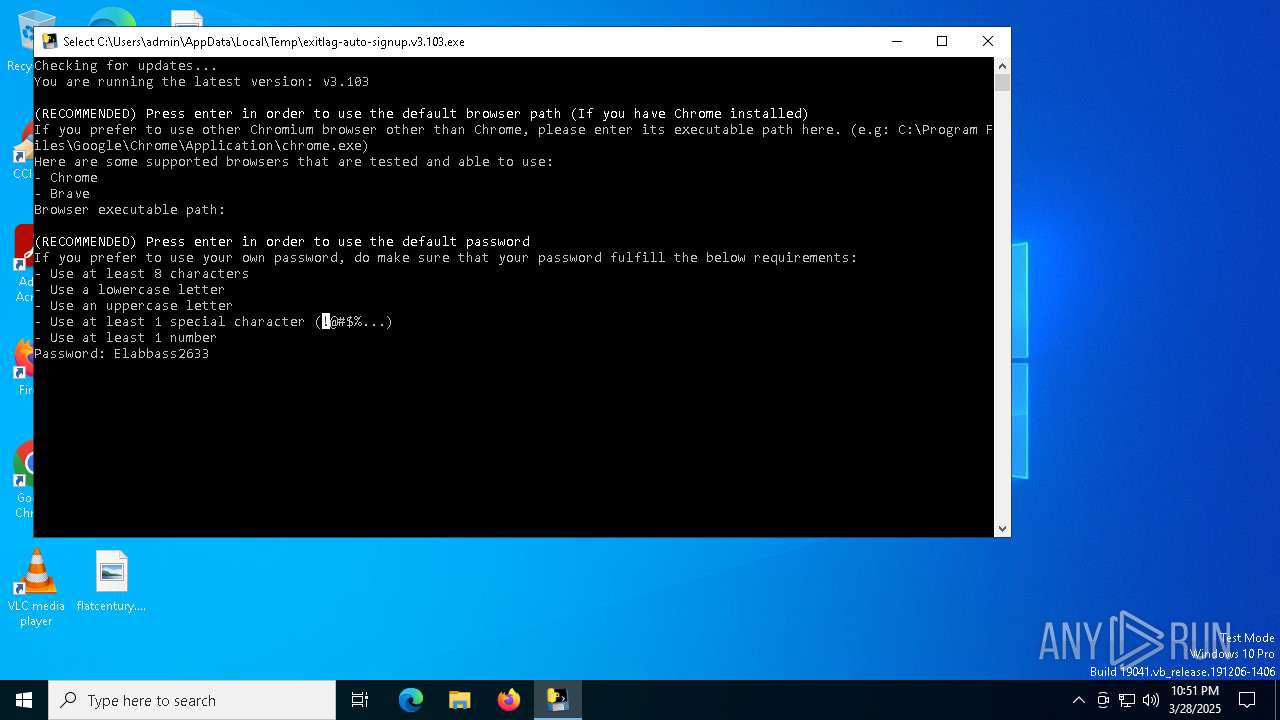
| File name: | exitlag-auto-signup.v3.103.exe |
| Full analysis: | https://app.any.run/tasks/6b6d6a39-6e46-46c0-ae17-333820df83d6 |
| Verdict: | Malicious activity |
| Analysis date: | March 28, 2025, 22:50:44 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 6 sections |
| MD5: | CE82270238D0F2EC90FFDD7755518611 |
| SHA1: | 7E83DCB4095C303C9474BC135595EE1ECDEABD96 |
| SHA256: | 9BA8642FD18A71DBD71A60EC5F25868A55AB4D5F0794E5E4015B1C7DC37073EE |
| SSDEEP: | 98304:kIyDeOUu8M4HmOVWjtKhtgADSptBNm9XLDbenkuA83wpYp2twVHHZPthn6YDEp1w:ez8YCXmMI54V3pIwf3495PEbZ |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops python dynamic module
- exitlag-auto-signup.v3.103.exe (PID: 1300)
Process drops legitimate windows executable
- exitlag-auto-signup.v3.103.exe (PID: 1300)
Application launched itself
- exitlag-auto-signup.v3.103.exe (PID: 1300)
Executable content was dropped or overwritten
- exitlag-auto-signup.v3.103.exe (PID: 1300)
The process drops C-runtime libraries
- exitlag-auto-signup.v3.103.exe (PID: 1300)
Starts CMD.EXE for commands execution
- exitlag-auto-signup.v3.103.exe (PID: 6972)
Loads Python modules
- exitlag-auto-signup.v3.103.exe (PID: 6972)
INFO
Checks supported languages
- exitlag-auto-signup.v3.103.exe (PID: 1300)
- exitlag-auto-signup.v3.103.exe (PID: 6972)
The sample compiled with english language support
- exitlag-auto-signup.v3.103.exe (PID: 1300)
Reads the computer name
- exitlag-auto-signup.v3.103.exe (PID: 1300)
- exitlag-auto-signup.v3.103.exe (PID: 6972)
Create files in a temporary directory
- exitlag-auto-signup.v3.103.exe (PID: 1300)
- exitlag-auto-signup.v3.103.exe (PID: 6972)
Reads the machine GUID from the registry
- exitlag-auto-signup.v3.103.exe (PID: 6972)
Checks proxy server information
- exitlag-auto-signup.v3.103.exe (PID: 6972)
- BackgroundTransferHost.exe (PID: 1388)
Checks operating system version
- exitlag-auto-signup.v3.103.exe (PID: 6972)
PyInstaller has been detected (YARA)
- exitlag-auto-signup.v3.103.exe (PID: 1300)
Reads security settings of Internet Explorer
- BackgroundTransferHost.exe (PID: 1196)
- BackgroundTransferHost.exe (PID: 1388)
- BackgroundTransferHost.exe (PID: 6388)
- BackgroundTransferHost.exe (PID: 300)
- BackgroundTransferHost.exe (PID: 4040)
Reads the software policy settings
- BackgroundTransferHost.exe (PID: 1388)
Creates files or folders in the user directory
- BackgroundTransferHost.exe (PID: 1388)
Drops encrypted JS script (Microsoft Script Encoder)
- exitlag-auto-signup.v3.103.exe (PID: 6972)
Application launched itself
- chrome.exe (PID: 6272)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2025:03:28 05:03:41+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.41 |
| CodeSize: | 176640 |
| InitializedDataSize: | 152576 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xc320 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows command line |
Total processes
184
Monitored processes
54
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 456 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | exitlag-auto-signup.v3.103.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 896 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Local\Temp\DrissionPage\autoPortData\34975" --no-appcompat-clear --remote-debugging-port=34975 --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=14 --mojo-platform-channel-handle=4896 --field-trial-handle=1924,i,18389647956977518349,6210703572714593118,262144 --disable-features=PrivacySandboxSettings4 --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1196 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1300 | "C:\Users\admin\AppData\Local\Temp\exitlag-auto-signup.v3.103.exe" | C:\Users\admin\AppData\Local\Temp\exitlag-auto-signup.v3.103.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 1388 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2516 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Local\Temp\DrissionPage\autoPortData\34975" --extension-process --no-appcompat-clear --remote-debugging-port=34975 --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=9 --mojo-platform-channel-handle=3844 --field-trial-handle=1924,i,18389647956977518349,6210703572714593118,262144 --disable-features=PrivacySandboxSettings4 --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 3140 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Local\Temp\DrissionPage\autoPortData\34975" --no-appcompat-clear --remote-debugging-port=34975 --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=12 --mojo-platform-channel-handle=3640 --field-trial-handle=1924,i,18389647956977518349,6210703572714593118,262144 --disable-features=PrivacySandboxSettings4 --variations-seed-version /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 4040 | "BackgroundTransferHost.exe" -ServerName:BackgroundTransferHost.1 | C:\Windows\System32\BackgroundTransferHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Download/Upload Host Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4068 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Local\Temp\DrissionPage\autoPortData\34975" --extension-process --no-appcompat-clear --remote-debugging-port=34975 --disable-databases --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --mojo-platform-channel-handle=4504 --field-trial-handle=1924,i,18389647956977518349,6210703572714593118,262144 --disable-features=PrivacySandboxSettings4 --variations-seed-version /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
Total events
13 811
Read events
13 778
Write events
31
Delete events
2
Modification events
| (PID) Process: | (1196) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1196) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1196) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1388) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1388) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1388) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6388) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6388) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (6388) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (300) BackgroundTransferHost.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\CurrentVersion\AppContainer\Storage\microsoft.windows.contentdeliverymanager_cw5n1h2txyewy\Internet Settings\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
Executable files
76
Suspicious files
230
Text files
98
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1300 | exitlag-auto-signup.v3.103.exe | C:\Users\admin\AppData\Local\Temp\_MEI13002\_bz2.pyd | executable | |
MD5:86D1B2A9070CD7D52124126A357FF067 | SHA256:62173A8FADD4BF4DD71AB89EA718754AA31620244372F0C5BBBAE102E641A60E | |||
| 1300 | exitlag-auto-signup.v3.103.exe | C:\Users\admin\AppData\Local\Temp\_MEI13002\_lzma.pyd | executable | |
MD5:7447EFD8D71E8A1929BE0FAC722B42DC | SHA256:60793C8592193CFBD00FD3E5263BE4315D650BA4F9E4FDA9C45A10642FD998BE | |||
| 1300 | exitlag-auto-signup.v3.103.exe | C:\Users\admin\AppData\Local\Temp\_MEI13002\_hashlib.pyd | executable | |
MD5:D4674750C732F0DB4C4DD6A83A9124FE | SHA256:CAA4D2F8795E9A55E128409CC016E2CC5C694CB026D7058FC561E4DD131ED1C9 | |||
| 1300 | exitlag-auto-signup.v3.103.exe | C:\Users\admin\AppData\Local\Temp\_MEI13002\_socket.pyd | executable | |
MD5:819166054FEC07EFCD1062F13C2147EE | SHA256:E6DEB751039CD5424A139708475CE83F9C042D43E650765A716CB4A924B07E4F | |||
| 1300 | exitlag-auto-signup.v3.103.exe | C:\Users\admin\AppData\Local\Temp\_MEI13002\api-ms-win-core-console-l1-1-0.dll | executable | |
MD5:9F746F4F7D845F063FEA3C37DCEBC27C | SHA256:88ACE577A9C51061CB7D1A36BABBBEFA48212FADC838FFDE98FDFFF60DE18386 | |||
| 1300 | exitlag-auto-signup.v3.103.exe | C:\Users\admin\AppData\Local\Temp\_MEI13002\_ssl.pyd | executable | |
MD5:7910FB2AF40E81BEE211182CFFEC0A06 | SHA256:D2A7999E234E33828888AD455BAA6AB101D90323579ABC1095B8C42F0F723B6F | |||
| 1300 | exitlag-auto-signup.v3.103.exe | C:\Users\admin\AppData\Local\Temp\_MEI13002\_sqlite3.pyd | executable | |
MD5:5279D497EEE4CF269D7B4059C72B14C2 | SHA256:B298A44AF162BE7107FD187F04B63FB3827F1374594E22910EC38829DA7A12DC | |||
| 1300 | exitlag-auto-signup.v3.103.exe | C:\Users\admin\AppData\Local\Temp\_MEI13002\api-ms-win-core-debug-l1-1-0.dll | executable | |
MD5:226A5983AE2CBBF0C1BDA85D65948ABC | SHA256:591358EB4D1531E9563EE0813E4301C552CE364C912CE684D16576EABF195DC3 | |||
| 1300 | exitlag-auto-signup.v3.103.exe | C:\Users\admin\AppData\Local\Temp\_MEI13002\api-ms-win-core-datetime-l1-1-0.dll | executable | |
MD5:8F8EB9CB9E78E3A611BC8ACAEC4399CB | SHA256:1BD81DFD19204B44662510D9054852FB77C9F25C1088D647881C9B976CC16818 | |||
| 1300 | exitlag-auto-signup.v3.103.exe | C:\Users\admin\AppData\Local\Temp\_MEI13002\api-ms-win-core-fibers-l1-1-0.dll | executable | |
MD5:B5E2760C5A46DBEB8AE18C75F335707E | SHA256:91D249D7BC0E38EF6BCB17158B1FDC6DD8888DC086615C9B8B750B87E52A5FB3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
40
DNS requests
39
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
3888 | backgroundTaskHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
1388 | BackgroundTransferHost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
4892 | chrome.exe | GET | 302 | 142.250.184.238:80 | http://redirector.gvt1.com/edgedl/chromewebstore/L2Nocm9tZV9leHRlbnNpb24vYmxvYnMvNzI0QUFXNV9zT2RvdUwyMERESEZGVmJnQQ/1.0.0.6_nmmhkkegccagdldgiimedpiccmgmieda.crx | unknown | — | — | whitelisted |
1096 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 184.24.77.29:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1096 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7012 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 184.24.77.29:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.172.255.217:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
6972 | exitlag-auto-signup.v3.103.exe | 140.82.121.5:443 | api.github.com | GITHUB | US | whitelisted |
6544 | svchost.exe | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3888 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
api.github.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
arc.msn.com |
| whitelisted |
www.bing.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |