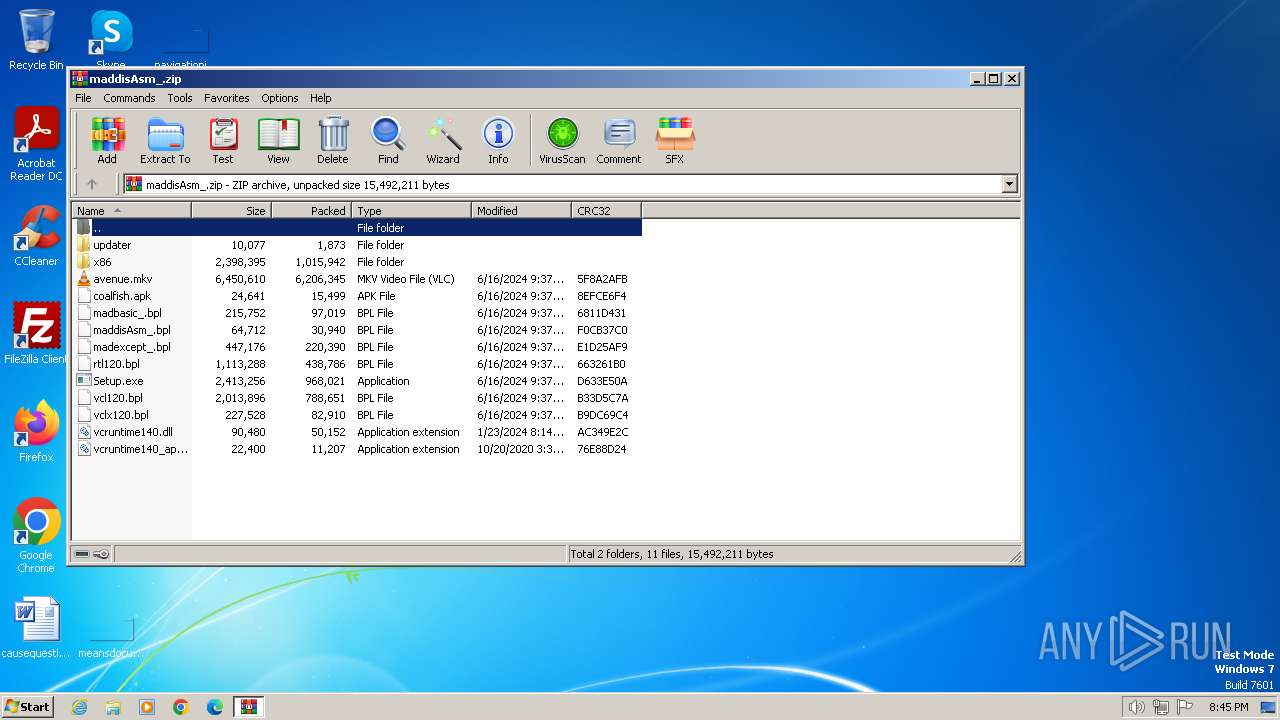
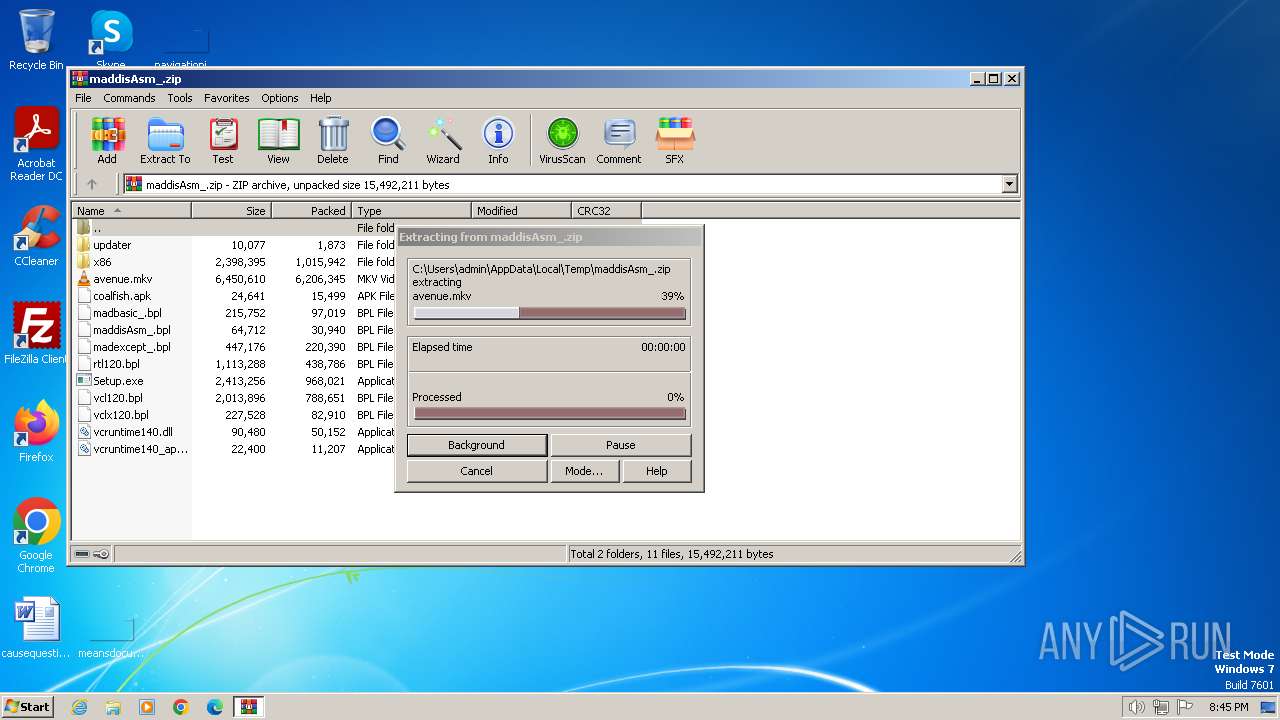
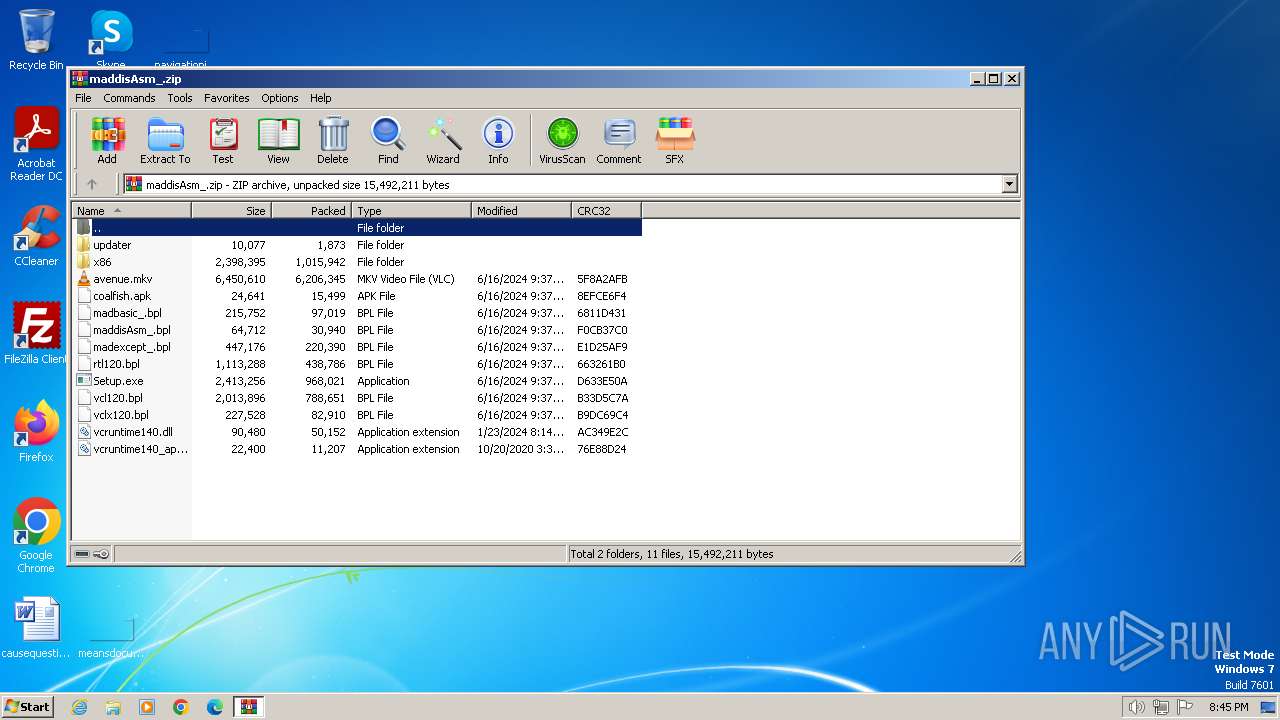
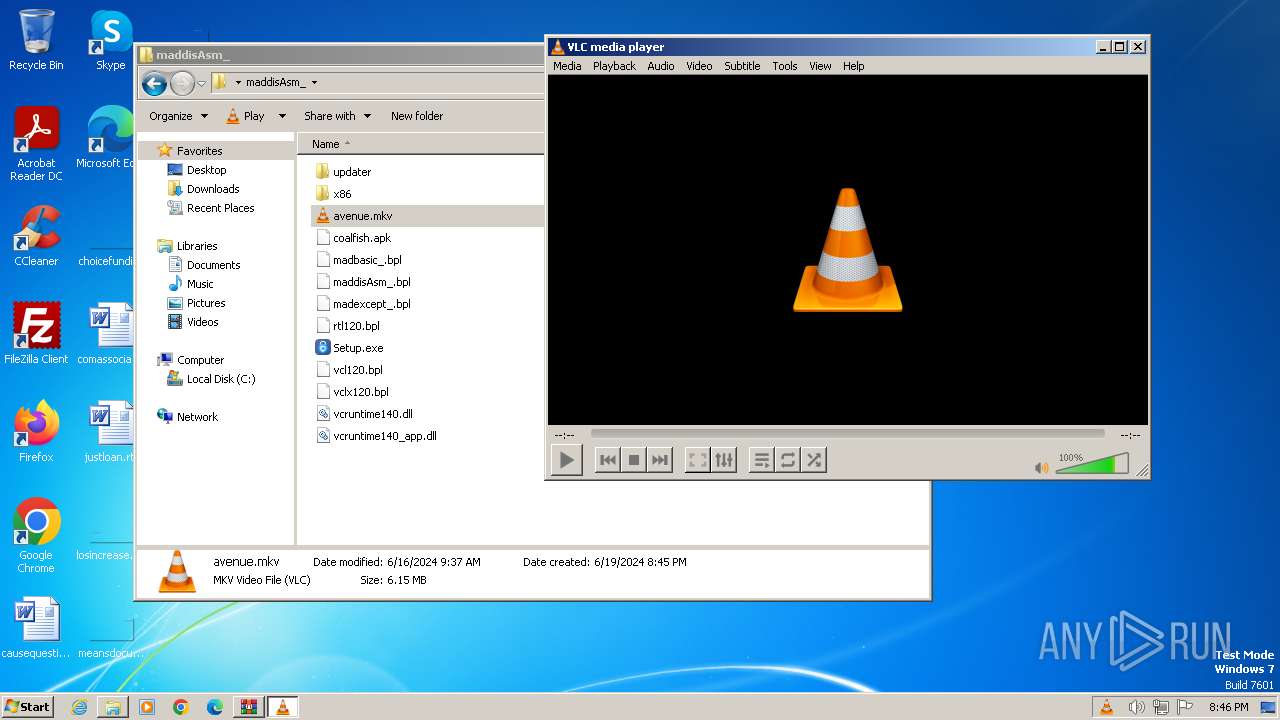
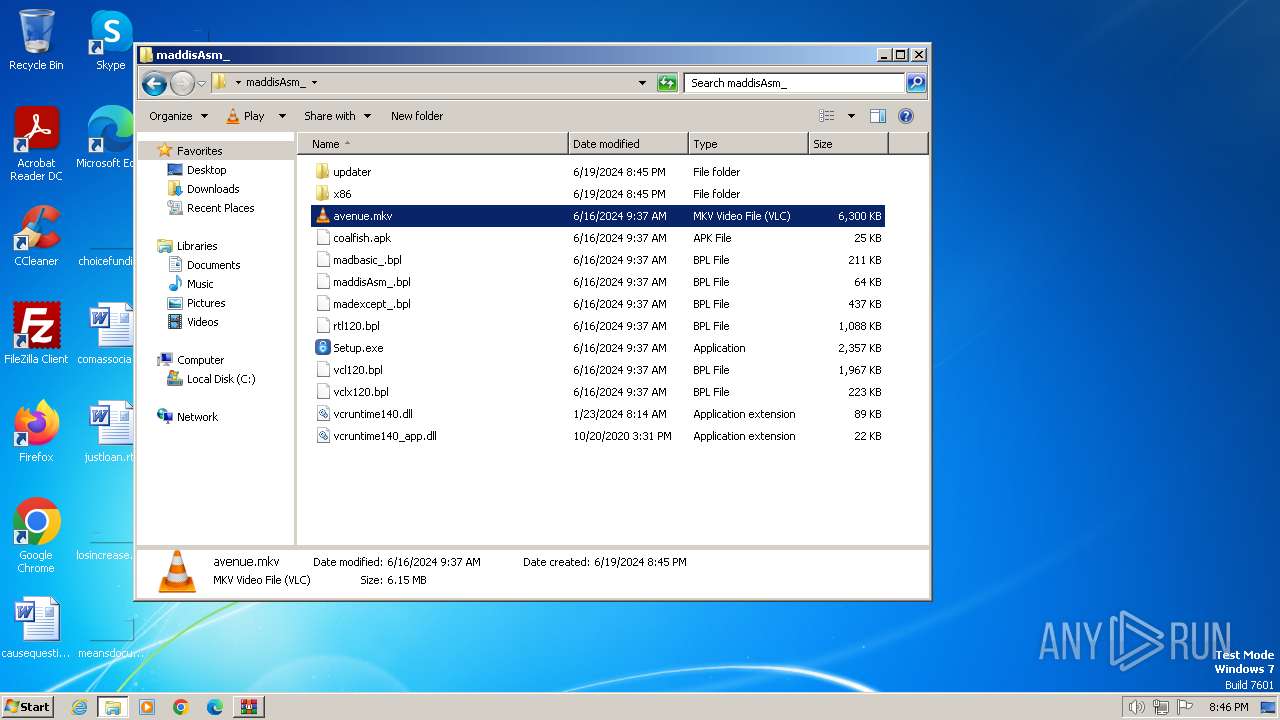
| File name: | maddisAsm_.zip |
| Full analysis: | https://app.any.run/tasks/67fb316b-ee2c-4217-8914-1e888f9994a7 |
| Verdict: | Malicious activity |
| Analysis date: | June 19, 2024, 19:45:20 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 5260B97EBCEFF9DB455F1A501EC80479 |
| SHA1: | A160598FCEC1A1813B8F30196B53C4E71F95A4D3 |
| SHA256: | 9BA7496463D47C72BC0A4B3B9AB4B58690E84A09E915D48273A22B3F627671D0 |
| SSDEEP: | 98304:i8F7nCH3QzJdwnRclIp695DrMPim0em8wBdYdpHXMnQG8mGm4xfeU6qFZn+Fbp51:HqXroqSO5TjPI |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3416)
SUSPICIOUS
Starts a Microsoft application from unusual location
- VSLauncher_[0MB]_[1].exe (PID: 3132)
Creates file in the systems drive root
- WinRAR.exe (PID: 3416)
Process drops legitimate windows executable
- WinRAR.exe (PID: 3416)
INFO
Checks supported languages
- VSLauncher_[0MB]_[1].exe (PID: 3132)
- NvStereoUtilityOGL_[1MB]_[1].exe (PID: 964)
- vlc.exe (PID: 3988)
- HDHelper_[0MB]_[1].exe (PID: 3852)
- Setup.exe (PID: 3200)
Manual execution by a user
- VSLauncher_[0MB]_[1].exe (PID: 3132)
- NvStereoUtilityOGL_[1MB]_[1].exe (PID: 964)
- vlc.exe (PID: 3988)
- Setup.exe (PID: 3200)
- HDHelper_[0MB]_[1].exe (PID: 3852)
Reads the computer name
- vlc.exe (PID: 3988)
- Setup.exe (PID: 3200)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3416)
Create files in a temporary directory
- HDHelper_[0MB]_[1].exe (PID: 3852)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:06:16 09:37:52 |
| ZipCRC: | 0x5f8a2afb |
| ZipCompressedSize: | 6206345 |
| ZipUncompressedSize: | 6450610 |
| ZipFileName: | avenue.mkv |
Total processes
48
Monitored processes
6
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
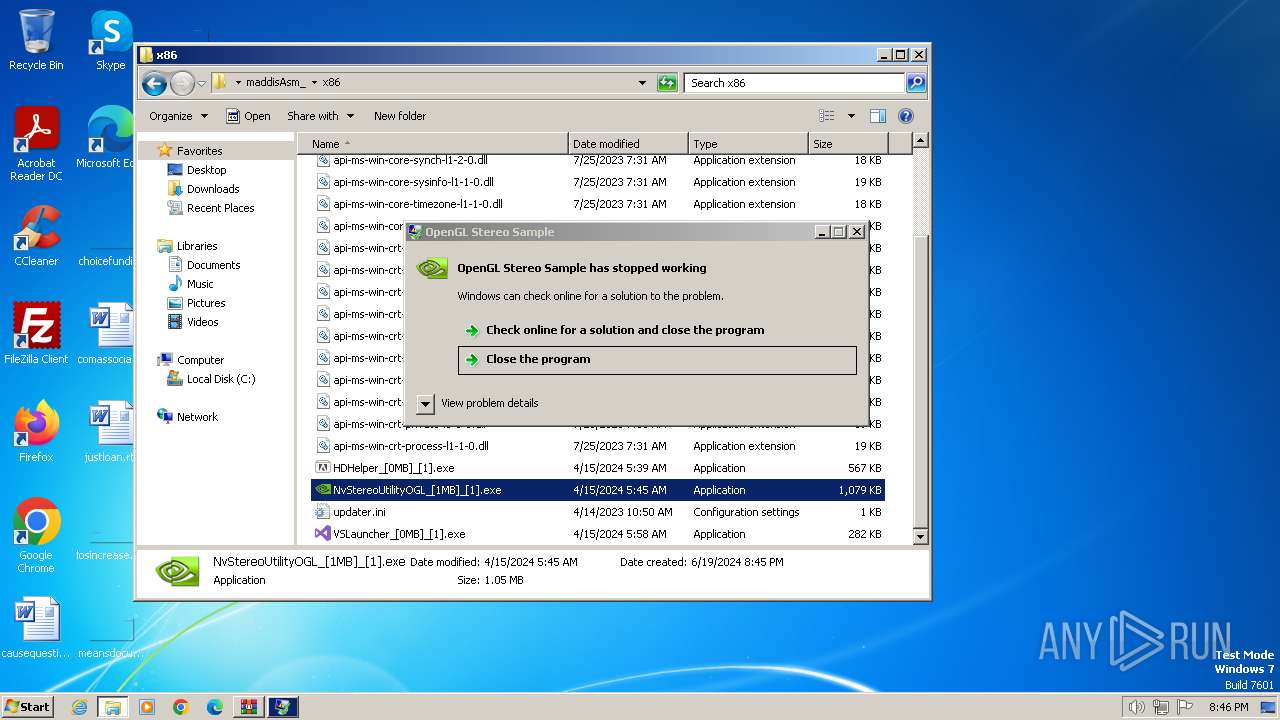
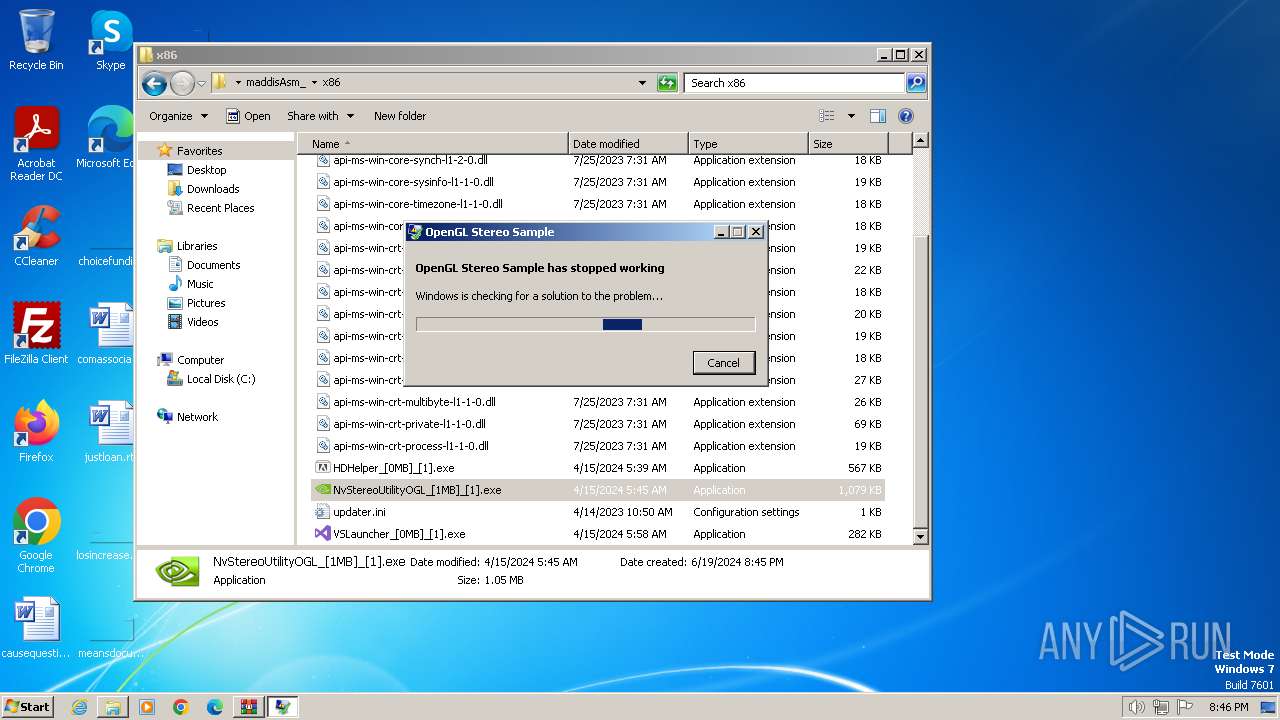
| 964 | "C:\Users\admin\Desktop\maddisAsm_\x86\NvStereoUtilityOGL_[1MB]_[1].exe" | C:\Users\admin\Desktop\maddisAsm_\x86\NvStereoUtilityOGL_[1MB]_[1].exe | explorer.exe | ||||||||||||
User: admin Company: NVIDIA Corporation Integrity Level: MEDIUM Description: OpenGL Stereo Sample Exit code: 3221225477 Version: 1, 2, 2, 0 Modules
| |||||||||||||||
| 3132 | "C:\Users\admin\Desktop\maddisAsm_\x86\VSLauncher_[0MB]_[1].exe" | C:\Users\admin\Desktop\maddisAsm_\x86\VSLauncher_[0MB]_[1].exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Visual Studio Version Selector Exit code: 4294967295 Version: 17.0.34205.65 built by: CBA-1005_101930_1 Modules
| |||||||||||||||
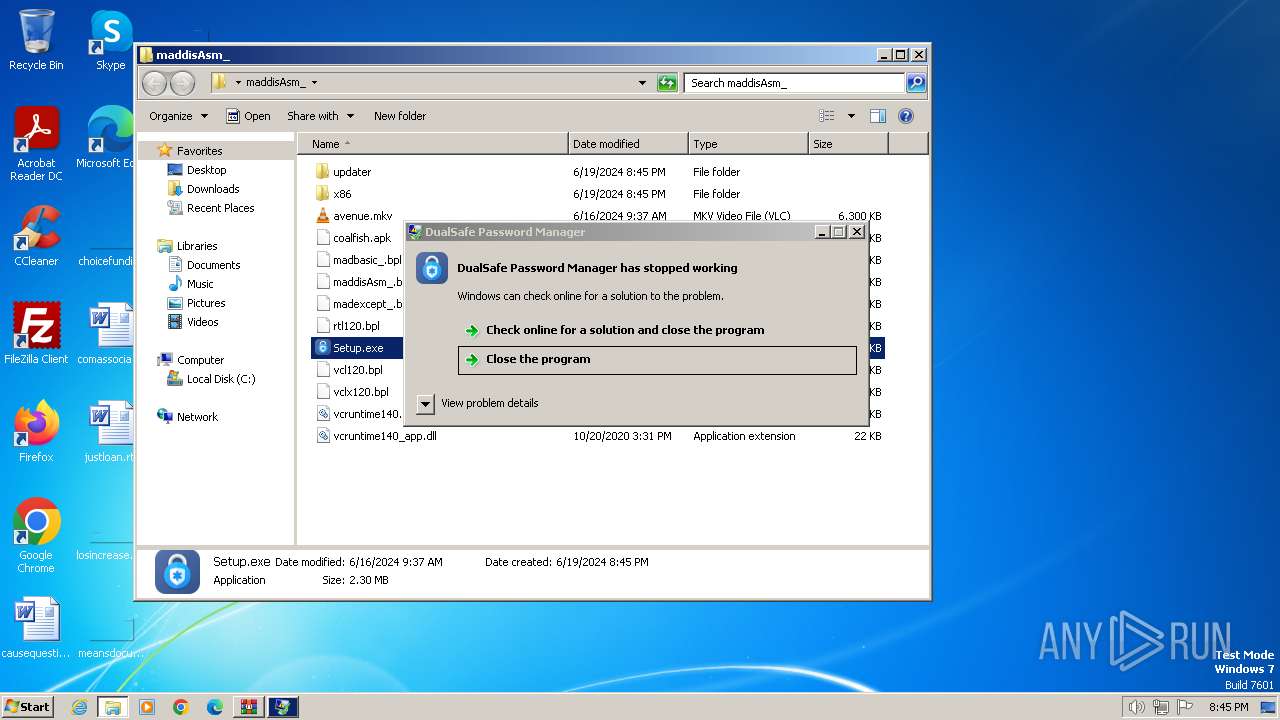
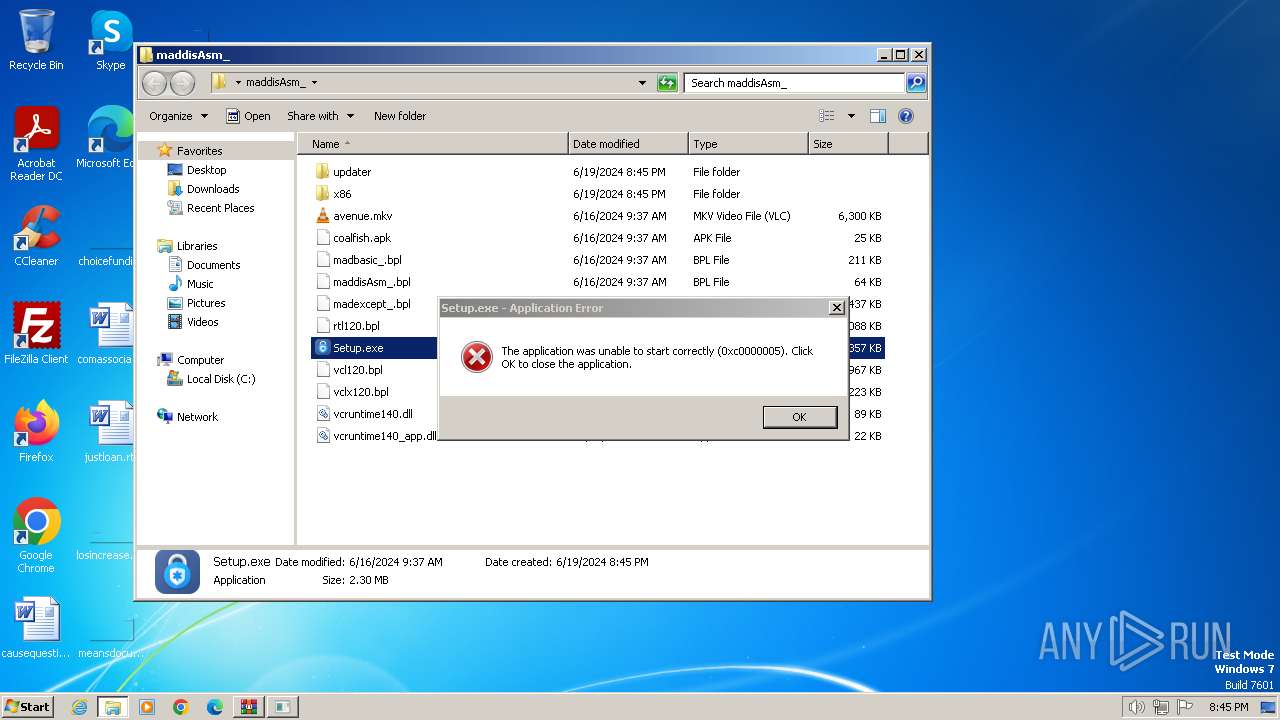
| 3200 | "C:\Users\admin\Desktop\maddisAsm_\Setup.exe" | C:\Users\admin\Desktop\maddisAsm_\Setup.exe | explorer.exe | ||||||||||||
User: admin Company: iTop Inc. Integrity Level: MEDIUM Description: DualSafe Password Manager Exit code: 3221225477 Version: 1.4.0.3 Modules
| |||||||||||||||
| 3416 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\maddisAsm_.zip | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3852 | "C:\Users\admin\Desktop\maddisAsm_\x86\HDHelper_[0MB]_[1].exe" | C:\Users\admin\Desktop\maddisAsm_\x86\HDHelper_[0MB]_[1].exe | — | explorer.exe | |||||||||||
User: admin Company: Adobe Inc. Integrity Level: MEDIUM Description: HD Helper Exit code: 4294967295 Version: 5.9.0.372 Modules
| |||||||||||||||
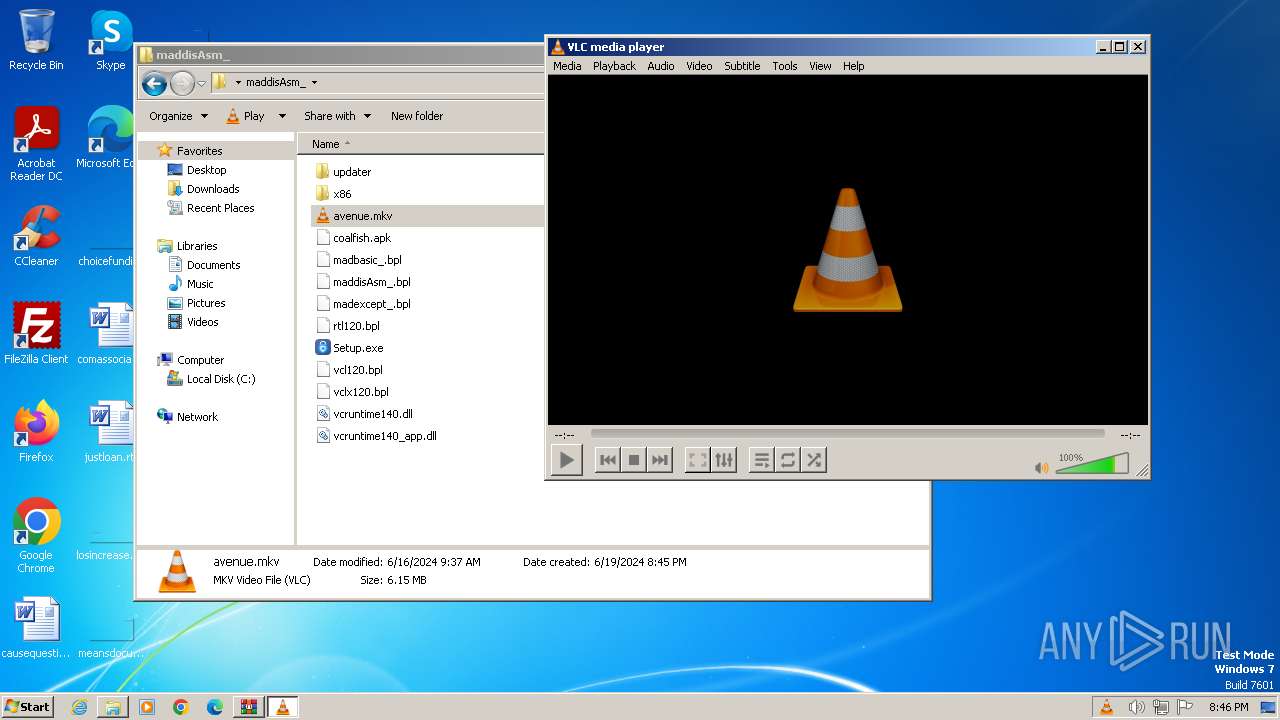
| 3988 | "C:\Program Files\VideoLAN\VLC\vlc.exe" --started-from-file "C:\Users\admin\Desktop\maddisAsm_\avenue.mkv" | C:\Program Files\VideoLAN\VLC\vlc.exe | explorer.exe | ||||||||||||
User: admin Company: VideoLAN Integrity Level: MEDIUM Description: VLC media player Exit code: 0 Version: 3.0.11 Modules
| |||||||||||||||
Total events
9 120
Read events
9 102
Write events
18
Delete events
0
Modification events
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\maddisAsm_.zip | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3416) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
31
Suspicious files
2
Text files
9
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3416 | WinRAR.exe | C:\Users\admin\Desktop\maddisAsm_\avenue.mkv | — | |
MD5:— | SHA256:— | |||
| 3416 | WinRAR.exe | C:\Users\admin\Desktop\maddisAsm_\madbasic_.bpl | executable | |
MD5:E03A0056E75D3A5707BA199BC2EA701F | SHA256:7826395127E791A883359EA81308174700DA0AF8052CC9853B19FD29C2E4BADB | |||
| 3416 | WinRAR.exe | C:\Users\admin\Desktop\maddisAsm_\maddisAsm_.bpl | executable | |
MD5:EF3B47B2EA3884914C13C778FF29EB5B | SHA256:475F7CDFFD8ED4D6F52BD98AE2BB684F1C923A1BE2A692757A9AF788A39B1D87 | |||
| 3416 | WinRAR.exe | C:\Users\admin\Desktop\maddisAsm_\coalfish.apk | binary | |
MD5:BF7F0863F57EA0B64FAFE755EEDB0C7F | SHA256:1D8A03E11F7AA0FBA3A3B45586505A3069D42983AD7F117ACA0F1656305AC3FA | |||
| 3416 | WinRAR.exe | C:\Users\admin\Desktop\maddisAsm_\x86\api-ms-win-core-profile-l1-1-0.dll | executable | |
MD5:6EE66DCA31C5CCE57740D677C85B4CE7 | SHA256:D00A0EDACE14715BF79DBD17B715D8A74A2300F0ADB1F3FC137EDFB7074C9B0A | |||
| 3416 | WinRAR.exe | C:\Users\admin\Desktop\maddisAsm_\madexcept_.bpl | executable | |
MD5:98E59596EDD9B888D906C5409E515803 | SHA256:A6CA13AF74A64E4AB5EBB2D12B757CECF1A683CB9CD0AE7906DB1B4B2C8A90C0 | |||
| 3416 | WinRAR.exe | C:\Users\admin\Desktop\maddisAsm_\x86\api-ms-win-core-synch-l1-1-0.dll | executable | |
MD5:979C67BA244E5328A1A2E588FF748E86 | SHA256:8BB38A7A59FBAA792B3D5F34F94580429588C8C592929CBD307AFD5579762ABC | |||
| 3416 | WinRAR.exe | C:\Users\admin\Desktop\maddisAsm_\x86\api-ms-win-core-synch-l1-2-0.dll | executable | |
MD5:659E4FEBC208545A2E23C0C8B881A30D | SHA256:9AC63682E03D55A5D18405D336634AF080DD0003B565D12A39D6D71AAA989F48 | |||
| 3416 | WinRAR.exe | C:\Users\admin\Desktop\maddisAsm_\vcruntime140.dll | executable | |
MD5:81B11024A8ED0C9ADFD5FBF6916B133C | SHA256:EB6A3A491EFCC911F9DFF457D42FED85C4C170139414470EA951B0DAFE352829 | |||
| 3416 | WinRAR.exe | C:\Users\admin\Desktop\maddisAsm_\x86\api-ms-win-core-sysinfo-l1-1-0.dll | executable | |
MD5:CEF4B9F680FAAE322170B961A3421C5B | SHA256:1FE918979F1653D63BB713D4716910D192CD09F50017A6ECB4CE026ED6285DF9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
13
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1372 | svchost.exe | GET | 304 | 23.36.163.30:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?33775f6043c93e33 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 23.36.163.20:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fbe613066ac7852b | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 239.255.255.250:3702 | — | — | — | unknown |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1372 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1372 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1372 | svchost.exe | 23.36.163.30:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | unknown |
1372 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
watson.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
vlc.exe | main libvlc debug: revision 3.0.11-0-gdc0c5ced72
|
vlc.exe | main libvlc debug: Copyright © 1996-2020 the VideoLAN team
|
vlc.exe | main libvlc debug: using multimedia timers as clock source
|
vlc.exe | main libvlc debug: VLC media player - 3.0.11 Vetinari
|
vlc.exe | main libvlc debug: configured with ../extras/package/win32/../../../configure '--enable-update-check' '--enable-lua' '--enable-faad' '--enable-flac' '--enable-theora' '--enable-avcodec' '--enable-merge-ffmpeg' '--enable-dca' '--enable-mpc' '--enable-libass' '--enable-schroedinger' '--enable-realrtsp' '--enable-live555' '--enable-dvdread' '--enable-shout' '--enable-goom' '--enable-caca' '--enable-qt' '--enable-skins2' '--enable-sse' '--enable-mmx' '--enable-libcddb' '--enable-zvbi' '--disable-telx' '--enable-nls' '--host=i686-w64-mingw32' '--with-breakpad=https://win.crashes.videolan.org' 'host_alias=i686-w64-mingw32' 'PKG_CONFIG_LIBDIR=/home/jenkins/workspace/vlc-release/windows/vlc-release-win32-x86/contrib/i686-w64-mingw32/lib/pkgconfig'
|
vlc.exe | main libvlc debug: min period: 1 ms, max period: 1000000 ms
|
vlc.exe | main libvlc debug: searching plug-in modules
|
vlc.exe | main libvlc error: stale plugins cache: modified C:\Program Files\VideoLAN\VLC\plugins\access\libaccess_mms_plugin.dll
|
vlc.exe | main libvlc error: stale plugins cache: modified C:\Program Files\VideoLAN\VLC\plugins\access\libaccess_concat_plugin.dll
|
vlc.exe | main libvlc error: stale plugins cache: modified C:\Program Files\VideoLAN\VLC\plugins\access\libaccess_imem_plugin.dll
|