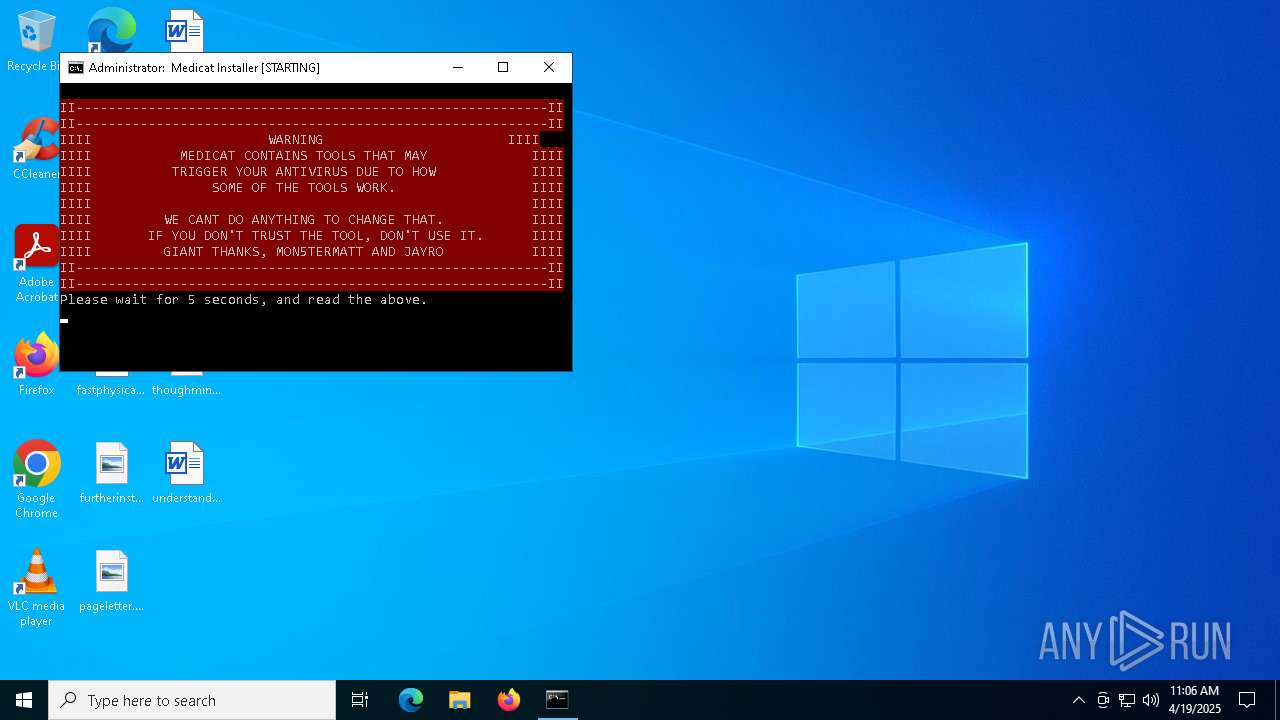
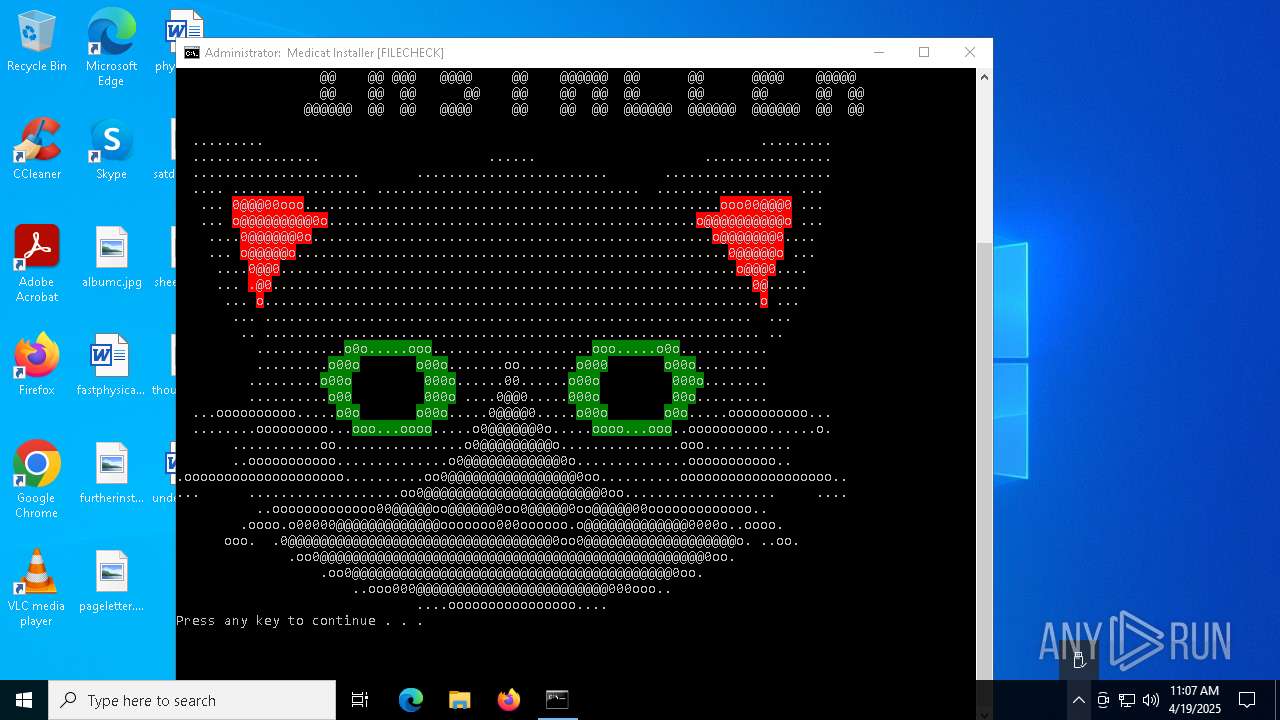
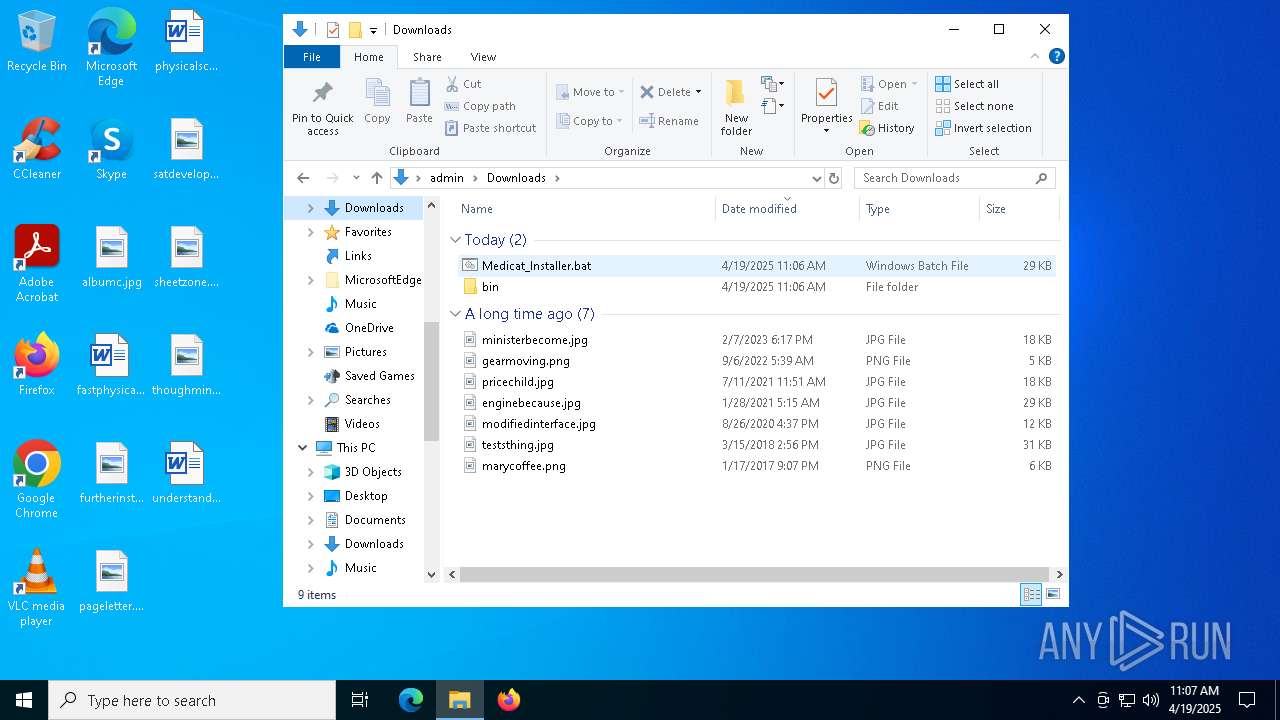
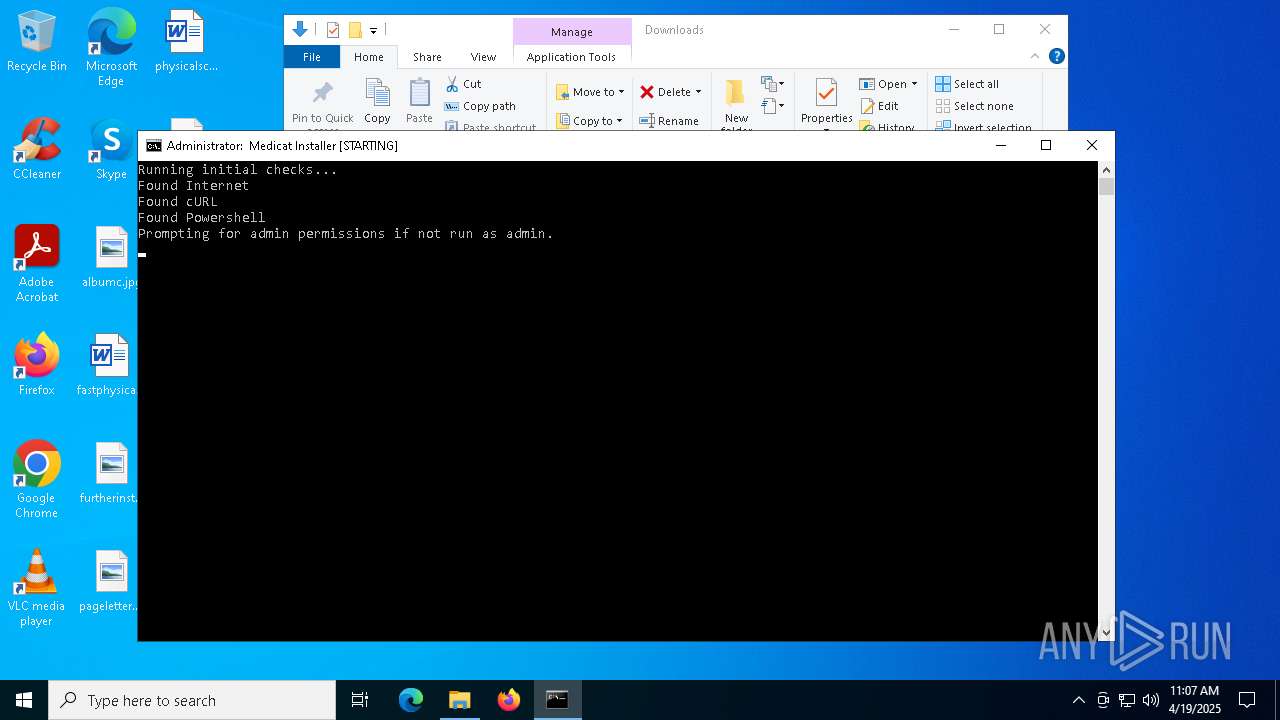
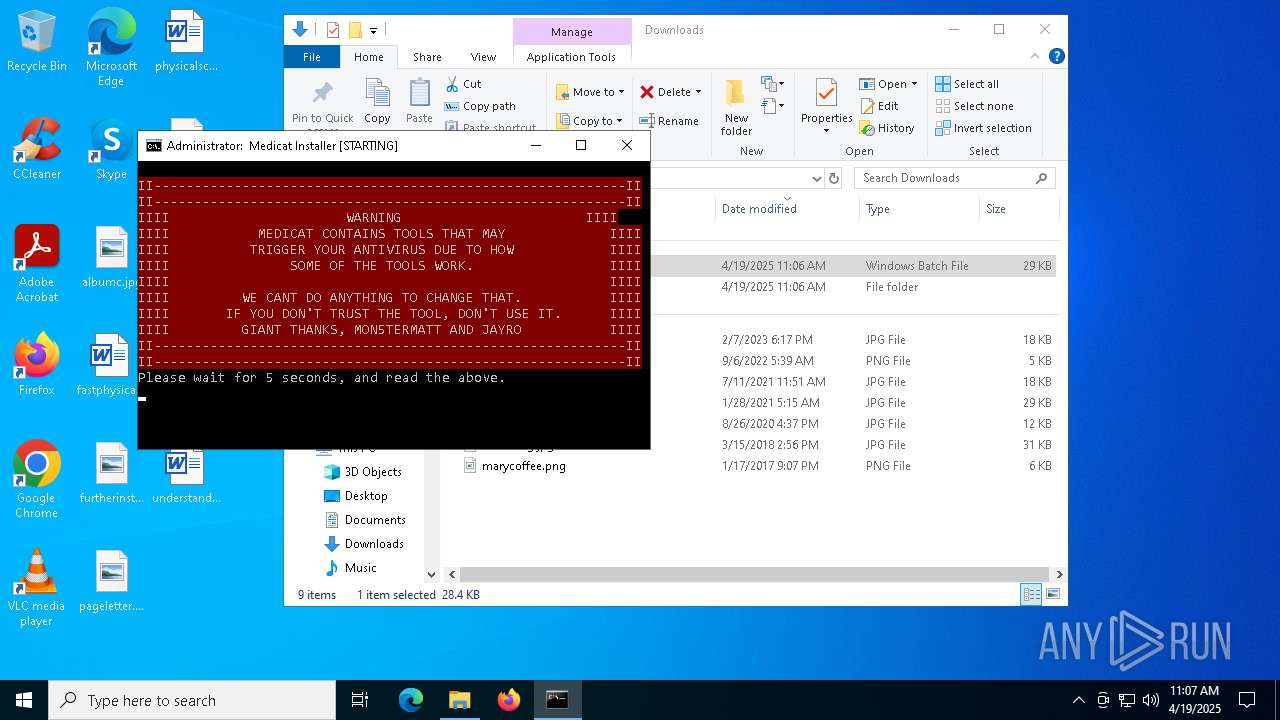
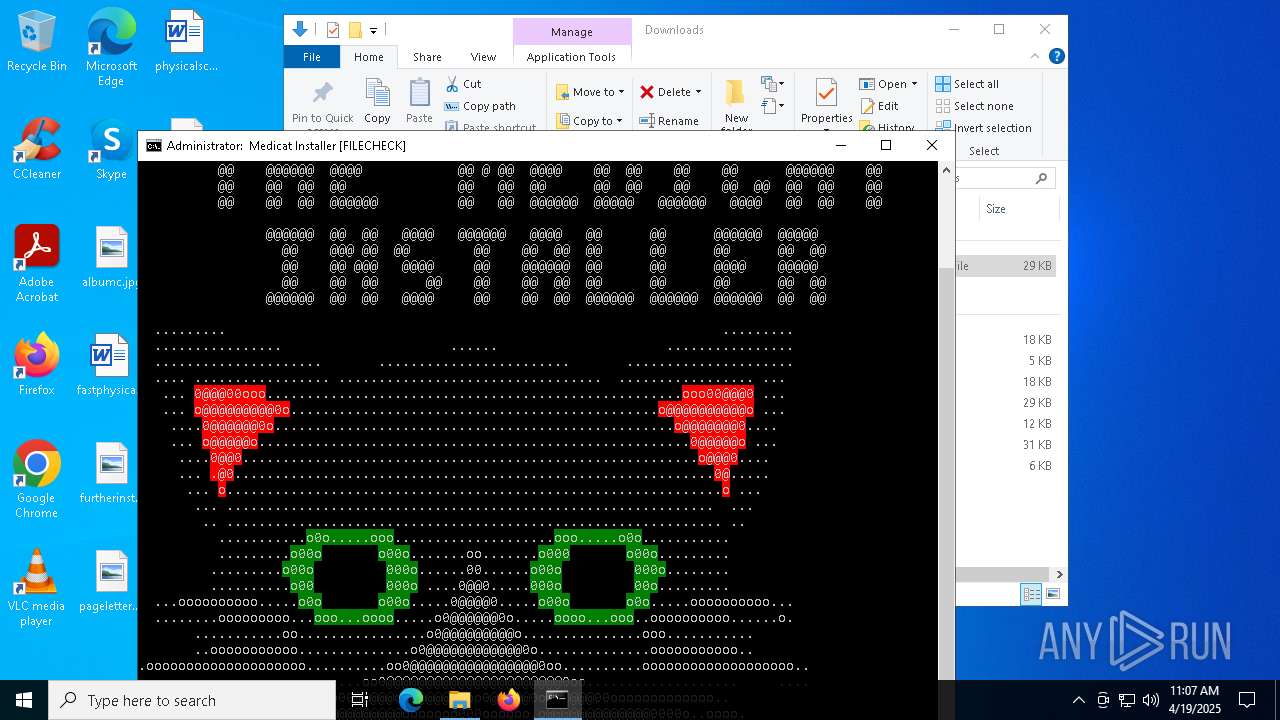
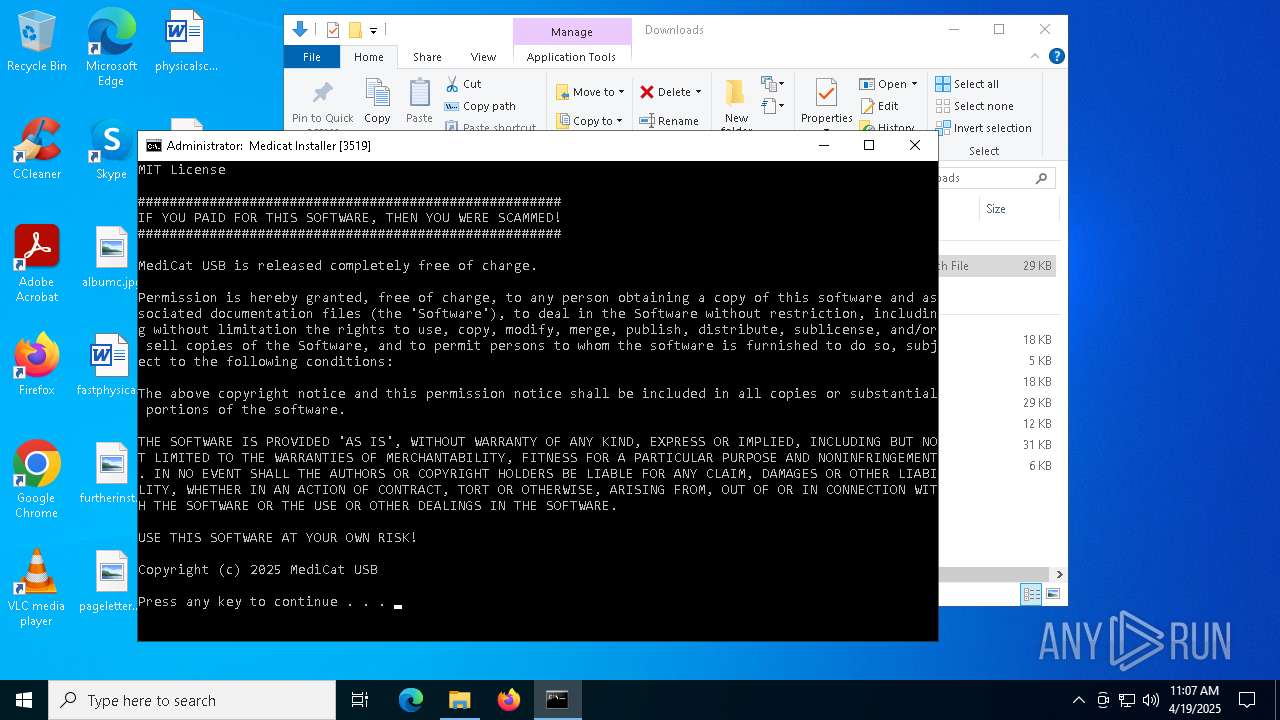
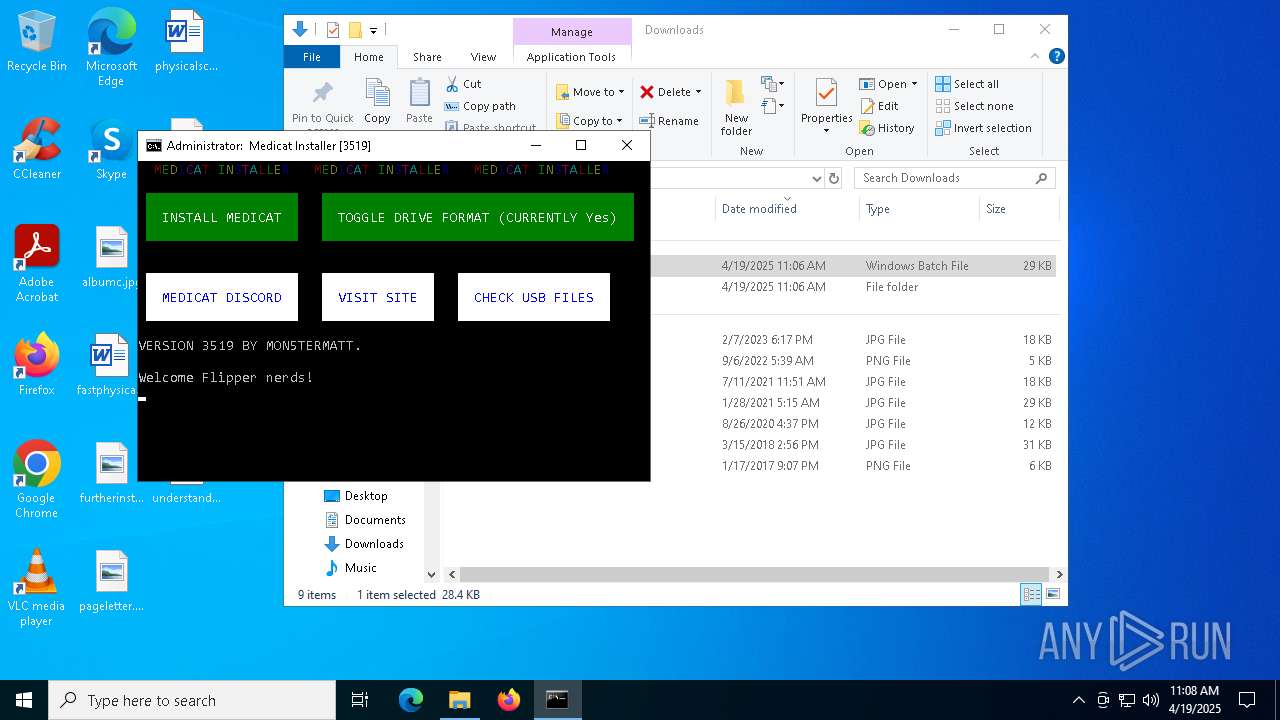
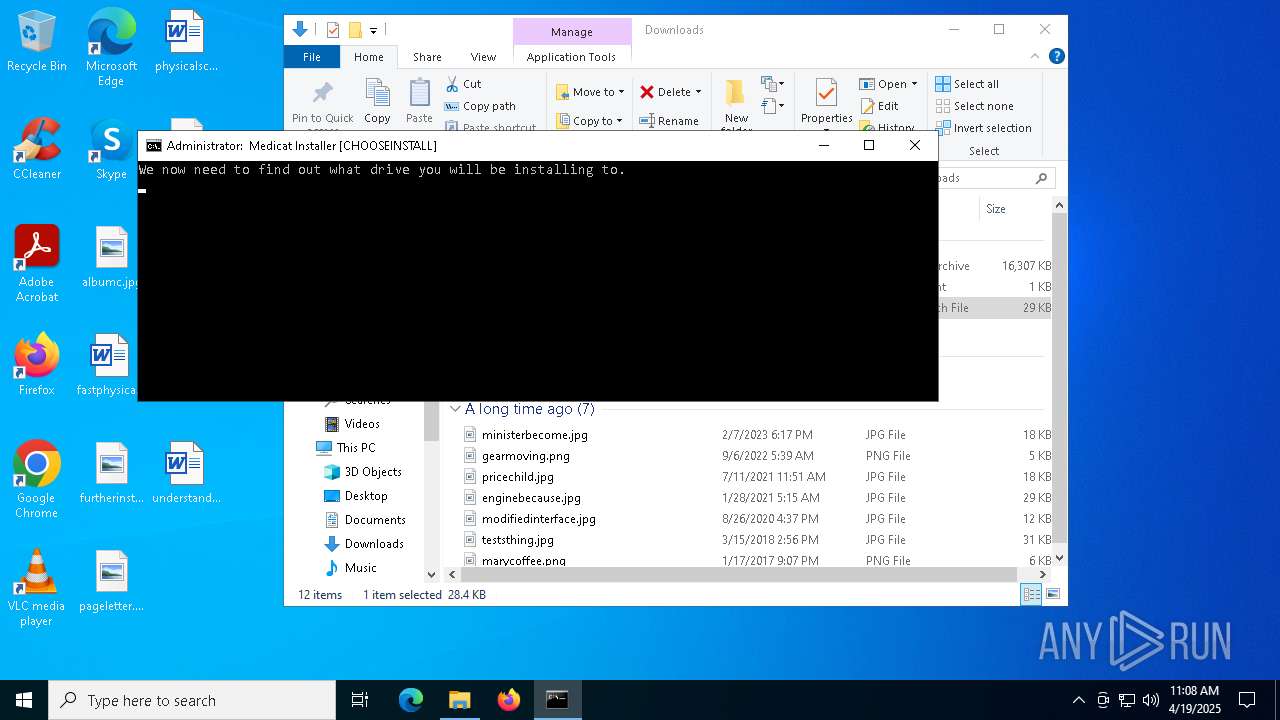
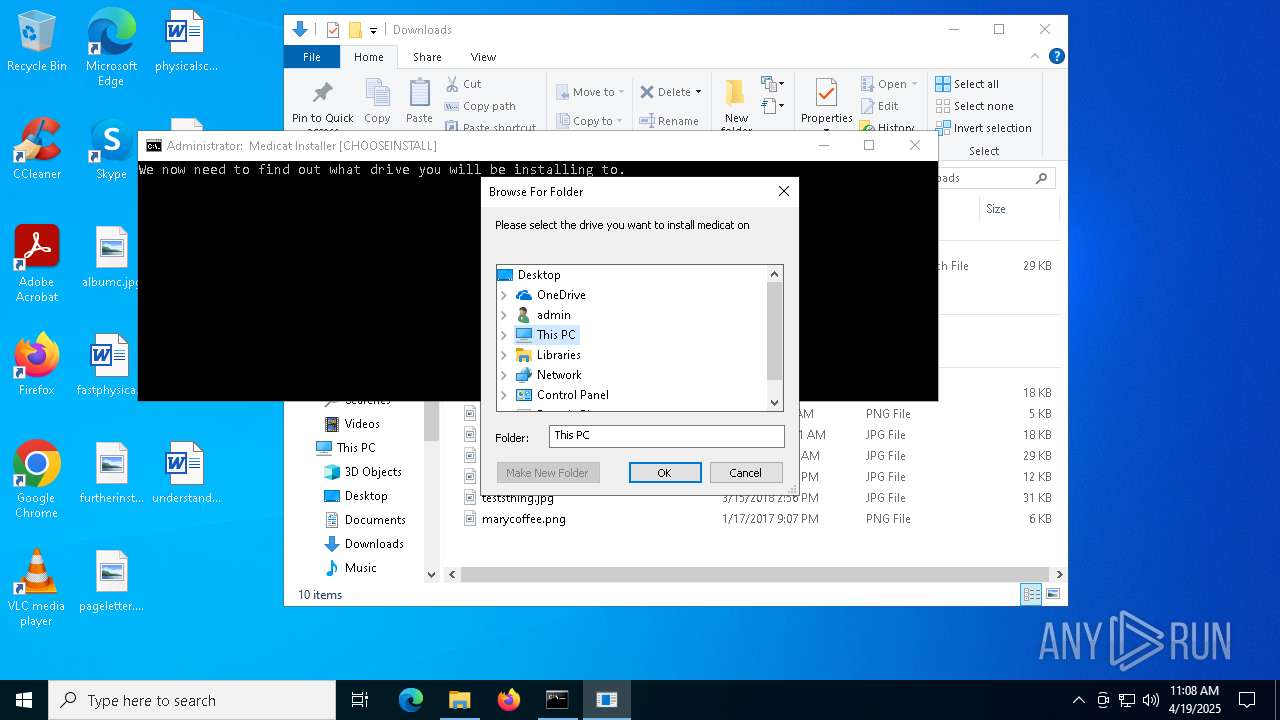
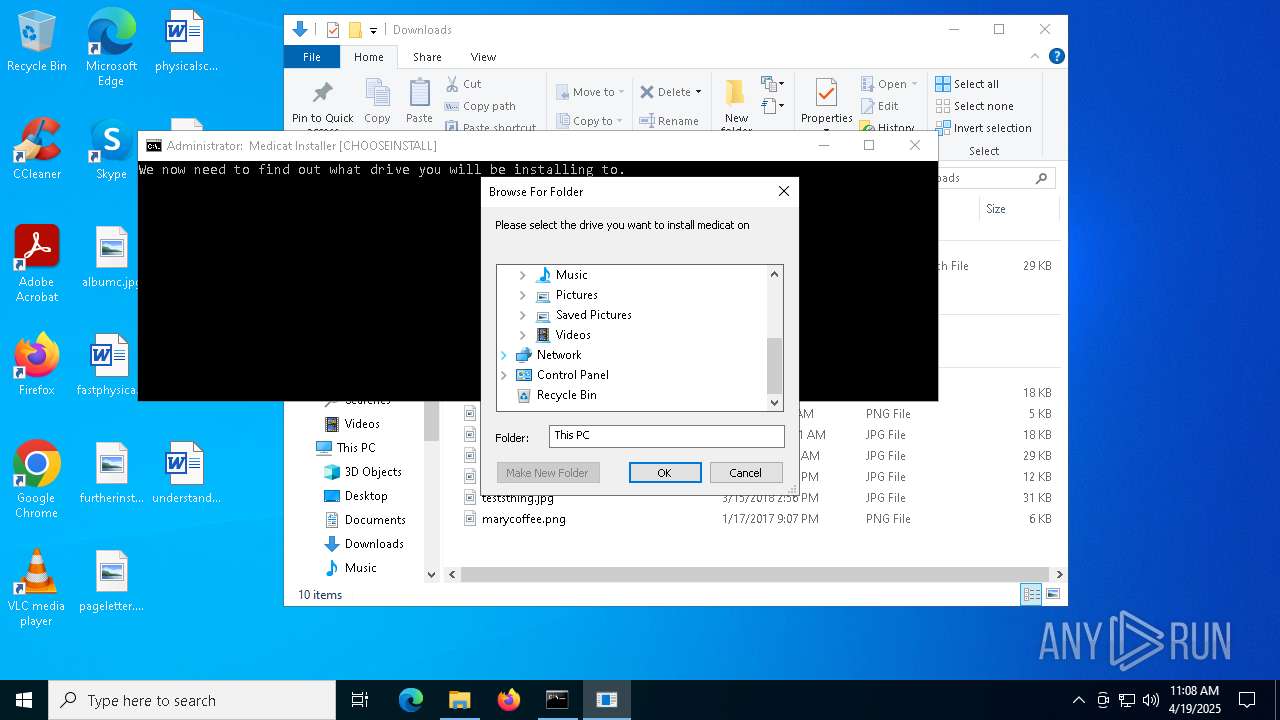
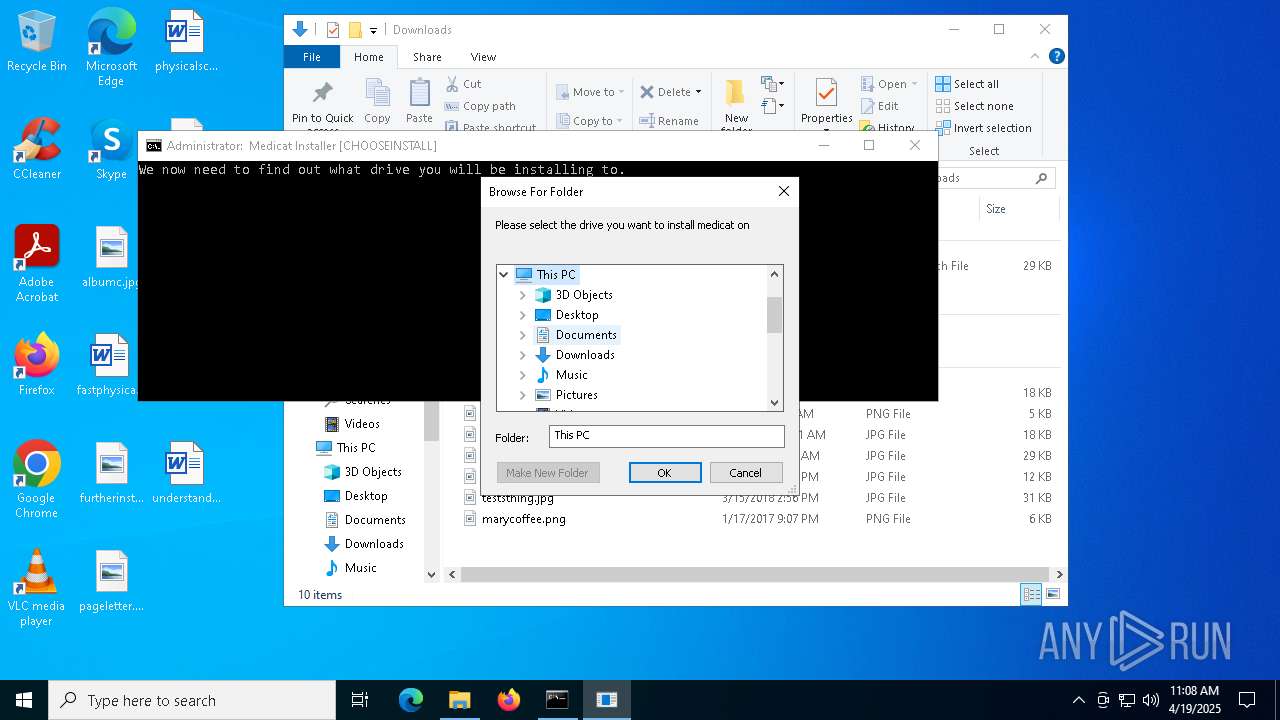
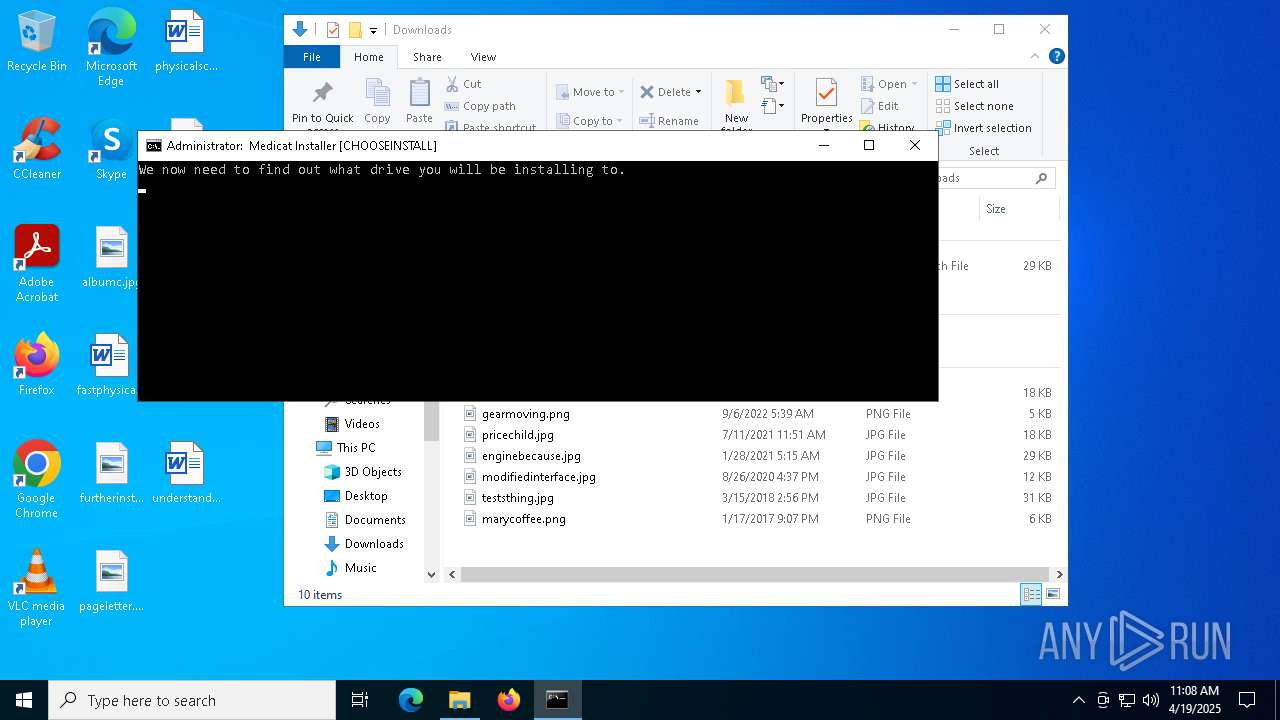
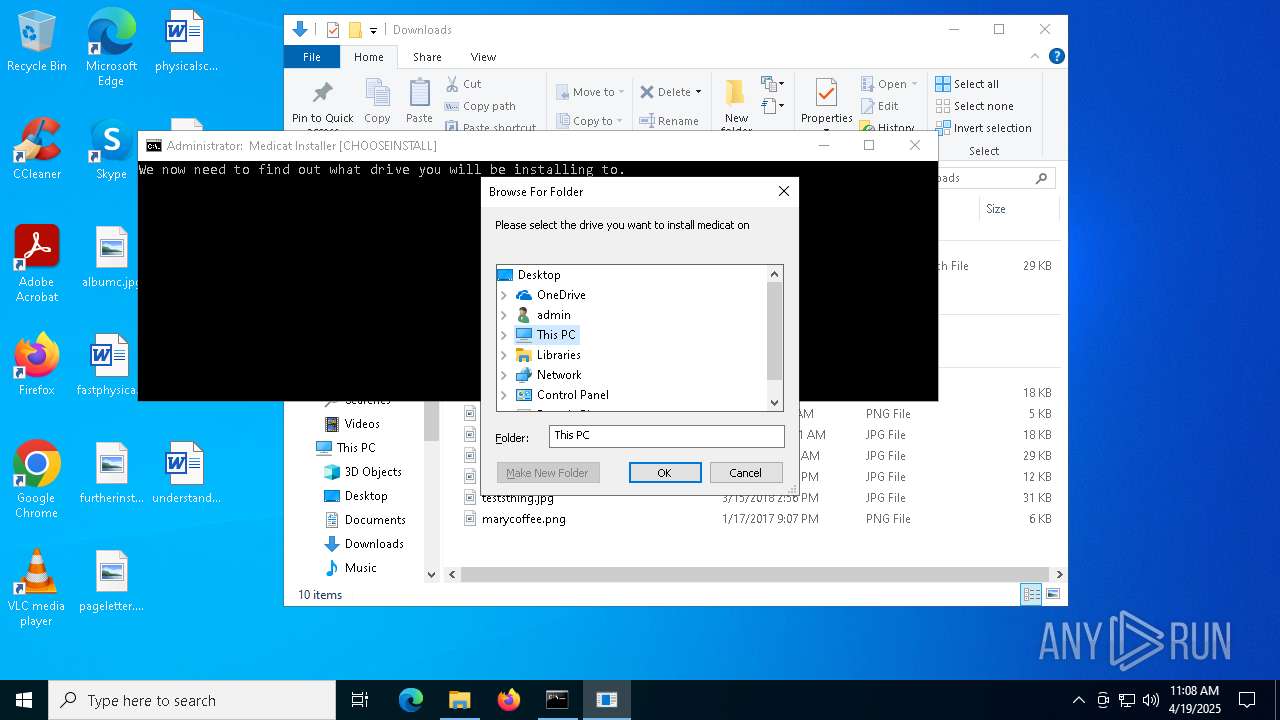
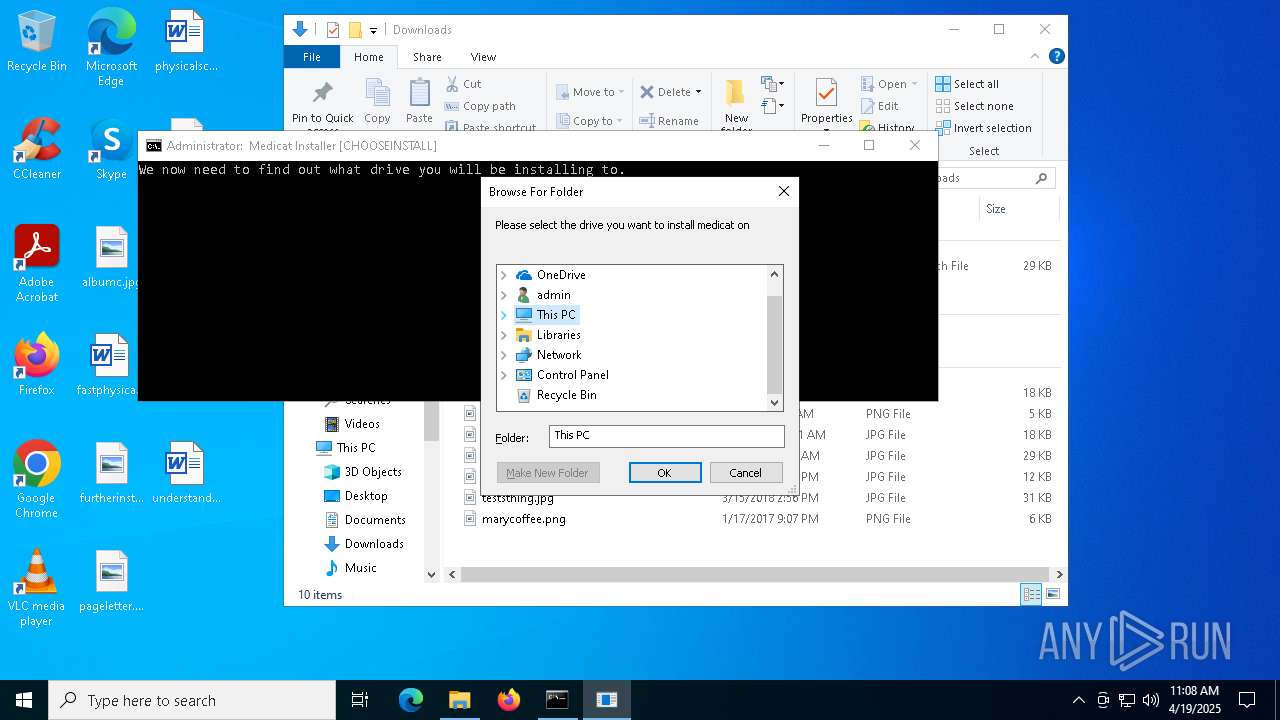
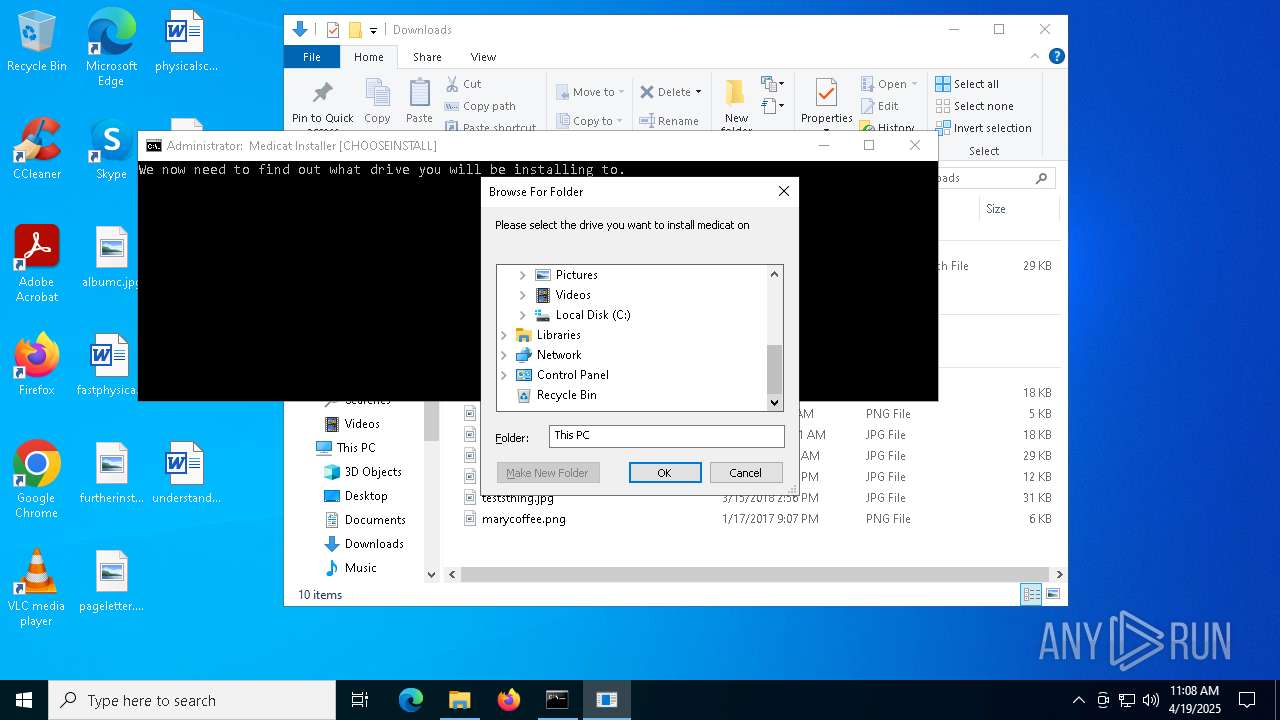
| File name: | Medicat_Installer.bat |
| Full analysis: | https://app.any.run/tasks/d4680b99-6379-4829-81ac-10a9ae03cc7e |
| Verdict: | Malicious activity |
| Analysis date: | April 19, 2025, 11:06:13 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with escape sequences |
| MD5: | 43E14B2C0E7E5FD8F0ED3A98B4DF67D1 |
| SHA1: | 7BEF25B7ECCEFA7F5528FC6973937DA56D10BE4C |
| SHA256: | 9C1C2D2E0C0D8E216C2E1269E339E01169BD0DD40939016F3FE3F12646965334 |
| SSDEEP: | 192:UMCw3UbaLX13a7BJ2ZOTH5mkuEYb+oMGR3EUgXLcHgKjAZqNrF8rzGF86kWyz5Bj:Kw3KaLcH5mk4cANAEAYpNe1+r2tP |
MALICIOUS
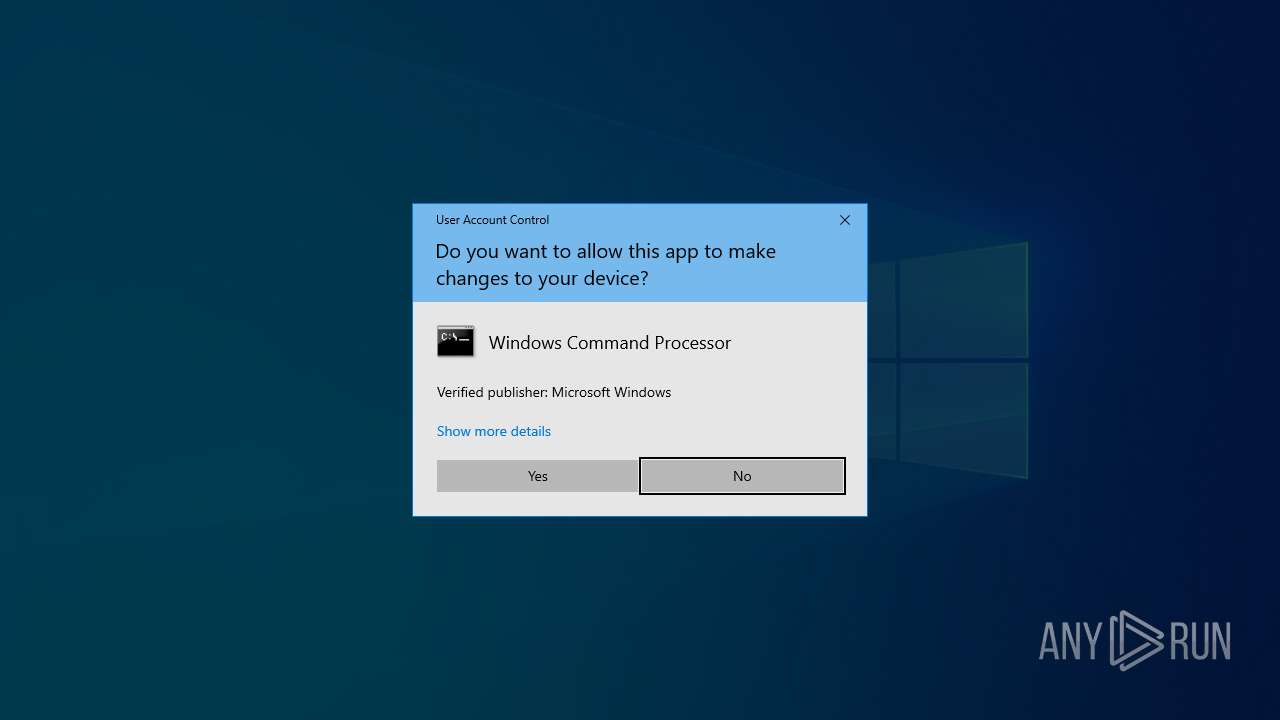
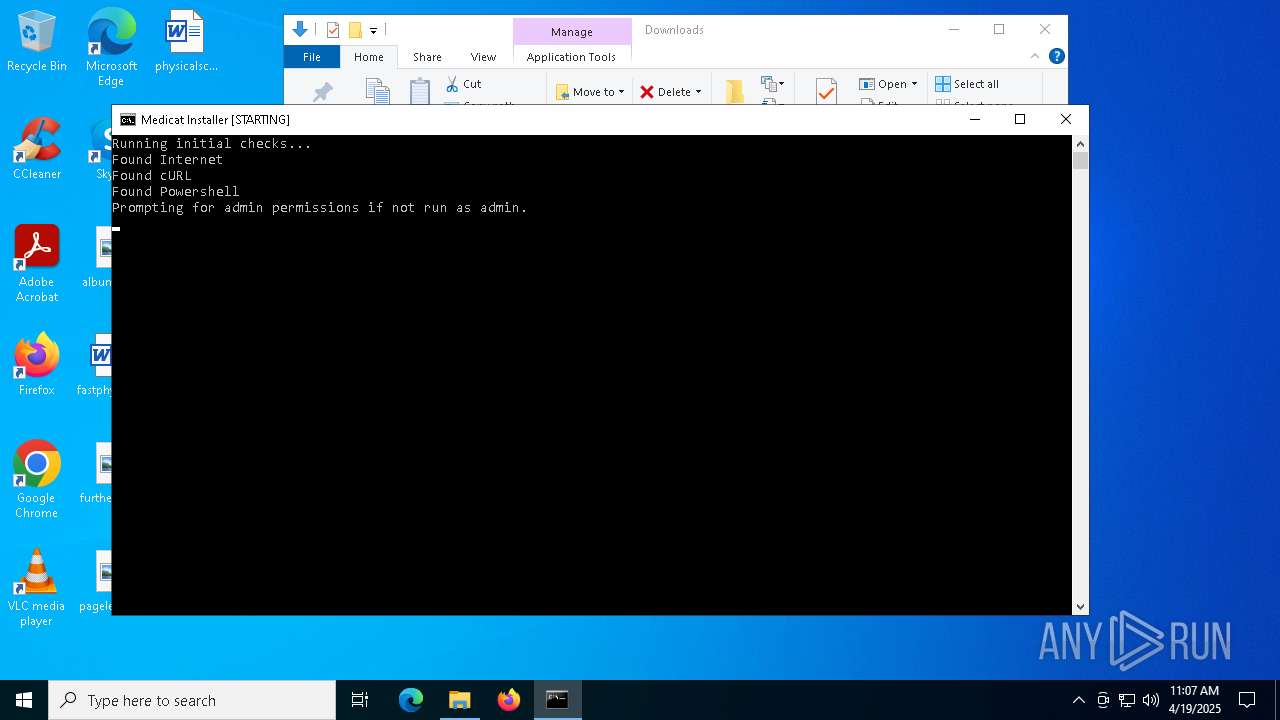
Changes powershell execution policy (RemoteSigned)
- cmd.exe (PID: 7816)
- cmd.exe (PID: 3332)
SUSPICIOUS
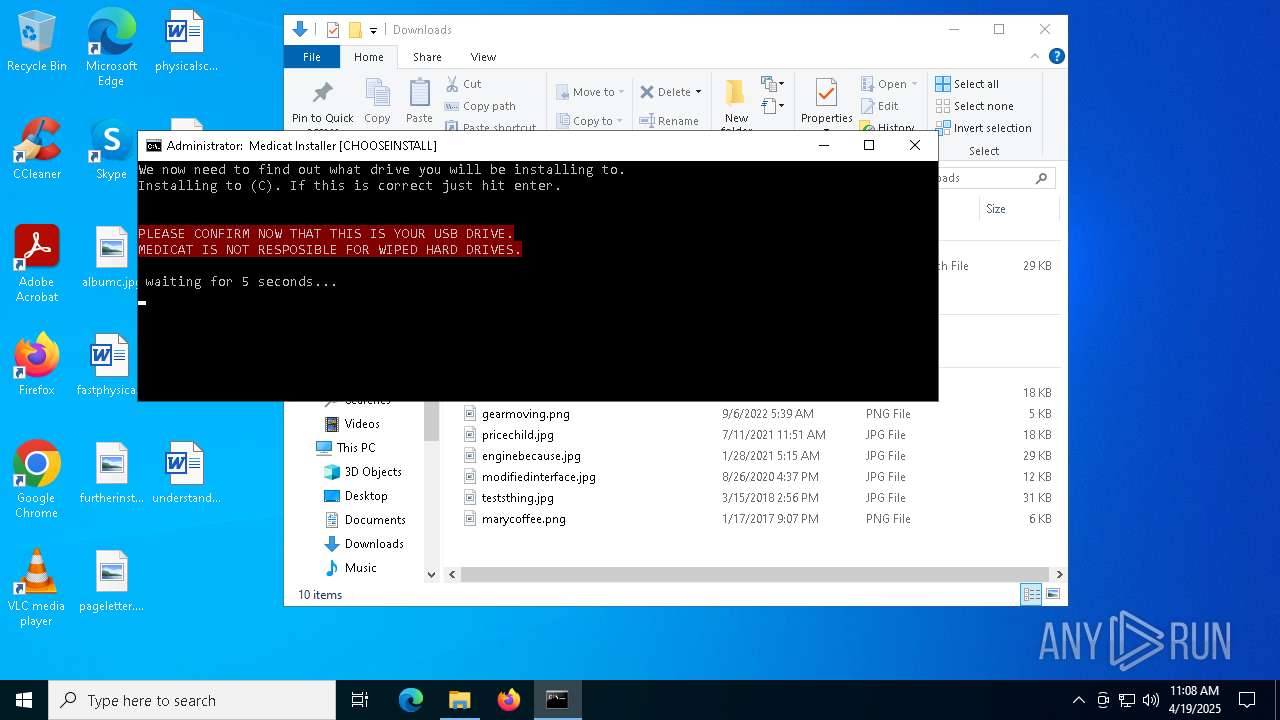
Uses TIMEOUT.EXE to delay execution
- cmd.exe (PID: 1628)
- cmd.exe (PID: 7816)
- cmd.exe (PID: 4000)
- cmd.exe (PID: 3332)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 1628)
- powershell.exe (PID: 5324)
- cmd.exe (PID: 7816)
- cmd.exe (PID: 4000)
- powershell.exe (PID: 7976)
- cmd.exe (PID: 3332)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 1628)
- cmd.exe (PID: 7816)
- cmd.exe (PID: 4000)
- cmd.exe (PID: 3332)
Application launched itself
- cmd.exe (PID: 1628)
- cmd.exe (PID: 7816)
- cmd.exe (PID: 4000)
- cmd.exe (PID: 3332)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1628)
- cmd.exe (PID: 7816)
- cmd.exe (PID: 4000)
- cmd.exe (PID: 3332)
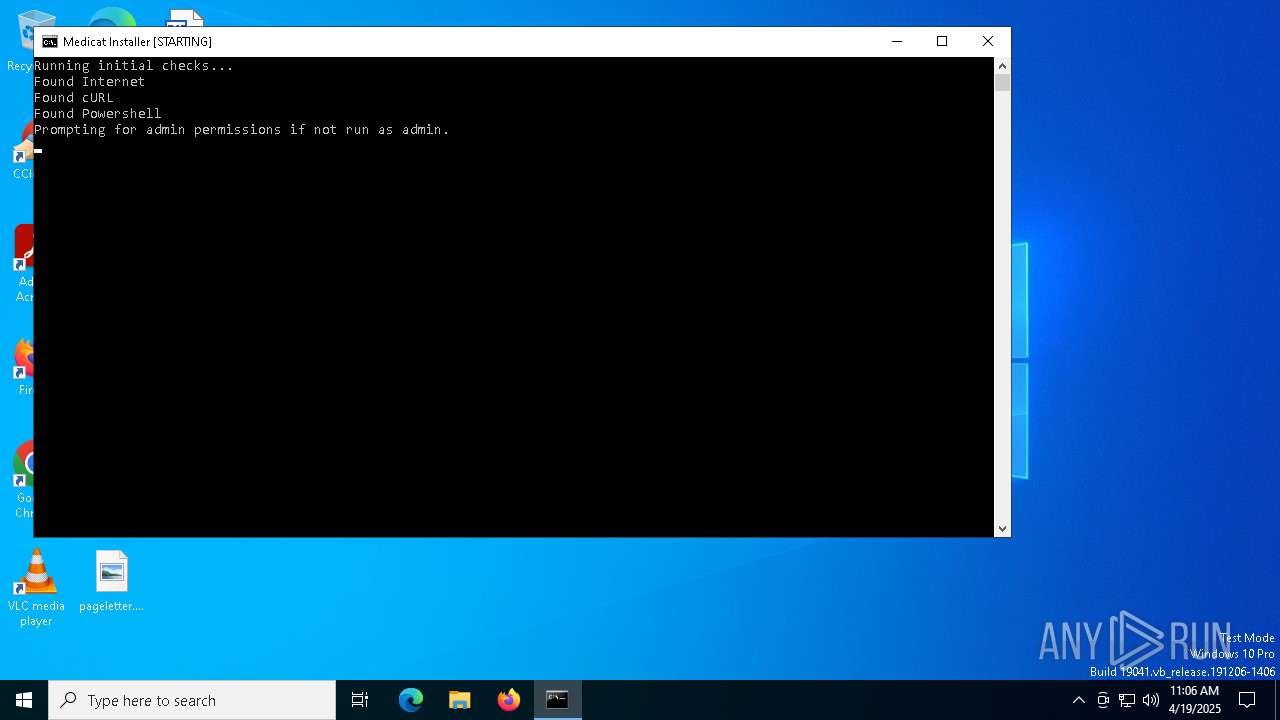
Executing commands from a ".bat" file
- powershell.exe (PID: 5324)
- powershell.exe (PID: 7976)
Download files or web resources using Curl/Wget
- cmd.exe (PID: 7816)
- cmd.exe (PID: 3332)
Probably obfuscated PowerShell command line is found
- cmd.exe (PID: 7816)
- cmd.exe (PID: 3332)
Executable content was dropped or overwritten
- curl.exe (PID: 1188)
- curl.exe (PID: 6388)
- curl.exe (PID: 7192)
- curl.exe (PID: 2268)
- curl.exe (PID: 5360)
- curl.exe (PID: 7396)
- 7z.exe (PID: 3016)
Drops 7-zip archiver for unpacking
- curl.exe (PID: 2268)
- curl.exe (PID: 5360)
The process executes Powershell scripts
- cmd.exe (PID: 3332)
The executable file from the user directory is run by the CMD process
- batbox.exe (PID: 6560)
- batbox.exe (PID: 4572)
- batbox.exe (PID: 2664)
- batbox.exe (PID: 2564)
- GetInput.exe (PID: 7644)
- batbox.exe (PID: 7848)
- 7z.exe (PID: 3016)
- batbox.exe (PID: 3156)
- folderbrowse.exe (PID: 7792)
- folderbrowse.exe (PID: 7184)
Reads security settings of Internet Explorer
- folderbrowse.exe (PID: 7792)
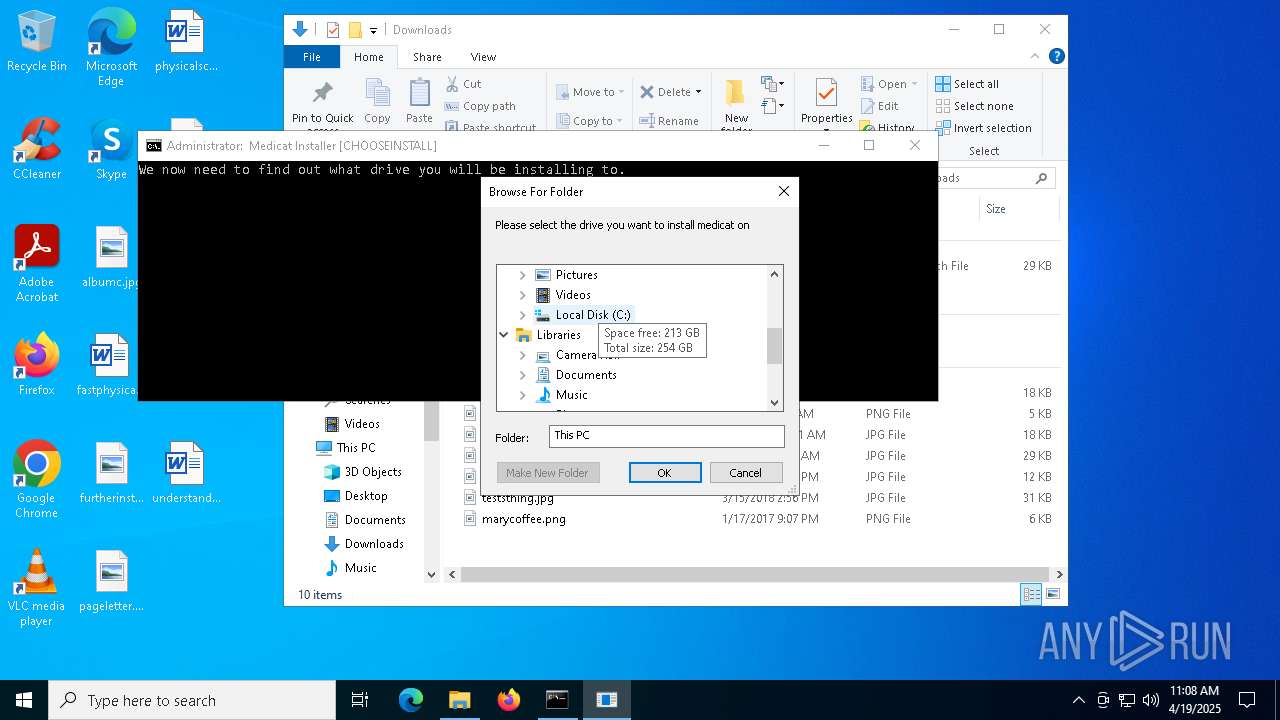
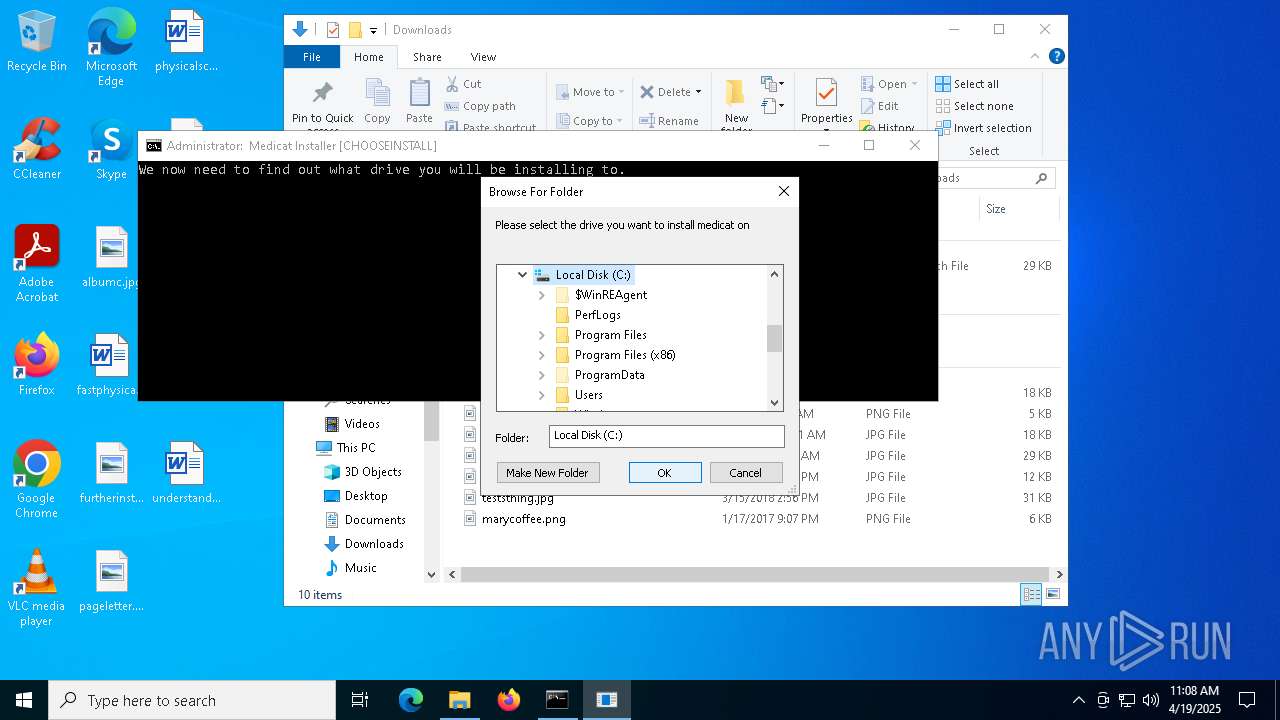
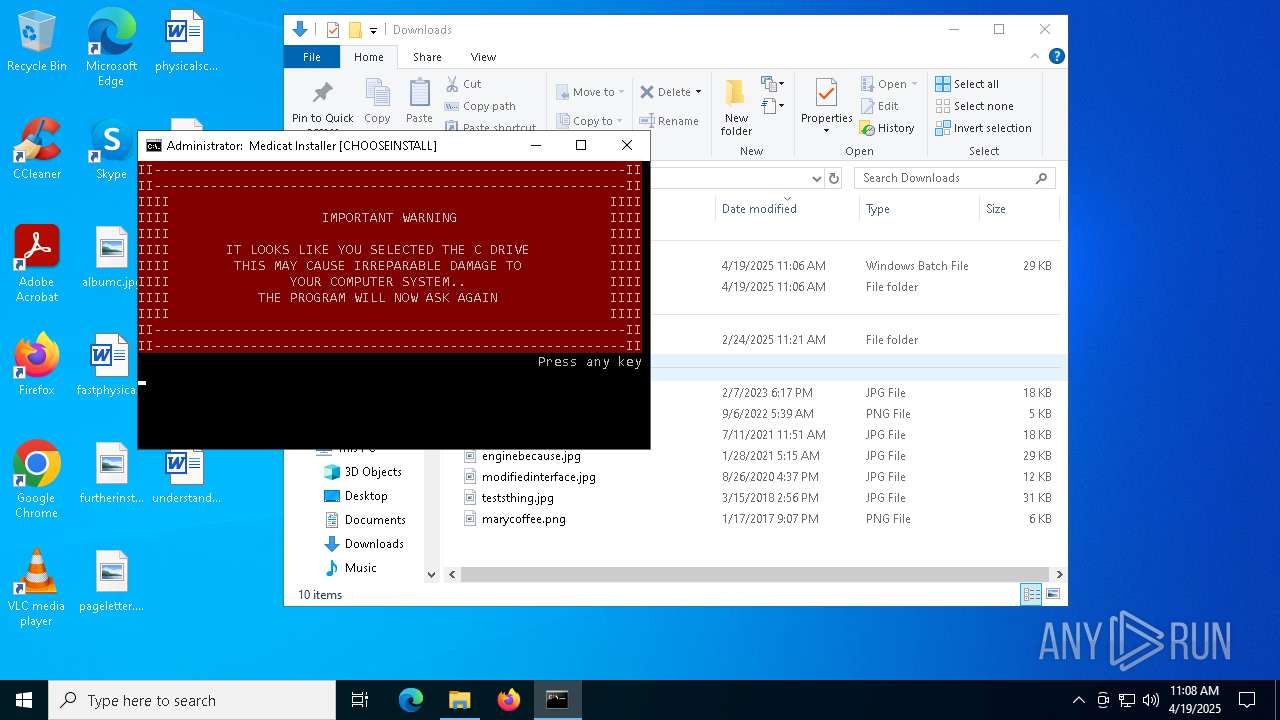
Creates file in the systems drive root
- folderbrowse.exe (PID: 7792)
INFO
Checks supported languages
- curl.exe (PID: 7968)
- curl.exe (PID: 6564)
- mode.com (PID: 8100)
- curl.exe (PID: 1188)
- curl.exe (PID: 6540)
- curl.exe (PID: 2384)
- curl.exe (PID: 6272)
- curl.exe (PID: 7192)
- curl.exe (PID: 7396)
- curl.exe (PID: 2268)
- curl.exe (PID: 5360)
- curl.exe (PID: 5756)
- mode.com (PID: 7780)
- curl.exe (PID: 4464)
- curl.exe (PID: 7916)
- curl.exe (PID: 4784)
- mode.com (PID: 6324)
- curl.exe (PID: 5260)
- curl.exe (PID: 2552)
- curl.exe (PID: 5756)
- curl.exe (PID: 7180)
- curl.exe (PID: 4528)
- curl.exe (PID: 6468)
- curl.exe (PID: 5136)
- curl.exe (PID: 7632)
- curl.exe (PID: 208)
- curl.exe (PID: 6388)
- curl.exe (PID: 5576)
- mode.com (PID: 2516)
- mode.com (PID: 1748)
- curl.exe (PID: 2908)
- curl.exe (PID: 7516)
- curl.exe (PID: 7412)
- batbox.exe (PID: 6560)
- mode.com (PID: 3396)
- batbox.exe (PID: 4572)
- batbox.exe (PID: 2664)
- batbox.exe (PID: 2564)
- batbox.exe (PID: 3156)
- batbox.exe (PID: 7848)
- curl.exe (PID: 8136)
- 7z.exe (PID: 3016)
- folderbrowse.exe (PID: 7792)
- folderbrowse.exe (PID: 7184)
- mode.com (PID: 5344)
- mode.com (PID: 7568)
- mode.com (PID: 8036)
Execution of CURL command
- cmd.exe (PID: 1628)
- cmd.exe (PID: 7816)
- cmd.exe (PID: 4000)
- cmd.exe (PID: 3332)
Checks operating system version
- cmd.exe (PID: 7816)
- cmd.exe (PID: 3332)
Starts MODE.COM to configure console settings
- mode.com (PID: 8100)
- mode.com (PID: 7780)
- mode.com (PID: 6324)
- mode.com (PID: 2516)
- mode.com (PID: 3396)
- mode.com (PID: 1748)
- mode.com (PID: 5344)
- mode.com (PID: 7568)
- mode.com (PID: 8036)
Disables trace logs
- powershell.exe (PID: 8124)
- powershell.exe (PID: 2140)
- powershell.exe (PID: 3032)
- powershell.exe (PID: 5324)
- powershell.exe (PID: 7868)
Checks proxy server information
- powershell.exe (PID: 8124)
- powershell.exe (PID: 2140)
- powershell.exe (PID: 3032)
- powershell.exe (PID: 7868)
- powershell.exe (PID: 5324)
- slui.exe (PID: 7836)
Reads the computer name
- curl.exe (PID: 1188)
- curl.exe (PID: 2384)
- curl.exe (PID: 6540)
- curl.exe (PID: 6272)
- curl.exe (PID: 6388)
- curl.exe (PID: 7192)
- curl.exe (PID: 7396)
- curl.exe (PID: 2268)
- curl.exe (PID: 5360)
- curl.exe (PID: 5756)
- curl.exe (PID: 4464)
- curl.exe (PID: 2552)
- curl.exe (PID: 5260)
- curl.exe (PID: 5756)
- curl.exe (PID: 4528)
- curl.exe (PID: 7632)
- curl.exe (PID: 7180)
- curl.exe (PID: 208)
- curl.exe (PID: 2908)
- curl.exe (PID: 5576)
- curl.exe (PID: 7516)
- curl.exe (PID: 7412)
- curl.exe (PID: 8136)
- 7z.exe (PID: 3016)
- folderbrowse.exe (PID: 7792)
- curl.exe (PID: 6468)
- folderbrowse.exe (PID: 7184)
- curl.exe (PID: 5136)
The sample compiled with english language support
- curl.exe (PID: 1188)
- curl.exe (PID: 2268)
- curl.exe (PID: 5360)
Reads the software policy settings
- slui.exe (PID: 7248)
- slui.exe (PID: 7836)
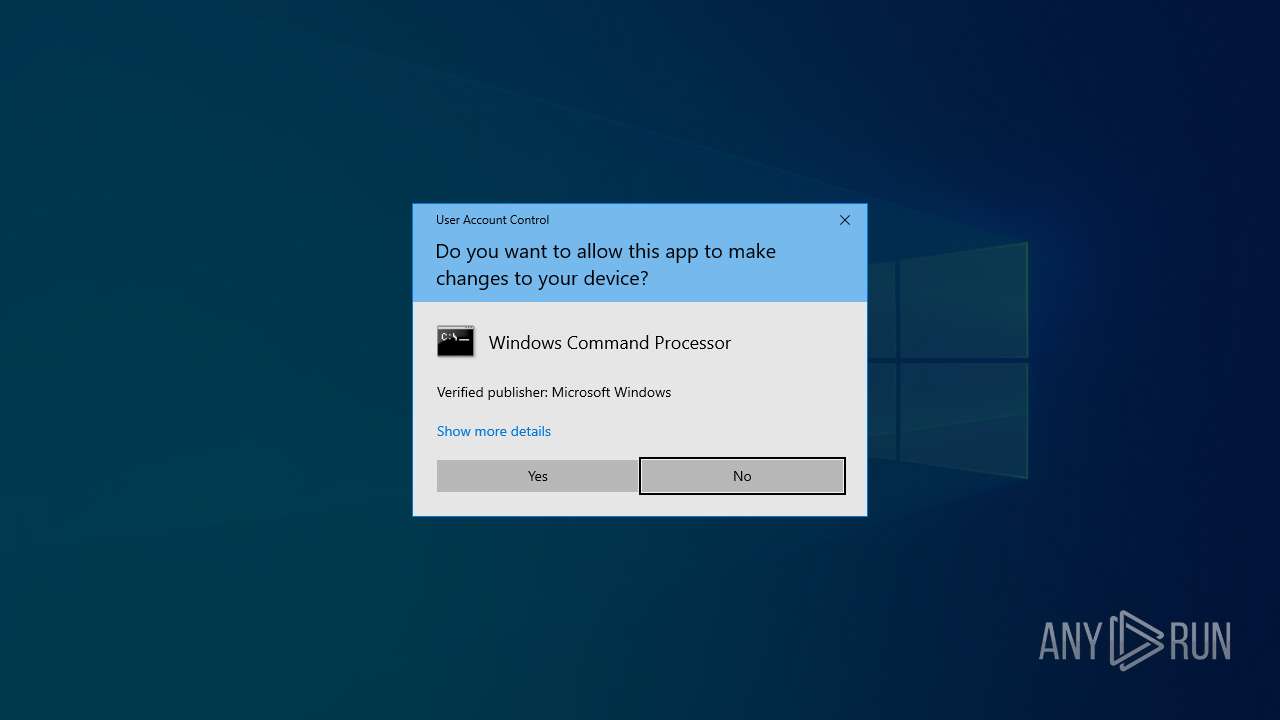
Manual execution by a user
- cmd.exe (PID: 4000)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
238
Monitored processes
104
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 208 | curl "https://raw.githubusercontent.com/mon5termatt/medicat_installer/main/bin/folderbrowse.exe" -o ./bin/folderbrowse.exe -s -L | C:\Windows\System32\curl.exe | cmd.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: HIGH Description: The curl executable Exit code: 0 Version: 8.4.0 Modules
| |||||||||||||||
| 664 | REG QUERY "HKEY_CURRENT_USER\Control Panel\International" /v "LocaleName" | C:\Windows\System32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | ping 1.1.1.1 -n 1 -w 1000 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 904 | ping 1.1.1.1 -n 1 -w 1000 | C:\Windows\System32\PING.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Ping Command Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1088 | timeout 1 | C:\Windows\System32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1188 | curl "https://raw.githubusercontent.com/mon5termatt/medicat_installer/main/bin/QuickSFV.EXE" -o ./bin/QuickSFV.exe -s -L | C:\Windows\System32\curl.exe | cmd.exe | ||||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: HIGH Description: The curl executable Exit code: 0 Version: 8.4.0 Modules
| |||||||||||||||
| 1276 | C:\WINDOWS\system32\cmd.exe /c REG QUERY "HKEY_CURRENT_USER\Control Panel\International" /v "LocaleName" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1452 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1628 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Downloads\Medicat_Installer.bat" " | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1748 | mode con:cols=100 lines=30 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
63 054
Read events
63 048
Write events
6
Delete events
0
Modification events
| (PID) Process: | (5228) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PowerShell\1\ShellIds\Microsoft.PowerShell |
| Operation: | write | Name: | ExecutionPolicy |
Value: RemoteSigned | |||
| (PID) Process: | (7532) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\PowerShell\1\ShellIds\Microsoft.PowerShell |
| Operation: | write | Name: | ExecutionPolicy |
Value: RemoteSigned | |||
| (PID) Process: | (7772) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\PowerShell\1\ShellIds\Microsoft.PowerShell |
| Operation: | write | Name: | ExecutionPolicy |
Value: RemoteSigned | |||
| (PID) Process: | (7732) powershell.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\PowerShell\1\ShellIds\Microsoft.PowerShell |
| Operation: | write | Name: | ExecutionPolicy |
Value: RemoteSigned | |||
| (PID) Process: | (7792) folderbrowse.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Width |
Value: 318 | |||
| (PID) Process: | (7792) folderbrowse.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer |
| Operation: | write | Name: | Browse For Folder Height |
Value: 288 | |||
Executable files
14
Suspicious files
7
Text files
62
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2384 | curl.exe | C:\Users\admin\Downloads\bin\QuickSFV.ini | text | |
MD5:7BE5A47066EDCCD7AA0D3B0D69D607FF | SHA256:2EEA3FA7D366D65C1B27B1D0796FDD9F560E289A6FA9F24DD339E5131D0B099B | |||
| 6388 | curl.exe | C:\Users\admin\Downloads\bin\GetInput.exe | executable | |
MD5:2BA62AE6F88B11D0E262AF35D8DB8CA9 | SHA256:3F5C64717A0092AE214154A730E96E2E56921BE2E3F1121A3E98B1BA84627665 | |||
| 8124 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_zrzum2t0.rfe.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 6272 | curl.exe | C:\Users\admin\Downloads\bin\Button.bat | text | |
MD5:5B727EFF91DE52000CEA8E61694F2A03 | SHA256:03A86F9FCDCCBAA499EA4435434A45178E367639D8FB755C5211F304C70744B5 | |||
| 7192 | curl.exe | C:\Users\admin\Downloads\bin\batbox.exe | executable | |
MD5:CB4A44BAA20AD26BF74615A7FC515A84 | SHA256:9553BC17FA0FD08E026C1865812B3388E3D5495A5394BBF671E5A8F21C79989A | |||
| 1188 | curl.exe | C:\Users\admin\Downloads\bin\QuickSFV.exe | executable | |
MD5:4B1D5EC11B2B5DB046233A28DBA73B83 | SHA256:A6371461DA7439F4EF7008ED53331209747CBA960B85C70A902D46451247A29C | |||
| 8124 | powershell.exe | C:\Users\admin\Downloads\curver.ini | text | |
MD5:98995EA103B6D9384BDC22590C7FF2AF | SHA256:AE7062214D11FB30F4A56750478500107C3B8423D23EF8EA6B1EC84CFD720879 | |||
| 5228 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_vw0aag4c.emh.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 5756 | curl.exe | C:\Users\admin\Downloads\bin\motd.ps1 | text | |
MD5:BBDA74A620427266ABE74651AE10FBA0 | SHA256:F9E99F64BCFD05B80679E91A13267FFE051AA5C2D107AF1F4F0A946F7E0681B4 | |||
| 7396 | curl.exe | C:\Users\admin\Downloads\bin\folderbrowse.exe | executable | |
MD5:574AEC8F205BEEEB937E066B021A2673 | SHA256:DDBA12696F9543C83CAA99E420C9B9A012C4DBED2B1BE0D0952EAC09861605DD | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
63
DNS requests
27
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.32:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEH1bUSa0droR23QWC7xTDac%3D | unknown | — | — | whitelisted |
7604 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | unknown | — | — | whitelisted |
7604 | SIHClient.exe | GET | 200 | 2.16.253.202:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCEQDzZE5rbgBQI34JRr174fUd | unknown | — | — | whitelisted |
8108 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
756 | lsass.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTPlNxcMEqnlIVyH5VuZ4lawhZX3QQU9oUKOxGG4QR9DqoLLNLuzGR7e64CEQCrZoa1YnvoBZaCEzAShkn1 | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 2.16.164.32:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 40.126.32.74:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.23.77.188:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
8124 | powershell.exe | 140.82.121.5:443 | api.github.com | GITHUB | US | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1188 | curl.exe | 185.199.111.133:443 | raw.githubusercontent.com | FASTLY | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
api.github.com |
| whitelisted |
raw.githubusercontent.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |