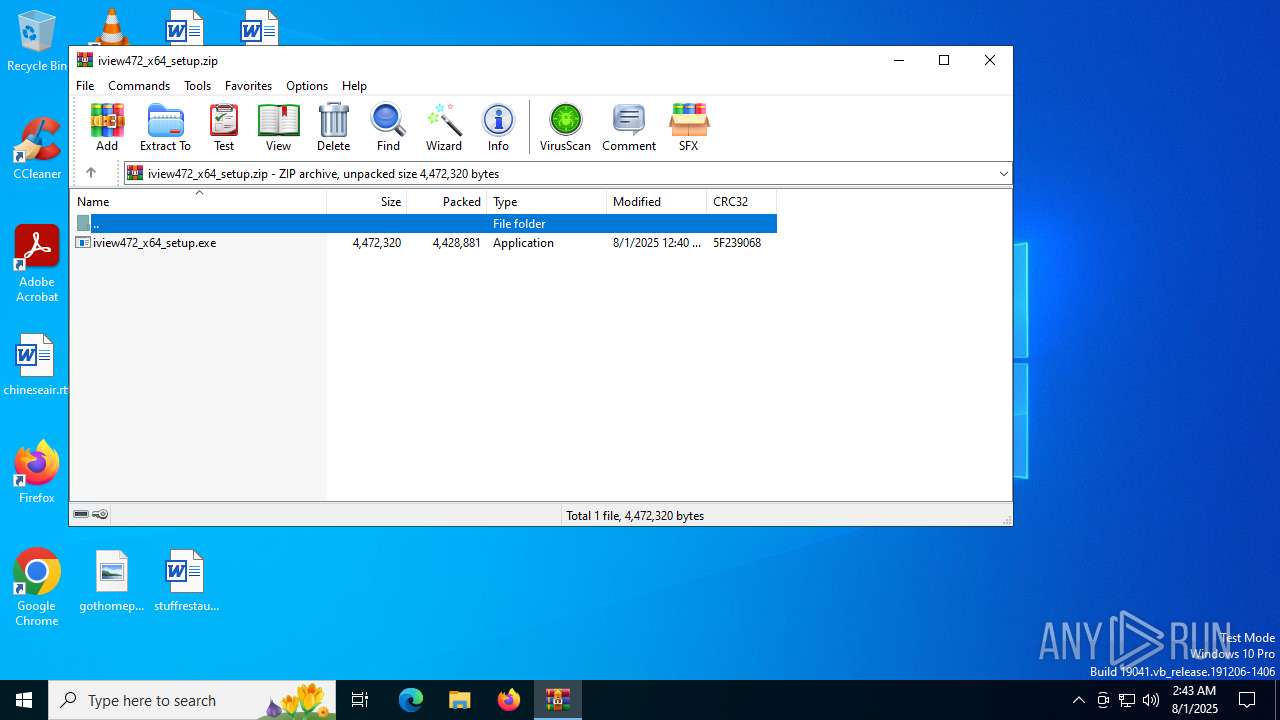
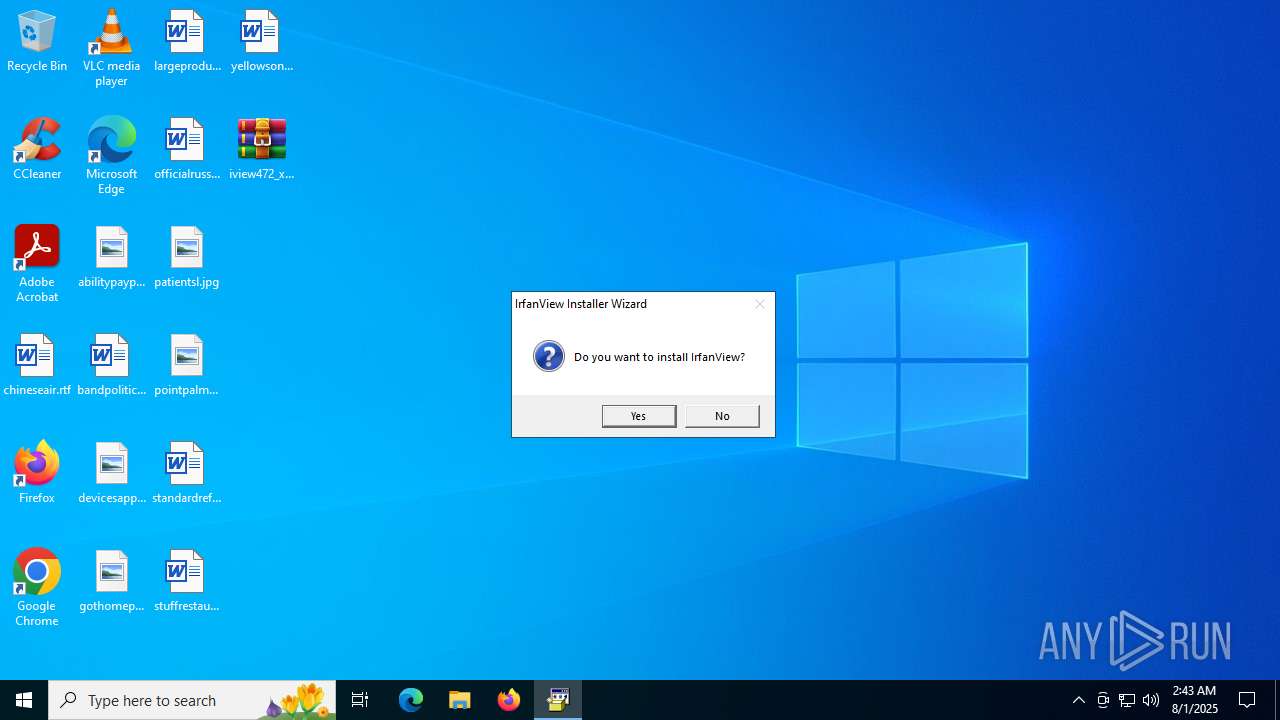
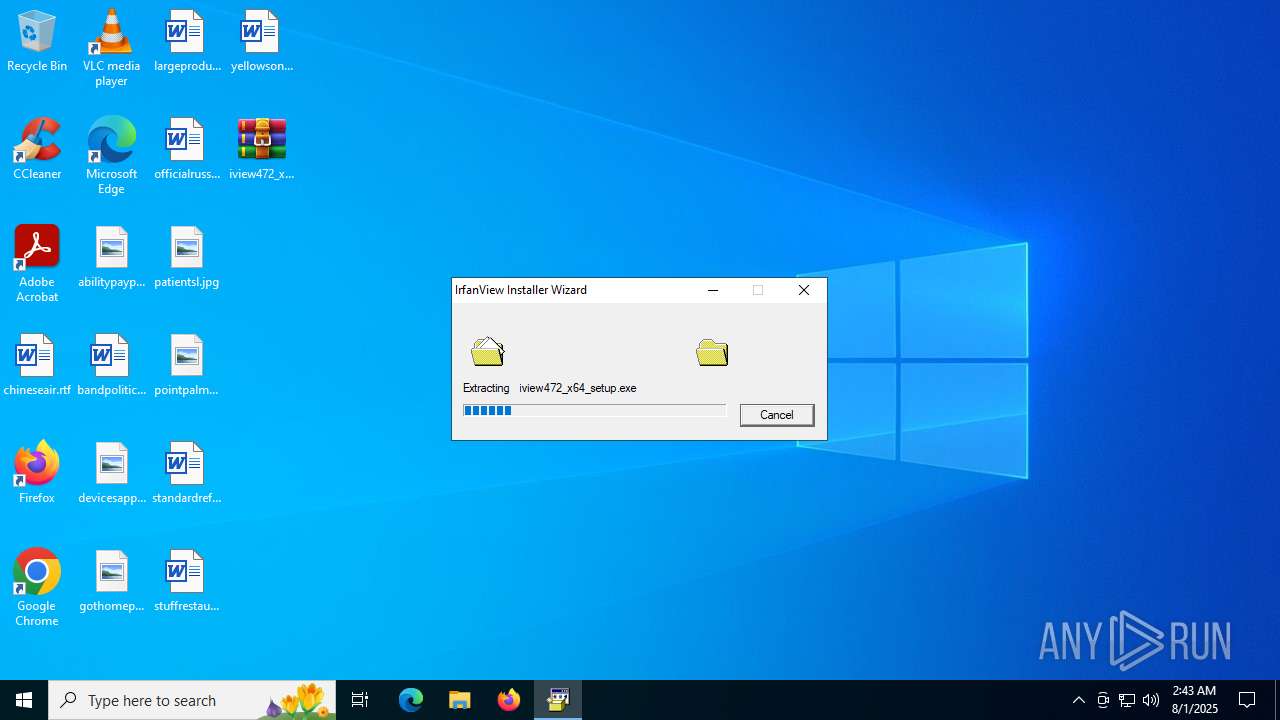
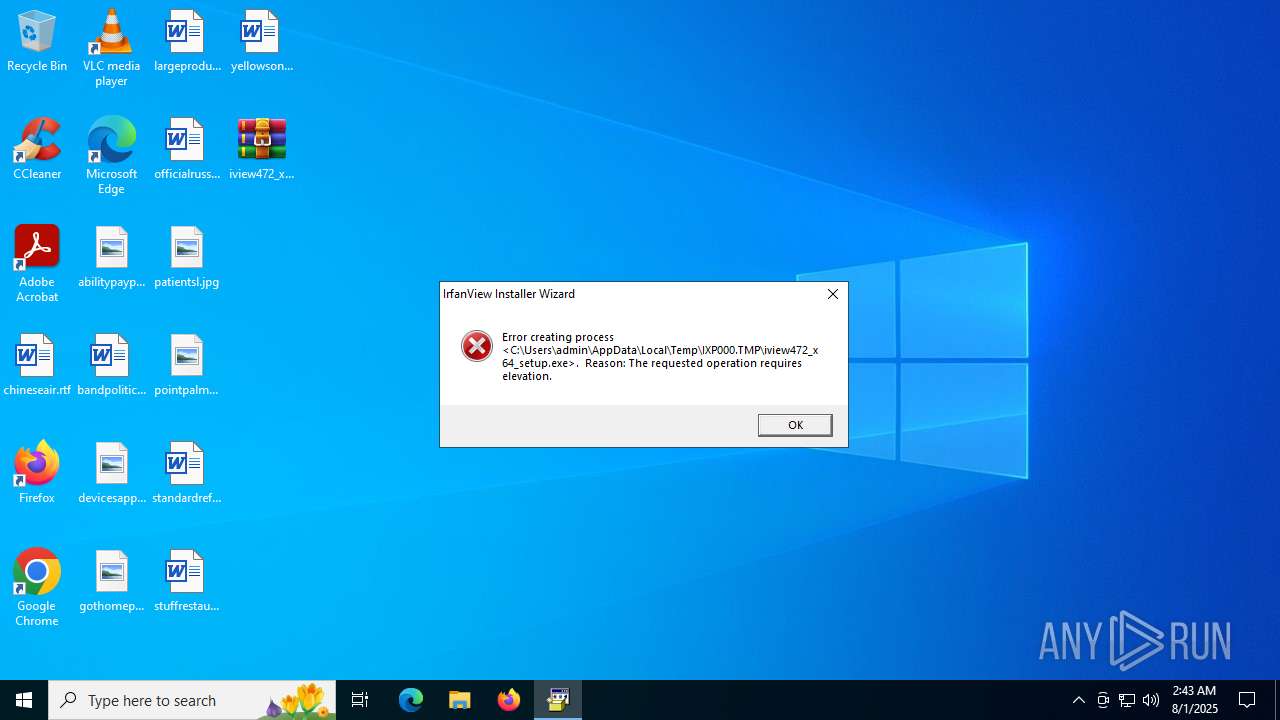
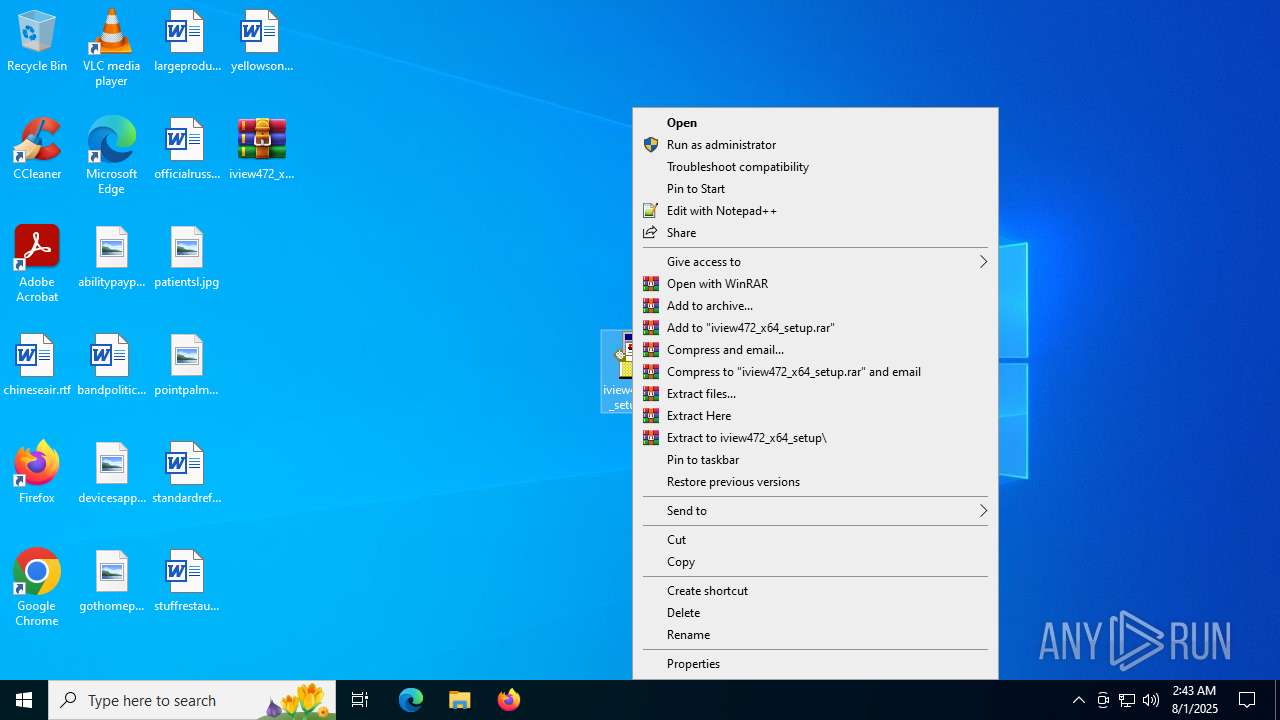
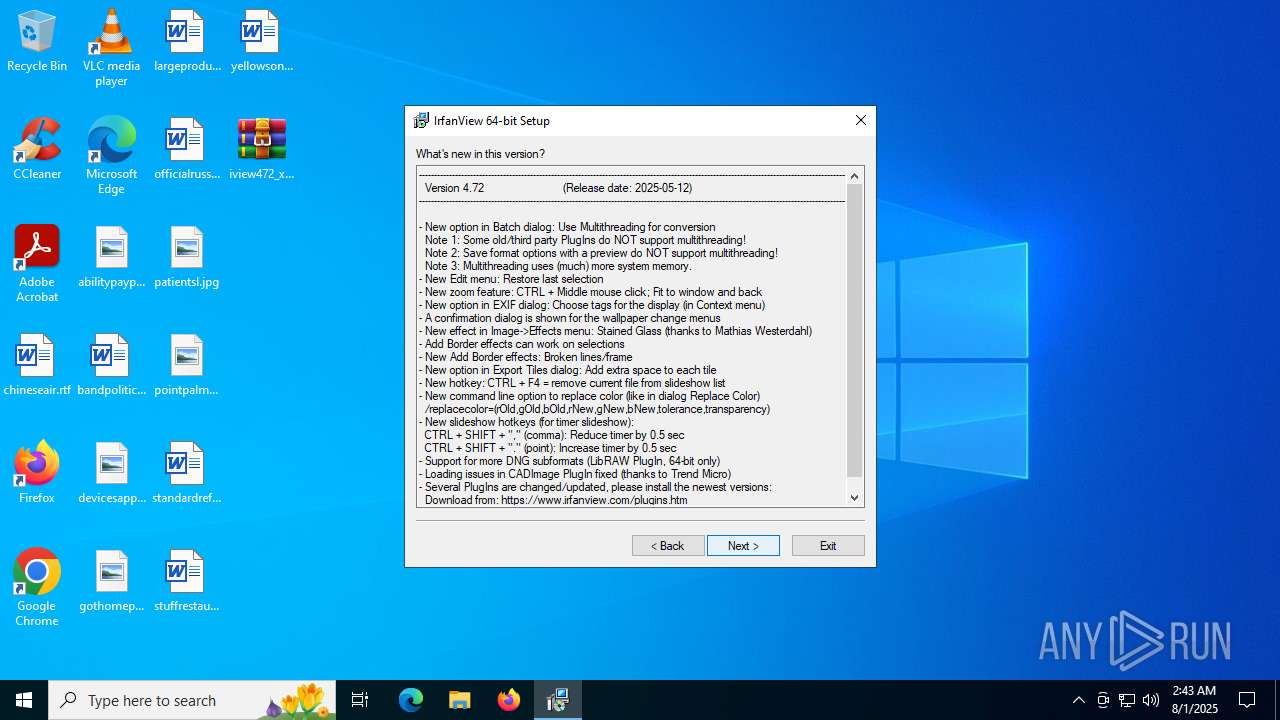
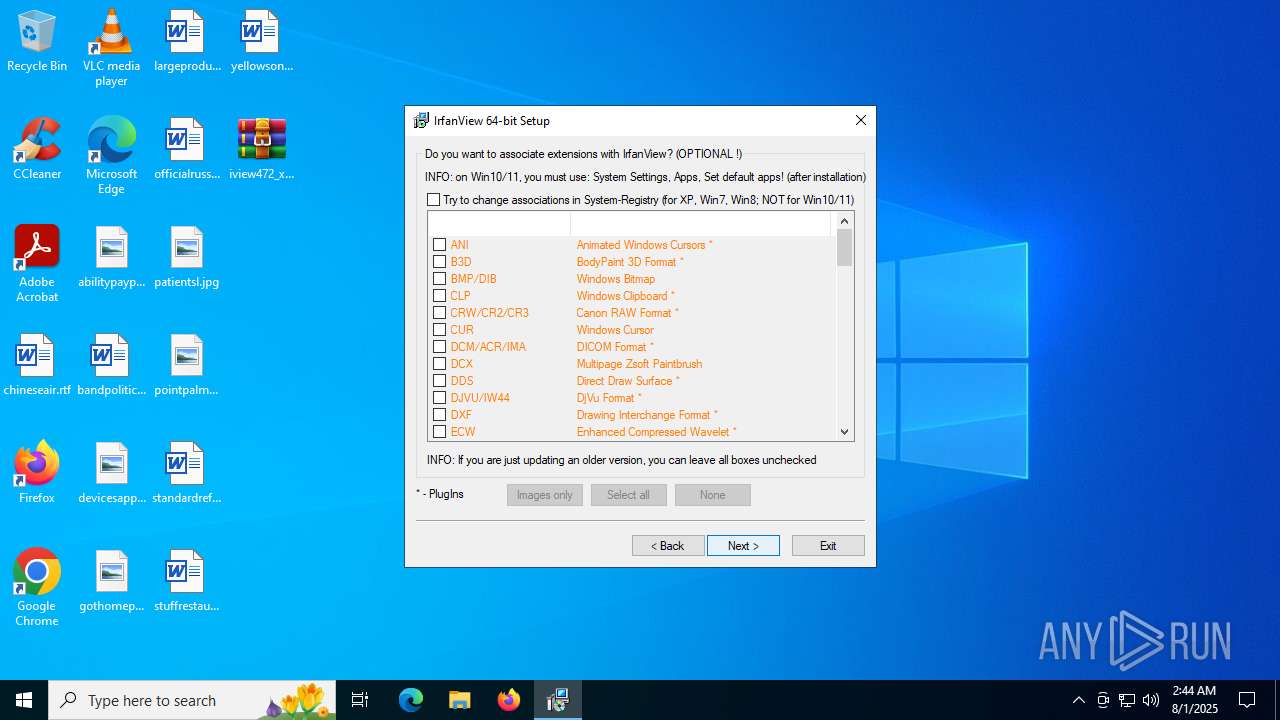
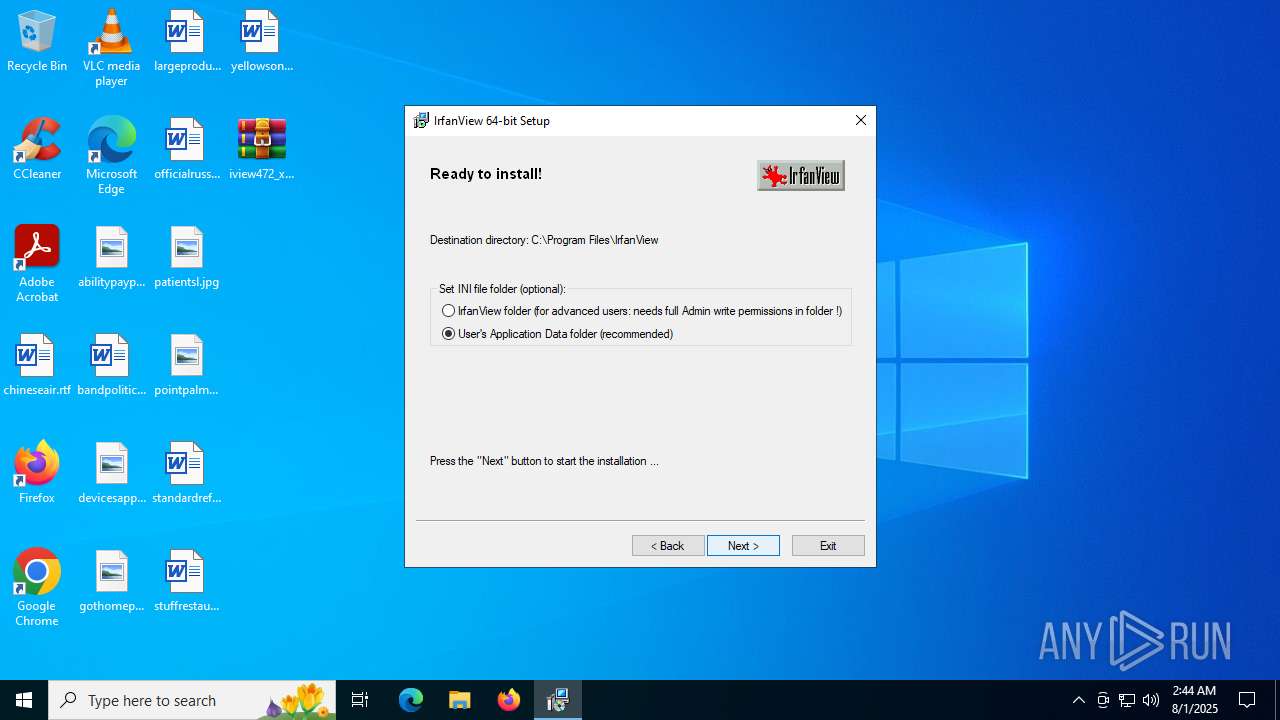
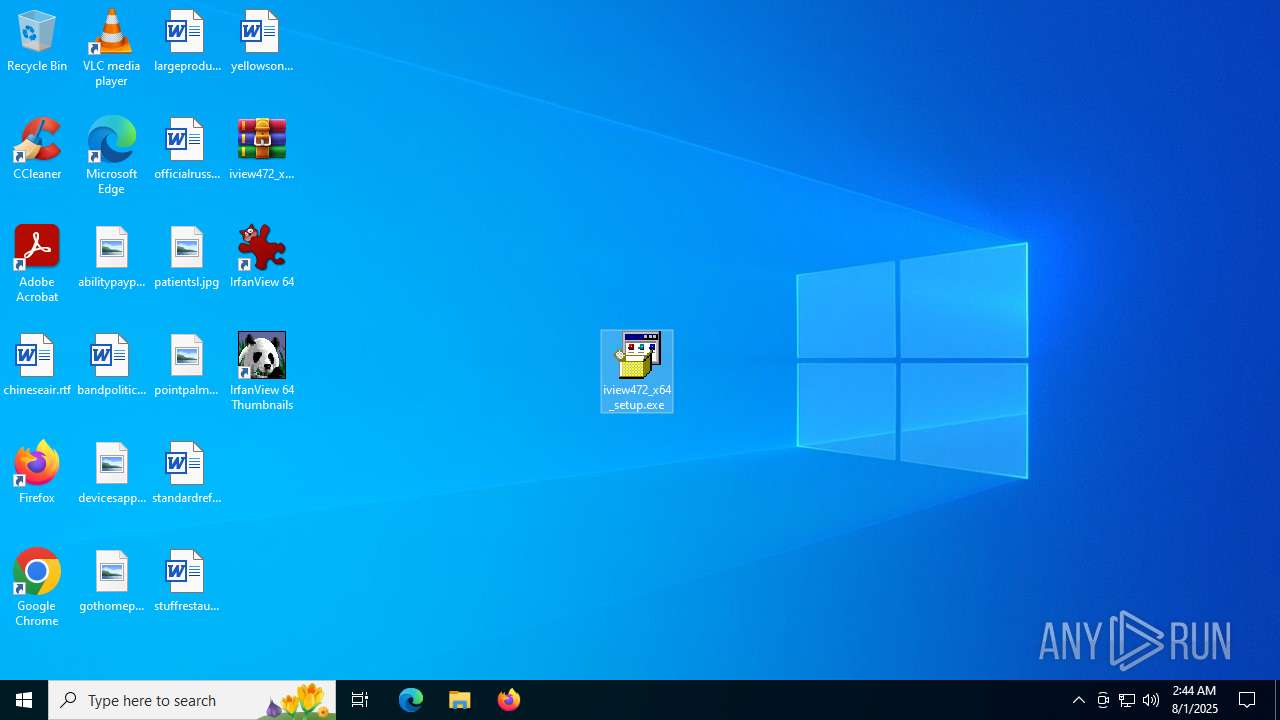
| File name: | iview472_x64_setup.zip |
| Full analysis: | https://app.any.run/tasks/038a35f7-6b2f-466c-9160-5783d0730b61 |
| Verdict: | Malicious activity |
| Analysis date: | August 01, 2025, 02:43:06 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 2B78EADDF07A54BEB2B23F4FBFF99E36 |
| SHA1: | AFDA120A205D57DF2EF60B9ACB4EFE64702E1F57 |
| SHA256: | 9BC13A6E0CAC3673D8469DBCD604A8AA77AD6A7A1E24D614B7A202169A26C051 |
| SSDEEP: | 98304:ttRgo5+ckdla7vkkozjO7SbPPgDR9PjBHNImMKK8RgHbYs/ZuB36ykExebsDjApF:rZdu |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 6340)
Changes the autorun value in the registry
- iview472_x64_setup.exe (PID: 5564)
- MSASCui.exe (PID: 5124)
- wuauclt.exe (PID: 5352)
- VGAuthService.exe (PID: 6584)
SUSPICIOUS
Starts a Microsoft application from unusual location
- iview472_x64_setup.exe (PID: 2188)
- iview472_x64_setup.exe (PID: 5564)
- MSASCui.exe (PID: 5124)
- wuauclt.exe (PID: 5352)
- VGAuthService.exe (PID: 6584)
Process drops legitimate windows executable
- WinRAR.exe (PID: 6340)
- iview472_x64_setup.exe (PID: 2188)
- iview472_x64_setup.exe (PID: 5564)
- MSASCui.exe (PID: 5124)
- wuauclt.exe (PID: 5352)
Executable content was dropped or overwritten
- iview472_x64_setup.exe (PID: 2188)
- iview472_x64_setup.exe (PID: 5564)
- iview472_x64_setup.exe (PID: 5032)
- MSASCui.exe (PID: 5124)
- wuauclt.exe (PID: 5352)
- VGAuthService.exe (PID: 6584)
There is functionality for taking screenshot (YARA)
- iview472_x64_setup.exe (PID: 5032)
Creates a software uninstall entry
- iview472_x64_setup.exe (PID: 5032)
The process creates files with name similar to system file names
- iview472_x64_setup.exe (PID: 5032)
INFO
The sample compiled with english language support
- WinRAR.exe (PID: 6340)
- iview472_x64_setup.exe (PID: 2188)
- iview472_x64_setup.exe (PID: 5564)
- iview472_x64_setup.exe (PID: 5032)
- MSASCui.exe (PID: 5124)
- wuauclt.exe (PID: 5352)
Checks supported languages
- iview472_x64_setup.exe (PID: 2188)
- iview472_x64_setup.exe (PID: 5564)
- iview472_x64_setup.exe (PID: 5032)
- MSASCui.exe (PID: 5124)
- wuauclt.exe (PID: 5352)
- VGAuthService.exe (PID: 6584)
- taskeng.exe (PID: 2432)
Reads the computer name
- iview472_x64_setup.exe (PID: 2188)
- iview472_x64_setup.exe (PID: 5564)
- iview472_x64_setup.exe (PID: 5032)
- taskeng.exe (PID: 2432)
Create files in a temporary directory
- iview472_x64_setup.exe (PID: 2188)
- iview472_x64_setup.exe (PID: 5564)
- iview472_x64_setup.exe (PID: 5032)
- MSASCui.exe (PID: 5124)
- wuauclt.exe (PID: 5352)
- VGAuthService.exe (PID: 6584)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 6340)
Manual execution by a user
- iview472_x64_setup.exe (PID: 2188)
- iview472_x64_setup.exe (PID: 5564)
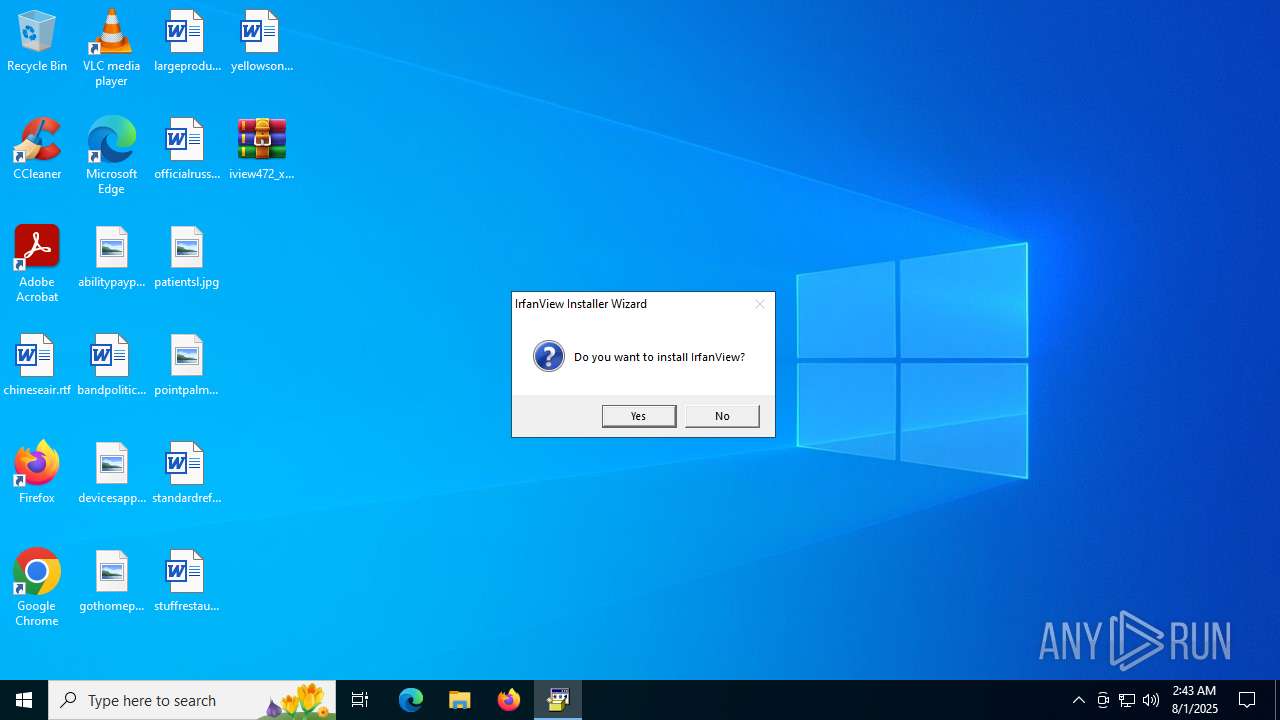
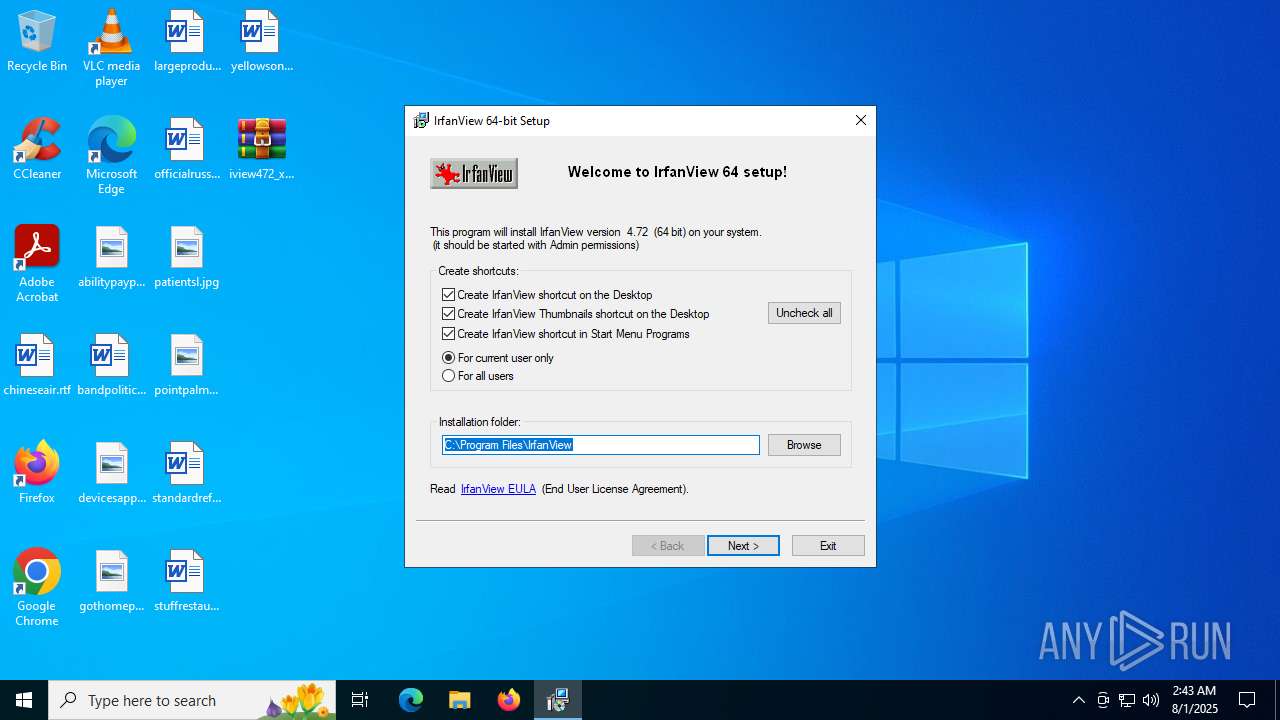
IrfanView executable
- iview472_x64_setup.exe (PID: 2188)
- iview472_x64_setup.exe (PID: 5564)
Launching a file from a Registry key
- iview472_x64_setup.exe (PID: 5564)
- MSASCui.exe (PID: 5124)
- wuauclt.exe (PID: 5352)
- VGAuthService.exe (PID: 6584)
Creates files in the program directory
- iview472_x64_setup.exe (PID: 5032)
Reads product name
- iview472_x64_setup.exe (PID: 5032)
Reads Environment values
- iview472_x64_setup.exe (PID: 5032)
Reads the machine GUID from the registry
- taskeng.exe (PID: 2432)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:08:01 12:40:34 |
| ZipCRC: | 0x5f239068 |
| ZipCompressedSize: | 4428881 |
| ZipUncompressedSize: | 4472320 |
| ZipFileName: | iview472_x64_setup.exe |
Total processes
146
Monitored processes
10
Malicious processes
4
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2188 | "C:\Users\admin\Desktop\iview472_x64_setup.exe" | C:\Users\admin\Desktop\iview472_x64_setup.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Win32 Cabinet Self-Extractor Exit code: 2147943140 Version: 6.0.6001.18000 (longhorn_rtm.080118-1840) Modules
| |||||||||||||||
| 2432 | C:\Users\admin\AppData\Local\Temp\IXP003.TMP\taskeng.exe | C:\Users\admin\AppData\Local\Temp\IXP003.TMP\taskeng.exe | — | VGAuthService.exe | |||||||||||
User: admin Integrity Level: HIGH Modules
| |||||||||||||||
| 4520 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5032 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\iview472_x64_setup.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\iview472_x64_setup.exe | iview472_x64_setup.exe | ||||||||||||
User: admin Company: Irfan Skiljan Integrity Level: HIGH Description: IrfanView 64-bit Installer Exit code: 0 Version: 4.72.0.0 Modules
| |||||||||||||||
| 5124 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\MSASCui.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\MSASCui.exe | iview472_x64_setup.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Win32 Cabinet Self-Extractor Version: 6.0.6001.18000 (longhorn_rtm.080118-1840) Modules
| |||||||||||||||
| 5352 | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\wuauclt.exe | C:\Users\admin\AppData\Local\Temp\IXP001.TMP\wuauclt.exe | MSASCui.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Win32 Cabinet Self-Extractor Version: 6.0.6001.18000 (longhorn_rtm.080118-1840) Modules
| |||||||||||||||
| 5564 | "C:\Users\admin\Desktop\iview472_x64_setup.exe" | C:\Users\admin\Desktop\iview472_x64_setup.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Win32 Cabinet Self-Extractor Version: 6.0.6001.18000 (longhorn_rtm.080118-1840) Modules
| |||||||||||||||
| 6340 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\iview472_x64_setup.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 6508 | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\iview472_x64_setup.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\iview472_x64_setup.exe | — | iview472_x64_setup.exe | |||||||||||
User: admin Company: Irfan Skiljan Integrity Level: MEDIUM Description: IrfanView 64-bit Installer Exit code: 3221226540 Version: 4.72.0.0 Modules
| |||||||||||||||
| 6584 | C:\Users\admin\AppData\Local\Temp\IXP002.TMP\VGAuthService.exe | C:\Users\admin\AppData\Local\Temp\IXP002.TMP\VGAuthService.exe | wuauclt.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Win32 Cabinet Self-Extractor Version: 6.0.6001.18000 (longhorn_rtm.080118-1840) Modules
| |||||||||||||||
Total events
4 147
Read events
4 025
Write events
122
Delete events
0
Modification events
| (PID) Process: | (6340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (6340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (6340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (6340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (6340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (6340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\iview472_x64_setup.zip | |||
| (PID) Process: | (6340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (6340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (6340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (6340) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
24
Suspicious files
1
Text files
22
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5032 | iview472_x64_setup.exe | C:\Program Files\IrfanView\Plugins\Effects.dll | executable | |
MD5:5708224A335E8BC04B281D03A8700D53 | SHA256:CFA3670E36731FFACF1870F68D85C019B2E5CDE0AFC6B039AFAA1FEB1DF027DB | |||
| 5032 | iview472_x64_setup.exe | C:\Users\admin\AppData\Local\Temp\iview_x64.zip | compressed | |
MD5:DD3758B03FAFC579B30C414F81022D5D | SHA256:6AB7B71E137D3A7AECC79C52DE47DB319556EB7597D264D892EB6B5C4AC0508A | |||
| 5032 | iview472_x64_setup.exe | C:\Program Files\IrfanView\i_about.txt | text | |
MD5:978342921F6F81C0C5B4E81FC7F33478 | SHA256:7BD56C8AF3CA4831D0B1A421A961A4769F70D630FADBCC391BB5C2068EE02490 | |||
| 5032 | iview472_x64_setup.exe | C:\Program Files\IrfanView\i_options.txt | text | |
MD5:0A536A50ADFA64FF85FB376544BBB976 | SHA256:145419DA895183DEAC8CCC1C089288F1FDD09282A26164BDCB919EC8170FAAA0 | |||
| 5032 | iview472_x64_setup.exe | C:\Program Files\IrfanView\i_changes.txt | text | |
MD5:5E3BBB34A844219EA767AE8A267EBF95 | SHA256:1B48801C559F1101EAA0CBDD11F70A255592766EEE1098E2B5F8380AC6FCD06B | |||
| 5032 | iview472_x64_setup.exe | C:\Program Files\IrfanView\iv_uninstall.exe | executable | |
MD5:92D2C69FE445E4F7DB1FA19CCFE4525B | SHA256:7BCB4C03A98BAF59643BA3E4C46900551A3AF6A91282F0E7A6D4AAAFF7AC1BF6 | |||
| 5032 | iview472_x64_setup.exe | C:\Program Files\IrfanView\Plugins\Icons.dll | executable | |
MD5:39D9B94B71C432859EAD3513E82E9DE4 | SHA256:4A2EAE12A9C53B74A2E1833A090E8572150AD2E46A01554280D23A75C84D2E01 | |||
| 5032 | iview472_x64_setup.exe | C:\Program Files\IrfanView\Plugins\Slideshow.exe | executable | |
MD5:7A0C00320760F09A172ACA44451DB76B | SHA256:CCED90019780DC6B9B24D1FAAD8455581F560C647B88F1C834C7E59C2D93E701 | |||
| 5032 | iview472_x64_setup.exe | C:\Program Files\IrfanView\Html\thumbnails.html | html | |
MD5:1AC8A9A77F1A5C674463F925431D14BD | SHA256:CCA0218B31DACEA39F1A73C7504E4DB720A8038A275DAE552BF29A807FA8877D | |||
| 5032 | iview472_x64_setup.exe | C:\Program Files\IrfanView\i_languages.txt | text | |
MD5:97AB52F18CC61F0867445520F02C48DE | SHA256:1582F3F3EB1996F65110E6CE2B36417D1733699CF804EB41E1980D0900D5DB27 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
21
DNS requests
17
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
512 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6956 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
512 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5944 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5372 | RUXIMICS.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6956 | svchost.exe | 40.126.31.1:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6956 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |