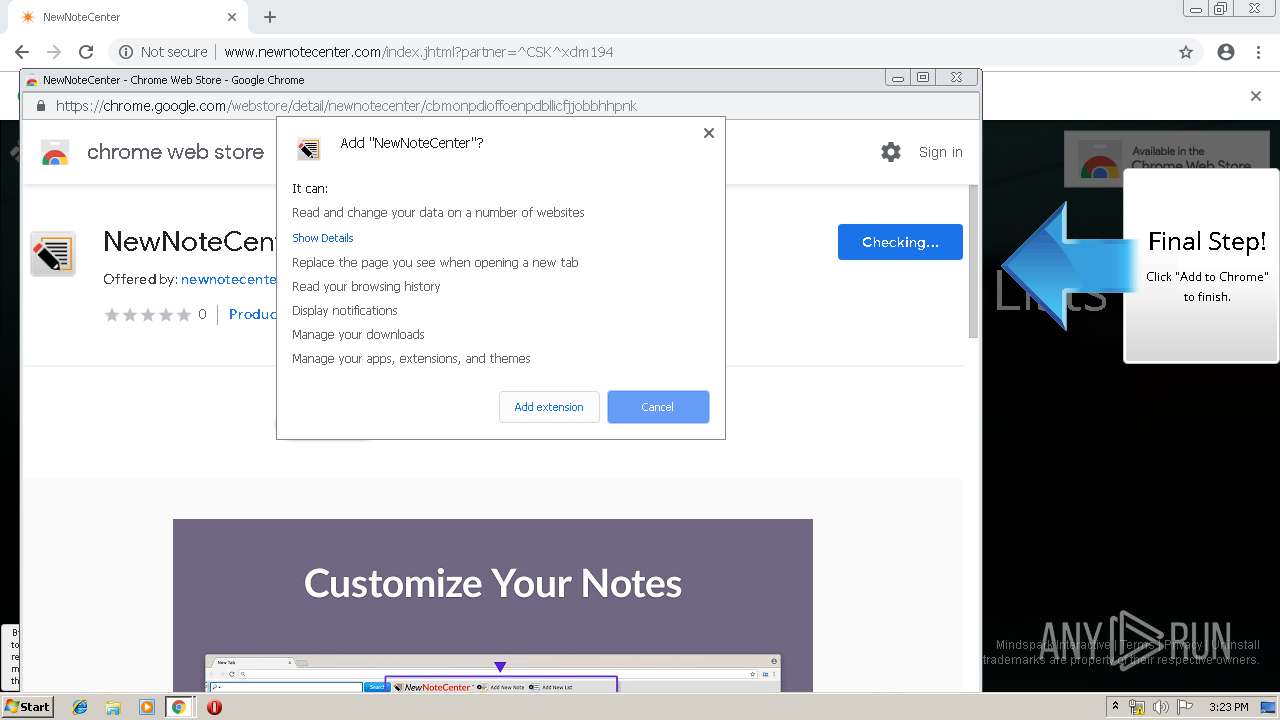
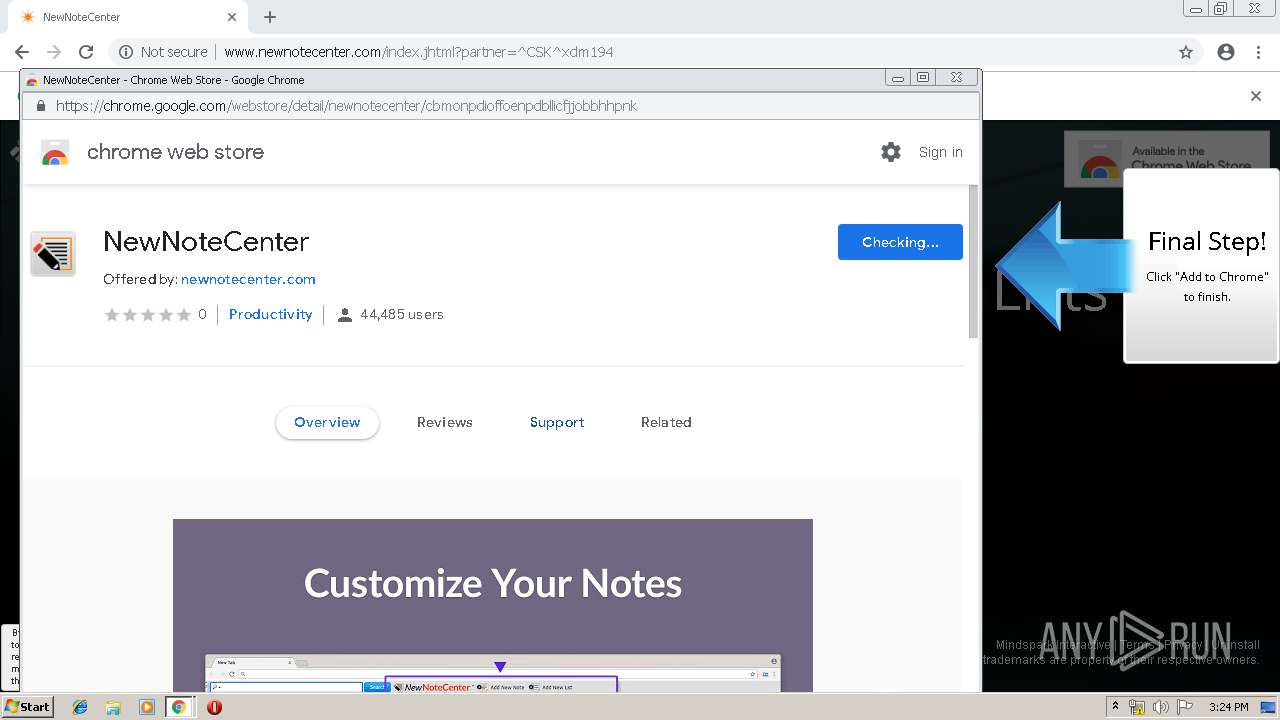
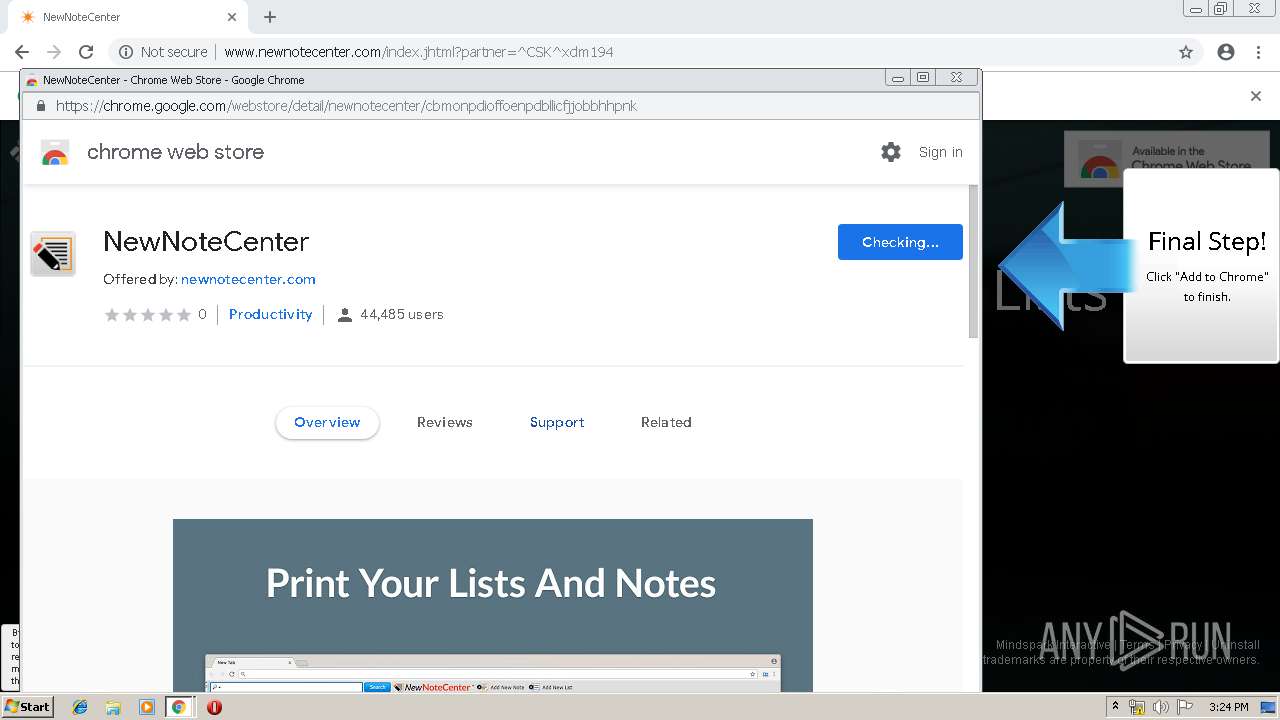
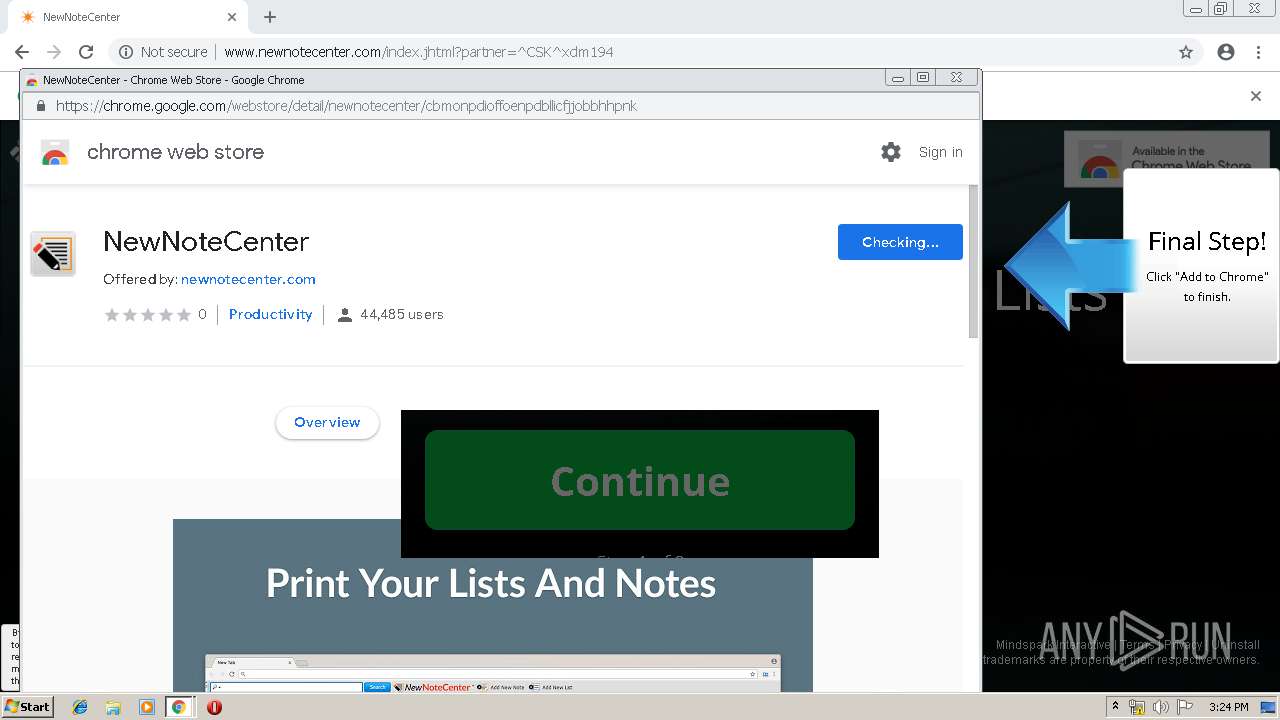
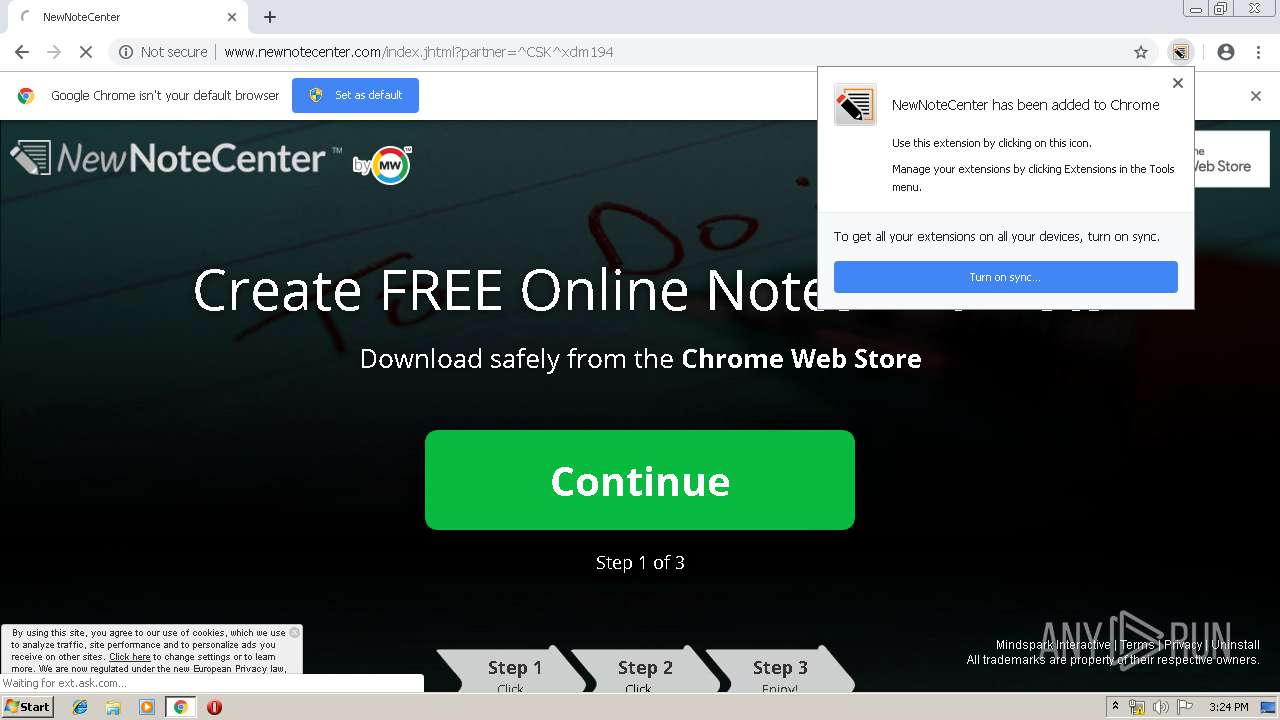
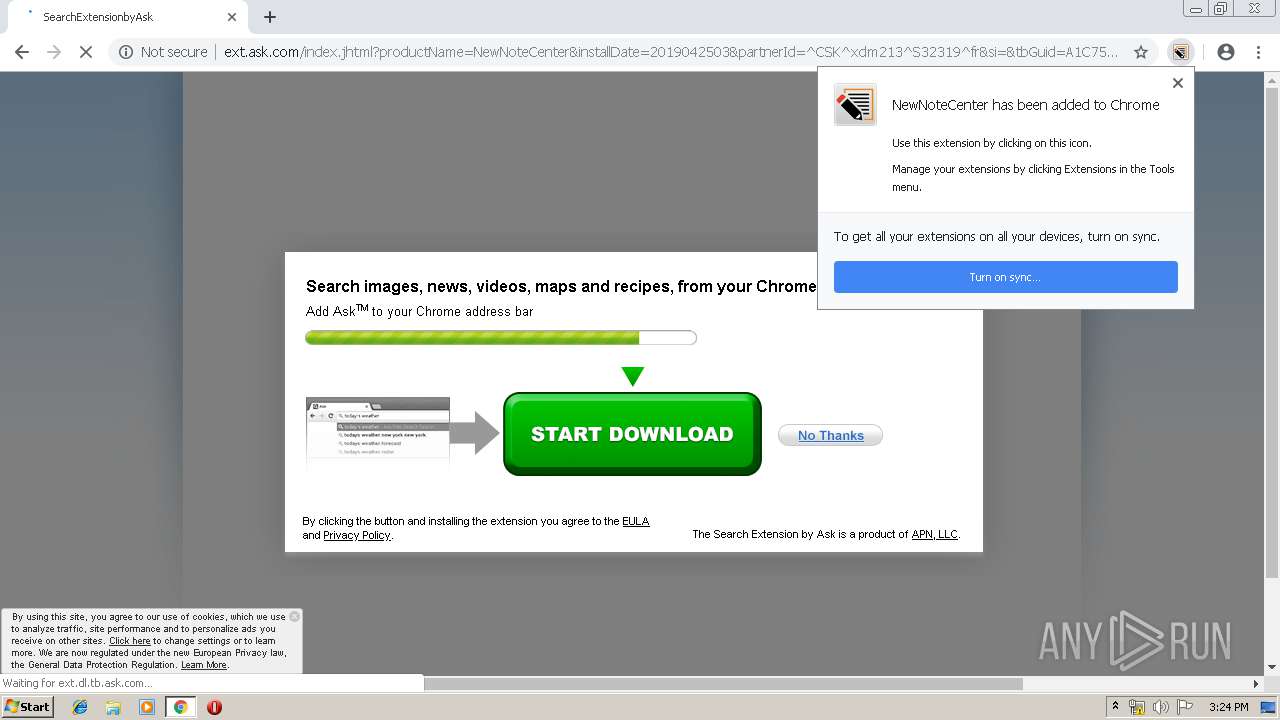
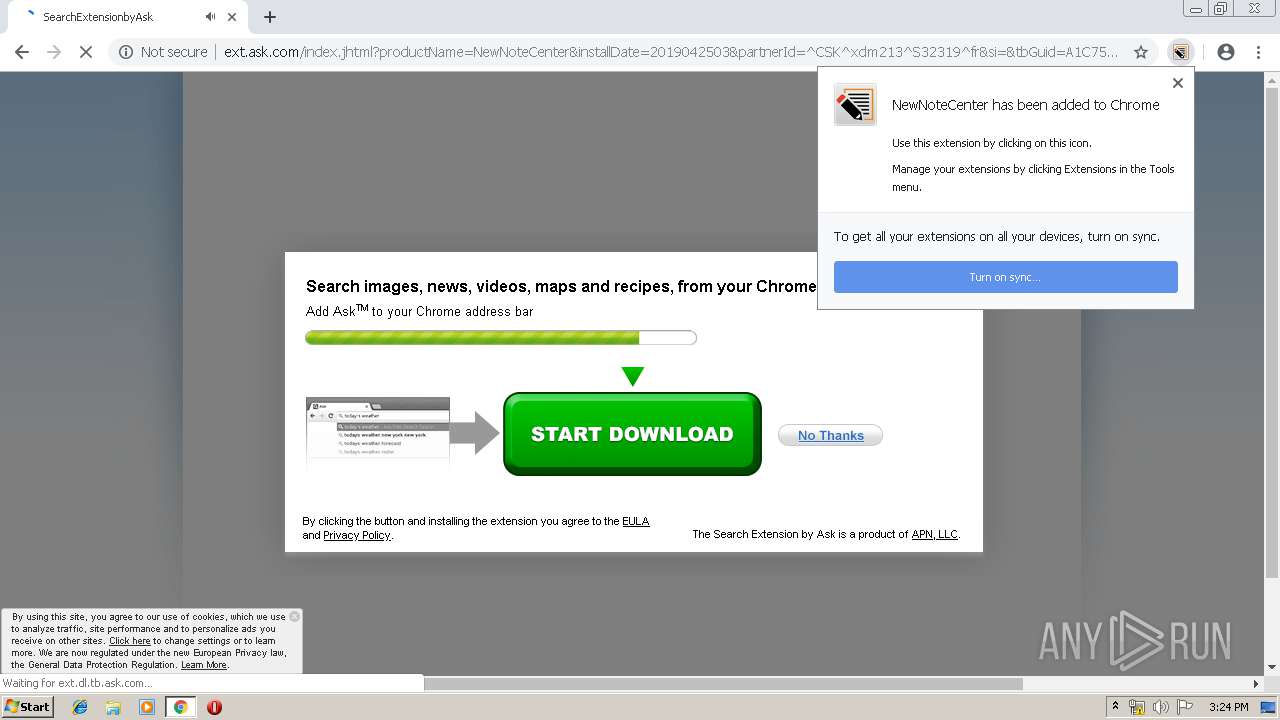
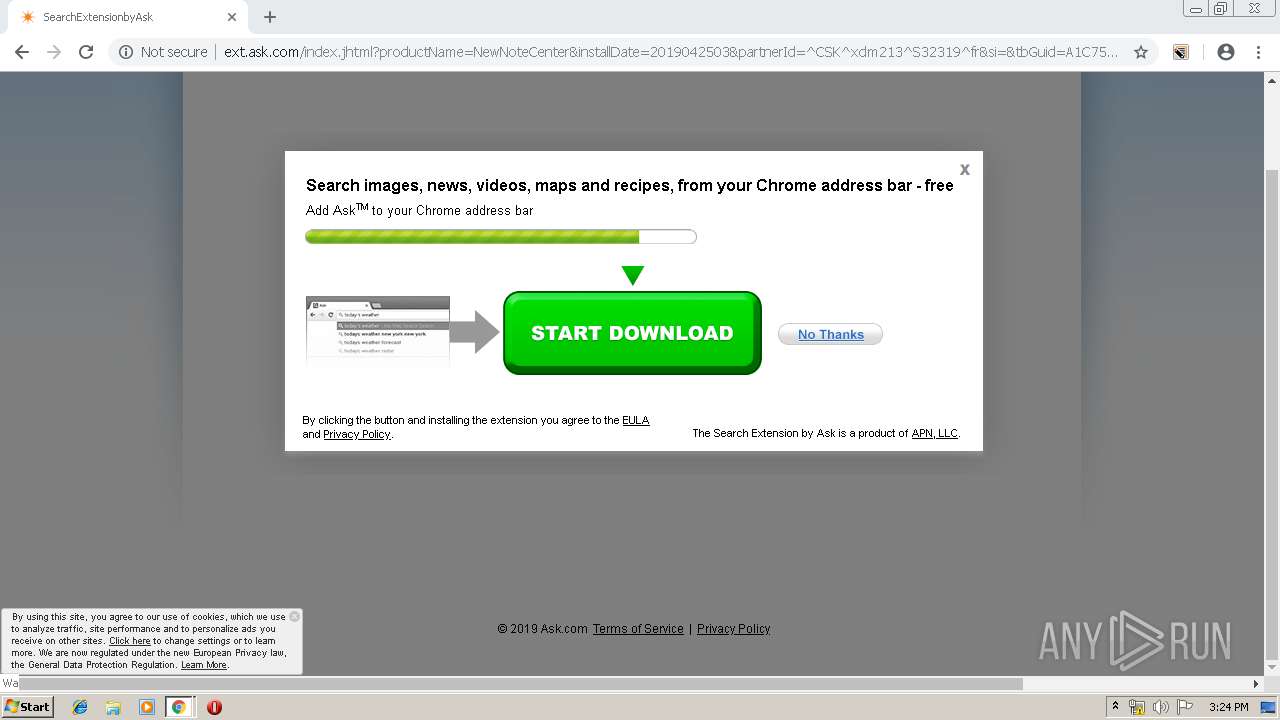
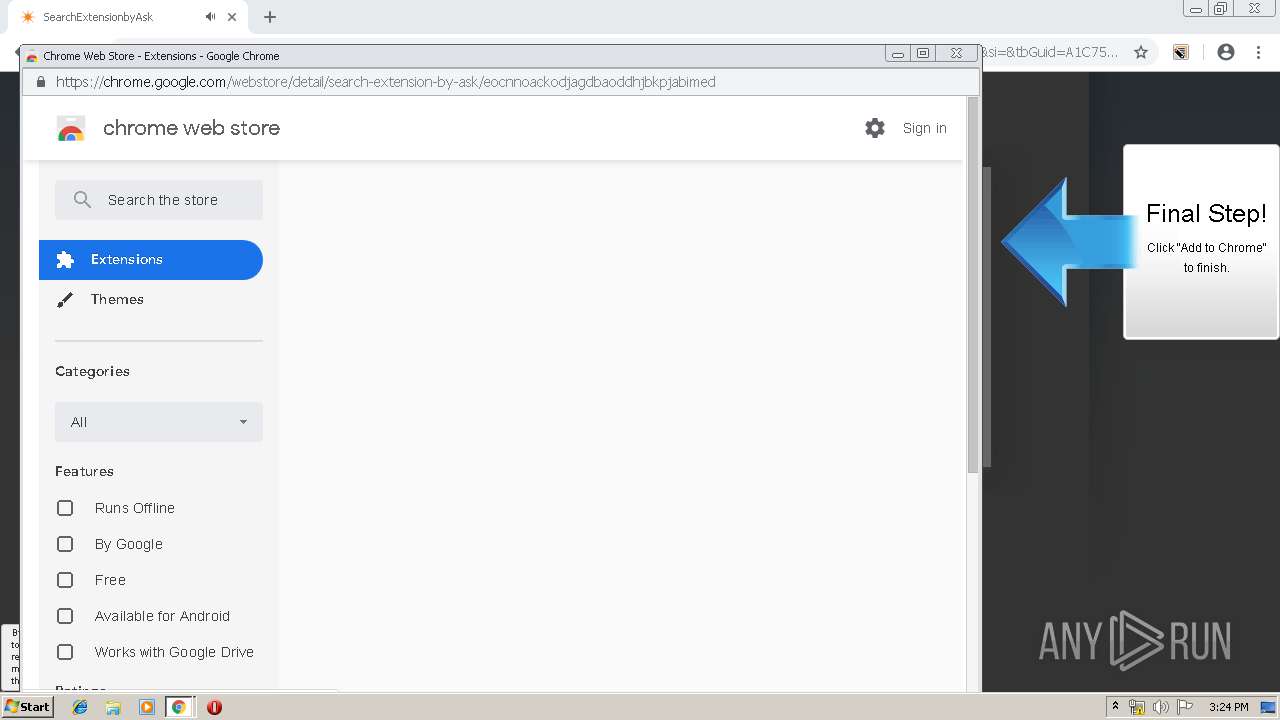
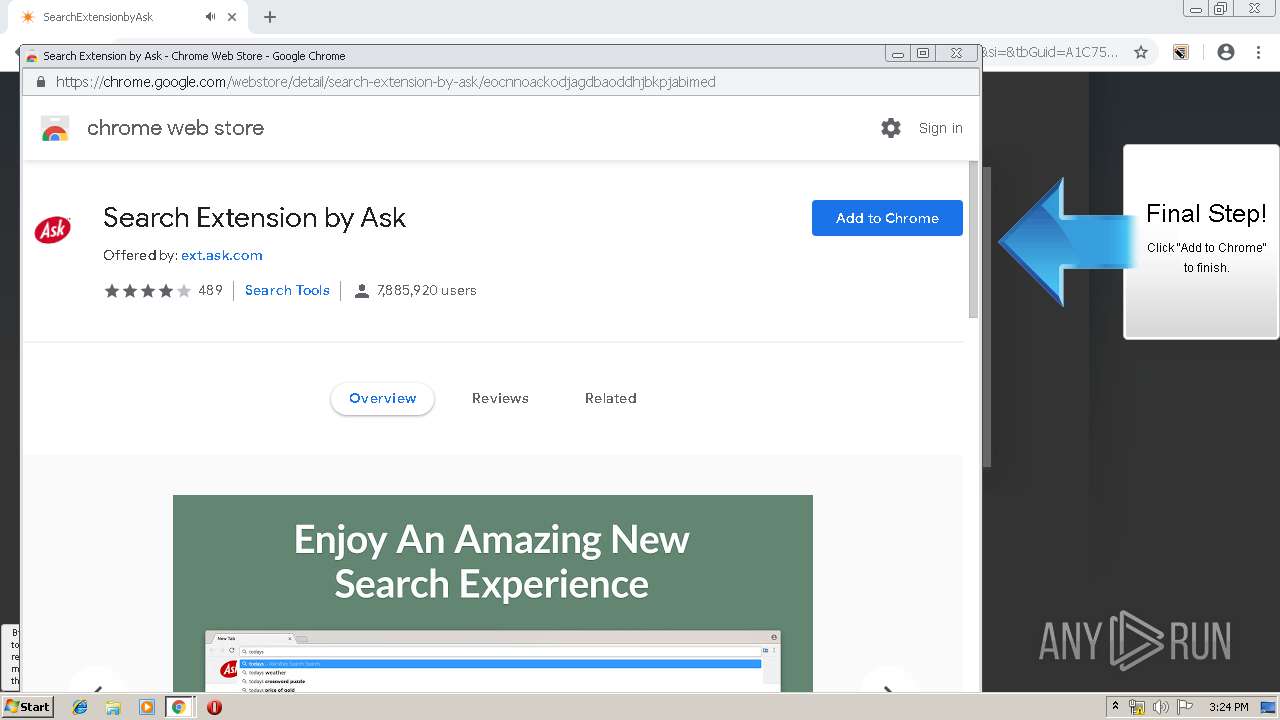
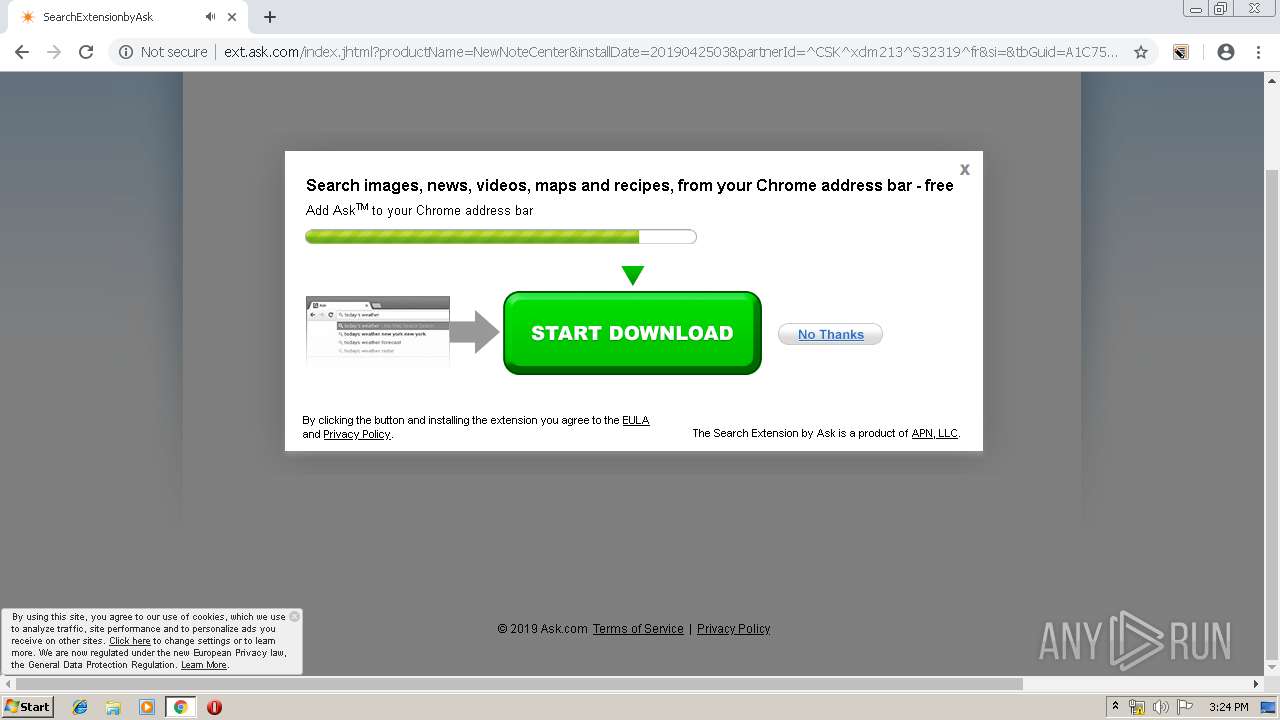
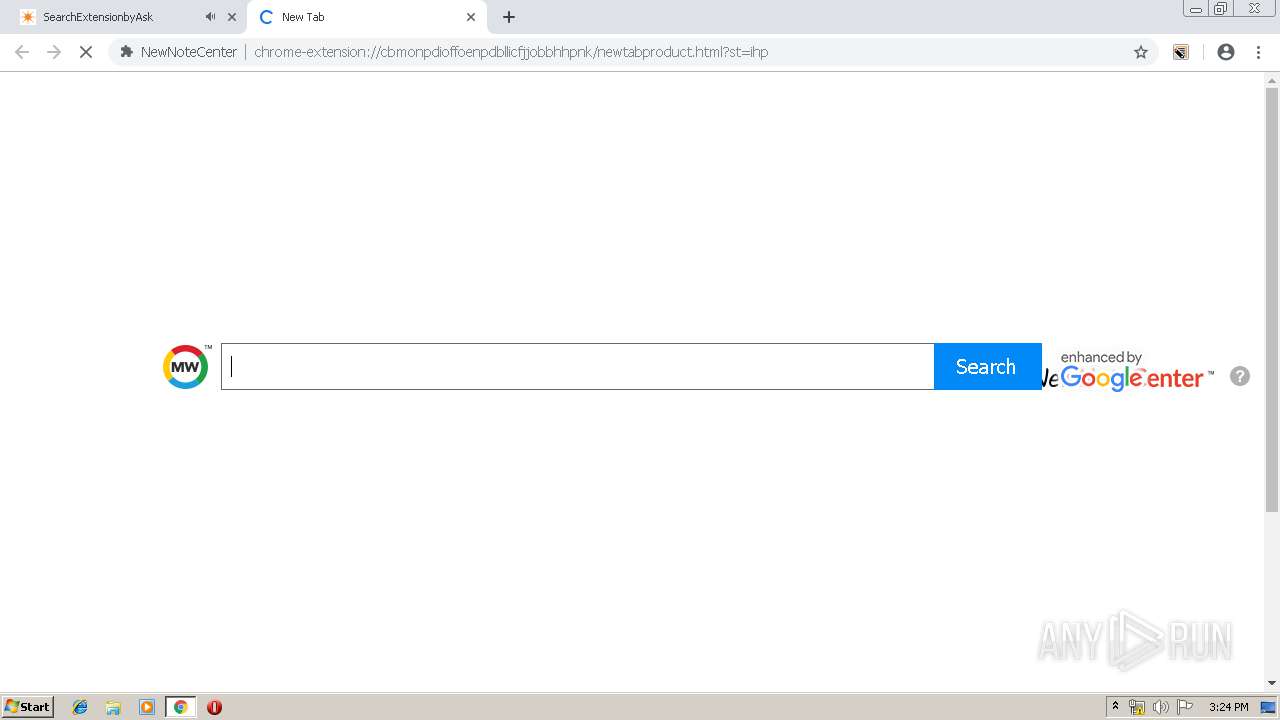
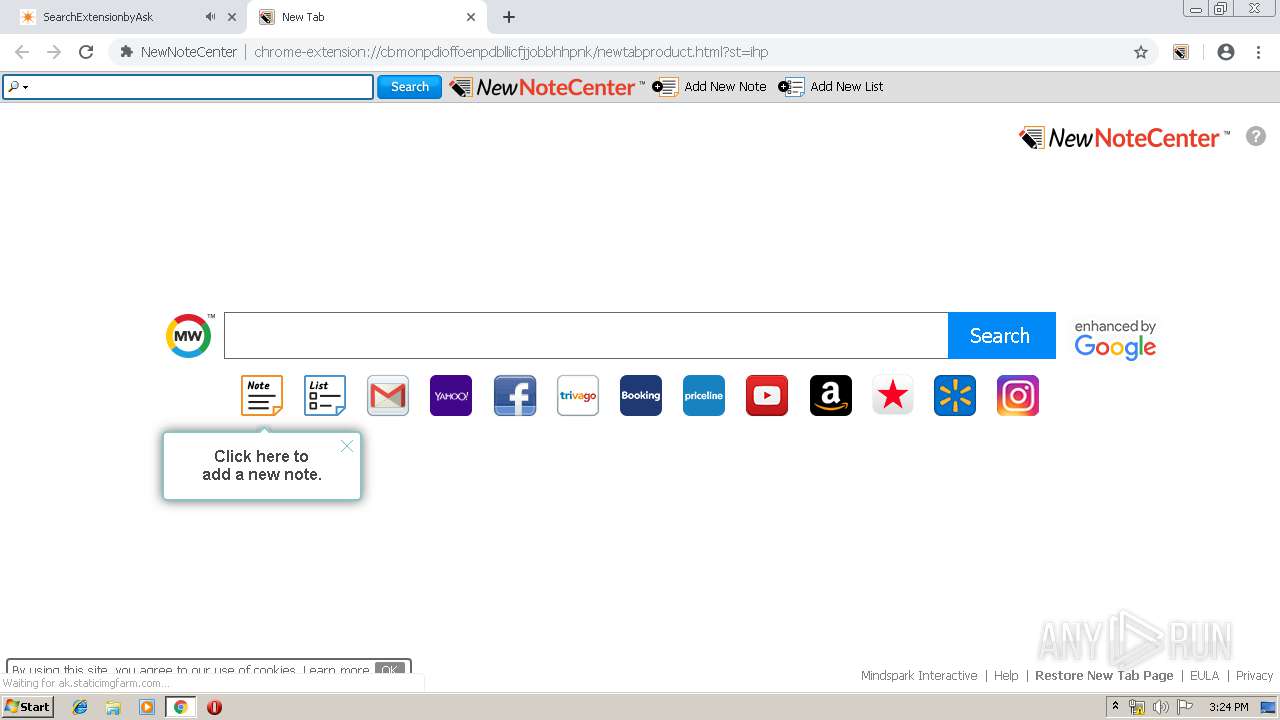
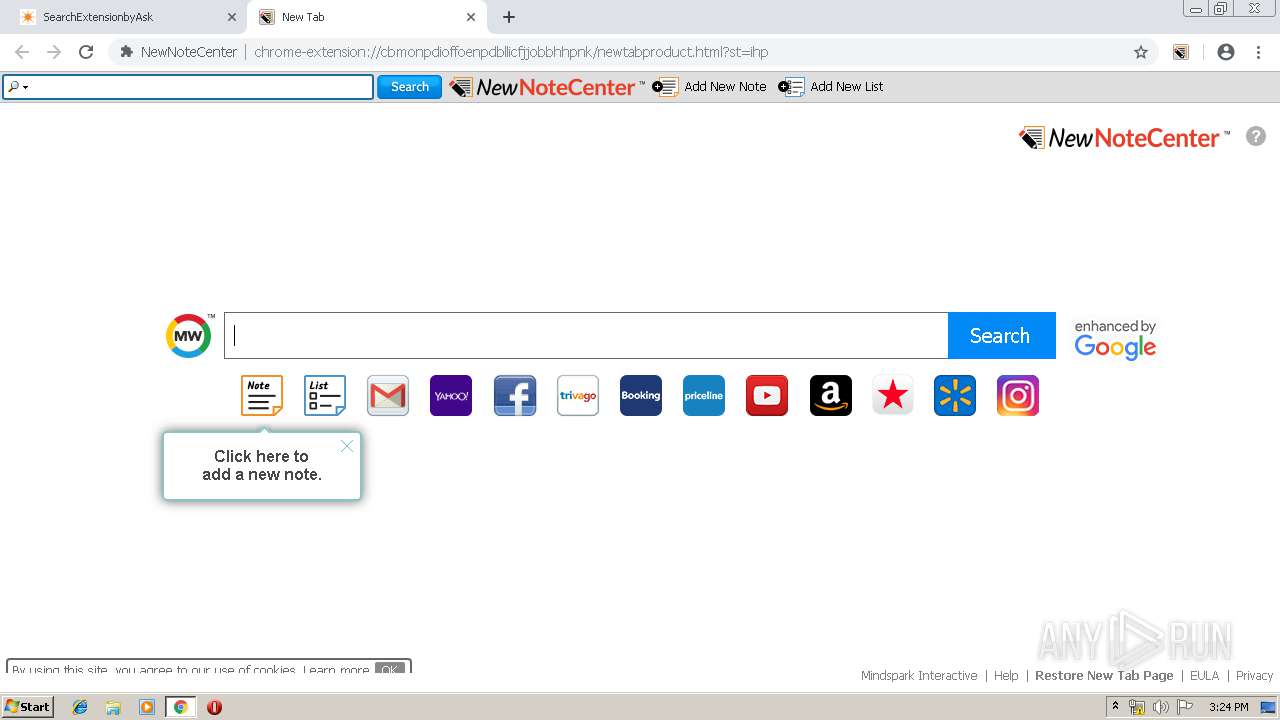
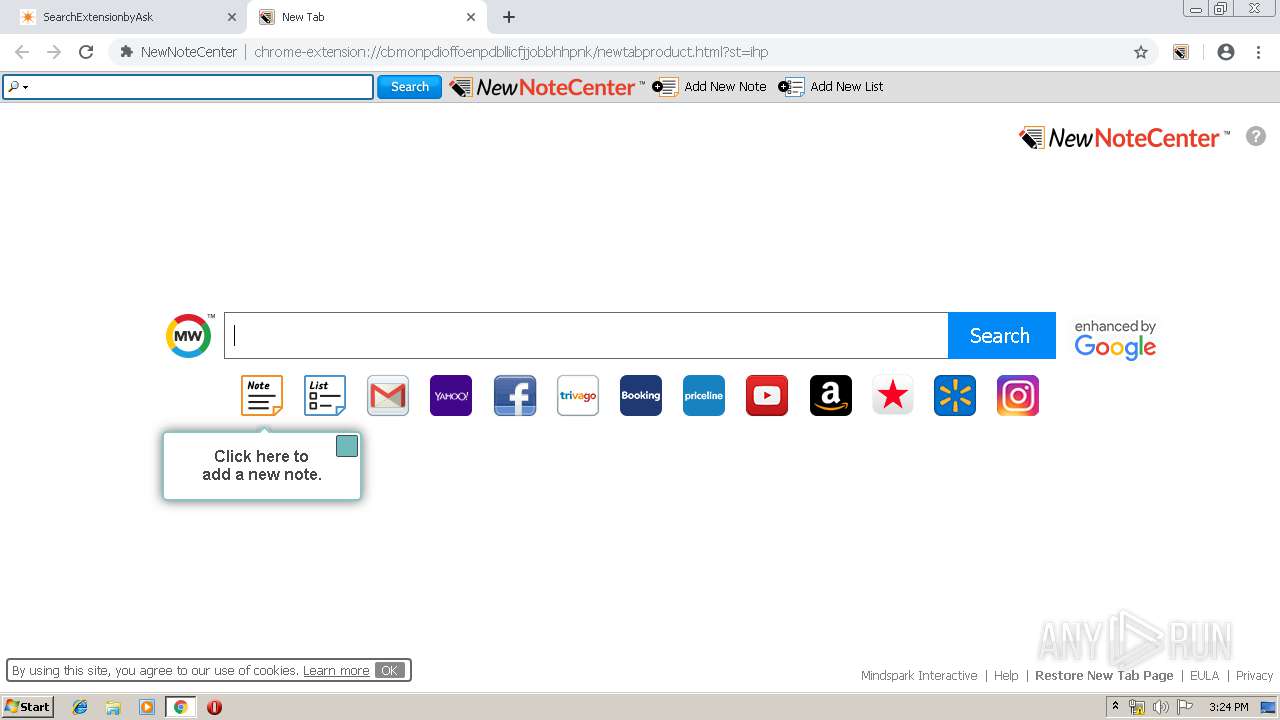
| URL: | http://www.newnotecenter.com/index.jhtml?partner=^CSK^xdm194 |
| Full analysis: | https://app.any.run/tasks/0e3e4b11-58e5-4906-9cf8-4ff1640c47fe |
| Verdict: | Malicious activity |
| Analysis date: | April 25, 2019, 14:22:52 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | ECDB17ED08E874E33FA9B1F8EB14BCE6 |
| SHA1: | 9854646F1AA8ACCC9B0D76C2B931017CC4B3D69E |
| SHA256: | 9CAD56CFAC7E52861074F7711475F49083FC09F16C3DC6029468B982BF2616DA |
| SSDEEP: | 3:N1KJS404iA6GKbBUUVEXR0xg:Cc40Z5BUUuXWg |
MALICIOUS
No malicious indicators.SUSPICIOUS
Modifies files in Chrome extension folder
- chrome.exe (PID: 1640)
INFO
Creates files in the user directory
- chrome.exe (PID: 1640)
Application launched itself
- chrome.exe (PID: 1640)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
73
Monitored processes
41
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 184 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=920,11659240946840176554,15815387434956610658,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=9144260984579155393 --mojo-platform-channel-handle=2856 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 320 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=920,11659240946840176554,15815387434956610658,131072 --enable-features=PasswordImport --service-pipe-token=3441641636029546378 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=3441641636029546378 --renderer-client-id=5 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2020 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 636 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=920,11659240946840176554,15815387434956610658,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=9835530348311002573 --mojo-platform-channel-handle=6104 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 760 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=920,11659240946840176554,15815387434956610658,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=7534789438624025912 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7534789438624025912 --renderer-client-id=7 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3780 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 768 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=920,11659240946840176554,15815387434956610658,131072 --enable-features=PasswordImport --service-pipe-token=5829328105843343547 --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5829328105843343547 --renderer-client-id=3 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2208 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1016 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=watcher --main-thread-id=2168 --on-initialized-event-handle=308 --parent-handle=312 /prefetch:6 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1136 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=920,11659240946840176554,15815387434956610658,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=14117026037778684278 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=14117026037778684278 --renderer-client-id=34 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2616 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1296 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=920,11659240946840176554,15815387434956610658,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=4774369285881914917 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=4774369285881914917 --renderer-client-id=12 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=5624 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1452 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=920,11659240946840176554,15815387434956610658,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=6809888598045300521 --mojo-platform-channel-handle=4408 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
| 1476 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=920,11659240946840176554,15815387434956610658,131072 --enable-features=PasswordImport --disable-gpu-compositing --service-pipe-token=9626853083083108199 --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9626853083083108199 --renderer-client-id=37 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=1732 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google Inc. Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 73.0.3683.75 Modules
| |||||||||||||||
Total events
756
Read events
618
Write events
132
Delete events
6
Modification events
| (PID) Process: | (1640) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (1640) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (1640) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: | |||
| (PID) Process: | (1640) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\ThirdParty |
| Operation: | write | Name: | StatusCodes |
Value: 01000000 | |||
| (PID) Process: | (1640) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (1016) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | write | Name: | 1640-13200675793051750 |
Value: 259 | |||
| (PID) Process: | (1640) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Update\ClientState\{8A69D345-D564-463c-AFF1-A69D9E530F96} |
| Operation: | write | Name: | dr |
Value: 1 | |||
| (PID) Process: | (1640) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome |
| Operation: | write | Name: | UsageStatsInSample |
Value: 0 | |||
| (PID) Process: | (1640) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 3488-13197474229333984 |
Value: 0 | |||
| (PID) Process: | (1640) chrome.exe | Key: | HKEY_CURRENT_USER\Software\Google\Chrome\BrowserExitCodes |
| Operation: | delete value | Name: | 1640-13200675793051750 |
Value: 259 | |||
Executable files
0
Suspicious files
79
Text files
241
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1640 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 1640 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
| 1640 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_1 | — | |
MD5:— | SHA256:— | |||
| 1640 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_2 | — | |
MD5:— | SHA256:— | |||
| 1640 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\ShaderCache\GPUCache\data_3 | — | |
MD5:— | SHA256:— | |||
| 1640 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\1c9c16f0-a4af-4a1f-84c4-061e8d2effec.tmp | — | |
MD5:— | SHA256:— | |||
| 1640 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\000018.dbtmp | — | |
MD5:— | SHA256:— | |||
| 1640 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\data_reduction_proxy_leveldb\CURRENT | — | |
MD5:— | SHA256:— | |||
| 1640 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\index | — | |
MD5:— | SHA256:— | |||
| 1640 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\GPUCache\data_0 | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
67
TCP/UDP connections
96
DNS requests
65
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1640 | chrome.exe | GET | 204 | 35.244.218.203:80 | http://www.newnotecenter.com/anemone.jhtml?anxuu=E3C3841C-B919-43FD-94A3-3C1086CAE514&anxa=CAPDownloadProcess&anxv=1.0.0&anxd=2011-06-01T00%3A00%3A00Z&anxsn=prod-dlp-europe-west1-93zm&anxu=http%3A%2F%2Fwww.newnotecenter.com%2Findex.jhtml&anxl=en-US&anxlv=1556202196116&anxsq=5&cookiesEnabled=1&pageLoad=1318&anxe=SplashLanding&anxr=1983800630 | US | — | — | whitelisted |
1640 | chrome.exe | GET | 302 | 185.31.128.129:80 | http://20787046p.rfihub.com/ca.gif?rb=32555&ca=20787046&_o=32555&_t=20787046&ra=REPLACE_ME_WITH_YOUR_CACHE_BUSTING | US | — | — | whitelisted |
1640 | chrome.exe | GET | 200 | 35.244.218.203:80 | http://www.newnotecenter.com/index.jhtml?partner=^CSK^xdm194 | US | html | 44.8 Kb | whitelisted |
1640 | chrome.exe | GET | 200 | 35.244.218.203:80 | http://www.newnotecenter.com/splashPixels.jhtml?partner=%5eCSK%5exdm194 | US | html | 1.19 Kb | whitelisted |
1640 | chrome.exe | GET | 200 | 172.217.16.130:80 | http://www.googleadservices.com/pagead/conversion.js | US | text | 9.02 Kb | whitelisted |
1640 | chrome.exe | GET | 200 | 35.244.218.203:80 | http://www.newnotecenter.com/static/cws/audio.js | US | text | 649 b | whitelisted |
1640 | chrome.exe | GET | 200 | 2.18.232.251:80 | http://ak.staticimgfarm.com/images/webtooltab/ttdetect-2/prd/ttDetectUtil.js | unknown | text | 3.81 Kb | whitelisted |
1640 | chrome.exe | GET | 200 | 2.18.232.251:80 | http://ak.staticimgfarm.com/images/download/assist_21.gif | unknown | image | 39.5 Kb | whitelisted |
1640 | chrome.exe | GET | 204 | 35.244.218.203:80 | http://www.newnotecenter.com/anemone.jhtml?anxuu=E3C3841C-B919-43FD-94A3-3C1086CAE514&anxa=CAPDownloadProcess&anxv=1.0.0&anxd=2011-06-01T00%3A00%3A00Z&anxsn=prod-dlp-europe-west1-93zm&anxu=http%3A%2F%2Fwww.newnotecenter.com%2Findex.jhtml&anxl=en-US&anxlv=1556202195370&anxrd=none&anxrp=-&anxrk=-&anxrm=-&anxrb=-&anxrc=-&anxrs=-&anxsq=1&anxi=64293A5D-68C5-4DF8-A5A2-F831D2579FD1&anxe=backFill&anxr=165876050 | US | compressed | 649 b | whitelisted |
1640 | chrome.exe | GET | 200 | 35.244.218.203:80 | http://newnotecenter.dl.myway.com/localStorage.jhtml | US | html | 2.20 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1640 | chrome.exe | 172.217.16.131:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
1640 | chrome.exe | 35.244.218.203:80 | www.newnotecenter.com | — | US | whitelisted |
1640 | chrome.exe | 172.217.18.106:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
1640 | chrome.exe | 2.18.232.251:80 | ak.staticimgfarm.com | Akamai International B.V. | — | whitelisted |
1640 | chrome.exe | 2.18.232.251:443 | ak.staticimgfarm.com | Akamai International B.V. | — | whitelisted |
1640 | chrome.exe | 172.217.16.163:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
— | — | 35.244.218.203:80 | www.newnotecenter.com | — | US | whitelisted |
1640 | chrome.exe | 172.217.22.40:443 | www.googletagmanager.com | Google Inc. | US | whitelisted |
1640 | chrome.exe | 172.217.16.130:80 | www.googleadservices.com | Google Inc. | US | whitelisted |
1640 | chrome.exe | 185.31.128.129:80 | 20787046p.rfihub.com | Rocket Fuel Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
clientservices.googleapis.com |
| whitelisted |
www.newnotecenter.com |
| whitelisted |
accounts.google.com |
| shared |
fonts.googleapis.com |
| whitelisted |
ak.staticimgfarm.com |
| whitelisted |
ak.imgfarm.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
akz.imgfarm.com |
| whitelisted |
eula.mindspark.com |
| malicious |
support.myway.com |
| whitelisted |