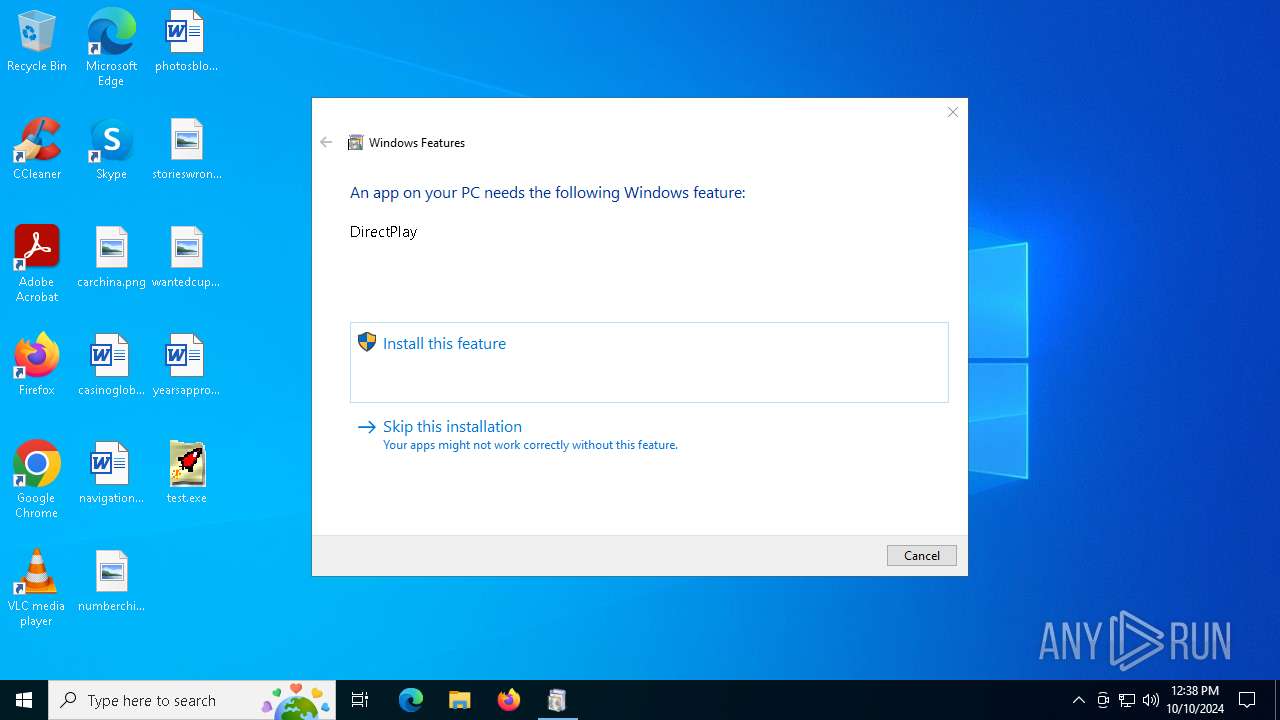
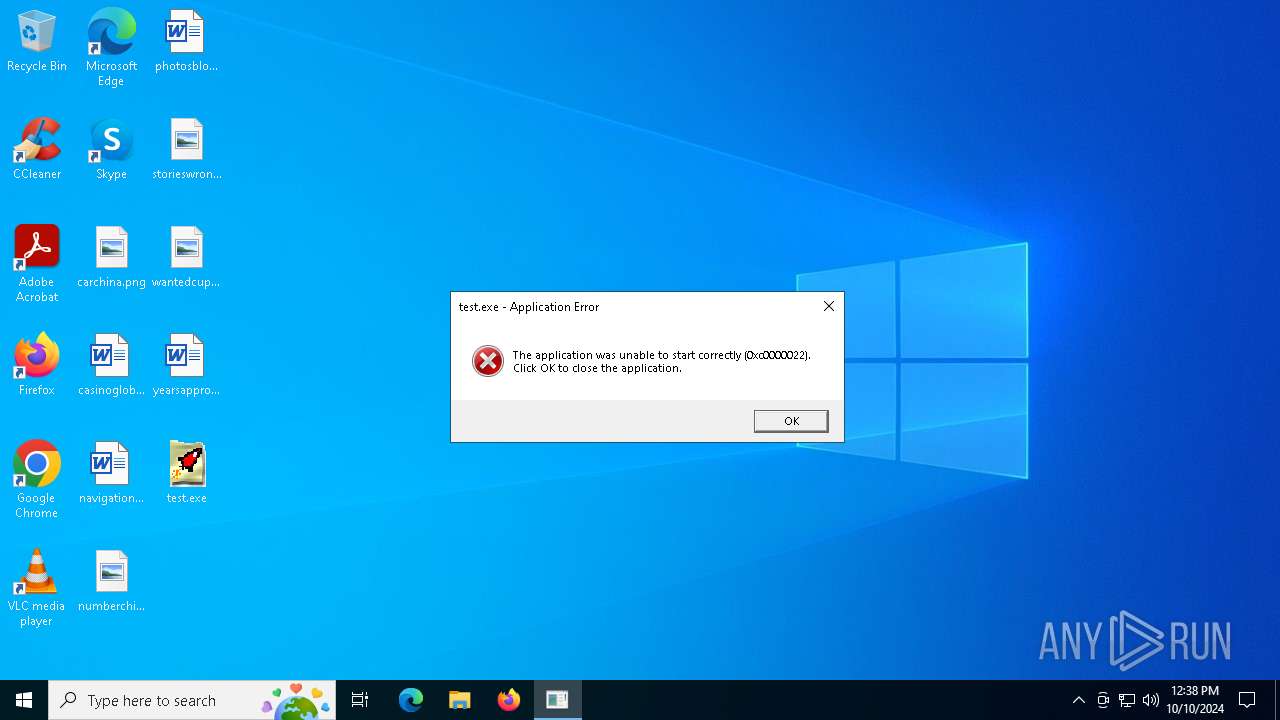
| File name: | test.exe |
| Full analysis: | https://app.any.run/tasks/43fd3e5b-5023-46dc-ba9e-0fee235cf440 |
| Verdict: | Malicious activity |
| Analysis date: | October 10, 2024, 12:37:53 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | FF4703EF138C31258B2802BF1D9F8C05 |
| SHA1: | DF653A2A6330C791EF53654CCF82631105C29BEE |
| SHA256: | 9C0519F8B48C08570CFEE7CFEE0CBC8A934AEF58A98FA6CE986BC30B545E085A |
| SSDEEP: | 49152:oVZJMnZCnYYAJO8aHN3BfPqnjHa4I9nXdu/PIsHQKRJhiufU3J+gmFZC:oVZunZC0JO8aHhkTM9nXdqgswKJi2U3g |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- TiWorker.exe (PID: 1160)
Process drops legitimate windows executable
- TiWorker.exe (PID: 1160)
Executes as Windows Service
- VSSVC.exe (PID: 2888)
INFO
Manual execution by a user
- test.exe (PID: 1452)
Manages system restore points
- SrTasks.exe (PID: 6820)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (64.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.4) |
| .exe | | | Win32 Executable (generic) (10.5) |
| .exe | | | Generic Win/DOS Executable (4.6) |
| .exe | | | DOS Executable Generic (4.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2014:02:26 02:05:15+00:00 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 1064960 |
| InitializedDataSize: | 528384 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x14c7 |
| OSVersion: | 4 |
| ImageVersion: | - |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
Total processes
146
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1160 | C:\WINDOWS\winsxs\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe -Embedding | C:\Windows\WinSxS\amd64_microsoft-windows-servicingstack_31bf3856ad364e35_10.0.19041.3989_none_7ddb45627cb30e03\TiWorker.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Modules Installer Worker Version: 10.0.19041.3989 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1452 | "C:\Users\admin\Desktop\test.exe" | C:\Users\admin\Desktop\test.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2888 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5892 | "C:\Users\admin\Desktop\test.exe" | C:\Users\admin\Desktop\test.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221225506 Modules
| |||||||||||||||
| 6820 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | TiWorker.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7052 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
27 341
Read events
26 878
Write events
381
Delete events
82
Modification events
| (PID) Process: | (1160) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdHigh |
Value: 31136529 | |||
| (PID) Process: | (1160) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | SessionIdLow |
Value: | |||
| (PID) Process: | (1160) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS\ServicingStackVersions |
| Operation: | write | Name: | 10.0.19041.3989 (WinBuild.160101.0800) |
Value: 2024/10/10:12:38:31.951 10.0.19041.3989 (WinBuild.160101.0800) | |||
| (PID) Process: | (1160) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS |
| Operation: | delete value | Name: | PendingRequired |
Value: | |||
| (PID) Process: | (1160) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS |
| Operation: | delete value | Name: | PendingXmlIdentifier |
Value: | |||
| (PID) Process: | (1160) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS |
| Operation: | delete value | Name: | PoqexecFailure |
Value: | |||
| (PID) Process: | (1160) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS |
| Operation: | delete value | Name: | ExecutionState |
Value: | |||
| (PID) Process: | (1160) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\COMPONENTS |
| Operation: | delete value | Name: | RepairTransactionPended |
Value: | |||
| (PID) Process: | (1160) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | DoqTime |
Value: 0 | |||
| (PID) Process: | (1160) TiWorker.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Component Based Servicing |
| Operation: | write | Name: | DoqCount |
Value: 0 | |||
Executable files
42
Suspicious files
35
Text files
14
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1160 | TiWorker.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 1160 | TiWorker.exe | C:\Windows\servicing\Sessions\31136529_1334019411.xml | xml | |
MD5:561CA1D56DF00B9F2EFDD1D016628854 | SHA256:074DB964CFE284FB14C922CD26162E6131E7AC80AF4BE319F54FD81DB94B49E1 | |||
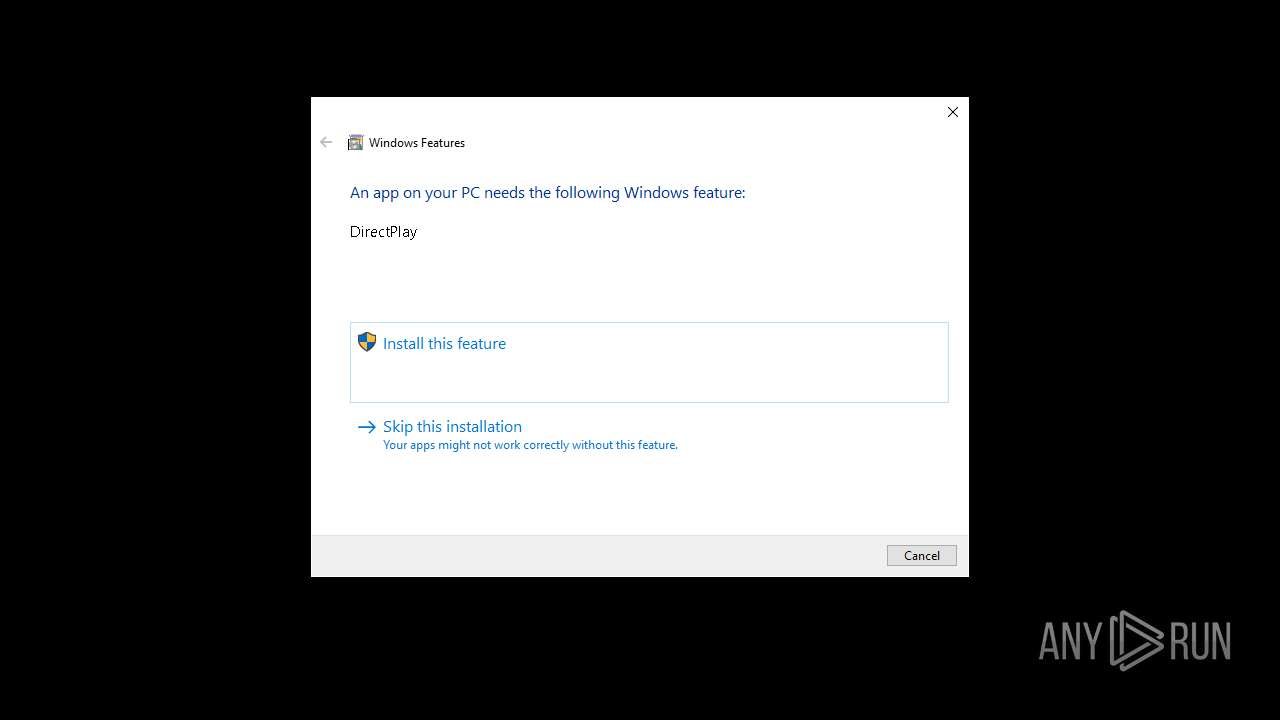
| 1160 | TiWorker.exe | C:\Windows\WinSxS\Temp\InFlight\20178f5d111bdb01110000008804a819\x86_microsoft-windows-d..directplay4-payload_31bf3856ad364e35_10.0.19041.1_none_ba3fa9706f28b589\dpwsockx.dll | executable | |
MD5:152786505316BF34B54D68F3731C62AE | SHA256:48D98E0F6F3854AD1CE9955E2FDD6719C3D57AB9C951FD0B707C701EEF8AA7F4 | |||
| 1160 | TiWorker.exe | C:\System Volume Information\SPP\OnlineMetadataCache\{5d000297-24e2-4161-9f4d-f20ec31cc8f6}_OnDiskSnapshotProp | binary | |
MD5:8929E13A0B75D91E6F9DB946AB5BE9BB | SHA256:E1BB39E2200B9CA45E9B6CC8A369B9849FB0304E96D8B15497D73CEEC1A202EF | |||
| 1160 | TiWorker.exe | C:\Windows\WinSxS\Temp\InFlight\20178f5d111bdb01110000008804a819\x86_microsoft-windows-d..directplay4-payload_31bf3856ad364e35_10.0.19041.1_none_ba3fa9706f28b589\dplaysvr.exe | executable | |
MD5:F825C2679BB5177E015FD3F0133B7788 | SHA256:EBC69C1285014C40D286ABFAC9CB3CE18B99B422AA9A30B56313C9CA7E1E8804 | |||
| 1160 | TiWorker.exe | C:\Windows\WinSxS\Temp\InFlight\20178f5d111bdb01110000008804a819\x86_microsoft-windows-d..directplay4-payload_31bf3856ad364e35_10.0.19041.1_none_ba3fa9706f28b589\dplayx.dll | executable | |
MD5:27D86453433108C3E1DF2EC84F8B3758 | SHA256:32C9CA064999D8A87CAB3EE4AA2D9566278D254326A7EFAED8D33E6A44170759 | |||
| 1160 | TiWorker.exe | C:\Windows\WinSxS\Temp\InFlight\20178f5d111bdb01110000008804a819\x86_microsoft-windows-d..directplay4-payload_31bf3856ad364e35_10.0.19041.1_none_ba3fa9706f28b589\dpmodemx.dll | executable | |
MD5:CDE67309989D9E0944501F71A690DA95 | SHA256:4482FDFA30C60A6FF68DAB91B3DD340A16990A7BCE04A4D11481B09BB6BD796E | |||
| 1160 | TiWorker.exe | C:\Windows\WinSxS\Temp\PendingDeletes\b42e965d111bdb01120000008804a819.dplaysvr.exe | binary | |
MD5:00AF941460A4DDBC9EE252B33713E94E | SHA256:5303EF7D0F6F248B1CD3F3569D547E25B4A5238B2D3CDFFC4424106C9851EF1D | |||
| 1160 | TiWorker.exe | C:\Windows\WinSxS\Temp\PendingDeletes\b42e965d111bdb01130000008804a819.dplayx.dll | binary | |
MD5:67F6E60F724E64263537288C3498A8F6 | SHA256:BC0AA84E7381824399A62A68F8E1CEC8DD44E3152CB80CC668BD46C5661D6AE0 | |||
| 1160 | TiWorker.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:8929E13A0B75D91E6F9DB946AB5BE9BB | SHA256:E1BB39E2200B9CA45E9B6CC8A369B9849FB0304E96D8B15497D73CEEC1A202EF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
60
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4360 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
624 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5524 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6804 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
5524 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
7060 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5488 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6944 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6944 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6944 | svchost.exe | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
6944 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4360 | SearchApp.exe | 92.123.104.63:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4360 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |