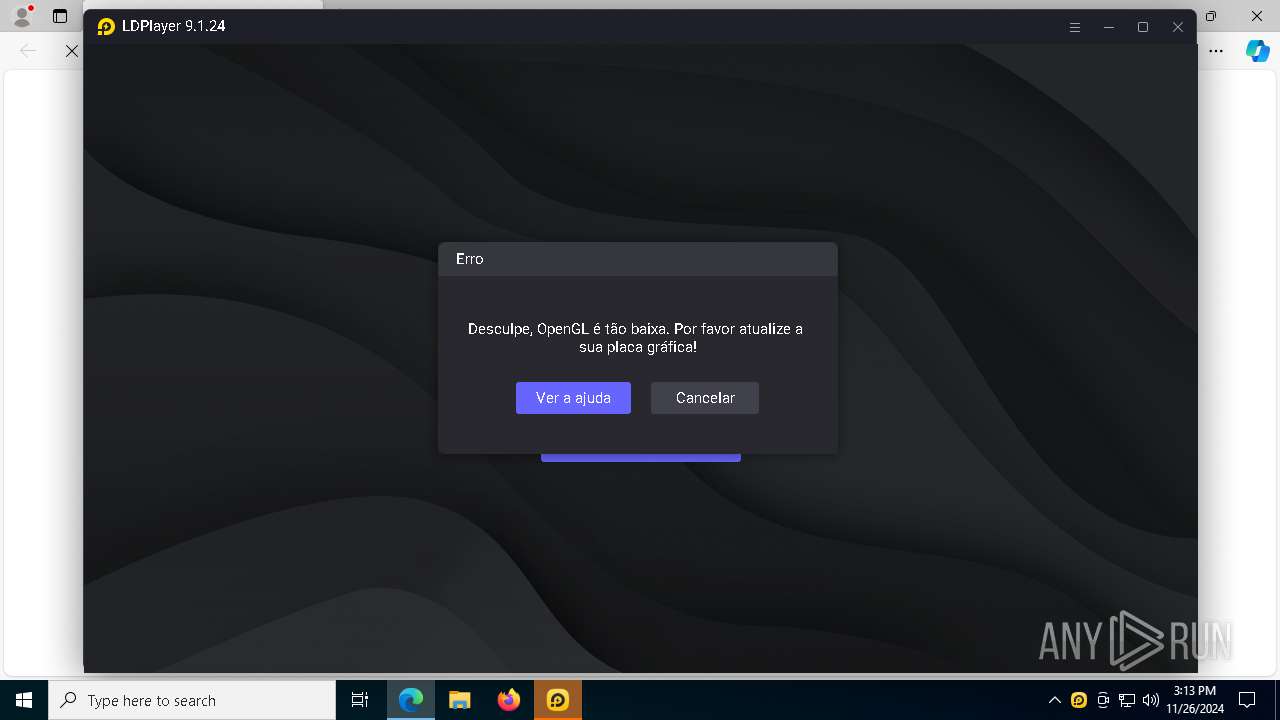
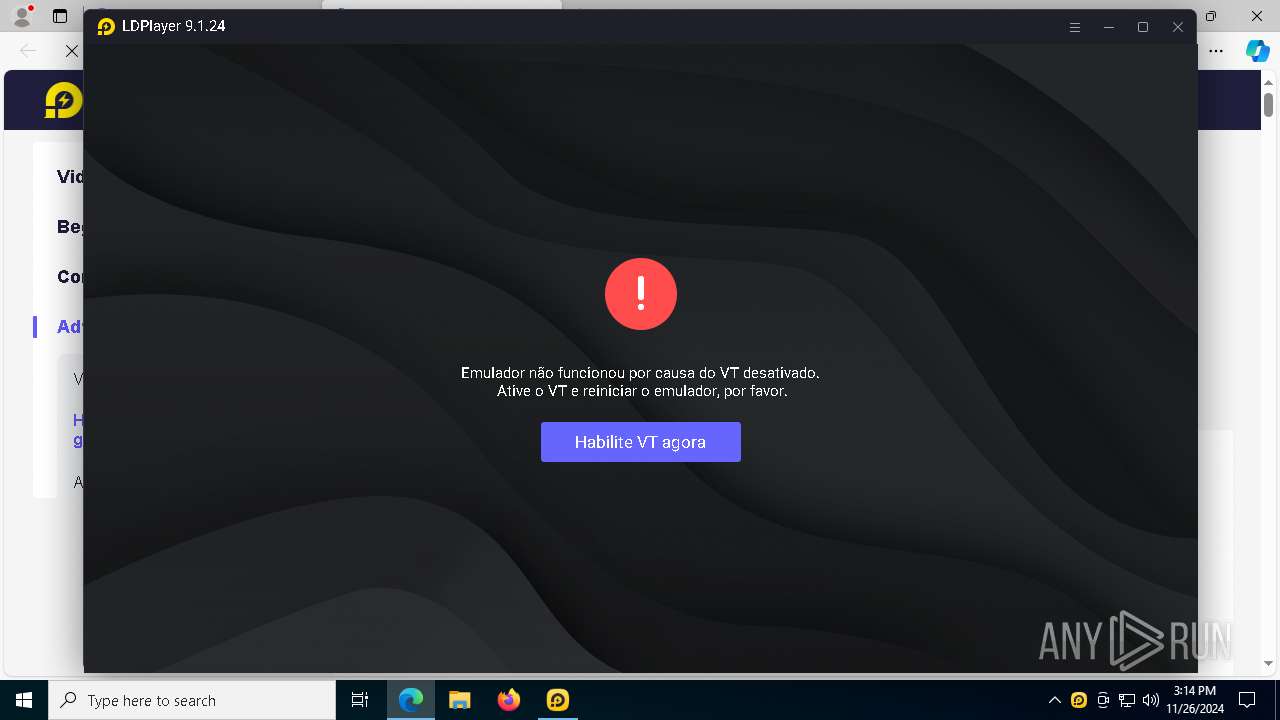
| File name: | LDPlayer9_pt_1008_ld.exe |
| Full analysis: | https://app.any.run/tasks/13025021-d35f-4be4-afb1-b4c35d8810bd |
| Verdict: | Malicious activity |
| Analysis date: | November 26, 2024, 15:09:12 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | 4B3458B9C6AAA39EF37FC290459B6908 |
| SHA1: | BA8B683ECA181784D049EFD008F50AACF5CF4079 |
| SHA256: | 9BB59EA13D91B11739E9EB8E39AB243D80935310838B0F60B450AC2A906AABEE |
| SSDEEP: | 98304:K1EQlUiLeiYxQKN5DooPUEUMoj4Flc891YtoAlVXm1M3cJRRL+rssQarhYfLrt2j:C |
MALICIOUS
Starts NET.EXE for service management
- dnrepairer.exe (PID: 1904)
- net.exe (PID: 5252)
Registers / Runs the DLL via REGSVR32.EXE
- dnrepairer.exe (PID: 1904)
SUSPICIOUS
Reads security settings of Internet Explorer
- LDPlayer9_pt_1008_ld.exe (PID: 6312)
Checks Windows Trust Settings
- LDPlayer9_pt_1008_ld.exe (PID: 6312)
Process drops legitimate windows executable
- LDPlayer.exe (PID: 2972)
- dnrepairer.exe (PID: 1904)
- dnplayer.exe (PID: 2076)
Executable content was dropped or overwritten
- LDPlayer.exe (PID: 2972)
- Dism.exe (PID: 6844)
- dnrepairer.exe (PID: 1904)
- dnplayer.exe (PID: 2076)
Drops 7-zip archiver for unpacking
- LDPlayer.exe (PID: 2972)
The process drops C-runtime libraries
- LDPlayer.exe (PID: 2972)
- dnplayer.exe (PID: 2076)
- dnrepairer.exe (PID: 1904)
Takes ownership (TAKEOWN.EXE)
- dnrepairer.exe (PID: 1904)
- LDPlayer.exe (PID: 2972)
Uses ICACLS.EXE to modify access control lists
- dnrepairer.exe (PID: 1904)
- LDPlayer.exe (PID: 2972)
Starts a Microsoft application from unusual location
- DismHost.exe (PID: 6984)
Drops a system driver (possible attempt to evade defenses)
- dnrepairer.exe (PID: 1904)
Starts POWERSHELL.EXE for commands execution
- dnrepairer.exe (PID: 1904)
INFO
Checks supported languages
- LDPlayer9_pt_1008_ld.exe (PID: 6312)
Creates files or folders in the user directory
- LDPlayer9_pt_1008_ld.exe (PID: 6312)
Reads the computer name
- LDPlayer9_pt_1008_ld.exe (PID: 6312)
Checks proxy server information
- LDPlayer9_pt_1008_ld.exe (PID: 6312)
Reads the software policy settings
- LDPlayer9_pt_1008_ld.exe (PID: 6312)
Reads the machine GUID from the registry
- LDPlayer9_pt_1008_ld.exe (PID: 6312)
Manual execution by a user
- msedge.exe (PID: 6956)
Application launched itself
- msedge.exe (PID: 3952)
- msedge.exe (PID: 6956)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:11:06 02:04:33+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 1216000 |
| InitializedDataSize: | 1440768 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xec908 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
Total processes
256
Monitored processes
120
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 520 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 732 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1016 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | sc.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 1080 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=2748 --field-trial-handle=2240,i,13695763631352937515,7938521398000395677,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 | |||||||||||||||
| 1192 | "C:\WINDOWS\system32\sc" start Ld9BoxSup | C:\Windows\SysWOW64\sc.exe | — | dnrepairer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1296 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1460 | "powershell.exe" New-NetFirewallRule -DisplayName "Ld9BoxSup" -Direction Inbound -Program 'C:\Program Files\ldplayer9box\Ld9BoxHeadless.exe' -RemoteAddress LocalSubnet -Action Allow | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | dnrepairer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1556 | sc query HvHost | C:\Windows\SysWOW64\sc.exe | — | dnrepairer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1732 | "regsvr32" "C:\Program Files\ldplayer9box\x86\VBoxClient-x86.dll" /s | C:\Windows\SysWOW64\regsvr32.exe | — | dnrepairer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1904 | "C:\LDPlayer\LDPlayer9\dnrepairer.exe" listener=459462 | C:\LDPlayer\LDPlayer9\dnrepairer.exe | LDPlayer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
57 164
Read events
56 683
Write events
452
Delete events
29
Modification events
| (PID) Process: | (6312) LDPlayer9_pt_1008_ld.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\lden |
| Operation: | write | Name: | pcmac |
Value: 0bc2376885b90fbc11f1e41ba75ee1e9 | |||
| (PID) Process: | (2972) LDPlayer.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\ld\dnplayer_en |
| Operation: | write | Name: | pcid |
Value: 0bc2376885b90fbc11f1e41ba75ee1e9 | |||
| (PID) Process: | (2232) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Cryptography\Providers\Trust\Usages\1.3.6.1.5.5.7.3.3 |
| Operation: | write | Name: | DefaultId |
Value: {00AAC56B-CD44-11D0-8CC2-00C04FC295EE} | |||
| (PID) Process: | (2232) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Cryptography\Providers\Trust\FinalPolicy\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE} |
| Operation: | write | Name: | $DLL |
Value: WINTRUST.DLL | |||
| (PID) Process: | (2232) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Cryptography\Providers\Trust\FinalPolicy\{00AAC56B-CD44-11D0-8CC2-00C04FC295EE} |
| Operation: | write | Name: | $Function |
Value: SoftpubAuthenticode | |||
| (PID) Process: | (2232) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Cryptography\Providers\Trust\Initialization\{64B9D180-8DA2-11CF-8736-00AA00A485EB} |
| Operation: | write | Name: | $DLL |
Value: WINTRUST.DLL | |||
| (PID) Process: | (2232) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Cryptography\Providers\Trust\Initialization\{64B9D180-8DA2-11CF-8736-00AA00A485EB} |
| Operation: | write | Name: | $Function |
Value: SoftpubInitialize | |||
| (PID) Process: | (2232) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Cryptography\Providers\Trust\Message\{64B9D180-8DA2-11CF-8736-00AA00A485EB} |
| Operation: | write | Name: | $DLL |
Value: WINTRUST.DLL | |||
| (PID) Process: | (2232) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Cryptography\Providers\Trust\Message\{64B9D180-8DA2-11CF-8736-00AA00A485EB} |
| Operation: | write | Name: | $Function |
Value: SoftpubLoadMessage | |||
| (PID) Process: | (2232) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Cryptography\Providers\Trust\Signature\{64B9D180-8DA2-11CF-8736-00AA00A485EB} |
| Operation: | write | Name: | $DLL |
Value: WINTRUST.DLL | |||
Executable files
476
Suspicious files
429
Text files
196
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6312 | LDPlayer9_pt_1008_ld.exe | C:\LDPlayer\LDPlayer9\LDPlayer.exe.tmp | — | |
MD5:— | SHA256:— | |||
| 6312 | LDPlayer9_pt_1008_ld.exe | C:\LDPlayer\LDPlayer9\LDPlayer.exe | — | |
MD5:— | SHA256:— | |||
| 2972 | LDPlayer.exe | C:\Users\admin\AppData\Roaming\XuanZhi\fonts\NotoSans-Regular.otf | — | |
MD5:— | SHA256:— | |||
| 2972 | LDPlayer.exe | C:\LDPlayer\LDPlayer9\data-3G.vmdk | — | |
MD5:— | SHA256:— | |||
| 2972 | LDPlayer.exe | C:\LDPlayer\LDPlayer9\data.vmdk | — | |
MD5:— | SHA256:— | |||
| 2972 | LDPlayer.exe | C:\LDPlayer\LDPlayer9\dnresource.rcc | — | |
MD5:— | SHA256:— | |||
| 6312 | LDPlayer9_pt_1008_ld.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B039FEA45CB4CC4BBACFC013C7C55604_32532FE6EE279C8A04951B3E75CC9341 | binary | |
MD5:D00EDAB366FF3E4A2E79009EFE044E5B | SHA256:B435A182648129DEDE839455B23D4378B5777167A02C1F4ADCD3233B839B8398 | |||
| 6312 | LDPlayer9_pt_1008_ld.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B039FEA45CB4CC4BBACFC013C7C55604_32532FE6EE279C8A04951B3E75CC9341 | der | |
MD5:6F59F72BB1503B8B577358C03E5467DA | SHA256:6FA74FF0E875140CD4E4B2BC586725DBE13ED447CDE3D191848009BECB909F5D | |||
| 6312 | LDPlayer9_pt_1008_ld.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\75CA58072B9926F763A91F0CC2798706_645BC4A49DCDC40FE5917FA45C6D4517 | binary | |
MD5:3A069FAA58703D00B63980026FDDBB9D | SHA256:3F6B5AF3EE309581DECFFF9E5F49C2A9773C0A598922D8EC3EA4BA06C6A0E9FC | |||
| 6312 | LDPlayer9_pt_1008_ld.exe | C:\Users\admin\AppData\Roaming\lddownloader_en\fonts\NanumGothicLight.otf | binary | |
MD5:E2E37D20B47D7EE294B91572F69E323A | SHA256:153161AB882DB768C70A753AF5E8129852B9C9CAE5511A23653BEB6414D834A2 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
17
TCP/UDP connections
130
DNS requests
174
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6312 | LDPlayer9_pt_1008_ld.exe | GET | 200 | 104.18.20.226:80 | http://ocsp2.globalsign.com/rootr3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCEH6Hwxq9kZ5xalNEESzfRqk%3D | unknown | — | — | whitelisted |
6312 | LDPlayer9_pt_1008_ld.exe | GET | 200 | 18.66.145.213:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEkzUBtJnwJkc3SmanzgxeYU%3D | unknown | — | — | unknown |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.166:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1544 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
7024 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7024 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2972 | LDPlayer.exe | GET | 301 | 13.32.99.62:80 | http://apipt.ldmnq.com/statisticsMnqEvent?sv=0900012401&openid=1008&m=0bc2376885b90fbc11f1e41ba75ee1e9&event_key=install&event_value=&event_type=player&z=1732633987 | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5732 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.166:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
1176 | svchost.exe | 20.190.159.2:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
6312 | LDPlayer9_pt_1008_ld.exe | 163.181.92.230:443 | res.ldrescdn.com | Zhejiang Taobao Network Co.,Ltd | DE | unknown |
6312 | LDPlayer9_pt_1008_ld.exe | 216.58.212.142:443 | www.google-analytics.com | GOOGLE | US | whitelisted |
6312 | LDPlayer9_pt_1008_ld.exe | 104.18.20.226:80 | ocsp2.globalsign.com | CLOUDFLARENET | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
res.ldrescdn.com |
| unknown |
www.google-analytics.com |
| whitelisted |
ocsp2.globalsign.com |
| whitelisted |
apipt.ldmnq.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
— | — | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
— | — | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
— | — | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
— | — | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
— | — | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
— | — | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
— | — | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
— | — | Misc activity | ET INFO Observed Discord Domain (discordapp .com in TLS SNI) |
— | — | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discordapp .com) |
Process | Message |
|---|---|
Dism.exe | PID=6844 TID=6864 Provider has not previously been encountered. Attempting to initialize the provider. - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=6844 TID=6864 Attempting to initialize the logger from the Image Session. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=6844 TID=6864 Loading Provider from location C:\WINDOWS\System32\Dism\LogProvider.dll - CDISMProviderStore::Internal_GetProvider |
Dism.exe | PID=6844 TID=6864 Instantiating the Provider Store. - CDISMImageSession::get_ProviderStore |
Dism.exe | PID=6844 TID=6864 Initializing a provider store for the LOCAL session type. - CDISMProviderStore::Final_OnConnect |
Dism.exe | PID=6844 TID=6864 Connecting to the provider located at C:\WINDOWS\System32\Dism\LogProvider.dll. - CDISMProviderStore::Internal_LoadProvider |
DismHost.exe | PID=6984 TID=4984 Disconnecting the provider store - CDISMImageSession::Final_OnDisconnect |
DismHost.exe | PID=6984 TID=4984 Encountered a loaded provider DISMLogger. - CDISMProviderStore::Internal_DisconnectProvider |
DismHost.exe | PID=6984 TID=4984 Disconnecting Provider: DISMLogger - CDISMProviderStore::Internal_DisconnectProvider |
Dism.exe | PID=6844 TID=6864 Encountered a loaded provider DISMLogger. - CDISMProviderStore::Internal_DisconnectProvider |