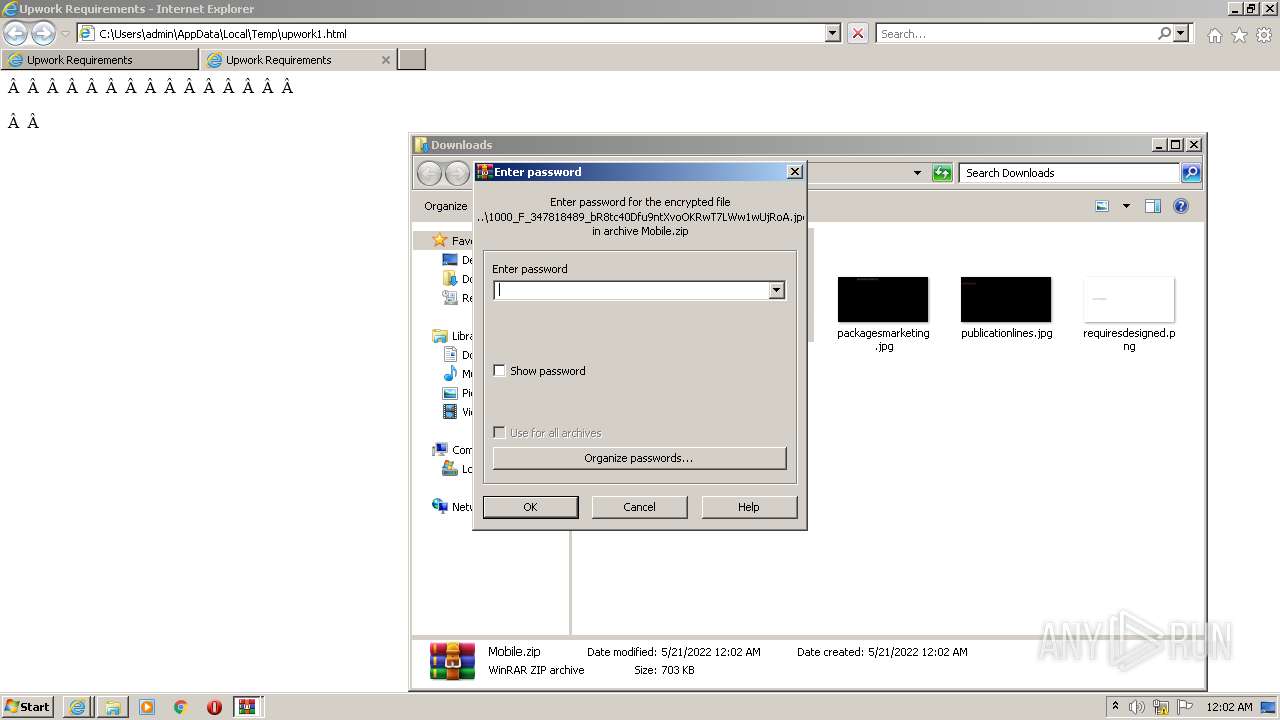
| download: | upwork1 |
| Full analysis: | https://app.any.run/tasks/7a404c7f-6182-4b75-976e-215e6c3da662 |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2022, 23:02:07 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/html |
| File info: | HTML document, UTF-8 Unicode text, with CRLF line terminators |
| MD5: | B8DD5BBB5B79D1CBE0350452574F155A |
| SHA1: | 3E60BF86E873E03D6C65E2BEAE8D32668562359B |
| SHA256: | 9BAE55F07001A9268E1C4F8612671D19594BB31D699C6813A3206FA6A7808770 |
| SSDEEP: | 6:h4QboY+oMOO2Rg9AtJav1uZKaoJTwMGNAFKUYUHPGb:hPQofRgitoao5cUVPGb |
MALICIOUS
Drops executable file immediately after starts
- WinRAR.exe (PID: 3184)
Application was dropped or rewritten from another process
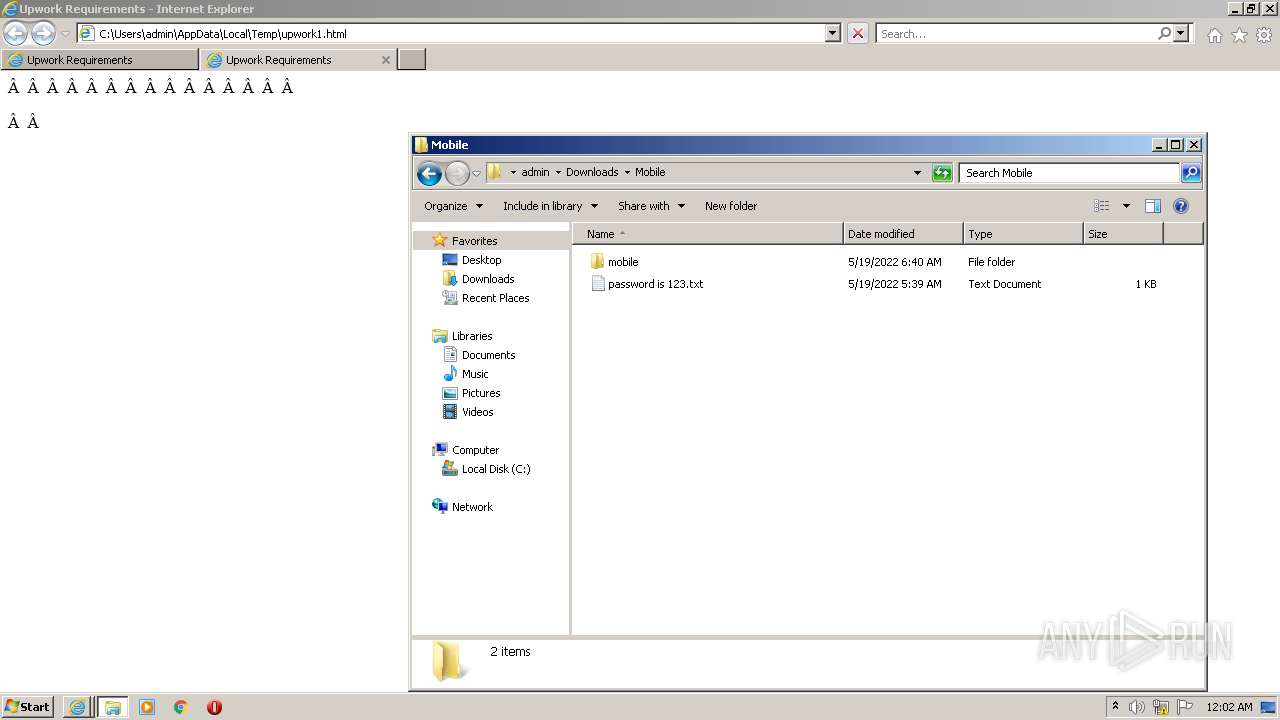
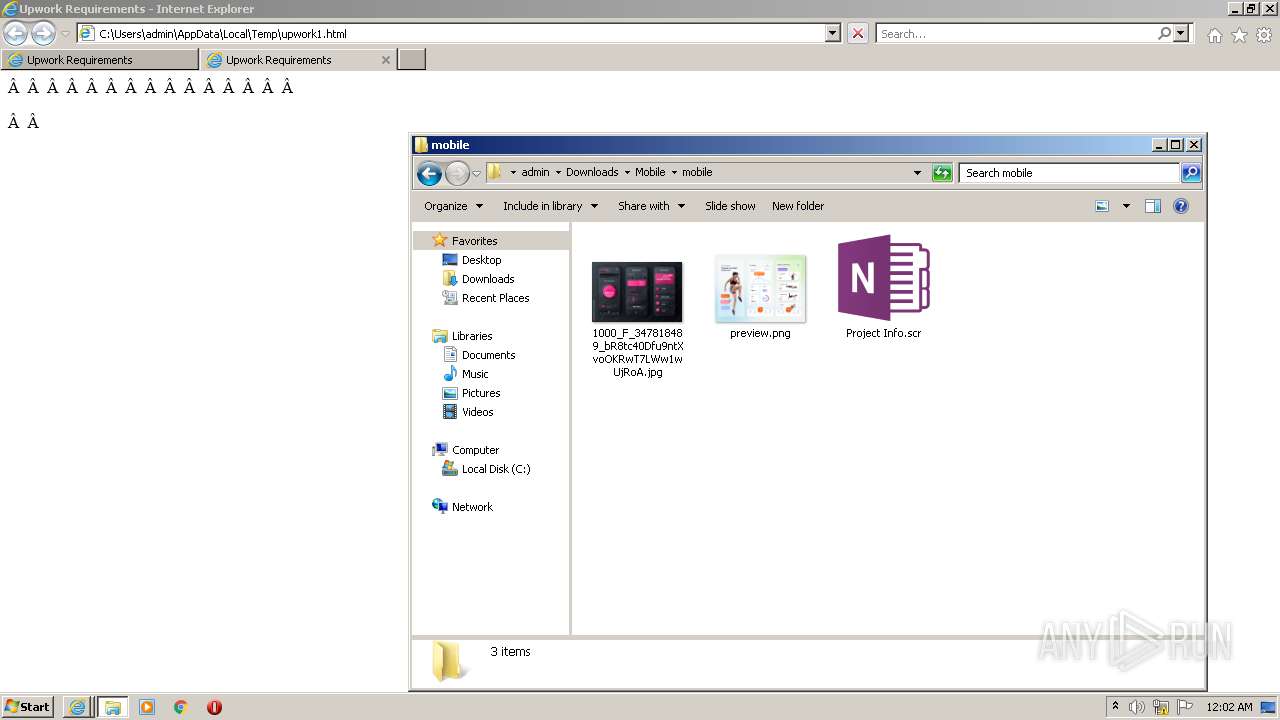
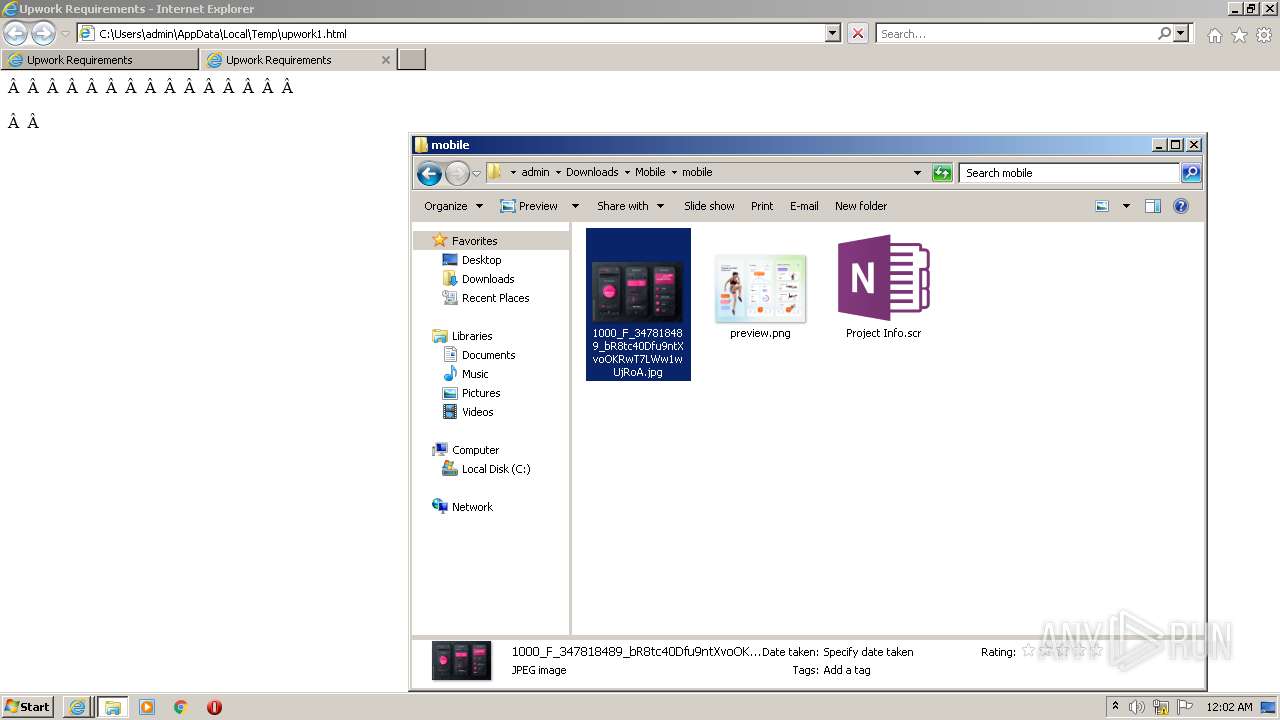
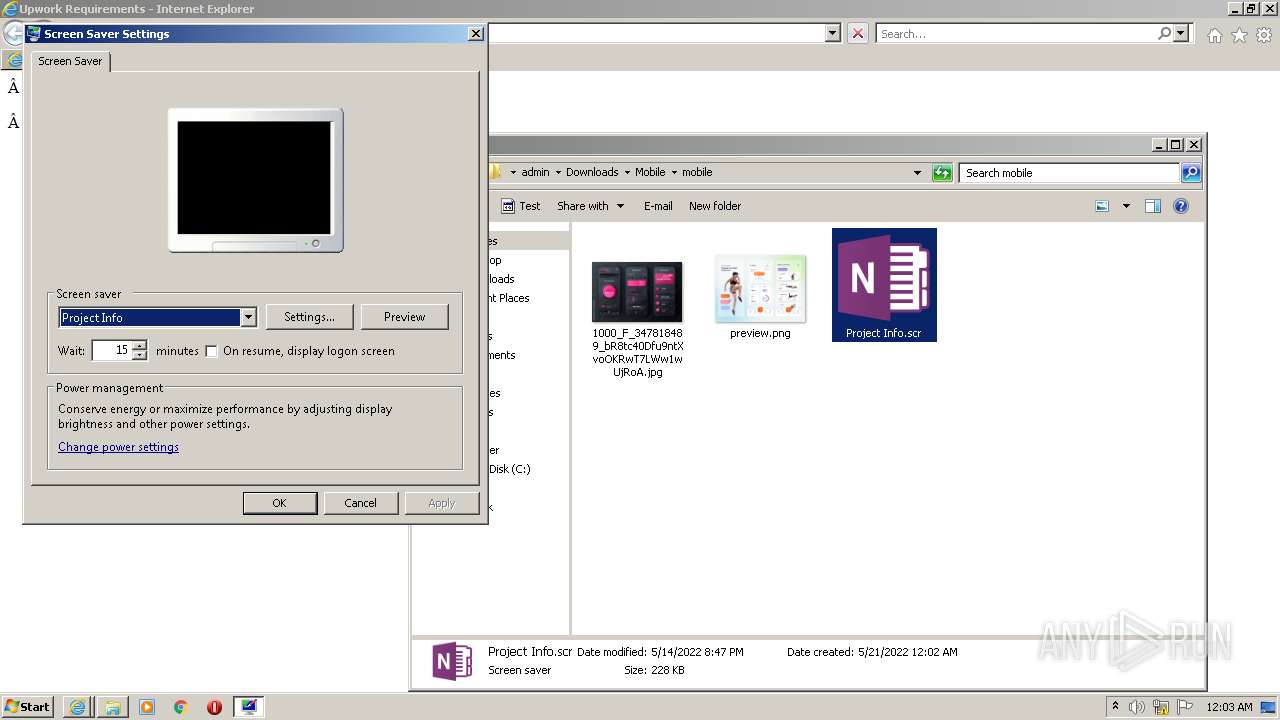
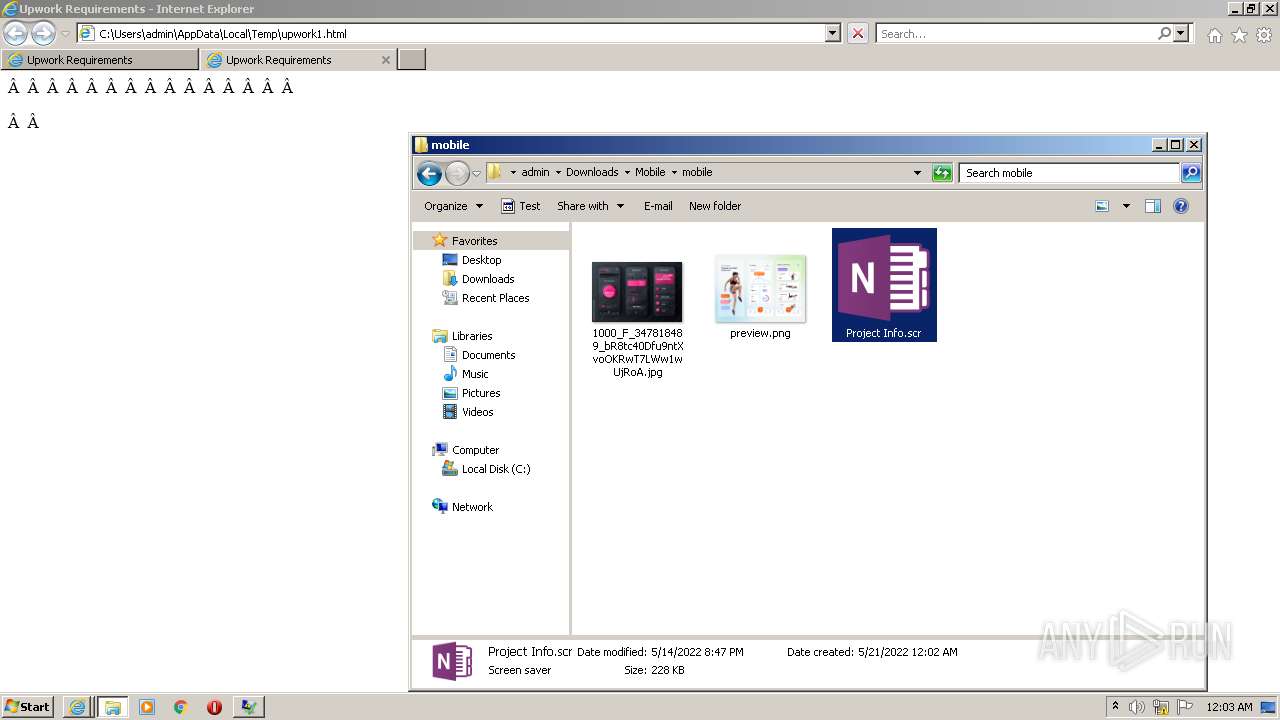
- Project Info.scr (PID: 2480)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 3808)
- iexplore.exe (PID: 2280)
- iexplore.exe (PID: 3772)
Checks supported languages
- WinRAR.exe (PID: 3184)
- Project Info.scr (PID: 2480)
Drops a file with a compile date too recent
- WinRAR.exe (PID: 3184)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3184)
Starts application with an unusual extension
- rundll32.exe (PID: 3092)
Reads the computer name
- WinRAR.exe (PID: 3184)
- Project Info.scr (PID: 2480)
Executed via COM
- DllHost.exe (PID: 3800)
Reads Environment values
- Project Info.scr (PID: 2480)
INFO
Checks supported languages
- iexplore.exe (PID: 924)
- iexplore.exe (PID: 3808)
- iexplore.exe (PID: 3772)
- iexplore.exe (PID: 2280)
- DllHost.exe (PID: 3800)
- rundll32.exe (PID: 3092)
Reads the computer name
- iexplore.exe (PID: 924)
- iexplore.exe (PID: 3772)
- iexplore.exe (PID: 3808)
- iexplore.exe (PID: 2280)
- DllHost.exe (PID: 3800)
- rundll32.exe (PID: 3092)
Application launched itself
- iexplore.exe (PID: 924)
- iexplore.exe (PID: 3808)
Changes internet zones settings
- iexplore.exe (PID: 924)
Reads internet explorer settings
- iexplore.exe (PID: 3808)
- iexplore.exe (PID: 2280)
Checks Windows Trust Settings
- iexplore.exe (PID: 3772)
- iexplore.exe (PID: 924)
- iexplore.exe (PID: 3808)
- iexplore.exe (PID: 2280)
Reads settings of System Certificates
- iexplore.exe (PID: 3772)
- iexplore.exe (PID: 924)
- Project Info.scr (PID: 2480)
- iexplore.exe (PID: 2280)
- iexplore.exe (PID: 3808)
Modifies the phishing filter of IE
- iexplore.exe (PID: 924)
Manual execution by user
- WinRAR.exe (PID: 3184)
- rundll32.exe (PID: 3092)
Creates files in the user directory
- iexplore.exe (PID: 924)
Changes settings of System certificates
- iexplore.exe (PID: 924)
Adds / modifies Windows certificates
- iexplore.exe (PID: 924)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .html | | | HyperText Markup Language (100) |
|---|
EXIF
HTML
| Refresh: | 2; url = https://zarkai.com/upwork1/Mobile.zip |
|---|---|
| Title: | Upwork Requirements |
Total processes
47
Monitored processes
8
Malicious processes
0
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 924 | "C:\Program Files\Internet Explorer\iexplore.exe" "C:\Users\admin\AppData\Local\Temp\upwork1.html" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2280 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:924 CREDAT:144390 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
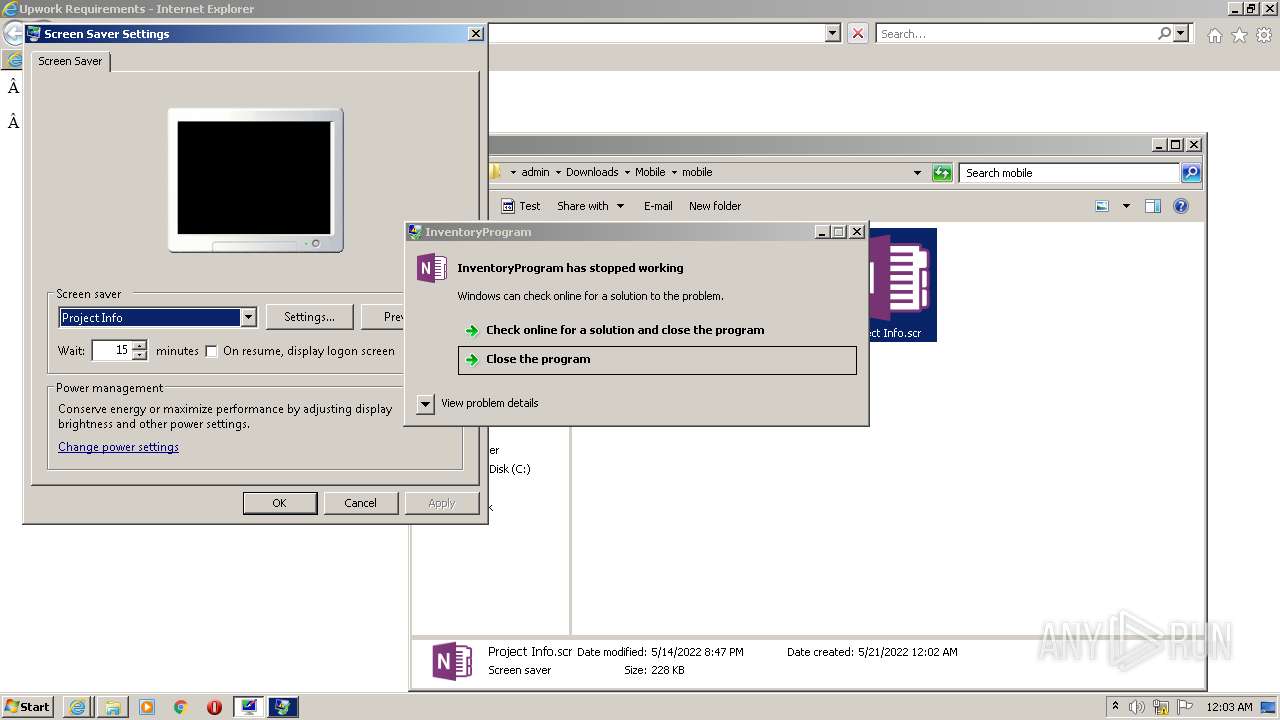
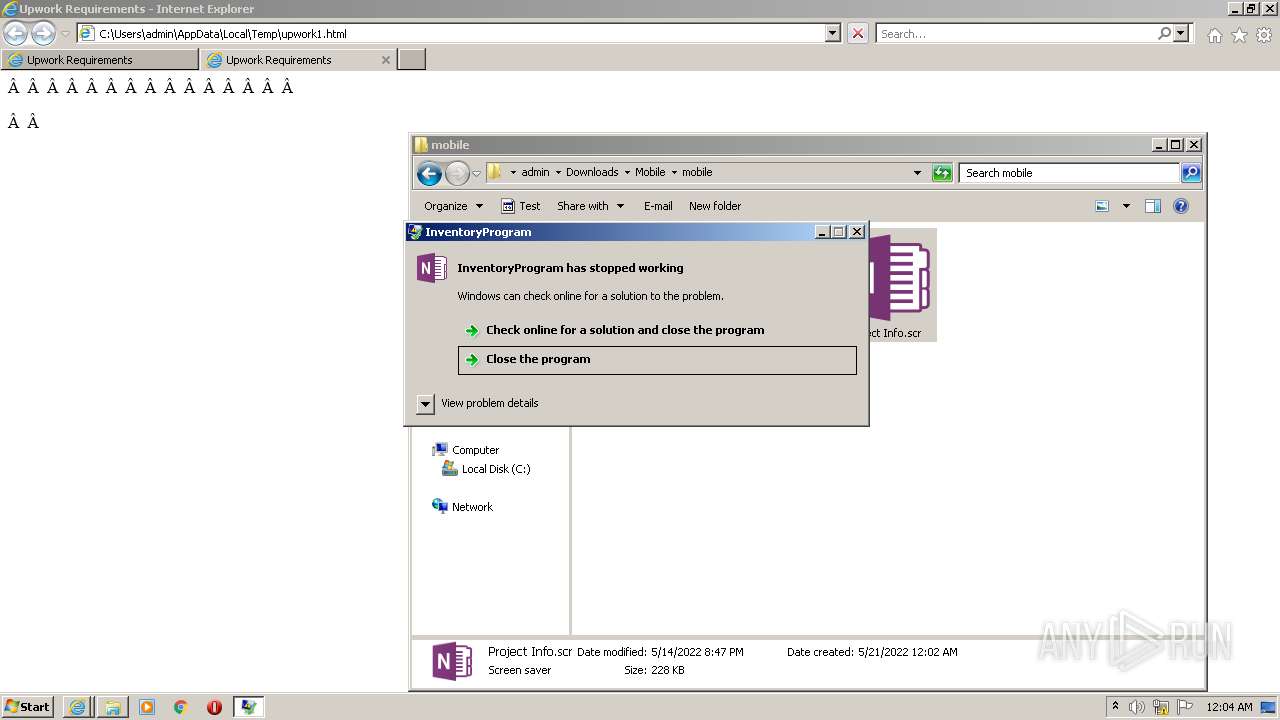
| 2480 | "C:\Users\admin\Downloads\Mobile\mobile\Project Info.scr" /p 262846 | C:\Users\admin\Downloads\Mobile\mobile\Project Info.scr | rundll32.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: InventoryProgram Exit code: 3762504530 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3092 | "rundll32.exe" desk.cpl,InstallScreenSaver C:\Users\admin\Downloads\Mobile\mobile\Project Info.scr | C:\Windows\system32\rundll32.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3184 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Downloads\Mobile.zip" C:\Users\admin\Downloads\Mobile\ | C:\Program Files\WinRAR\WinRAR.exe | Explorer.EXE | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3772 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:924 CREDAT:333057 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3800 | C:\Windows\system32\DllHost.exe /Processid:{76D0CB12-7604-4048-B83C-1005C7DDC503} | C:\Windows\system32\DllHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: COM Surrogate Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3808 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:924 CREDAT:144385 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
22 613
Read events
22 306
Write events
305
Delete events
2
Modification events
| (PID) Process: | (924) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (924) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (924) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30960797 | |||
| (PID) Process: | (924) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (924) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30960797 | |||
| (PID) Process: | (924) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (924) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (924) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (924) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (924) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
1
Suspicious files
17
Text files
22
Unknown types
9
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3772 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3772 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_2DBE917624E9880FE0C7C5570D56E691 | binary | |
MD5:— | SHA256:— | |||
| 3772 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\5080DC7A65DB6A5960ECD874088F3328_862BA1770B2FEE013603D2FF9ABEAFDA | binary | |
MD5:— | SHA256:— | |||
| 3772 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_2DBE917624E9880FE0C7C5570D56E691 | der | |
MD5:— | SHA256:— | |||
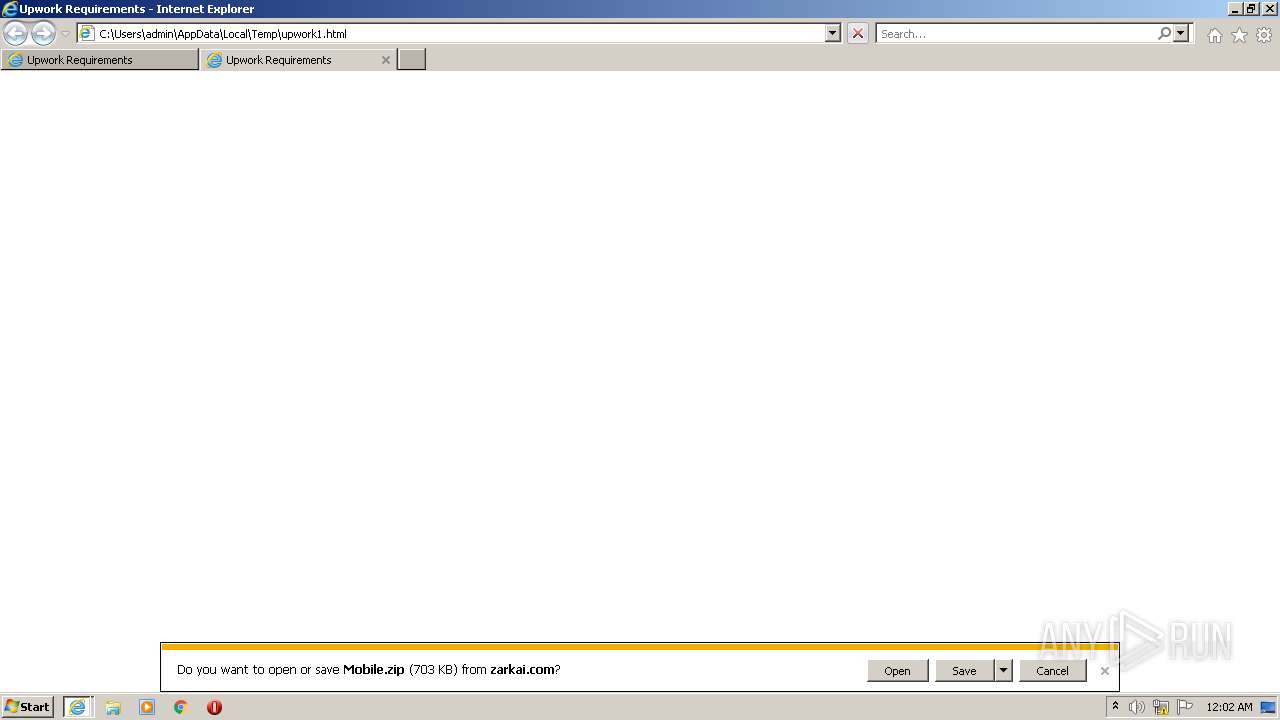
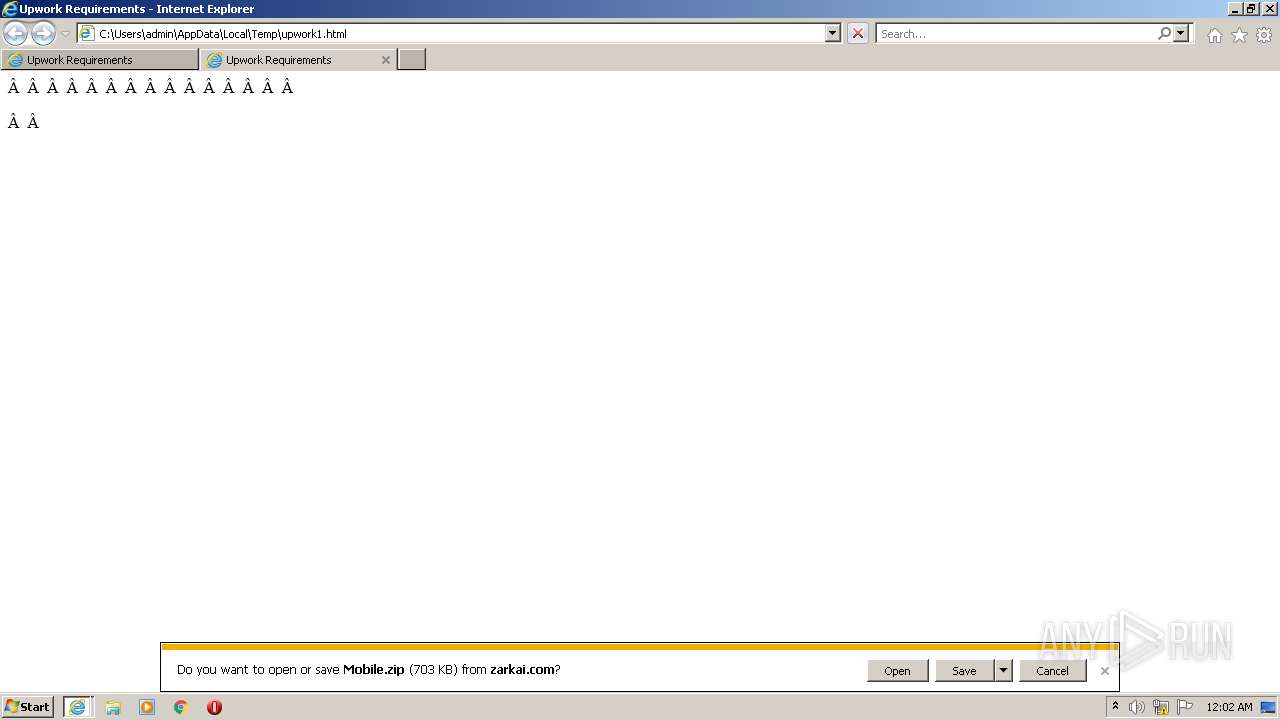
| 3772 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\Mobile[1].zip | compressed | |
MD5:— | SHA256:— | |||
| 3772 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\5080DC7A65DB6A5960ECD874088F3328_862BA1770B2FEE013603D2FF9ABEAFDA | der | |
MD5:— | SHA256:— | |||
| 924 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\~DF8125D221BF659078.TMP | gmc | |
MD5:— | SHA256:— | |||
| 3772 | iexplore.exe | C:\Users\admin\Downloads\Mobile.zip.e6xmxbi.partial | compressed | |
MD5:— | SHA256:— | |||
| 924 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6BADA8974A10C4BD62CC921D13E43B18_711ED44619924BA6DC33E69F97E7FF63 | der | |
MD5:— | SHA256:— | |||
| 924 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\Recovery\Active\{E212BF9B-D890-11EC-8695-18C4897E77EE}.dat | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
24
DNS requests
34
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3772 | iexplore.exe | GET | 200 | 172.64.155.188:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEGfe9D7xe9riT%2FWUBgbSwIQ%3D | US | der | 471 b | whitelisted |
924 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?e8b2a2d22bb01ab4 | US | compressed | 4.70 Kb | whitelisted |
3772 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?790639385af19279 | US | compressed | 4.70 Kb | whitelisted |
924 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?1e99a519cecb2e10 | US | compressed | 4.70 Kb | whitelisted |
3772 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9821b281a62b84bb | US | compressed | 4.70 Kb | whitelisted |
924 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
924 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | US | der | 471 b | whitelisted |
3772 | iexplore.exe | GET | 200 | 172.64.155.188:80 | http://ocsp.comodoca.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBReAhtobFzTvhaRmVeJ38QUchY9AwQUu69%2BAj36pvE8hI6t7jiY7NkyMtQCEQDwHUvue3yjezwFZqwFlyRY | US | der | 728 b | whitelisted |
924 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3772 | iexplore.exe | 95.111.231.140:443 | zarkai.com | Intertelecom Ltd | UA | unknown |
924 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
924 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
924 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
924 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2480 | Project Info.scr | 180.188.192.80:443 | burgercircus.com.hk | i-System Technology Limited | HK | unknown |
3808 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2280 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
924 | iexplore.exe | 204.79.197.203:443 | www.msn.com | Microsoft Corporation | US | malicious |
924 | iexplore.exe | 23.222.48.85:443 | go.microsoft.com | Akamai Technologies, Inc. | NL | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
zarkai.com |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
burgercircus.com.hk |
| unknown |
ieonline.microsoft.com |
| whitelisted |