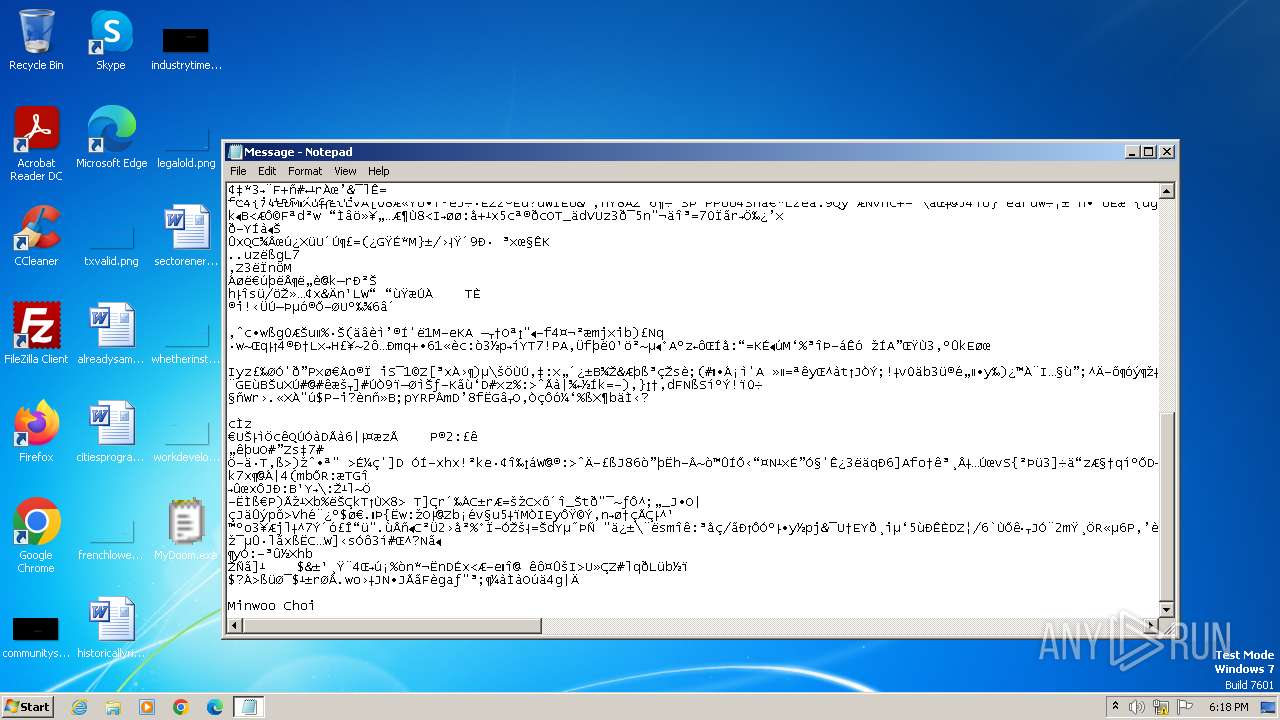
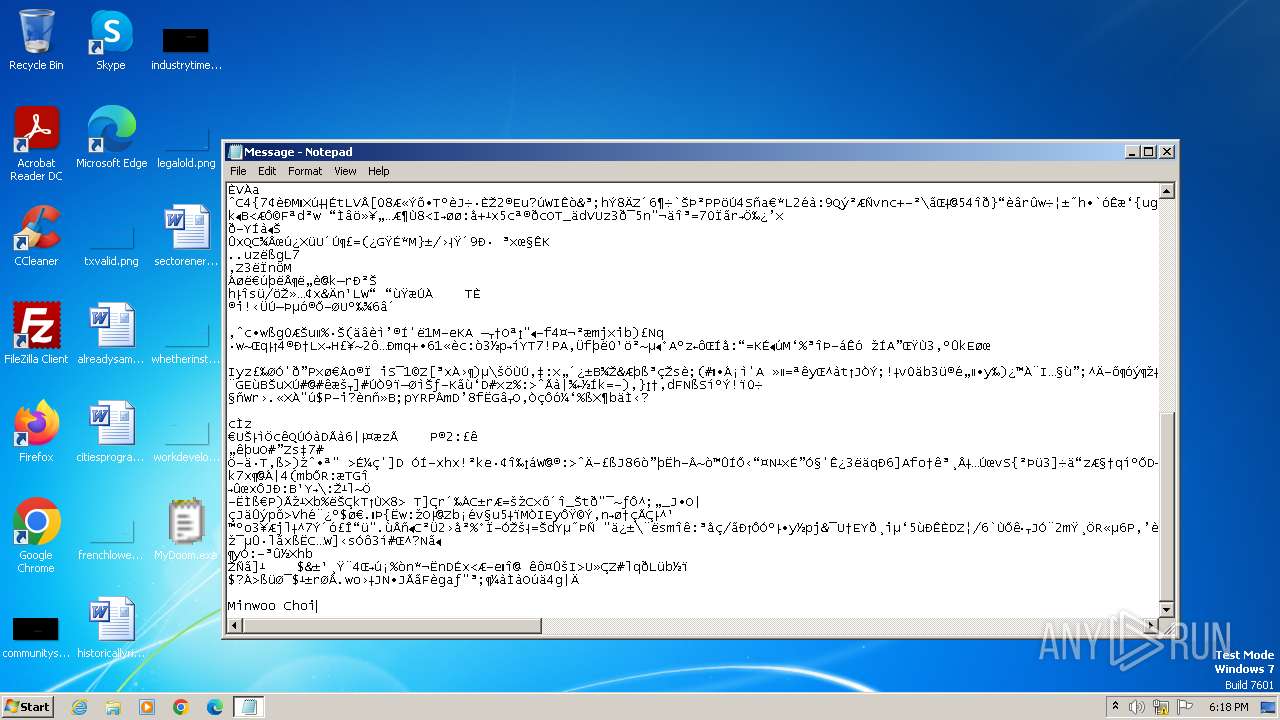
| File name: | MyDoom.exe |
| Full analysis: | https://app.any.run/tasks/703dd436-66d3-4055-84eb-04e29544bd8e |
| Verdict: | Malicious activity |
| Analysis date: | February 02, 2025, 18:17:54 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | D4F4D6CEF290E72331CF4F53DF1FD3BA |
| SHA1: | 4486371422BF3ACB6411963AAD6544752787B794 |
| SHA256: | 9C3AC72B7248A9DE2F996E08A53919AEA831322EA41EBBB63556AB719A714EDB |
| SSDEEP: | 3072:Aapie41LuJ1L/5S8tQG6ffk+2YCc9mhT3jeDpdYMwwxWlnTECtI8Y:JAe4EJx5FUffk+2YCc4hT3jatCt5Y |
MALICIOUS
Changes the autorun value in the registry
- MyDoom.exe (PID: 1792)
SUSPICIOUS
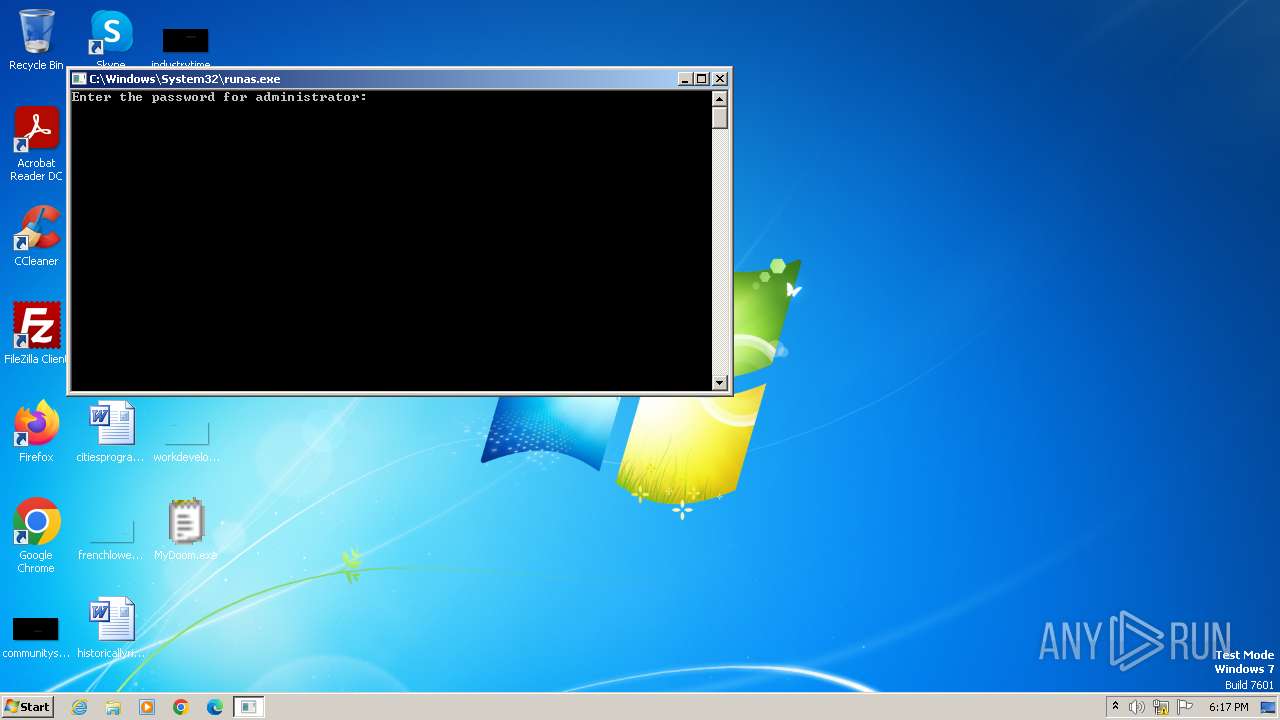
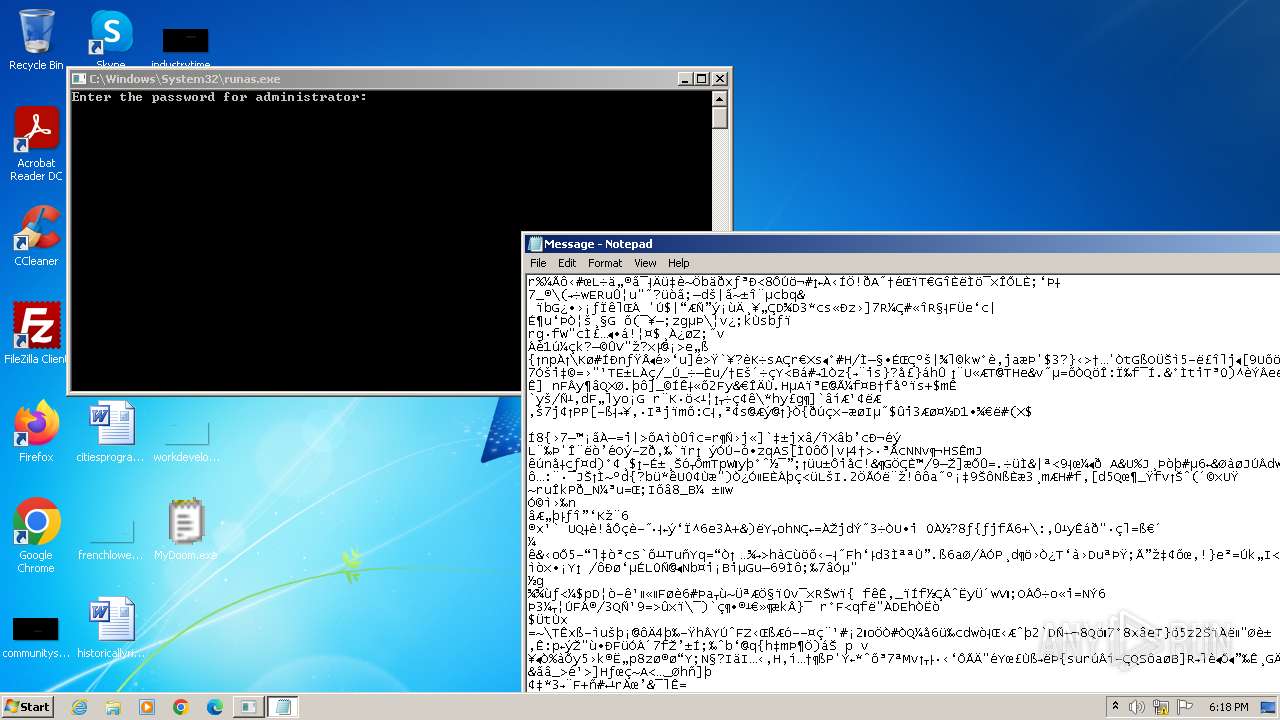
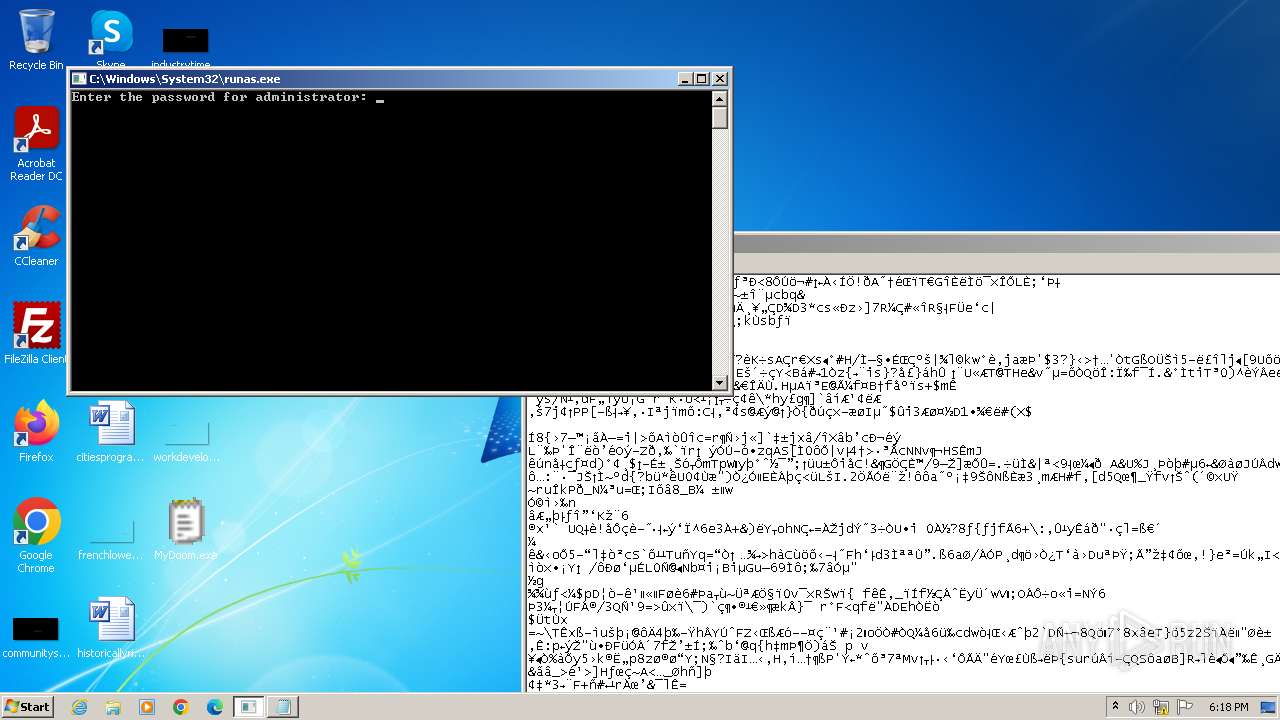
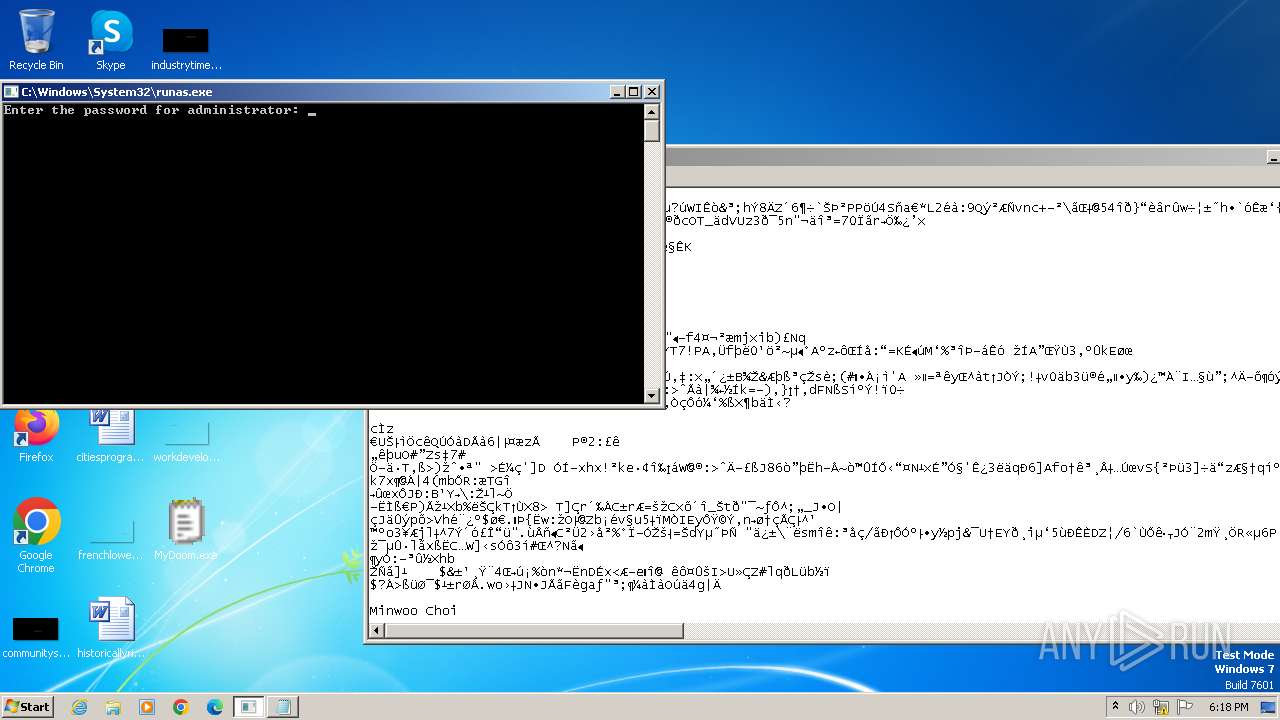
Starts another process probably with elevated privileges via RUNAS.EXE
- runas.exe (PID: 1560)
Reads the Internet Settings
- MyDoom.exe (PID: 1792)
Connects to SMTP port
- MyDoom.exe (PID: 1792)
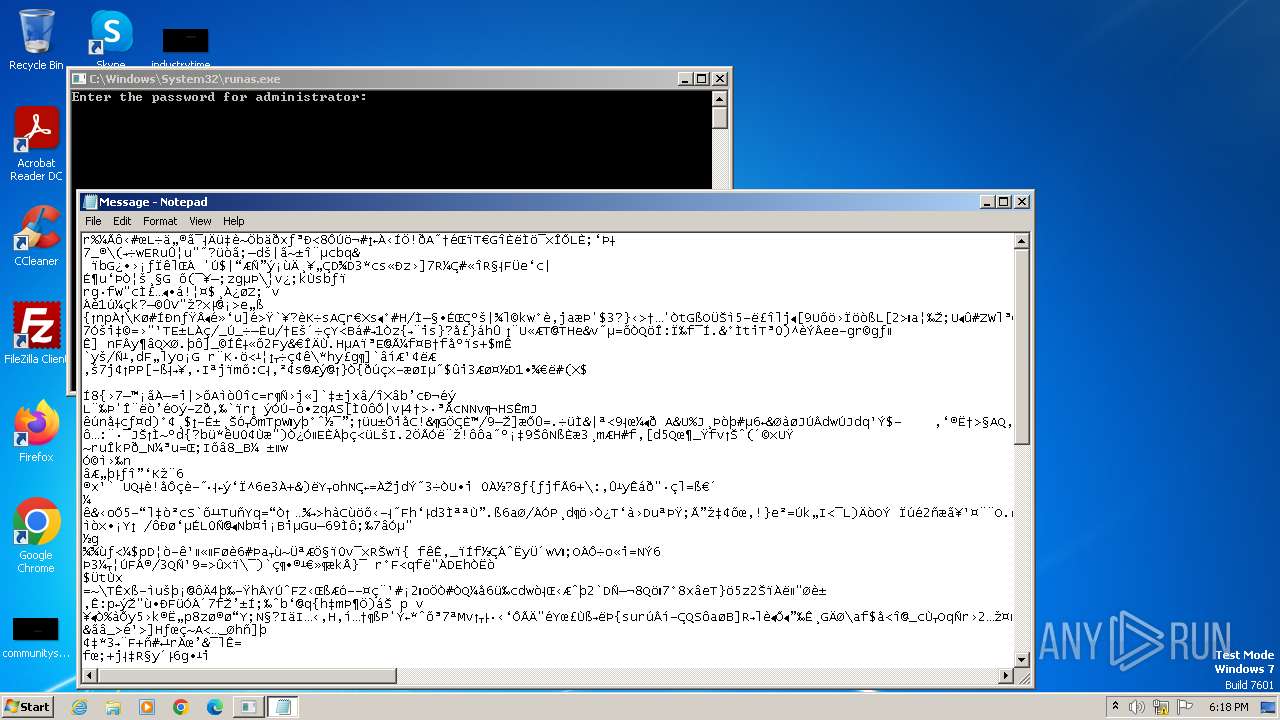
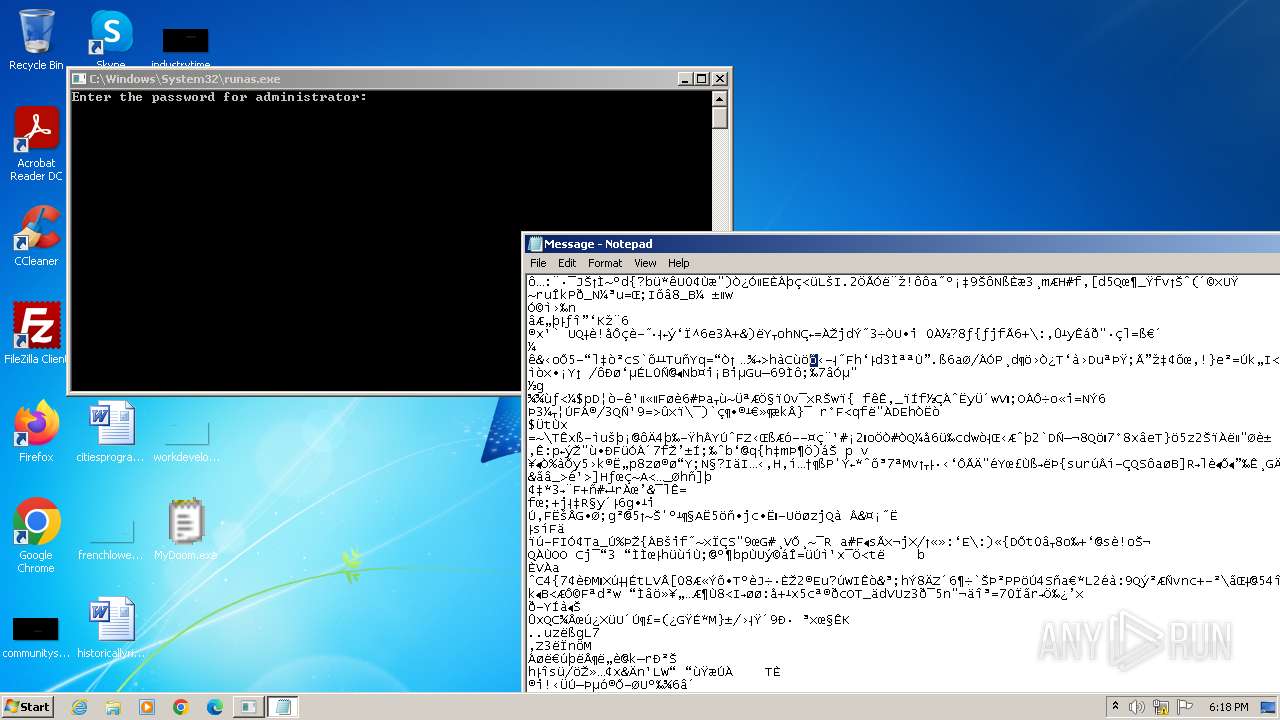
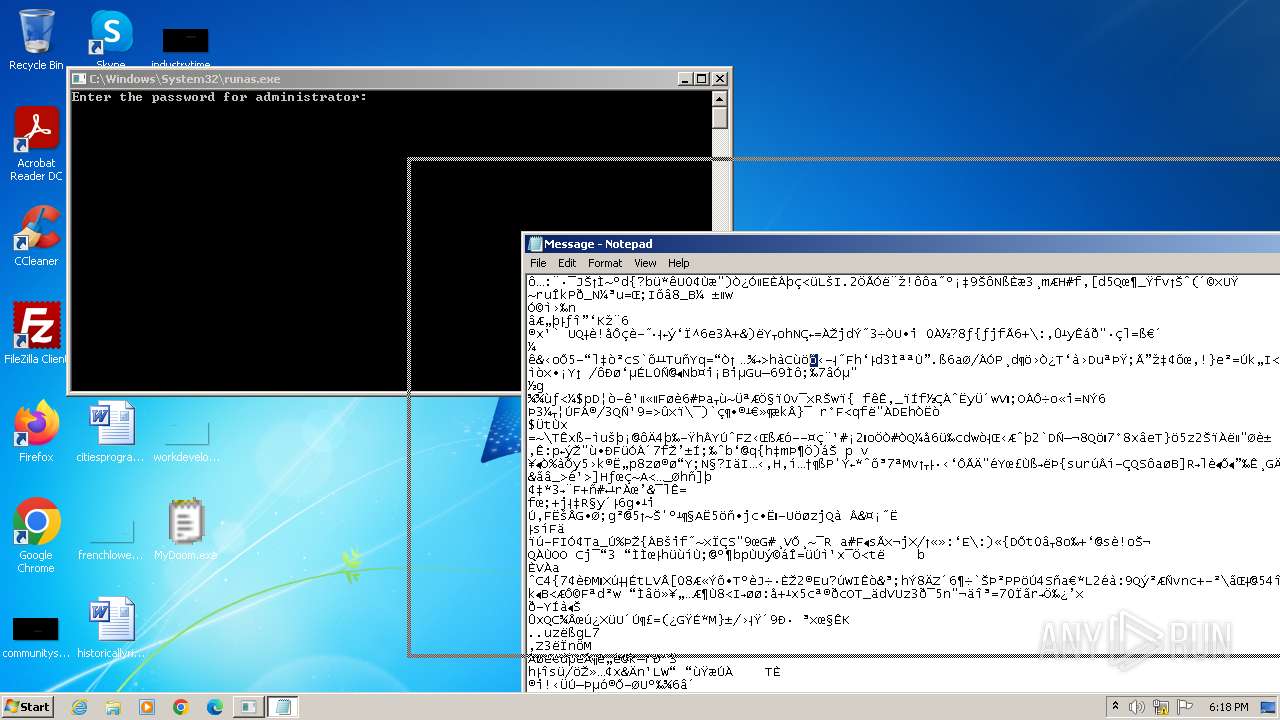
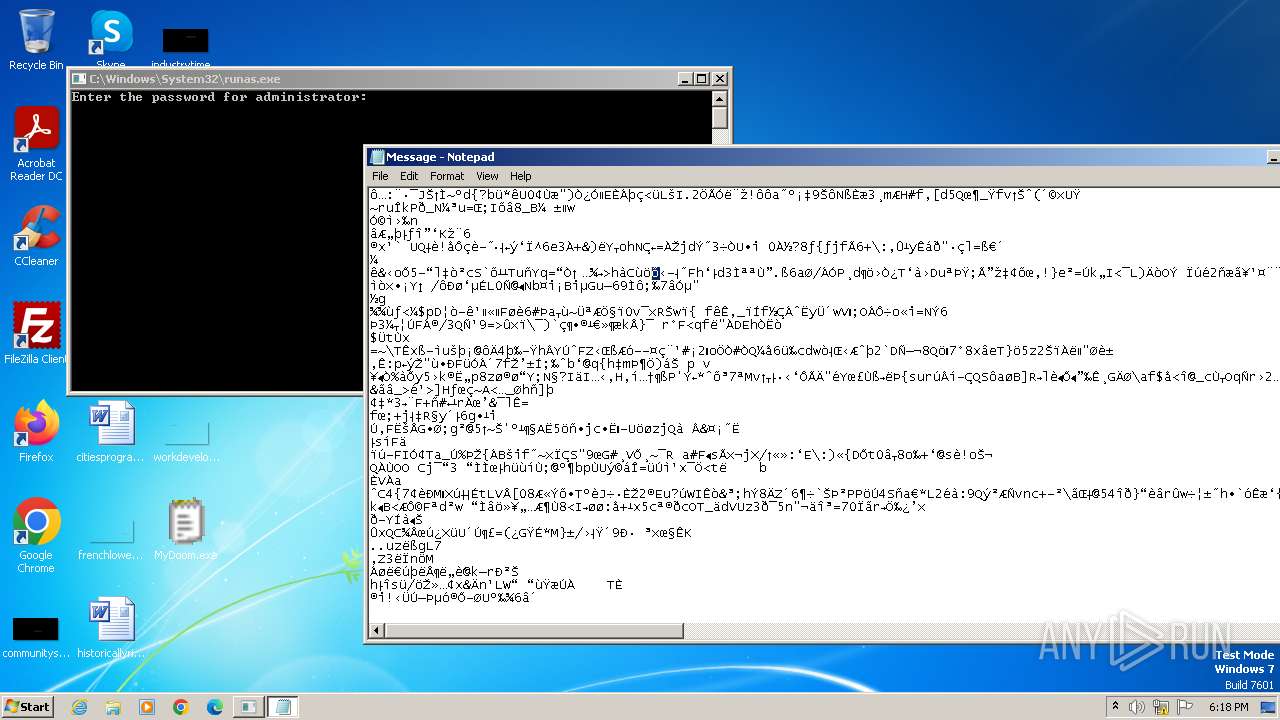
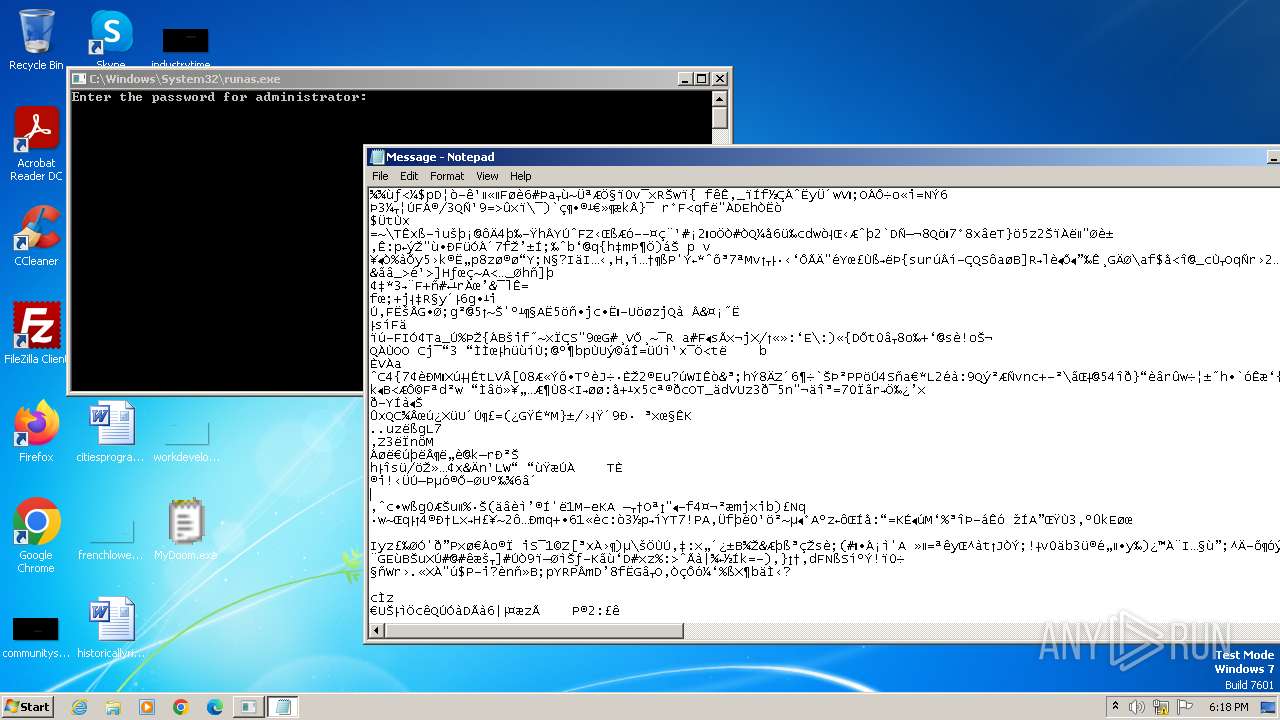
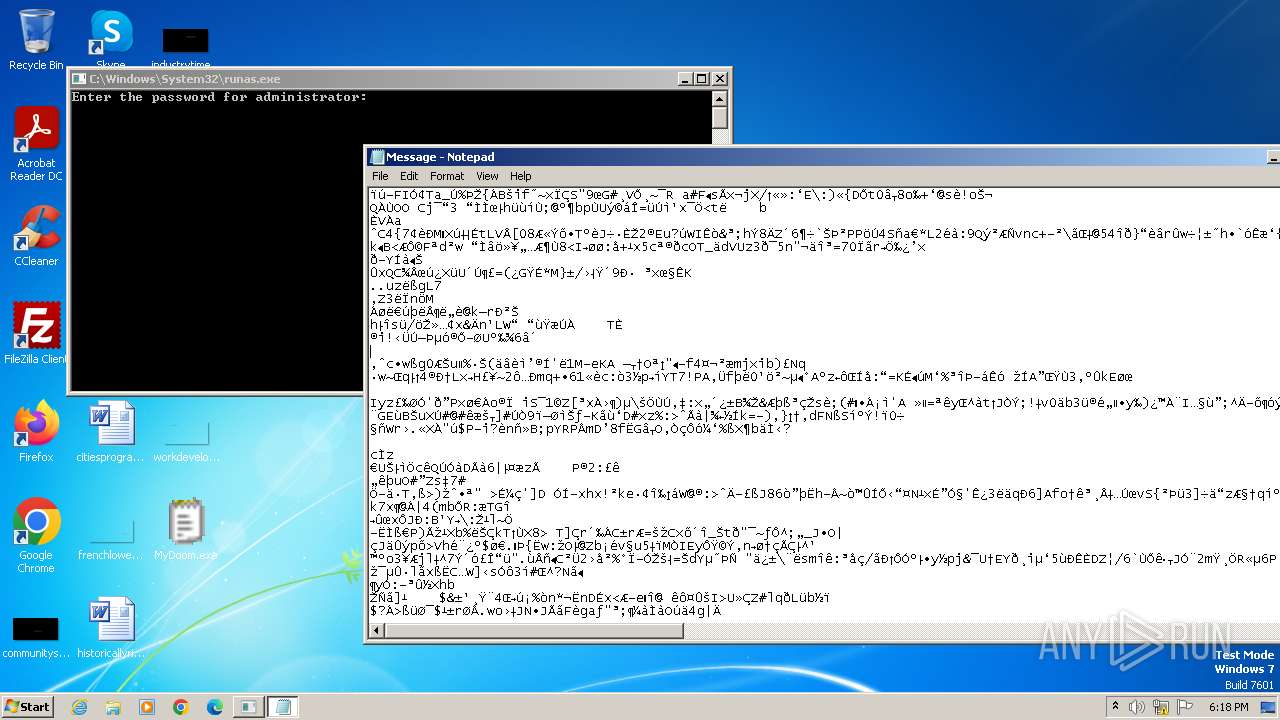
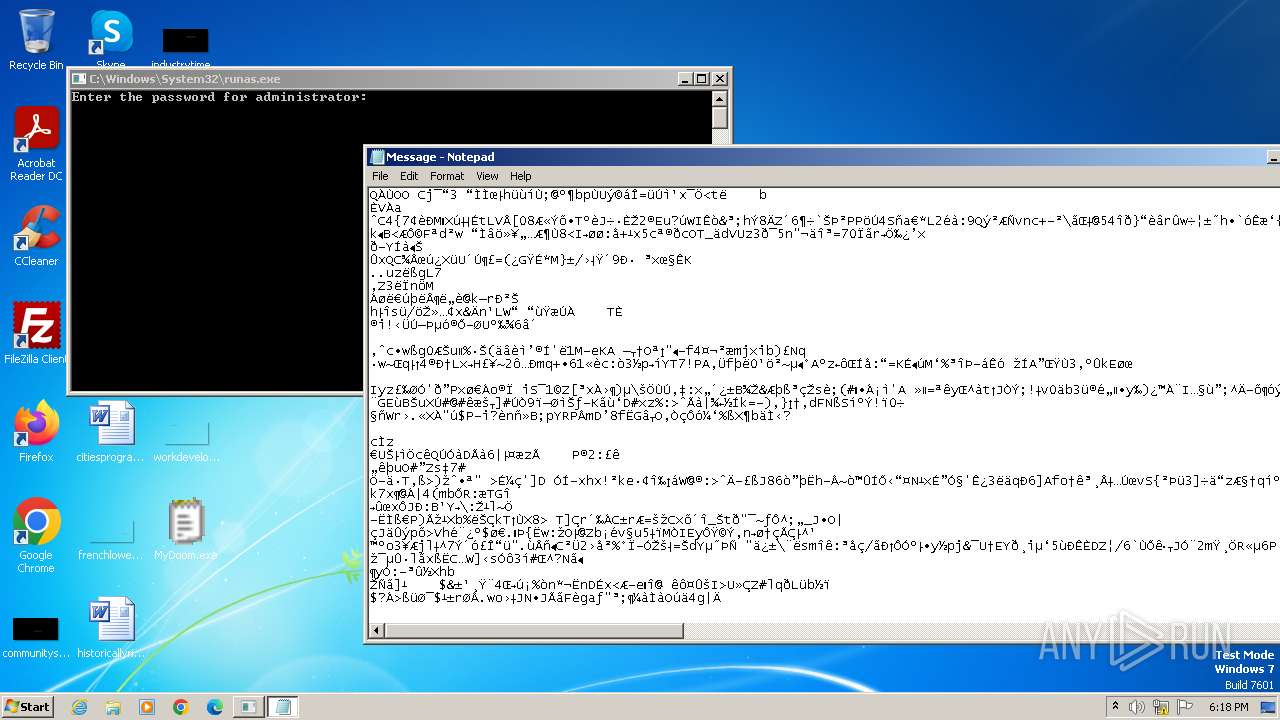
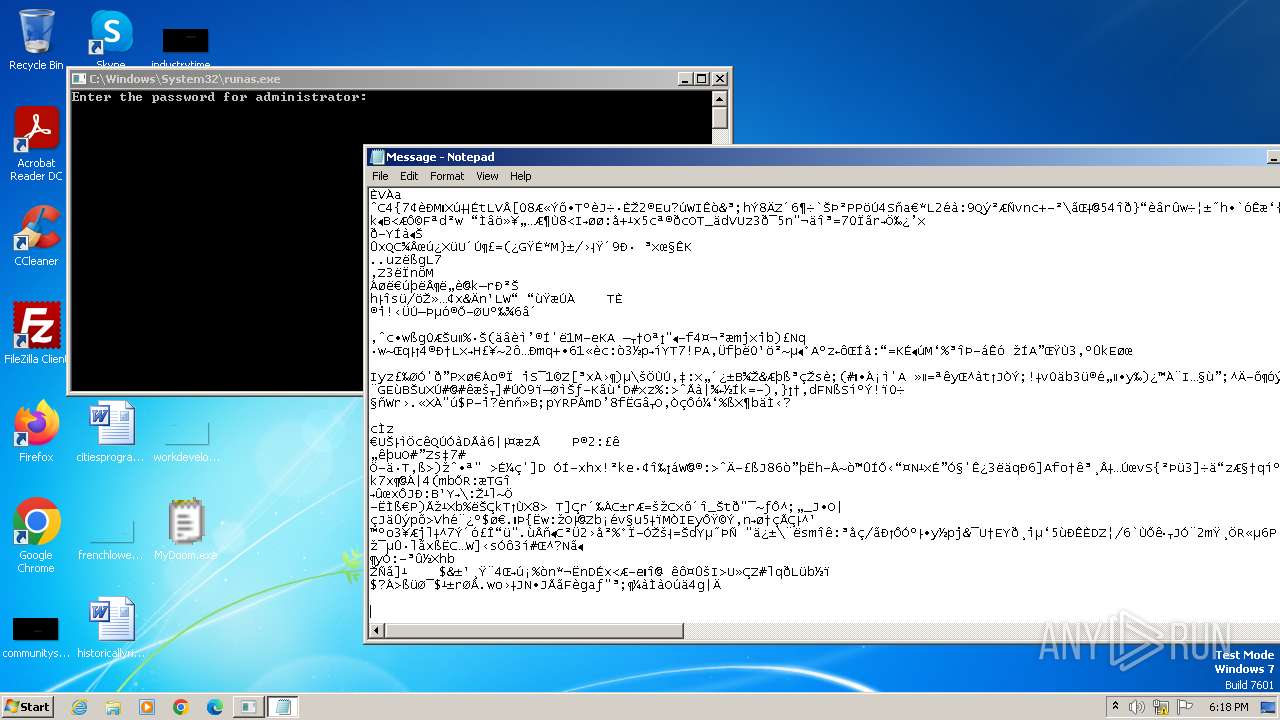
Start notepad (likely ransomware note)
- MyDoom.exe (PID: 1792)
Executable content was dropped or overwritten
- MyDoom.exe (PID: 1792)
INFO
Manual execution by a user
- wmpnscfg.exe (PID: 328)
- MyDoom.exe (PID: 1792)
Checks supported languages
- wmpnscfg.exe (PID: 328)
- MyDoom.exe (PID: 1792)
Reads the computer name
- wmpnscfg.exe (PID: 328)
- MyDoom.exe (PID: 1792)
Potential library load (Base64 Encoded 'LoadLibrary')
- MyDoom.exe (PID: 1792)
Checks proxy server information
- MyDoom.exe (PID: 1792)
Potential dynamic function import (Base64 Encoded 'GetProcAddress')
- MyDoom.exe (PID: 1792)
Failed to create an executable file in Windows directory
- MyDoom.exe (PID: 1792)
Create files in a temporary directory
- MyDoom.exe (PID: 1792)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:12:10 18:34:33+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 65536 |
| InitializedDataSize: | 41472 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x6695 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Total processes
38
Monitored processes
5
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 328 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1108 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1560 | "C:\Windows\System32\runas.exe" /user:administrator C:\Users\admin\Desktop\MyDoom.exe | C:\Windows\System32\runas.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Run As Utility Exit code: 3221225786 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1608 | notepad C:\Users\admin\AppData\Local\Temp\Message | C:\Windows\System32\notepad.exe | — | MyDoom.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1792 | "C:\Users\admin\Desktop\MyDoom.exe" | C:\Users\admin\Desktop\MyDoom.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
Total events
798
Read events
791
Write events
3
Delete events
4
Modification events
| (PID) Process: | (1792) MyDoom.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | TaskMon |
Value: C:\Users\admin\AppData\Local\Temp\taskmon.exe | |||
| (PID) Process: | (1792) MyDoom.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (1792) MyDoom.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyServer |
Value: | |||
| (PID) Process: | (1792) MyDoom.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyOverride |
Value: | |||
| (PID) Process: | (1792) MyDoom.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoConfigURL |
Value: | |||
| (PID) Process: | (1792) MyDoom.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoDetect |
Value: | |||
| (PID) Process: | (1792) MyDoom.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005F010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
1
Suspicious files
3
Text files
0
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1792 | MyDoom.exe | C:\Users\admin\AppData\Local\Temp\taskmon.exe | executable | |
MD5:D4F4D6CEF290E72331CF4F53DF1FD3BA | SHA256:9C3AC72B7248A9DE2F996E08A53919AEA831322EA41EBBB63556AB719A714EDB | |||
| 1792 | MyDoom.exe | C:\Users\admin\AppData\Local\Temp\Message | binary | |
MD5:F009CEBB01FCF45D2859A6CA8E30338B | SHA256:E49DD1B92B22941BAFE67945CCD8FDBF634C3CC52AD52819AC915B55A90FA96B | |||
| 1792 | MyDoom.exe | C:\Users\admin\AppData\Local\Temp\tmpE215.tmp | compressed | |
MD5:142FB4CBF73619FBCF1834813D9DFA1C | SHA256:E956741DE555E21CBB670C3DBB79F30058F1CC8CEA8B15F2BCD7620F19FECAB0 | |||
| 1792 | MyDoom.exe | C:\Users\admin\AppData\Local\Temp\tmpE225.tmp | compressed | |
MD5:B676676FC0614C006BCFD0A1B77CD721 | SHA256:F521A9A92314D7C2A6AF2169F98A7DA063153F42FE7A2D1D071BC415551D737E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
13
DNS requests
29
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1108 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
1792 | MyDoom.exe | 17.57.170.2:25 | mx-in.g.apple.com | APPLE-ENGINEERING | US | whitelisted |
1792 | MyDoom.exe | 138.197.213.185:25 | mx1.forwardemail.net | DIGITALOCEAN-ASN | US | malicious |
1792 | MyDoom.exe | 64.29.151.236:25 | ismtp.sitestar.everyone.net | INFB2-AS | US | whitelisted |
1792 | MyDoom.exe | 108.177.98.26:25 | alt4.gmail-smtp-in.l.google.com | GOOGLE | US | whitelisted |
1792 | MyDoom.exe | 98.136.96.75:25 | mta5.am0.yahoodns.net | YAHOO-NE1 | US | malicious |
1792 | MyDoom.exe | 104.248.224.170:25 | mx2.forwardemail.net | DIGITALOCEAN-ASN | US | unknown |
1792 | MyDoom.exe | 20.172.142.146:25 | theriver.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
apple.com |
| whitelisted |
mx-in.g.apple.com |
| whitelisted |
bryson.demon.co.uk |
| whitelisted |
theriver.com |
| unknown |
src.dec.com |
| unknown |
cl.cam.ac.uk |
| whitelisted |
mx1.forwardemail.net |
| unknown |
ismtp.sitestar.everyone.net |
| whitelisted |
mx.src.dec.com |
| unknown |