| File name: | Purchase Order No. 141908.xlsx |
| Full analysis: | https://app.any.run/tasks/0d3babc4-b9e6-45c2-b8d2-2d8cd0c61004 |
| Verdict: | Malicious activity |
| Threats: | Trojans are a group of malicious programs distinguished by their ability to masquerade as benign software. Depending on their type, trojans possess a variety of capabilities, ranging from maintaining full remote control over the victim’s machine to stealing data and files, as well as dropping other malware. At the same time, the main functionality of each trojan family can differ significantly depending on its type. The most common trojan infection chain starts with a phishing email. |
| Analysis date: | October 05, 2022, 07:42:42 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.spreadsheetml.sheet |
| File info: | Microsoft Excel 2007+ |
| MD5: | 9171F153C2EE511B3EF50A16AE71BA98 |
| SHA1: | 80780B71F7C45F1BDE715FC0D7C8EFC8ACA0C53C |
| SHA256: | 9C155C61D7930D06C181947BAF3A2CAEAB788B34AE3C813E8C7254D254C6DDFF |
| SSDEEP: | 24576:sagcAgRs1/M2FuhpWjiBbAWjhKntSTavZhClrnIhmu3wlbWTHM33ZsZfWR0cKRkK:WcTs5jFGbAkhKtSTgSDIhMWD0mkrK |
MALICIOUS
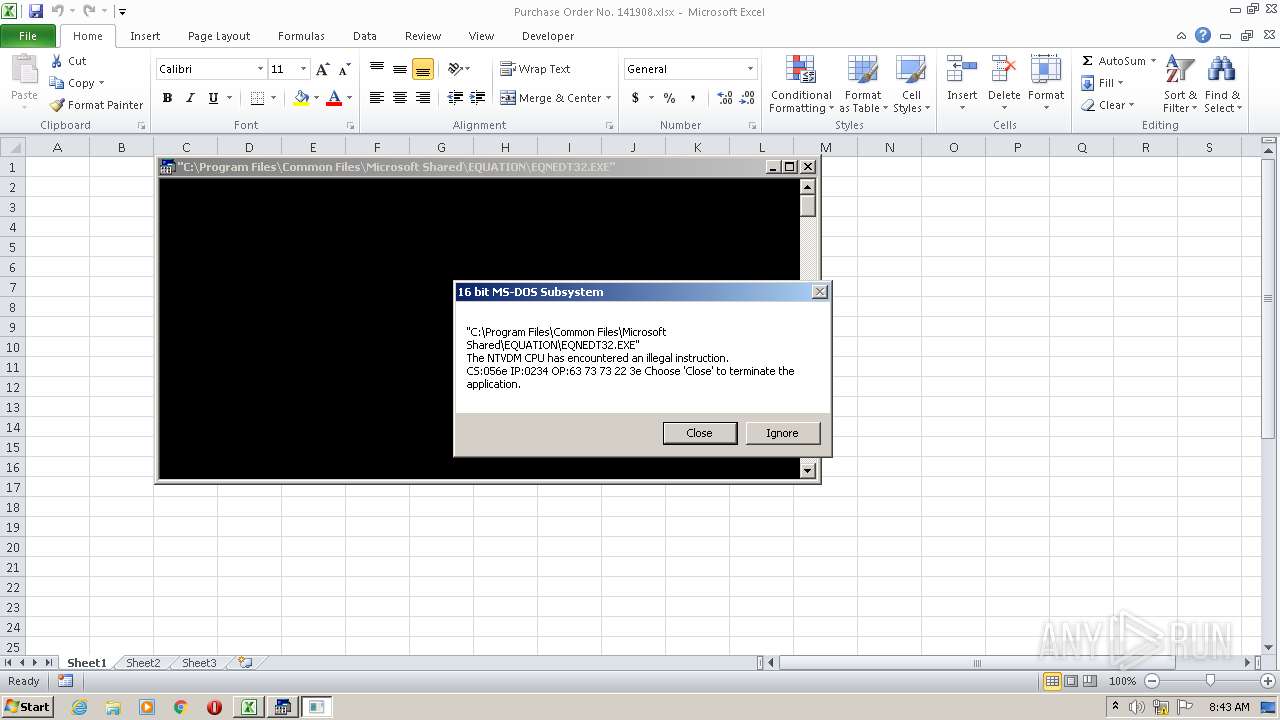
Equation Editor starts application (CVE-2017-11882)
- EQNEDT32.EXE (PID: 3952)
SUSPICIOUS
Reads Internet Settings
- EQNEDT32.EXE (PID: 3952)
- AdobeARM.exe (PID: 2932)
Reads the machine GUID from the registry
- EQNEDT32.EXE (PID: 3952)
- AdobeARM.exe (PID: 2932)
Process downloads binary or script
- EQNEDT32.EXE (PID: 3952)
Executes application which crashes
- EQNEDT32.EXE (PID: 3952)
Checks Windows Trust Settings
- AdobeARM.exe (PID: 2932)
Reads security settings of Internet Explorer
- AdobeARM.exe (PID: 2932)
Executable content was dropped or overwritten
- AdobeARM.exe (PID: 2932)
Reads settings of System Certificates
- AdobeARM.exe (PID: 2932)
INFO
Checks supported languages
- EQNEDT32.EXE (PID: 3952)
- AdobeARM.exe (PID: 2932)
- Reader_sl.exe (PID: 3696)
Reads the computer name
- EQNEDT32.EXE (PID: 3952)
- AdobeARM.exe (PID: 2932)
Process checks LSA protection
- EQNEDT32.EXE (PID: 3952)
- AdobeARM.exe (PID: 2932)
Creates files in the user directory
- EQNEDT32.EXE (PID: 3952)
- powershell.exe (PID: 1648)
- AdobeARM.exe (PID: 2932)
Manual execution by user
- cmd.exe (PID: 1704)
- AcroRd32.exe (PID: 2108)
Reads security settings of Internet Explorer
- powershell.exe (PID: 1648)
Reads the machine GUID from the registry
- powershell.exe (PID: 1648)
Checks Windows Trust Settings
- powershell.exe (PID: 1648)
Creates a file in a temporary directory
- powershell.exe (PID: 1648)
- AdobeARM.exe (PID: 2932)
Reads the hosts file
- RdrCEF.exe (PID: 1924)
Application launched itself
- RdrCEF.exe (PID: 1924)
- AcroRd32.exe (PID: 2108)
Drops the executable file immediately after the start
- RdrCEF.exe (PID: 1924)
Process checks are UAC notifies on
- AdobeARM.exe (PID: 2932)
Creates files in the program directory
- AdobeARM.exe (PID: 2932)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xlsx | | | Excel Microsoft Office Open XML Format document (61.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (31.5) |
| .zip | | | ZIP compressed archive (7.2) |
Total processes
57
Monitored processes
16
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1364 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1184,1014279364205962815,12138567421833564517,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7013359701608917522 --renderer-client-id=6 --mojo-platform-channel-handle=1264 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1648 | powershell | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 3221225786 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1704 | "C:\Windows\system32\cmd.exe" | C:\Windows\system32\cmd.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 1924 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --backgroundcolor=16514043 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2108 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | Explorer.EXE | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2352 | "C:\Windows\system32\ntvdm.exe" -i1 | C:\Windows\system32\ntvdm.exe | — | EQNEDT32.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 255 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2656 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1184,1014279364205962815,12138567421833564517,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9801099815976291907 --renderer-client-id=7 --mojo-platform-channel-handle=1612 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2800 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1184,1014279364205962815,12138567421833564517,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=9864249018776730205 --renderer-client-id=2 --mojo-platform-channel-handle=1192 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2932 | "C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe" /PRODUCT:Reader /VERSION:20.0 /MODE:3 | C:\Program Files\Common Files\Adobe\ARM\1.0\AdobeARM.exe | AcroRd32.exe | ||||||||||||
User: admin Company: Adobe Inc. Integrity Level: MEDIUM Description: Adobe Reader and Acrobat Manager Exit code: 0 Version: 1.824.39.9311 Modules
| |||||||||||||||
| 3168 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1184,1014279364205962815,12138567421833564517,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=6724426863414932915 --mojo-platform-channel-handle=1220 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
Total events
19 899
Read events
19 705
Write events
175
Delete events
19
Modification events
| (PID) Process: | (3540) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | p7? |
Value: 70373F00D40D0000010000000000000000000000 | |||
| (PID) Process: | (3540) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3540) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3540) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3540) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3540) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3540) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3540) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3540) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3540) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
Executable files
1
Suspicious files
131
Text files
10
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3540 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR5FD0.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3540 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\Purchase Order No. 141908.xlsx.LNK | lnk | |
MD5:— | SHA256:— | |||
| 3540 | EXCEL.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | ini | |
MD5:— | SHA256:— | |||
| 1924 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\2a426f11fd8ebe18_0 | binary | |
MD5:— | SHA256:— | |||
| 1924 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\560e9c8bff5008d8_0 | binary | |
MD5:— | SHA256:— | |||
| 1924 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\aba6710fde0876af_0 | binary | |
MD5:— | SHA256:— | |||
| 1924 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\72d9f526d2e2e7c8_0 | binary | |
MD5:— | SHA256:— | |||
| 1924 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\4a0e94571d979b3c_0 | binary | |
MD5:— | SHA256:— | |||
| 3952 | EQNEDT32.EXE | C:\Users\admin\AppData\Roaming\vga.exe | html | |
MD5:5343C1A8B203C162A3BF3870D9F50FD4 | SHA256:DC1D54DAB6EC8C00F70137927504E4F222C8395F10760B6BEECFCFA94E08249F | |||
| 1924 | RdrCEF.exe | C:\Users\admin\AppData\LocalLow\Adobe\AcroCef\DC\Acrobat\Cache\Code Cache\js\0786087c3c360803_0 | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
16
DNS requests
12
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2108 | AcroRd32.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAH9o%2BtuynXIiEOLckvPvJE%3D | US | der | 471 b | whitelisted |
3952 | EQNEDT32.EXE | GET | 404 | 43.245.183.172:80 | http://lutanedukasi.co.id/wp-includes/maxbndv4.4.1.exe | ID | html | 1.22 Kb | malicious |
2108 | AcroRd32.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?3d4dcfa9b3f8d459 | US | compressed | 4.70 Kb | whitelisted |
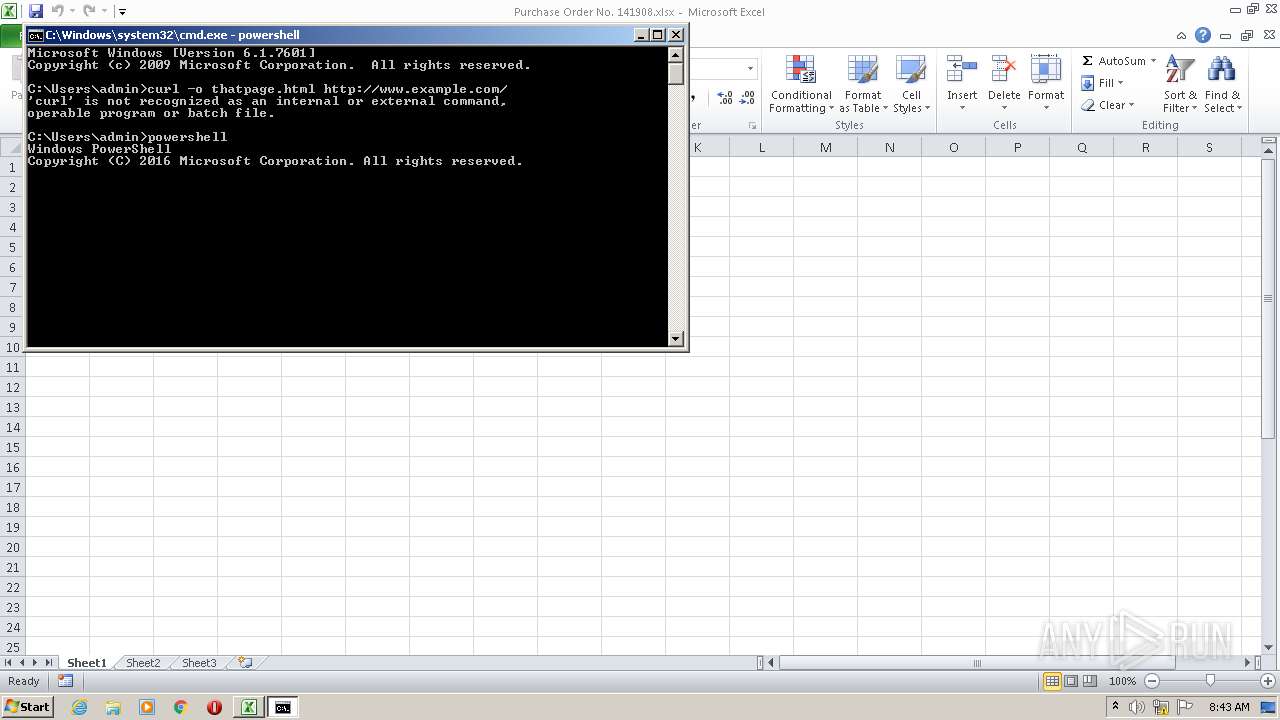
1648 | powershell.exe | GET | 200 | 93.184.216.34:80 | http://www.example.com/ | US | html | 1.23 Kb | whitelisted |
2108 | AcroRd32.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8f0b223941198bb1 | US | compressed | 4.70 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3952 | EQNEDT32.EXE | 43.245.183.172:80 | lutanedukasi.co.id | PT Infinys System Indonesia | ID | malicious |
1648 | powershell.exe | 93.184.216.34:80 | www.example.com | EDGECAST | US | whitelisted |
1924 | RdrCEF.exe | 23.35.236.137:443 | geo2.adobe.com | AKAMAI-AS | DE | suspicious |
— | — | 23.35.236.137:443 | geo2.adobe.com | AKAMAI-AS | DE | suspicious |
1924 | RdrCEF.exe | 18.207.85.246:443 | p13n.adobe.io | AMAZON-AES | US | suspicious |
808 | svchost.exe | 2.18.233.74:443 | armmf.adobe.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.48.23.39:443 | ardownload3.adobe.com | Akamai International B.V. | DE | suspicious |
2932 | AdobeARM.exe | 23.48.23.39:443 | ardownload3.adobe.com | Akamai International B.V. | DE | suspicious |
1924 | RdrCEF.exe | 2.18.233.74:443 | armmf.adobe.com | AKAMAI-AS | DE | whitelisted |
2108 | AcroRd32.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
lutanedukasi.co.id |
| malicious |
www.example.com |
| whitelisted |
geo2.adobe.com |
| whitelisted |
p13n.adobe.io |
| whitelisted |
armmf.adobe.com |
| whitelisted |
acroipm2.adobe.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
ardownload3.adobe.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3952 | EQNEDT32.EXE | A Network Trojan was detected | ET TROJAN EXE Download Request To Wordpress Folder Likely Malicious |
3952 | EQNEDT32.EXE | A Network Trojan was detected | AV TROJAN Possible infected Wordpress - Payload download attempt |
3952 | EQNEDT32.EXE | Potential Corporate Privacy Violation | AV POLICY HTTP request for .exe file with no User-Agent |
1648 | powershell.exe | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
808 | svchost.exe | Potentially Bad Traffic | ET INFO TLS Handshake Failure |