| File name: | 9c13ef91493296ed4f24f0dd83915556b8459e95cef08e7d1f7fc273e98a8f28 |
| Full analysis: | https://app.any.run/tasks/90b2e5dc-a4ed-4206-bfda-99d9127b2c51 |
| Verdict: | Malicious activity |
| Analysis date: | May 16, 2025, 15:28:47 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
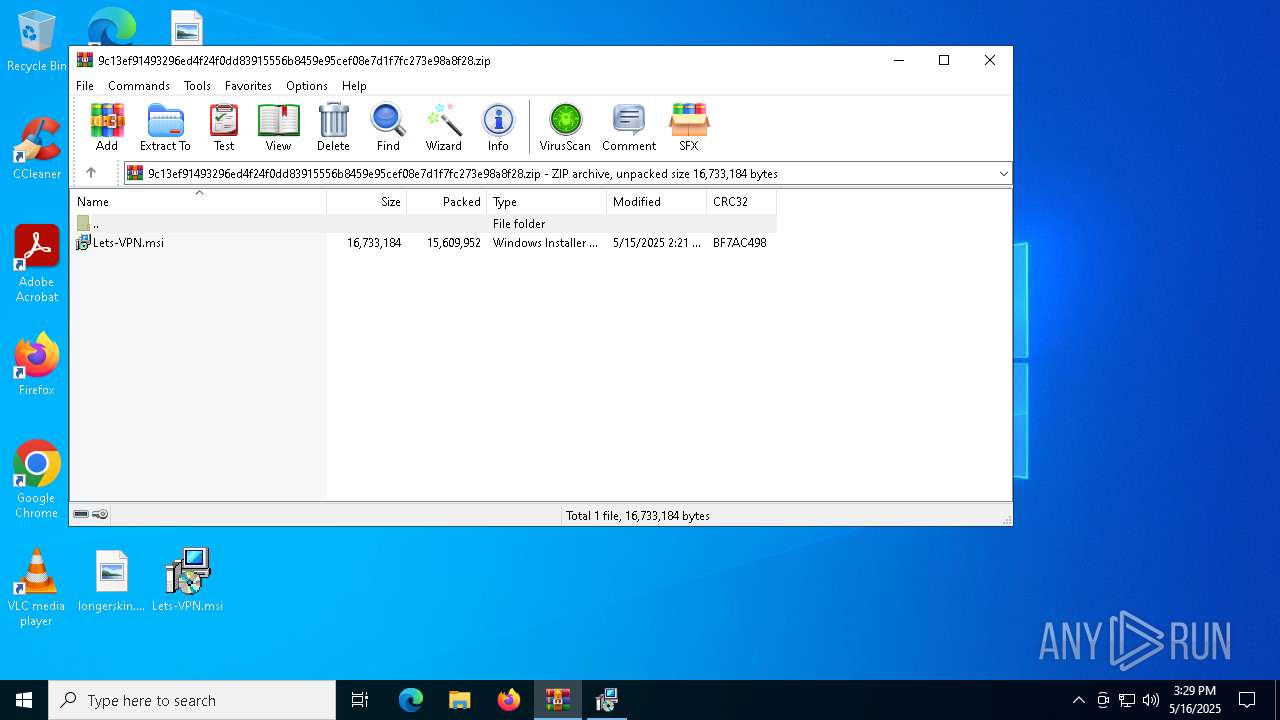
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 0085637E786F663D3A0025A28904BD2D |
| SHA1: | 065B0DD587FB13B33D2DFA4EAB616ED18392533F |
| SHA256: | 9C13EF91493296ED4F24F0DD83915556B8459E95CEF08E7D1F7FC273E98A8F28 |
| SSDEEP: | 98304:Bdz1ixJyX04HP6RFl5Rf/Adq6RJpRPIaaaU9nY7spKDWl9QeKXknVt+QX9Sm+d0+:2xa4Sp/SDjayBLQlNGUYWLhNNxr0ncH |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 616)
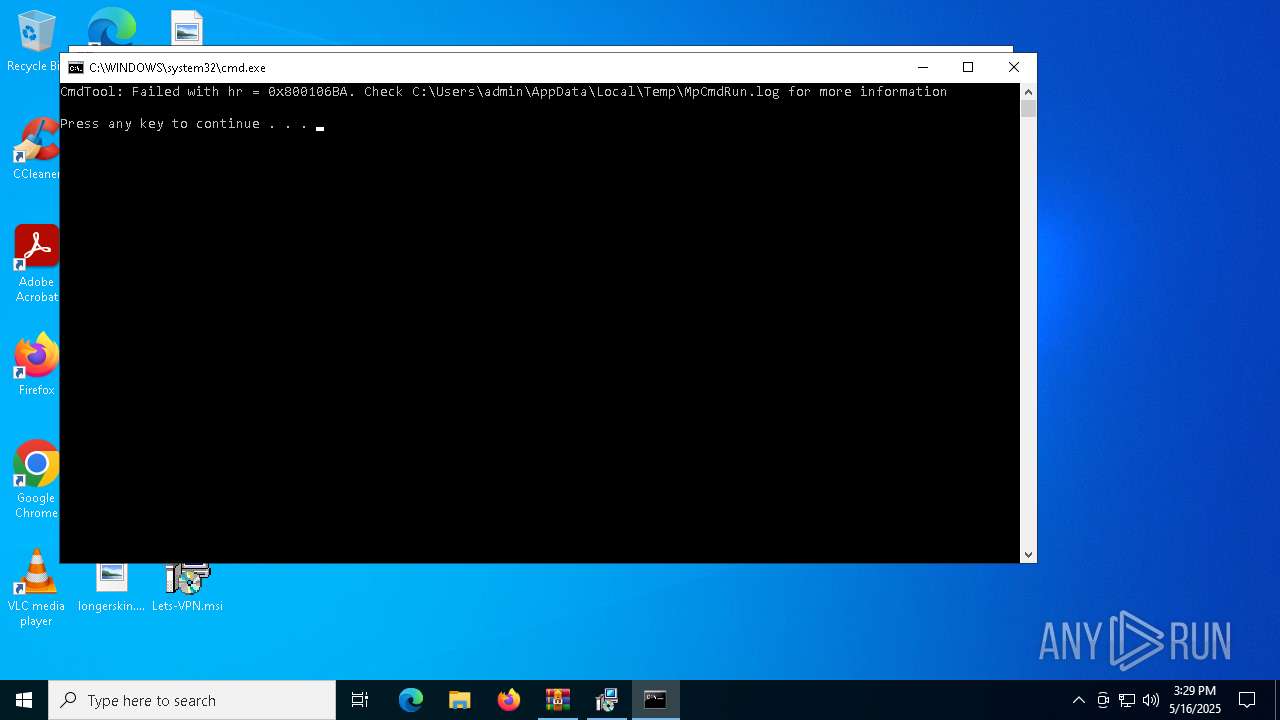
Changes Windows Defender settings
- cmd.exe (PID: 928)
Adds path to the Windows Defender exclusion list
- cmd.exe (PID: 928)
SUSPICIOUS
Detects AdvancedInstaller (YARA)
- msiexec.exe (PID: 728)
- msiexec.exe (PID: 3100)
Executes as Windows Service
- VSSVC.exe (PID: 6824)
Executing commands from a ".bat" file
- WinRAR.exe (PID: 616)
- msiexec.exe (PID: 3100)
- cmd.exe (PID: 668)
Starts CMD.EXE for commands execution
- WinRAR.exe (PID: 616)
- msiexec.exe (PID: 3100)
- cmd.exe (PID: 1748)
- cmd.exe (PID: 668)
Executing commands from ".cmd" file
- msiexec.exe (PID: 3100)
- cmd.exe (PID: 1748)
Application launched itself
- cmd.exe (PID: 1748)
- cmd.exe (PID: 668)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 928)
Uses NETSH.EXE to change the status of the firewall
- cmd.exe (PID: 3024)
Script adds exclusion path to Windows Defender
- cmd.exe (PID: 928)
Executable content was dropped or overwritten
- 1.exe (PID: 472)
Malware-specific behavior (creating "System.dll" in Temp)
- 1.exe (PID: 472)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 3024)
INFO
Manual execution by a user
- msiexec.exe (PID: 728)
Reads the computer name
- msiexec.exe (PID: 3100)
Checks supported languages
- msiexec.exe (PID: 3100)
Manages system restore points
- SrTasks.exe (PID: 6800)
Executable content was dropped or overwritten
- msiexec.exe (PID: 3100)
The sample compiled with english language support
- msiexec.exe (PID: 3100)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:05:15 22:21:48 |
| ZipCRC: | 0xbf7ac498 |
| ZipCompressedSize: | 15609952 |
| ZipUncompressedSize: | 16733184 |
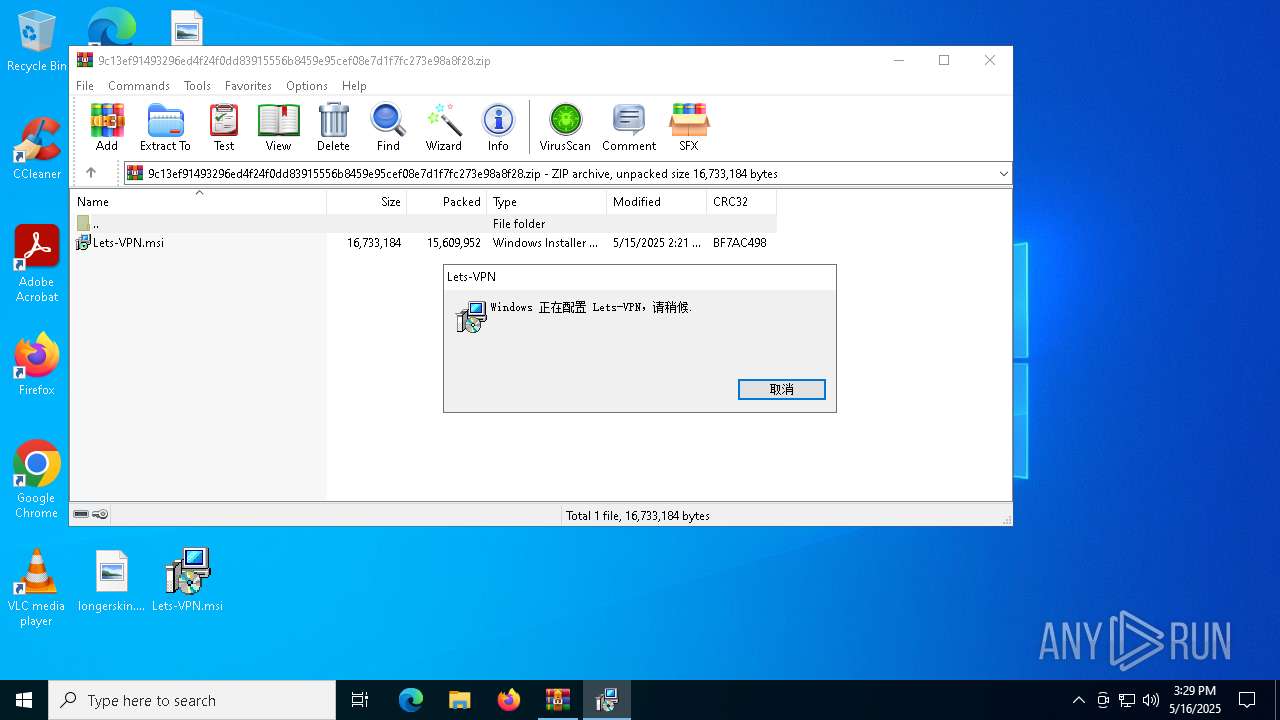
| ZipFileName: | Lets-VPN.msi |
Total processes
184
Monitored processes
53
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 472 | "C:\Program Files (x86)\Googgle\1.exe" | C:\Program Files (x86)\Googgle\1.exe | msiexec.exe | ||||||||||||
User: admin Company: Letsgo Network Incorporated Integrity Level: MEDIUM Description: LetsVPN Setup EXE Version: 3.14.3.0 Modules
| |||||||||||||||
| 616 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\9c13ef91493296ed4f24f0dd83915556b8459e95cef08e7d1f7fc273e98a8f28.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 632 | netsh advfirewall firewall add rule name="TCP_1080" dir=out action=block protocol=TCP remoteport=1080 | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 668 | C:\WINDOWS\system32\cmd.exe /c ""C:\ProgramData\Updatte\dfdfdfd42q3re.bat"" | C:\Windows\System32\cmd.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\Desktop\Lets-VPN.msi | C:\Windows\System32\msiexec.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 840 | netsh advfirewall firewall add rule name="TCP_6666" dir=out action=block protocol=TCP remoteport=6666 | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 840 | netsh advfirewall firewall add rule name="TCP_4433" dir=out action=block protocol=TCP remoteport=4433 | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 840 | netsh advfirewall firewall add rule name="TCP_13280" dir=out action=block protocol=TCP remoteport=13280 | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 896 | "C:\Program Files\Windows Defender\MpCmdRun.exe" -Scan -ScanType 3 -File "C:\Users\admin\AppData\Local\Temp\Rar$VR616.18478" | C:\Program Files\Windows Defender\MpCmdRun.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Malware Protection Command Line Utility Exit code: 2 Version: 4.18.1909.6 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 904 | netsh advfirewall firewall add rule name="TCP_6067" dir=out action=block protocol=TCP remoteport=6067 | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
23 580
Read events
23 360
Write events
203
Delete events
17
Modification events
| (PID) Process: | (3100) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 48000000000000008149C34677C6DB011C0C000068100000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3100) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000CFD7C74677C6DB011C0C000068100000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\9c13ef91493296ed4f24f0dd83915556b8459e95cef08e7d1f7fc273e98a8f28.zip | |||
| (PID) Process: | (616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (616) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
15
Suspicious files
19
Text files
7
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 616 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR616.18478\9c13ef91493296ed4f24f0dd83915556b8459e95cef08e7d1f7fc273e98a8f28.zip\Lets-VPN.msi | — | |
MD5:— | SHA256:— | |||
| 3100 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 3100 | msiexec.exe | C:\Windows\Installer\119075.msi | — | |
MD5:— | SHA256:— | |||
| 3100 | msiexec.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:59F3F59B1DD6D1E50F62831FC8D0D876 | SHA256:83C6BD56257FB0A14C05F7DF6CA4F03B745DD3AB3A53F7B50416F6FADF554302 | |||
| 3100 | msiexec.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{b59cd518-c351-4b16-b03b-ebb0361afc6e}_OnDiskSnapshotProp | binary | |
MD5:59F3F59B1DD6D1E50F62831FC8D0D876 | SHA256:83C6BD56257FB0A14C05F7DF6CA4F03B745DD3AB3A53F7B50416F6FADF554302 | |||
| 3100 | msiexec.exe | C:\Windows\Installer\MSI9A2D.tmp | executable | |
MD5:89F70B588A48793450DD603B6CD4096F | SHA256:066C52ED8EBF63A33AB8290B7C58D0C13F79C14FAA8BF12B1B41F643D3EBE281 | |||
| 3100 | msiexec.exe | C:\Windows\Installer\MSI9E27.tmp | executable | |
MD5:14C0948E2BB94C5F263CC8B107EB728B | SHA256:EE42C70ED98EF30A312BA31A4E2C30D400BFBA3419F6FD3409D1857D73F804A9 | |||
| 3100 | msiexec.exe | C:\Windows\Installer\MSI9BC4.tmp | executable | |
MD5:89F70B588A48793450DD603B6CD4096F | SHA256:066C52ED8EBF63A33AB8290B7C58D0C13F79C14FAA8BF12B1B41F643D3EBE281 | |||
| 616 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$VR616.18478\Rar$Scan29858.bat | text | |
MD5:7B47A0A79E866036BB2A581202720676 | SHA256:38E5C6275DB234FB2475B14B161CB773B29336065C79867A5C8BB976778A4EF5 | |||
| 3100 | msiexec.exe | C:\Windows\Installer\MSI99BE.tmp | executable | |
MD5:89F70B588A48793450DD603B6CD4096F | SHA256:066C52ED8EBF63A33AB8290B7C58D0C13F79C14FAA8BF12B1B41F643D3EBE281 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
55
DNS requests
16
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5364 | SIHClient.exe | GET | 200 | 23.216.77.26:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5364 | SIHClient.exe | GET | 200 | 23.216.77.26:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut_2010-06-23.crl | unknown | — | — | whitelisted |
5364 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5364 | SIHClient.exe | GET | 200 | 23.216.77.26:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
5364 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
5364 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
5364 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
5364 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.2.crl | unknown | — | — | whitelisted |
2920 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6544 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 172.211.123.249:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | FR | unknown |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | FR | unknown |
6708 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5776 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5364 | SIHClient.exe | 4.245.163.56:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
yh1.ksdcks2.org |
| unknown |
nexusrules.officeapps.live.com |
| whitelisted |