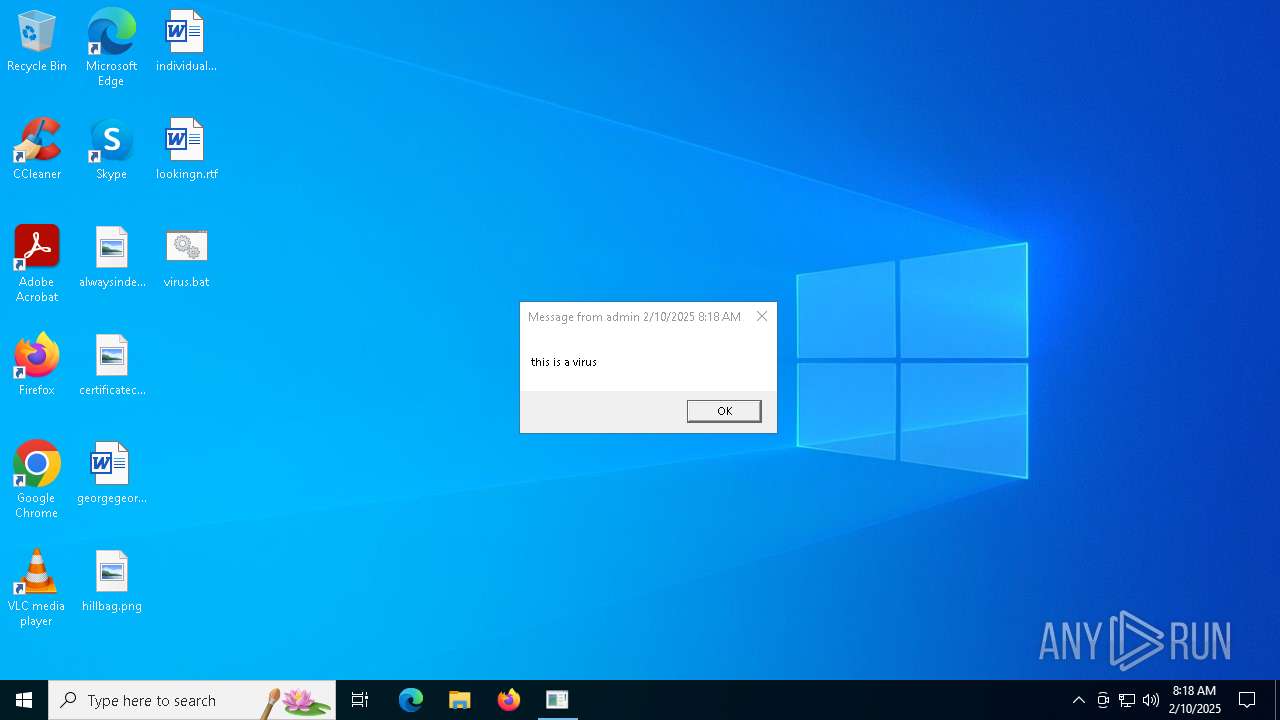
| File name: | virus.bat |
| Full analysis: | https://app.any.run/tasks/f4e6388d-7b4f-45de-bbdc-bbafbcc649a8 |
| Verdict: | Malicious activity |
| Analysis date: | February 10, 2025, 08:17:43 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text |
| MD5: | 0AAF835B7BAB1EBDBFFB5FCD053924F6 |
| SHA1: | E96FBD911A5E76D9C67959A1A68818B1D581A35A |
| SHA256: | 9B792C1E7A1F10A79D88AC1433ED91B30FECAE539E999D7135D173311C666A2B |
| SSDEEP: | 24:qIMOZGdh166G3bG3wuclxazc/G3b6zz2dBG3MUz8G3M3NG3Mzepecru9G3IPK:qIMFf166G3bG3TQBG3b6mHG3MTG3M9Gn |
MALICIOUS
SONIC has been detected
- cmd.exe (PID: 4876)
SUSPICIOUS
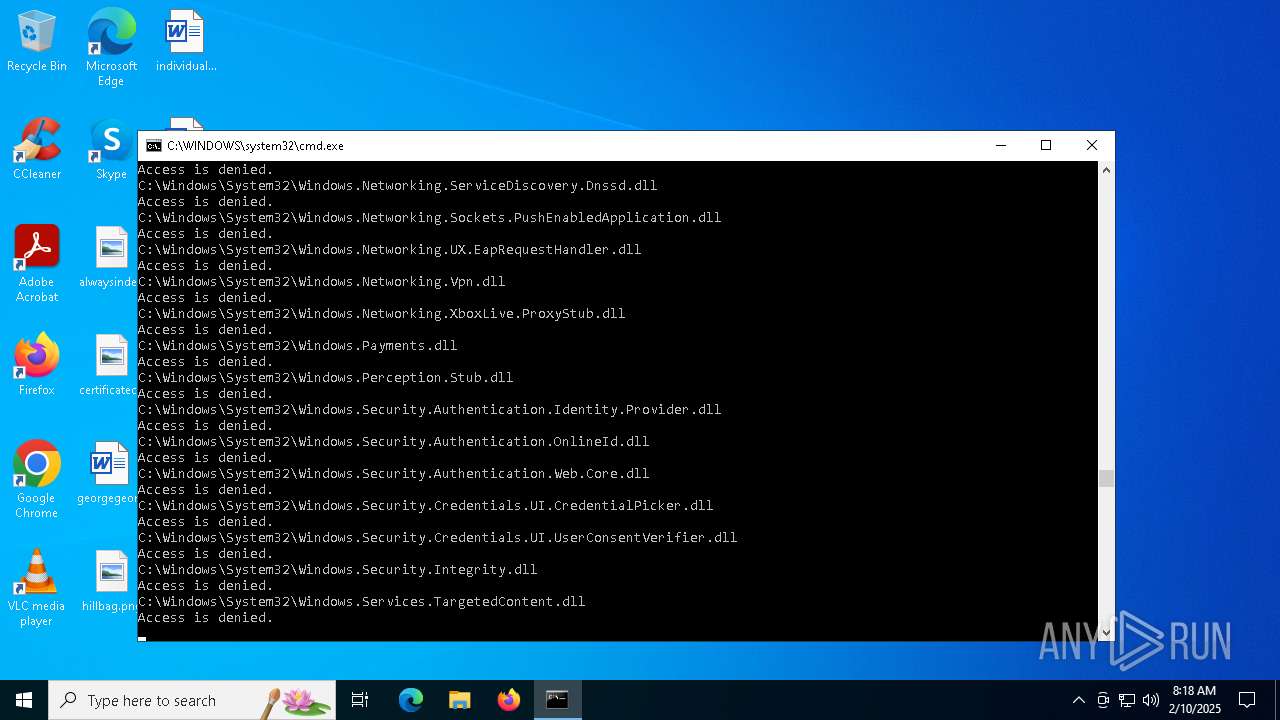
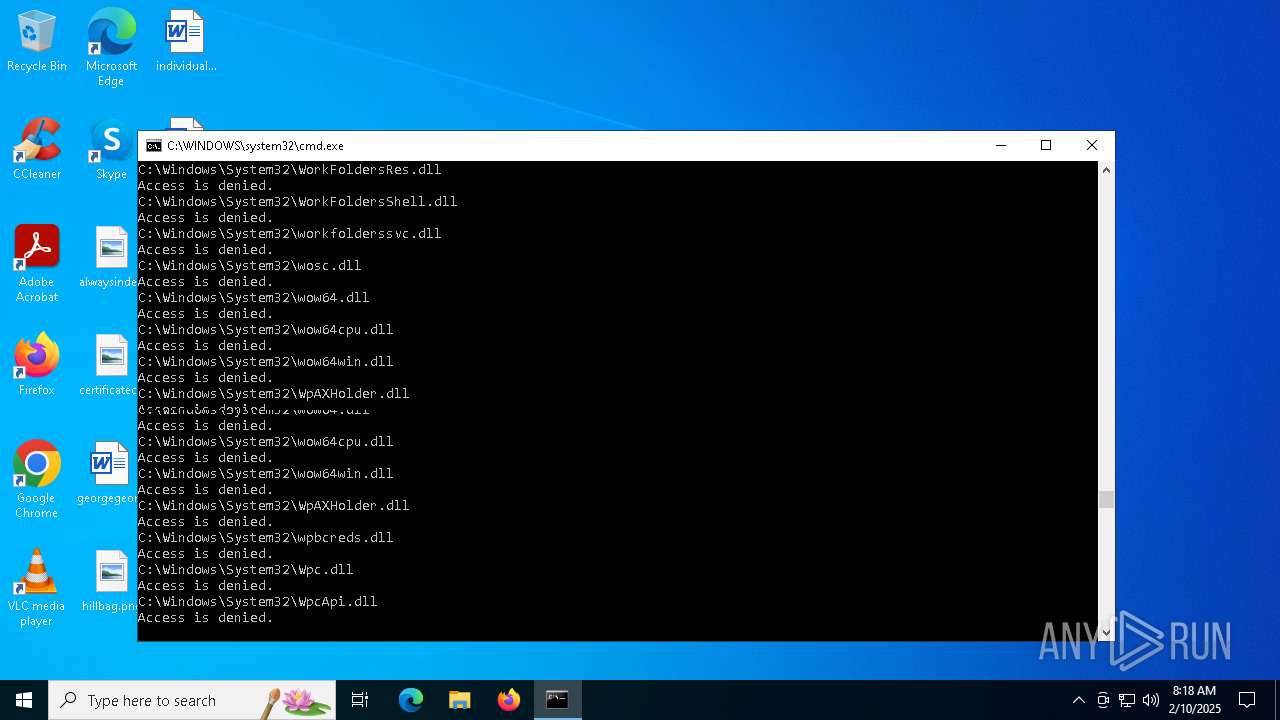
Creates file in the systems drive root
- cmd.exe (PID: 4876)
Reads security settings of Internet Explorer
- StartMenuExperienceHost.exe (PID: 5912)
Reads the date of Windows installation
- StartMenuExperienceHost.exe (PID: 5912)
- SearchApp.exe (PID: 4384)
INFO
Checks supported languages
- StartMenuExperienceHost.exe (PID: 5912)
- TextInputHost.exe (PID: 4856)
- SearchApp.exe (PID: 4384)
Reads the computer name
- StartMenuExperienceHost.exe (PID: 5912)
- TextInputHost.exe (PID: 4856)
- SearchApp.exe (PID: 4384)
Process checks computer location settings
- StartMenuExperienceHost.exe (PID: 5912)
- SearchApp.exe (PID: 4384)
Checks proxy server information
- SearchApp.exe (PID: 4384)
Reads Environment values
- SearchApp.exe (PID: 4384)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 4384)
Reads the software policy settings
- SearchApp.exe (PID: 4384)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
130
Monitored processes
14
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1476 | tskill explorer | C:\Windows\System32\tskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Desktop Services End Process Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3436 | tskill yahoomessenger | C:\Windows\System32\tskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Desktop Services End Process Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3692 | tskill ccapp | C:\Windows\System32\tskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Desktop Services End Process Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4384 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4628 | tskill firefox | C:\Windows\System32\tskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Desktop Services End Process Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4824 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4840 | tskill chrome | C:\Windows\System32\tskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Desktop Services End Process Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4856 | "C:\WINDOWS\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe" -ServerName:InputApp.AppXjd5de1g66v206tj52m9d0dtpppx4cgpn.mca | C:\Windows\SystemApps\MicrosoftWindows.Client.CBS_cw5n1h2txyewy\TextInputHost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Version: 123.26505.0.0 Modules
| |||||||||||||||
| 4876 | C:\WINDOWS\system32\cmd.exe /c ""C:\Users\admin\Desktop\virus.bat" " | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5240 | tskill iexplorer | C:\Windows\System32\tskill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Remote Desktop Services End Process Utility Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
13 445
Read events
13 370
Write events
72
Delete events
3
Modification events
| (PID) Process: | (5912) StartMenuExperienceHost.exe | Key: | \REGISTRY\A\{6889f4c8-e7c7-6b74-2a32-dcad51de1762}\LocalState\DataCorruptionRecovery |
| Operation: | write | Name: | InitializationAttemptCount |
Value: 0100000079E5484B947BDB01 | |||
| (PID) Process: | (5912) StartMenuExperienceHost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\TileDataModel\Migration\StartNonLayoutProperties |
| Operation: | write | Name: | Completed |
Value: 1 | |||
| (PID) Process: | (5912) StartMenuExperienceHost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\TileDataModel\Migration\StartNonLayoutProperties_AppUsageData |
| Operation: | write | Name: | Completed |
Value: 1 | |||
| (PID) Process: | (5912) StartMenuExperienceHost.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows NT\CurrentVersion\TileDataModel\Migration\StartNonLayoutProperties_TargetedContentTiles |
| Operation: | write | Name: | Completed |
Value: 1 | |||
| (PID) Process: | (5912) StartMenuExperienceHost.exe | Key: | \REGISTRY\A\{6889f4c8-e7c7-6b74-2a32-dcad51de1762}\LocalState\DataCorruptionRecovery |
| Operation: | write | Name: | InitializationAttemptCount |
Value: 00000000E9CBB14B947BDB01 | |||
| (PID) Process: | (4384) SearchApp.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\SearchSettings |
| Operation: | write | Name: | SafeSearchMode |
Value: 1 | |||
| (PID) Process: | (4384) SearchApp.exe | Key: | \REGISTRY\A\{5fc042d1-6b7a-8246-929e-6ca933dd57ea}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_USEREMAIL |
Value: 0000EE92D54B947BDB01 | |||
| (PID) Process: | (4384) SearchApp.exe | Key: | \REGISTRY\A\{5fc042d1-6b7a-8246-929e-6ca933dd57ea}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_ACCOUNTTYPETEXT |
Value: 0000EE92D54B947BDB01 | |||
| (PID) Process: | (4384) SearchApp.exe | Key: | \REGISTRY\A\{5fc042d1-6b7a-8246-929e-6ca933dd57ea}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_ACCOUNTTYPE |
Value: 0000EE92D54B947BDB01 | |||
| (PID) Process: | (4384) SearchApp.exe | Key: | \REGISTRY\A\{5fc042d1-6b7a-8246-929e-6ca933dd57ea}\LocalState |
| Operation: | write | Name: | BINGIDENTITY_PROP_ACCOUNTTYPE |
Value: 4E006F006E0065000000EE92D54B947BDB01 | |||
Executable files
2
Suspicious files
26
Text files
12
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4384 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\TokenBroker\Cache\fbaf94e759052658216786bfbabcdced1b67a5c2.tbres | binary | |
MD5:1198252F2928BEC62E5A31EE21657CA9 | SHA256:D2D513FC24C1B62BEC93EE4299D28CAC8DFF84167DC6EAEB1E22D2FEC706EC3B | |||
| 4384 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\4WxI_EMO9Il3V3PSPu01Sq7MLMc.br[1].js | binary | |
MD5:5DC3BA5585074A9525CCB1545D1EA46F | SHA256:59D0BFC8FE4AE7615F04537FD80E571FE3AB81F2525777593790BE58B171948C | |||
| 4384 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\Internet Explorer\DOMStore\ZWUI0EBX\www.bing[1].xml | text | |
MD5:CA0681973D5C2F3B3CB6814B9D70E3F5 | SHA256:7C92F90B23B67604EF319E1882ACA9AF369E584E2B68312B9555A602AF4A6100 | |||
| 4876 | cmd.exe | C:\Users\admin\Documents\virus.bat | text | |
MD5:0AAF835B7BAB1EBDBFFB5FCD053924F6 | SHA256:9B792C1E7A1F10A79D88AC1433ED91B30FECAE539E999D7135D173311C666A2B | |||
| 4384 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\0SrfjVbd4BJYe5wzcCR3l-BPV6c[1].js | binary | |
MD5:93C8EEB694177EFB7AFE347F5C67A9F9 | SHA256:736C9B4487EDDD28E6D8695DF77EBC8BA760F3BA0709E9CA7C151856E76D4FBB | |||
| 4384 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\wU-YmSK-j9YaNg2gj_x4wAl_UoI[1].css | text | |
MD5:44A48564B38CFFD08E4E098D900F5CF0 | SHA256:E2398DFC8C05AAFCB7C357CB533F6610E5F59BFE2731AA127B606746E32A7AE1 | |||
| 4384 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\-iNIzuEypRdgRJ6xnyVHizZ3bpM.br[1].js | binary | |
MD5:E86ABEFE45E62F7E2F865D8A344D0B6F | SHA256:5D54790C856CE13811590E18AC3B0ACEEFEFB61258852490F4C5C60748365E89 | |||
| 4384 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\4BpQ1bD8vX1mXuJObN-gg9RqkyQ.br[1].js | binary | |
MD5:8465A334065673EB6A6487C8D87539DB | SHA256:84ED6C495B322B0F2213CC33EC6C652D84D82E010C928B1141DB2290D4365F3D | |||
| 4384 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\AppCache\5Y734AMR\67\5qSqWyip_grL-s7BafaqI3Mrk9M.br[1].js | binary | |
MD5:23C987E711C002D4CA3CD02DEEDC9BBF | SHA256:A1C2F4C8CA6113EBDAC36F2C33D6CE19BCF2F4BD99EC06E8BA845E2B25B03322 | |||
| 4384 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\DeviceSearchCache\AppCache133836490883720467.txt~RF13b440.TMP | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
35
TCP/UDP connections
20
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.86.251.20:443 | https://www.bing.com/rb/18/jnc,nj/6hU_LneafI_NFLeDvM367ebFaKQ.js?bu=DyIrb3t-gQF4cnWyAbUBK6UBK7gB&or=w | unknown | binary | 21.3 Kb | whitelisted |
— | — | GET | 200 | 184.86.251.20:443 | https://www.bing.com/manifest/threshold.appcache | unknown | text | 3.46 Kb | whitelisted |
— | — | GET | 200 | 184.86.251.20:443 | https://www.bing.com/rb/16/jnc,nj/0SrfjVbd4BJYe5wzcCR3l-BPV6c.js?bu=Dis0e4gBjwGSAYUBfoIBxwHKATS-Ac0B&or=w | unknown | binary | 21.5 Kb | whitelisted |
— | — | POST | 204 | 184.86.251.15:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.86.251.13:443 | https://www.bing.com/rb/19/cir3,ortl,cc,nc/vOJNaIfAXvJzmnBm845ss-M9YR8.css?bu=B_kCWecCzwFtbYQD&or=w | unknown | text | 5.97 Kb | whitelisted |
— | — | GET | 200 | 184.86.251.16:443 | https://www.bing.com/rb/6k/ortl,cc,nc/QNBBNqWD9F_Blep-UqQSqnMp-FI.css?bu=AcEK&or=w | unknown | text | 6 b | whitelisted |
— | — | GET | 200 | 184.86.251.8:443 | https://www.bing.com/rb/6k/ortl,cc,nc/fvNdnrKxhhxDQUEi09cCaSWpzzE.css?bu=Ca0MwQqyDMEKtgzBCsEKwQrBCg&or=w | unknown | text | 428 Kb | whitelisted |
— | — | GET | 200 | 184.86.251.9:443 | https://www.bing.com/rp/0u2b9EXo8LdXut1MFm4AD0phBuM.br.js | unknown | binary | 1.44 Kb | whitelisted |
— | — | GET | 200 | 184.86.251.12:443 | https://www.bing.com/rb/6k/cir3,ortl,cc,nc/wU-YmSK-j9YaNg2gj_x4wAl_UoI.css?bu=M8cKwQrNCsEKsQvBCrcLwQrBCsEKwgvBCskLwQrPC8EK1QvBCtsLwQrfCsEK5QrBCtkKwQrBCqgLwQr0CsEK-grBCu4KwQqAC4oLjQvBCsEKpQuTC8EKmQucC8EKhwzBCuELwQrADA&or=w | unknown | text | 444 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
3976 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4384 | SearchApp.exe | 184.86.251.15:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |