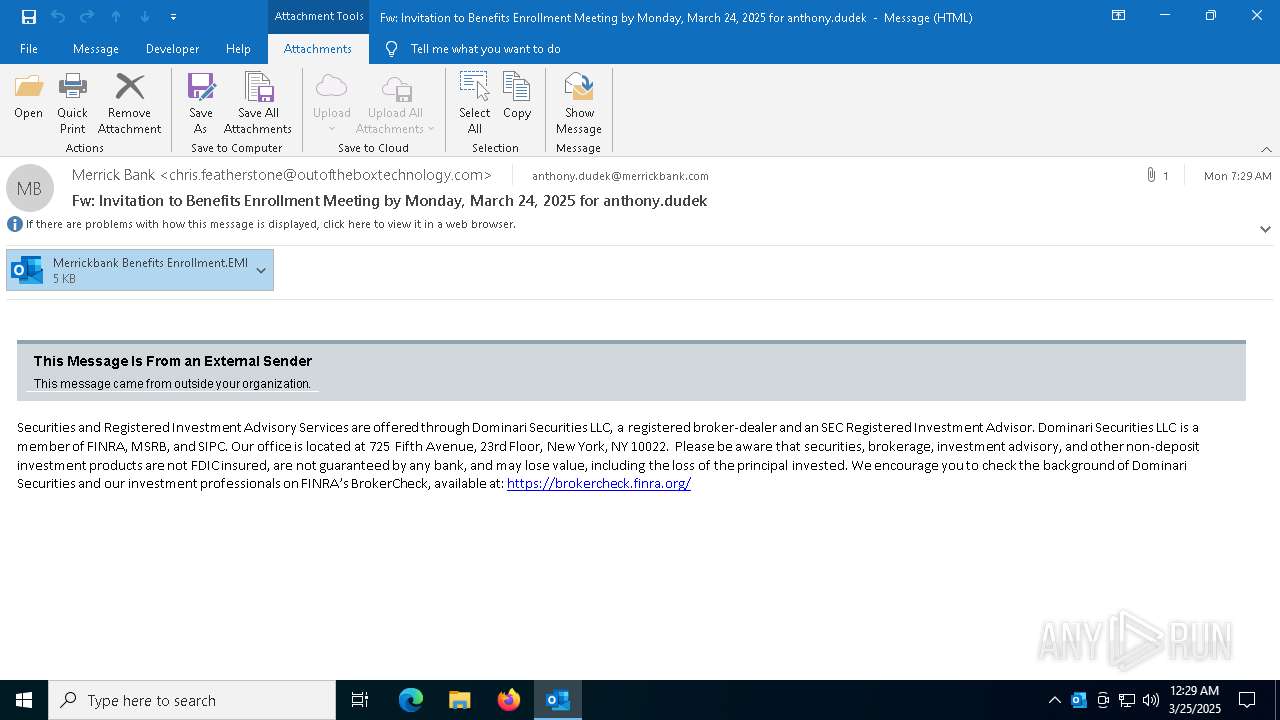
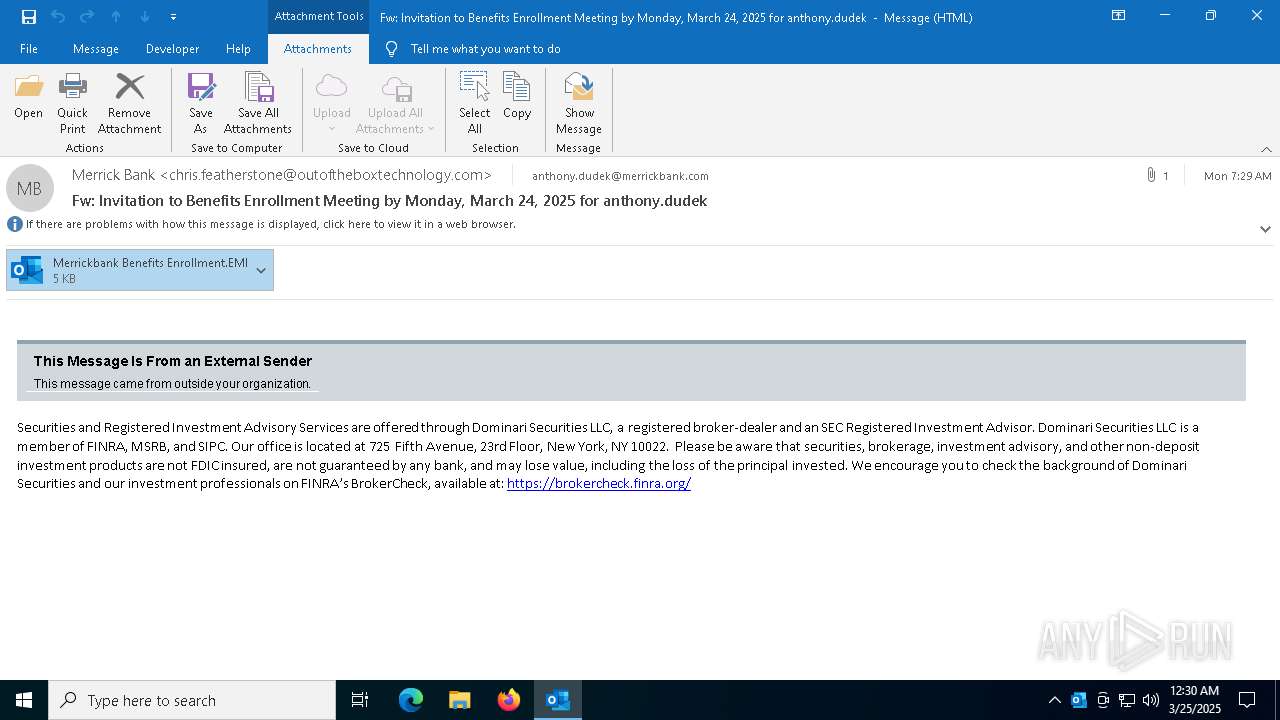
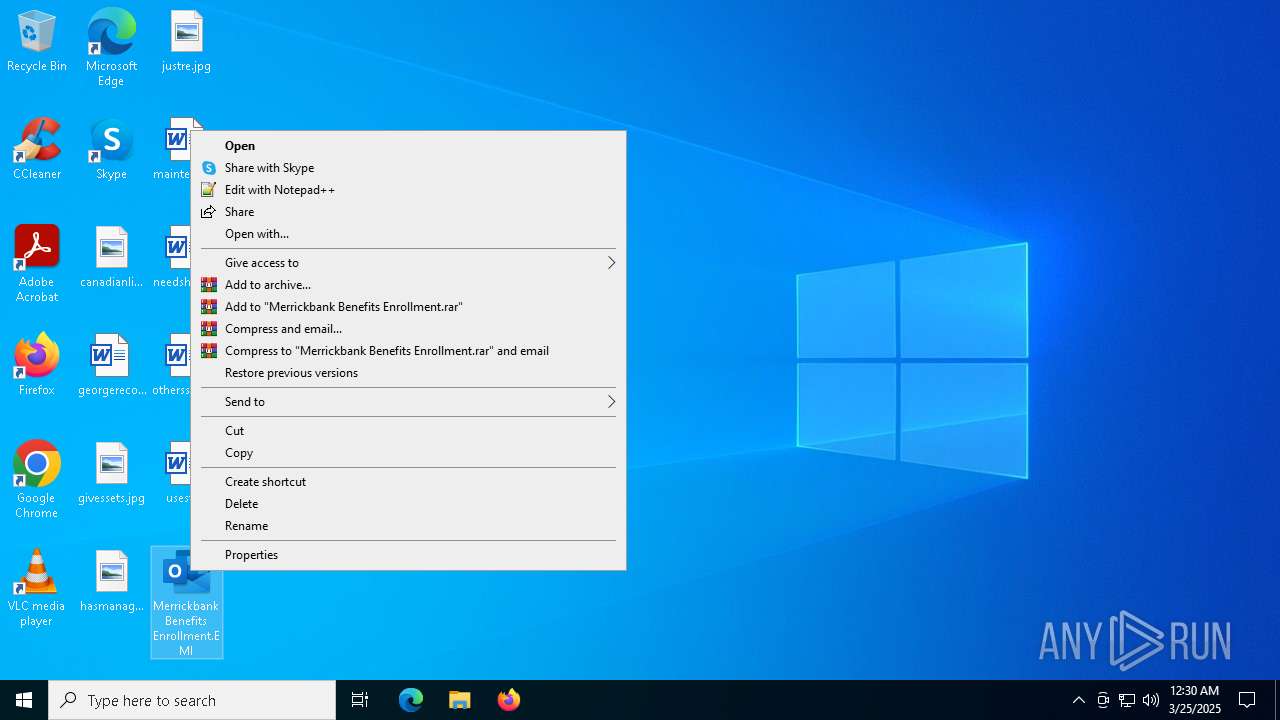
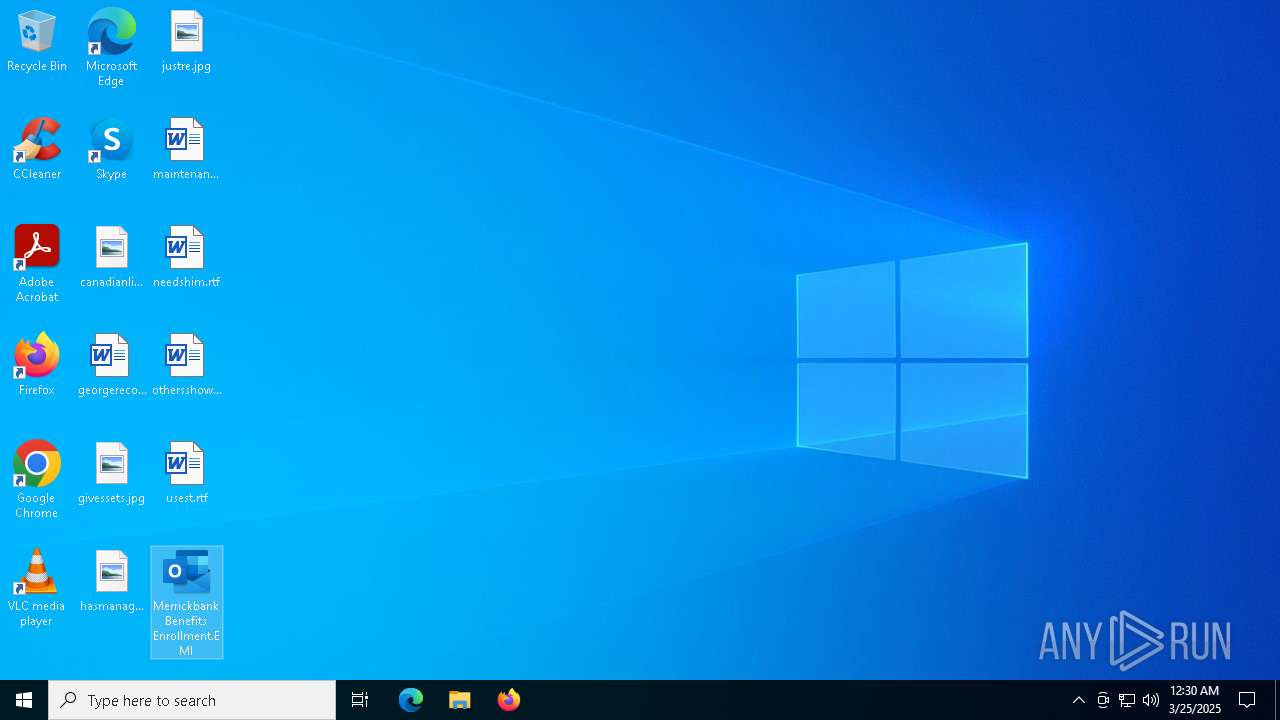
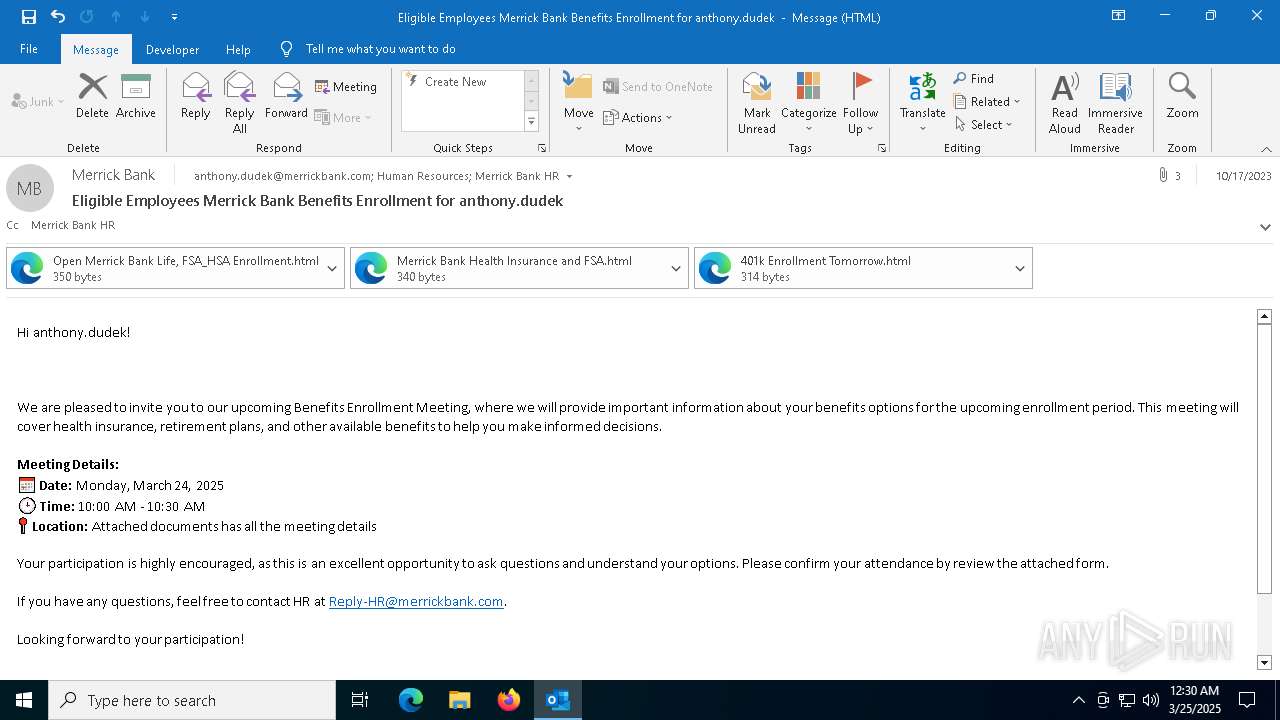
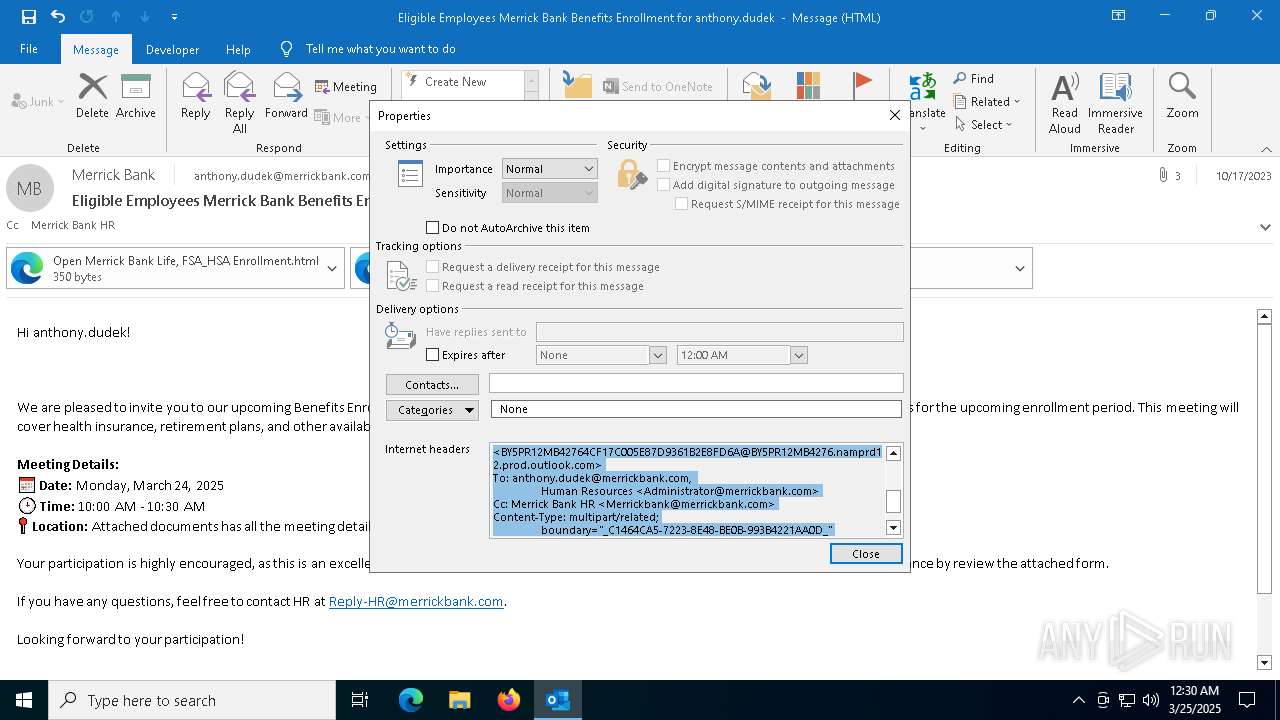
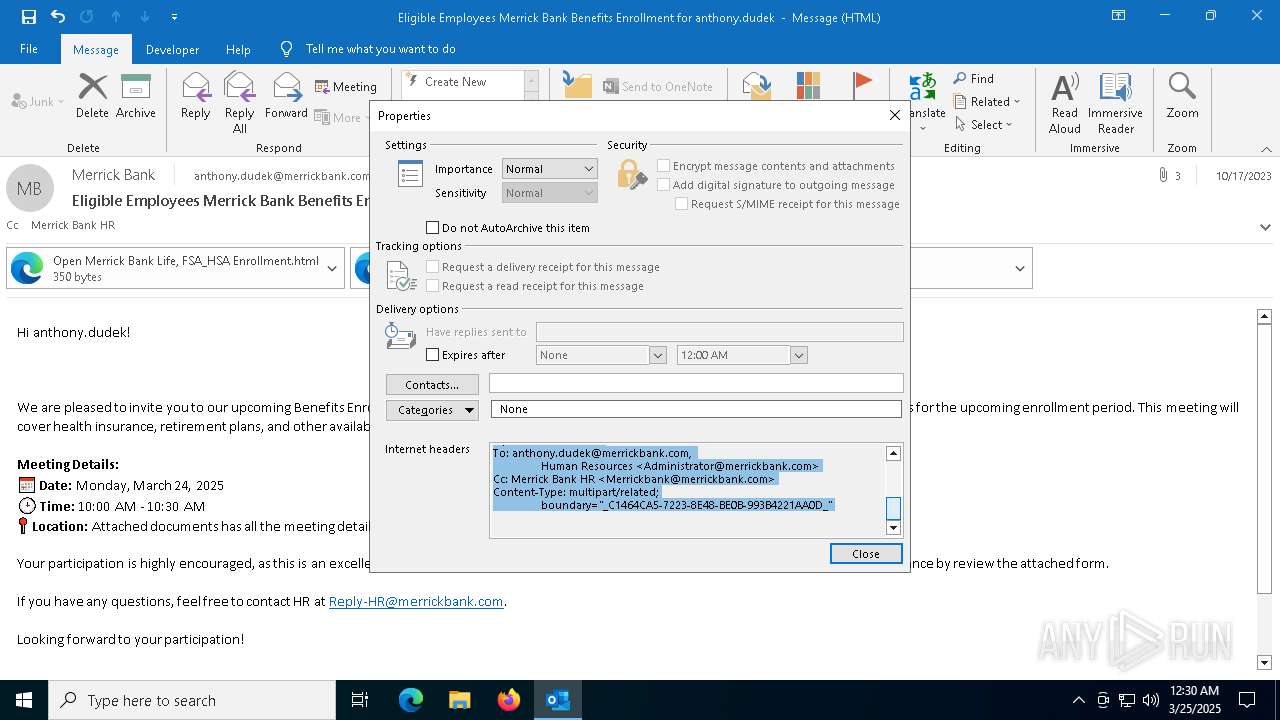
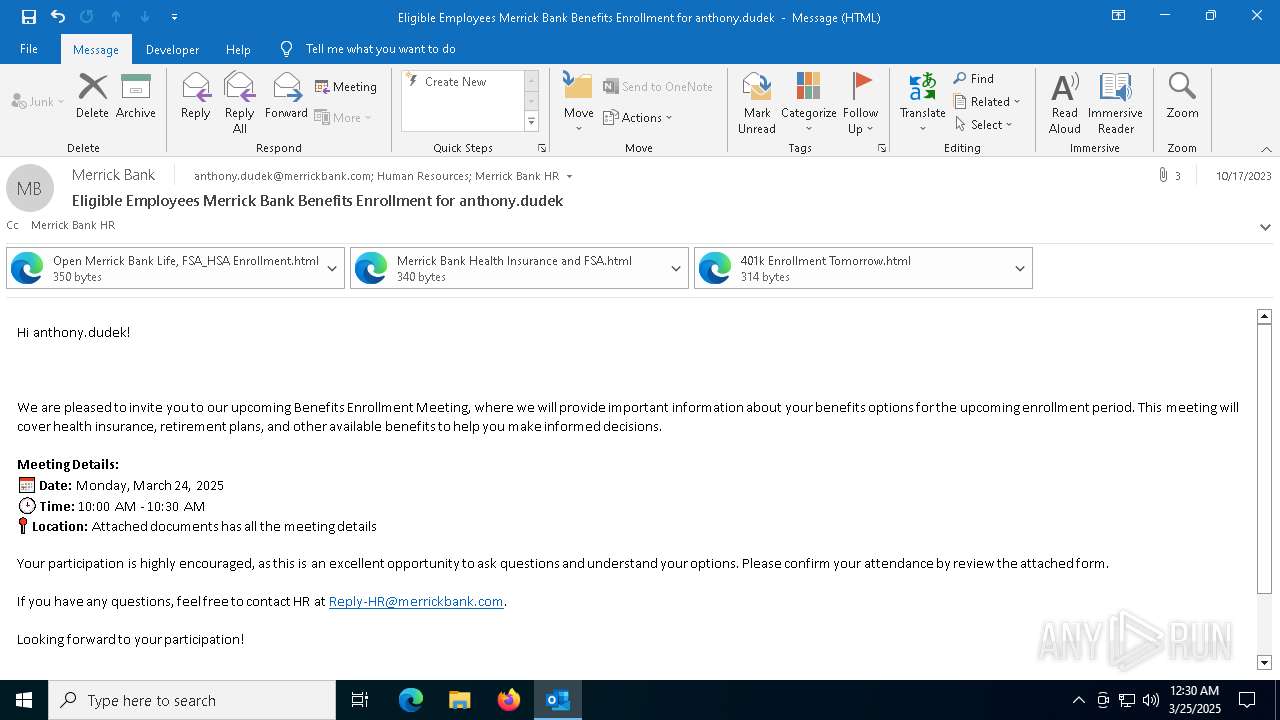
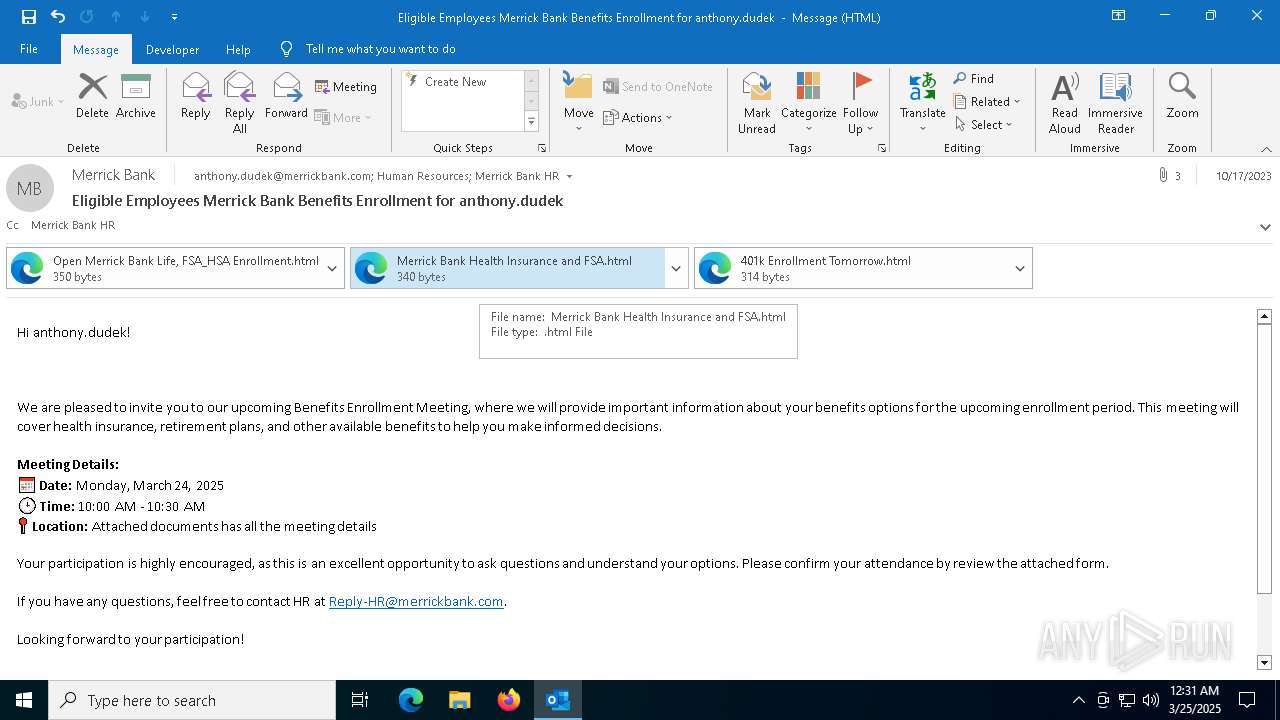
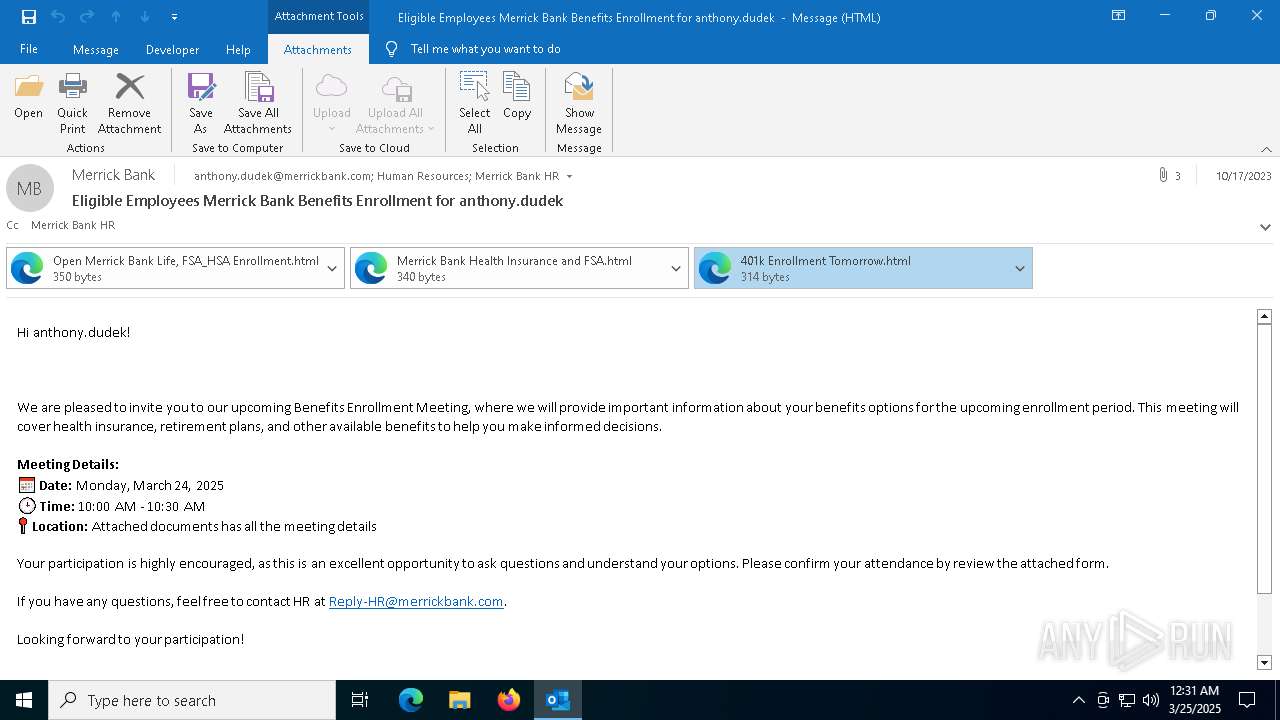
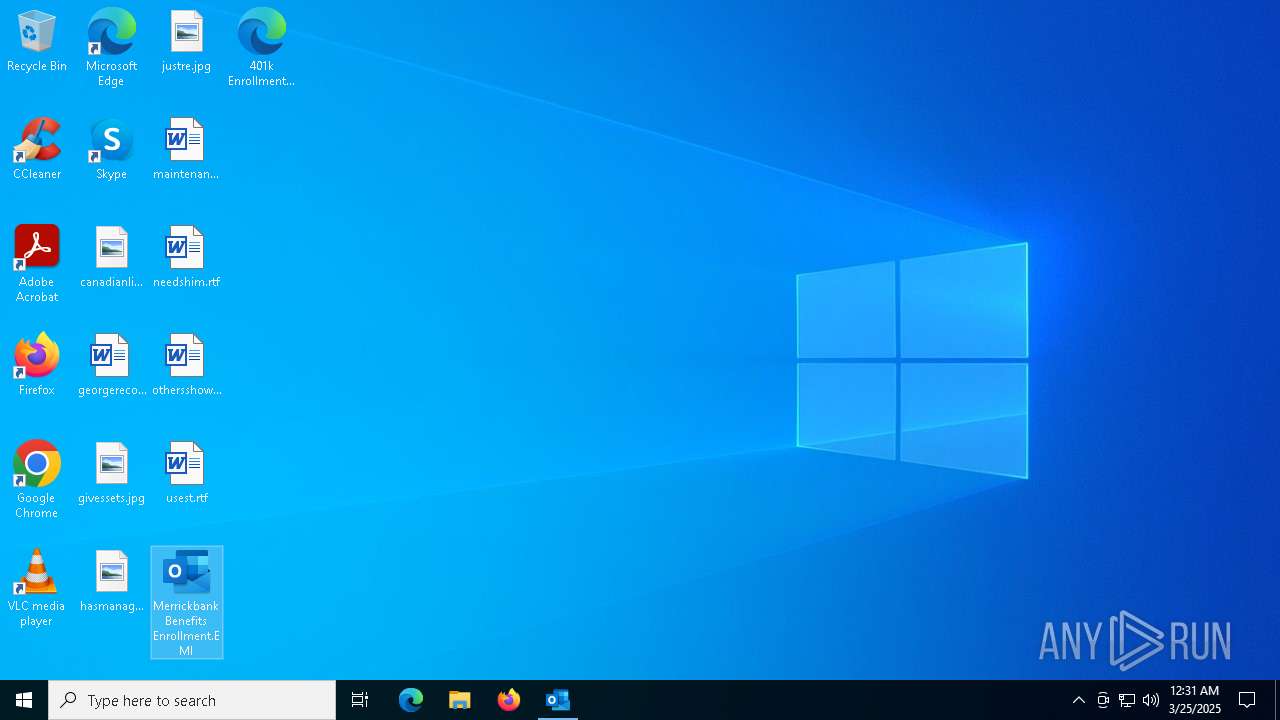
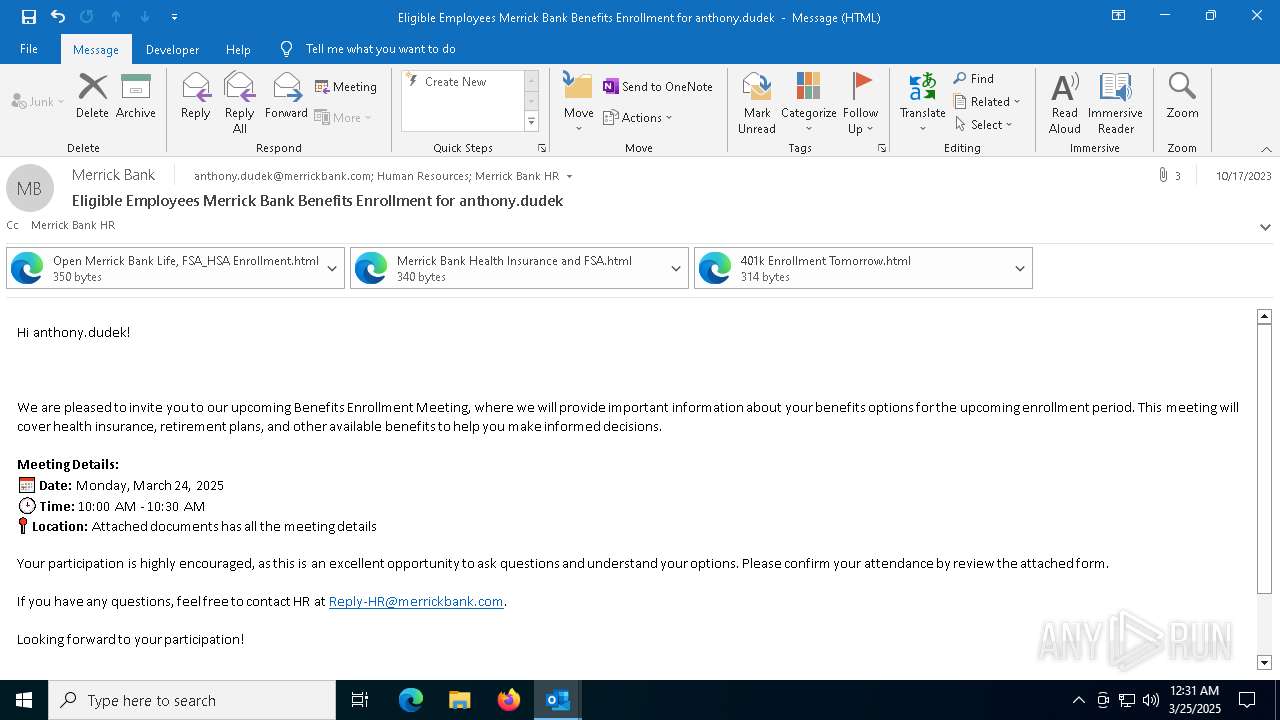
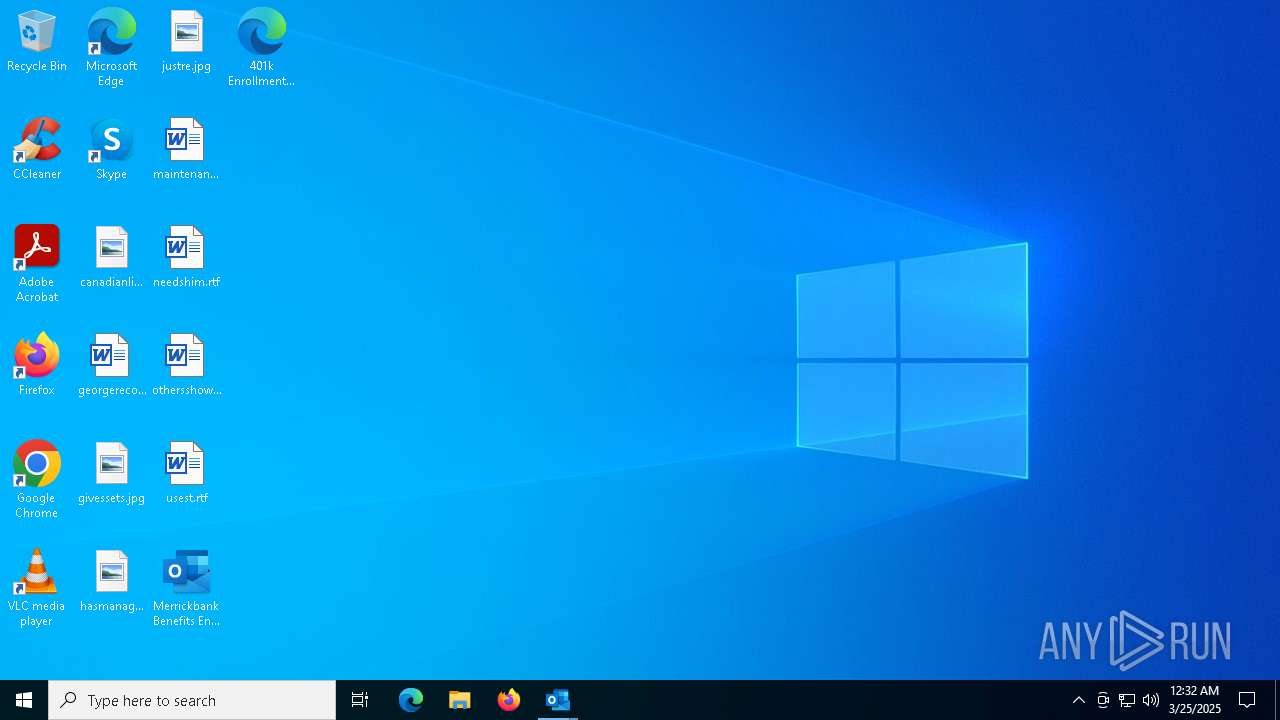
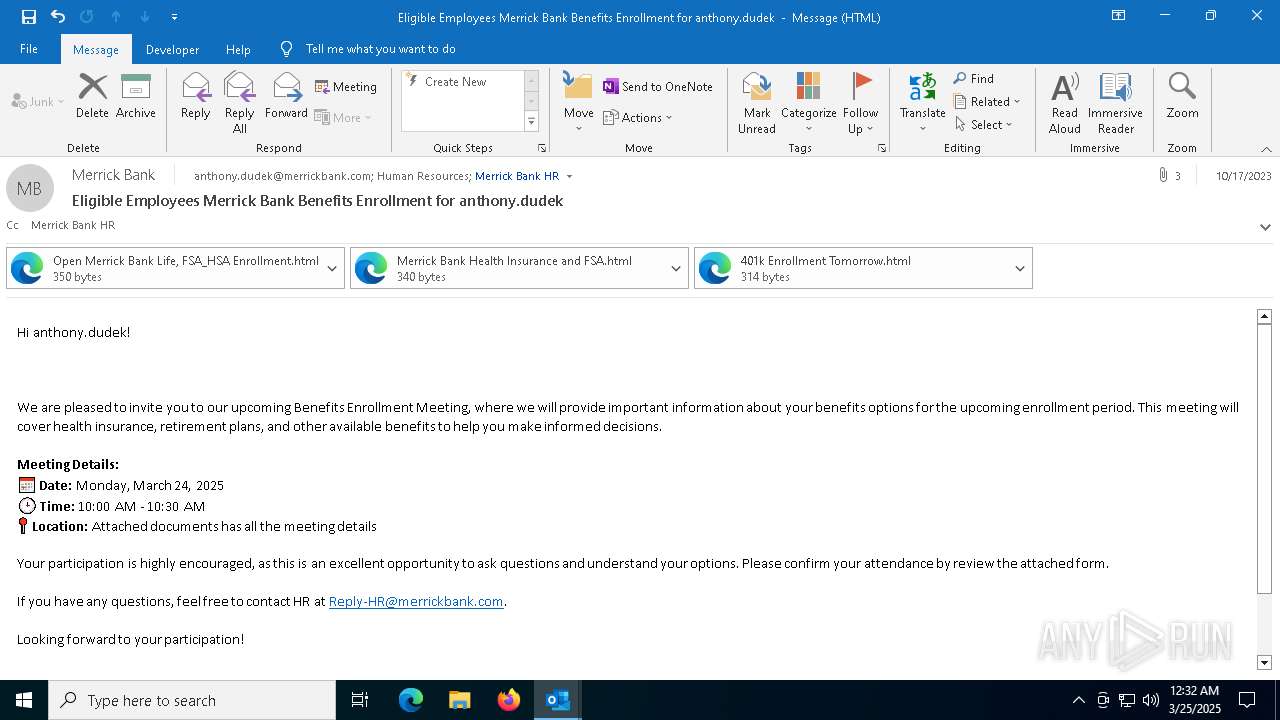
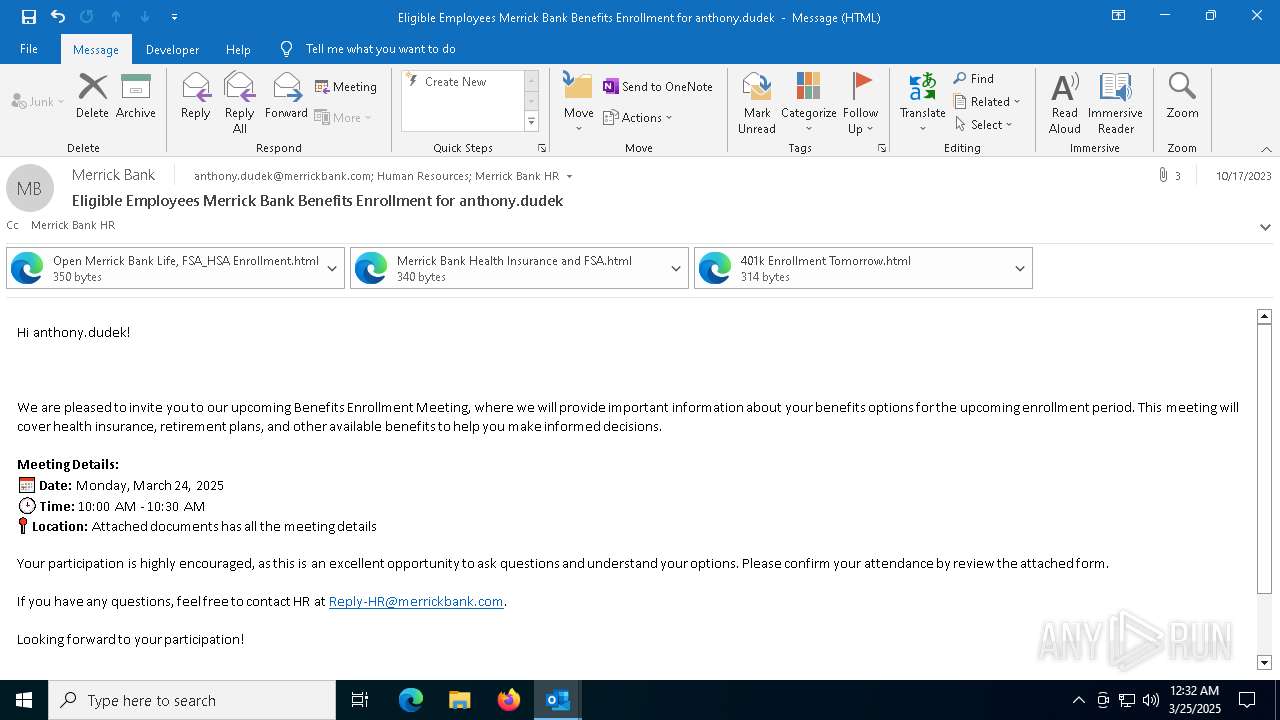
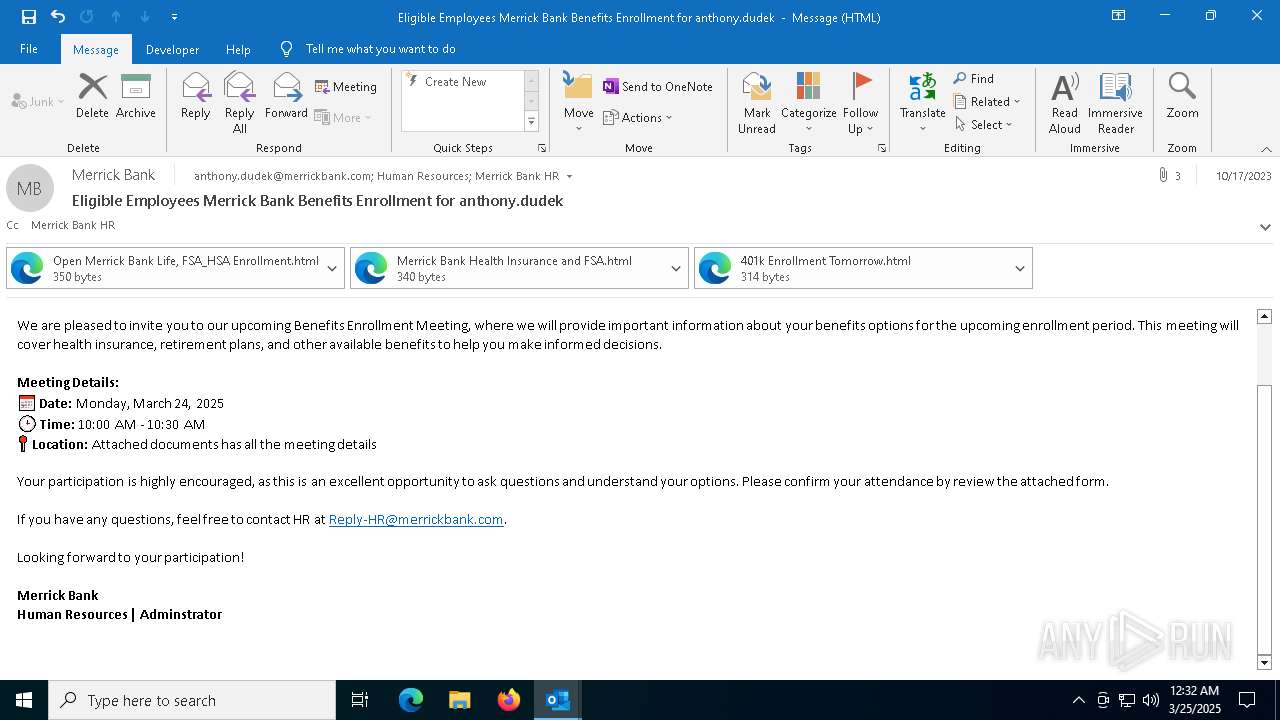
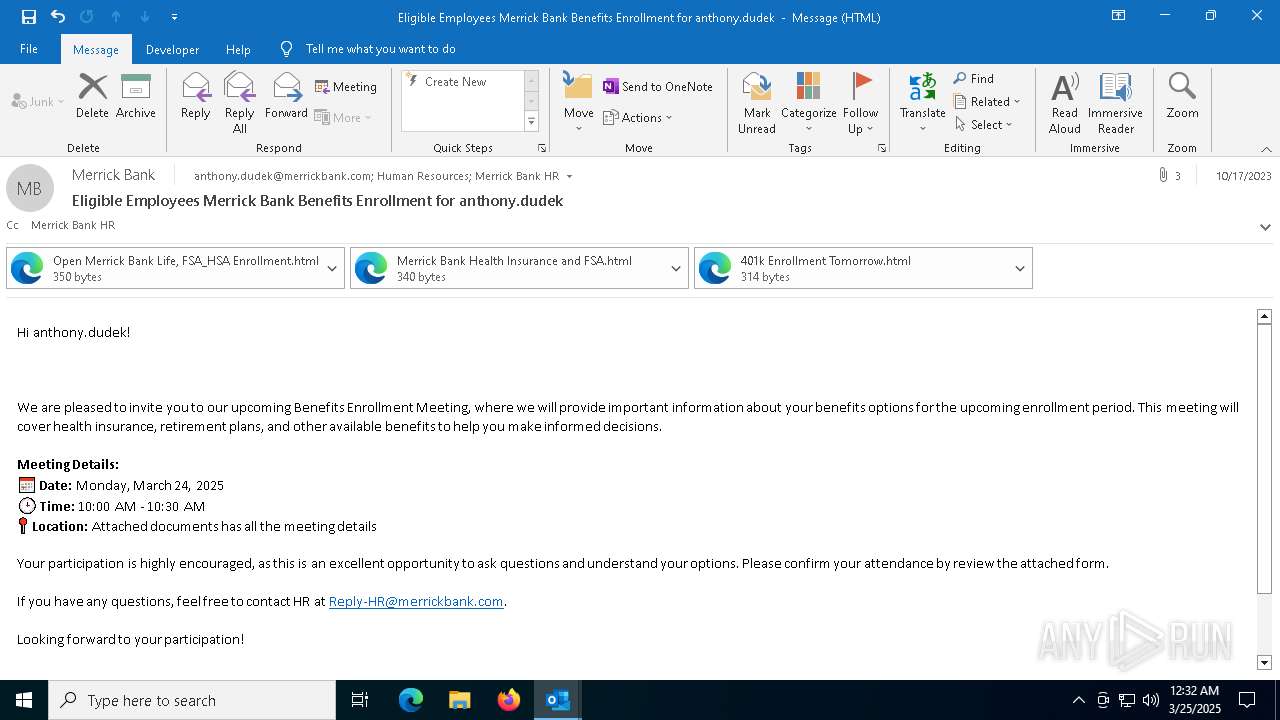
| File name: | Message.eml |
| Full analysis: | https://app.any.run/tasks/0b9ff655-e2de-442b-855f-a28b86ec6557 |
| Verdict: | Malicious activity |
| Analysis date: | March 25, 2025, 00:29:36 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | text/plain |
| File info: | Unicode text, UTF-8 (with BOM) text, with CRLF line terminators |
| MD5: | AF246CB5035E88993285771F5C026597 |
| SHA1: | ECF28976C52899496DBBFB5CFECD15FD9E8A6A45 |
| SHA256: | 9B640C368DCBBB090B20372DDDA9F6B39AD48ED4A5C4FFDC93413DB9244AEBA4 |
| SSDEEP: | 384:hinYjQq8A8dFQElaRM6iGnlswqNhbZKnilNGwyNP36IPNCKPYMAfc:gqRiTaLiGlsJNhbIifday4NCKP/AU |
MALICIOUS
Email came from third-party service (Amazon SES)
- OUTLOOK.EXE (PID: 2320)
SUSPICIOUS
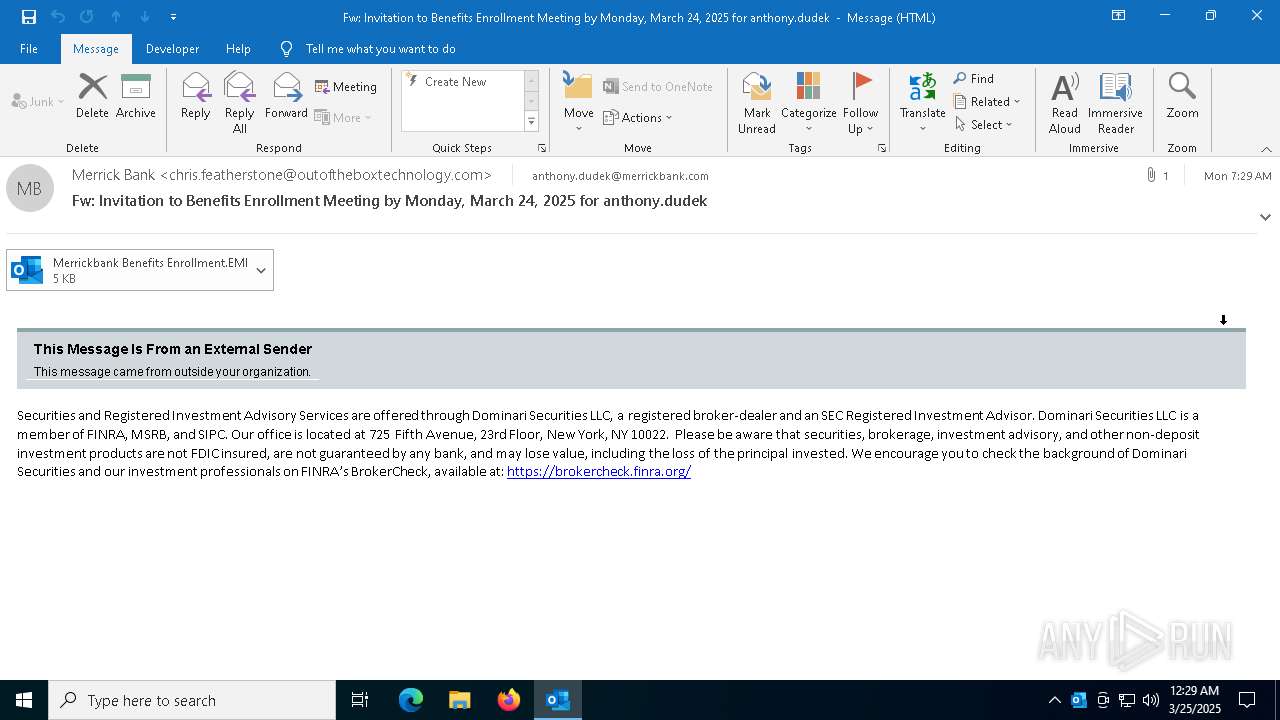
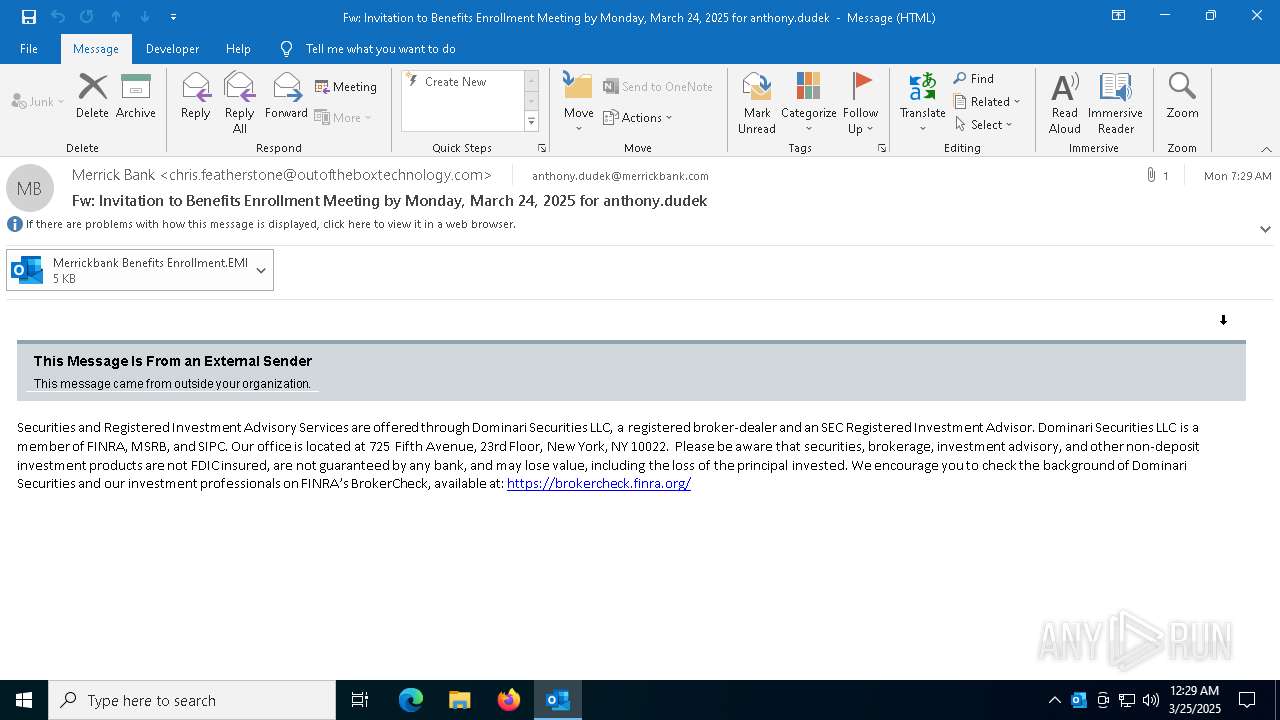
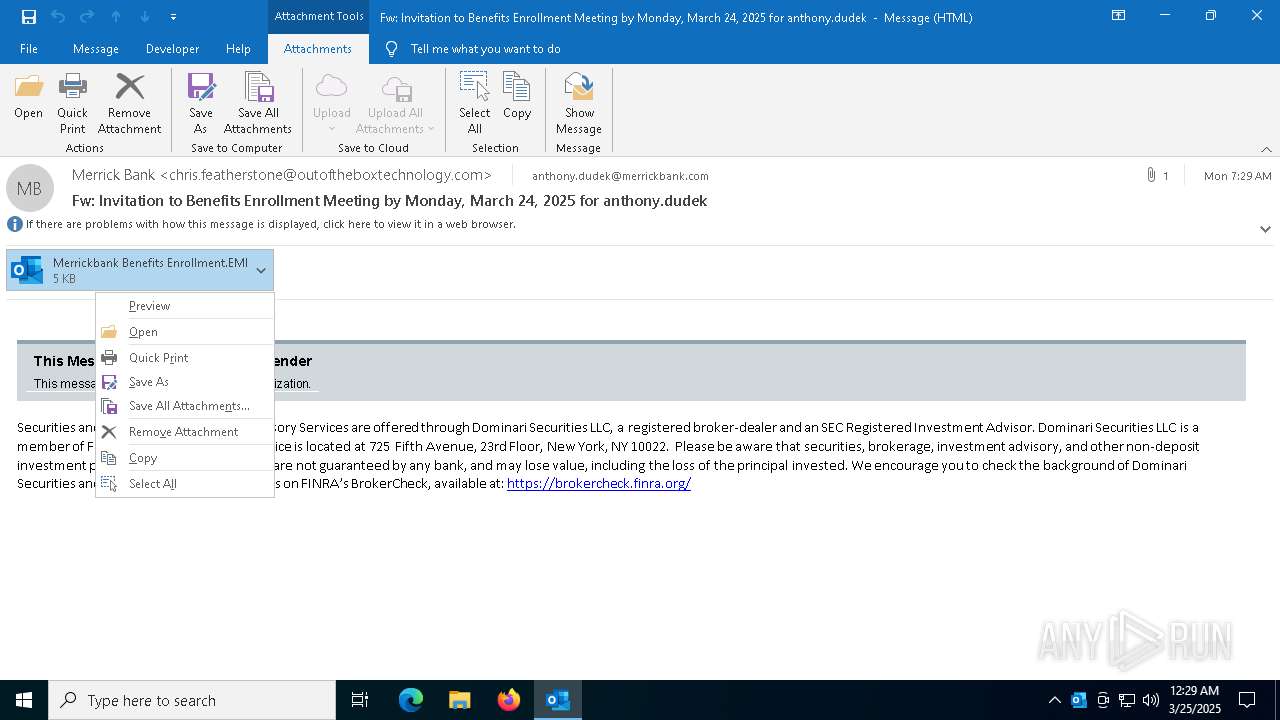
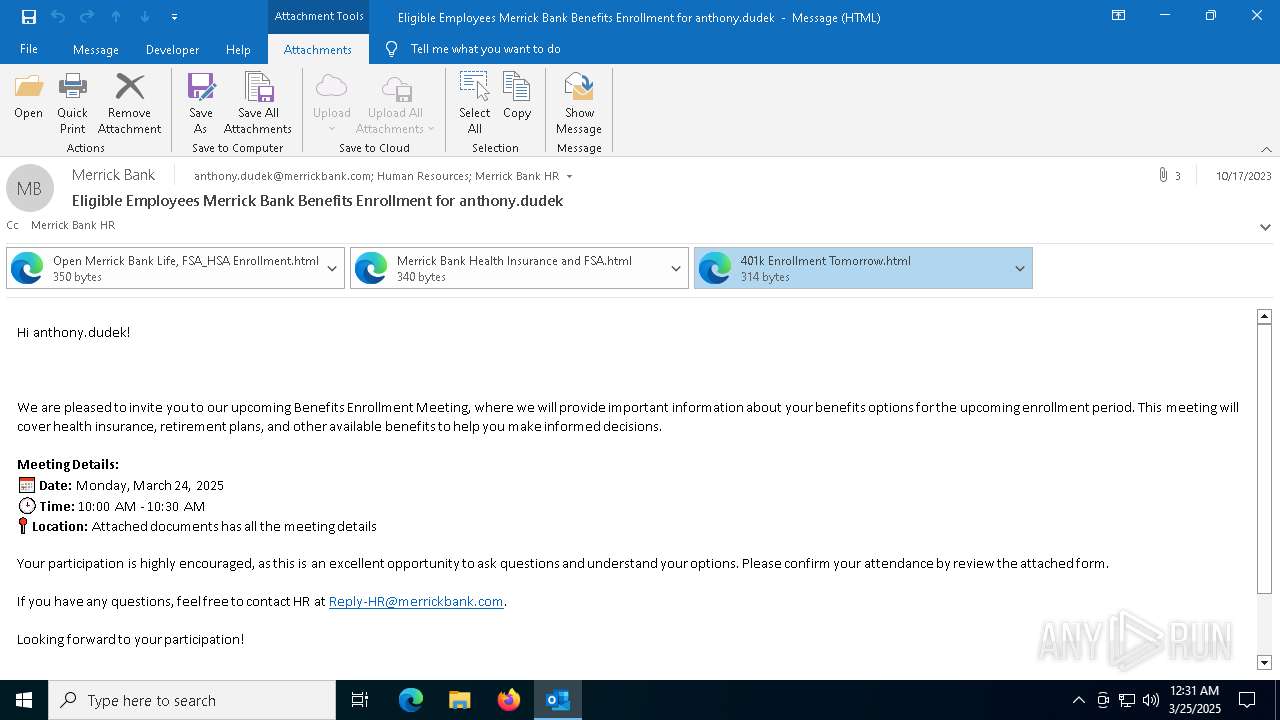
Email with suspicious attachment
- OUTLOOK.EXE (PID: 2320)
INFO
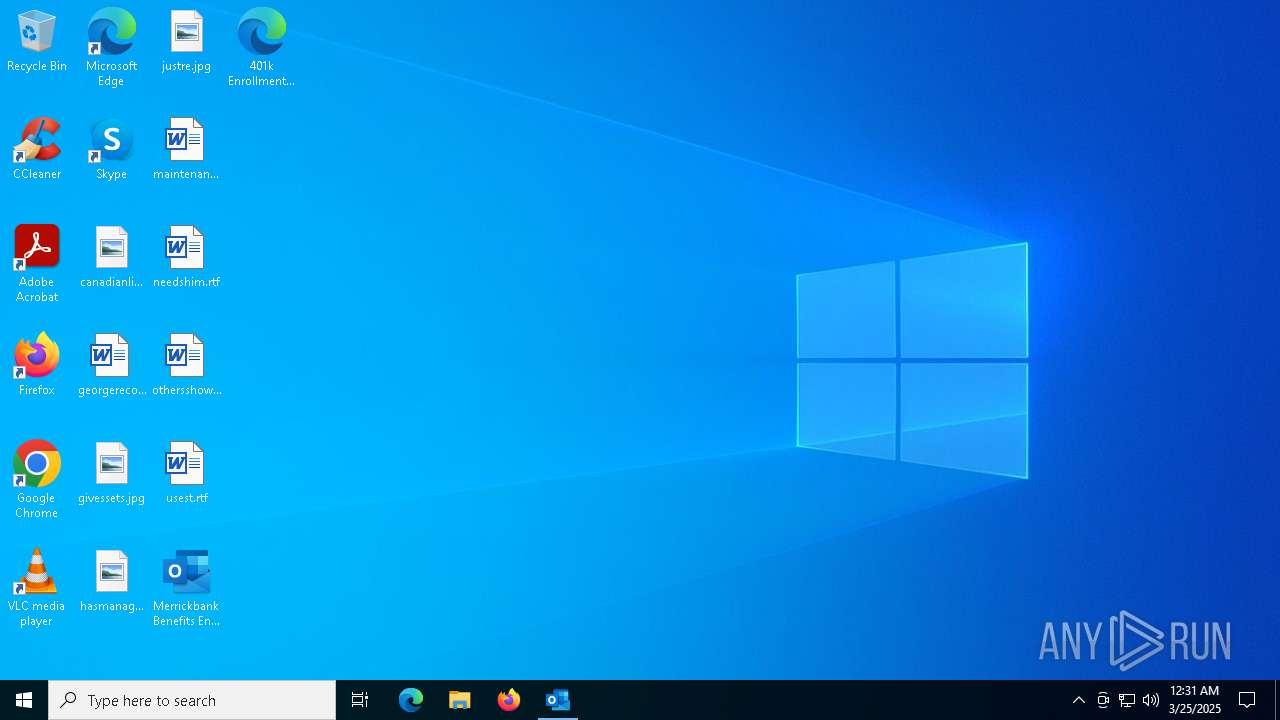
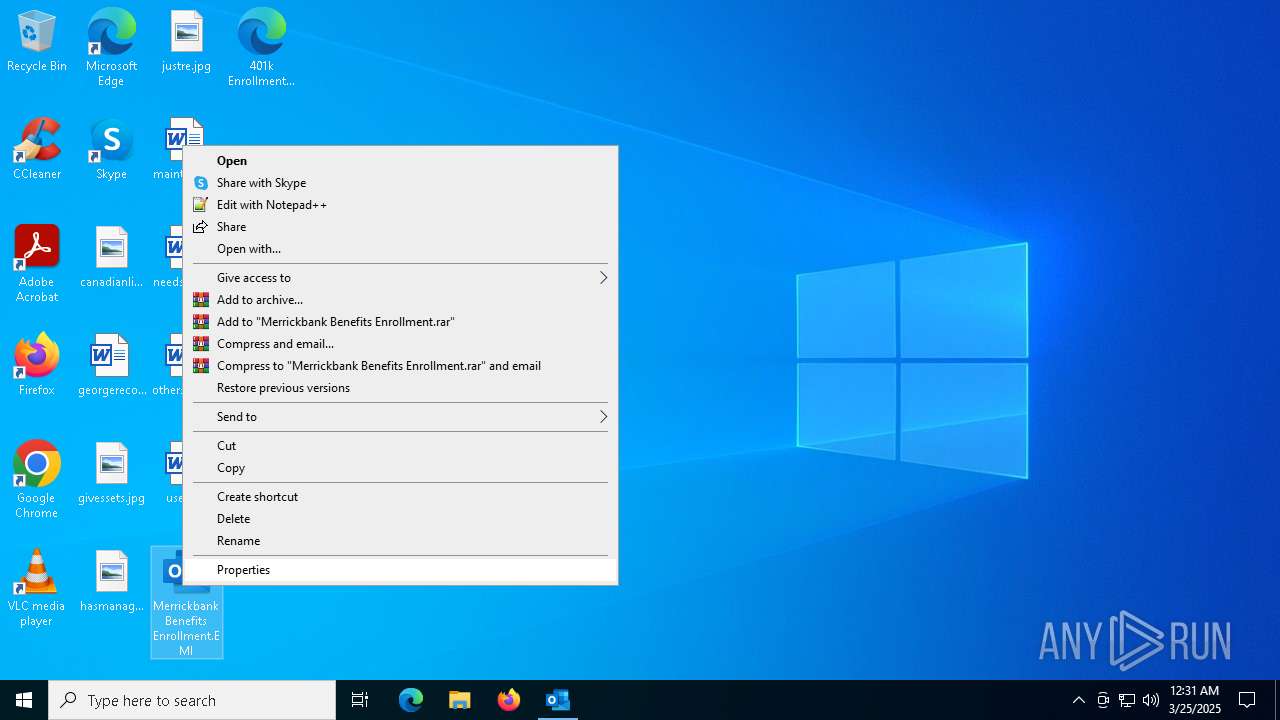
Manual execution by a user
- OUTLOOK.EXE (PID: 7444)
- OUTLOOK.EXE (PID: 5544)
- OUTLOOK.EXE (PID: 7940)
Email verification fail (SPF, DKIM or DMARC)
- OUTLOOK.EXE (PID: 2320)
Email with attachments
- OUTLOOK.EXE (PID: 2320)
Reads the software policy settings
- slui.exe (PID: 5228)
Checks proxy server information
- slui.exe (PID: 5228)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .txt | | | Text - UTF-8 encoded (100) |
|---|
Total processes
145
Monitored processes
8
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2320 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml C:\Users\admin\AppData\Local\Temp\Message.eml | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 5228 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5544 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\Desktop\Merrickbank Benefits Enrollment.EMl" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 7444 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\Desktop\Merrickbank Benefits Enrollment.EMl" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 7452 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "A6FAA89A-E3DE-4766-BEB5-FF8F1095491F" "32EBEAEC-37E5-46AA-938C-4433E1D58C44" "7444" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 7540 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) | |||||||||||||||
| 7700 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "CD99FA68-8D7B-469B-8293-3AFCE3B23B20" "8AF95790-E260-4CFA-B32C-4F8832AD89FB" "2320" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | OUTLOOK.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Exit code: 0 Version: 0.12.2.0 Modules
| |||||||||||||||
| 7940 | "C:\Program Files\Microsoft Office\Root\Office16\OUTLOOK.EXE" /eml "C:\Users\admin\Desktop\Merrickbank Benefits Enrollment.EMl" | C:\Program Files\Microsoft Office\root\Office16\OUTLOOK.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
24 672
Read events
23 267
Write events
1 197
Delete events
208
Modification events
| (PID) Process: | (2320) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | v': |
Value: 76273A001009000004000000000000004864C7041D9DDB0196000000010000008E000000430043003A005C00550073006500720073005C00610064006D0069006E005C0041007000700044006100740061005C0052006F0061006D0069006E0067005C004D006900630072006F0073006F00660074005C00540065006D0070006C0061007400650073005C004E006F0072006D0061006C0045006D00610069006C002E0064006F0074006D00000000000000 | |||
| (PID) Process: | (2320) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Resiliency\StartupItems |
| Operation: | delete value | Name: | v': |
Value: ❶:ऐ | |||
| (PID) Process: | (2320) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Resiliency\StartupItems |
| Operation: | delete value | Name: | j>: |
Value: 㹪:ऐ | |||
| (PID) Process: | (2320) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Resiliency\StartupItems |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2320) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Outlook\Resiliency |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2320) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Roaming |
| Operation: | write | Name: | RoamingConfigurableSettings |
Value: DC00000000000000803A090041060100010001000000000000000000000000000000000000000000201C0000201C00008051010080510100805101008051010080F4030080F4030080F403002C01000084030000805101000000000084030000805101000A0000001E0000001E000000000000000000000080510100010000000100000000000000000000000000000000000000008D2700008D2700008D2700010000000A000000805101000000300000003000000030000000000084030000805101001E0000008403000080510100050000000500000005000000 | |||
| (PID) Process: | (2320) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Roaming |
| Operation: | write | Name: | RoamingConfigurableSettings |
Value: DC00000000000000803A0900E90703000200190000001D0033002603000000000000000000000000201C0000201C00008051010080510100805101008051010080F4030080F4030080F403002C01000084030000805101000000000084030000805101000A0000001E0000001E000000000000000000000080510100010000000100000000000000000000000000000000000000008D2700008D2700008D2700010000000A000000805101000000300000003000000030000000000084030000805101001E0000008403000080510100050000000500000005000000 | |||
| (PID) Process: | (2320) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Roaming |
| Operation: | write | Name: | RoamingLastSyncTimeOutlook |
Value: E90703000200190000001D0033003603 | |||
| (PID) Process: | (2320) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\Roaming |
| Operation: | write | Name: | RoamingLastWriteTimeOutlook |
Value: E90703000200190000001D0033003603 | |||
| (PID) Process: | (2320) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\OUTLOOK\2320 |
| Operation: | write | Name: | 0 |
Value: 0B0E10B459640059236248B5AF2122D1065F78230046C59F829BD0A3E7ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC9062E226E745A7A6A31357452514C512B4E36497471594230494F4C433762703843745A4D6E6B4475414D2B6253413D22CA0D4201A201C2190000C50E8908C91003783634C5119012D2120B6F00750074006C006F006F006B002E00650078006500C51620C517808004C91808323231322D44656300 | |||
Executable files
0
Suspicious files
18
Text files
13
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2320 | OUTLOOK.EXE | C:\Users\admin\Documents\Outlook Files\Outlook1.pst | — | |
MD5:— | SHA256:— | |||
| 2320 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:B496118C1A55DD555535FB928C300E1B | SHA256:33F489042D4FC4B36245C893415AD741E439C0FBC5872372B216D5FEF3F7DFD6 | |||
| 2320 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:C777B9B13225DD5EA3B709913B007C0F | SHA256:4A0AC28559658F25979731EC2E2E204FE80E646F37CF9AFF99591402E92AA07E | |||
| 2320 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | binary | |
MD5:0BBEDBE65D529A83D458D6526145E2AD | SHA256:F5E7FDED7887B5235D7A33796629D2A057CAED455093A0D8ADAD0E9E2B2FE3D6 | |||
| 2320 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntitiesUpdated.bin | text | |
MD5:B10FF77016EF312D57D674F0DC9C8216 | SHA256:76352AEF3C80510FC5F11FF9523CBBBBBD60DE3E5A9A7D14DC76394BB7F0CC6B | |||
| 2320 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:D09FBF9E17B1C0823A67B31B31F00BA1 | SHA256:B6CC4652115D67629155748E21E09848183F660996A5274A76C2AC476D241896 | |||
| 2320 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | binary | |
MD5:3730A354BB56E40FB557B212DC0D82D7 | SHA256:4A762653B696293868B330AE927157608828300CF153222321812E85FA069539 | |||
| 2320 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\3B3800A6-5F56-41B4-8FA9-F2DD961F29F9 | xml | |
MD5:5BB63F300215ACD4BEA8AB27DEC0B5D7 | SHA256:C4B1902C560ED96B90633A0E1D2C1A7C69EE2E0EBAF8A4496BF95109A21732F4 | |||
| 2320 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\Content.Outlook\TCOF84VI\Merrickbank Benefits Enrollment.EMl | text | |
MD5:BC61D47F3012EEB3CD3429C0EDE8140B | SHA256:3BEB492ABB267881DEA3D9876E59A6B4B49E3621A54A34EE248A1A1C91EF7C97 | |||
| 2320 | OUTLOOK.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_363582827213C09529A76F35FB615187 | binary | |
MD5:1891FA32EFC0DC0D5430E9B66EE16A2C | SHA256:37982AE9FF59C271BA5D3F0F5D37BBE8103A1CBC4D16D5D9D5409A08FDA098CF | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
39
DNS requests
27
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
2320 | OUTLOOK.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2320 | OUTLOOK.EXE | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
2284 | backgroundTaskHost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
6112 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6112 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 40.115.3.253:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.190.160.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
— | — | 52.109.76.240:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 52.123.128.14:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2320 | OUTLOOK.EXE | 52.109.68.129:443 | roaming.officeapps.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
2320 | OUTLOOK.EXE | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
roaming.officeapps.live.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |