| File name: | GetPDFQuick_49223263.msi |
| Full analysis: | https://app.any.run/tasks/45509269-71bd-4bcf-90dc-5fafac8525e3 |
| Verdict: | Malicious activity |
| Analysis date: | May 21, 2024, 14:34:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, MSI Installer, Code page: 1252, Title: Installation Database, Subject: PDFFlex, Author: PDFFlex.io, Keywords: Installer, MSI, Database, Comments: A base dados do instalador contm a lgica e os dados necessrios para instalar o PDFFlex., Create Time/Date: Fri May 3 06:40:18 2024, Name of Creating Application: PDFFlex, Security: 0, Template: ;1033, Last Saved By: ;1046, Revision Number: {B47F4499-DF9E-4B07-91DD-DD89A1A9640C}3.202.1208.0;{B47F4499-DF9E-4B07-91DD-DD89A1A9640C}3.202.1208.0;{50C54027-847F-4B86-849A-9C02C888EE0B}, Number of Pages: 450, Number of Characters: 63 |
| MD5: | 4012EFD9C8B10B519E58BF29930A55FA |
| SHA1: | 7B4DAE32939D09CF18298D68F3317501D09BCF90 |
| SHA256: | 9C5D756045FD479A742B81241CCF439D02FC668581A3002913811A341278DE43 |
| SSDEEP: | 98304:S9IYolSpkBN/2Wex0xaAW9I+9DE+mzSE5lIP4GASazPtiG6CPUF0csMof+iZZjDR:gNG7z |
MALICIOUS
Changes powershell execution policy (Bypass)
- msiexec.exe (PID: 1036)
- msiexec.exe (PID: 2600)
Bypass execution policy to execute commands
- powershell.exe (PID: 1876)
- powershell.exe (PID: 552)
- powershell.exe (PID: 444)
- powershell.exe (PID: 2536)
Drops the executable file immediately after the start
- msiexec.exe (PID: 2072)
- msiexec.exe (PID: 2600)
Changes the autorun value in the registry
- msiexec.exe (PID: 2072)
SUSPICIOUS
Reads the Internet Settings
- msiexec.exe (PID: 3972)
- powershell.exe (PID: 444)
- msiexec.exe (PID: 2600)
- MSI742D.tmp (PID: 1032)
- powershell.exe (PID: 2536)
- msiexec.exe (PID: 1036)
- WMIC.exe (PID: 1756)
The process bypasses the loading of PowerShell profile settings
- msiexec.exe (PID: 1036)
- msiexec.exe (PID: 2600)
The process hide an interactive prompt from the user
- msiexec.exe (PID: 1036)
- msiexec.exe (PID: 2600)
The process executes Powershell scripts
- msiexec.exe (PID: 1036)
- msiexec.exe (PID: 2600)
Checks Windows Trust Settings
- msiexec.exe (PID: 2072)
- msiexec.exe (PID: 2600)
Reads the Windows owner or organization settings
- msiexec.exe (PID: 2072)
Reverses array data (POWERSHELL)
- powershell.exe (PID: 552)
Starts POWERSHELL.EXE for commands execution
- msiexec.exe (PID: 1036)
- msiexec.exe (PID: 2600)
Executes as Windows Service
- VSSVC.exe (PID: 2064)
Process drops legitimate windows executable
- msiexec.exe (PID: 2072)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 2600)
- msiexec.exe (PID: 1036)
- MSI742D.tmp (PID: 1032)
Unusual connection from system programs
- powershell.exe (PID: 444)
- powershell.exe (PID: 2536)
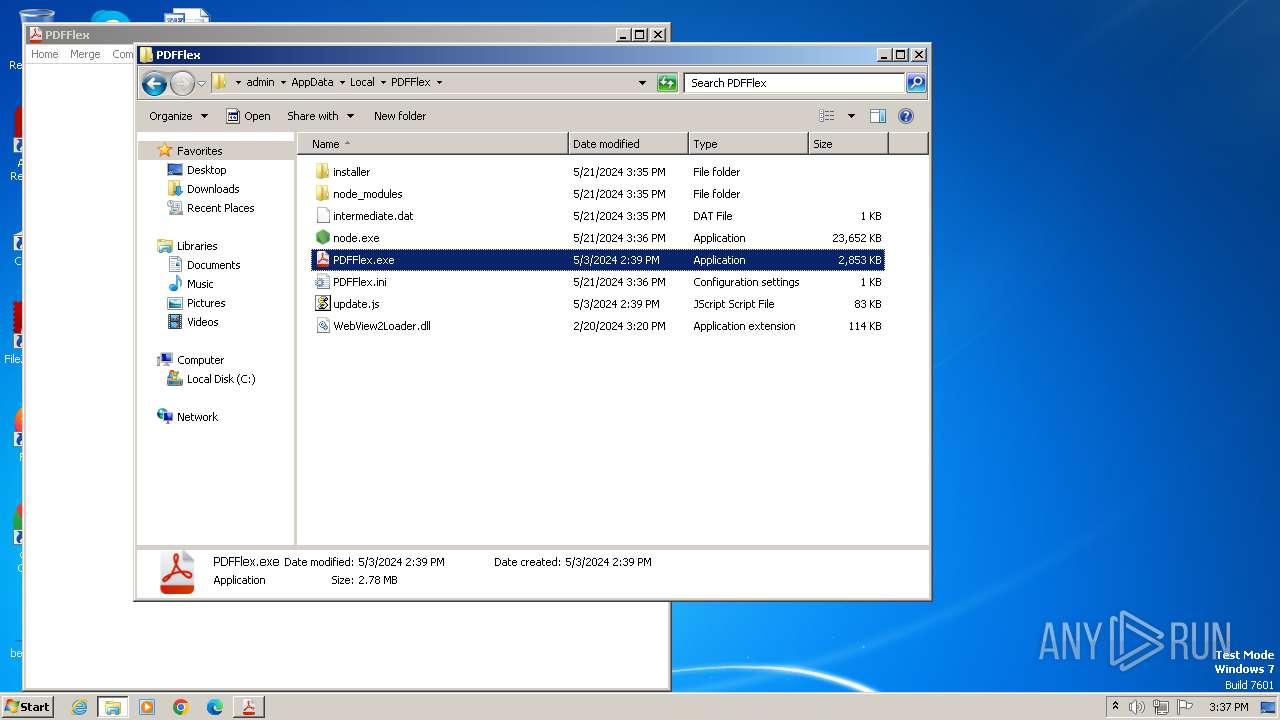
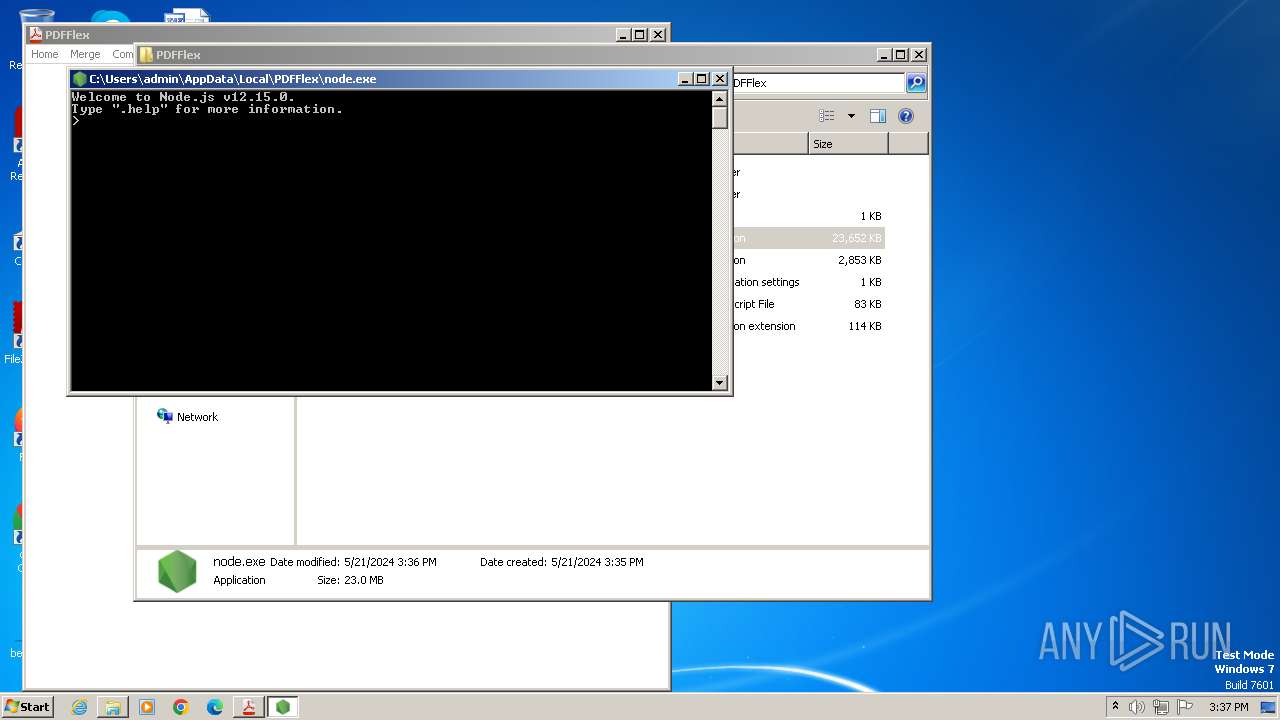
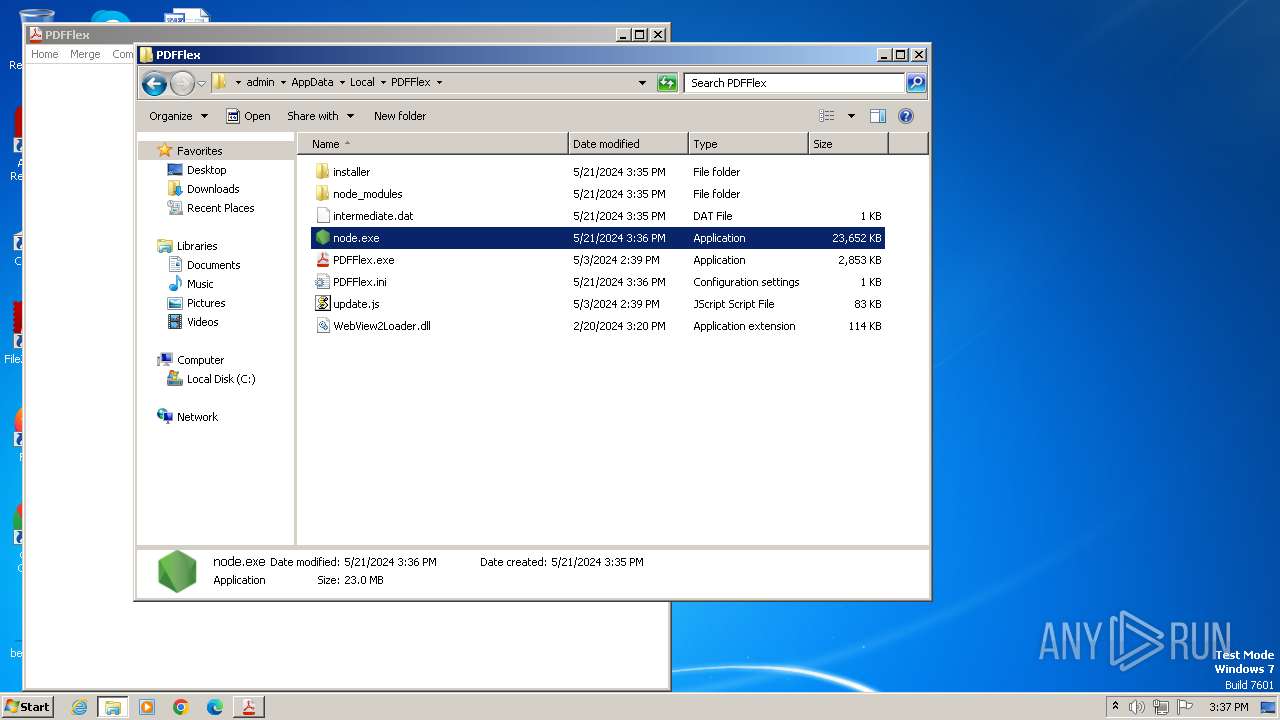
Node.exe was dropped
- msiexec.exe (PID: 2600)
Starts CMD.EXE for commands execution
- msiexec.exe (PID: 1036)
- node.exe (PID: 2024)
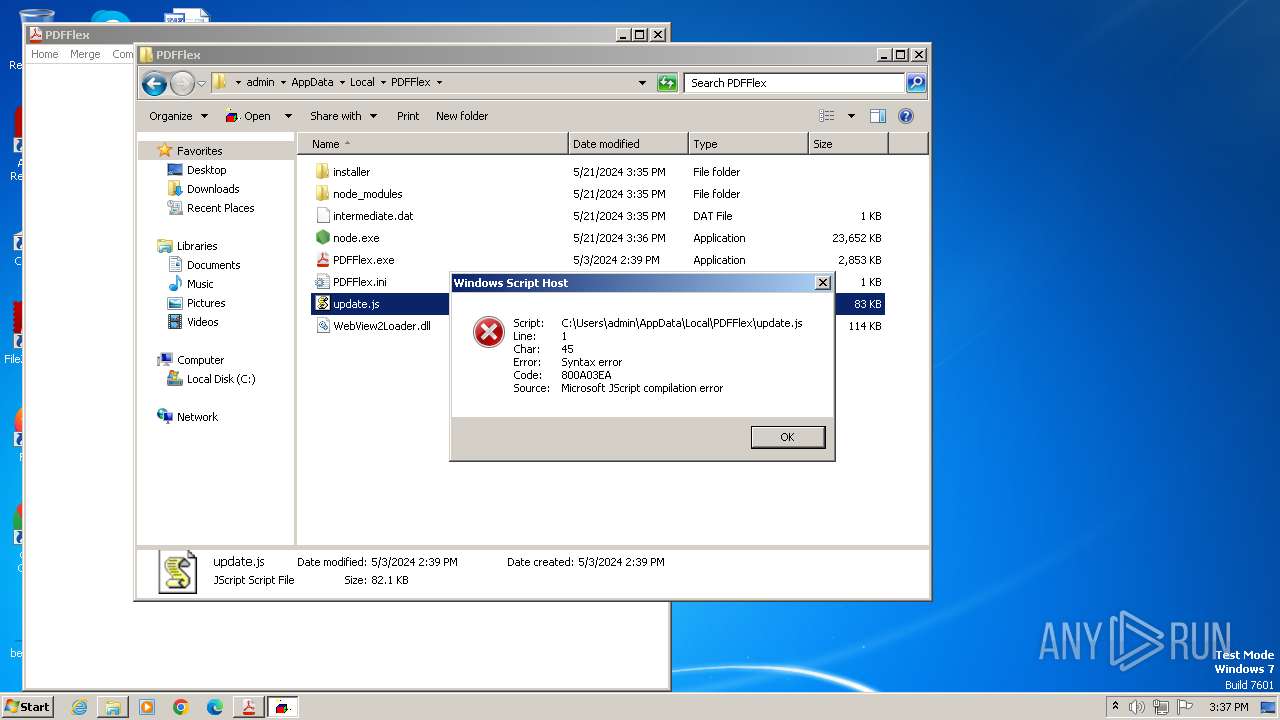
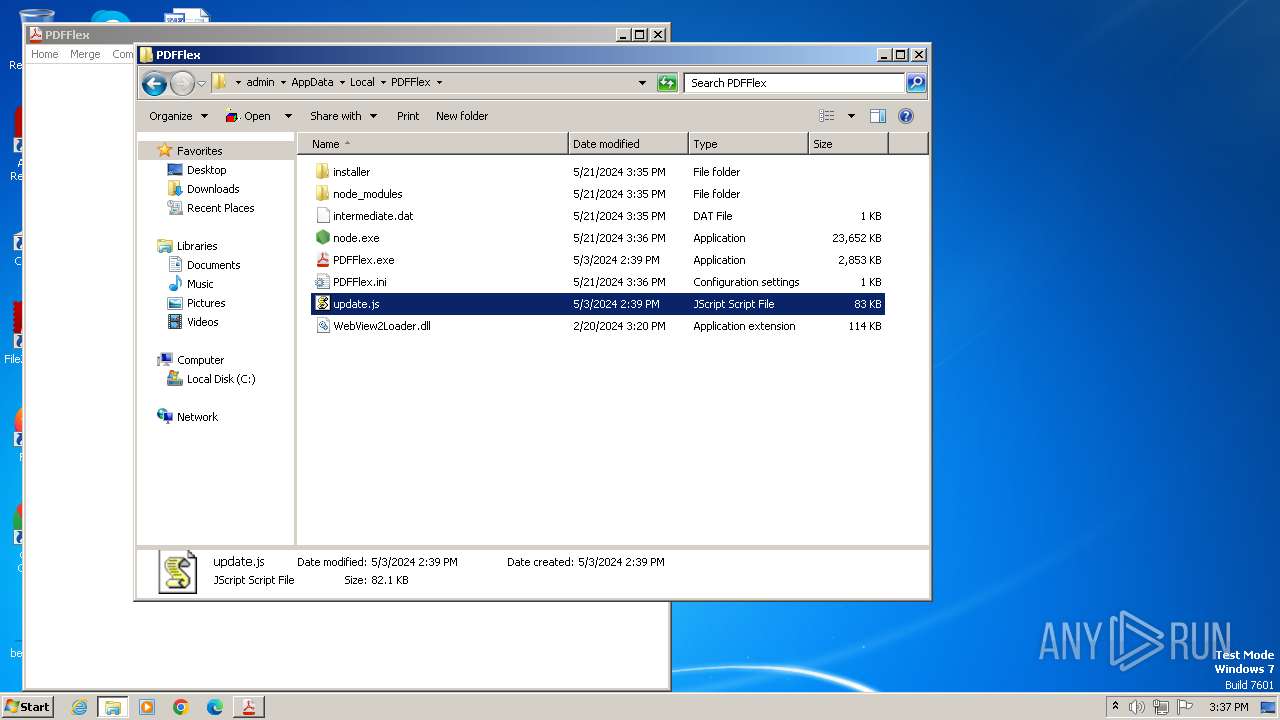
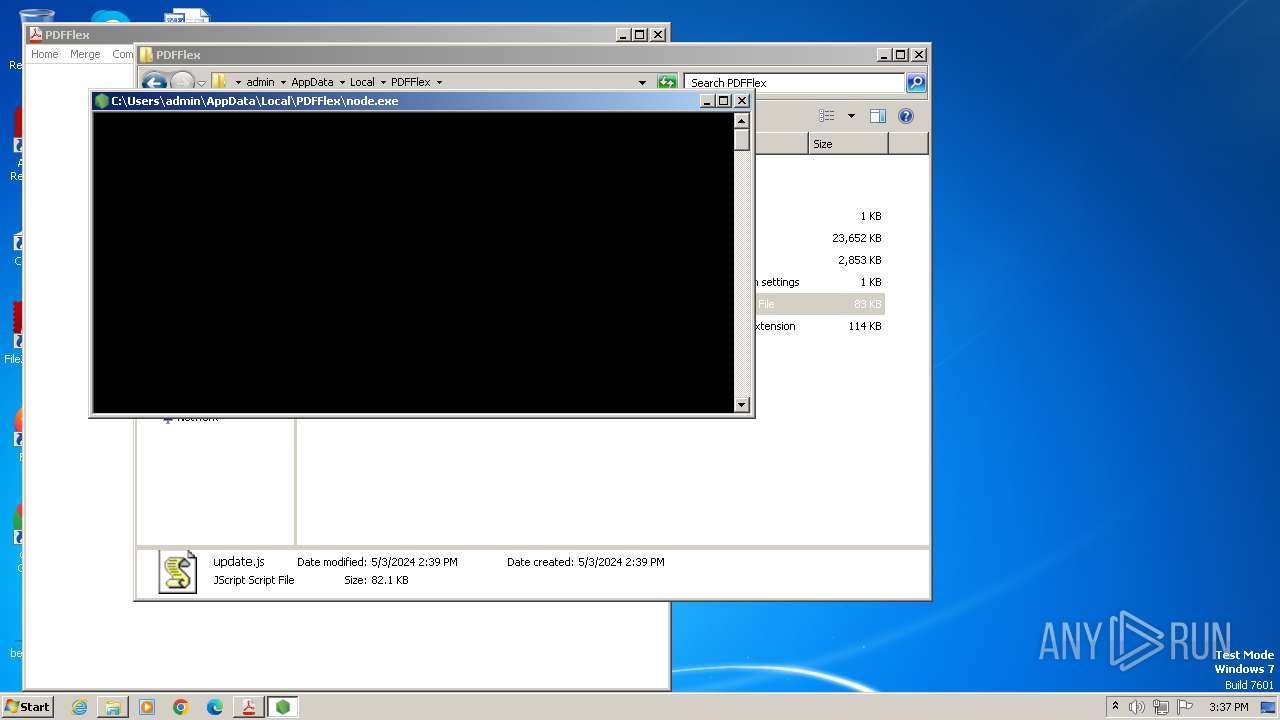
Executes script using NodeJS
- node.exe (PID: 2024)
Uses WMIC.EXE to obtain user accounts information
- cmd.exe (PID: 2316)
INFO
Reads the software policy settings
- msiexec.exe (PID: 3972)
- msiexec.exe (PID: 2072)
- msiexec.exe (PID: 2600)
Creates files or folders in the user directory
- msiexec.exe (PID: 3972)
- msiexec.exe (PID: 2072)
- msiexec.exe (PID: 2600)
- PDFFlex.exe (PID: 2872)
An automatically generated document
- msiexec.exe (PID: 3972)
Checks supported languages
- msiexec.exe (PID: 2072)
- msiexec.exe (PID: 1036)
- msiexec.exe (PID: 2600)
- wmpnscfg.exe (PID: 2484)
- MSI744E.tmp (PID: 1644)
- node.exe (PID: 3544)
- node.exe (PID: 2024)
- PDFFlex.exe (PID: 2872)
- MSI742D.tmp (PID: 1032)
Reads the machine GUID from the registry
- msiexec.exe (PID: 2072)
- msiexec.exe (PID: 2600)
- msiexec.exe (PID: 1036)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 3972)
- powershell.exe (PID: 1876)
- powershell.exe (PID: 552)
- powershell.exe (PID: 444)
- powershell.exe (PID: 2536)
Reads the computer name
- msiexec.exe (PID: 2072)
- msiexec.exe (PID: 1036)
- msiexec.exe (PID: 2600)
- wmpnscfg.exe (PID: 2484)
- MSI742D.tmp (PID: 1032)
- node.exe (PID: 2024)
- MSI744E.tmp (PID: 1644)
Create files in a temporary directory
- msiexec.exe (PID: 3972)
- msiexec.exe (PID: 1036)
- powershell.exe (PID: 552)
- powershell.exe (PID: 1876)
- msiexec.exe (PID: 2600)
- powershell.exe (PID: 444)
- msiexec.exe (PID: 2072)
- powershell.exe (PID: 2536)
Drops the executable file immediately after the start
- msiexec.exe (PID: 3972)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 552)
- powershell.exe (PID: 1876)
- powershell.exe (PID: 444)
- powershell.exe (PID: 2536)
Executable content was dropped or overwritten
- msiexec.exe (PID: 2072)
- msiexec.exe (PID: 3972)
- msiexec.exe (PID: 2600)
Application launched itself
- msiexec.exe (PID: 2072)
Reads Environment values
- msiexec.exe (PID: 2600)
- msiexec.exe (PID: 1036)
- node.exe (PID: 3544)
Disables trace logs
- powershell.exe (PID: 444)
- powershell.exe (PID: 2536)
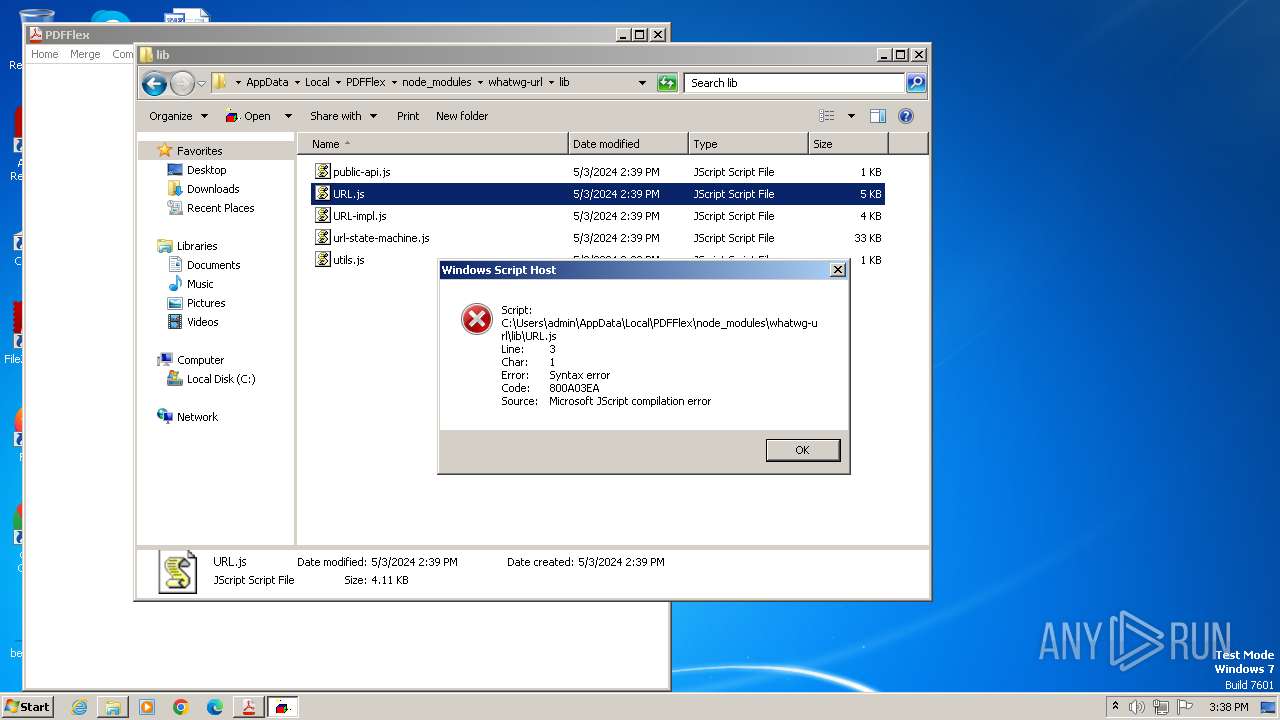
Manual execution by a user
- wmpnscfg.exe (PID: 2484)
- node.exe (PID: 3544)
- wscript.exe (PID: 3564)
- node.exe (PID: 2024)
- wscript.exe (PID: 2996)
- notepad.exe (PID: 864)
- notepad.exe (PID: 4024)
Checks proxy server information
- msiexec.exe (PID: 2600)
Creates a software uninstall entry
- msiexec.exe (PID: 2072)
Starts application with an unusual extension
- msiexec.exe (PID: 2072)
Reads product name
- node.exe (PID: 3544)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (81.9) |
|---|---|---|
| .mst | | | Windows SDK Setup Transform Script (9.2) |
| .msp | | | Windows Installer Patch (7.6) |
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| Security: | None |
|---|---|
| CodePage: | Windows Latin 1 (Western European) |
| RevisionNumber: | {5CC5243C-3A9A-4868-90C3-9CEA3AEEFCAF} |
| Words: | 10 |
| Subject: | PDFFlex |
| Author: | PDFFlex.io |
| LastModifiedBy: | - |
| Software: | PDFFlex |
| Template: | ;1033,1046,3082,1055 |
| Comments: | PDFFlex 3.202.1208.0 |
| Title: | Installation Database |
| Keywords: | Installer, MSI, Database |
| CreateDate: | 2024:05:03 06:40:36 |
| ModifyDate: | 2024:05:03 06:40:36 |
| LastPrinted: | 2024:05:03 06:40:36 |
| Pages: | 450 |
| Characters: | 63 |
Total processes
74
Monitored processes
22
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 444 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\pssBB08.ps1" -propFile "C:\Users\admin\AppData\Local\Temp\msiBAF5.txt" -scriptFile "C:\Users\admin\AppData\Local\Temp\scrBAF6.ps1" -scriptArgsFile "C:\Users\admin\AppData\Local\Temp\scrBAF7.txt" -propSep " :<->: " -lineSep " <<:>> " -testPrefix "_testValue." | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 552 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\pss7FC9.ps1" -propFile "C:\Users\admin\AppData\Local\Temp\msi7FA7.txt" -scriptFile "C:\Users\admin\AppData\Local\Temp\scr7FA8.ps1" -scriptArgsFile "C:\Users\admin\AppData\Local\Temp\scr7FA9.txt" -propSep " :<->: " -lineSep " <<:>> " -testPrefix "_testValue." | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 864 | "C:\Windows\System32\Notepad.exe" C:\Users\admin\AppData\Local\PDFFlex\node_modules\whatwg-url\lib\URL.js | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1032 | "C:\Windows\Installer\MSI742D.tmp" /DontWait /dir "C:\Users\admin\AppData\Local\PDFFlex\" "C:\Users\admin\AppData\Local\PDFFlex\PDFFlex.exe" | C:\Windows\Installer\MSI742D.tmp | — | msiexec.exe | |||||||||||
User: admin Company: Caphyon LTD Integrity Level: MEDIUM Description: File that launches another file Exit code: 0 Version: 21.5.1.0 Modules
| |||||||||||||||
| 1036 | C:\Windows\system32\MsiExec.exe -Embedding 0E812E20AD3476A854CF9F31D7DFC038 C | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1644 | "C:\Windows\Installer\MSI744E.tmp" /HideWindow /dir "C:\Users\admin\AppData\Local\PDFFlex\installer\" "C:\Users\admin\AppData\Local\PDFFlex\installer\OperaSetup.exe" --silent --allusers=0 | C:\Windows\Installer\MSI744E.tmp | — | msiexec.exe | |||||||||||
User: admin Company: Caphyon LTD Integrity Level: MEDIUM Description: File that launches another file Exit code: 4294967295 Version: 21.5.1.0 Modules
| |||||||||||||||
| 1756 | wmic useraccount where name="admin" get sid | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1876 | -NoProfile -Noninteractive -ExecutionPolicy Bypass -File "C:\Users\admin\AppData\Local\Temp\pss78CF.ps1" -propFile "C:\Users\admin\AppData\Local\Temp\msi78AC.txt" -scriptFile "C:\Users\admin\AppData\Local\Temp\scr78AD.ps1" -scriptArgsFile "C:\Users\admin\AppData\Local\Temp\scr78AE.txt" -propSep " :<->: " -lineSep " <<:>> " -testPrefix "_testValue." | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2024 | "C:\Users\admin\AppData\Local\PDFFlex\node.exe" C:\Users\admin\AppData\Local\PDFFlex\update.js | C:\Users\admin\AppData\Local\PDFFlex\node.exe | — | explorer.exe | |||||||||||
User: admin Company: Node.js Integrity Level: MEDIUM Description: Node.js: Server-side JavaScript Exit code: 0 Version: 12.15.0 Modules
| |||||||||||||||
| 2064 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
39 458
Read events
39 102
Write events
334
Delete events
22
Modification events
| (PID) Process: | (3972) msiexec.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2072) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 40000000000000005C3690148CABDA011808000004080000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2072) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 40000000000000005C3690148CABDA011808000004080000D0070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2072) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 75 | |||
| (PID) Process: | (2072) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 4000000000000000BA0643158CABDA011808000004080000D3070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2072) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000BA0643158CABDA01180800000C060000E8030000010000000000000000000000BF04B430AD5E9A40995B75FD11004AF10000000000000000 | |||
| (PID) Process: | (2064) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\COM+ REGDB Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000D65451158CABDA01100800006C040000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2064) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\ASR Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000D65451158CABDA011008000014080000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2064) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000D65451158CABDA0110080000E4080000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2064) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\services\VSS\Diag\Shadow Copy Optimization Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4000000000000000D65451158CABDA0110080000B8080000E8030000010000000100000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
25
Suspicious files
42
Text files
32
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1036 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\msi78AC.txt | — | |
MD5:— | SHA256:— | |||
| 1036 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\scr78AD.ps1 | — | |
MD5:— | SHA256:— | |||
| 1036 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\scr78AE.txt | — | |
MD5:— | SHA256:— | |||
| 1036 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\pss78CF.ps1 | — | |
MD5:— | SHA256:— | |||
| 1036 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\msi7FA7.txt | — | |
MD5:— | SHA256:— | |||
| 1036 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\scr7FA8.ps1 | — | |
MD5:— | SHA256:— | |||
| 1036 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\scr7FA9.txt | — | |
MD5:— | SHA256:— | |||
| 1036 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\pss7FC9.ps1 | — | |
MD5:— | SHA256:— | |||
| 3972 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI77F5.tmp | executable | |
MD5:D0C9613582605F3793FDAD7279DE428B | SHA256:8BD84F1156EBDFA44AFAAC8A4579BA56A8C7513E3D51E00822167EA144923726 | |||
| 2072 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
14
DNS requests
9
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3972 | msiexec.exe | GET | 200 | 104.18.21.226:80 | http://secure.globalsign.com/cacert/codesigningrootr45.crt | unknown | — | — | unknown |
444 | powershell.exe | POST | 200 | 18.66.107.68:80 | http://d1jorhhovk7rc8.cloudfront.net/ | unknown | — | — | unknown |
2600 | msiexec.exe | GET | 200 | 108.138.2.195:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | unknown | — | — | unknown |
1088 | svchost.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9fb5557a30a98ae7 | unknown | — | — | unknown |
2536 | powershell.exe | POST | 200 | 18.66.107.68:80 | http://d1jorhhovk7rc8.cloudfront.net/ | unknown | — | — | unknown |
2600 | msiexec.exe | GET | 304 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e997f9bb455b8e51 | unknown | — | — | unknown |
2600 | msiexec.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEjgLnWaIozse2b%2BczaaODg8%3D | unknown | — | — | unknown |
2600 | msiexec.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | unknown | — | — | unknown |
3972 | msiexec.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?d9bbfac475ce855a | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | unknown |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
3972 | msiexec.exe | 104.18.21.226:80 | secure.globalsign.com | CLOUDFLARENET | — | shared |
3972 | msiexec.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
444 | powershell.exe | 18.66.107.68:80 | d1jorhhovk7rc8.cloudfront.net | AMAZON-02 | US | unknown |
2600 | msiexec.exe | 18.66.92.169:443 | dn0diw4x4ljz4.cloudfront.net | — | US | unknown |
2600 | msiexec.exe | 93.184.221.240:80 | ctldl.windowsupdate.com | EDGECAST | GB | whitelisted |
2600 | msiexec.exe | 108.138.2.195:80 | o.ss2.us | AMAZON-02 | US | unknown |
2600 | msiexec.exe | 18.245.39.64:80 | ocsp.rootg2.amazontrust.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
secure.globalsign.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
d1jorhhovk7rc8.cloudfront.net |
| unknown |
dn0diw4x4ljz4.cloudfront.net |
| unknown |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
d1eypqyai0o69n.cloudfront.net |
| unknown |
d25xn4y1w1xf3s.cloudfront.net |
| unknown |
Threats
Process | Message |
|---|---|
PDFFlex.exe | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|