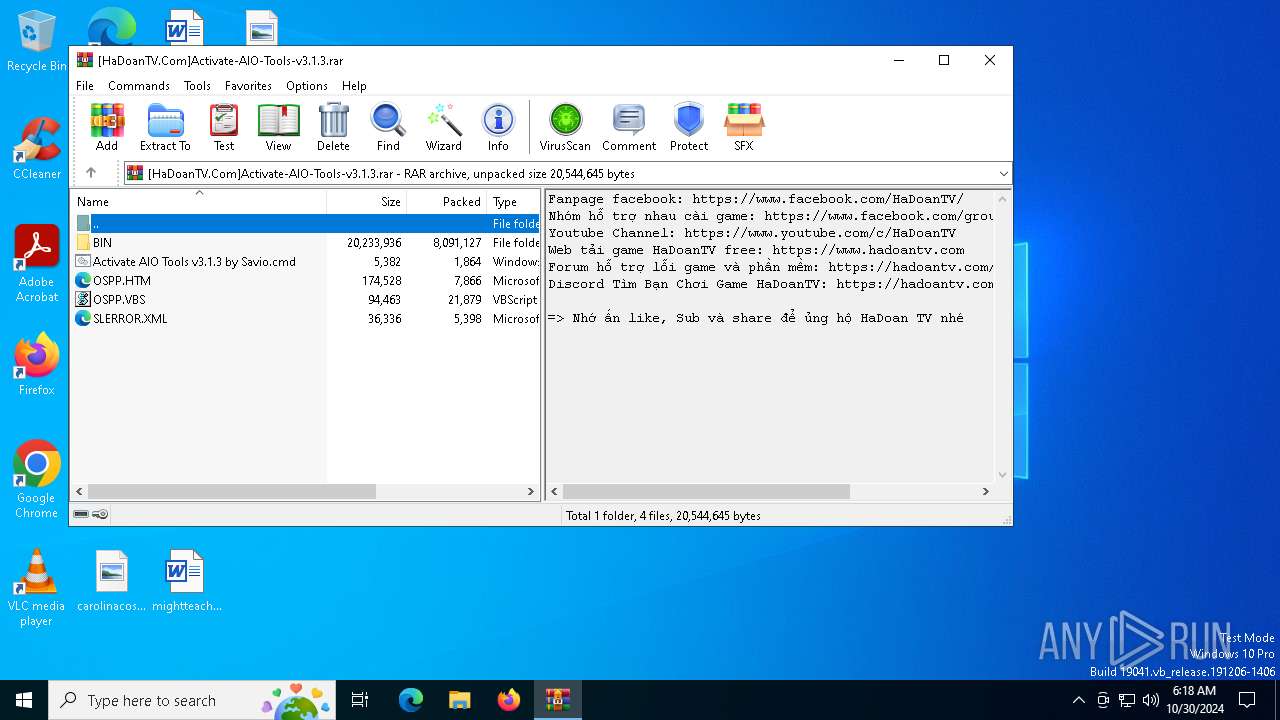
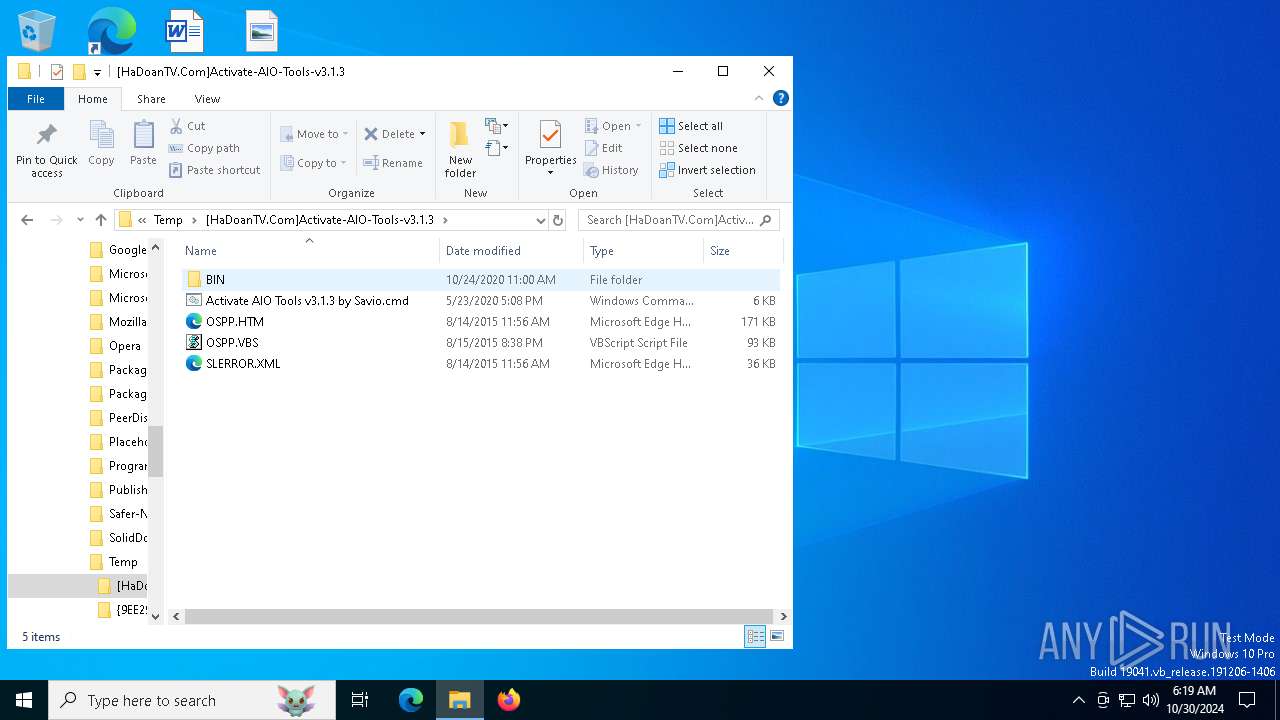
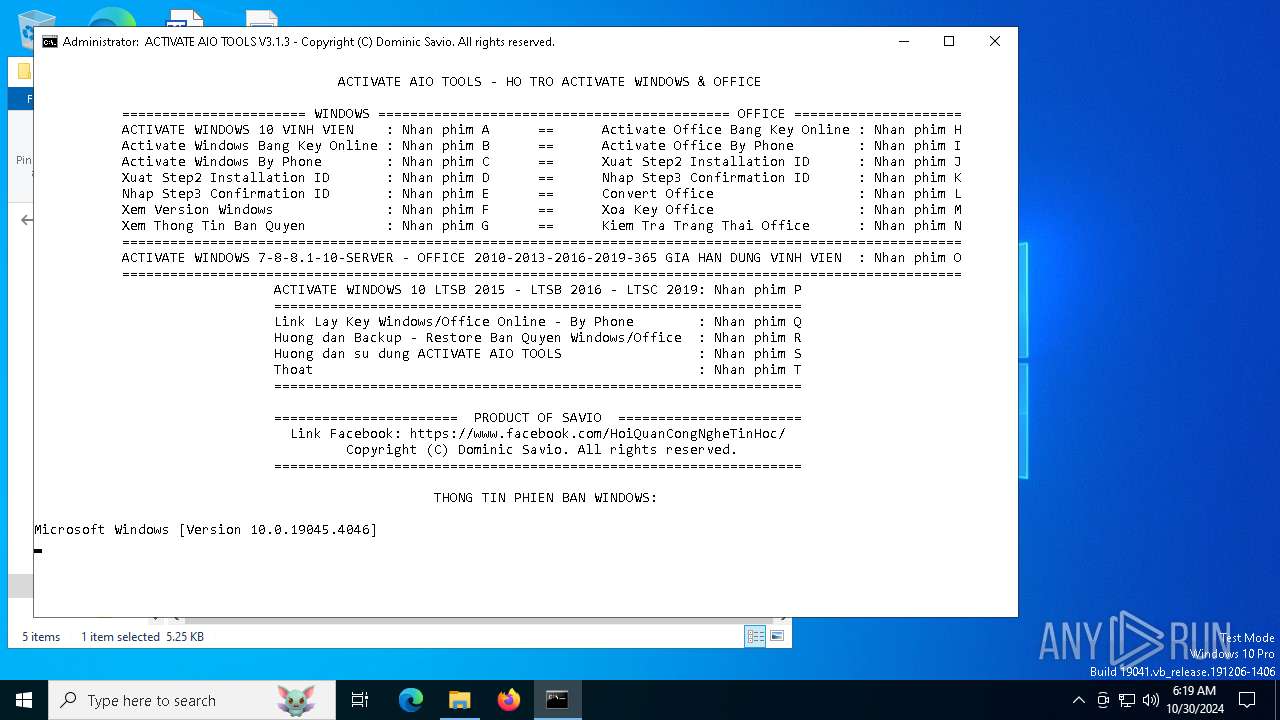
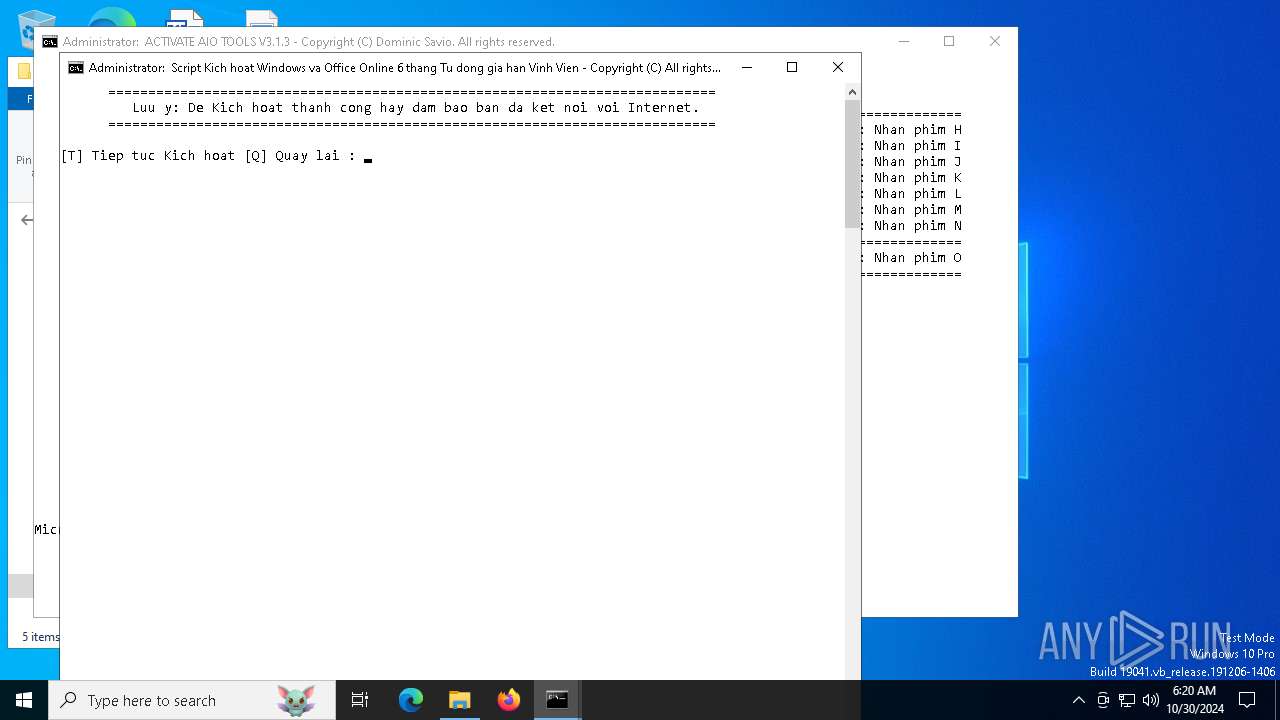
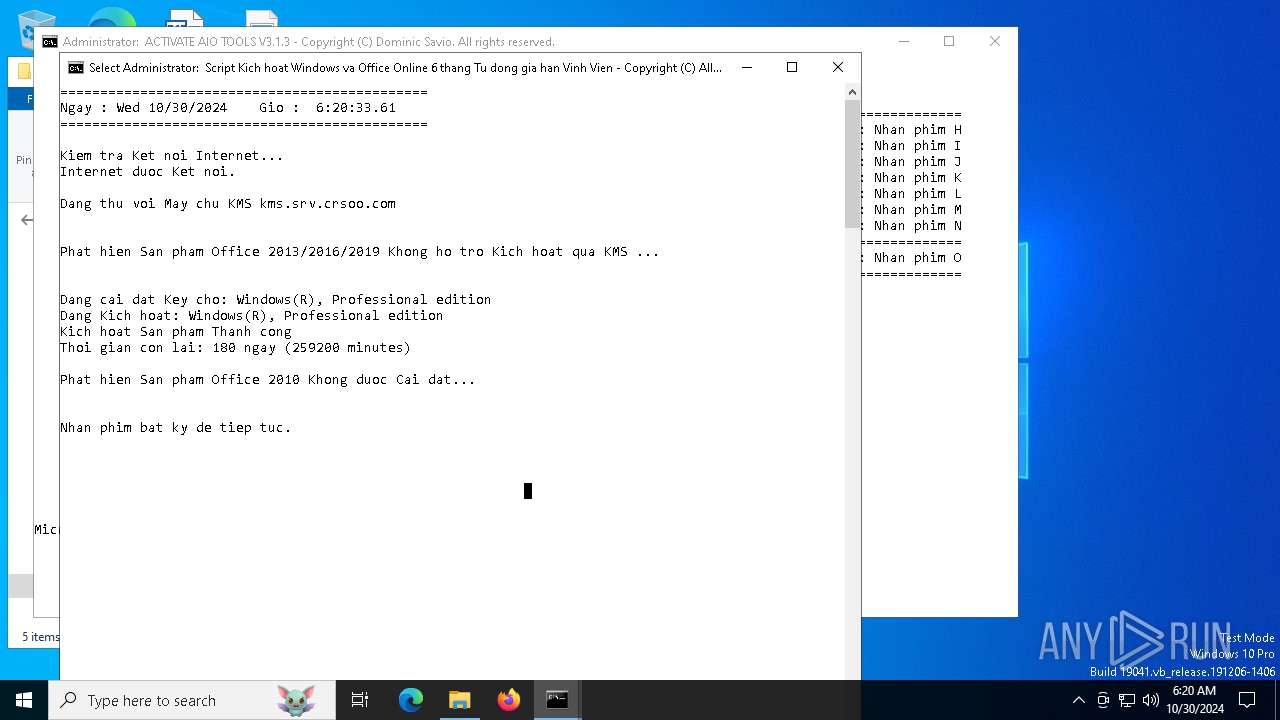
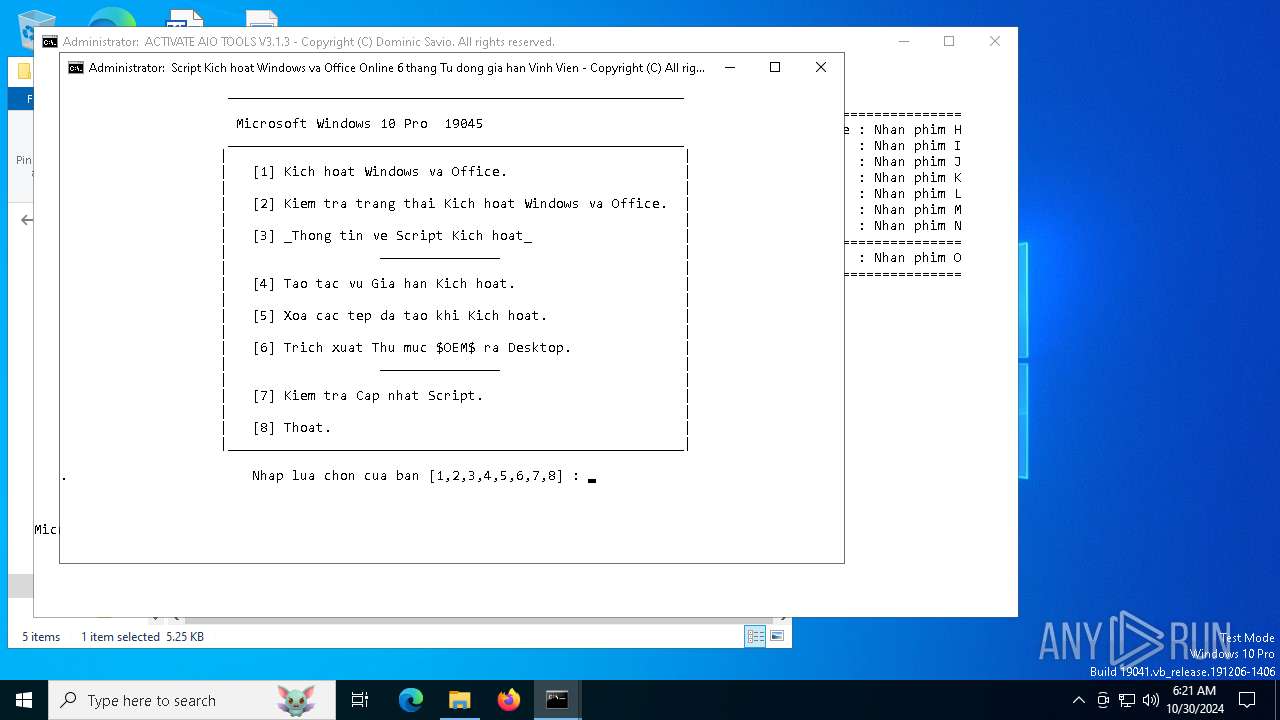
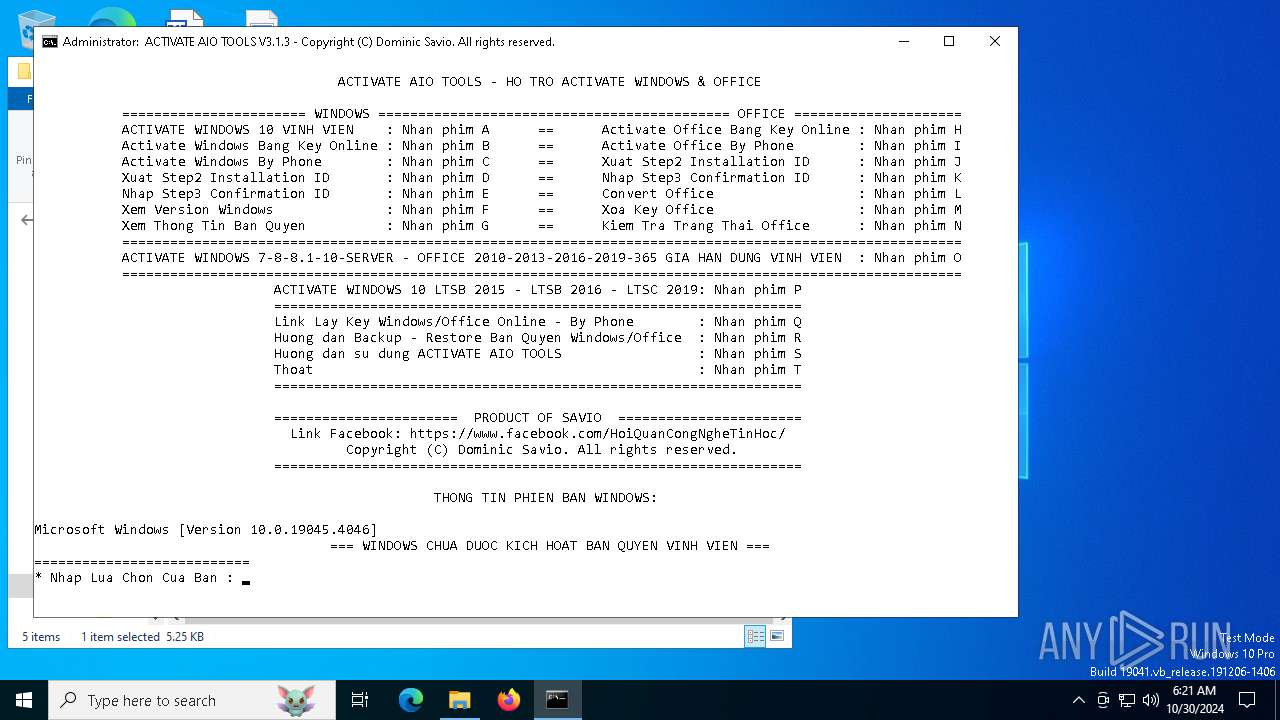
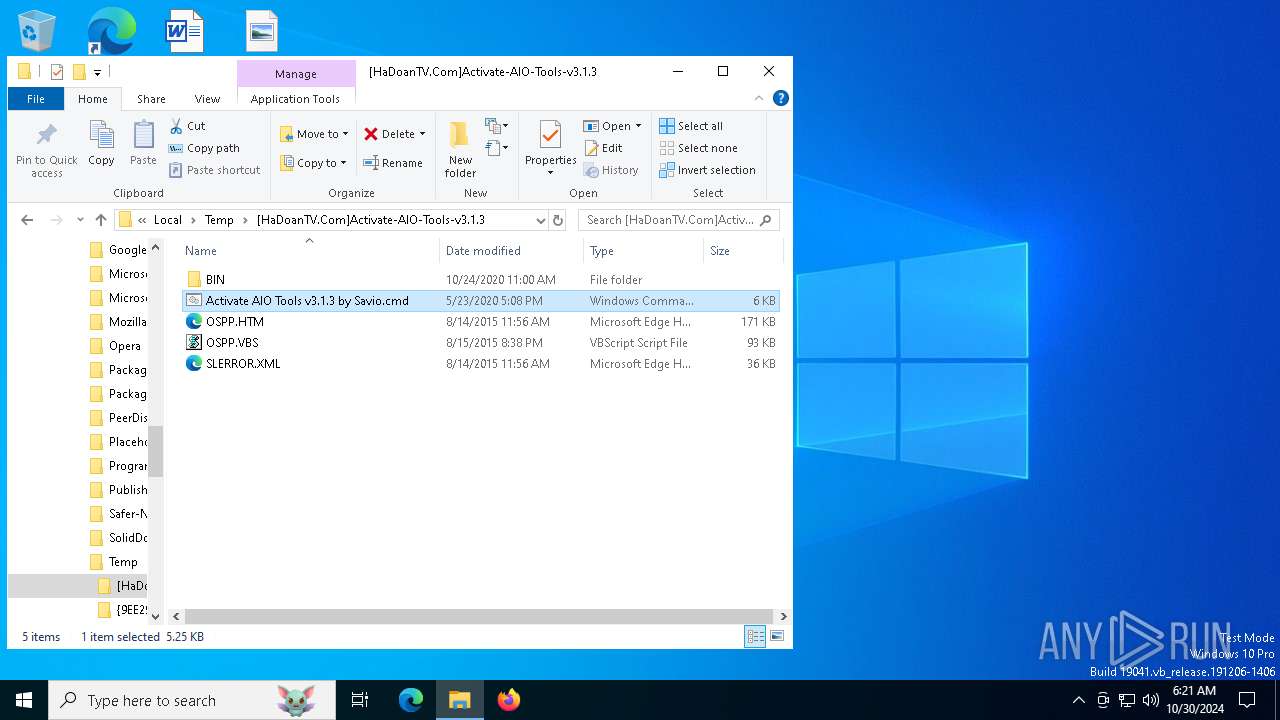
| File name: | [HaDoanTV.Com]Activate-AIO-Tools-v3.1.3.rar |
| Full analysis: | https://app.any.run/tasks/673723d6-cdf2-4117-9d33-96499fead9b6 |
| Verdict: | Malicious activity |
| Analysis date: | October 30, 2024, 06:18:43 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | DF6EB4A243821A2A662D30E033F5C95D |
| SHA1: | 8B31398273FFF8E8F6C62615BC68E3D144644EC1 |
| SHA256: | 9BBEACA16D04FB6B4488AAE472E77BE10F32E089D08EE48FBAA091A344A67D57 |
| SSDEEP: | 98304:q1M6lEEOxpUKr+Pt0/OeFFGkShrPc752m+Gdog9fQc661a13hfo8CD7knZKXc7ba:icOERzb2Il82IT90tx1PNIQ |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 5612)
SUSPICIOUS
The process executes VB scripts
- cmd.exe (PID: 5948)
- cmd.exe (PID: 1572)
- cmd.exe (PID: 6760)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 5948)
- cmd.exe (PID: 1572)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 5948)
- cmd.exe (PID: 1572)
Process drops legitimate windows executable
- WinRAR.exe (PID: 3008)
Application launched itself
- cmd.exe (PID: 1572)
- cmd.exe (PID: 5948)
Executing commands from ".cmd" file
- cmd.exe (PID: 5948)
Starts application with an unusual extension
- cmd.exe (PID: 5948)
Uses ICACLS.EXE to modify access control lists
- cmd.exe (PID: 5948)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 5652)
- cmd.exe (PID: 7136)
- cmd.exe (PID: 1880)
- cmd.exe (PID: 6588)
- cmd.exe (PID: 5372)
- cmd.exe (PID: 7056)
Hides command output
- cmd.exe (PID: 6100)
- cmd.exe (PID: 3024)
- cmd.exe (PID: 3904)
- cmd.exe (PID: 712)
- cmd.exe (PID: 5616)
- cmd.exe (PID: 6736)
- cmd.exe (PID: 700)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 1572)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 1572)
Uses WMIC.EXE to obtain Windows Installer data
- cmd.exe (PID: 6936)
- cmd.exe (PID: 1572)
- cmd.exe (PID: 1732)
- cmd.exe (PID: 204)
- cmd.exe (PID: 6764)
- cmd.exe (PID: 6440)
Uses WMIC.EXE to obtain service application data
- cmd.exe (PID: 1880)
- cmd.exe (PID: 1572)
Connects to unusual port
- SppExtComObj.Exe (PID: 696)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3008)
Manual execution by a user
- WinRAR.exe (PID: 3008)
- cmd.exe (PID: 5948)
Starts MODE.COM to configure console settings
- mode.com (PID: 2196)
- mode.com (PID: 2796)
- mode.com (PID: 6484)
- mode.com (PID: 6836)
- mode.com (PID: 4088)
Changes the display of characters in the console
- cmd.exe (PID: 5948)
Checks operating system version
- cmd.exe (PID: 1572)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|
Total processes
298
Monitored processes
167
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 204 | choice /C:12345678 /N /M ". Nhap lua chon cua ban [1,2,3,4,5,6,7,8] : " | C:\Windows\System32\choice.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Offers the user a choice Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 204 | C:\WINDOWS\system32\cmd.exe /c "wmic path SoftwareLicensingProduct where (Description like '%KMSCLIENT%') get ID /VALUE" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 300 | cscript //nologo C:\WINDOWS\system32\slmgr.vbs /xpr | C:\Windows\System32\cscript.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft ® Console Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 624 | findstr "1" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 696 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | svchost.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 700 | C:\WINDOWS\system32\cmd.exe /c "reg query HKLM\SOFTWARE\Wow6432Node\Microsoft\Office\14.0\Common\InstallRoot /v Path" 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 712 | C:\WINDOWS\system32\cmd.exe /c "reg query HKLM\SOFTWARE\Microsoft\Office\16.0\Common\InstallRoot /v Path" 2>nul | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 784 | wmic path SoftwareLicensingProduct where ID='3f1afc82-f8ac-4f6c-8005-1d233e606eee' get Name | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 784 | findstr "1" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 848 | wmic Path Win32_OperatingSystem Get CSDVersion /format:LIST | C:\Windows\System32\wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 515
Read events
13 490
Write events
25
Delete events
0
Modification events
| (PID) Process: | (5612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\GoogleChromeEnterpriseBundle64.zip | |||
| (PID) Process: | (5612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\[HaDoanTV.Com]Activate-AIO-Tools-v3.1.3.rar | |||
| (PID) Process: | (5612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (5612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (5612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (5612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (5612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
| (PID) Process: | (5612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (5612) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | psize |
Value: 80 | |||
Executable files
23
Suspicious files
3
Text files
285
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\[HaDoanTV.Com]Activate-AIO-Tools-v3.1.3\BIN\ActWin10Digital\ActLTSBLTSC\ActLTSB2015Digital\ActLTSB2015Digital.cmd | text | |
MD5:7197630F8784496254B5707D05187265 | SHA256:4BE2650D035B4570EFA5F08C10F14B048203426FBCC6E84C6FC6C7E09BBE52AA | |||
| 3008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\[HaDoanTV.Com]Activate-AIO-Tools-v3.1.3\BIN\ActWin10Digital\ActWin10All\BIN\gatherosstate.exe | executable | |
MD5:15CE0753A16DD4F9B9F0F9926DD37C4E | SHA256:028C8FBE58F14753B946475DE9F09A9C7A05FD62E81A1339614C9E138FC2A21D | |||
| 3008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\[HaDoanTV.Com]Activate-AIO-Tools-v3.1.3\BIN\ActWin10Digital\ActLTSBLTSC\ActLTSB2016Digital\BIN\slc.dll | executable | |
MD5:E2840606372AB67B7107CE757D506C28 | SHA256:37E20A504ADE965184D92ED5CA415CDE899090A6A20EA3ABF8C85FF9648B66F4 | |||
| 3008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\[HaDoanTV.Com]Activate-AIO-Tools-v3.1.3\BIN\ActWin10Digital\ActLTSBLTSC\ActLTSB2015Digital\BIN\slc.dll | executable | |
MD5:E2840606372AB67B7107CE757D506C28 | SHA256:37E20A504ADE965184D92ED5CA415CDE899090A6A20EA3ABF8C85FF9648B66F4 | |||
| 3008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\[HaDoanTV.Com]Activate-AIO-Tools-v3.1.3\BIN\ActWin10Digital\ActLTSBLTSC\ActLTSC2019years38\bin\ARM64_gatherosstate.exe | executable | |
MD5:CD65269EE38B3E89E9F1F95C422EAE2E | SHA256:44244E541B6A5BE14E6C2053B752F06E1AF0415B2252CED2BED0A562B3ED6462 | |||
| 3008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\[HaDoanTV.Com]Activate-AIO-Tools-v3.1.3\BIN\ActWin10Digital\ActWin10All\BIN\ARM64_slc.dll | executable | |
MD5:21101B68F168BA3BAC0FB3733267DFEF | SHA256:8B01AAB03C529433FE39C83D9B70C52654B83970F9C92FCD5E3DA2A5598BF89F | |||
| 3008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\[HaDoanTV.Com]Activate-AIO-Tools-v3.1.3\BIN\ActWin10Digital\ActLTSBLTSC\ActLTSC2019years38\bin\ARM64_slc.dll | executable | |
MD5:21101B68F168BA3BAC0FB3733267DFEF | SHA256:8B01AAB03C529433FE39C83D9B70C52654B83970F9C92FCD5E3DA2A5598BF89F | |||
| 3008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\[HaDoanTV.Com]Activate-AIO-Tools-v3.1.3\BIN\ActWin10Digital\ActLTSBLTSC\ActLTSB2015Digital\BIN\gatherosstate.exe | executable | |
MD5:239EBED4DB9FDB3AE93D1592EA2F8132 | SHA256:971A591B9C2F4D06D77268787D54220A48BAC7B17B000B13777FF89F2D11C15C | |||
| 3008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\[HaDoanTV.Com]Activate-AIO-Tools-v3.1.3\BIN\ActWin10Digital\ActLTSBLTSC\ActLTSC2019years38\bin\gatherosstate.exe | executable | |
MD5:15CE0753A16DD4F9B9F0F9926DD37C4E | SHA256:028C8FBE58F14753B946475DE9F09A9C7A05FD62E81A1339614C9E138FC2A21D | |||
| 3008 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\[HaDoanTV.Com]Activate-AIO-Tools-v3.1.3\BIN\ActWin10Digital\ActLTSBLTSC\ActLTSB2016Digital\BIN\gatherosstate.exe | executable | |
MD5:E2C16921EE7D949DBB70234FC235F726 | SHA256:BDFE57913C83BC1E5647EF0B75C647FF3B36673790D2ABB3593DCF9F1B426AD6 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
48
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4004 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6364 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 23.53.40.178:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3740 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6944 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3740 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
5488 | MoUsoCoreWorker.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3396 | RUXIMICS.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4360 | SearchApp.exe | 104.126.37.130:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6944 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4004 | svchost.exe | 20.190.159.4:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4004 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4360 | SearchApp.exe | 104.126.37.128:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
th.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |