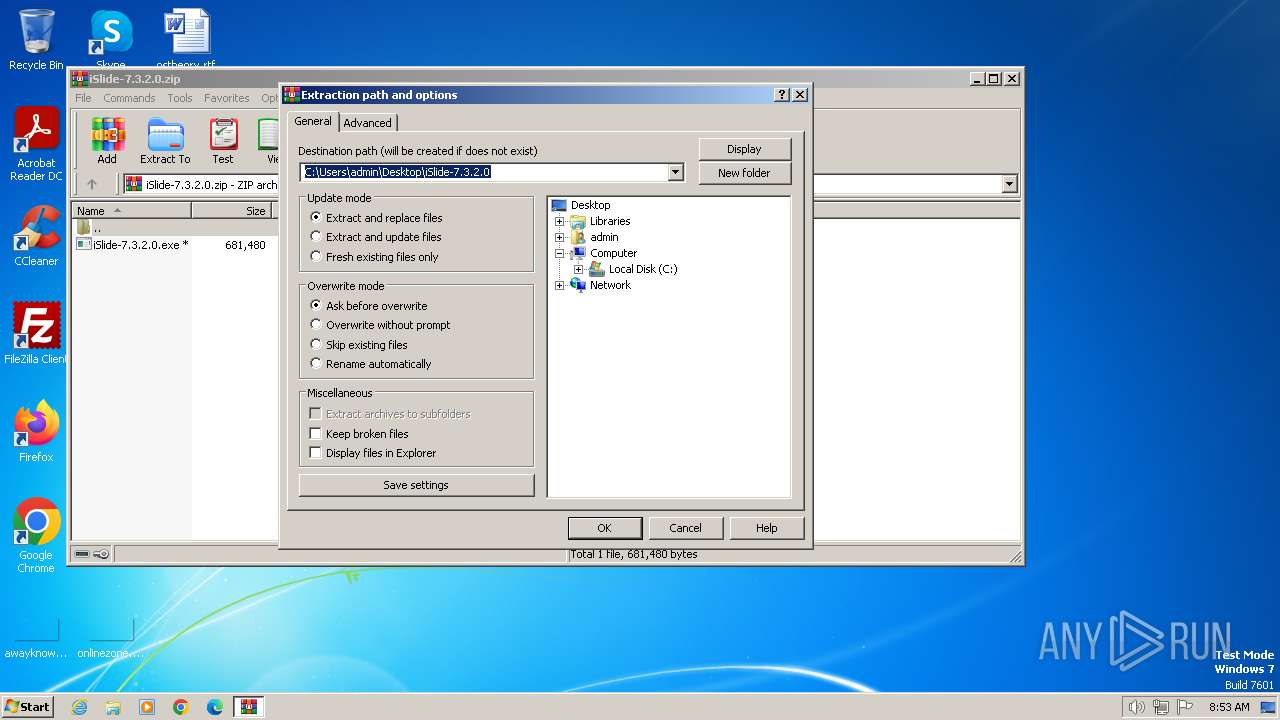
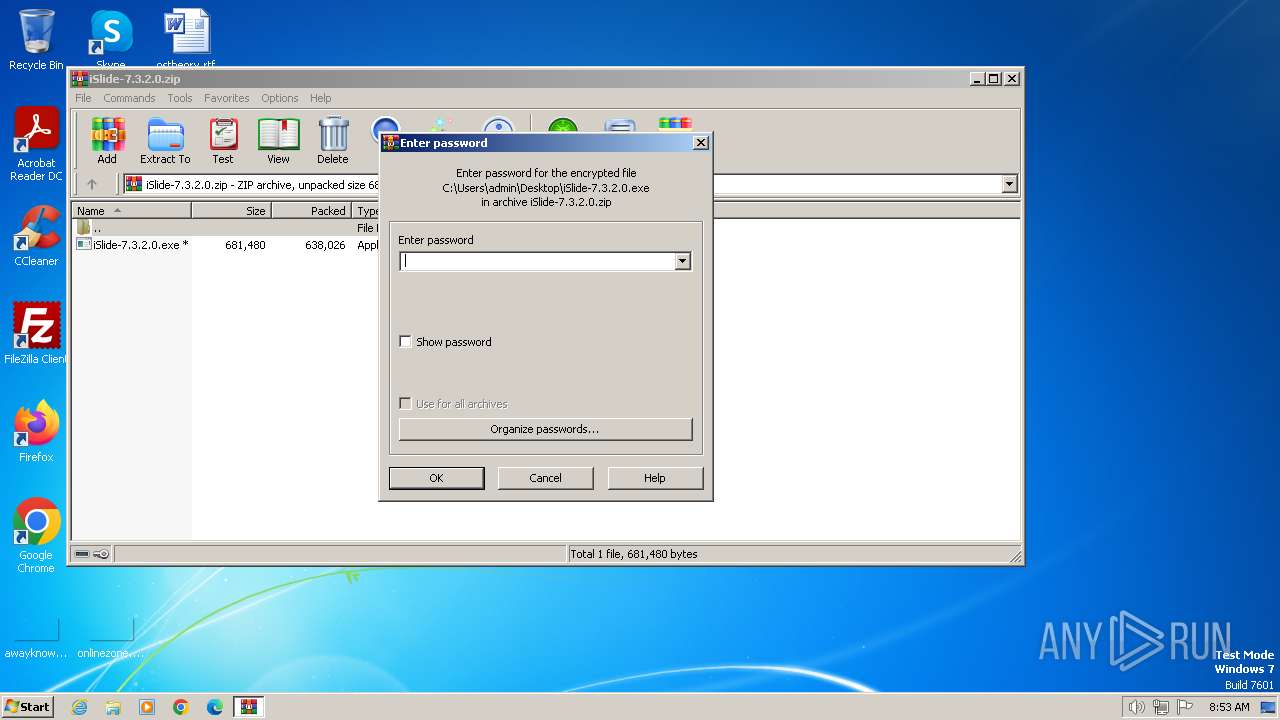
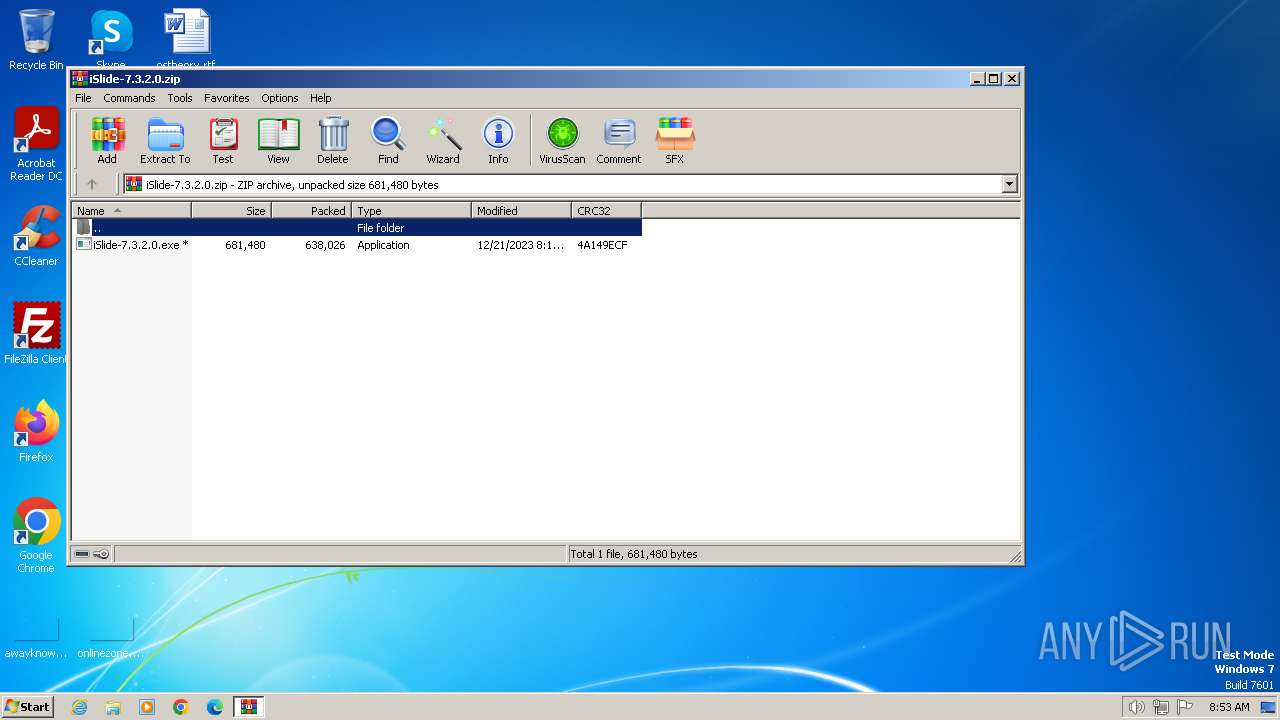
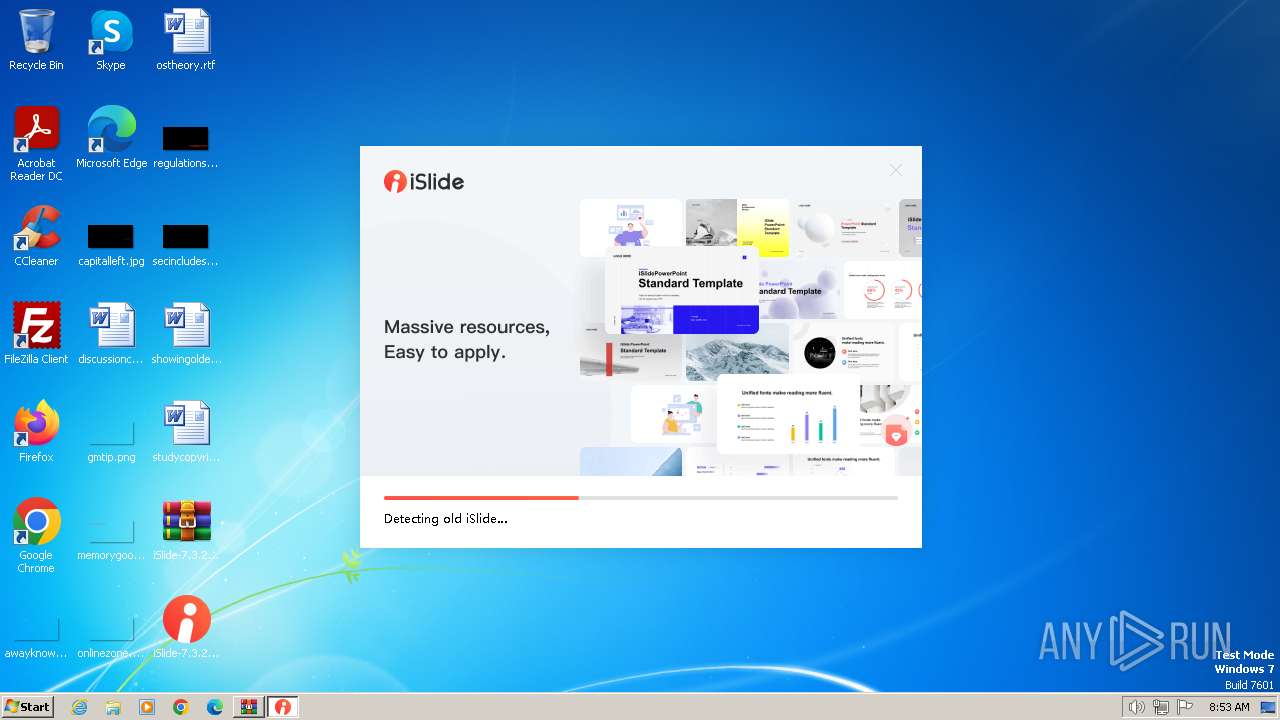
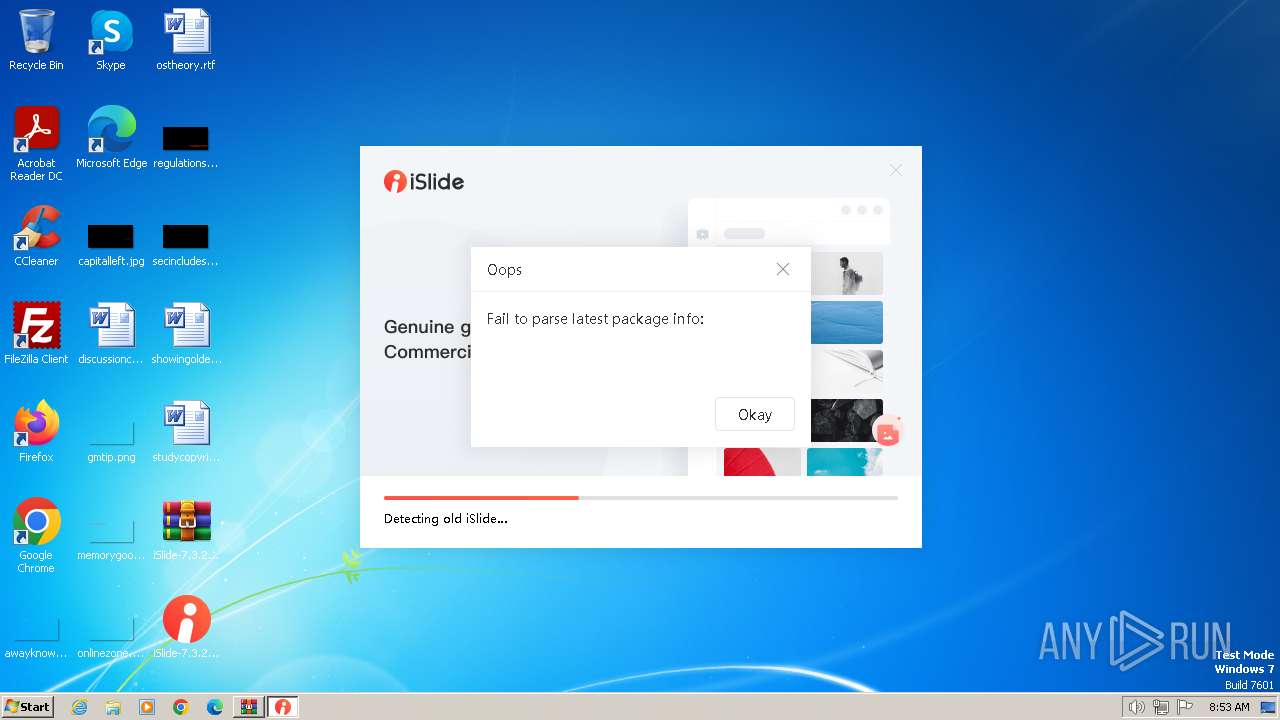
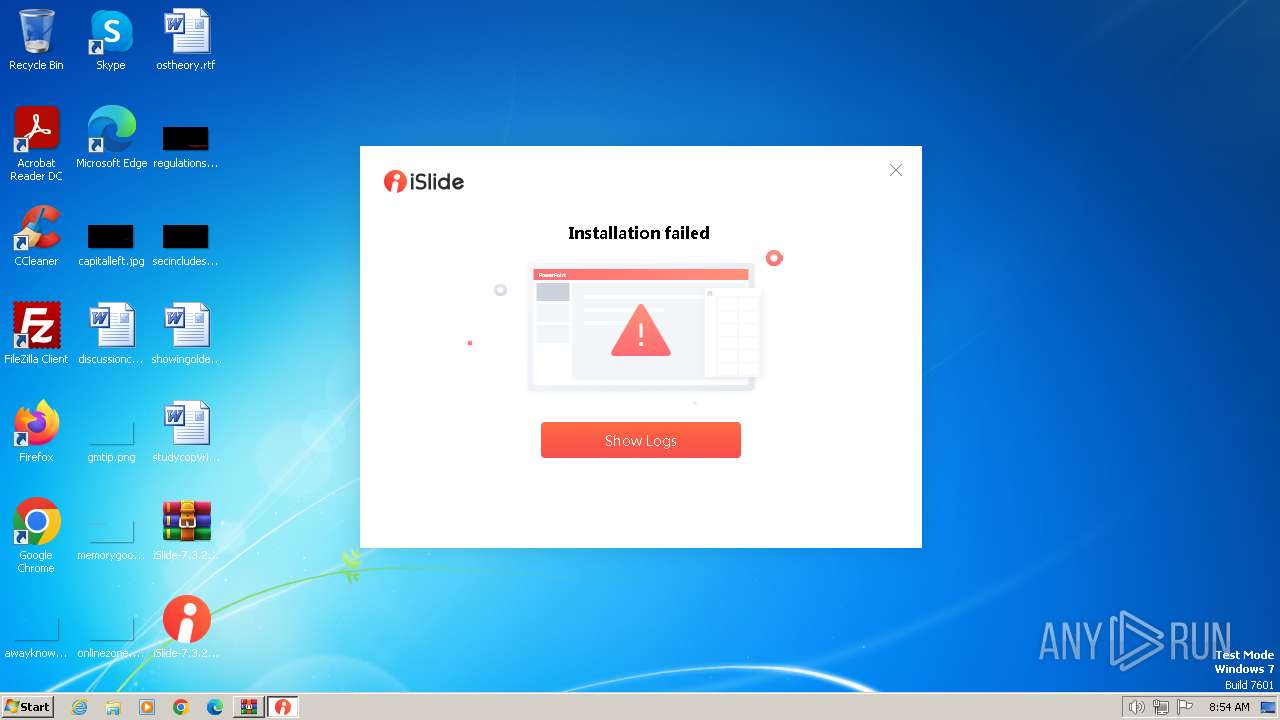
| File name: | iSlide-7.3.2.0.zip |
| Full analysis: | https://app.any.run/tasks/b875b829-0719-45a6-93c9-ccce48aba074 |
| Verdict: | Malicious activity |
| Analysis date: | December 21, 2023, 08:52:55 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 0D8497020643E4080ABA75302C7DE4BC |
| SHA1: | 41E16D5F866448209F60C0ED99B6CEB0AA013A80 |
| SHA256: | 9B8DC5B133B4FA52DA9646DCC7A61F7E4A8DB17A5750E2433AC80B7AA350BA56 |
| SSDEEP: | 24576:LXw+3GRc0Q+QgbT2I6B/IXKX1dzCWKRJ23R4YiixsZv/4rDe4UujYyZaOXnyXW:LXw+3GRc0Q+QgH2I6B/+KX1dzCWKRJ27 |
MALICIOUS
Deletes shadow copies
- ns586F.tmp (PID: 1848)
- ns59C8.tmp (PID: 2296)
- ns5AB3.tmp (PID: 2440)
- ns5B9F.tmp (PID: 2736)
- ns5C1D.tmp (PID: 2472)
- ns5D08.tmp (PID: 2404)
SUSPICIOUS
The process creates files with name similar to system file names
- iSlide-7.3.2.0.exe (PID: 1972)
Reads the Internet Settings
- iSlide-7.3.2.0.exe (PID: 1972)
- WMIC.exe (PID: 1784)
- WMIC.exe (PID: 2096)
- WMIC.exe (PID: 2624)
- WMIC.exe (PID: 452)
- WMIC.exe (PID: 664)
- WMIC.exe (PID: 1556)
Starts application with an unusual extension
- iSlide-7.3.2.0.exe (PID: 1972)
Uses WMIC.EXE to obtain data on processes
- ns586F.tmp (PID: 1848)
- ns59C8.tmp (PID: 2296)
- ns5AB3.tmp (PID: 2440)
- ns5B9F.tmp (PID: 2736)
- ns5C1D.tmp (PID: 2472)
- ns5D08.tmp (PID: 2404)
Adds/modifies Windows certificates
- iSlide-7.3.2.0.exe (PID: 1972)
Checks Windows Trust Settings
- iSlide-7.3.2.0.exe (PID: 1972)
Reads settings of System Certificates
- iSlide-7.3.2.0.exe (PID: 1972)
Reads security settings of Internet Explorer
- iSlide-7.3.2.0.exe (PID: 1972)
INFO
Create files in a temporary directory
- iSlide-7.3.2.0.exe (PID: 2020)
- iSlide-7.3.2.0.exe (PID: 1972)
Checks supported languages
- iSlide-7.3.2.0.exe (PID: 2020)
- iSlide-7.3.2.0.exe (PID: 1972)
- ns586F.tmp (PID: 1848)
- ns5C1D.tmp (PID: 2472)
- ns5AB3.tmp (PID: 2440)
- ns5B9F.tmp (PID: 2736)
- ns5D08.tmp (PID: 2404)
- ns59C8.tmp (PID: 2296)
Reads the computer name
- iSlide-7.3.2.0.exe (PID: 2020)
- iSlide-7.3.2.0.exe (PID: 1972)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 116)
- iSlide-7.3.2.0.exe (PID: 2020)
- iSlide-7.3.2.0.exe (PID: 1972)
Manual execution by a user
- iSlide-7.3.2.0.exe (PID: 2020)
- notepad.exe (PID: 2892)
Application launched itself
- iSlide-7.3.2.0.exe (PID: 2020)
Malware-specific behavior (creating "System.dll" in Temp)
- iSlide-7.3.2.0.exe (PID: 1972)
Process checks are UAC notifies on
- iSlide-7.3.2.0.exe (PID: 2020)
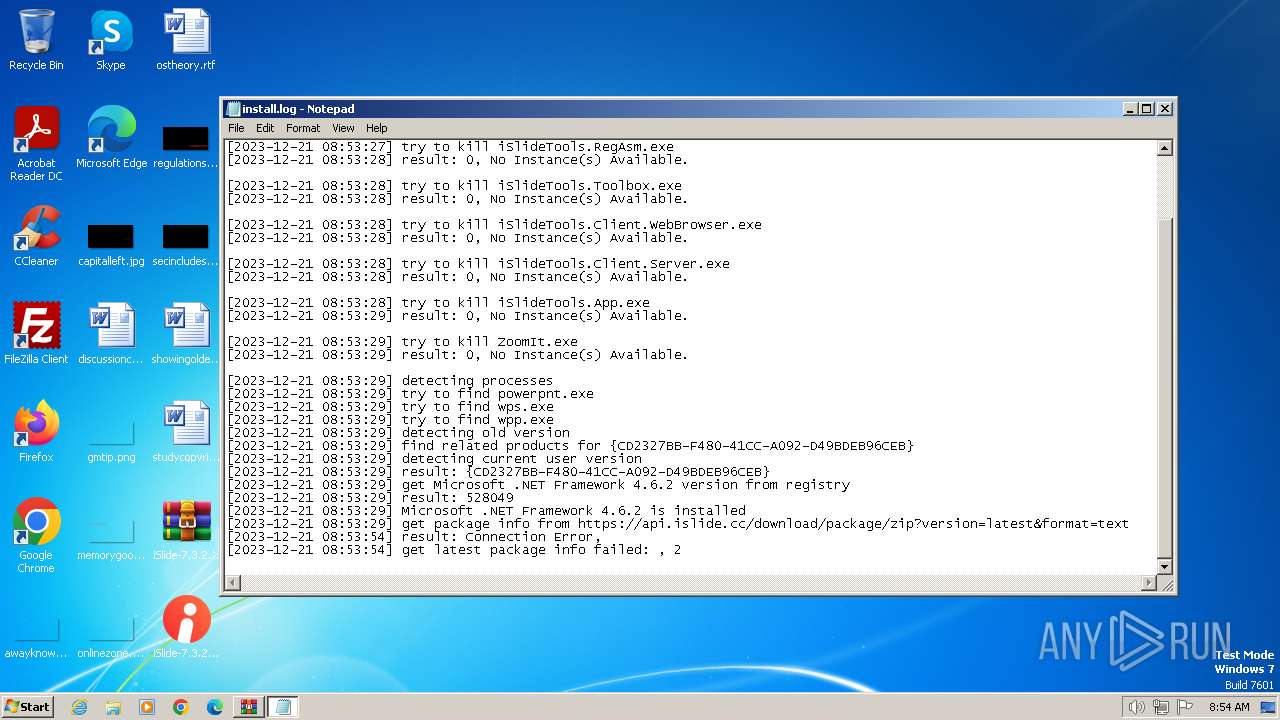
Checks proxy server information
- iSlide-7.3.2.0.exe (PID: 1972)
Reads the machine GUID from the registry
- iSlide-7.3.2.0.exe (PID: 1972)
Creates files or folders in the user directory
- iSlide-7.3.2.0.exe (PID: 1972)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:12:21 16:13:36 |
| ZipCRC: | 0x4a149ecf |
| ZipCompressedSize: | 638026 |
| ZipUncompressedSize: | 681480 |
| ZipFileName: | iSlide-7.3.2.0.exe |
Total processes
61
Monitored processes
16
Malicious processes
8
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\iSlide-7.3.2.0.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 452 | wmic process where "name='iSlideTools.Client.Server.exe'" delete | C:\Windows\System32\wbem\WMIC.exe | — | ns5B9F.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 664 | wmic process where "name='iSlideTools.App.exe'" delete | C:\Windows\System32\wbem\WMIC.exe | — | ns5C1D.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1556 | wmic process where "name='ZoomIt.exe'" delete | C:\Windows\System32\wbem\WMIC.exe | — | ns5D08.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1784 | wmic process where "name='iSlideTools.RegAsm.exe'" delete | C:\Windows\System32\wbem\WMIC.exe | — | ns586F.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1848 | "C:\Users\admin\AppData\Local\Temp\nst4563.tmp\ns586F.tmp" wmic process where "name='iSlideTools.RegAsm.exe'" delete | C:\Users\admin\AppData\Local\Temp\nst4563.tmp\ns586F.tmp | — | iSlide-7.3.2.0.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1972 | "C:\Users\admin\Desktop\iSlide-7.3.2.0.exe" /UAC:4016A /NCRC | C:\Users\admin\Desktop\iSlide-7.3.2.0.exe | iSlide-7.3.2.0.exe | ||||||||||||
User: admin Company: iSlide Integrity Level: HIGH Description: iSlide Installer Exit code: 0 Version: 7.3.2.0 Modules
| |||||||||||||||
| 2020 | "C:\Users\admin\Desktop\iSlide-7.3.2.0.exe" | C:\Users\admin\Desktop\iSlide-7.3.2.0.exe | — | explorer.exe | |||||||||||
User: admin Company: iSlide Integrity Level: MEDIUM Description: iSlide Installer Exit code: 0 Version: 7.3.2.0 Modules
| |||||||||||||||
| 2096 | wmic process where "name='iSlideTools.Toolbox.exe'" delete | C:\Windows\System32\wbem\WMIC.exe | — | ns59C8.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2296 | "C:\Users\admin\AppData\Local\Temp\nst4563.tmp\ns59C8.tmp" wmic process where "name='iSlideTools.Toolbox.exe'" delete | C:\Users\admin\AppData\Local\Temp\nst4563.tmp\ns59C8.tmp | — | iSlide-7.3.2.0.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
Total events
4 345
Read events
4 299
Write events
46
Delete events
0
Modification events
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1972) iSlide-7.3.2.0.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | SecureProtocols |
Value: 2688 | |||
Executable files
21
Suspicious files
3
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2020 | iSlide-7.3.2.0.exe | C:\Users\admin\AppData\Local\Temp\nsh41C9.tmp\UAC.dll | executable | |
MD5:113C5F02686D865BC9E8332350274FD1 | SHA256:0D21041A1B5CD9F9968FC1D457C78A802C9C5A23F375327E833501B65BCD095D | |||
| 2020 | iSlide-7.3.2.0.exe | C:\Users\admin\AppData\Local\Temp\nsh41C9.tmp\UserInfo.dll | executable | |
MD5:D458B8251443536E4A334147E0170E95 | SHA256:4913D4CCCF84CD0534069107CFF3E8E2F427160CAD841547DB9019310AC86CC7 | |||
| 1972 | iSlide-7.3.2.0.exe | C:\Users\admin\AppData\Local\Temp\nst4563.tmp\UserInfo.dll | executable | |
MD5:D458B8251443536E4A334147E0170E95 | SHA256:4913D4CCCF84CD0534069107CFF3E8E2F427160CAD841547DB9019310AC86CC7 | |||
| 1972 | iSlide-7.3.2.0.exe | C:\Users\admin\AppData\Local\Temp\nst4563.tmp\nsArray.dll | executable | |
MD5:DA4BC09439ED21FAF7620A53433AAC92 | SHA256:216D68D3F0B37BB2203B3A438A84A089E8C388608F46377AD7E7D6A2709CF9B0 | |||
| 1972 | iSlide-7.3.2.0.exe | C:\Users\admin\AppData\Local\Temp\nst4563.tmp\System.dll | executable | |
MD5:4ADD245D4BA34B04F213409BFE504C07 | SHA256:9111099EFE9D5C9B391DC132B2FAF0A3851A760D4106D5368E30AC744EB42706 | |||
| 1972 | iSlide-7.3.2.0.exe | C:\Users\admin\AppData\Local\Temp\nst4563.tmp\ns586F.tmp | executable | |
MD5:B4579BC396ACE8CAFD9E825FF63FE244 | SHA256:01E72332362345C415A7EDCB366D6A1B52BE9AC6E946FB9DA49785C140BA1A4B | |||
| 1972 | iSlide-7.3.2.0.exe | C:\Users\admin\AppData\Local\Temp\nst4563.tmp\LogEx.dll | executable | |
MD5:0F96D9EB959AD4E8FD205E6D58CF01B8 | SHA256:57EDE354532937E38C4AE9DA3710EE295705EA9770C402DFB3A5C56A32FD4314 | |||
| 116 | WinRAR.exe | C:\Users\admin\Desktop\iSlide-7.3.2.0.exe | executable | |
MD5:6809F0DD12623A7642A56E70E913DEF6 | SHA256:6106E6AD581064AB6240DE935A98B70F0ED4AE25FB9E70FA6CCEFB39840609E0 | |||
| 1972 | iSlide-7.3.2.0.exe | C:\Users\admin\AppData\Local\Temp\nst4563.tmp\UAC.dll | executable | |
MD5:113C5F02686D865BC9E8332350274FD1 | SHA256:0D21041A1B5CD9F9968FC1D457C78A802C9C5A23F375327E833501B65BCD095D | |||
| 1972 | iSlide-7.3.2.0.exe | C:\Users\admin\AppData\Local\Temp\iSlide\iSlide Tools\UI\Install.dat | compressed | |
MD5:B457CE805D2281054E2ADED570641584 | SHA256:4FED3D9CE3349BB0E7E871EFE162DE77CC2CCC08E6FC412226C600224509CF72 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
5
DNS requests
2
Threats
2
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1972 | iSlide-7.3.2.0.exe | 90.84.161.17:443 | api.islide.cc | Orange | FR | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
api.islide.cc |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |
1080 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .cc TLD |