| download: | index.html |
| Full analysis: | https://app.any.run/tasks/635e7bc3-9252-474e-9b43-de60c66e14f6 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2019, 13:06:44 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, ASCII text, with very long lines, with CRLF, LF line terminators |
| MD5: | 0ACA717C0A0993368212980E9213543C |
| SHA1: | C5562AAA1E01DCA1A101C30DFCAA2DD213D520E7 |
| SHA256: | 9BF2BA1CB4B52E57682E149A7F7B6E5501ACC1A40654996A9672A52CF78D4541 |
| SSDEEP: | 1536:+qC307J5Q0sVtNbkfq5D723FUhQT/bIrUOwhR60h7vbt2uOAmYEzseVdk0OU5vXt:+Hky0+Ngfq5D723F/wI4zt |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Changes internet zones settings
- iexplore.exe (PID: 3604)
Application launched itself
- iexplore.exe (PID: 3604)
Creates files in the user directory
- iexplore.exe (PID: 3248)
- iexplore.exe (PID: 2896)
- FlashUtil32_26_0_0_131_ActiveX.exe (PID: 3680)
- iexplore.exe (PID: 3604)
Reads internet explorer settings
- iexplore.exe (PID: 3248)
- iexplore.exe (PID: 2896)
Reads Internet Cache Settings
- iexplore.exe (PID: 3248)
- iexplore.exe (PID: 3604)
- iexplore.exe (PID: 2896)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3604)
Changes settings of System certificates
- iexplore.exe (PID: 3604)
Reads settings of System Certificates
- iexplore.exe (PID: 3604)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .aiml | | | Artificial Intelligence Markup Language (48.3) |
|---|---|---|
| .htm/html | | | HyperText Markup Language with DOCTYPE (41.6) |
| .html | | | HyperText Markup Language (9.9) |
EXIF
HTML
| HTTPEquivXUACompatible: | IE=edge,chrome=1 |
|---|---|
| viewport: | width=device-width |
| formatDetection: | telephone=no |
| referrer: | origin-when-cross-origin |
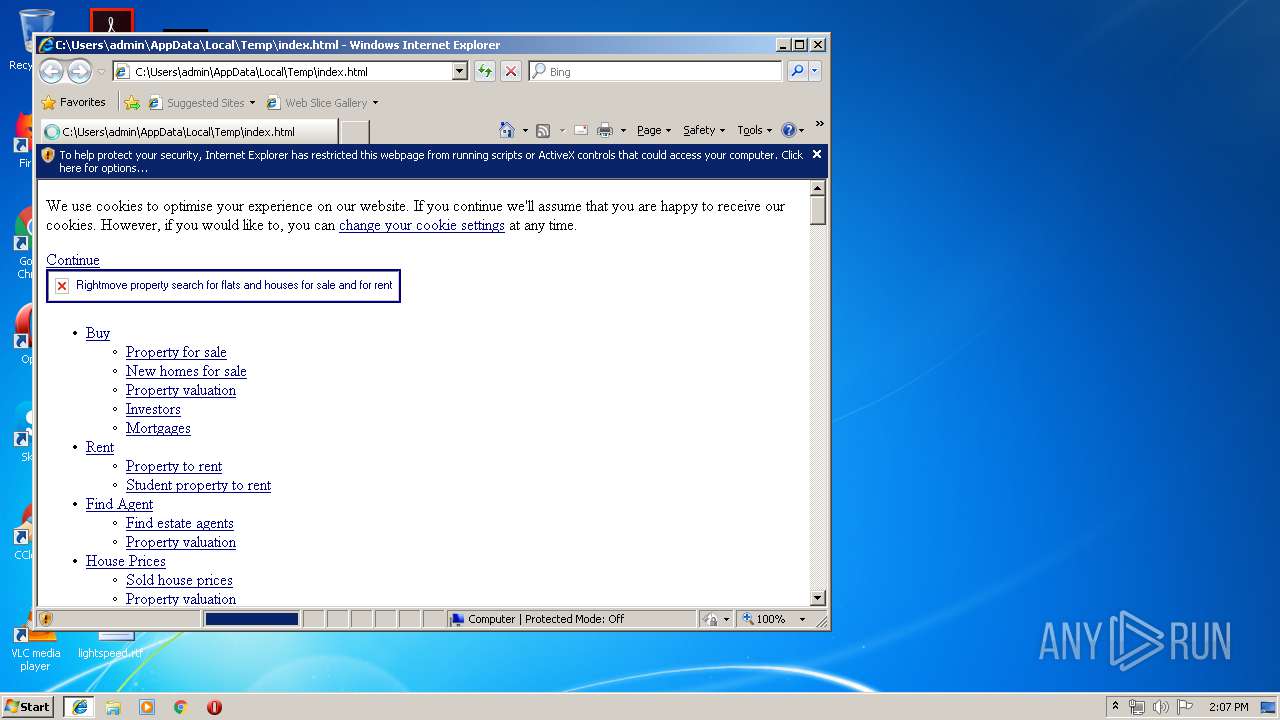
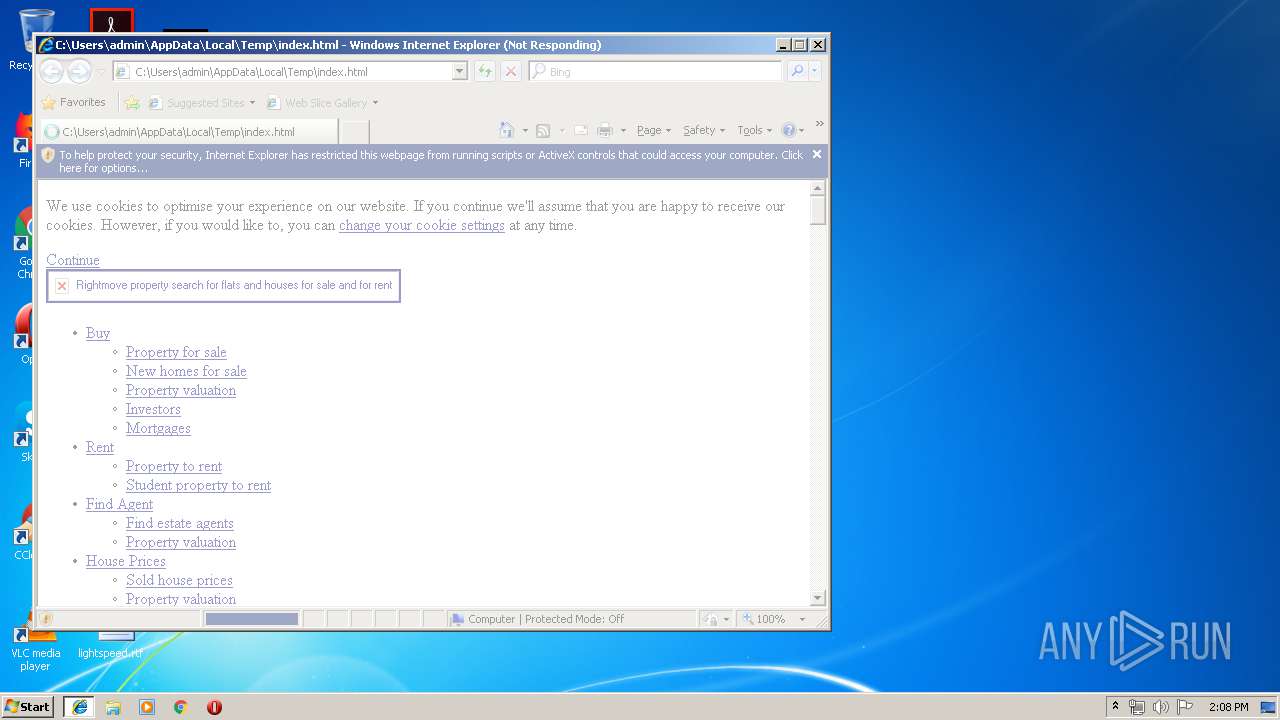
| Title: | Rightmove - UK's number one property website for properties for sale and to rent |
| Description: | Search over a Million properties for sale and to rent from the top estate agents and developers in the UK - Rightmove. |
| Robots: | NOODP |
| verifyV1: | LUZdEr1PhXT72UfkdqB1ojk22rBaaY76kxRzJhHceFI= |
| msvalidate01: | A80A4714497C87913B3B8716391153C7 |
| googleSiteVerification: | DrdmvokP07R4_MNoWI2jQb_ZVjjffXVpFV8E_wEiDk0 |
| appleMobileWebAppTitle: | Rightmove |
| applicationName: | Rightmove |
| themeColor: | #262637 |
| msapplicationTileColor: | #262637 |
| msapplicationTileImage: | /ps/images/favicons/mstile-144x144.png |
| msapplicationConfig: | /ps/images/favicons/browserconfig.xml |
| slice: | off |
| appleItunesApp: | app-id=323822803, affiliate-data=at=11lqxx&ct=smartbanner |
Total processes
40
Monitored processes
4
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2896 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3604 CREDAT:203009 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3248 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3604 CREDAT:79873 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3604 | "C:\Program Files\Internet Explorer\iexplore.exe" C:\Users\admin\AppData\Local\Temp\index.html | C:\Program Files\Internet Explorer\iexplore.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3680 | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe -Embedding | C:\Windows\system32\Macromed\Flash\FlashUtil32_26_0_0_131_ActiveX.exe | — | svchost.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe® Flash® Player Installer/Uninstaller 26.0 r0 Exit code: 0 Version: 26,0,0,131 Modules
| |||||||||||||||
Total events
718
Read events
599
Write events
115
Delete events
4
Modification events
| (PID) Process: | (3604) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3604) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3604) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3604) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (3604) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3604) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000071000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3604) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Recovery\Active |
| Operation: | write | Name: | {52688DF5-7712-11E9-A370-5254004A04AF} |
Value: 0 | |||
| (PID) Process: | (3604) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Type |
Value: 4 | |||
| (PID) Process: | (3604) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Count |
Value: 1 | |||
| (PID) Process: | (3604) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Ext\Stats\{2670000A-7350-4F3C-8081-5663EE0C6C49}\iexplore |
| Operation: | write | Name: | Time |
Value: E307050003000F000D00070000005A01 | |||
Executable files
0
Suspicious files
1
Text files
92
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3604 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\I0488CJO\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3604 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 3248 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\History.IE5\MSHist012019051520190516\index.dat | dat | |
MD5:— | SHA256:— | |||
| 3248 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\errorPageStrings[1] | text | |
MD5:1A0563F7FB85A678771450B131ED66FD | SHA256:EB5678DE9D8F29CA6893D4E6CA79BD5AB4F312813820FE4997B009A2B1A1654C | |||
| 3248 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\dnserror[1] | html | |
MD5:68E03ED57EC741A4AFBBCD11FAB1BDBE | SHA256:1FF3334C3EB27033F8F37029FD72F648EDD4551FCE85FC1F5159FEAEA1439630 | |||
| 3248 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\JGRR2OYX\down[1] | image | |
MD5:555E83CE7F5D280D7454AF334571FB25 | SHA256:70F316A5492848BB8242D49539468830B353DDAA850964DB4E60A6D2D7DB4880 | |||
| 3248 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\noConnect[1] | image | |
MD5:3CB8FACCD5DE434D415AB75C17E8FD86 | SHA256:6976C426E3AC66D66303C114B22B2B41109A7DE648BA55FFC3E5A53BD0DB09E7 | |||
| 3248 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\httpErrorPagesScripts[1] | text | |
MD5:E7CA76A3C9EE0564471671D500E3F0F3 | SHA256:58268CA71A28973B756A48BBD7C9DC2F6B87B62AE343E582CE067C725275B63C | |||
| 3248 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favcenter[1] | image | |
MD5:25D76EE5FB5B890F2CC022D94A42FE19 | SHA256:07D07A467E4988D3C377ACD6DC9E53ABCA6B64E8FBF70F6BE19D795A1619289B | |||
| 3248 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\H6QNMHE9\ErrorPageTemplate[1] | text | |
MD5:F4FE1CB77E758E1BA56B8A8EC20417C5 | SHA256:8D018639281B33DA8EB3CE0B21D11E1D414E59024C3689F92BE8904EB5779B5F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
83
DNS requests
26
Threats
20
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3248 | iexplore.exe | OPTIONS | — | 172.217.22.40:80 | http://www.googletagmanager.com/ | US | — | — | whitelisted |
3248 | iexplore.exe | OPTIONS | 400 | 172.217.22.40:80 | http://www.googletagmanager.com/ | US | html | 1.52 Kb | whitelisted |
3248 | iexplore.exe | OPTIONS | 400 | 172.217.22.40:80 | http://www.googletagmanager.com/ | US | html | 1.52 Kb | whitelisted |
3248 | iexplore.exe | OPTIONS | 400 | 172.217.22.40:80 | http://www.googletagmanager.com/ | US | html | 1.52 Kb | whitelisted |
3248 | iexplore.exe | OPTIONS | 400 | 172.217.22.40:80 | http://www.googletagmanager.com/ | US | html | 1.52 Kb | whitelisted |
— | — | OPTIONS | 400 | 172.217.22.40:80 | http://www.googletagmanager.com/ | US | html | 1.52 Kb | whitelisted |
3248 | iexplore.exe | OPTIONS | 400 | 172.217.22.40:80 | http://www.googletagmanager.com/ | US | html | 1.52 Kb | whitelisted |
3248 | iexplore.exe | OPTIONS | 400 | 172.217.22.40:80 | http://www.googletagmanager.com/ | US | html | 1.52 Kb | whitelisted |
3248 | iexplore.exe | OPTIONS | 400 | 172.217.22.40:80 | http://www.googletagmanager.com/ | US | html | 1.52 Kb | whitelisted |
3248 | iexplore.exe | OPTIONS | 400 | 172.217.22.40:80 | http://www.googletagmanager.com/ | US | html | 1.52 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 172.217.22.40:445 | www.googletagmanager.com | Google Inc. | US | whitelisted |
3248 | iexplore.exe | 172.217.22.40:80 | www.googletagmanager.com | Google Inc. | US | whitelisted |
4 | System | 172.217.22.40:139 | www.googletagmanager.com | Google Inc. | US | whitelisted |
— | — | 151.101.120.70:443 | media.rightmove.co.uk | Fastly | US | unknown |
3248 | iexplore.exe | 151.101.120.70:443 | media.rightmove.co.uk | Fastly | US | unknown |
4 | System | 172.217.21.194:445 | googleads.g.doubleclick.net | Google Inc. | US | whitelisted |
4 | System | 172.217.21.194:139 | googleads.g.doubleclick.net | Google Inc. | US | whitelisted |
2896 | iexplore.exe | 104.18.46.154:443 | www.blogderocha.com.br | Cloudflare Inc | US | shared |
2896 | iexplore.exe | 172.217.18.3:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
2896 | iexplore.exe | 104.18.46.154:80 | www.blogderocha.com.br | Cloudflare Inc | US | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.googletagmanager.com |
| whitelisted |
media.rightmove.co.uk |
| malicious |
googleads.g.doubleclick.net |
| whitelisted |
www.bing.com |
| whitelisted |
www.blogderocha.com.br |
| unknown |
fonts.googleapis.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
wordpress.com |
| whitelisted |
connect.facebook.net |
| whitelisted |
secure.gravatar.com |
| whitelisted |
Threats
20 ETPRO signatures available at the full report