| File name: | Payment.rar |
| Full analysis: | https://app.any.run/tasks/c6d03903-f207-45c3-a82b-7d9ceded92c2 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2019, 09:22:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v4, os: Win32 |
| MD5: | D1066474DA7DA2E212923F9443E66409 |
| SHA1: | 1BFAD86362FFC72A3F23C8163EC37DDB43EAD0B9 |
| SHA256: | 9B7F93CF144C7C8015FD4C801189C7FBB008F95F510BDC33ABA168D45C7CF4CB |
| SSDEEP: | 3072:/2EcOfgB/8Kp5qQlFIOuL2h7RrYCw+OWqgR1S3Q:uEHfg/vcElcDWqgR1S3Q |
MALICIOUS
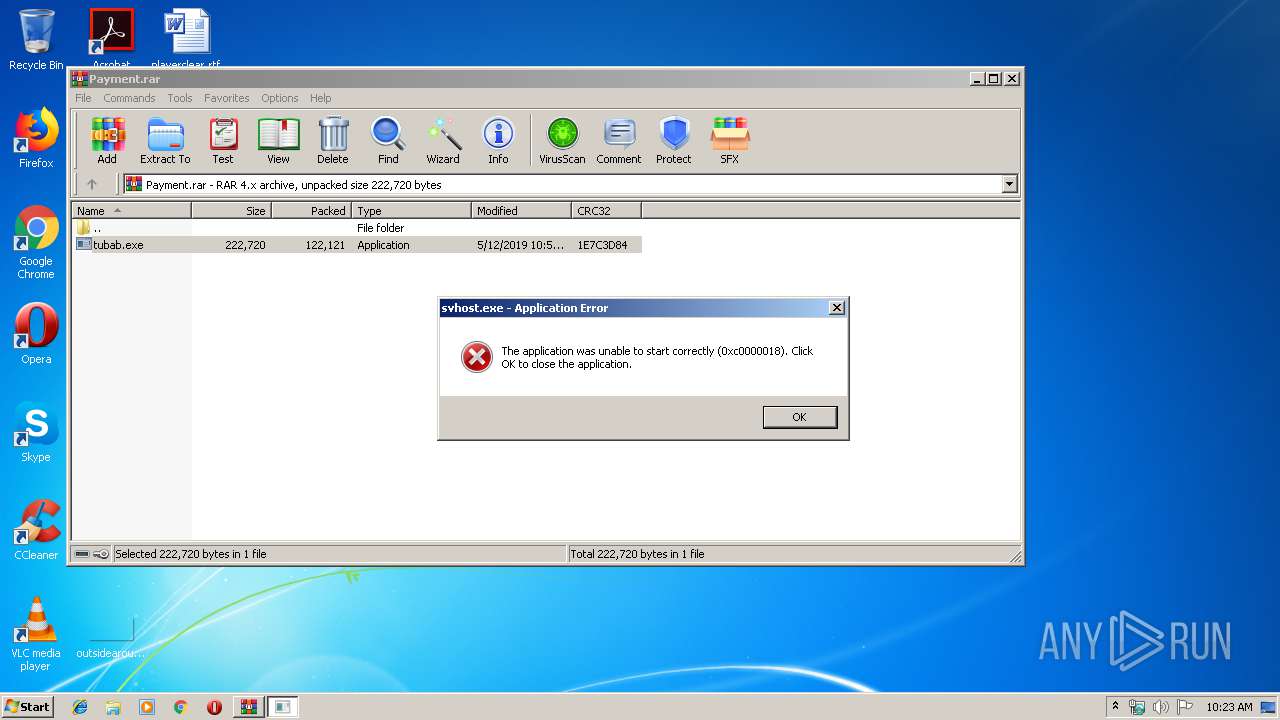
Application was dropped or rewritten from another process
- tubab.exe (PID: 2428)
- svhost.exe (PID: 2320)
- tubab.exe (PID: 2768)
Runs app for hidden code execution
- tubab.exe (PID: 2768)
Changes the autorun value in the registry
- reg.exe (PID: 3712)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2956)
- tubab.exe (PID: 2768)
- cmd.exe (PID: 2088)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2088)
Starts CMD.EXE for commands execution
- tubab.exe (PID: 2768)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v-4.x) (58.3) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (41.6) |
EXIF
ZIP
| CompressedSize: | 122156 |
|---|---|
| UncompressedSize: | 222720 |
| OperatingSystem: | Win32 |
| ModifyDate: | 2019:05:12 22:55:02 |
| PackingMethod: | Normal |
| ArchivedFileName: | tubab.exe |
Total processes
45
Monitored processes
8
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2088 | "cmd.exe" | C:\Windows\system32\cmd.exe | tubab.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2320 | "C:\Users\admin\AppData\Local\Temp\svhost.exe" | C:\Users\admin\AppData\Local\Temp\svhost.exe | — | tubab.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Visual Basic Command Line Compiler Exit code: 0 Version: 9.0.30729.5420 Modules
| |||||||||||||||
| 2428 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2956.19081\tubab.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2956.19081\tubab.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Windscribe Limited Integrity Level: MEDIUM Description: Windscribe Setup Exit code: 3221226540 Version: Modules
| |||||||||||||||
| 2476 | cmd /c C:\Users\admin\AppData\Local\Temp\FolderN\name.exe.bat | C:\Windows\system32\cmd.exe | — | tubab.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2768 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2956.19081\tubab.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2956.19081\tubab.exe | WinRAR.exe | ||||||||||||
User: admin Company: Windscribe Limited Integrity Level: HIGH Description: Windscribe Setup Exit code: 0 Version: Modules
| |||||||||||||||
| 2956 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Payment.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3136 | timeout /t 300 | C:\Windows\system32\timeout.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: timeout - pauses command processing Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3712 | reg add "HKCU\Software\Microsoft\Windows NT\CurrentVersion\Windows" /v Load /t REG_SZ /d "C:\Users\admin\AppData\Local\Temp\FolderN\name.exe.lnk" /f | C:\Windows\system32\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
615
Read events
602
Write events
13
Delete events
0
Modification events
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Payment.rar | |||
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
3
Suspicious files
0
Text files
2
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2956 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2956.19081\tubab.exe | executable | |
MD5:— | SHA256:— | |||
| 2088 | cmd.exe | C:\Users\admin\AppData\Local\Temp\FolderN\name.exe | executable | |
MD5:— | SHA256:— | |||
| 2088 | cmd.exe | C:\Users\admin\AppData\Local\Temp\FolderN\name.exe:Zone.Identifier | text | |
MD5:130A75A932A2FE57BFEA6A65B88DA8F6 | SHA256:F2B79CAE559D6772AFC1C2ED9468988178F8B6833D5028A15DEA73CE47D0196E | |||
| 2768 | tubab.exe | C:\Users\admin\AppData\Local\Temp\FolderN\name.exe.lnk | lnk | |
MD5:B7F2CFEC6823A438DBA7530A8F4AE648 | SHA256:612F6D646DAAA368D40443AB894042EBB8B93AC485658E78682731BAD9AB52CC | |||
| 2768 | tubab.exe | C:\Users\admin\AppData\Local\Temp\svhost.exe | executable | |
MD5:32827E69B293B99013BBBE37D029245D | SHA256:9250B89157770E3AB59A2C7E2DD6B12B3C61D9B7C6620C3B4727E4BFFF10F01F | |||
| 2768 | tubab.exe | C:\Users\admin\AppData\Local\Temp\FolderN\name.exe.bat | text | |
MD5:4C8485419E996A63B390E1E42AE851A8 | SHA256:6B8CCB3DB87E52C95A7EA8D41B7BFF269A26C9573E74AF142525C7DC49EA2467 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report