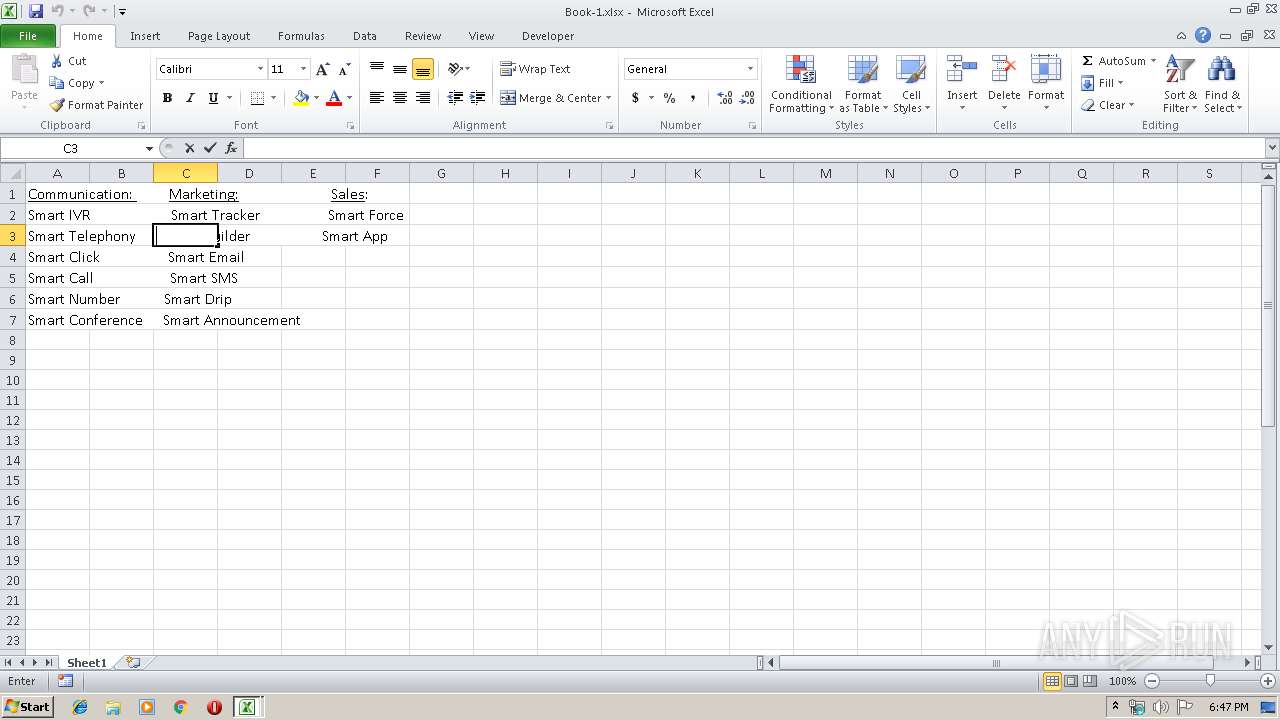
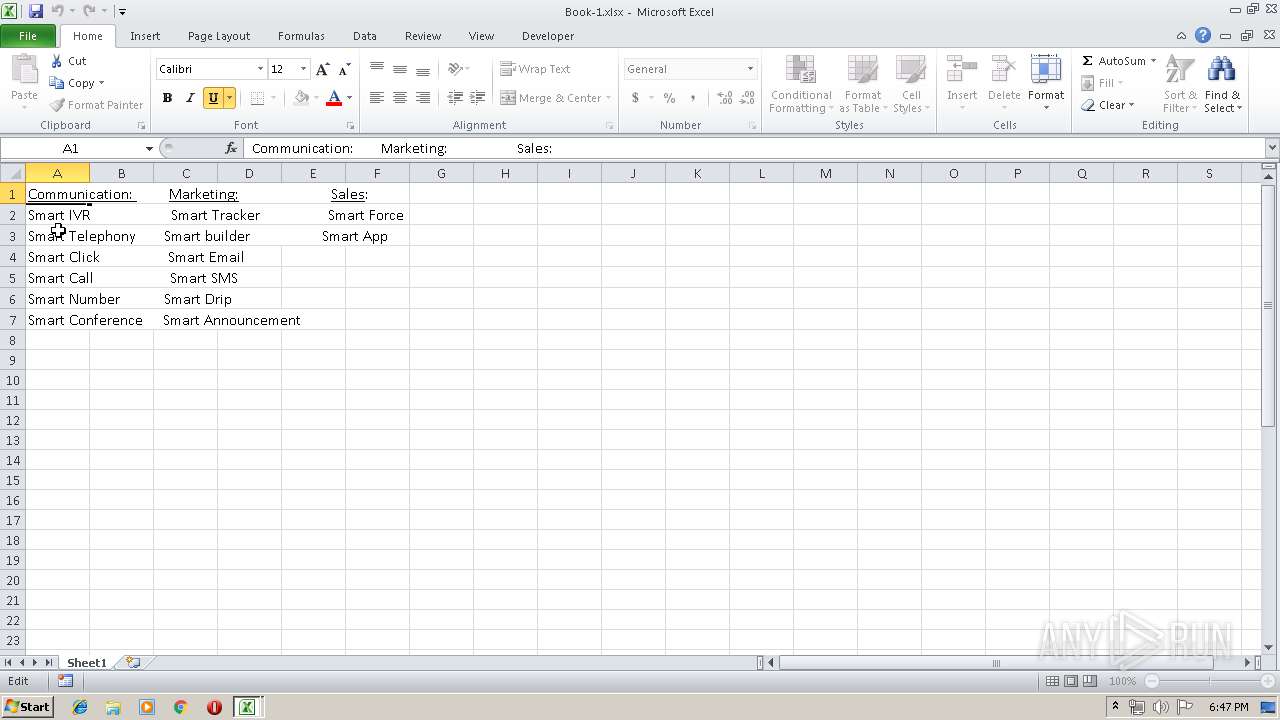
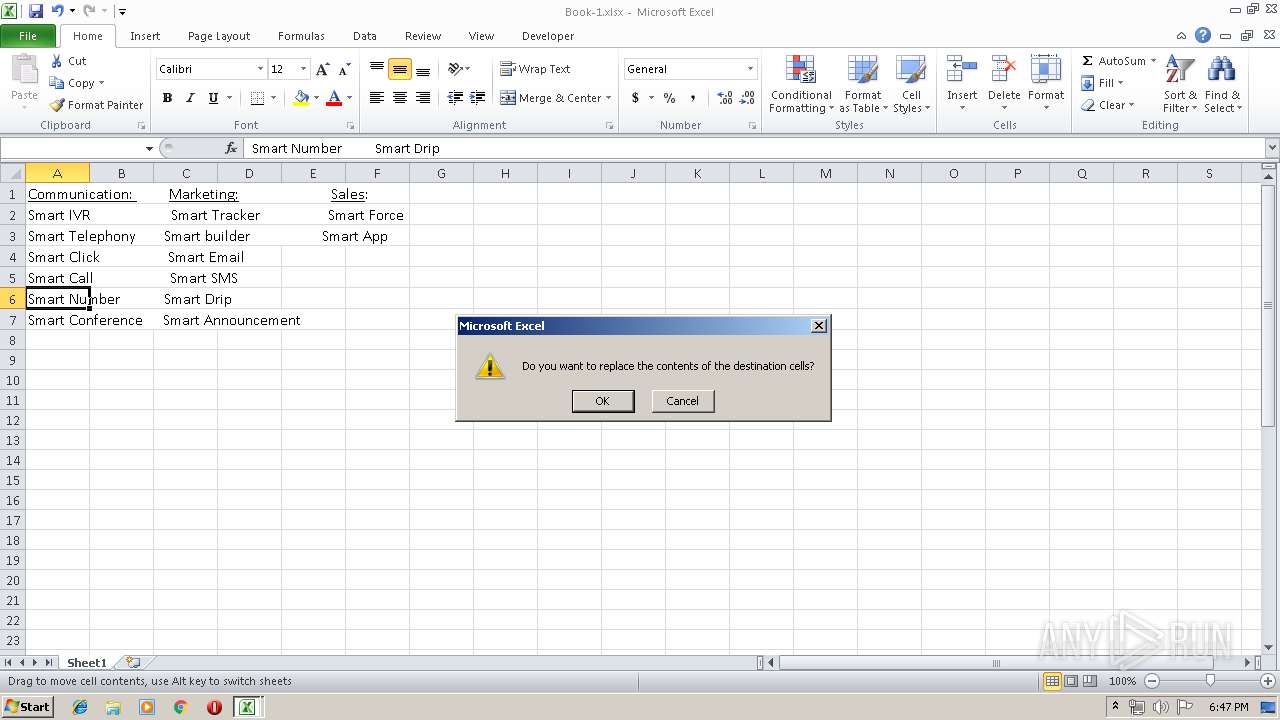
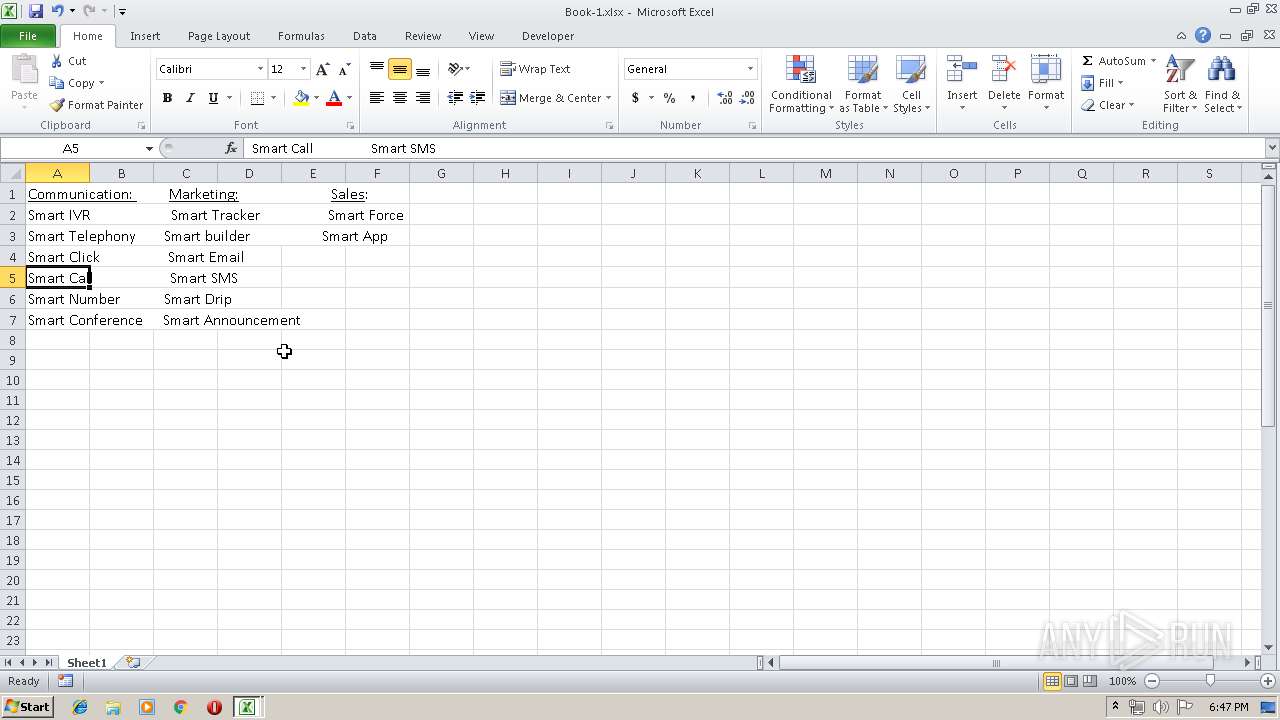
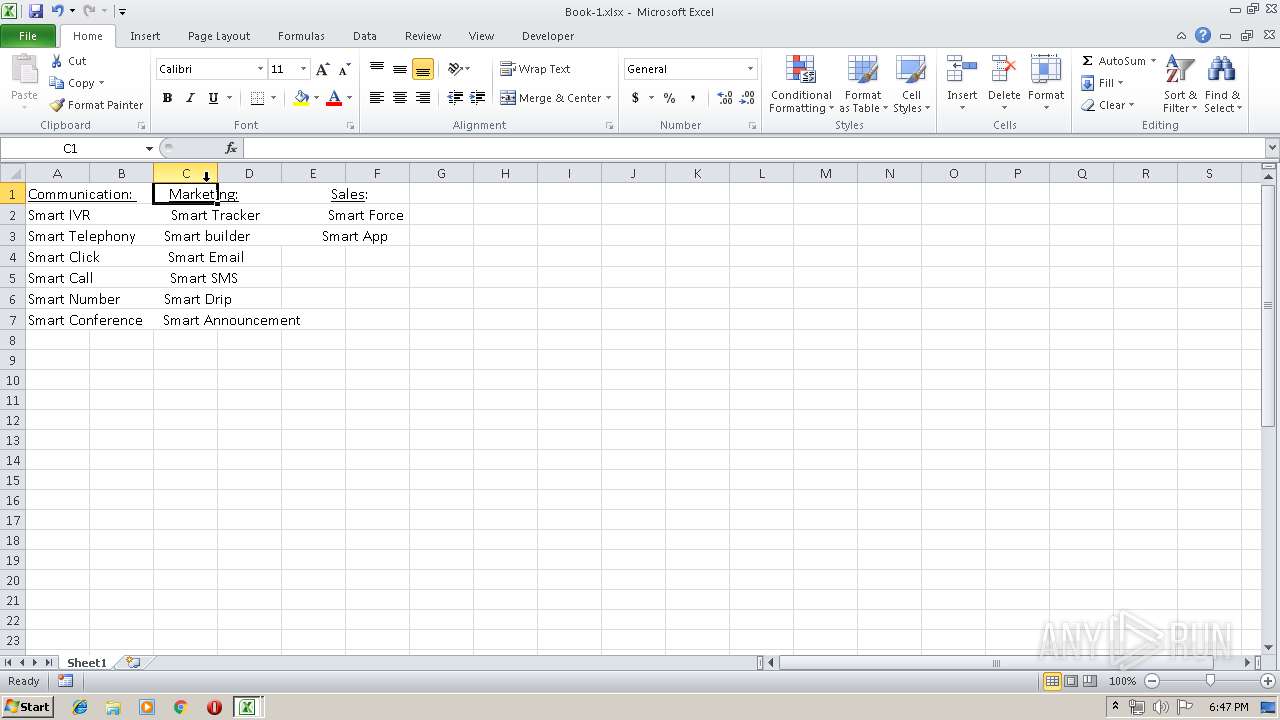
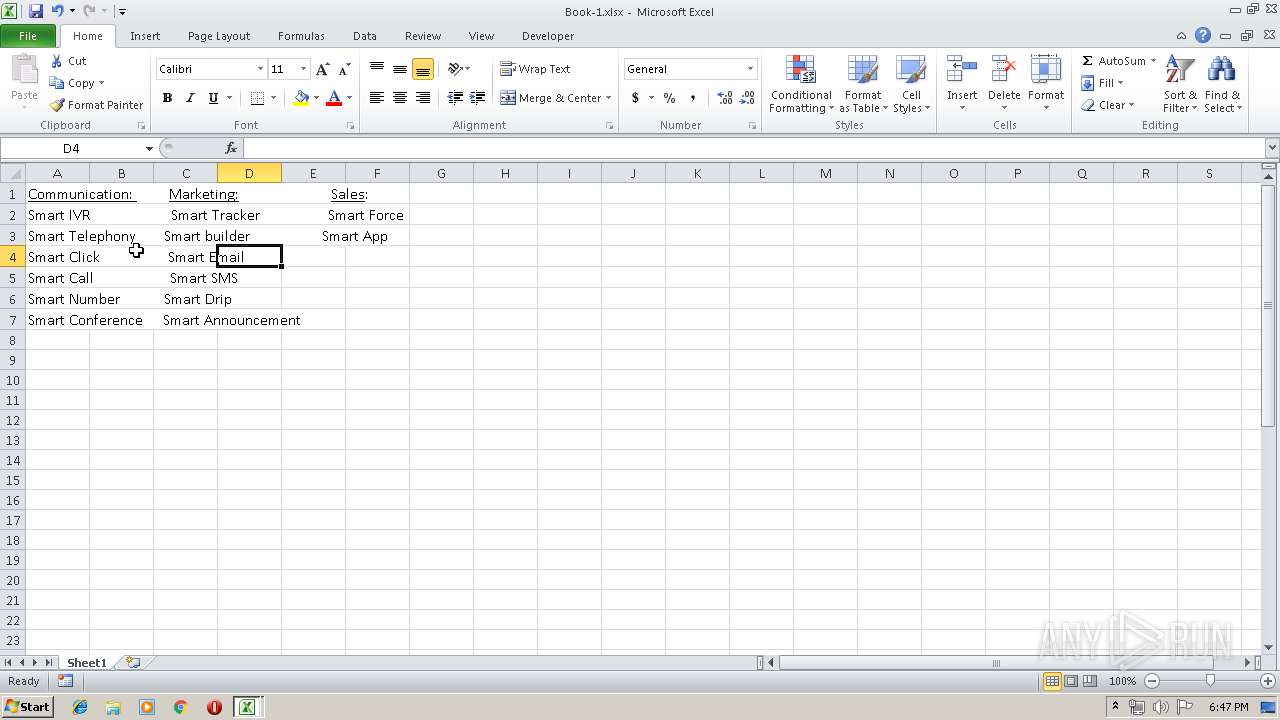
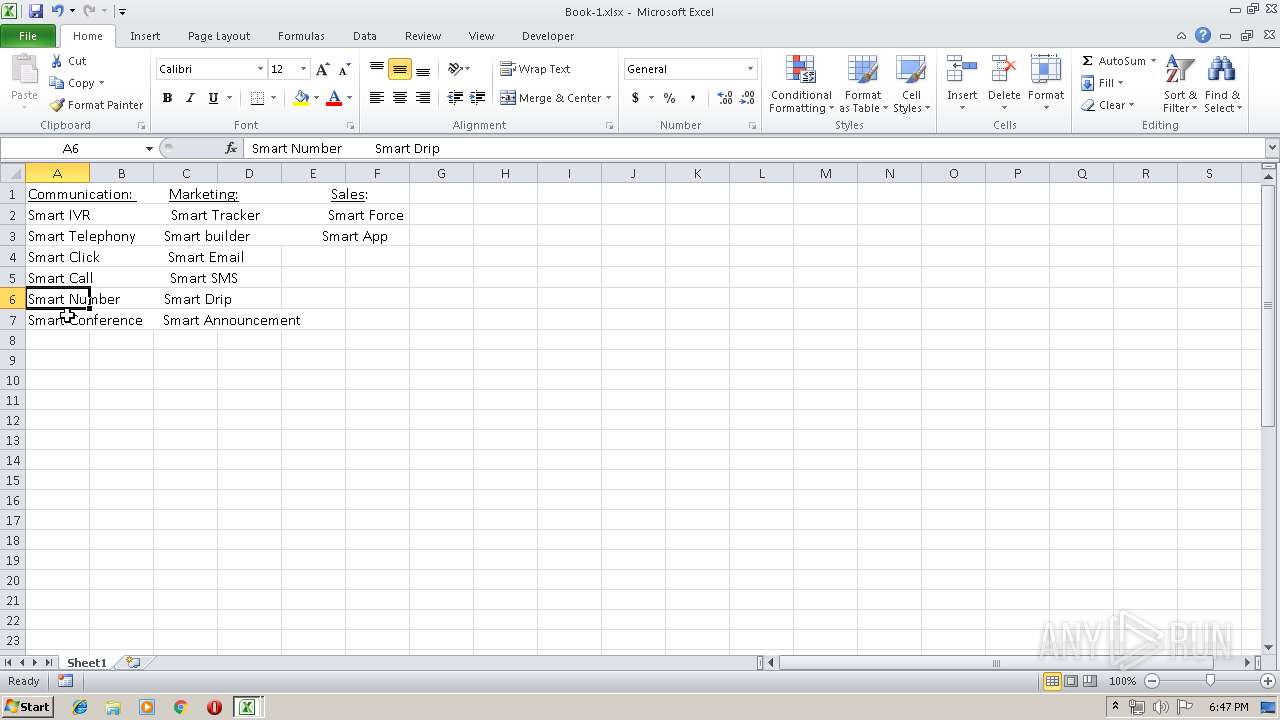
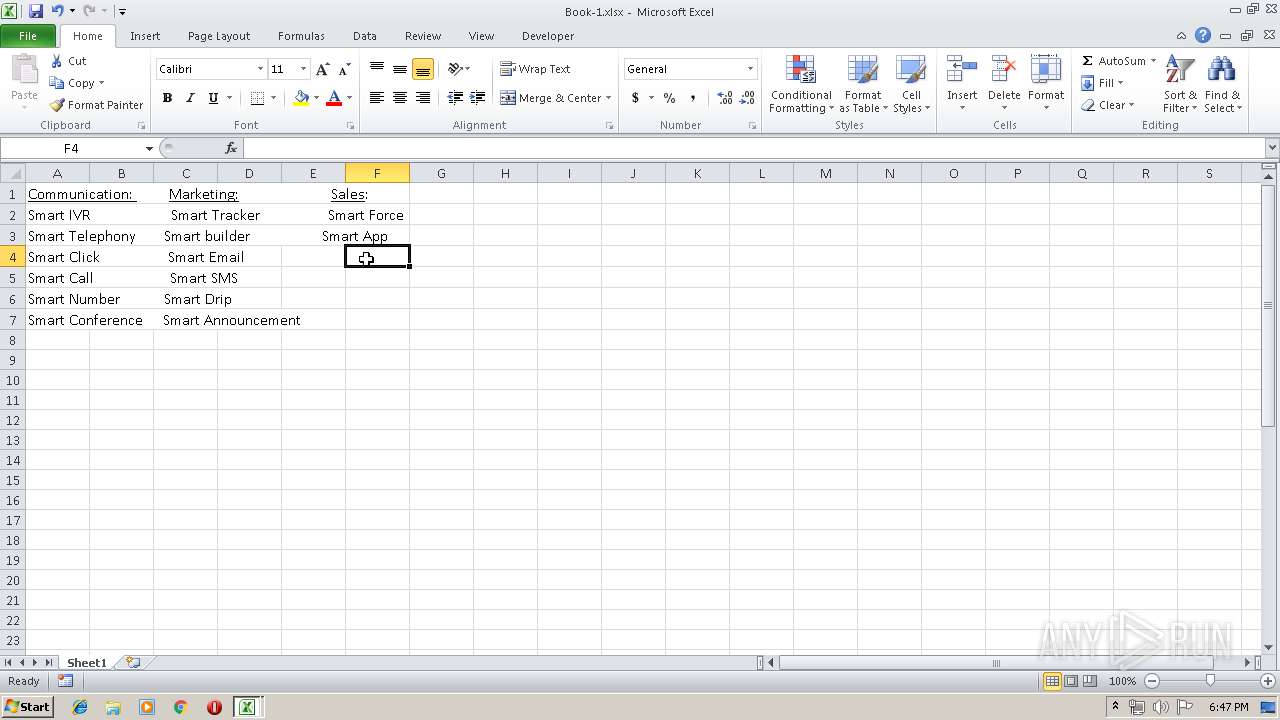
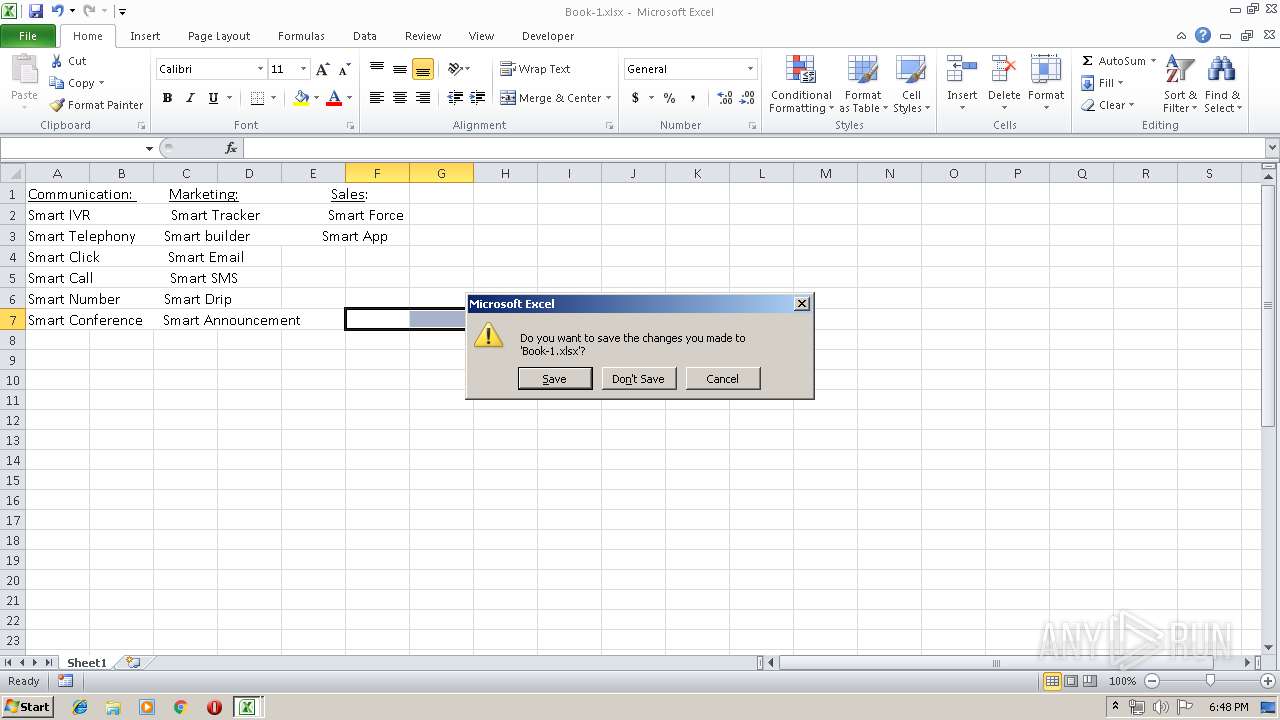
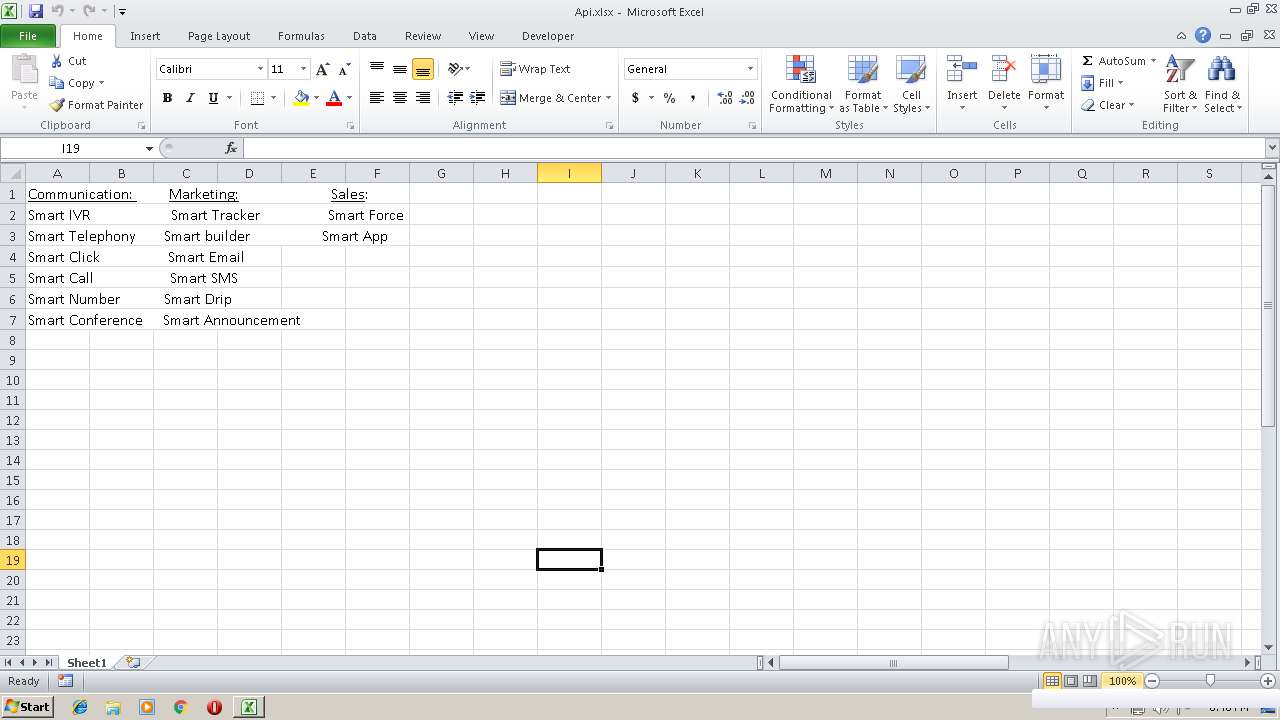
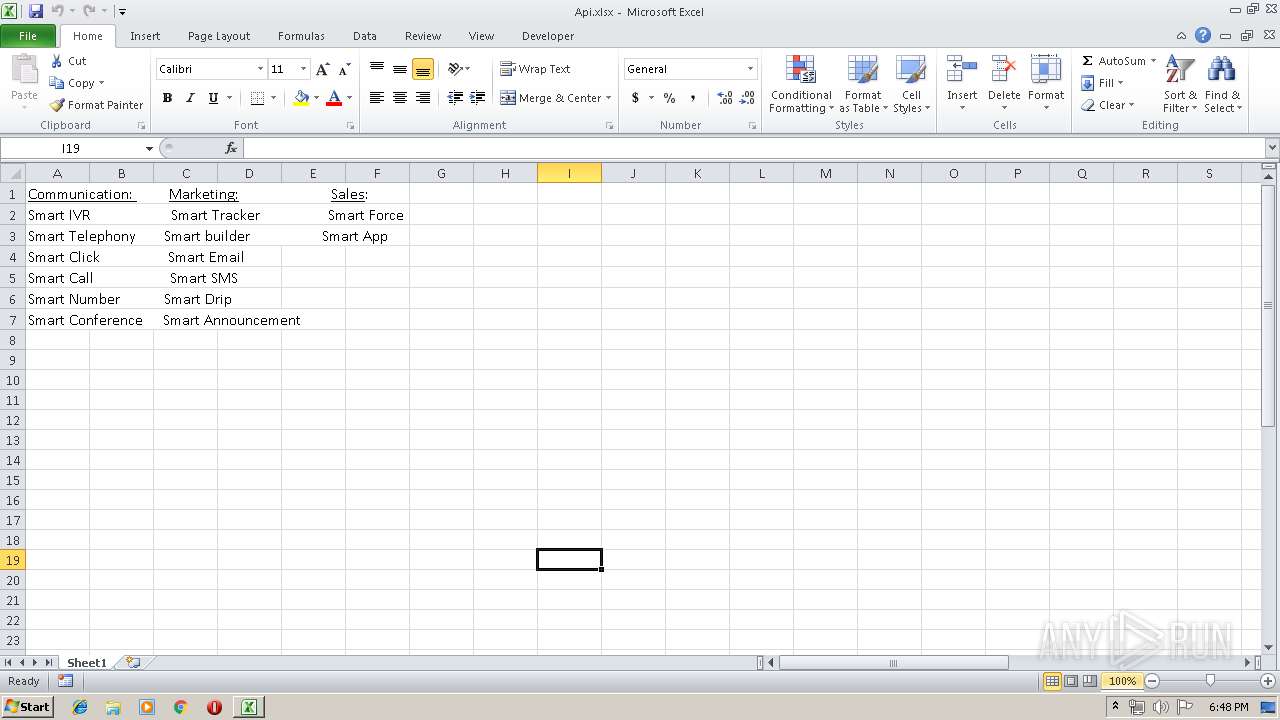
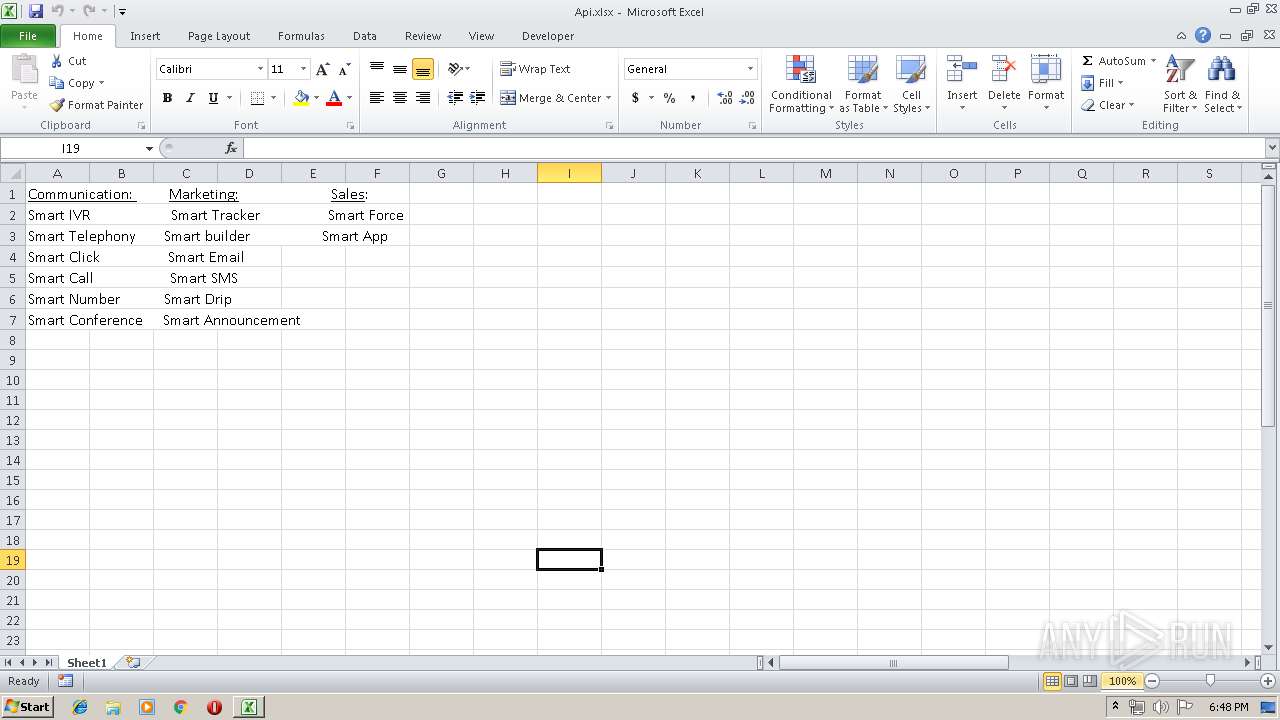
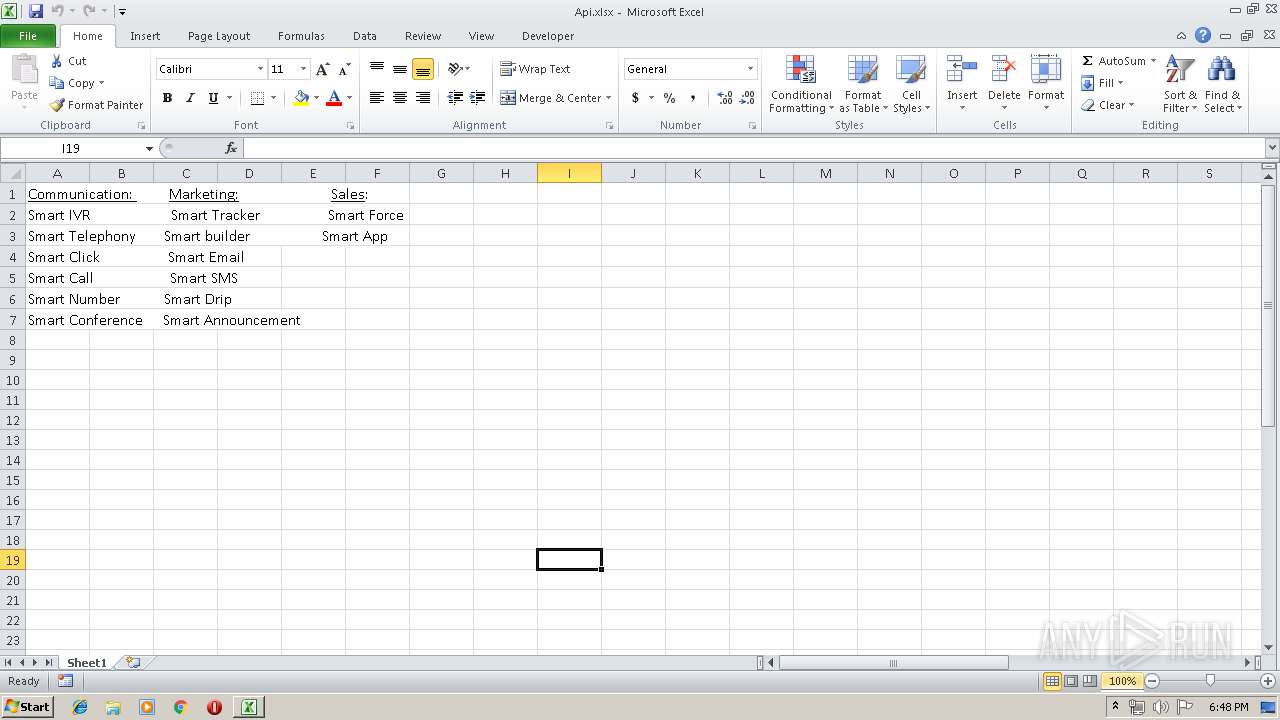
| File name: | Api.xlsx |
| Full analysis: | https://app.any.run/tasks/0b3f5d30-488d-4643-9a10-defcb3967049 |
| Verdict: | Malicious activity |
| Analysis date: | September 18, 2019, 17:46:50 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.spreadsheetml.sheet |
| File info: | Microsoft Excel 2007+ |
| MD5: | D663BADCAA2ED66E46FE2C40070DFB6A |
| SHA1: | 34066DC32E1BD8EC5685FBDD53C675E25AB61B33 |
| SHA256: | 9BD3DB55472AA810ED1D87DC72ED5BCBDA9267FE52C61C63D624041D10E62305 |
| SSDEEP: | 1536:d8t/oP5QYMMscvJSvn3hhb2mnGh7zMC56Px3DeKpzOamN:d8G1MMVvJSf3hhbA5ACWx3DhpS1 |
MALICIOUS
Equation Editor starts application (CVE-2017-11882)
- EQNEDT32.EXE (PID: 3500)
Application was dropped or rewritten from another process
- intel.exe (PID: 2556)
- gfj.exe (PID: 3360)
Changes the autorun value in the registry
- gfj.exe (PID: 3360)
Writes to a start menu file
- gfj.exe (PID: 3360)
SUSPICIOUS
Creates files in the program directory
- EQNEDT32.EXE (PID: 3500)
Executed via COM
- EQNEDT32.EXE (PID: 3500)
Executable content was dropped or overwritten
- EQNEDT32.EXE (PID: 3500)
- intel.exe (PID: 2556)
Drop AutoIt3 executable file
- intel.exe (PID: 2556)
Creates files in the user directory
- gfj.exe (PID: 3360)
INFO
Reads Microsoft Office registry keys
- EXCEL.EXE (PID: 3408)
Dropped object may contain Bitcoin addresses
- intel.exe (PID: 2556)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .xlsx | | | Excel Microsoft Office Open XML Format document (61.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (31.5) |
| .zip | | | ZIP compressed archive (7.2) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0002 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:09:17 11:20:14 |
| ZipCRC: | 0xa97f1e42 |
| ZipCompressedSize: | 386 |
| ZipUncompressedSize: | 1505 |
| ZipFileName: | [Content_Types].xml |
XMP
| Creator: | Windows User |
|---|
XML
| LastModifiedBy: | Windows User |
|---|---|
| CreateDate: | 2019:09:11 23:33:40Z |
| ModifyDate: | 2019:09:14 05:13:44Z |
| Application: | Microsoft Excel |
| DocSecurity: | None |
| ScaleCrop: | No |
| HeadingPairs: |
|
| TitlesOfParts: | Sheet1 |
| Company: | - |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| AppVersion: | 15.03 |
Total processes
37
Monitored processes
5
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2556 | "C:\ProgramData\intel.exe" | C:\ProgramData\intel.exe | EQNEDT32.EXE | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3360 | "C:\Users\admin\AppData\Local\Temp\09141351\gfj.exe" mkkkqe | C:\Users\admin\AppData\Local\Temp\09141351\gfj.exe | intel.exe | ||||||||||||
User: admin Company: AutoIt Team Integrity Level: MEDIUM Description: AutoIt v3 Script Exit code: 0 Version: 3, 3, 8, 1 Modules
| |||||||||||||||
| 3408 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" /dde | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 3500 | "C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE" -Embedding | C:\Program Files\Common Files\Microsoft Shared\EQUATION\EQNEDT32.EXE | svchost.exe | ||||||||||||
User: admin Company: Design Science, Inc. Integrity Level: MEDIUM Description: Microsoft Equation Editor Exit code: 0 Version: 00110900 Modules
| |||||||||||||||
| 3908 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegSvcs.exe | gfj.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft .NET Services Installation Utility Exit code: 0 Version: 4.7.3062.0 built by: NET472REL1 Modules
| |||||||||||||||
Total events
1 710
Read events
1 330
Write events
367
Delete events
13
Modification events
| (PID) Process: | (3408) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | write | Name: | tp# |
Value: 74702300500D0000010000000000000000000000 | |||
| (PID) Process: | (3408) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3408) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (3408) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel |
| Operation: | write | Name: | MTTT |
Value: 500D00000AA25E16496ED50100000000 | |||
| (PID) Process: | (3408) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete value | Name: | tp# |
Value: 74702300500D0000010000000000000000000000 | |||
| (PID) Process: | (3408) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\StartupItems |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3408) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency |
| Operation: | delete key | Name: | |
Value: | |||
| (PID) Process: | (3408) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (3408) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (3408) EXCEL.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Excel\Resiliency\DocumentRecovery\16A35A |
| Operation: | write | Name: | 16A35A |
Value: 04000000500D00002A00000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C004100700069002E0078006C0073007800000000002200000043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C004C006F00630061006C005C00540065006D0070005C000100000000000000A0CFF317496ED5015AA316005AA3160000000000AC020000001000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
3
Suspicious files
1
Text files
56
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3408 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR9C44.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2556 | intel.exe | C:\Users\admin\AppData\Local\Temp\09141351\mkkkqe | — | |
MD5:— | SHA256:— | |||
| 3500 | EQNEDT32.EXE | C:\ProgramData\intel.exe | executable | |
MD5:— | SHA256:— | |||
| 2556 | intel.exe | C:\Users\admin\AppData\Local\Temp\09141351\gut.docx | text | |
MD5:— | SHA256:— | |||
| 2556 | intel.exe | C:\Users\admin\AppData\Local\Temp\09141351\hjx.docx | text | |
MD5:— | SHA256:— | |||
| 2556 | intel.exe | C:\Users\admin\AppData\Local\Temp\09141351\sji.icm | text | |
MD5:— | SHA256:— | |||
| 2556 | intel.exe | C:\Users\admin\AppData\Local\Temp\09141351\pui.pdf | text | |
MD5:— | SHA256:— | |||
| 2556 | intel.exe | C:\Users\admin\AppData\Local\Temp\09141351\dmq.xls | text | |
MD5:— | SHA256:— | |||
| 2556 | intel.exe | C:\Users\admin\AppData\Local\Temp\09141351\efh.msc | text | |
MD5:— | SHA256:— | |||
| 2556 | intel.exe | C:\Users\admin\AppData\Local\Temp\09141351\krf.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
4
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3500 | EQNEDT32.EXE | 207.174.215.236:80 | indulfastag.com | PDR | US | malicious |
3908 | RegSvcs.exe | 79.134.225.61:5552 | info1.nowddns.com | Andreas Fink trading as Fink Telecom Services | CH | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
indulfastag.com |
| malicious |
info1.nowddns.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3500 | EQNEDT32.EXE | Potentially Bad Traffic | ET CURRENT_EVENTS Terse alphanumeric executable downloader high likelihood of being hostile |
3500 | EQNEDT32.EXE | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |