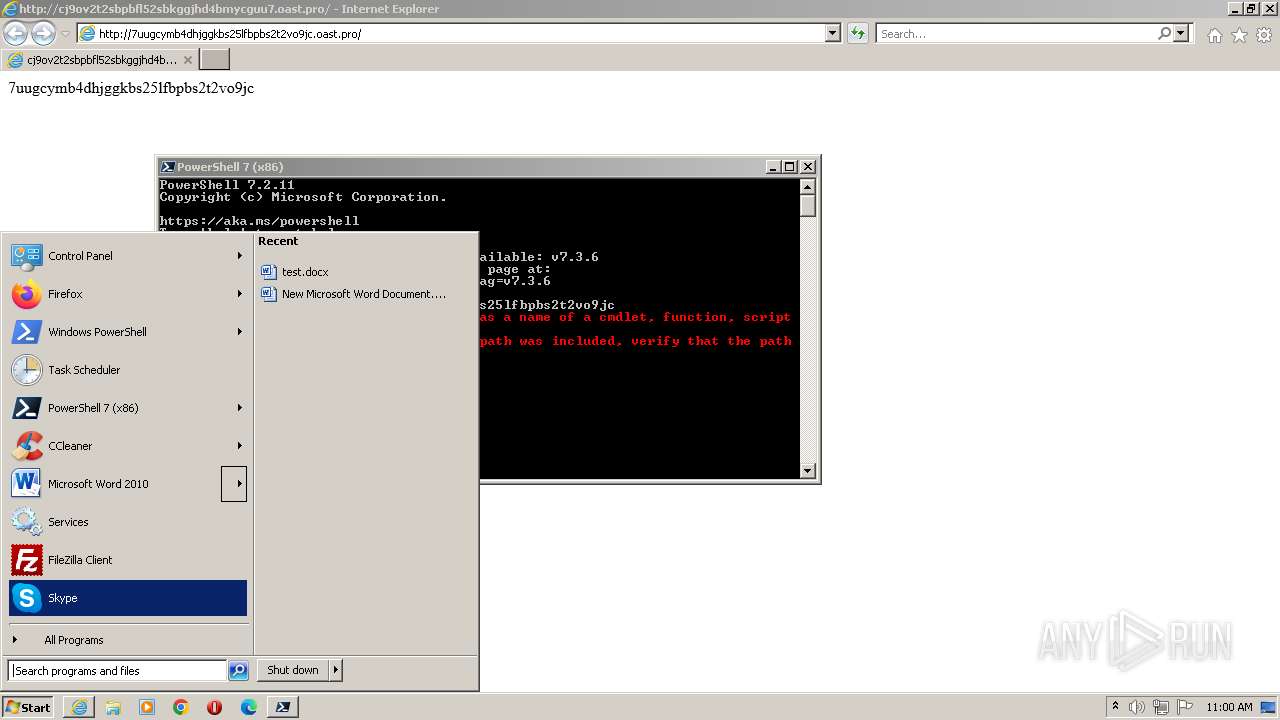
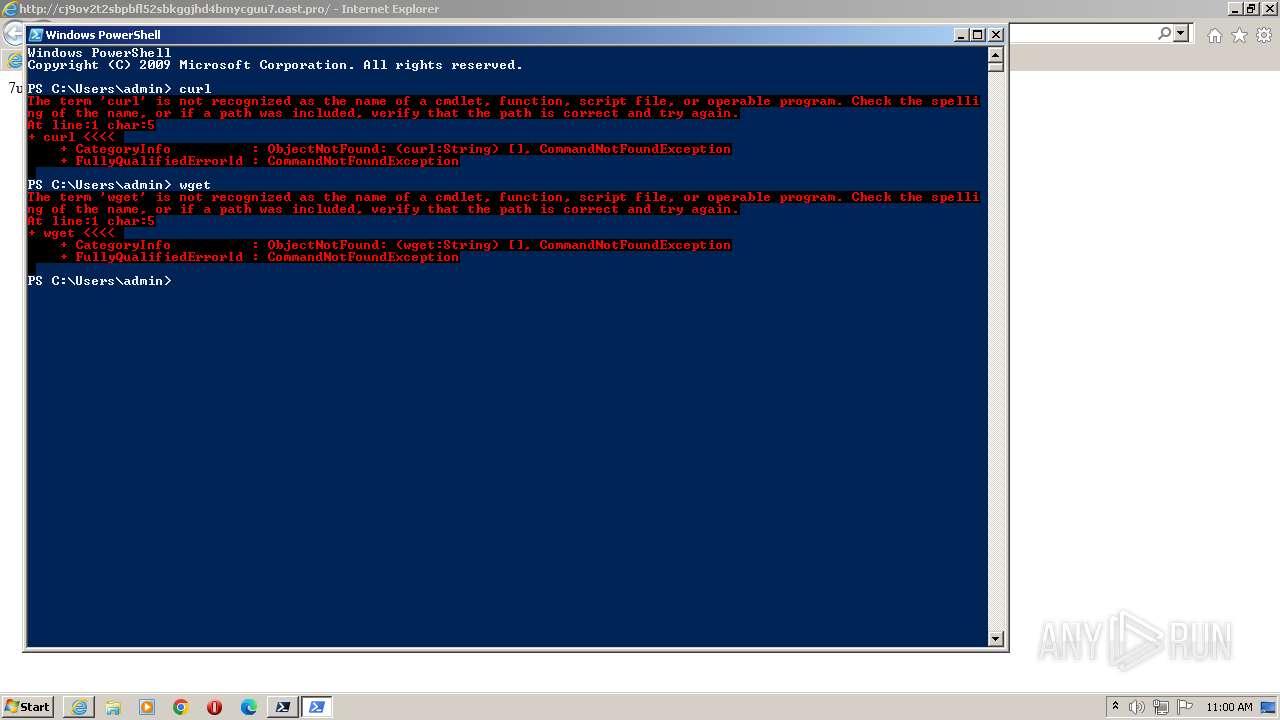
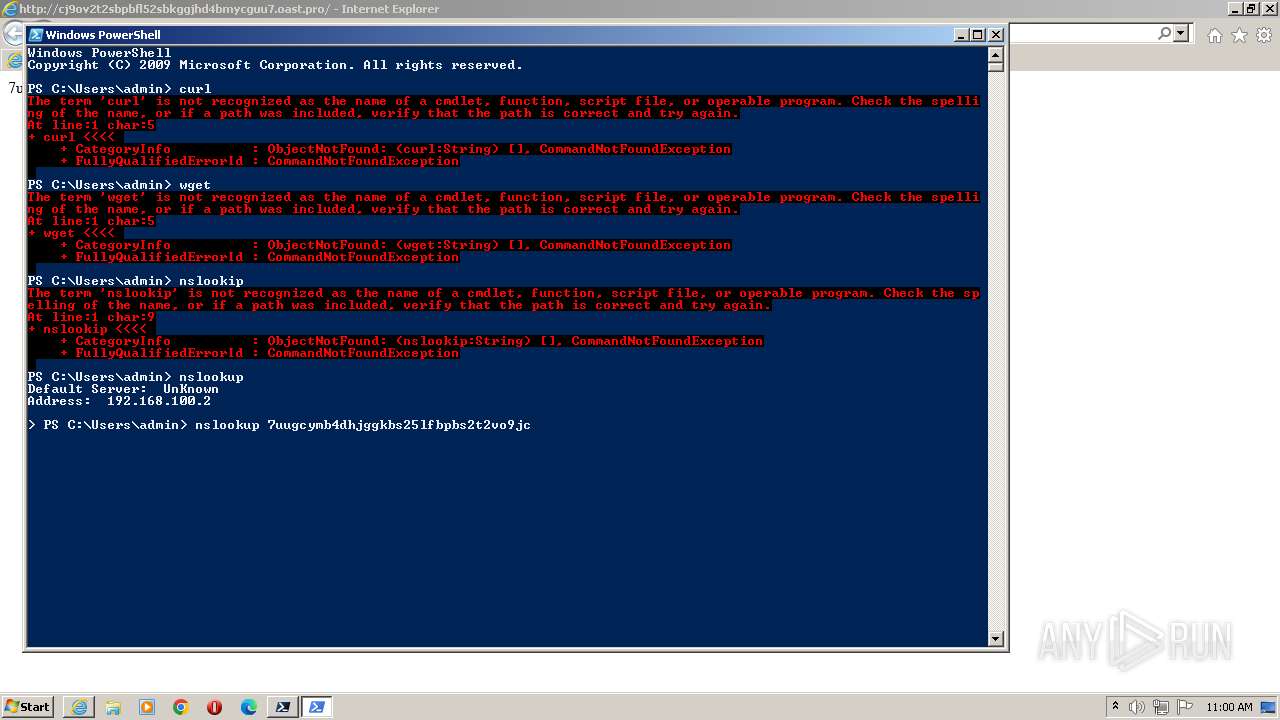
| URL: | http://cj9ov2t2sbpbfl52sbkggjhd4bmycguu7.oast.pro |
| Full analysis: | https://app.any.run/tasks/e3a39f55-2f78-4ae5-a5a8-7278d8676e36 |
| Verdict: | Malicious activity |
| Analysis date: | August 24, 2023, 09:59:32 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | C62C867F7BFB3C75748EB54163269DF3 |
| SHA1: | 24F1F21D3198C913C68F4746D890F867A5C43582 |
| SHA256: | 9C9065B892EB8D3BD9C2CA6F08CFFE8ADEEBF8A2D223808F57589133D78E971B |
| SSDEEP: | 3:N1KdPcKTXRXAt6QOCMHmKEWXKn:CvXAt6bTHmK/XK |
MALICIOUS
The DLL Hijacking
- pwsh.exe (PID: 4068)
SUSPICIOUS
Powershell version downgrade attack
- powershell.exe (PID: 616)
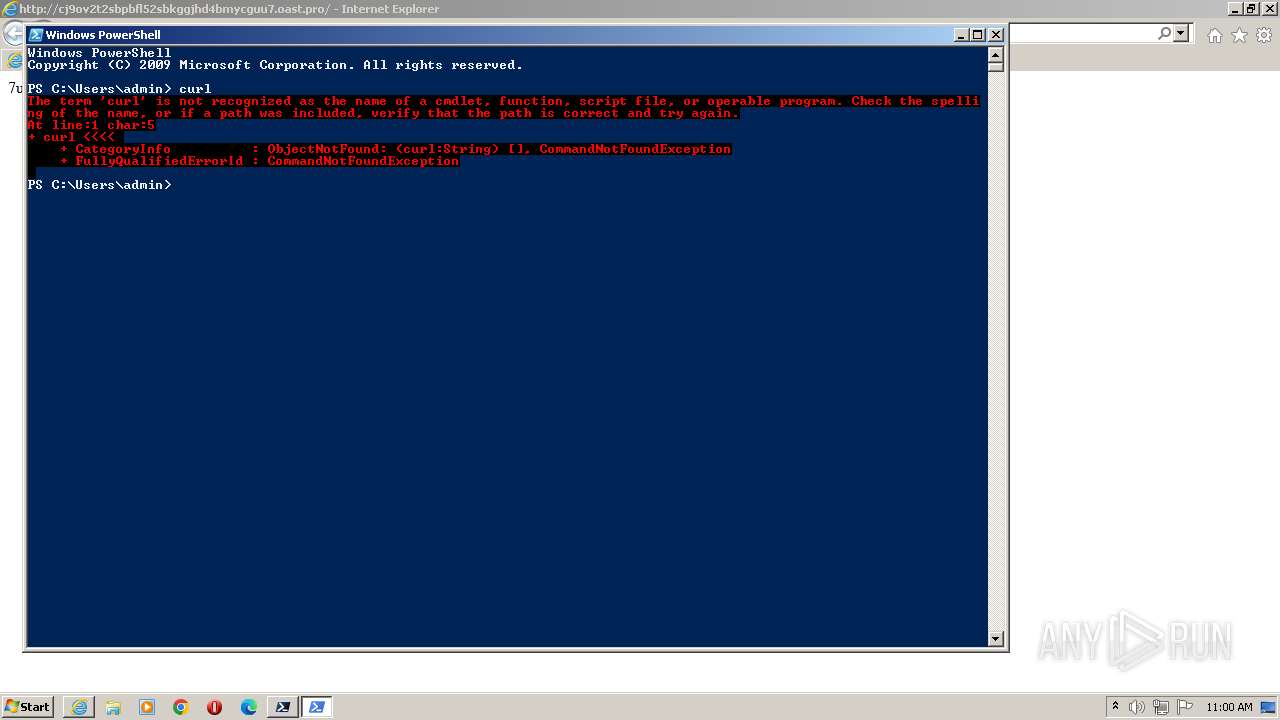
Uses NSLOOKUP.EXE to check DNS info
- powershell.exe (PID: 616)
INFO
Manual execution by a user
- pwsh.exe (PID: 4068)
- powershell.exe (PID: 616)
Checks supported languages
- pwsh.exe (PID: 4068)
Reads the machine GUID from the registry
- pwsh.exe (PID: 4068)
Create files in a temporary directory
- pwsh.exe (PID: 4068)
Reads security settings of Internet Explorer
- pwsh.exe (PID: 4068)
Application launched itself
- iexplore.exe (PID: 124)
Reads Environment values
- pwsh.exe (PID: 4068)
Reads product name
- pwsh.exe (PID: 4068)
Reads the computer name
- pwsh.exe (PID: 4068)
Creates files or folders in the user directory
- pwsh.exe (PID: 4068)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
42
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 124 | "C:\Program Files\Internet Explorer\iexplore.exe" "http://cj9ov2t2sbpbfl52sbkggjhd4bmycguu7.oast.pro" | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
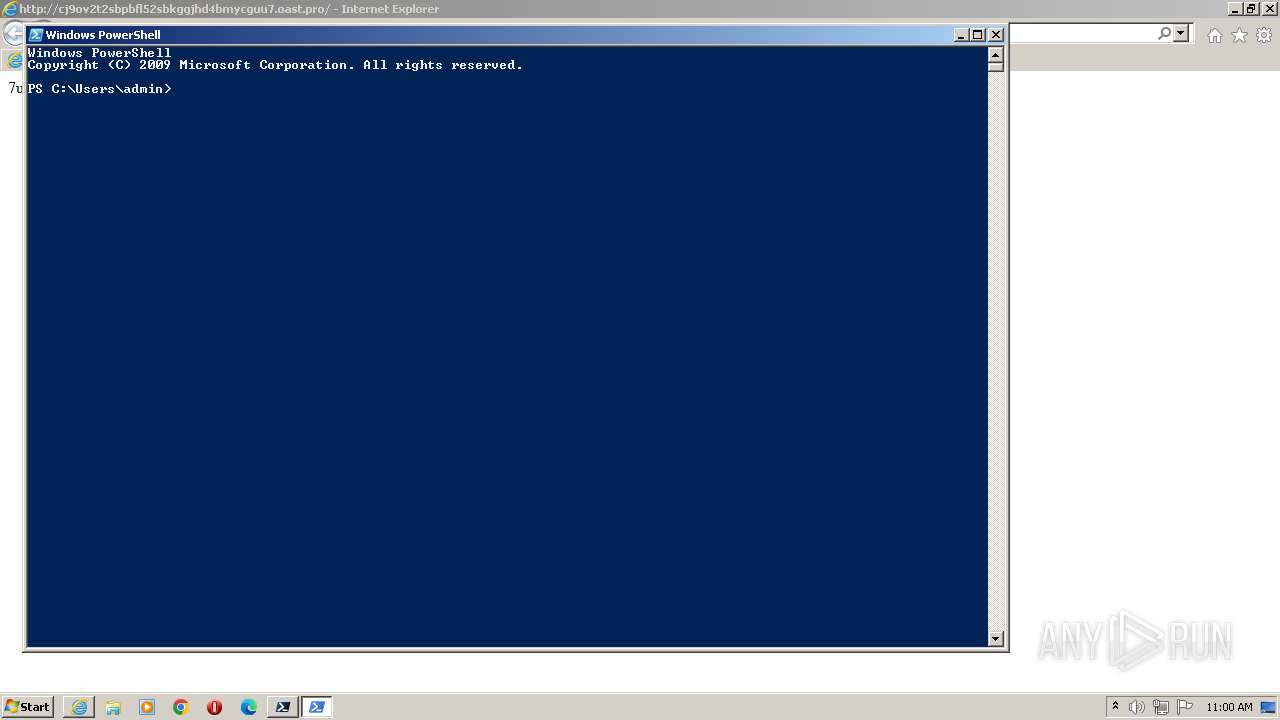
| 616 | "C:\WINDOWS\system32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 620 | "C:\Windows\system32\nslookup.exe" | C:\Windows\System32\nslookup.exe | powershell.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: nslookup Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2372 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:124 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 4068 | "C:\Program Files\PowerShell\7\pwsh.exe" -WorkingDirectory ~ | C:\Program Files\PowerShell\7\pwsh.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: pwsh Exit code: 0 Version: 7.2.11.500 Modules
| |||||||||||||||
Total events
13 550
Read events
13 355
Write events
195
Delete events
0
Modification events
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (124) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
0
Suspicious files
19
Text files
24
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | binary | |
MD5:CDE0B750D16BCF65956DFE1A042F7628 | SHA256:A6EB37B5288ED682CB3E4ABA6B8AF520F668104AE81B17E0C7B941B2A87A36B1 | |||
| 124 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\favicon[1].htm | html | |
MD5:9BB47F504C34063DBE6486AD643BB734 | SHA256:0DE426C0DC14D3CDF83C6EF871B7192DDA6E2927A960A6632F74DD8520014A5D | |||
| 2372 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\JETQTPG6.htm | html | |
MD5:9BB47F504C34063DBE6486AD643BB734 | SHA256:0DE426C0DC14D3CDF83C6EF871B7192DDA6E2927A960A6632F74DD8520014A5D | |||
| 4068 | pwsh.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4faf3hae.vqo.ps1 | text | |
MD5:49E937918A6394F1069D452F2B13D875 | SHA256:030003C8F60F8C3F080BCC20A1DC01862C9CA705ACCB4C59E64E0E08C15B8AF2 | |||
| 124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | der | |
MD5:B2C81DC385D8027DFE5316AF20681390 | SHA256:B487445E858A87D2A91424E02A843CE6A56E859760674C5C7666418130C63406 | |||
| 4068 | pwsh.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_bbyasj1v.3gy.psm1 | text | |
MD5:49E937918A6394F1069D452F2B13D875 | SHA256:030003C8F60F8C3F080BCC20A1DC01862C9CA705ACCB4C59E64E0E08C15B8AF2 | |||
| 4068 | pwsh.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\2SQM6E411ZY2WW9WVFCH.temp | binary | |
MD5:A20A86C096ADCB3F2B94729E95AC8359 | SHA256:9B6C50119EFA806C4BD1CD2C2B0A8524F261AA19EC2B882AD52677A2A0ADC273 | |||
| 124 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\favicon[1].htm | html | |
MD5:9BB47F504C34063DBE6486AD643BB734 | SHA256:0DE426C0DC14D3CDF83C6EF871B7192DDA6E2927A960A6632F74DD8520014A5D | |||
| 124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:BAABDB575E966F032AD96A5FF613B17C | SHA256:5B5F39C9BDE42895F091DAAD2D65F035F5401692CA1DF7F3B9F6D580D76EFF9B | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
23
DNS requests
18
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2372 | iexplore.exe | GET | — | 178.128.212.209:80 | http://7uugcymb4dhjggkbs25lfbpbs2t2vo9jc.oast.pro/ | GR | — | — | unknown |
124 | iexplore.exe | GET | 200 | 178.128.212.209:80 | http://cj9ov2t2sbpbfl52sbkggjhd4bmycguu7.oast.pro/favicon.ico | GR | html | 72 b | unknown |
124 | iexplore.exe | GET | 200 | 178.128.212.209:80 | http://cj9ov2t2sbpbfl52sbkggjhd4bmycguu7.oast.pro/favicon.ico | GR | html | 72 b | unknown |
2372 | iexplore.exe | GET | 200 | 178.128.212.209:80 | http://cj9ov2t2sbpbfl52sbkggjhd4bmycguu7.oast.pro/ | GR | html | 72 b | unknown |
2372 | iexplore.exe | GET | 200 | 178.128.212.209:80 | http://cj9ov2t2sbpbfl52sbkggjhd4bmycguu7.oast.pro/ | GR | html | 72 b | unknown |
124 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
124 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
124 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?01b8db33a7e68146 | US | compressed | 4.70 Kb | whitelisted |
124 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0793fa8ddfdb5d3d | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3284 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2372 | iexplore.exe | 178.128.212.209:80 | cj9ov2t2sbpbfl52sbkggjhd4bmycguu7.oast.pro | DIGITALOCEAN-ASN | SG | unknown |
124 | iexplore.exe | 178.128.212.209:80 | cj9ov2t2sbpbfl52sbkggjhd4bmycguu7.oast.pro | DIGITALOCEAN-ASN | SG | unknown |
2372 | iexplore.exe | 13.107.5.80:443 | api.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
124 | iexplore.exe | 2.23.209.179:443 | www.bing.com | Akamai International B.V. | GB | suspicious |
124 | iexplore.exe | 2.23.209.185:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
124 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
124 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
124 | iexplore.exe | 152.199.19.161:443 | r20swj13mr.microsoft.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
cj9ov2t2sbpbfl52sbkggjhd4bmycguu7.oast.pro |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
7uugcymb4dhjggkbs25lfbpbs2t2vo9jc.oast.pro |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
aka.ms |
| whitelisted |
pscoretestdata.blob.core.windows.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1088 | svchost.exe | Potentially Bad Traffic | ET INFO Out-of-Band Interaction Domain in DNS Lookup (oast .pro) |
1088 | svchost.exe | Potentially Bad Traffic | ET INFO Out-of-Band Interaction Domain in DNS Lookup (oast .pro) |
1088 | svchost.exe | Potentially Bad Traffic | ET INFO Out-of-Band Interaction Domain in DNS Lookup (oast .pro) |
Process | Message |
|---|---|
pwsh.exe | Profiler was prevented from loading notification profiler due to app settings.
Process ID (decimal): 4068. Message ID: [0x2509].
|